Security Risk Analysis and Management Report - InelliTrade
VerifiedAdded on 2022/09/07
|26
|6268
|39
Report
AI Summary
This report provides a comprehensive security risk analysis and management assessment for InelliTrade, a small organization developing high-frequency trading algorithms. The report begins with an overview of threat modeling, emphasizing its role in optimizing network security by identifying vulnerabilities and facilitating effective mitigation strategies. It then delves into quantitative risk analysis, contrasting it with qualitative methods and highlighting its importance in quantifying potential project impacts. The report includes a detailed analysis of the InelliTrade case study, including impact evaluation, vulnerability descriptions, and threat descriptions. It presents a risk evaluation table and proposes security mitigation techniques, culminating in a plan for implementing these techniques. The analysis covers various aspects of risk management, from identifying and measuring threats to examining and deploying solutions. The report underscores the importance of proactive risk management in safeguarding sensitive information and ensuring business continuity.

Running head: SECURITY RISK ANALYSIS AND MANAGEMENT
SECURITY RISK ANALYSIS AND MANAGEMENT
Name of the Student
Name of the University
Author Note
SECURITY RISK ANALYSIS AND MANAGEMENT
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY RISK ANALYSIS AND MANAGEMENT
Table of Contents
a) Threat modelling......................................................................................................................2
b) Quantitative risk analysis........................................................................................................3
Question 2:.......................................................................................................................................6
About the case study....................................................................................................................6
Impact evaluation table................................................................................................................6
Vulnerability description table....................................................................................................8
Threat description table...............................................................................................................9
Risk evaluation table..................................................................................................................10
Possible security mitigation techniques.....................................................................................12
Plan of security mitigation techniques.......................................................................................15
Question 3......................................................................................................................................17
Reference.......................................................................................................................................22
Table of Contents
a) Threat modelling......................................................................................................................2
b) Quantitative risk analysis........................................................................................................3
Question 2:.......................................................................................................................................6
About the case study....................................................................................................................6
Impact evaluation table................................................................................................................6
Vulnerability description table....................................................................................................8
Threat description table...............................................................................................................9
Risk evaluation table..................................................................................................................10
Possible security mitigation techniques.....................................................................................12
Plan of security mitigation techniques.......................................................................................15
Question 3......................................................................................................................................17
Reference.......................................................................................................................................22

2SECURITY RISK ANALYSIS AND MANAGEMENT
Question 1
a) Threat modelling
Threat tree modeling is a procedure that is used for the purpose of optimizing the network
security by determining the key objectives and vulnerabilities efficiently. Beside this once the
security aspects are determined it becomes easy to prevent the threats and proper mitigation
strategies needed. Threat tree is referred to the system that is used for the purpose of providing
an efficient way for representing the attacks against the system that is represented in the form of
tree. Threat tree is introduced with the aim of determining the cyber threat attacks efficiently so
that it can make sure that a better comprised way of ordering the conceptualized components can
be maintained effectively. The major benefits that are offered with the use of threat tree
modeling is that it helps in keeping the people motivated and ensures that the goals are being set
right for managing the performance.
The threat trees helps determining the rapid visualization process effectively. This
focuses on determining the individual components with the potential threats so that it becomes
easy to prevent the threats. The security controls assists in determining the adequacy within the
existing security controls that can be treated against the possible threats (Hossain et al. 2015).
Beside this with the help of threat tree policy it becomes easy to map the security policies for the
purpose of identifying the actions. This also ensures that the challenges are mitigated
successfully with the help of determined process.
The major aim behind using threat modelling in networking is that it helps in determining
the efforts that are needed to be applied within the system so that it becomes easy to maintain the
performance. However it has been observed that the performance and factors associated with the
system can change depending upon the features that are added towards the system (Amara 2017).
Question 1
a) Threat modelling
Threat tree modeling is a procedure that is used for the purpose of optimizing the network
security by determining the key objectives and vulnerabilities efficiently. Beside this once the
security aspects are determined it becomes easy to prevent the threats and proper mitigation
strategies needed. Threat tree is referred to the system that is used for the purpose of providing
an efficient way for representing the attacks against the system that is represented in the form of
tree. Threat tree is introduced with the aim of determining the cyber threat attacks efficiently so
that it can make sure that a better comprised way of ordering the conceptualized components can
be maintained effectively. The major benefits that are offered with the use of threat tree
modeling is that it helps in keeping the people motivated and ensures that the goals are being set
right for managing the performance.
The threat trees helps determining the rapid visualization process effectively. This
focuses on determining the individual components with the potential threats so that it becomes
easy to prevent the threats. The security controls assists in determining the adequacy within the
existing security controls that can be treated against the possible threats (Hossain et al. 2015).
Beside this with the help of threat tree policy it becomes easy to map the security policies for the
purpose of identifying the actions. This also ensures that the challenges are mitigated
successfully with the help of determined process.
The major aim behind using threat modelling in networking is that it helps in determining
the efforts that are needed to be applied within the system so that it becomes easy to maintain the
performance. However it has been observed that the performance and factors associated with the
system can change depending upon the features that are added towards the system (Amara 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SECURITY RISK ANALYSIS AND MANAGEMENT
Threat modelling is one of the iterative modelling procedure that is used for the purpose of
identifying the importance and use of application in respect to other assets. This ensures that the
products and systems are prioritized based on the needs and the impacts.
The major challenge that is faced within the information is the security aspects. There is a
huge need to ensure the security within the information so that it becomes easy to exercise the
security aspects. The threat needs to be arranged hierarchically so that it becomes easy to
determine the impacts that will be created with this risks. This helps in identifying the different
type of attacks that has the possibilities to harm the performance. Thus it can be stated that with
the assist of correct threat tree analysis it becomes easier to determine the threats.
The key benefits that are offered with threat tree is that it helps in identifying the model
efficiently and ensures that proper communication has taken place. Threat planning takes place at
the planning, designing, and after the implementation phases (Kerzner 2017). With the help of
threat modelling it becomes easy to understand the product better and also ensures that the
components are utilized successfully within the application. The threats can be determined easily
and this helps in managing the performance effectively. There are very minimal drawbacks and
thus it can be stated that the risk management can be performed effectively.
b) Quantitative risk analysis
Risk management within a project is a continuous and collaborative process that includes
two different types that are quantitative and qualitative risk analysis techniques. Qualitative risk
analysis is referred to the process that is used for the purpose of assessing the project risks that
arises with individual project (Hopkin 2018). This helps in identifying the project risks that has
the ability to influence the execution of a project. The key objective of the qualitative analysis
risk is to prioritize the risks effectively so that it becomes easy to determine the impact and
Threat modelling is one of the iterative modelling procedure that is used for the purpose of
identifying the importance and use of application in respect to other assets. This ensures that the
products and systems are prioritized based on the needs and the impacts.
The major challenge that is faced within the information is the security aspects. There is a
huge need to ensure the security within the information so that it becomes easy to exercise the
security aspects. The threat needs to be arranged hierarchically so that it becomes easy to
determine the impacts that will be created with this risks. This helps in identifying the different
type of attacks that has the possibilities to harm the performance. Thus it can be stated that with
the assist of correct threat tree analysis it becomes easier to determine the threats.
The key benefits that are offered with threat tree is that it helps in identifying the model
efficiently and ensures that proper communication has taken place. Threat planning takes place at
the planning, designing, and after the implementation phases (Kerzner 2017). With the help of
threat modelling it becomes easy to understand the product better and also ensures that the
components are utilized successfully within the application. The threats can be determined easily
and this helps in managing the performance effectively. There are very minimal drawbacks and
thus it can be stated that the risk management can be performed effectively.
b) Quantitative risk analysis
Risk management within a project is a continuous and collaborative process that includes
two different types that are quantitative and qualitative risk analysis techniques. Qualitative risk
analysis is referred to the process that is used for the purpose of assessing the project risks that
arises with individual project (Hopkin 2018). This helps in identifying the project risks that has
the ability to influence the execution of a project. The key objective of the qualitative analysis
risk is to prioritize the risks effectively so that it becomes easy to determine the impact and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURITY RISK ANALYSIS AND MANAGEMENT
probability. The qualitative risks analysis is used for the purpose of improving the understanding
of the risks that are likely to arise within a project. Beside this qualitative risk assessment is also
considered as one of the fasters and cheapest way of determining and defining the risks. With the
assist of proper qualitative threat analysis it becomes easier to organize (Weber et al. 2016). The
qualitative risk analysis does not focus on analyzing the risks mathematically for the purpose of
identifying the risks. This focuses on using the stakeholder inputs for the purpose of determining
the likelihood and impact.
Quantitative risk analysis is referred to the process of analyzing the risks based on the
priority. These are mainly identified with the help of quantitative rating.
Quantitative analysis helps in quantifying the possible outcomes that has the potential to
impact the project. This also focuses on assessing the poor probability that is present within a
specific project. In order to perform quantitative analysis it becomes very much essential to
identify the risks at the first stage. Once the risks are identified from the list it becomes essential
to prioritize the risks into a risk register. After this the risks are identified and ranked according
to their impacts.
With the assist of quantitative threat analyses process it becomes easier to create realistic
and achievable cost. This process executes on high-quality data with the will develop the project
model. The prioritized list helps in managing the risks effectively.
The key inputs for performing the qualitative risk analysis are risk management plan,
developing the risk register, enterprise environmental factors and processing the assets. The
output that is offered towards the qualitative risk analysis is the updated project documents
(Joslin & Müller 2016). The different types of analysis techniques that has the potential to
probability. The qualitative risks analysis is used for the purpose of improving the understanding
of the risks that are likely to arise within a project. Beside this qualitative risk assessment is also
considered as one of the fasters and cheapest way of determining and defining the risks. With the
assist of proper qualitative threat analysis it becomes easier to organize (Weber et al. 2016). The
qualitative risk analysis does not focus on analyzing the risks mathematically for the purpose of
identifying the risks. This focuses on using the stakeholder inputs for the purpose of determining
the likelihood and impact.
Quantitative risk analysis is referred to the process of analyzing the risks based on the
priority. These are mainly identified with the help of quantitative rating.
Quantitative analysis helps in quantifying the possible outcomes that has the potential to
impact the project. This also focuses on assessing the poor probability that is present within a
specific project. In order to perform quantitative analysis it becomes very much essential to
identify the risks at the first stage. Once the risks are identified from the list it becomes essential
to prioritize the risks into a risk register. After this the risks are identified and ranked according
to their impacts.
With the assist of quantitative threat analyses process it becomes easier to create realistic
and achievable cost. This process executes on high-quality data with the will develop the project
model. The prioritized list helps in managing the risks effectively.
The key inputs for performing the qualitative risk analysis are risk management plan,
developing the risk register, enterprise environmental factors and processing the assets. The
output that is offered towards the qualitative risk analysis is the updated project documents
(Joslin & Müller 2016). The different types of analysis techniques that has the potential to

5SECURITY RISK ANALYSIS AND MANAGEMENT
manage the project are Delphi technique, swift analysis, bow-tie analysis and decision tree
analysis. With the help of this techniques it becomes easy to perform the risk analysis within a
project. The major benefits that are offered with the use of qualitative risk analysis are that it
offers easy presentation, prioritization can be done easily and there is no need to determine the
frequency (Marchewka 2016). Apart from this there are certain disadvantages that comes along
with the use of qualitative method is that it does not allow the determination of probabilities and
does not evaluate the project based on the numerical data. Beside this the cost benefit analysis
becomes difficult and thus it can hamper the budget of the project. However after analyzing the
possible disadvantages and advantages it can be stated that the benefits outweigh the
disadvantages. Thus the offered advantages will ensure that the performance has enhanced
efficiently.
c) Risk management is one of the essential factor that is needed to be controlled properly so that
it can ensure that proper security is offered towards the information stored. Cost benefit analysis
is referred to the systematic approach that is used for the purpose of estimating the strengths and
weaknesses. The risk associated with a project requires to be controlled efficiently so that it can
upgrade the risks within the project (Binder 2016). Cost benefit analysis is used for the purpose
of understanding the costs and this helps in conducting a better process of analyzing the benefits.
The framework requires to be properly analyzed so that it becomes easy to determine the
threats at the first stage and will ensure that the technology has been implemented successfully.
The project needs to be properly managed so that it becomes easy to analyze the key aspects
effectively (Sanjab et al. 2016). The assets need to be prioritized properly so that it becomes easy
to organize the different aspects. Risk management is considered as one of the important factor
as this helps in revealing the threats that are likely to harm the execution of business. Risk
manage the project are Delphi technique, swift analysis, bow-tie analysis and decision tree
analysis. With the help of this techniques it becomes easy to perform the risk analysis within a
project. The major benefits that are offered with the use of qualitative risk analysis are that it
offers easy presentation, prioritization can be done easily and there is no need to determine the
frequency (Marchewka 2016). Apart from this there are certain disadvantages that comes along
with the use of qualitative method is that it does not allow the determination of probabilities and
does not evaluate the project based on the numerical data. Beside this the cost benefit analysis
becomes difficult and thus it can hamper the budget of the project. However after analyzing the
possible disadvantages and advantages it can be stated that the benefits outweigh the
disadvantages. Thus the offered advantages will ensure that the performance has enhanced
efficiently.
c) Risk management is one of the essential factor that is needed to be controlled properly so that
it can ensure that proper security is offered towards the information stored. Cost benefit analysis
is referred to the systematic approach that is used for the purpose of estimating the strengths and
weaknesses. The risk associated with a project requires to be controlled efficiently so that it can
upgrade the risks within the project (Binder 2016). Cost benefit analysis is used for the purpose
of understanding the costs and this helps in conducting a better process of analyzing the benefits.
The framework requires to be properly analyzed so that it becomes easy to determine the
threats at the first stage and will ensure that the technology has been implemented successfully.
The project needs to be properly managed so that it becomes easy to analyze the key aspects
effectively (Sanjab et al. 2016). The assets need to be prioritized properly so that it becomes easy
to organize the different aspects. Risk management is considered as one of the important factor
as this helps in revealing the threats that are likely to harm the execution of business. Risk
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SECURITY RISK ANALYSIS AND MANAGEMENT
management is considered as an imperative to business manager so that the structure can be
organized. Risk management will ensure that the better communication has been offered and
ensures that better focus can be maintained within the project.
The important steps that are related with managing the threats includes identifying the
risks at first stage, measuring the threats, examining the solutions, deploying solution and
monitoring the outputs for the purpose of managing the execution (Khan and Al-Yasiri 2018).
With the assist of this management of risk phase it becomes easier to manage the threats
effectively.
Question 2:
About the case study
The InelliTrade is a small organization that aims at developing next generation high
frequency trading algorithm. They currently employs six people that are the founder, 1 sales
manager, 3 engineers and 1 secretary. The organization operates a wide range of different
desktop computers, server and laptops for the purpose of trading solution. The access can be
made easily so that it can enhance the performance of SSH tunnel.
Impact evaluation table
Impact evaluation table is used for the purpose of determining the impacts that are likely
to be created with the different levels of the system. Every organization phases different major
challenges that are needed to be organized properly so that it can enhance the performance
within the organization.
management is considered as an imperative to business manager so that the structure can be
organized. Risk management will ensure that the better communication has been offered and
ensures that better focus can be maintained within the project.
The important steps that are related with managing the threats includes identifying the
risks at first stage, measuring the threats, examining the solutions, deploying solution and
monitoring the outputs for the purpose of managing the execution (Khan and Al-Yasiri 2018).
With the assist of this management of risk phase it becomes easier to manage the threats
effectively.
Question 2:
About the case study
The InelliTrade is a small organization that aims at developing next generation high
frequency trading algorithm. They currently employs six people that are the founder, 1 sales
manager, 3 engineers and 1 secretary. The organization operates a wide range of different
desktop computers, server and laptops for the purpose of trading solution. The access can be
made easily so that it can enhance the performance of SSH tunnel.
Impact evaluation table
Impact evaluation table is used for the purpose of determining the impacts that are likely
to be created with the different levels of the system. Every organization phases different major
challenges that are needed to be organized properly so that it can enhance the performance
within the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
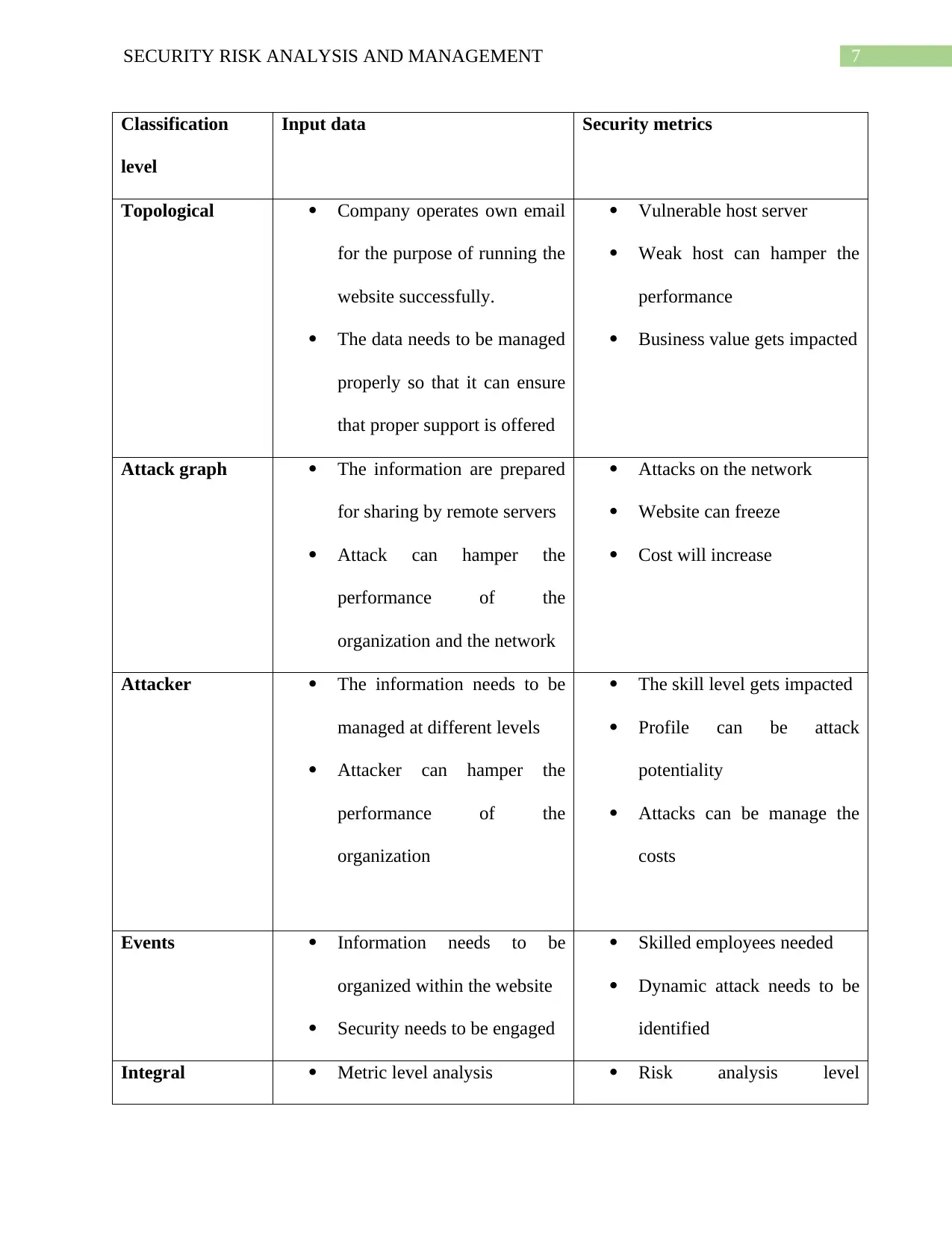
7SECURITY RISK ANALYSIS AND MANAGEMENT
Classification
level
Input data Security metrics
Topological Company operates own email
for the purpose of running the
website successfully.
The data needs to be managed
properly so that it can ensure
that proper support is offered
Vulnerable host server
Weak host can hamper the
performance
Business value gets impacted
Attack graph The information are prepared
for sharing by remote servers
Attack can hamper the
performance of the
organization and the network
Attacks on the network
Website can freeze
Cost will increase
Attacker The information needs to be
managed at different levels
Attacker can hamper the
performance of the
organization
The skill level gets impacted
Profile can be attack
potentiality
Attacks can be manage the
costs
Events Information needs to be
organized within the website
Security needs to be engaged
Skilled employees needed
Dynamic attack needs to be
identified
Integral Metric level analysis Risk analysis level
Classification
level
Input data Security metrics
Topological Company operates own email
for the purpose of running the
website successfully.
The data needs to be managed
properly so that it can ensure
that proper support is offered
Vulnerable host server
Weak host can hamper the
performance
Business value gets impacted
Attack graph The information are prepared
for sharing by remote servers
Attack can hamper the
performance of the
organization and the network
Attacks on the network
Website can freeze
Cost will increase
Attacker The information needs to be
managed at different levels
Attacker can hamper the
performance of the
organization
The skill level gets impacted
Profile can be attack
potentiality
Attacks can be manage the
costs
Events Information needs to be
organized within the website
Security needs to be engaged
Skilled employees needed
Dynamic attack needs to be
identified
Integral Metric level analysis Risk analysis level
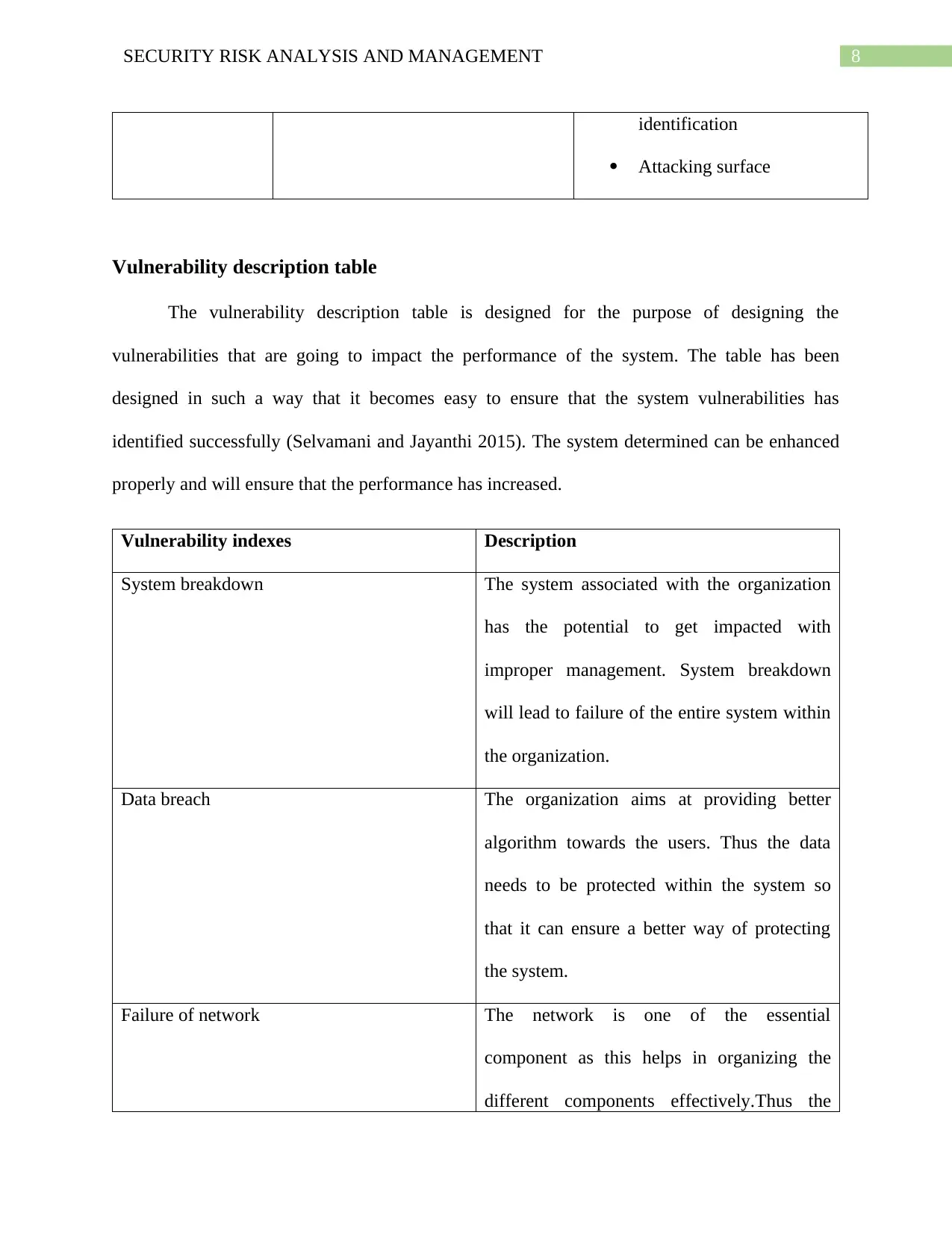
8SECURITY RISK ANALYSIS AND MANAGEMENT
identification
Attacking surface
Vulnerability description table
The vulnerability description table is designed for the purpose of designing the
vulnerabilities that are going to impact the performance of the system. The table has been
designed in such a way that it becomes easy to ensure that the system vulnerabilities has
identified successfully (Selvamani and Jayanthi 2015). The system determined can be enhanced
properly and will ensure that the performance has increased.
Vulnerability indexes Description
System breakdown The system associated with the organization
has the potential to get impacted with
improper management. System breakdown
will lead to failure of the entire system within
the organization.
Data breach The organization aims at providing better
algorithm towards the users. Thus the data
needs to be protected within the system so
that it can ensure a better way of protecting
the system.
Failure of network The network is one of the essential
component as this helps in organizing the
different components effectively.Thus the
identification
Attacking surface
Vulnerability description table
The vulnerability description table is designed for the purpose of designing the
vulnerabilities that are going to impact the performance of the system. The table has been
designed in such a way that it becomes easy to ensure that the system vulnerabilities has
identified successfully (Selvamani and Jayanthi 2015). The system determined can be enhanced
properly and will ensure that the performance has increased.
Vulnerability indexes Description
System breakdown The system associated with the organization
has the potential to get impacted with
improper management. System breakdown
will lead to failure of the entire system within
the organization.
Data breach The organization aims at providing better
algorithm towards the users. Thus the data
needs to be protected within the system so
that it can ensure a better way of protecting
the system.
Failure of network The network is one of the essential
component as this helps in organizing the
different components effectively.Thus the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
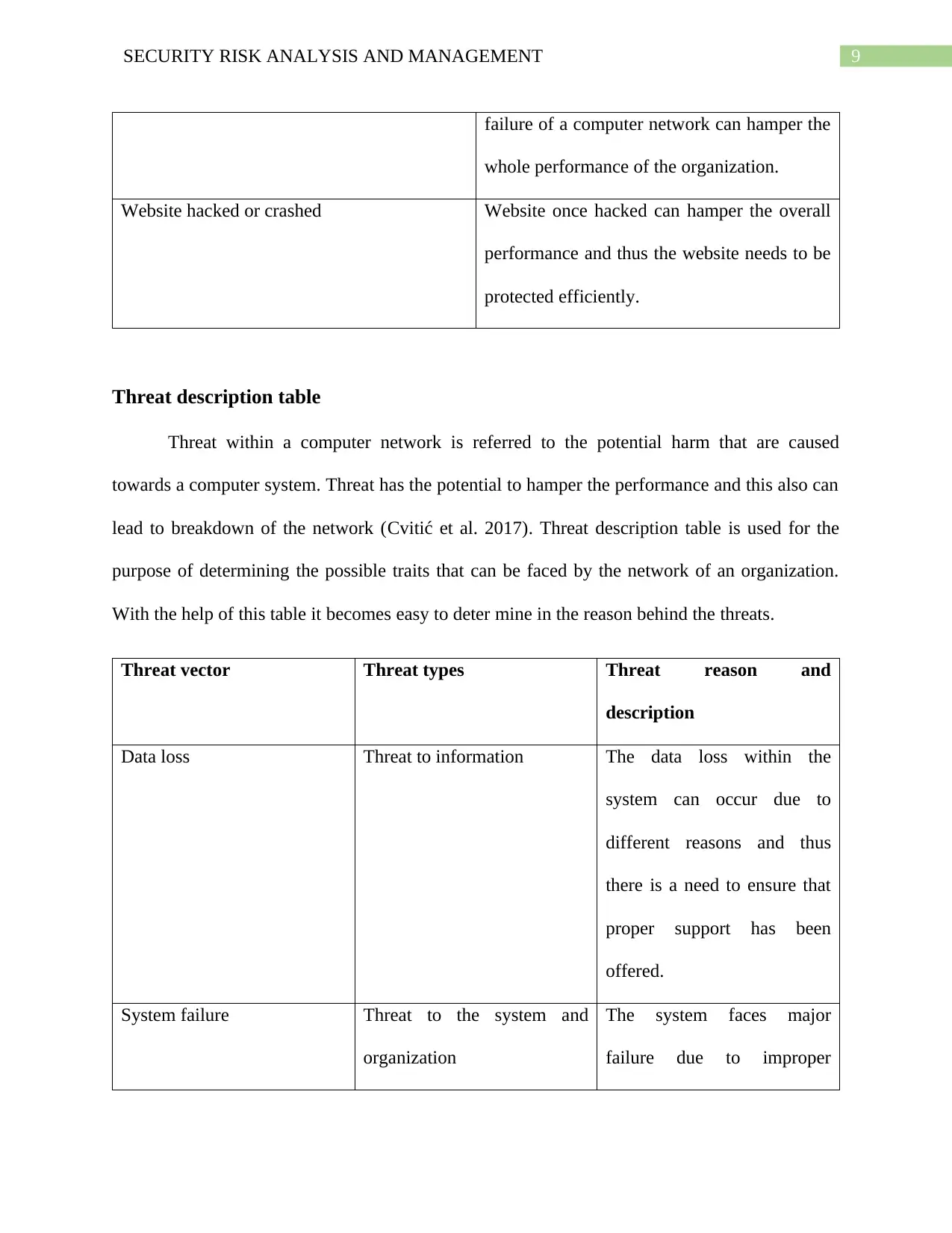
9SECURITY RISK ANALYSIS AND MANAGEMENT
failure of a computer network can hamper the
whole performance of the organization.
Website hacked or crashed Website once hacked can hamper the overall
performance and thus the website needs to be
protected efficiently.
Threat description table
Threat within a computer network is referred to the potential harm that are caused
towards a computer system. Threat has the potential to hamper the performance and this also can
lead to breakdown of the network (Cvitić et al. 2017). Threat description table is used for the
purpose of determining the possible traits that can be faced by the network of an organization.
With the help of this table it becomes easy to deter mine in the reason behind the threats.
Threat vector Threat types Threat reason and
description
Data loss Threat to information The data loss within the
system can occur due to
different reasons and thus
there is a need to ensure that
proper support has been
offered.
System failure Threat to the system and
organization
The system faces major
failure due to improper
failure of a computer network can hamper the
whole performance of the organization.
Website hacked or crashed Website once hacked can hamper the overall
performance and thus the website needs to be
protected efficiently.
Threat description table
Threat within a computer network is referred to the potential harm that are caused
towards a computer system. Threat has the potential to hamper the performance and this also can
lead to breakdown of the network (Cvitić et al. 2017). Threat description table is used for the
purpose of determining the possible traits that can be faced by the network of an organization.
With the help of this table it becomes easy to deter mine in the reason behind the threats.
Threat vector Threat types Threat reason and
description
Data loss Threat to information The data loss within the
system can occur due to
different reasons and thus
there is a need to ensure that
proper support has been
offered.
System failure Threat to the system and
organization
The system faces major
failure due to improper
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
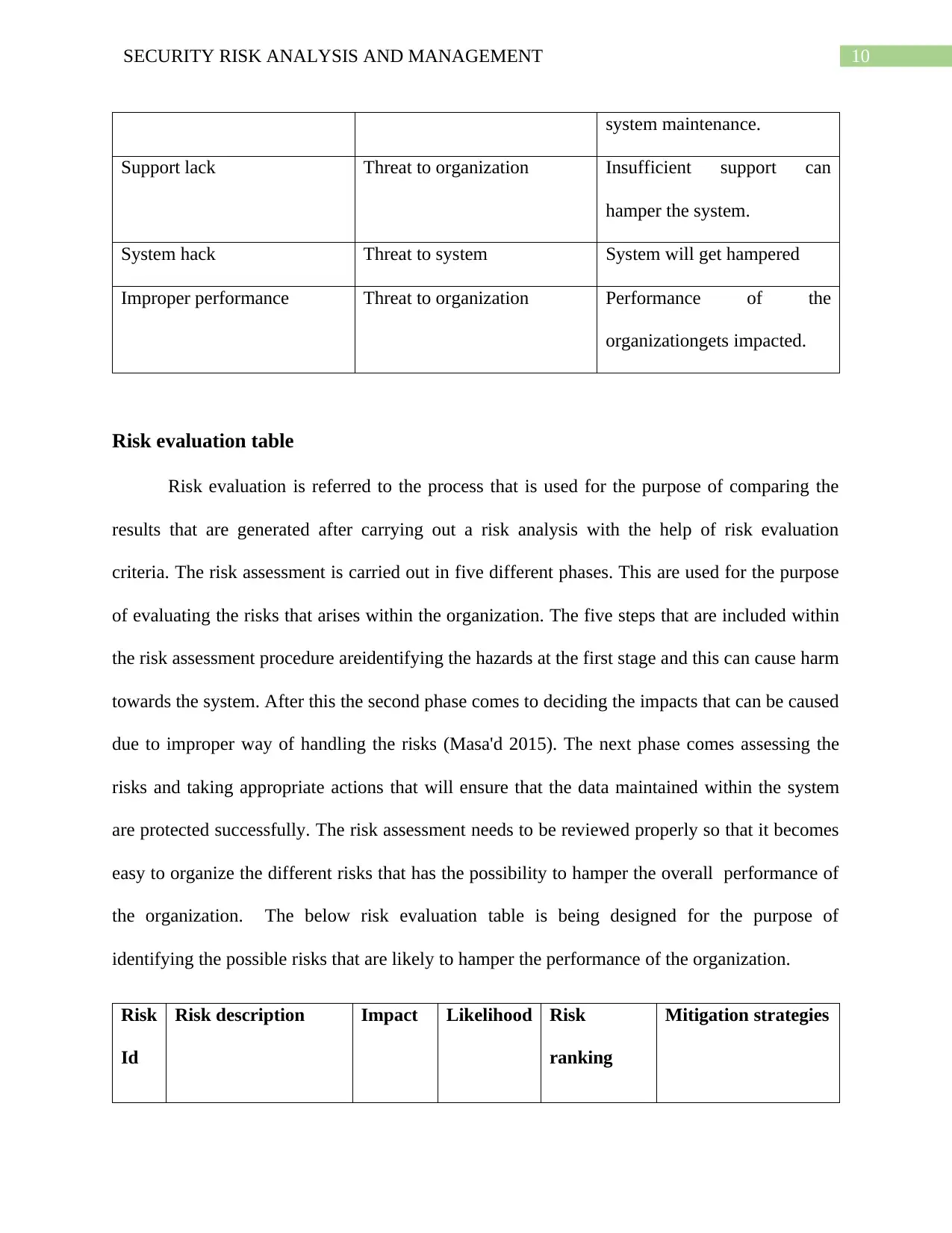
10SECURITY RISK ANALYSIS AND MANAGEMENT
system maintenance.
Support lack Threat to organization Insufficient support can
hamper the system.
System hack Threat to system System will get hampered
Improper performance Threat to organization Performance of the
organizationgets impacted.
Risk evaluation table
Risk evaluation is referred to the process that is used for the purpose of comparing the
results that are generated after carrying out a risk analysis with the help of risk evaluation
criteria. The risk assessment is carried out in five different phases. This are used for the purpose
of evaluating the risks that arises within the organization. The five steps that are included within
the risk assessment procedure areidentifying the hazards at the first stage and this can cause harm
towards the system. After this the second phase comes to deciding the impacts that can be caused
due to improper way of handling the risks (Masa'd 2015). The next phase comes assessing the
risks and taking appropriate actions that will ensure that the data maintained within the system
are protected successfully. The risk assessment needs to be reviewed properly so that it becomes
easy to organize the different risks that has the possibility to hamper the overall performance of
the organization. The below risk evaluation table is being designed for the purpose of
identifying the possible risks that are likely to hamper the performance of the organization.
Risk
Id
Risk description Impact Likelihood Risk
ranking
Mitigation strategies
system maintenance.
Support lack Threat to organization Insufficient support can
hamper the system.
System hack Threat to system System will get hampered
Improper performance Threat to organization Performance of the
organizationgets impacted.
Risk evaluation table
Risk evaluation is referred to the process that is used for the purpose of comparing the
results that are generated after carrying out a risk analysis with the help of risk evaluation
criteria. The risk assessment is carried out in five different phases. This are used for the purpose
of evaluating the risks that arises within the organization. The five steps that are included within
the risk assessment procedure areidentifying the hazards at the first stage and this can cause harm
towards the system. After this the second phase comes to deciding the impacts that can be caused
due to improper way of handling the risks (Masa'd 2015). The next phase comes assessing the
risks and taking appropriate actions that will ensure that the data maintained within the system
are protected successfully. The risk assessment needs to be reviewed properly so that it becomes
easy to organize the different risks that has the possibility to hamper the overall performance of
the organization. The below risk evaluation table is being designed for the purpose of
identifying the possible risks that are likely to hamper the performance of the organization.
Risk
Id
Risk description Impact Likelihood Risk
ranking
Mitigation strategies
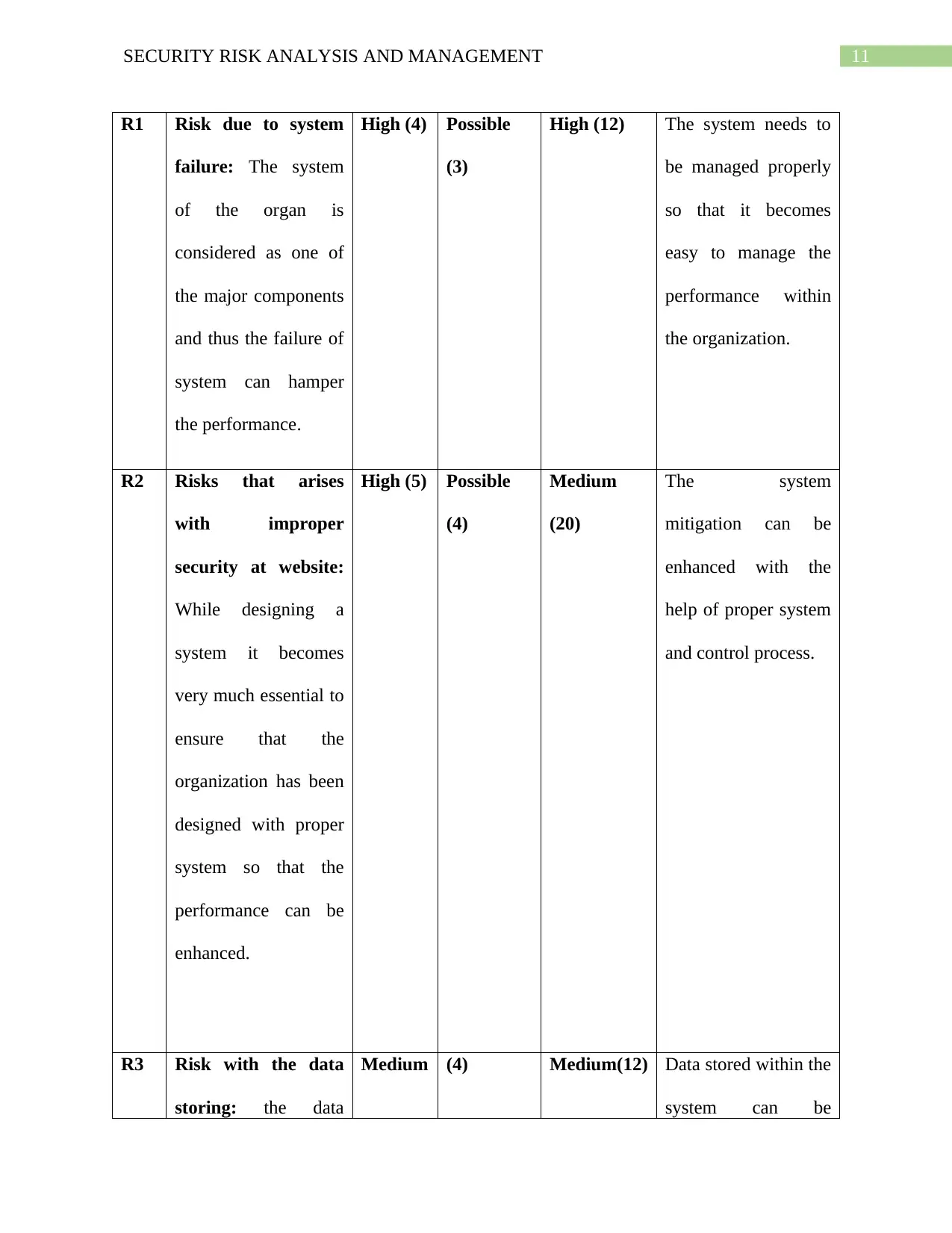
11SECURITY RISK ANALYSIS AND MANAGEMENT
R1 Risk due to system
failure: The system
of the organ is
considered as one of
the major components
and thus the failure of
system can hamper
the performance.
High (4) Possible
(3)
High (12) The system needs to
be managed properly
so that it becomes
easy to manage the
performance within
the organization.
R2 Risks that arises
with improper
security at website:
While designing a
system it becomes
very much essential to
ensure that the
organization has been
designed with proper
system so that the
performance can be
enhanced.
High (5) Possible
(4)
Medium
(20)
The system
mitigation can be
enhanced with the
help of proper system
and control process.
R3 Risk with the data
storing: the data
Medium (4) Medium(12) Data stored within the
system can be
R1 Risk due to system
failure: The system
of the organ is
considered as one of
the major components
and thus the failure of
system can hamper
the performance.
High (4) Possible
(3)
High (12) The system needs to
be managed properly
so that it becomes
easy to manage the
performance within
the organization.
R2 Risks that arises
with improper
security at website:
While designing a
system it becomes
very much essential to
ensure that the
organization has been
designed with proper
system so that the
performance can be
enhanced.
High (5) Possible
(4)
Medium
(20)
The system
mitigation can be
enhanced with the
help of proper system
and control process.
R3 Risk with the data
storing: the data
Medium (4) Medium(12) Data stored within the
system can be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





