Analysis of IS Security and Risk Management at Hewlett-Packard
VerifiedAdded on 2020/04/07
|16
|4024
|37
Report
AI Summary
This report provides a comprehensive analysis of Information System (IS) security and risk management, particularly focusing on the practices of Hewlett-Packard (HP). It explores the importance of IS security in today's business environment, highlighting the increasing exposure to cyber security threats and the need for robust risk management systems. The report delves into various techniques used in risk management, including risk assessment, analysis matrix, and control measures. It examines the identification of threats and vulnerabilities, the development of disaster recovery plans, and the implementation of contingency plans. The report also discusses HP's approach to securing its systems, including the use of firewalls, security modules, and continuous monitoring. Furthermore, it outlines the responsibilities of IS owners and the importance of configuration management. The report concludes by emphasizing the need for a proactive and integrated approach to IS security and risk management to protect assets and ensure business continuity.

Running head: IS SECURITY AND RISK MANAGEMENT
IS Security and Risk Management
Student Name
Institution
IS Security and Risk Management
Student Name
Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IS SECURITY AND RISK MANAGEMENT 2
Information system security and Risk Management at Hewlett-Packard Manufacturing
Company
Introduction
Information System has become a very important infrastructure in any company across
the world. The survival of most companies today is based on the security of their information
system. However, there has never been an integrated model that has the capacity to access the
possible security risks and effectively protect the information as well as the assets. Information
systems such as emails, messengers, e-commerce, chatting, and m-commerce via the internet, are
increasingly exposed to cyber security accidents (Bagchi, 2017). In order to ensure effective
performance of any information System, a company must invest in securing the system. In
addition, a proper risk management system must be put in place. This can only be done through
the employment of several distinct measures. It is indisputable that there is a continued need to
secure information systems (IS) (Anton, Anderson, Mesic, & Scheier, 2004).
There have been increased incidences of IS security and risks (Kaschek, Kop, & Claudia,
2008). Information system security and risk management require continuous assessment of any
risk that may be exposed to the system. Discovery of any risk should be prevented within the
shortest time possible. The major component of Information system security is risk management
process (Pfleeger & Pfleeger, 2012). The process should be incorporated alongside risk
assessment. The process of risk management should be done through the installation of
preventive measures of future security problems to the system. SI risk assessment practice is in
compliance with the security standards that have been set by HIPAA as well as CEISP. Risk
assessment enables organizations to determine risk levels that are acceptable to them. They are
then able to set appropriate security requirements.
Information system security and Risk Management at Hewlett-Packard Manufacturing
Company
Introduction
Information System has become a very important infrastructure in any company across
the world. The survival of most companies today is based on the security of their information
system. However, there has never been an integrated model that has the capacity to access the
possible security risks and effectively protect the information as well as the assets. Information
systems such as emails, messengers, e-commerce, chatting, and m-commerce via the internet, are
increasingly exposed to cyber security accidents (Bagchi, 2017). In order to ensure effective
performance of any information System, a company must invest in securing the system. In
addition, a proper risk management system must be put in place. This can only be done through
the employment of several distinct measures. It is indisputable that there is a continued need to
secure information systems (IS) (Anton, Anderson, Mesic, & Scheier, 2004).
There have been increased incidences of IS security and risks (Kaschek, Kop, & Claudia,
2008). Information system security and risk management require continuous assessment of any
risk that may be exposed to the system. Discovery of any risk should be prevented within the
shortest time possible. The major component of Information system security is risk management
process (Pfleeger & Pfleeger, 2012). The process should be incorporated alongside risk
assessment. The process of risk management should be done through the installation of
preventive measures of future security problems to the system. SI risk assessment practice is in
compliance with the security standards that have been set by HIPAA as well as CEISP. Risk
assessment enables organizations to determine risk levels that are acceptable to them. They are
then able to set appropriate security requirements.

IS SECURITY AND RISK MANAGEMENT 3
Investigation, tools, and techniques
According to Information System (IS) security experts, one of the main techniques of risk
management process is a risk assessment. The assessment should be done by professionals who
are well trained and can easily identify risks in the information system before the system
becomes vulnerable. Risk management refers to continuous a process that involves analysis,
planning, monitoring and implementation of security measures of an information system
(Kovacich, 2003). The process has since become a policy in most organizations across the world.
Risk assessment which is a type of risk management process is executed in an interval of time. It
can be done on yearly basis or on demand, based on the security requirement of the given
Information System. It is important to note that risk management is a process that entails a
sequence of events and activities.
There are structuring and re-configuration processes that are involved in risk
management. Organizations often tend to generate instantiations that are favorable to them. It is
necessary to conduct an assessment of an organization’s IS the security controls from time to
time. However, the continuous assessment cannot fully secure an information system (Tipton &
Nozaki, 2012). A fully secure system demands for continuous monitoring of the system. A
development life cycle of the system should also be put in place to monitor the effectiveness of
the system over time. One technique that Hewlett-Packard Company uses for securing the system
is through continued monitoring of the systems security details. In addition, all the changes that
are made to the system are documented so that there is a reference whenever there is a security
Investigation, tools, and techniques
According to Information System (IS) security experts, one of the main techniques of risk
management process is a risk assessment. The assessment should be done by professionals who
are well trained and can easily identify risks in the information system before the system
becomes vulnerable. Risk management refers to continuous a process that involves analysis,
planning, monitoring and implementation of security measures of an information system
(Kovacich, 2003). The process has since become a policy in most organizations across the world.
Risk assessment which is a type of risk management process is executed in an interval of time. It
can be done on yearly basis or on demand, based on the security requirement of the given
Information System. It is important to note that risk management is a process that entails a
sequence of events and activities.
There are structuring and re-configuration processes that are involved in risk
management. Organizations often tend to generate instantiations that are favorable to them. It is
necessary to conduct an assessment of an organization’s IS the security controls from time to
time. However, the continuous assessment cannot fully secure an information system (Tipton &
Nozaki, 2012). A fully secure system demands for continuous monitoring of the system. A
development life cycle of the system should also be put in place to monitor the effectiveness of
the system over time. One technique that Hewlett-Packard Company uses for securing the system
is through continued monitoring of the systems security details. In addition, all the changes that
are made to the system are documented so that there is a reference whenever there is a security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IS SECURITY AND RISK MANAGEMENT 4
threat to the system. Reference can also be made when a risk is discovered in the information
system (Jones & Ashenden, 2005).
Based on the result of security assessment report, remediation actions would be
conducted at a later stage. The final security status is reported to the officials who are in charge
of the system. HP company management has made effort and ensured that there is periodic
review of the information system’s security status. The security techniques are based on the
guidance of NIST SP800-37. The company has come up with their own approaches that they use
in managing their information systems and the possible changes that may be associated with
them. Responsibilities of an owner of the information system would be greatly reduced if
configuration management is done so that there is only one common security control. However,
HP is a multinational company and has the financial capacity to employ enough personnel who
can effectively manage their systems. In addition, Hewlett-Packard’s information system
administrators have accorded priority to volatile security controls in the system since they have a
greater impact in any organization (Alberts & Dorofee, 2002).
Risk analysis matrix and control
It is almost impossible to develop an integrated security model that can be used to
address all the risks associated with an information system (Bidgoli, 2016). The proposed risk
analysis matrix is through adaptation of software risk management. One of the attributes of
software quality is the software itself. The security risk should, therefore, be investigated in
terms of the software risk. Security risk refers to the damage or attacks that are made towards an
information system. According to the risk analysis matrix, damages that are made on the assets
of any organization as a result of cybersecurity can be categorized according to the vulnerability
and threats to the assets.
threat to the system. Reference can also be made when a risk is discovered in the information
system (Jones & Ashenden, 2005).
Based on the result of security assessment report, remediation actions would be
conducted at a later stage. The final security status is reported to the officials who are in charge
of the system. HP company management has made effort and ensured that there is periodic
review of the information system’s security status. The security techniques are based on the
guidance of NIST SP800-37. The company has come up with their own approaches that they use
in managing their information systems and the possible changes that may be associated with
them. Responsibilities of an owner of the information system would be greatly reduced if
configuration management is done so that there is only one common security control. However,
HP is a multinational company and has the financial capacity to employ enough personnel who
can effectively manage their systems. In addition, Hewlett-Packard’s information system
administrators have accorded priority to volatile security controls in the system since they have a
greater impact in any organization (Alberts & Dorofee, 2002).
Risk analysis matrix and control
It is almost impossible to develop an integrated security model that can be used to
address all the risks associated with an information system (Bidgoli, 2016). The proposed risk
analysis matrix is through adaptation of software risk management. One of the attributes of
software quality is the software itself. The security risk should, therefore, be investigated in
terms of the software risk. Security risk refers to the damage or attacks that are made towards an
information system. According to the risk analysis matrix, damages that are made on the assets
of any organization as a result of cybersecurity can be categorized according to the vulnerability
and threats to the assets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IS SECURITY AND RISK MANAGEMENT 5
The security analysis matrix shows four steps involved in the security risk analysis. In the
first step, assets, vulnerabilities, and threats of a given organization are identified. They are then
evaluated.
The resultant outputs are finally used to carry out security risk analysis. Finally, risk
mitigation measures are put in place to reduce, and where possible eliminate threats that the
assets may be exposed to. The mitigation measures, therefore, play a very crucial role in
minimizing security risks. Domain analysis which is the first step of customizing security risk
analysis is meant to improve the accuracy of the model. The threats, assets, and vulnerabilities
are therefore analyzed based on their domains (Kramer, 2013). For example, information
systems of a financial institution are completely different from those of a financial institution or
a learning institution. The analysis that follows is that of classification of the assets, vulnerability
and the threats. Assets can be classified as data, documents, software, hardware, and
Vulnerability Threats Assets
Risk
The security analysis matrix shows four steps involved in the security risk analysis. In the
first step, assets, vulnerabilities, and threats of a given organization are identified. They are then
evaluated.
The resultant outputs are finally used to carry out security risk analysis. Finally, risk
mitigation measures are put in place to reduce, and where possible eliminate threats that the
assets may be exposed to. The mitigation measures, therefore, play a very crucial role in
minimizing security risks. Domain analysis which is the first step of customizing security risk
analysis is meant to improve the accuracy of the model. The threats, assets, and vulnerabilities
are therefore analyzed based on their domains (Kramer, 2013). For example, information
systems of a financial institution are completely different from those of a financial institution or
a learning institution. The analysis that follows is that of classification of the assets, vulnerability
and the threats. Assets can be classified as data, documents, software, hardware, and
Vulnerability Threats Assets
Risk
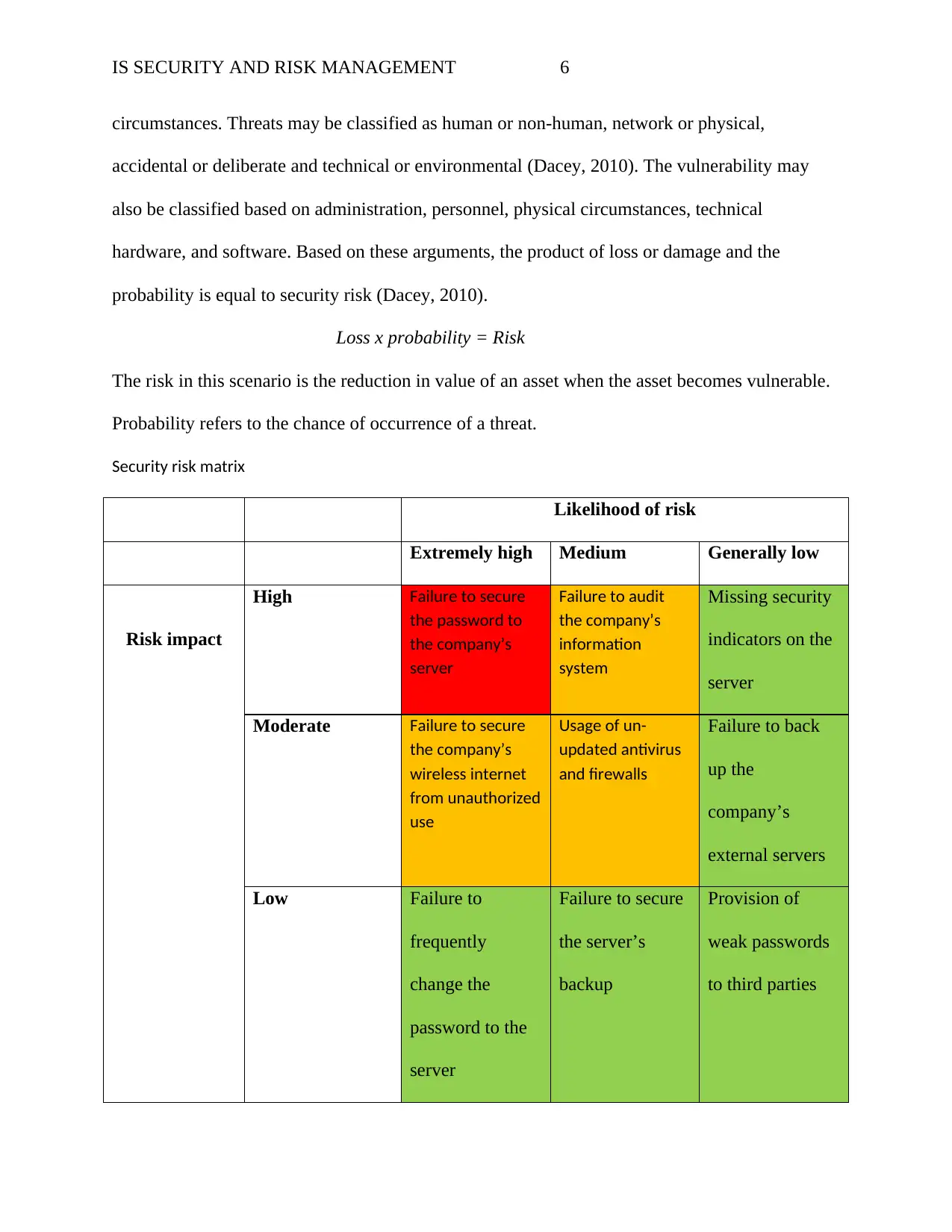
IS SECURITY AND RISK MANAGEMENT 6
circumstances. Threats may be classified as human or non-human, network or physical,
accidental or deliberate and technical or environmental (Dacey, 2010). The vulnerability may
also be classified based on administration, personnel, physical circumstances, technical
hardware, and software. Based on these arguments, the product of loss or damage and the
probability is equal to security risk (Dacey, 2010).
Loss x probability = Risk
The risk in this scenario is the reduction in value of an asset when the asset becomes vulnerable.
Probability refers to the chance of occurrence of a threat.
Security risk matrix
Likelihood of risk
Extremely high Medium Generally low
Risk impact
High Failure to secure
the password to
the company’s
server
Failure to audit
the company’s
information
system
Missing security
indicators on the
server
Moderate Failure to secure
the company’s
wireless internet
from unauthorized
use
Usage of un-
updated antivirus
and firewalls
Failure to back
up the
company’s
external servers
Low Failure to
frequently
change the
password to the
server
Failure to secure
the server’s
backup
Provision of
weak passwords
to third parties
circumstances. Threats may be classified as human or non-human, network or physical,
accidental or deliberate and technical or environmental (Dacey, 2010). The vulnerability may
also be classified based on administration, personnel, physical circumstances, technical
hardware, and software. Based on these arguments, the product of loss or damage and the
probability is equal to security risk (Dacey, 2010).
Loss x probability = Risk
The risk in this scenario is the reduction in value of an asset when the asset becomes vulnerable.
Probability refers to the chance of occurrence of a threat.
Security risk matrix
Likelihood of risk
Extremely high Medium Generally low
Risk impact
High Failure to secure
the password to
the company’s
server
Failure to audit
the company’s
information
system
Missing security
indicators on the
server
Moderate Failure to secure
the company’s
wireless internet
from unauthorized
use
Usage of un-
updated antivirus
and firewalls
Failure to back
up the
company’s
external servers
Low Failure to
frequently
change the
password to the
server
Failure to secure
the server’s
backup
Provision of
weak passwords
to third parties
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IS SECURITY AND RISK MANAGEMENT 7
Analysis of relevant threats and vulnerabilities
The first step of any analysis of threats and vulnerabilities is the identification of threats
that could expose vulnerabilities of an information system. The identification can be done
through consideration of the connections and dependencies of the system. In addition, inherited
risks, software faults, controls, incorrect file permissions and personal changes must also be
closely monitored. Possible vulnerabilities that are associated with every threat are then
considered. There is the possibility of a vulnerability being associated with a series of threats if
not just one threat. Inputs are then collected from past risk assessments, security advisories,
security test results, audits among many others.
Disaster Recovery (DR) plan
The success of any disaster recovery plan is determined by how well the design is. It is,
therefore, necessary to ensure efficient operations during disaster recovery (Kim & Solomon,
2016). The recovery should start with a strong defense that provides border protection. The
defense should be provided by an external firewall that borders the services of VPN and the
router (Velliquette, 2004). Hewlett-Packard has installed an external firewall to their VPN and
all their routers. All the three have configurations that have the capacity to transverse all the
boundaries of the organization or company (Swanson, 2011). Firewall is the main component of
the security infrastructure of any information system. Computer security network should
incorporate firewall that incorporates hardware specifications as well as software specifications.
Issues of redundancy and physical security should also be taken into account. There should then
be an approach plan for fulfilling the primary needs of the organization or company in the course
Analysis of relevant threats and vulnerabilities
The first step of any analysis of threats and vulnerabilities is the identification of threats
that could expose vulnerabilities of an information system. The identification can be done
through consideration of the connections and dependencies of the system. In addition, inherited
risks, software faults, controls, incorrect file permissions and personal changes must also be
closely monitored. Possible vulnerabilities that are associated with every threat are then
considered. There is the possibility of a vulnerability being associated with a series of threats if
not just one threat. Inputs are then collected from past risk assessments, security advisories,
security test results, audits among many others.
Disaster Recovery (DR) plan
The success of any disaster recovery plan is determined by how well the design is. It is,
therefore, necessary to ensure efficient operations during disaster recovery (Kim & Solomon,
2016). The recovery should start with a strong defense that provides border protection. The
defense should be provided by an external firewall that borders the services of VPN and the
router (Velliquette, 2004). Hewlett-Packard has installed an external firewall to their VPN and
all their routers. All the three have configurations that have the capacity to transverse all the
boundaries of the organization or company (Swanson, 2011). Firewall is the main component of
the security infrastructure of any information system. Computer security network should
incorporate firewall that incorporates hardware specifications as well as software specifications.
Issues of redundancy and physical security should also be taken into account. There should then
be an approach plan for fulfilling the primary needs of the organization or company in the course
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IS SECURITY AND RISK MANAGEMENT 8
of disaster recovery (Velliquette, 2004). Meanwhile, the management of the company should
certain their prioritized services so as to secure their systems further.
In addition, companies should sign against the limited functionalities during disaster
recovery (Velliquette, 2004). The management of HP has equally made that as a rule to be
followed by its staff in charge of information system management. Any recovery approach that
has been agreed upon should be configured with the perimeter defense such that the perimeter
defense would automatically shift to the state of pre-disaster just before any normal operation.
The current policy of the company should be considered during the development of the firewall
contingency plan. Security modules such as A CERT can be used to test the disaster policy of
many firewalls. A method should be implemented to monitor traffic that moves from pre-disaster
state to post-disaster state. The method can be tested with the use of relevant data from the very
company. A border router that has packet filtering can be used in non-application type of
vulnerabilities.
Proposal for a contingency plan
Information System plays a very important role in the world today. It should, therefore,
be in a position to operate without any disruption (Khosrowpour, 1996). A contingency plan is
intended to set back the system back into operation whenever there is a disruption. Most of the
disruptions are as a result of security risks. The plan simply revolves the acronym of the system
and then sets the information system back into operation. A robust contingency plan should
incorporate ISCOs and other disaster recovery plans (Kovacich, 2003). Hewlett-Packard
company has recovery disaster plans which is in accordance with International security
management Acts. The company has incorporated a disaster recovery that can be used to retrieve
its information system’s acronym in the event of any disruption
of disaster recovery (Velliquette, 2004). Meanwhile, the management of the company should
certain their prioritized services so as to secure their systems further.
In addition, companies should sign against the limited functionalities during disaster
recovery (Velliquette, 2004). The management of HP has equally made that as a rule to be
followed by its staff in charge of information system management. Any recovery approach that
has been agreed upon should be configured with the perimeter defense such that the perimeter
defense would automatically shift to the state of pre-disaster just before any normal operation.
The current policy of the company should be considered during the development of the firewall
contingency plan. Security modules such as A CERT can be used to test the disaster policy of
many firewalls. A method should be implemented to monitor traffic that moves from pre-disaster
state to post-disaster state. The method can be tested with the use of relevant data from the very
company. A border router that has packet filtering can be used in non-application type of
vulnerabilities.
Proposal for a contingency plan
Information System plays a very important role in the world today. It should, therefore,
be in a position to operate without any disruption (Khosrowpour, 1996). A contingency plan is
intended to set back the system back into operation whenever there is a disruption. Most of the
disruptions are as a result of security risks. The plan simply revolves the acronym of the system
and then sets the information system back into operation. A robust contingency plan should
incorporate ISCOs and other disaster recovery plans (Kovacich, 2003). Hewlett-Packard
company has recovery disaster plans which is in accordance with International security
management Acts. The company has incorporated a disaster recovery that can be used to retrieve
its information system’s acronym in the event of any disruption

IS SECURITY AND RISK MANAGEMENT 9
An established plan that consists of the recovery phase, activation phase, and
reconstitution phase should be maximized (Kovacich, 2003). Thereafter, resources and
procedures should be identified. They would assist in maximizing the effectiveness of the
operation. Responsibilities should be assigned to facility personnel. They would provide further
advice that would be of great benefit in the recovery process. Finally, there should be
cooperation among all the persons who are involved in the Contingency planning (Swanson,
2011). There should also be a coordination of external points and associated vendors.
Furthermore, the owners of an Information system must support the development of a proper
ISCPs. The developed ISCOs would be meant for those Information Systems that are ranked
much higher. Hewlett-Packard, being a renowned world leading electronics company, the
company management has taken all these measures in securing and managing their information
systems.
Analysis and report on Controls
How tools are used in the organization with reference to OSI layers
The very first step that should be considered when securing information is the elimination
of any information leakage. The information resources should never be compromised at any cost.
The physical layer of OSI model explains that obvious things should never be considered as
being obvious. In many occasions, technologists have failed to realize that simple measures are
equally very important in life (Pace, 2004). Hewlett-Packard Company for an instant has put in
place stringent measures to secure leakage of information from the company. Simply obtaining a
clue of a resource is enough to declare it as one that has been compromised. There should a
proper plan for recovering information in the event that the information data is compromised. A
good recovery plan is judged based on its success in the event that information resource has been
An established plan that consists of the recovery phase, activation phase, and
reconstitution phase should be maximized (Kovacich, 2003). Thereafter, resources and
procedures should be identified. They would assist in maximizing the effectiveness of the
operation. Responsibilities should be assigned to facility personnel. They would provide further
advice that would be of great benefit in the recovery process. Finally, there should be
cooperation among all the persons who are involved in the Contingency planning (Swanson,
2011). There should also be a coordination of external points and associated vendors.
Furthermore, the owners of an Information system must support the development of a proper
ISCPs. The developed ISCOs would be meant for those Information Systems that are ranked
much higher. Hewlett-Packard, being a renowned world leading electronics company, the
company management has taken all these measures in securing and managing their information
systems.
Analysis and report on Controls
How tools are used in the organization with reference to OSI layers
The very first step that should be considered when securing information is the elimination
of any information leakage. The information resources should never be compromised at any cost.
The physical layer of OSI model explains that obvious things should never be considered as
being obvious. In many occasions, technologists have failed to realize that simple measures are
equally very important in life (Pace, 2004). Hewlett-Packard Company for an instant has put in
place stringent measures to secure leakage of information from the company. Simply obtaining a
clue of a resource is enough to declare it as one that has been compromised. There should a
proper plan for recovering information in the event that the information data is compromised. A
good recovery plan is judged based on its success in the event that information resource has been
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IS SECURITY AND RISK MANAGEMENT 10
compromised. There are some harmful tools towards OSI model. However, the problem can be
eliminated through an analysis. The network layer of an OSI model is where routers and
firewalls operate. The layer provides the best path that links a destination to the source.
It is also within the layer that IP addresses are provided so that variables or systems can
be uniquely identified. A system that is connected to the internet has an IP address. The address
provides a way such that there is contact between the outside world and the system. In order to
find a system on the internet, it is a requirement that one has to know the specific public IP
address of the system. The same applies to applications. Security of the system is therefore
increased through the configuration of the IP addresses such that one cannot easily compromise.
Just like other world leading companies, Hewlett-Packard Company has configured their IP
address. In addition, they have encrypted all their services to further enhance the security of their
information system. The encryption service symbolizes the presentation layer of OSI layer. The
technique scrambles all the available content. Encryption provides a sophisticated special code.
One must, therefore, reveal the code before he or she can access the system. The application
layer of OSI points towards applications that are based on end-user products. The layer supports
authentication and use of other applications (Pace, 2004). The commonly used authentication at
the level is a password which is assigned to a unique ID.
An individual must key in the unique ID alongside a password in order to access
information data. Failure to present the unique ID and a correct password mean that the
individual would not have access to the system. It, therefore, reinforces the security of the system
since it eliminates people who are not supposed to access the system. An account can be
redesigned so that it adheres to a policy. For example, it can specify the length of the password, a
combination of letters, digits and or even special characters. The duration over which one can
compromised. There are some harmful tools towards OSI model. However, the problem can be
eliminated through an analysis. The network layer of an OSI model is where routers and
firewalls operate. The layer provides the best path that links a destination to the source.
It is also within the layer that IP addresses are provided so that variables or systems can
be uniquely identified. A system that is connected to the internet has an IP address. The address
provides a way such that there is contact between the outside world and the system. In order to
find a system on the internet, it is a requirement that one has to know the specific public IP
address of the system. The same applies to applications. Security of the system is therefore
increased through the configuration of the IP addresses such that one cannot easily compromise.
Just like other world leading companies, Hewlett-Packard Company has configured their IP
address. In addition, they have encrypted all their services to further enhance the security of their
information system. The encryption service symbolizes the presentation layer of OSI layer. The
technique scrambles all the available content. Encryption provides a sophisticated special code.
One must, therefore, reveal the code before he or she can access the system. The application
layer of OSI points towards applications that are based on end-user products. The layer supports
authentication and use of other applications (Pace, 2004). The commonly used authentication at
the level is a password which is assigned to a unique ID.
An individual must key in the unique ID alongside a password in order to access
information data. Failure to present the unique ID and a correct password mean that the
individual would not have access to the system. It, therefore, reinforces the security of the system
since it eliminates people who are not supposed to access the system. An account can be
redesigned so that it adheres to a policy. For example, it can specify the length of the password, a
combination of letters, digits and or even special characters. The duration over which one can
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IS SECURITY AND RISK MANAGEMENT 11
use a password can equally be altered. Such move would simply increase the security level of the
system network (Pace, 2004).
Organizational units covered by the security policy
The information system has security policies that must be observed in every company. At
Hewlett-Packard Company, there are users who have been assigned appropriate policy rights.
The users are the only ones who are able to modify the security policy of the company. If a new
computer if brought into the company domain, then the security policy of the domain would
apply to the new computer (Brotby, 2009). The policy of the domain overrides any change that
an individual may make to the system at the level of computer desktop (Syngress, 2003).
Security policy is a preserve of computers. There are also security groups which are in use in the
company by many employees.
Security policy enables an individual to apply a given security profile to several
computers that are meant to be secured. On the other hand, security group provides standardized
rights that are to be adhered to by all the members of a given group. Organizational units can be
regrouped to form logical units that are to be used by the users, resource objects and groups as
well. The adjustment is always done through a hierarchy which is nested within a domain
(Johnson, 2014). Organizational units that are based on a given domain operate independently.
Every domain, therefore, has the capacity to fulfill the demands of its own hierarchy. Similarly,
domains that are coordinated from one central authority can employ common organizational unit
hierarchies.
Business Contingency Plan (BCP) based on the risk plan
It is sound superfluous for a company to plan for disaster when all its systems are
smoothly functioning. Despite that, some degree of care must be undertaken. Hewlett-Packard
use a password can equally be altered. Such move would simply increase the security level of the
system network (Pace, 2004).
Organizational units covered by the security policy
The information system has security policies that must be observed in every company. At
Hewlett-Packard Company, there are users who have been assigned appropriate policy rights.
The users are the only ones who are able to modify the security policy of the company. If a new
computer if brought into the company domain, then the security policy of the domain would
apply to the new computer (Brotby, 2009). The policy of the domain overrides any change that
an individual may make to the system at the level of computer desktop (Syngress, 2003).
Security policy is a preserve of computers. There are also security groups which are in use in the
company by many employees.
Security policy enables an individual to apply a given security profile to several
computers that are meant to be secured. On the other hand, security group provides standardized
rights that are to be adhered to by all the members of a given group. Organizational units can be
regrouped to form logical units that are to be used by the users, resource objects and groups as
well. The adjustment is always done through a hierarchy which is nested within a domain
(Johnson, 2014). Organizational units that are based on a given domain operate independently.
Every domain, therefore, has the capacity to fulfill the demands of its own hierarchy. Similarly,
domains that are coordinated from one central authority can employ common organizational unit
hierarchies.
Business Contingency Plan (BCP) based on the risk plan
It is sound superfluous for a company to plan for disaster when all its systems are
smoothly functioning. Despite that, some degree of care must be undertaken. Hewlett-Packard

IS SECURITY AND RISK MANAGEMENT 12
Company uses logic manage and cloud based tools as its business continuity tools. The tools are
able to retrofit all the company’s data in case of disaster and then load it back to the system. All
gaps would hence be eliminated. The business continuity plan hence foster confidence among the
managers of the company’s information system. In addition it increases their efficiency and
encourages them to embrace innovation.
Best practices in security risk management
Best practices are necessary for ensuring that the information system of a company is
completely secured. Some of the best practices include;
(i) Expertise should be considered when choosing the individuals in charge of
managing the company’s information system. The chosen personnel should avoid
access to the company’s security controls. The individuals should also have been
certified by international associations in charge of privacy such as CIPM or CIPP
among others (Brotby, 2009).
(ii) Business associates of the company must adhere to security and privacy
requirements of the same level. They must also comply with HIPAA
(iii) The management of information system of the company must regularly provide
an audit report of the system and recommendations. The report should be detailed
detailing all possible vulnerabilities.
Conclusion
Effectiveness in the performance of a given information system is based on its
management. There are several security risks that Information systems are exposed to. Managers
of organizations and companies must, therefore, invest in securing the information systems. A
Company uses logic manage and cloud based tools as its business continuity tools. The tools are
able to retrofit all the company’s data in case of disaster and then load it back to the system. All
gaps would hence be eliminated. The business continuity plan hence foster confidence among the
managers of the company’s information system. In addition it increases their efficiency and
encourages them to embrace innovation.
Best practices in security risk management
Best practices are necessary for ensuring that the information system of a company is
completely secured. Some of the best practices include;
(i) Expertise should be considered when choosing the individuals in charge of
managing the company’s information system. The chosen personnel should avoid
access to the company’s security controls. The individuals should also have been
certified by international associations in charge of privacy such as CIPM or CIPP
among others (Brotby, 2009).
(ii) Business associates of the company must adhere to security and privacy
requirements of the same level. They must also comply with HIPAA
(iii) The management of information system of the company must regularly provide
an audit report of the system and recommendations. The report should be detailed
detailing all possible vulnerabilities.
Conclusion
Effectiveness in the performance of a given information system is based on its
management. There are several security risks that Information systems are exposed to. Managers
of organizations and companies must, therefore, invest in securing the information systems. A
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





