Security Service Ltd: IS Value, Strategy, Potential, and IT Location
VerifiedAdded on 2024/06/28
|10
|2464
|398
Report
AI Summary
This report examines Security Service Limited's (SSL) information systems, focusing on value identification, strategic alignment, and investment potential. It analyzes how SSL can identify the value derived from its current IS portfolio and evaluates techniques for assessing future IS investments. The report explores the construction of a coherent IS strategy supportive of SSL's business strategy and the benefits derived from it. Furthermore, it investigates the strategic potential for greater investment in information systems and technology at SSL from both divisional and company-wide perspectives, considering the utility of business process re-engineering. Finally, the report describes the current location of IS functions within SSL and recommends the optimal future location for IT services, offering a comprehensive overview of SSL's IS landscape and strategic opportunities.
Security Service Limited
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................3
Q1 Analyse how SSL may identify the value that it obtains from its current portfolio of
information systems and evaluate the techniques that may be used in assessing future IS
investments...................................................................................................................................... 4
Q2 In many parts of the company, it is clear that SSL does not have a coherent IS strategy.
Analyze how it may construct an IS strategy that is supportive of its business strategy and the
benefits that it would derive from this............................................................................................. 6
Q3 Analyse the strategic potential for greater investment in information systems and technology
at SSL both from a divisional and company-wide perspective. Could the business process re-
engineering be a useful tool in maximizing the potential of IS and IT within the company?
Explain and justify your answers.....................................................................................................7
Q4 Describe the current location of IS functions within SSL. Recommend the best location for IT
services in the future........................................................................................................................ 8
Conclusion....................................................................................................................................... 9
References......................................................................................................................................10
Introduction......................................................................................................................................3
Q1 Analyse how SSL may identify the value that it obtains from its current portfolio of
information systems and evaluate the techniques that may be used in assessing future IS
investments...................................................................................................................................... 4
Q2 In many parts of the company, it is clear that SSL does not have a coherent IS strategy.
Analyze how it may construct an IS strategy that is supportive of its business strategy and the
benefits that it would derive from this............................................................................................. 6
Q3 Analyse the strategic potential for greater investment in information systems and technology
at SSL both from a divisional and company-wide perspective. Could the business process re-
engineering be a useful tool in maximizing the potential of IS and IT within the company?
Explain and justify your answers.....................................................................................................7
Q4 Describe the current location of IS functions within SSL. Recommend the best location for IT
services in the future........................................................................................................................ 8
Conclusion....................................................................................................................................... 9
References......................................................................................................................................10

Introduction
The organization Security Service Limited has seen a large increment in its growth in the last
three decades in being among the major organizations that provide private services in the sector
of security in the United Kingdom. The total benefit for the financial year that was terminated in
April 1995 was increased by 17 percent to 98.4mn euros from the last year. The beneficially has
stayed stable at almost 10 percent of the total benefit for back to back 3 years. The Security
Service Limited has provided a large bracket of services to the organization, a person and even
the public sector. The organization owes to various factors that include the growth by the help of
the actual business, startups in the related sectors of securities. In the course of this document,
the dos and don’ts of the information systems of the SSL are discussed, while going through this
report a learner would be able to answer questions such as analysis of the ways by which the
organization would identify the value if the information systems or the strategies for planning of
the informational systems or their strategic potential and functions within it.
The organization Security Service Limited has seen a large increment in its growth in the last
three decades in being among the major organizations that provide private services in the sector
of security in the United Kingdom. The total benefit for the financial year that was terminated in
April 1995 was increased by 17 percent to 98.4mn euros from the last year. The beneficially has
stayed stable at almost 10 percent of the total benefit for back to back 3 years. The Security
Service Limited has provided a large bracket of services to the organization, a person and even
the public sector. The organization owes to various factors that include the growth by the help of
the actual business, startups in the related sectors of securities. In the course of this document,
the dos and don’ts of the information systems of the SSL are discussed, while going through this
report a learner would be able to answer questions such as analysis of the ways by which the
organization would identify the value if the information systems or the strategies for planning of
the informational systems or their strategic potential and functions within it.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Q1 Analyse how SSL may identify the value that it obtains from its current portfolio of
information systems and evaluate the techniques that may be used in assessing future IS
investments.
The choice of doing investment in the information systems is known to be among the greatest
challenges that are faced by almost every organization in the current times. As per the previous
studies that are done in the past on the same topic, in the last 20-30 years, the organizations that
are present around the globe have begun to realize that they are in a big and urgent requirement
of implementing the information system in their business. It has been almost impossible to avoid
the value of profits and a chance to create an increment in the performance by the help of this
kind of investment. It did not take long to observe that the information system has the ability to
support the business in order to cut short the expenses, creating increment in the competitive
benefits and enhancement of the performance and hence creation more benefits (Abbassi and
Khalid, 2014).
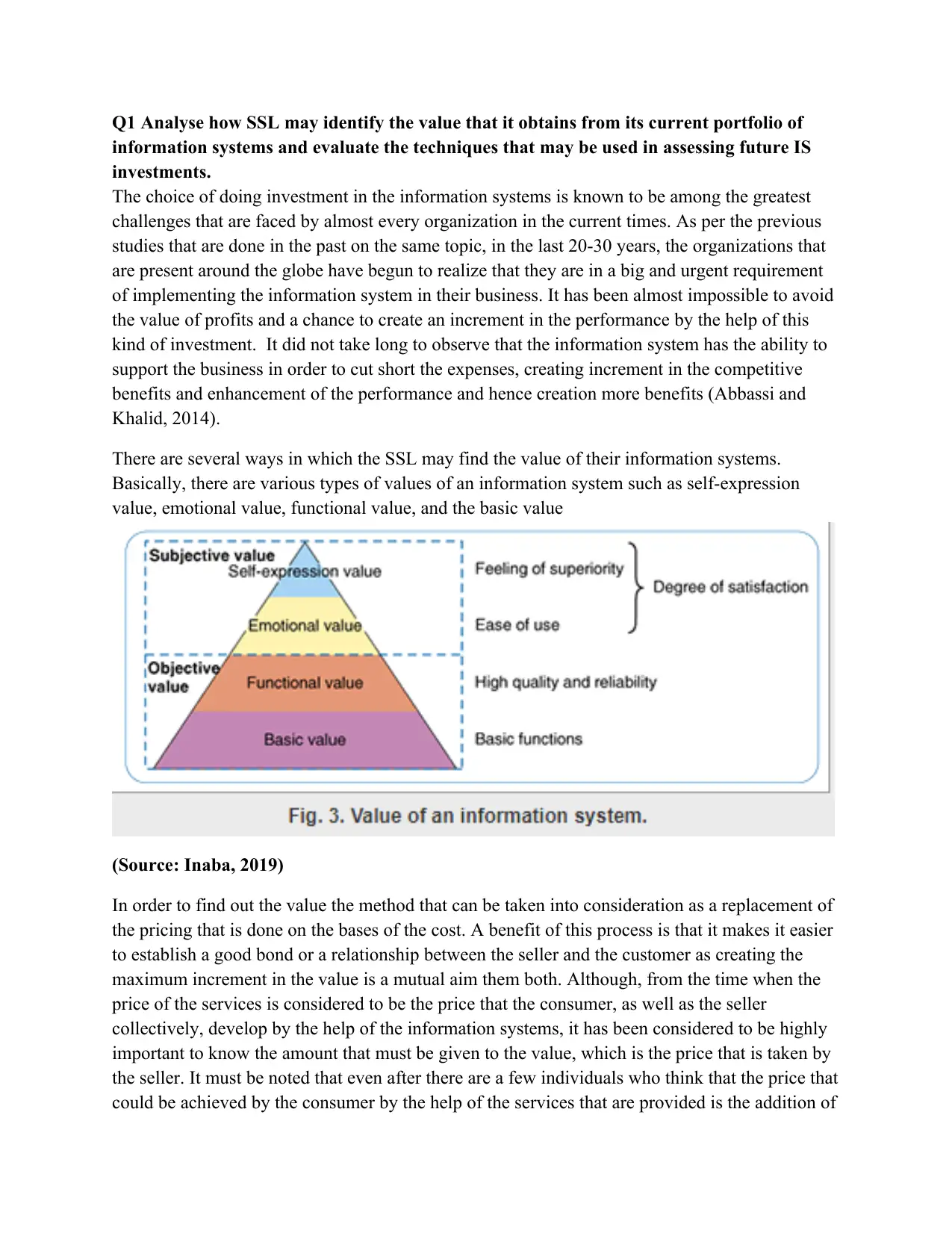
There are several ways in which the SSL may find the value of their information systems.
Basically, there are various types of values of an information system such as self-expression
value, emotional value, functional value, and the basic value
(Source: Inaba, 2019)
In order to find out the value the method that can be taken into consideration as a replacement of
the pricing that is done on the bases of the cost. A benefit of this process is that it makes it easier
to establish a good bond or a relationship between the seller and the customer as creating the
maximum increment in the value is a mutual aim them both. Although, from the time when the
price of the services is considered to be the price that the consumer, as well as the seller
collectively, develop by the help of the information systems, it has been considered to be highly
important to know the amount that must be given to the value, which is the price that is taken by
the seller. It must be noted that even after there are a few individuals who think that the price that
could be achieved by the consumer by the help of the services that are provided is the addition of
information systems and evaluate the techniques that may be used in assessing future IS
investments.
The choice of doing investment in the information systems is known to be among the greatest
challenges that are faced by almost every organization in the current times. As per the previous
studies that are done in the past on the same topic, in the last 20-30 years, the organizations that
are present around the globe have begun to realize that they are in a big and urgent requirement
of implementing the information system in their business. It has been almost impossible to avoid
the value of profits and a chance to create an increment in the performance by the help of this
kind of investment. It did not take long to observe that the information system has the ability to
support the business in order to cut short the expenses, creating increment in the competitive
benefits and enhancement of the performance and hence creation more benefits (Abbassi and
Khalid, 2014).
There are several ways in which the SSL may find the value of their information systems.
Basically, there are various types of values of an information system such as self-expression
value, emotional value, functional value, and the basic value
(Source: Inaba, 2019)
In order to find out the value the method that can be taken into consideration as a replacement of
the pricing that is done on the bases of the cost. A benefit of this process is that it makes it easier
to establish a good bond or a relationship between the seller and the customer as creating the
maximum increment in the value is a mutual aim them both. Although, from the time when the
price of the services is considered to be the price that the consumer, as well as the seller
collectively, develop by the help of the information systems, it has been considered to be highly
important to know the amount that must be given to the value, which is the price that is taken by
the seller. It must be noted that even after there are a few individuals who think that the price that
could be achieved by the consumer by the help of the services that are provided is the addition of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
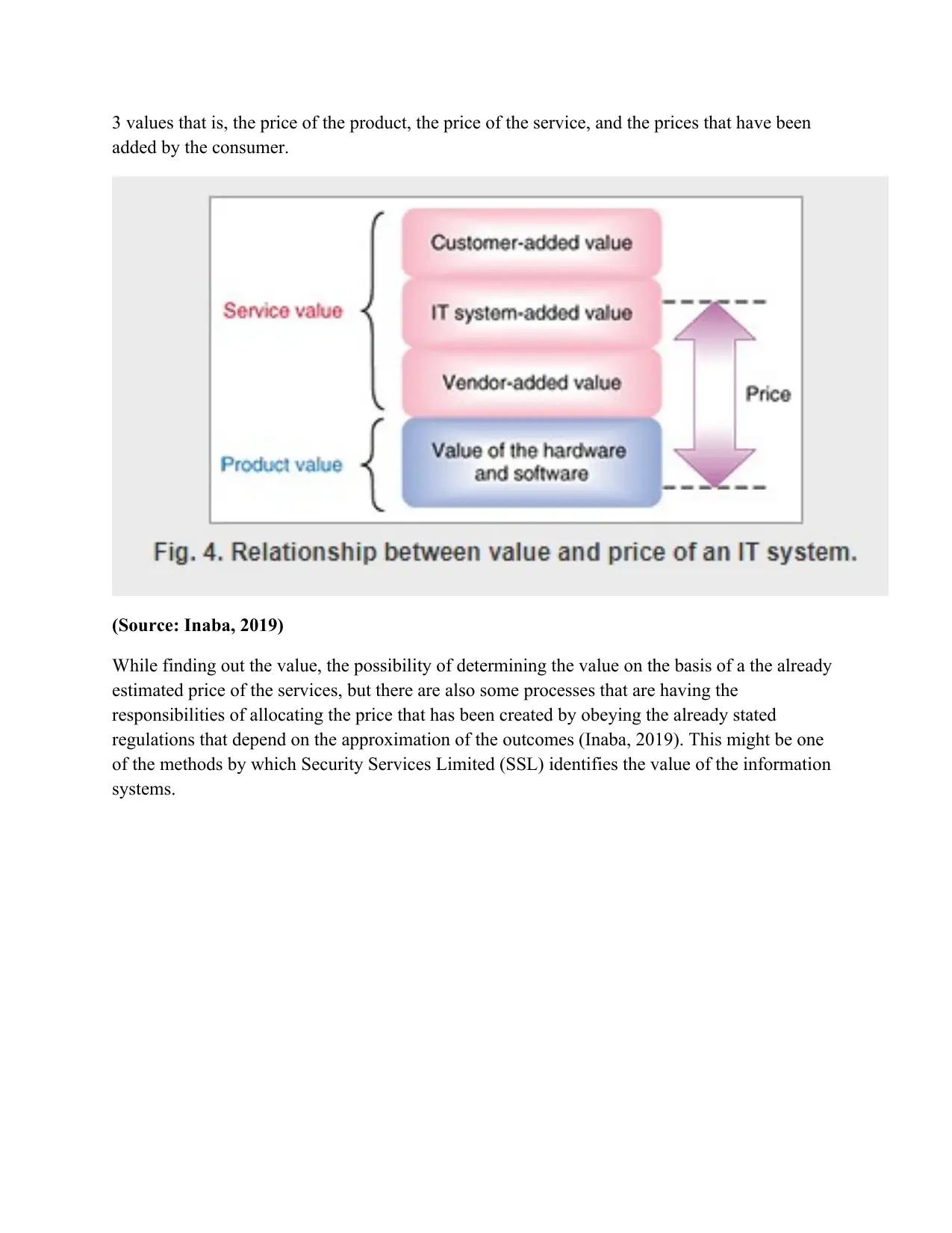
3 values that is, the price of the product, the price of the service, and the prices that have been
added by the consumer.
(Source: Inaba, 2019)
While finding out the value, the possibility of determining the value on the basis of a the already
estimated price of the services, but there are also some processes that are having the
responsibilities of allocating the price that has been created by obeying the already stated
regulations that depend on the approximation of the outcomes (Inaba, 2019). This might be one
of the methods by which Security Services Limited (SSL) identifies the value of the information
systems.
added by the consumer.
(Source: Inaba, 2019)
While finding out the value, the possibility of determining the value on the basis of a the already
estimated price of the services, but there are also some processes that are having the
responsibilities of allocating the price that has been created by obeying the already stated
regulations that depend on the approximation of the outcomes (Inaba, 2019). This might be one
of the methods by which Security Services Limited (SSL) identifies the value of the information
systems.

Q2 In many parts of the company, it is clear that SSL does not have a coherent IS strategy.
Analyze how it may construct an IS strategy that is supportive of its business strategy and
the benefits that it would derive from this.
An important component of realizing the strategies is the implementation of all the plannings that
are done until now. The implantation of all the planning that has been done till now is considered
to be an approach that is carried out gradually, the connection of determining factors of the
performances with initiatives that are taken for the strategies and processes that are created to
produce the organizational as well as personal actions. In a similar way, the implementation of
the strategies that are defined in the previous studies that are done in the past on the same topics
is considered to be the process of creating the ideas into action. It can be defined as the
conversion and execution of the intentions into the actual scenario (Marcial. 2013). The strategy
is made workable via the processes that are completely having the intention of the
implementation of the ideas that are segmented into various procedures. The execution is the
most important criterion that is having the usage of measuring the planning of success of the
information system. As per the previous studies that are done in the past on the same topic, it is
stated that the main issues that are faced during the execution of the ideas are: avoiding the
economic and financial aims, failure of the implementation of the financial and the economic
goals in to reality, and avoiding to have any kind of compromise with the plans of information
systems for the reflection of the key variation in the whole environment (Marcial. 2013).
The Strategic Planning of the Information System has in particular 3 essential keywords; those
keywords are Informational Systems, Plans, and Strategies. The informational system and the
information technologies are considered to be components of the plan. The Strategy that is
associated with the information technology is not having its derivation from the financial
strategies as the strategies that are associated with the information technology are having the
capabilities of having an impact on the business strategies (Harun and Hahsim, 2017). In
Security Services Limited (SSL) the same strategies must be applied in order to implement the
information systems.
Analyze how it may construct an IS strategy that is supportive of its business strategy and
the benefits that it would derive from this.
An important component of realizing the strategies is the implementation of all the plannings that
are done until now. The implantation of all the planning that has been done till now is considered
to be an approach that is carried out gradually, the connection of determining factors of the
performances with initiatives that are taken for the strategies and processes that are created to
produce the organizational as well as personal actions. In a similar way, the implementation of
the strategies that are defined in the previous studies that are done in the past on the same topics
is considered to be the process of creating the ideas into action. It can be defined as the
conversion and execution of the intentions into the actual scenario (Marcial. 2013). The strategy
is made workable via the processes that are completely having the intention of the
implementation of the ideas that are segmented into various procedures. The execution is the
most important criterion that is having the usage of measuring the planning of success of the
information system. As per the previous studies that are done in the past on the same topic, it is
stated that the main issues that are faced during the execution of the ideas are: avoiding the
economic and financial aims, failure of the implementation of the financial and the economic
goals in to reality, and avoiding to have any kind of compromise with the plans of information
systems for the reflection of the key variation in the whole environment (Marcial. 2013).
The Strategic Planning of the Information System has in particular 3 essential keywords; those
keywords are Informational Systems, Plans, and Strategies. The informational system and the
information technologies are considered to be components of the plan. The Strategy that is
associated with the information technology is not having its derivation from the financial
strategies as the strategies that are associated with the information technology are having the
capabilities of having an impact on the business strategies (Harun and Hahsim, 2017). In
Security Services Limited (SSL) the same strategies must be applied in order to implement the
information systems.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Q3 Analyse the strategic potential for greater investment in information systems and
technology at SSL both from a divisional and company-wide perspective. Could the
business process re-engineering be a useful tool in maximizing the potential of IS and IT
within the company? Explain and justify your answers.
It is not very hard to get that the usage of the conventional methods in the field of finances like
ROI and ROA that is the return on investments and return in asset, isn’t every time
comprehending enough to completely acknowledge the outcomes that have come out of
information technology use (Macada, et. al., 2012). The information technology is not a system
or a technology That automates the already present project, it is instead, a tool that has the usage
of publicizing the industrial variations that may take it to the extra benefits in performance,
profit, and the satisfactory outcomes and therefore the value of these variations would not be
having the ability of being gradually scaled with restricted economical as well as sensitive scales.
The importance of the studies that are acquired by the individuals who are working in the
organization, the application, the database and the industrial and consumer bonding capabilities
does not seem to be appearing in the conventional documentation of the accounts that are
associated with the information technology (Macada, et. al., 2012). Rather, the market value of
the information technology is far more understandable by just glancing at the results that it has
contributed in the direction of the volume that the individuals are having for the value of delivery
to the consumer. Therefore, it has been stated that the market price of the information systems
that are being used or in some way or the other associated to any firm of industry or a company,
is defined as the advantages that the information technologies provide in the direction of the
performances of the companies at the middle procedural levels like the value minimizations and
incremented performance scales in a particular job, and in the industrial surroundings too, such
as the development of the comparative benefits, this definition was created as per the studies that
has been done in the past on the same topic (Macada, et. al., 2012). In the Security Services
Limited (SSL) the investment would be having the same potential and hence the strategies that
are created must be thoroughly followed.
technology at SSL both from a divisional and company-wide perspective. Could the
business process re-engineering be a useful tool in maximizing the potential of IS and IT
within the company? Explain and justify your answers.
It is not very hard to get that the usage of the conventional methods in the field of finances like
ROI and ROA that is the return on investments and return in asset, isn’t every time
comprehending enough to completely acknowledge the outcomes that have come out of
information technology use (Macada, et. al., 2012). The information technology is not a system
or a technology That automates the already present project, it is instead, a tool that has the usage
of publicizing the industrial variations that may take it to the extra benefits in performance,
profit, and the satisfactory outcomes and therefore the value of these variations would not be
having the ability of being gradually scaled with restricted economical as well as sensitive scales.
The importance of the studies that are acquired by the individuals who are working in the
organization, the application, the database and the industrial and consumer bonding capabilities
does not seem to be appearing in the conventional documentation of the accounts that are
associated with the information technology (Macada, et. al., 2012). Rather, the market value of
the information technology is far more understandable by just glancing at the results that it has
contributed in the direction of the volume that the individuals are having for the value of delivery
to the consumer. Therefore, it has been stated that the market price of the information systems
that are being used or in some way or the other associated to any firm of industry or a company,
is defined as the advantages that the information technologies provide in the direction of the
performances of the companies at the middle procedural levels like the value minimizations and
incremented performance scales in a particular job, and in the industrial surroundings too, such
as the development of the comparative benefits, this definition was created as per the studies that
has been done in the past on the same topic (Macada, et. al., 2012). In the Security Services
Limited (SSL) the investment would be having the same potential and hence the strategies that
are created must be thoroughly followed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Q4 Describe the current location of IS functions within SSL. Recommend the best location
for IT services in the future.
Talking about the current location of the Security Services Limited (SSL) there is a great scope
improvement and that improvement is needed to be done as soon as possible. The current
locations of the Security Services Limited (SSL) are not having the ability to automatically send
the data or the information and that to from the location where the data was re-keyed only. As
per the documentation is done, apparently the department of the Security Services Limited (SSL)
that deals with the information technology are old fashioned in terms of the systems and
technologies and not well updated as the other departments are a great problem.
As per the given situation, the best location for the Security Services Limited (SSL) would be
where the sending of the information and the data would be automated and would not be needed
to be done manually. Also if the department of the Security Services Limited (SSL) that deals
with the Information Technology and the Information Systems must be updated and all the
technologies and the systems that were used there must be as latest as possible. The new DP
manager must be hired as soon as possible so that the headquarters and the divisions can be
managed in a proper manner
for IT services in the future.
Talking about the current location of the Security Services Limited (SSL) there is a great scope
improvement and that improvement is needed to be done as soon as possible. The current
locations of the Security Services Limited (SSL) are not having the ability to automatically send
the data or the information and that to from the location where the data was re-keyed only. As
per the documentation is done, apparently the department of the Security Services Limited (SSL)
that deals with the information technology are old fashioned in terms of the systems and
technologies and not well updated as the other departments are a great problem.
As per the given situation, the best location for the Security Services Limited (SSL) would be
where the sending of the information and the data would be automated and would not be needed
to be done manually. Also if the department of the Security Services Limited (SSL) that deals
with the Information Technology and the Information Systems must be updated and all the
technologies and the systems that were used there must be as latest as possible. The new DP
manager must be hired as soon as possible so that the headquarters and the divisions can be
managed in a proper manner

Conclusion
In the course of this document, the dos and don’ts of the information systems of the SSL are
discussed, while going through this report a learner would be able to answer questions such as
analysis of the ways by which the organization would identify the value if the information
systems or the strategies for planning of the informational systems or their strategic potential and
functions within it. In the whole report, it is tried to make the learner learn that the organization
Security Service Limited has seen a large increment in its growth in the last three decades in
being among the major organizations that provide private services in the sector of security in the
United Kingdoms. The total benefit for the financial year that was terminated in April 1995 was
increased by 17 percent to 98.4mn euros from the last year. The beneficially has stayed stable at
almost 10 percent of the total benefit for back to back 3 years. The Security Service Limited has
provided a large bracket of services to the organization, a person and even the public sector. The
organization owes to various factors that include the growth by the help of the actual business,
startups in the related sectors of securities.
In the course of this document, the dos and don’ts of the information systems of the SSL are
discussed, while going through this report a learner would be able to answer questions such as
analysis of the ways by which the organization would identify the value if the information
systems or the strategies for planning of the informational systems or their strategic potential and
functions within it. In the whole report, it is tried to make the learner learn that the organization
Security Service Limited has seen a large increment in its growth in the last three decades in
being among the major organizations that provide private services in the sector of security in the
United Kingdoms. The total benefit for the financial year that was terminated in April 1995 was
increased by 17 percent to 98.4mn euros from the last year. The beneficially has stayed stable at
almost 10 percent of the total benefit for back to back 3 years. The Security Service Limited has
provided a large bracket of services to the organization, a person and even the public sector. The
organization owes to various factors that include the growth by the help of the actual business,
startups in the related sectors of securities.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Inaba, Y., 2019, Method of Determining the Value of an Information Technology System
[Online]. NTT. Available at: https://www.ntt-review.jp/archive/ntttechnical.php?
contents=ntr200807sf2.html [Accessed on 4th June 2019]
Abbassi, A. and Khalid, C., 2014, The Decision to Invest in Information Systems: Case
of Adopting ERP in the Moroccan Public Largest Companies. International Journal of
Computer Applications. 88(15). Pp. 49-54
Marcial, D., E., 2013, Information Systems Strategic Planning in Higher Education
Institutions in the Philippines. Philippine Information Technology Journal. 6(2). Pp. 1-8
Harun, H. and Hashim, M., K., 2017, STRATEGIC INFORMATION SYSTEMS
PLANNING: A REVIEW OF ITS CONCEPT, DEFINITIONS, AND STAGES OF
DEVELOPMENT. International Journal of Research In Science & Engineering. 3(2). Pp.
432-441
Macada, A., C., G., Beltrame, M., M., Dolci, P., C. and Becker, J., L., 2012, IT Business
Value Model for Information Intensive Organizations. Brazilian Administration Review.
9(1). Pp. 44-65
Inaba, Y., 2019, Method of Determining the Value of an Information Technology System
[Online]. NTT. Available at: https://www.ntt-review.jp/archive/ntttechnical.php?
contents=ntr200807sf2.html [Accessed on 4th June 2019]
Abbassi, A. and Khalid, C., 2014, The Decision to Invest in Information Systems: Case
of Adopting ERP in the Moroccan Public Largest Companies. International Journal of
Computer Applications. 88(15). Pp. 49-54
Marcial, D., E., 2013, Information Systems Strategic Planning in Higher Education
Institutions in the Philippines. Philippine Information Technology Journal. 6(2). Pp. 1-8
Harun, H. and Hashim, M., K., 2017, STRATEGIC INFORMATION SYSTEMS
PLANNING: A REVIEW OF ITS CONCEPT, DEFINITIONS, AND STAGES OF
DEVELOPMENT. International Journal of Research In Science & Engineering. 3(2). Pp.
432-441
Macada, A., C., G., Beltrame, M., M., Dolci, P., C. and Becker, J., L., 2012, IT Business
Value Model for Information Intensive Organizations. Brazilian Administration Review.
9(1). Pp. 44-65
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


