MEM 508: Risk of Failure in Security Systems at Dubai EXPO 2020
VerifiedAdded on 2022/08/13
|15
|3845
|28
Report
AI Summary
This report presents a comprehensive risk management plan specifically designed for the security systems at Dubai EXPO 2020. The project's focus is on identifying, analyzing, evaluating, and mitigating potential risks to ensure the event's safety and success. The report begins with an introduction that emphasizes the importance of risk management in achieving organizational goals and outlines the project's scope, including the crucial role of security within the expo. The core of the report details the risk management process, encompassing risk identification through methods like SWOT analysis, risk analysis, and evaluation to prioritize risks. It further explores mitigation strategies, including cyber security risks, terrorism, and poor coordination. The report also delves into the practical aspects of risk management, such as stakeholder analysis, risk factor calculation, and the implementation of a risk mitigation plan. The conclusion underscores the significance of proactive risk management in safeguarding the event and its participants.

Risk Management Plan – risk of failure in Security systems in expo
2020
Table of Contents
Risk Management Plan – risk of failure Security systems in expo 2020.....................................................1
Introduction.................................................................................................................................................2
Project overview..........................................................................................................................................3
Problem statement...................................................................................................................................5
Risk Management Plan................................................................................................................................5
Risk identification...................................................................................................................................6
Risk analysis and evaluation....................................................................................................................9
Risk evaluation and prioritization..........................................................................................................11
Risk mitigation......................................................................................................................................12
Conclusion.................................................................................................................................................14
References.................................................................................................................................................14
2020
Table of Contents
Risk Management Plan – risk of failure Security systems in expo 2020.....................................................1
Introduction.................................................................................................................................................2
Project overview..........................................................................................................................................3
Problem statement...................................................................................................................................5
Risk Management Plan................................................................................................................................5
Risk identification...................................................................................................................................6
Risk analysis and evaluation....................................................................................................................9
Risk evaluation and prioritization..........................................................................................................11
Risk mitigation......................................................................................................................................12
Conclusion.................................................................................................................................................14
References.................................................................................................................................................14
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
For an organization to realize its goals and missions or for an event within an organization to achieve
success, the management has to identify and control the risks. The identification, mitigation and control
of the risks are components of risks management system for any organization. The success of the risk
management system used by an organization in day to day operations or for a particular event depends on
how efficient the system in terms of identifying the risks and controlling the risks. An elaborate risks
management system can also enhance the financial integrity and image of company. The engineering
management system must be able to keep the risks under acceptable standards or eliminate the risks
completely.
There are various methods or risks management systems for managing the risks and they have different
cost implications. Risk management is the process involving the identification, assessment, mitigation and
control of the risks that are faced on daily basis. Risk identification and assessment is a continuous
process. The mitigation measures taken to address the risks will depend on the risk level. There are some
risks that have a great impact on the operation and running of an organization or the success of an event.
These risks will involve elaborate and comprehensive mitigation mechanisms compared to risks with
relatively smaller impacts. The risks level is defined by both the probability of occurrence of the risks as
well as the impact the risks have. The control tools and devices used for monitoring the risks can vary
from one company to another. The control tools are affected by the organizations structure, infrastructure
and resources. The management will have to ensure that the resources are properly utilized in the bid to
achieve objectives and goals. The tools for identifications and monitoring should be should be easy to
use by those involved and they must be able to be used for a long time to capture all risks that the
organization may be exposed to.
Although there are particular departments or sections within the organization that are normally tasked
with managing risks, the whole staff must be involved in one way or another. Involving all the staff in
identification and other stages of risks management can bear good results as opposed to setting up a
section to look at risks and device the measures of controlling and managing risks. The management of an
organization plays a significant role in risks management by setting decisions that address the risks and
mitigate. The management can also see trends in risks management and hence initiate action oriented
decisions. Overlooking risks within an organization or failing to take prompt mitigation measures have
really affected the running and realizations of the company objectives. In other cases, it has led to the
failure of some organizations. Hence this shows how serious the issue of risk management must be taken
by organizations which intend to realize the missions and visions (Abbas, 2017). Analysts have concluded
For an organization to realize its goals and missions or for an event within an organization to achieve
success, the management has to identify and control the risks. The identification, mitigation and control
of the risks are components of risks management system for any organization. The success of the risk
management system used by an organization in day to day operations or for a particular event depends on
how efficient the system in terms of identifying the risks and controlling the risks. An elaborate risks
management system can also enhance the financial integrity and image of company. The engineering
management system must be able to keep the risks under acceptable standards or eliminate the risks
completely.
There are various methods or risks management systems for managing the risks and they have different
cost implications. Risk management is the process involving the identification, assessment, mitigation and
control of the risks that are faced on daily basis. Risk identification and assessment is a continuous
process. The mitigation measures taken to address the risks will depend on the risk level. There are some
risks that have a great impact on the operation and running of an organization or the success of an event.
These risks will involve elaborate and comprehensive mitigation mechanisms compared to risks with
relatively smaller impacts. The risks level is defined by both the probability of occurrence of the risks as
well as the impact the risks have. The control tools and devices used for monitoring the risks can vary
from one company to another. The control tools are affected by the organizations structure, infrastructure
and resources. The management will have to ensure that the resources are properly utilized in the bid to
achieve objectives and goals. The tools for identifications and monitoring should be should be easy to
use by those involved and they must be able to be used for a long time to capture all risks that the
organization may be exposed to.
Although there are particular departments or sections within the organization that are normally tasked
with managing risks, the whole staff must be involved in one way or another. Involving all the staff in
identification and other stages of risks management can bear good results as opposed to setting up a
section to look at risks and device the measures of controlling and managing risks. The management of an
organization plays a significant role in risks management by setting decisions that address the risks and
mitigate. The management can also see trends in risks management and hence initiate action oriented
decisions. Overlooking risks within an organization or failing to take prompt mitigation measures have
really affected the running and realizations of the company objectives. In other cases, it has led to the
failure of some organizations. Hence this shows how serious the issue of risk management must be taken
by organizations which intend to realize the missions and visions (Abbas, 2017). Analysts have concluded

that it is better to manage risks than cover the costs due to risks because these risks can results in the
collapse of the organization.
Project overview
This report is about the project risk management for Dubai EXPO 2020. This is a big event that
will take place in Dubai and hence there are a number of risks that will have to be managed in
order for the expo to be successful. Risk management for an event can be very challenging just
as much as risk management in an organization. The Dubai 2020 expo risk management include
activities like identification of risks, assessing the risks, mitigating the risk, controlling and
monitoring the risks. This being an international event, the 2020 expo will in itself comprise of
many activities including transport services, commercial services, security, administration,
recruitment for different works, public address, catering services, photography, media services
and forex exchange services among other services (L. Zhan & Yaochen, 2016). The activity that
is very crucial among those that will be taking place at the expo is the security services.
This project report is about the risk of security at the expo. The systems engineers are tasked
with coming up with security system that will be able to monitor any activity at the expo that
may breach the security of others. Since the security issues is not an independent activity but
involves all those at the expo, the security becomes a crucial segment of the project for the
success of the expo. Security is like the glue for all the other activities that will be taking place
during the event. Hence the security system developed by the systems engineer must be very
efficient and comprehensive in capturing data related to security, alerting promptly the
concerned parties of dangers.
The event organizers and stakeholders will ensure that the issue of security is properly handled
for the success of the event and hence they will organize and support all the security agencies
that will be handling matters security. The main custodial for providing the security of the people
at the event will be the Dubai police. The Dubai police are given the mandate of providing law
and order in the country and during any public event like this. In this case however, the security
will also be provided by other agencies and international security will be provided to ensure that
the security of international traders is paramount. Hence the security system developed by the
systems engineer will greatly contribute towards the security of the people before, during and
collapse of the organization.
Project overview
This report is about the project risk management for Dubai EXPO 2020. This is a big event that
will take place in Dubai and hence there are a number of risks that will have to be managed in
order for the expo to be successful. Risk management for an event can be very challenging just
as much as risk management in an organization. The Dubai 2020 expo risk management include
activities like identification of risks, assessing the risks, mitigating the risk, controlling and
monitoring the risks. This being an international event, the 2020 expo will in itself comprise of
many activities including transport services, commercial services, security, administration,
recruitment for different works, public address, catering services, photography, media services
and forex exchange services among other services (L. Zhan & Yaochen, 2016). The activity that
is very crucial among those that will be taking place at the expo is the security services.
This project report is about the risk of security at the expo. The systems engineers are tasked
with coming up with security system that will be able to monitor any activity at the expo that
may breach the security of others. Since the security issues is not an independent activity but
involves all those at the expo, the security becomes a crucial segment of the project for the
success of the expo. Security is like the glue for all the other activities that will be taking place
during the event. Hence the security system developed by the systems engineer must be very
efficient and comprehensive in capturing data related to security, alerting promptly the
concerned parties of dangers.
The event organizers and stakeholders will ensure that the issue of security is properly handled
for the success of the event and hence they will organize and support all the security agencies
that will be handling matters security. The main custodial for providing the security of the people
at the event will be the Dubai police. The Dubai police are given the mandate of providing law
and order in the country and during any public event like this. In this case however, the security
will also be provided by other agencies and international security will be provided to ensure that
the security of international traders is paramount. Hence the security system developed by the
systems engineer will greatly contribute towards the security of the people before, during and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

after the event is over. The success of the security system designed will depend on the
cooperation of the multi security agencies at the event.
The security system will help in data collection and sharing among the relevant agencies for
action to be taken. The Dubai police and other security agencies will have to be trained on how
to use the system before launching the system for use. Although there are risks that will still be
faced even during the implementation of the security system. Some of the risks identified are the
IT system failure, acts of terrorisms, poor coordination between staff and the security agencies
among others. Although the Dubai police have been touted as being effective when it comes to
handling crowds, maintaining law and order and having the best training in the world with
advanced security facilities, a crowd that is expected to be at the Dubai EXPO 2020 could pose
challenges even to the best security agencies in the world. Hence the security system will have to
be understood by the security agencies on how to use it in order to achieve the success of the
EXPO.
There are risks due to the security system that will be applied as well as the risks due to the
stakeholders and shareholders that will be using the system. The system will provide an
interphase for networking with other security systems that are already in use and the current
technology. There are many factors out there that could pose dangers to the operation of the
system and hence affect its viability. These factors can also be termed as risks on the system and
they include cyber-attacks, malwares, hacking, routers and other technological malpractices that
could render the system unusable. The system engineers are tasked with designing a system that
should overcome these challenges in order to achieve security of those at the EXPO 2020.
The security system will work by collecting data. The data will then be normalized into
languages that can be understood and interpreted for action. The data is then enriched by adding
information known to the public and those from the data bases collected before. At this stage, the
data will then be scanned for the next stage. After enriching the data, the data is scanned and
relationships with other information from the database are established. The correlated data is
prioritized for action and recommends the appropriate action to be taken. The signals are sent to
relevant organs for actions and for security measures to undertaken. The reporting of the
information by the system is through emails or quick messages and activity reports.
cooperation of the multi security agencies at the event.
The security system will help in data collection and sharing among the relevant agencies for
action to be taken. The Dubai police and other security agencies will have to be trained on how
to use the system before launching the system for use. Although there are risks that will still be
faced even during the implementation of the security system. Some of the risks identified are the
IT system failure, acts of terrorisms, poor coordination between staff and the security agencies
among others. Although the Dubai police have been touted as being effective when it comes to
handling crowds, maintaining law and order and having the best training in the world with
advanced security facilities, a crowd that is expected to be at the Dubai EXPO 2020 could pose
challenges even to the best security agencies in the world. Hence the security system will have to
be understood by the security agencies on how to use it in order to achieve the success of the
EXPO.
There are risks due to the security system that will be applied as well as the risks due to the
stakeholders and shareholders that will be using the system. The system will provide an
interphase for networking with other security systems that are already in use and the current
technology. There are many factors out there that could pose dangers to the operation of the
system and hence affect its viability. These factors can also be termed as risks on the system and
they include cyber-attacks, malwares, hacking, routers and other technological malpractices that
could render the system unusable. The system engineers are tasked with designing a system that
should overcome these challenges in order to achieve security of those at the EXPO 2020.
The security system will work by collecting data. The data will then be normalized into
languages that can be understood and interpreted for action. The data is then enriched by adding
information known to the public and those from the data bases collected before. At this stage, the
data will then be scanned for the next stage. After enriching the data, the data is scanned and
relationships with other information from the database are established. The correlated data is
prioritized for action and recommends the appropriate action to be taken. The signals are sent to
relevant organs for actions and for security measures to undertaken. The reporting of the
information by the system is through emails or quick messages and activity reports.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Problem statement
This report is about the risk management related to an event, Dubai EXPO 2020. The system engineers
are to come up with security security software that will play a critical role in tightening the security. The
security system will help to fight many risks like terrorisms; cyber related crimes and increased demand
for services. The expo will face different security challenges that must be addressed in satisfactory
manner and assure the shareholders that their security is guaranteed. In the current times where terrorism
activities are on the rise, the Dubai expo 2020 could be an easy target for terrorism. The large population
of people at the event could also pose other challenges like drug peddling and use of illicit weapons. The
event will also bring together people from different walks of life, some who may have unscrupulous
agenda. Designing a system that would be able to effectively assist in enhancing security for all those at
the event is a task for engineers. Hence there is need for cooperation from all stakeholders in planning and
implementation of the system. The main stakeholders in the security during the expo 2020 are the event
managers who will comprise of officials from the government and other international communities. This
group of stakeholders will play a pivotal role of ensuring the smooth operations as well as funds for
operations. Besides the managers, there are also coordinators who will work hand in hand to ensure the
communication related activities are handled properly. They will also look at thee revenue collection and
coordination between the even managers and the other agencies. The other stakeholders will involve
international agencies dealing win areas like security and trade. The public will also play a crucial role in
ensuring the expo is a success.
Risk Management Plan
The risk management plan involves all the stages of risk management and these are the risk identification,
Analysis, Mitigation, Tracking.
This report is about the risk management related to an event, Dubai EXPO 2020. The system engineers
are to come up with security security software that will play a critical role in tightening the security. The
security system will help to fight many risks like terrorisms; cyber related crimes and increased demand
for services. The expo will face different security challenges that must be addressed in satisfactory
manner and assure the shareholders that their security is guaranteed. In the current times where terrorism
activities are on the rise, the Dubai expo 2020 could be an easy target for terrorism. The large population
of people at the event could also pose other challenges like drug peddling and use of illicit weapons. The
event will also bring together people from different walks of life, some who may have unscrupulous
agenda. Designing a system that would be able to effectively assist in enhancing security for all those at
the event is a task for engineers. Hence there is need for cooperation from all stakeholders in planning and
implementation of the system. The main stakeholders in the security during the expo 2020 are the event
managers who will comprise of officials from the government and other international communities. This
group of stakeholders will play a pivotal role of ensuring the smooth operations as well as funds for
operations. Besides the managers, there are also coordinators who will work hand in hand to ensure the
communication related activities are handled properly. They will also look at thee revenue collection and
coordination between the even managers and the other agencies. The other stakeholders will involve
international agencies dealing win areas like security and trade. The public will also play a crucial role in
ensuring the expo is a success.
Risk Management Plan
The risk management plan involves all the stages of risk management and these are the risk identification,
Analysis, Mitigation, Tracking.
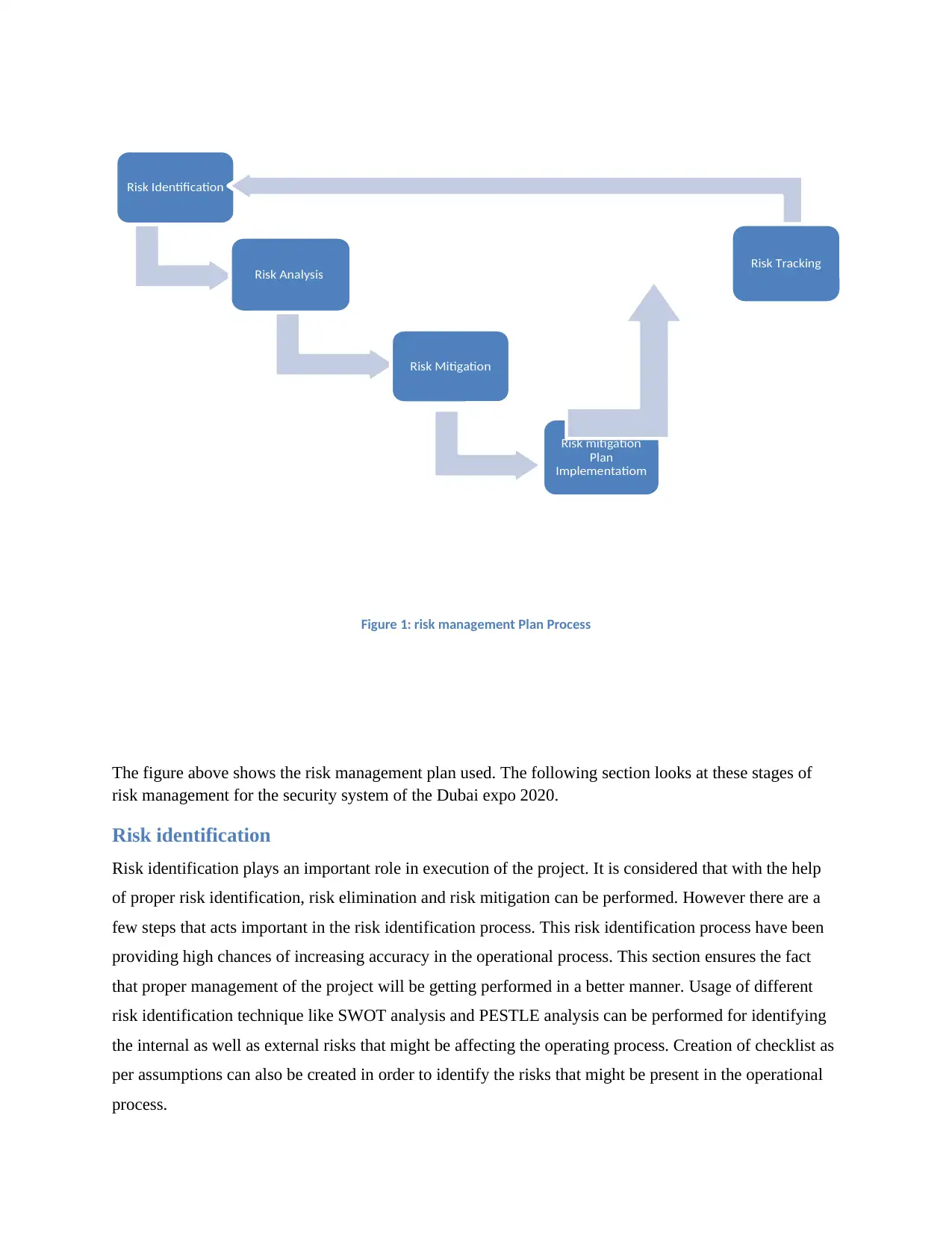
Figure 1: risk management Plan Process
The figure above shows the risk management plan used. The following section looks at these stages of
risk management for the security system of the Dubai expo 2020.
Risk identification
Risk identification plays an important role in execution of the project. It is considered that with the help
of proper risk identification, risk elimination and risk mitigation can be performed. However there are a
few steps that acts important in the risk identification process. This risk identification process have been
providing high chances of increasing accuracy in the operational process. This section ensures the fact
that proper management of the project will be getting performed in a better manner. Usage of different
risk identification technique like SWOT analysis and PESTLE analysis can be performed for identifying
the internal as well as external risks that might be affecting the operating process. Creation of checklist as
per assumptions can also be created in order to identify the risks that might be present in the operational
process.
Risk Identification
Risk Analysis
Risk Mitigation
Risk mitigation
Plan
Implementatiom
Risk Tracking
The figure above shows the risk management plan used. The following section looks at these stages of
risk management for the security system of the Dubai expo 2020.
Risk identification
Risk identification plays an important role in execution of the project. It is considered that with the help
of proper risk identification, risk elimination and risk mitigation can be performed. However there are a
few steps that acts important in the risk identification process. This risk identification process have been
providing high chances of increasing accuracy in the operational process. This section ensures the fact
that proper management of the project will be getting performed in a better manner. Usage of different
risk identification technique like SWOT analysis and PESTLE analysis can be performed for identifying
the internal as well as external risks that might be affecting the operating process. Creation of checklist as
per assumptions can also be created in order to identify the risks that might be present in the operational
process.
Risk Identification
Risk Analysis
Risk Mitigation
Risk mitigation
Plan
Implementatiom
Risk Tracking
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
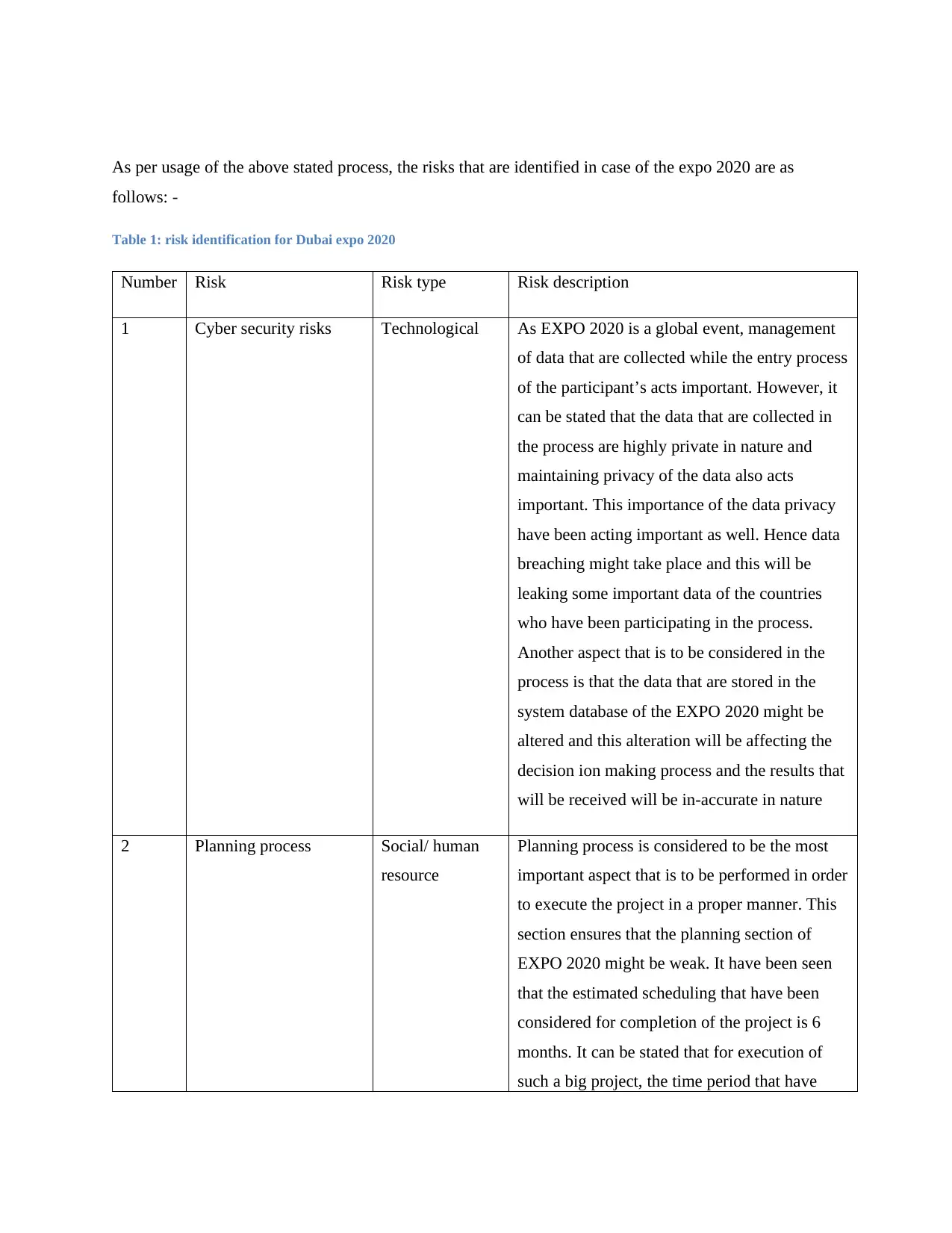
As per usage of the above stated process, the risks that are identified in case of the expo 2020 are as
follows: -
Table 1: risk identification for Dubai expo 2020
Number Risk Risk type Risk description
1 Cyber security risks Technological As EXPO 2020 is a global event, management
of data that are collected while the entry process
of the participant’s acts important. However, it
can be stated that the data that are collected in
the process are highly private in nature and
maintaining privacy of the data also acts
important. This importance of the data privacy
have been acting important as well. Hence data
breaching might take place and this will be
leaking some important data of the countries
who have been participating in the process.
Another aspect that is to be considered in the
process is that the data that are stored in the
system database of the EXPO 2020 might be
altered and this alteration will be affecting the
decision ion making process and the results that
will be received will be in-accurate in nature
2 Planning process Social/ human
resource
Planning process is considered to be the most
important aspect that is to be performed in order
to execute the project in a proper manner. This
section ensures that the planning section of
EXPO 2020 might be weak. It have been seen
that the estimated scheduling that have been
considered for completion of the project is 6
months. It can be stated that for execution of
such a big project, the time period that have
follows: -
Table 1: risk identification for Dubai expo 2020
Number Risk Risk type Risk description
1 Cyber security risks Technological As EXPO 2020 is a global event, management
of data that are collected while the entry process
of the participant’s acts important. However, it
can be stated that the data that are collected in
the process are highly private in nature and
maintaining privacy of the data also acts
important. This importance of the data privacy
have been acting important as well. Hence data
breaching might take place and this will be
leaking some important data of the countries
who have been participating in the process.
Another aspect that is to be considered in the
process is that the data that are stored in the
system database of the EXPO 2020 might be
altered and this alteration will be affecting the
decision ion making process and the results that
will be received will be in-accurate in nature
2 Planning process Social/ human
resource
Planning process is considered to be the most
important aspect that is to be performed in order
to execute the project in a proper manner. This
section ensures that the planning section of
EXPO 2020 might be weak. It have been seen
that the estimated scheduling that have been
considered for completion of the project is 6
months. It can be stated that for execution of
such a big project, the time period that have
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
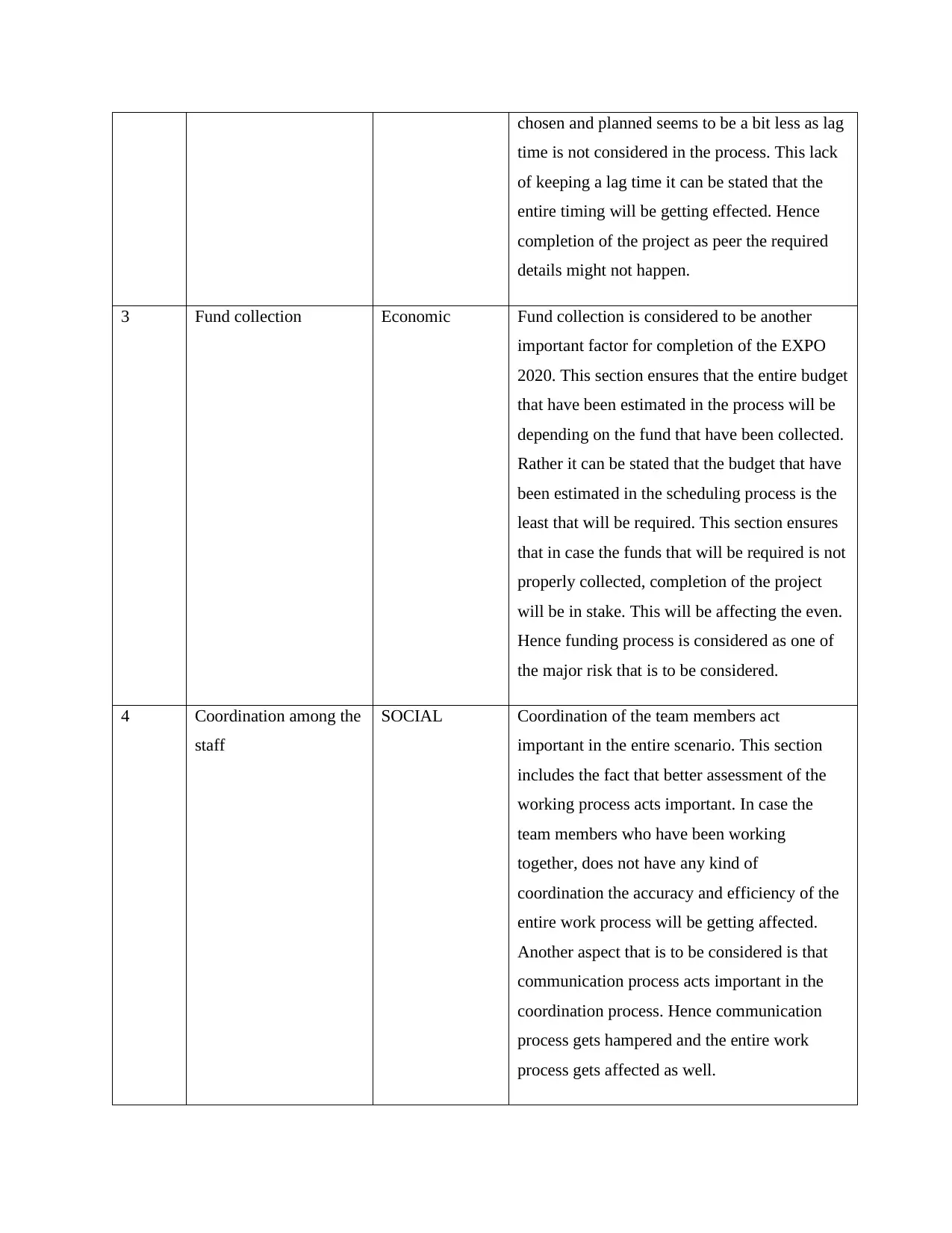
chosen and planned seems to be a bit less as lag
time is not considered in the process. This lack
of keeping a lag time it can be stated that the
entire timing will be getting effected. Hence
completion of the project as peer the required
details might not happen.
3 Fund collection Economic Fund collection is considered to be another
important factor for completion of the EXPO
2020. This section ensures that the entire budget
that have been estimated in the process will be
depending on the fund that have been collected.
Rather it can be stated that the budget that have
been estimated in the scheduling process is the
least that will be required. This section ensures
that in case the funds that will be required is not
properly collected, completion of the project
will be in stake. This will be affecting the even.
Hence funding process is considered as one of
the major risk that is to be considered.
4 Coordination among the
staff
SOCIAL Coordination of the team members act
important in the entire scenario. This section
includes the fact that better assessment of the
working process acts important. In case the
team members who have been working
together, does not have any kind of
coordination the accuracy and efficiency of the
entire work process will be getting affected.
Another aspect that is to be considered is that
communication process acts important in the
coordination process. Hence communication
process gets hampered and the entire work
process gets affected as well.
time is not considered in the process. This lack
of keeping a lag time it can be stated that the
entire timing will be getting effected. Hence
completion of the project as peer the required
details might not happen.
3 Fund collection Economic Fund collection is considered to be another
important factor for completion of the EXPO
2020. This section ensures that the entire budget
that have been estimated in the process will be
depending on the fund that have been collected.
Rather it can be stated that the budget that have
been estimated in the scheduling process is the
least that will be required. This section ensures
that in case the funds that will be required is not
properly collected, completion of the project
will be in stake. This will be affecting the even.
Hence funding process is considered as one of
the major risk that is to be considered.
4 Coordination among the
staff
SOCIAL Coordination of the team members act
important in the entire scenario. This section
includes the fact that better assessment of the
working process acts important. In case the
team members who have been working
together, does not have any kind of
coordination the accuracy and efficiency of the
entire work process will be getting affected.
Another aspect that is to be considered is that
communication process acts important in the
coordination process. Hence communication
process gets hampered and the entire work
process gets affected as well.
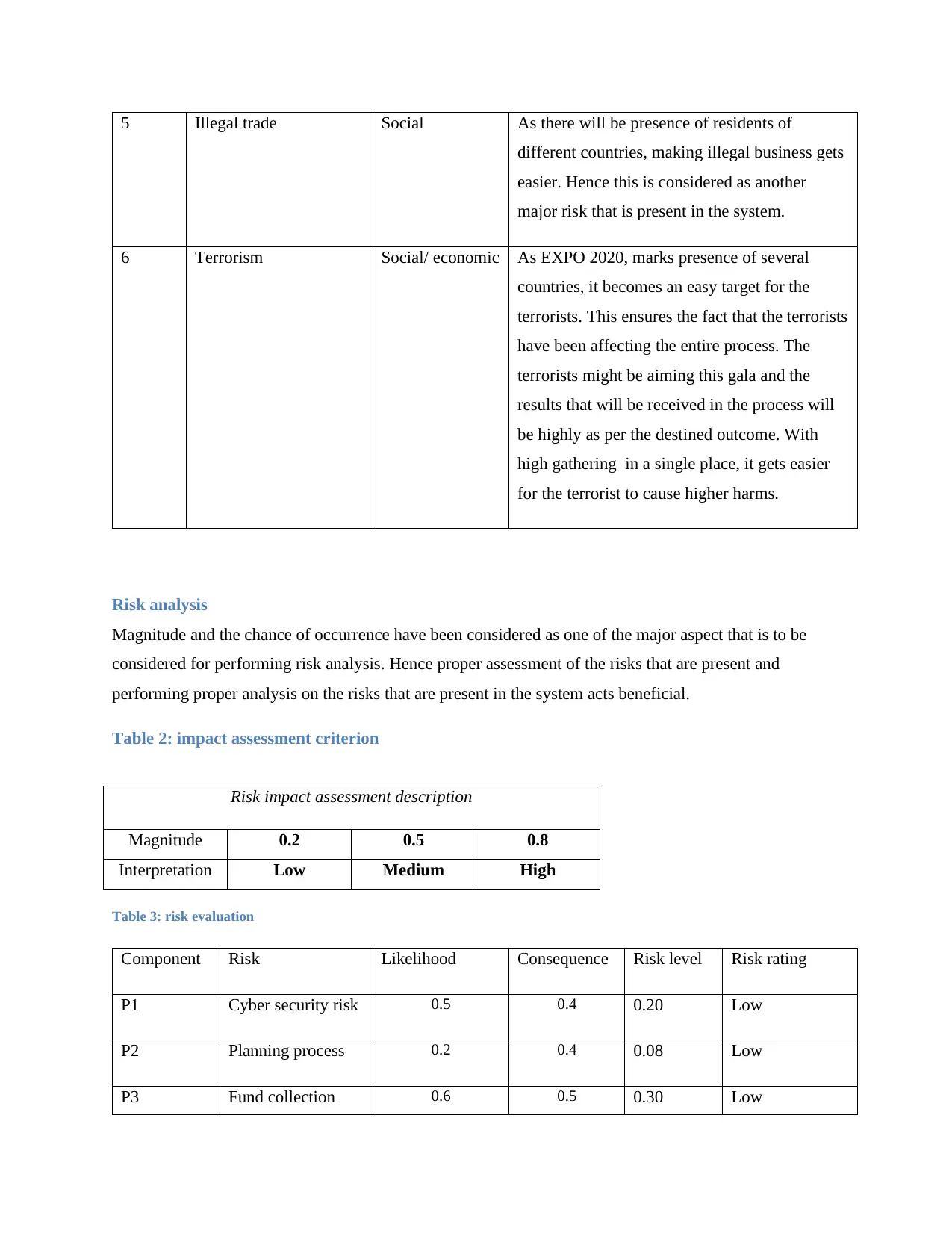
5 Illegal trade Social As there will be presence of residents of
different countries, making illegal business gets
easier. Hence this is considered as another
major risk that is present in the system.
6 Terrorism Social/ economic As EXPO 2020, marks presence of several
countries, it becomes an easy target for the
terrorists. This ensures the fact that the terrorists
have been affecting the entire process. The
terrorists might be aiming this gala and the
results that will be received in the process will
be highly as per the destined outcome. With
high gathering in a single place, it gets easier
for the terrorist to cause higher harms.
Risk analysis
Magnitude and the chance of occurrence have been considered as one of the major aspect that is to be
considered for performing risk analysis. Hence proper assessment of the risks that are present and
performing proper analysis on the risks that are present in the system acts beneficial.
Table 2: impact assessment criterion
Table 3: risk evaluation
Component Risk Likelihood Consequence Risk level Risk rating
P1 Cyber security risk 0.5 0.4 0.20 Low
P2 Planning process 0.2 0.4 0.08 Low
P3 Fund collection 0.6 0.5 0.30 Low
Risk impact assessment description
Magnitude 0.2 0.5 0.8
Interpretation Low Medium High
different countries, making illegal business gets
easier. Hence this is considered as another
major risk that is present in the system.
6 Terrorism Social/ economic As EXPO 2020, marks presence of several
countries, it becomes an easy target for the
terrorists. This ensures the fact that the terrorists
have been affecting the entire process. The
terrorists might be aiming this gala and the
results that will be received in the process will
be highly as per the destined outcome. With
high gathering in a single place, it gets easier
for the terrorist to cause higher harms.
Risk analysis
Magnitude and the chance of occurrence have been considered as one of the major aspect that is to be
considered for performing risk analysis. Hence proper assessment of the risks that are present and
performing proper analysis on the risks that are present in the system acts beneficial.
Table 2: impact assessment criterion
Table 3: risk evaluation
Component Risk Likelihood Consequence Risk level Risk rating
P1 Cyber security risk 0.5 0.4 0.20 Low
P2 Planning process 0.2 0.4 0.08 Low
P3 Fund collection 0.6 0.5 0.30 Low
Risk impact assessment description
Magnitude 0.2 0.5 0.8
Interpretation Low Medium High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
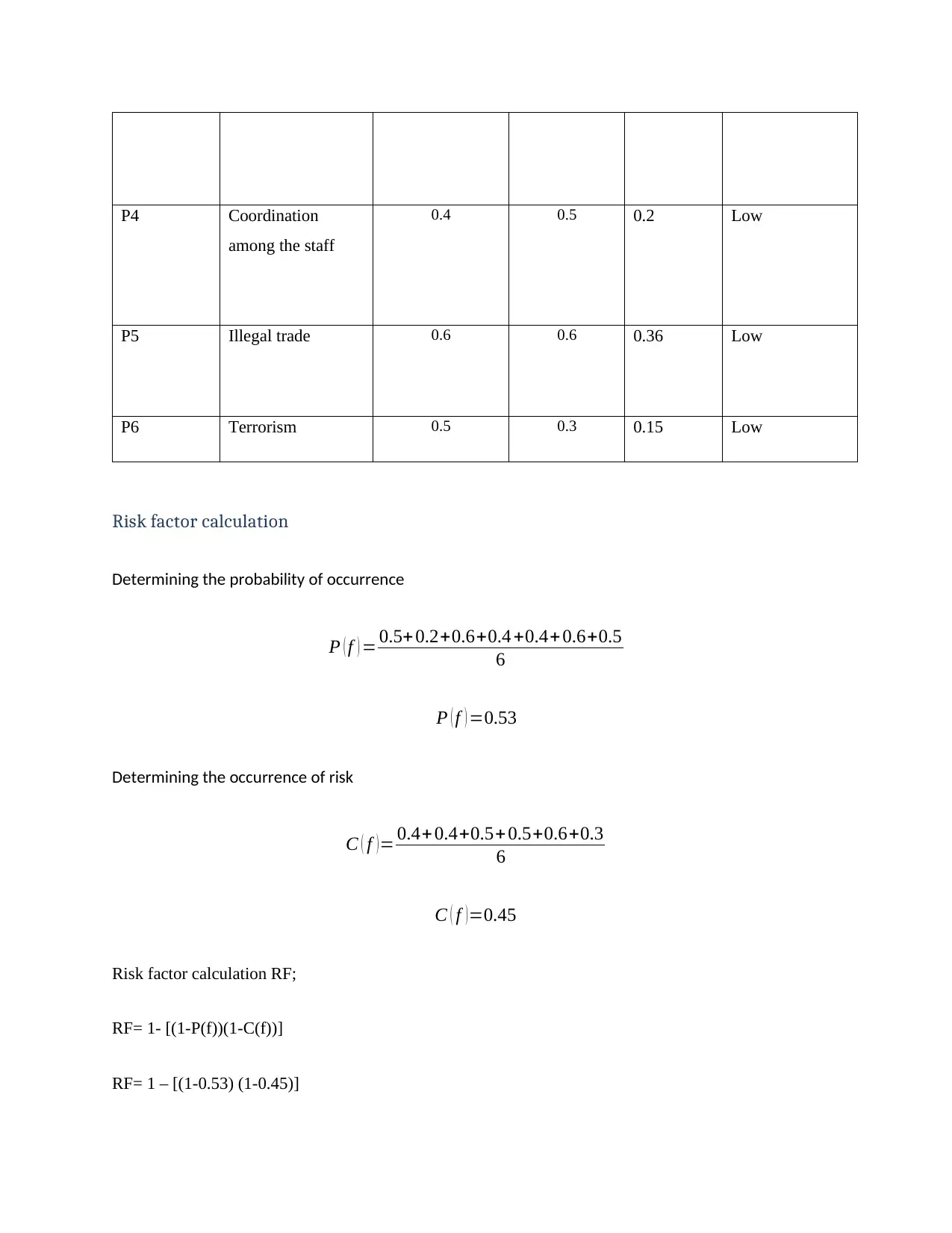
P4 Coordination
among the staff
0.4 0.5 0.2 Low
P5 Illegal trade 0.6 0.6 0.36 Low
P6 Terrorism 0.5 0.3 0.15 Low
Risk factor calculation
Determining the probability of occurrence
P ( f ) = 0.5+ 0.2+0.6+0.4 +0.4+ 0.6+0.5
6
P ( f ) =0.53
Determining the occurrence of risk
C ( f )= 0.4+ 0.4+0.5+ 0.5+0.6+0.3
6
C ( f ) =0.45
Risk factor calculation RF;
RF= 1- [(1-P(f))(1-C(f))]
RF= 1 – [(1-0.53) (1-0.45)]
among the staff
0.4 0.5 0.2 Low
P5 Illegal trade 0.6 0.6 0.36 Low
P6 Terrorism 0.5 0.3 0.15 Low
Risk factor calculation
Determining the probability of occurrence
P ( f ) = 0.5+ 0.2+0.6+0.4 +0.4+ 0.6+0.5
6
P ( f ) =0.53
Determining the occurrence of risk
C ( f )= 0.4+ 0.4+0.5+ 0.5+0.6+0.3
6
C ( f ) =0.45
Risk factor calculation RF;
RF= 1- [(1-P(f))(1-C(f))]
RF= 1 – [(1-0.53) (1-0.45)]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
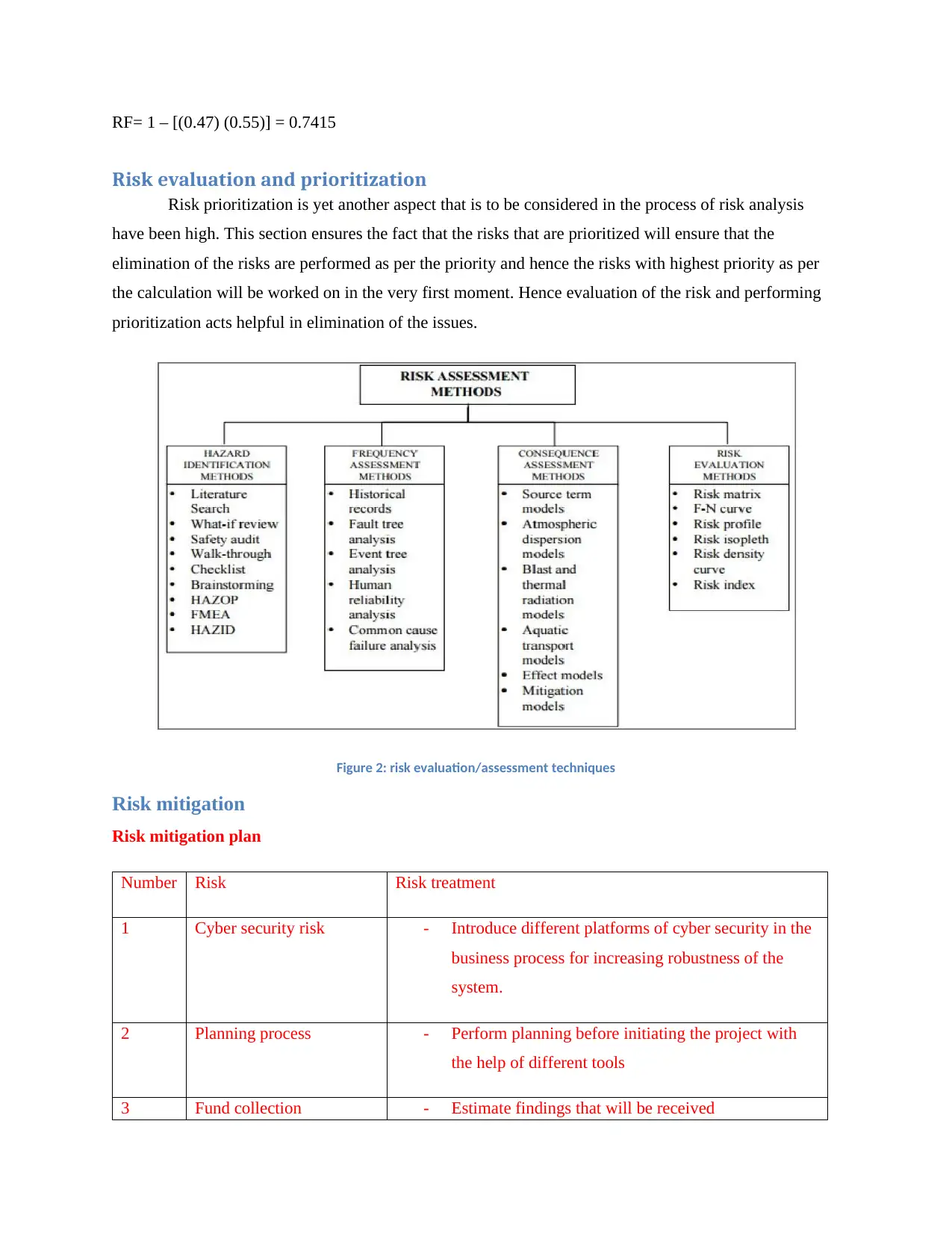
RF= 1 – [(0.47) (0.55)] = 0.7415
Risk evaluation and prioritization
Risk prioritization is yet another aspect that is to be considered in the process of risk analysis
have been high. This section ensures the fact that the risks that are prioritized will ensure that the
elimination of the risks are performed as per the priority and hence the risks with highest priority as per
the calculation will be worked on in the very first moment. Hence evaluation of the risk and performing
prioritization acts helpful in elimination of the issues.
Figure 2: risk evaluation/assessment techniques
Risk mitigation
Risk mitigation plan
Number Risk Risk treatment
1 Cyber security risk - Introduce different platforms of cyber security in the
business process for increasing robustness of the
system.
2 Planning process - Perform planning before initiating the project with
the help of different tools
3 Fund collection - Estimate findings that will be received
Risk evaluation and prioritization
Risk prioritization is yet another aspect that is to be considered in the process of risk analysis
have been high. This section ensures the fact that the risks that are prioritized will ensure that the
elimination of the risks are performed as per the priority and hence the risks with highest priority as per
the calculation will be worked on in the very first moment. Hence evaluation of the risk and performing
prioritization acts helpful in elimination of the issues.
Figure 2: risk evaluation/assessment techniques
Risk mitigation
Risk mitigation plan
Number Risk Risk treatment
1 Cyber security risk - Introduce different platforms of cyber security in the
business process for increasing robustness of the
system.
2 Planning process - Perform planning before initiating the project with
the help of different tools
3 Fund collection - Estimate findings that will be received
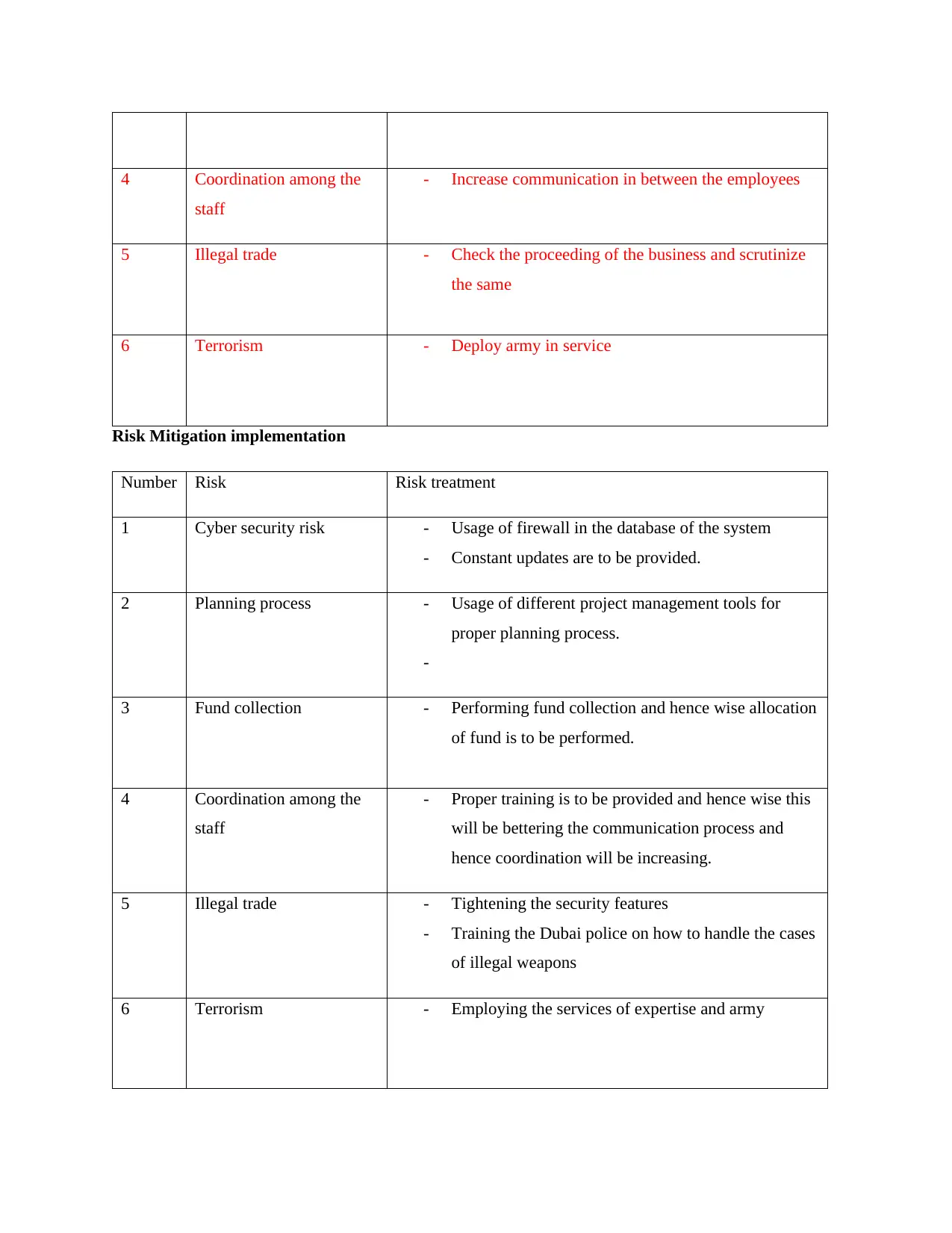
4 Coordination among the
staff
- Increase communication in between the employees
5 Illegal trade - Check the proceeding of the business and scrutinize
the same
6 Terrorism - Deploy army in service
Risk Mitigation implementation
Number Risk Risk treatment
1 Cyber security risk - Usage of firewall in the database of the system
- Constant updates are to be provided.
2 Planning process - Usage of different project management tools for
proper planning process.
-
3 Fund collection - Performing fund collection and hence wise allocation
of fund is to be performed.
4 Coordination among the
staff
- Proper training is to be provided and hence wise this
will be bettering the communication process and
hence coordination will be increasing.
5 Illegal trade - Tightening the security features
- Training the Dubai police on how to handle the cases
of illegal weapons
6 Terrorism - Employing the services of expertise and army
staff
- Increase communication in between the employees
5 Illegal trade - Check the proceeding of the business and scrutinize
the same
6 Terrorism - Deploy army in service
Risk Mitigation implementation
Number Risk Risk treatment
1 Cyber security risk - Usage of firewall in the database of the system
- Constant updates are to be provided.
2 Planning process - Usage of different project management tools for
proper planning process.
-
3 Fund collection - Performing fund collection and hence wise allocation
of fund is to be performed.
4 Coordination among the
staff
- Proper training is to be provided and hence wise this
will be bettering the communication process and
hence coordination will be increasing.
5 Illegal trade - Tightening the security features
- Training the Dubai police on how to handle the cases
of illegal weapons
6 Terrorism - Employing the services of expertise and army
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




