Network Security Report: ECHRS Ltd. Case Study and Analysis
VerifiedAdded on 2022/10/11
|22
|5061
|22
Report
AI Summary
This report provides an in-depth analysis of network security, focusing on the threats and vulnerabilities faced by IT-based companies, particularly using the case study of ECHRS Ltd. The report begins by outlining current security threats such as computer viruses, hackers, spyware, phishing, and SQL injection, and then discusses various tools and techniques to mitigate these threats, including encryption and vulnerability identification. It then assesses ECHRS Ltd.'s IT infrastructure, identifying vulnerabilities such as outdated systems, lack of a robust framework, and firewall configuration issues. The report considers legal, ethical, and professional issues, including GDPR compliance, and recommends specific security enhancements. The report highlights the importance of proactive and adaptive cybersecurity approaches to protect sensitive data and ensure the integrity of the network. Finally, the report concludes with a call for improved security measures and provides recommendations for ECHRS Ltd. to strengthen its network security posture and protect its clients and employees.
Running Head: Security of Network 0
Security of Network
Report
Student name
Security of Network
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security of Network 1
Table of Contents
Introduction......................................................................................................................................1
Task 1...............................................................................................................................................2
Current security threats................................................................................................................2
Computer viruses:.....................................................................................................................2
Hackers and Predators..............................................................................................................3
Spyware threats........................................................................................................................3
Phishing....................................................................................................................................3
SQL injection...........................................................................................................................3
Tools and techniques....................................................................................................................4
Encryption:...............................................................................................................................4
Vulnerabilities identification....................................................................................................4
Consideration of legal, ethical and professional issues................................................................4
Task 2...............................................................................................................................................5
Vulnerabilities in the company....................................................................................................8
Lack of updated in systems:.....................................................................................................8
No framework:.........................................................................................................................8
Firewall configuration:.............................................................................................................8
Selection, justification, and Evaluation........................................................................................9
Critical reflection.......................................................................................................................12
Recommendations..........................................................................................................................14
Conclusion.....................................................................................................................................15
References......................................................................................................................................16
Table of Contents
Introduction......................................................................................................................................1
Task 1...............................................................................................................................................2
Current security threats................................................................................................................2
Computer viruses:.....................................................................................................................2
Hackers and Predators..............................................................................................................3
Spyware threats........................................................................................................................3
Phishing....................................................................................................................................3
SQL injection...........................................................................................................................3
Tools and techniques....................................................................................................................4
Encryption:...............................................................................................................................4
Vulnerabilities identification....................................................................................................4
Consideration of legal, ethical and professional issues................................................................4
Task 2...............................................................................................................................................5
Vulnerabilities in the company....................................................................................................8
Lack of updated in systems:.....................................................................................................8
No framework:.........................................................................................................................8
Firewall configuration:.............................................................................................................8
Selection, justification, and Evaluation........................................................................................9
Critical reflection.......................................................................................................................12
Recommendations..........................................................................................................................14
Conclusion.....................................................................................................................................15
References......................................................................................................................................16
Security of Network 2
Introduction
In this report, task 1 will describe the security techniques for IT-based companies in the UK. In
task 2, it will explain about the issues of ECHRS Ltd with their IT Services and Its infrastructure.
It will include cybersecurity and other frameworks to secure their data from the third party.
Task 1
Equifax is a good and popular company in the UK. It provides various services to its customers.
It provides global information solution to their clients. It uses data analytics, unique data,
information technology, and experts for providing solutions. A computer network is an important
thing for an organization. A network is a group of computer systems and other networking
devices including router, switch, data centers, and other peripherals ( Beaver, 2013). There are
few things, which are a matter a lot for a network, which is the privacy and security of the data
and information. In addition, network management and controls are necessary to identify all the
things properly (Forouzan, 2007).
Current security threats
In the present era, various security threats are present in the network, which can damage data and
other things using malfunctions (Certiology, 2018). There are various threats for users and
companies for their data. Equifax is a well-known company of the UK, which has been faced
data breach in 2017 in which the company losses 143,000,000 number of records of financial and
credit reporting because of poor security. The company has few loopholes in their security.
There are some specific types of security threats are present in the environment, which can make
a huge impact on the reputation of Equifax, which areas:
Introduction
In this report, task 1 will describe the security techniques for IT-based companies in the UK. In
task 2, it will explain about the issues of ECHRS Ltd with their IT Services and Its infrastructure.
It will include cybersecurity and other frameworks to secure their data from the third party.
Task 1
Equifax is a good and popular company in the UK. It provides various services to its customers.
It provides global information solution to their clients. It uses data analytics, unique data,
information technology, and experts for providing solutions. A computer network is an important
thing for an organization. A network is a group of computer systems and other networking
devices including router, switch, data centers, and other peripherals ( Beaver, 2013). There are
few things, which are a matter a lot for a network, which is the privacy and security of the data
and information. In addition, network management and controls are necessary to identify all the
things properly (Forouzan, 2007).
Current security threats
In the present era, various security threats are present in the network, which can damage data and
other things using malfunctions (Certiology, 2018). There are various threats for users and
companies for their data. Equifax is a well-known company of the UK, which has been faced
data breach in 2017 in which the company losses 143,000,000 number of records of financial and
credit reporting because of poor security. The company has few loopholes in their security.
There are some specific types of security threats are present in the environment, which can make
a huge impact on the reputation of Equifax, which areas:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security of Network 3
Computer viruses:
Computer viruses are complex computer programs, which make a huge impact on the data and
processing of computer systems. In addition, these programs can damage the software of the
computer systems as well as a network of the company. The company can use proper antiviruses
to stop these programs from internal and external networks (Coles, 2018).
Hackers and Predators
A normal person can access another person’s computer system using his or her personal
information and other data, which is easily available. Therefore, it is necessary to secure all the
personal data from strangers in online activities ( Dosal, 2018). They access the system and theft
important information of the victim and use that information in their personal uses. It is a serious
issue in front of a normal user as well as a professional user. Therefore, always use protection to
secure all the documents and credentials from hackers (Du & Chen, 2008).
Spyware threats
A severe laptop protection risk, spyware can access the devices and monitor them using online
activities and take permission for the installation of third-party software, which can access the
permission of the whole system ( Dosal, 2018). In addition, some users share their marketing
information for data analysis and other official works, which is not good for the reputation of the
company (Cowley, 2012).
Phishing
An attacker’s access economic information of the user for personal and third party uses in a
process. It is a bad practice of hackers to identify the data on the client's systems and access that
data without the permission of that user (Dye, et al., 2007). Phishing attacks are some of the
Computer viruses:
Computer viruses are complex computer programs, which make a huge impact on the data and
processing of computer systems. In addition, these programs can damage the software of the
computer systems as well as a network of the company. The company can use proper antiviruses
to stop these programs from internal and external networks (Coles, 2018).
Hackers and Predators
A normal person can access another person’s computer system using his or her personal
information and other data, which is easily available. Therefore, it is necessary to secure all the
personal data from strangers in online activities ( Dosal, 2018). They access the system and theft
important information of the victim and use that information in their personal uses. It is a serious
issue in front of a normal user as well as a professional user. Therefore, always use protection to
secure all the documents and credentials from hackers (Du & Chen, 2008).
Spyware threats
A severe laptop protection risk, spyware can access the devices and monitor them using online
activities and take permission for the installation of third-party software, which can access the
permission of the whole system ( Dosal, 2018). In addition, some users share their marketing
information for data analysis and other official works, which is not good for the reputation of the
company (Cowley, 2012).
Phishing
An attacker’s access economic information of the user for personal and third party uses in a
process. It is a bad practice of hackers to identify the data on the client's systems and access that
data without the permission of that user (Dye, et al., 2007). Phishing attacks are some of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Security of Network 4
most successful techniques for cybercriminals. In addition, they are accessing all the information
and share that information with another person for personal benefits (Forouzan, 2007).
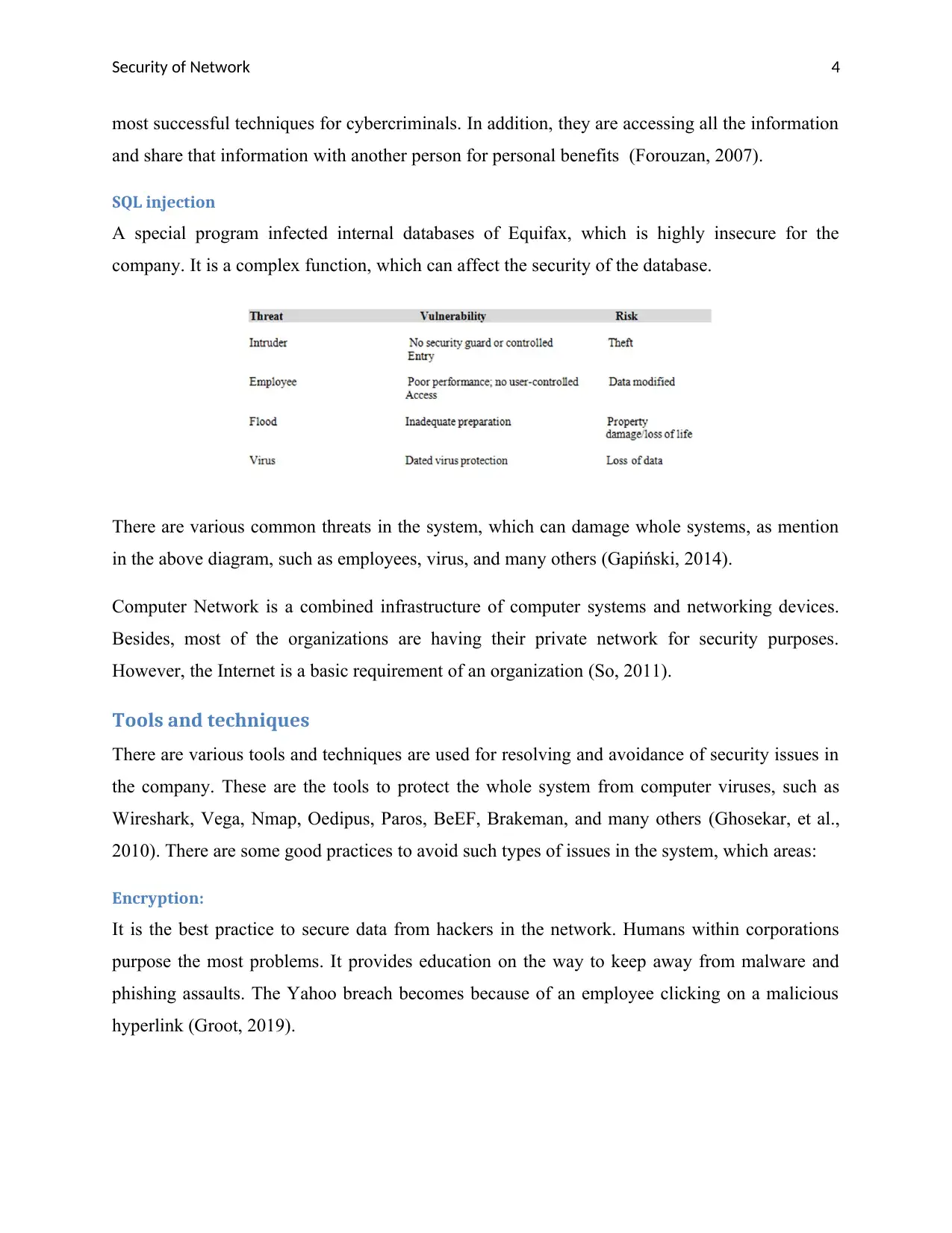
SQL injection
A special program infected internal databases of Equifax, which is highly insecure for the
company. It is a complex function, which can affect the security of the database.
There are various common threats in the system, which can damage whole systems, as mention
in the above diagram, such as employees, virus, and many others (Gapiński, 2014).
Computer Network is a combined infrastructure of computer systems and networking devices.
Besides, most of the organizations are having their private network for security purposes.
However, the Internet is a basic requirement of an organization (So, 2011).
Tools and techniques
There are various tools and techniques are used for resolving and avoidance of security issues in
the company. These are the tools to protect the whole system from computer viruses, such as
Wireshark, Vega, Nmap, Oedipus, Paros, BeEF, Brakeman, and many others (Ghosekar, et al.,
2010). There are some good practices to avoid such types of issues in the system, which areas:
Encryption:
It is the best practice to secure data from hackers in the network. Humans within corporations
purpose the most problems. It provides education on the way to keep away from malware and
phishing assaults. The Yahoo breach becomes because of an employee clicking on a malicious
hyperlink (Groot, 2019).
most successful techniques for cybercriminals. In addition, they are accessing all the information
and share that information with another person for personal benefits (Forouzan, 2007).
SQL injection
A special program infected internal databases of Equifax, which is highly insecure for the
company. It is a complex function, which can affect the security of the database.
There are various common threats in the system, which can damage whole systems, as mention
in the above diagram, such as employees, virus, and many others (Gapiński, 2014).
Computer Network is a combined infrastructure of computer systems and networking devices.
Besides, most of the organizations are having their private network for security purposes.
However, the Internet is a basic requirement of an organization (So, 2011).
Tools and techniques
There are various tools and techniques are used for resolving and avoidance of security issues in
the company. These are the tools to protect the whole system from computer viruses, such as
Wireshark, Vega, Nmap, Oedipus, Paros, BeEF, Brakeman, and many others (Ghosekar, et al.,
2010). There are some good practices to avoid such types of issues in the system, which areas:
Encryption:
It is the best practice to secure data from hackers in the network. Humans within corporations
purpose the most problems. It provides education on the way to keep away from malware and
phishing assaults. The Yahoo breach becomes because of an employee clicking on a malicious
hyperlink (Groot, 2019).

Security of Network 5
Vulnerabilities identification
It is necessary to identify vulnerabilities of the system and remove it as soon as possible to
secure the whole systems from various security issues because of that vulnerability (Hern, 2018).
Consideration of legal, ethical and professional issues
There are many legal rules and regulations have created for the security of information assets by
the local and federal governments to secure personal data and financial information. In addition,
laws are those rules that mandate the behavior of people in accessing data and other assets (Jain,
2011). Laws are drawn from ethics. Therefore, ethics are necessary for information security and
other things. In addition, laws carry the authority of different government bodies to protect the
system from cybercrimes. However, ethics do not carry any authority of government agencies
(Kenneth C. Mansfield & Antonakos, 2009).
In addition, there is a huge impact on social and ethical issues on the security of the company. It
is necessary to provide training to the employees to understand cybersecurity and other
securities. It will provide better results for the company in terms of security (Mahto & Yadav,
2017). Besides, there are some internal security issues in the company, which is poor security
management. Therefore, the company must provide full security to its information security.
Vulnerabilities identification
It is necessary to identify vulnerabilities of the system and remove it as soon as possible to
secure the whole systems from various security issues because of that vulnerability (Hern, 2018).
Consideration of legal, ethical and professional issues
There are many legal rules and regulations have created for the security of information assets by
the local and federal governments to secure personal data and financial information. In addition,
laws are those rules that mandate the behavior of people in accessing data and other assets (Jain,
2011). Laws are drawn from ethics. Therefore, ethics are necessary for information security and
other things. In addition, laws carry the authority of different government bodies to protect the
system from cybercrimes. However, ethics do not carry any authority of government agencies
(Kenneth C. Mansfield & Antonakos, 2009).
In addition, there is a huge impact on social and ethical issues on the security of the company. It
is necessary to provide training to the employees to understand cybersecurity and other
securities. It will provide better results for the company in terms of security (Mahto & Yadav,
2017). Besides, there are some internal security issues in the company, which is poor security
management. Therefore, the company must provide full security to its information security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security of Network 6
There are many security solutions available in the market, such as cybersecurity, security
software, and hardware (Masucci, 2016).
The company uses various social media for marketing and advertising. It is a useful thing to
analyze market-using data analytics based on social media data. The company uses DMZ and
Virtual Private Network (VPN) for security of the data. However, the company faced data
breaches because of poor security.
There are many security solutions available in the market, such as cybersecurity, security
software, and hardware (Masucci, 2016).
The company uses various social media for marketing and advertising. It is a useful thing to
analyze market-using data analytics based on social media data. The company uses DMZ and
Virtual Private Network (VPN) for security of the data. However, the company faced data
breaches because of poor security.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security of Network 7
Task 2
ECHRS Ltd has implemented a proper network to manage their various things. It provides
services in the healthcare sector. All the processes are properly monitored using DMZ and other
firewalls. In addition, the company has situated in Bradford. It provides web-portal and
telephone outsourcing services to various companies including payroll, and human resources
records. Besides, the company has a specialist division in Leicester, which handles health
services on causal zero-hour contracts with the help of doctors and nurses. The company has
maintained external clients from the ECHRS staff at Bradford.
In addition, General Data Protection Regulation (GDPR) has used for ethical and legal regulation
in the company, as the data of company and their customer’s data. Moreover, the company has a
proper IT infrastructure at Bradford, which full fill the basic requirements of all the clients. In the
present time, the company has implemented this hardware and software at the Bradford location,
which areas:
Personal computer with Windows 10 operating system
Windows Server 2012 R2 to run IIS web server and remote desktop services
FAX services
VoIP telephony server
Task 2
ECHRS Ltd has implemented a proper network to manage their various things. It provides
services in the healthcare sector. All the processes are properly monitored using DMZ and other
firewalls. In addition, the company has situated in Bradford. It provides web-portal and
telephone outsourcing services to various companies including payroll, and human resources
records. Besides, the company has a specialist division in Leicester, which handles health
services on causal zero-hour contracts with the help of doctors and nurses. The company has
maintained external clients from the ECHRS staff at Bradford.
In addition, General Data Protection Regulation (GDPR) has used for ethical and legal regulation
in the company, as the data of company and their customer’s data. Moreover, the company has a
proper IT infrastructure at Bradford, which full fill the basic requirements of all the clients. In the
present time, the company has implemented this hardware and software at the Bradford location,
which areas:
Personal computer with Windows 10 operating system
Windows Server 2012 R2 to run IIS web server and remote desktop services
FAX services
VoIP telephony server

Security of Network 8
The company makes a backup in magnetic tape, which is stored in the fireproof safe that is
situated at Bradford. The company has used GoDaddy to provide web and email services to their
clients. That division uses different types of systems, which are having Windows XP operating
systems as well as Windows 10 operating systems. All the staff members are using email
services though personal computer systems and few are accessing on their mobile devices as
well.
In addition, ISO/IEC 27001 framework is highly used at the international level to secure all
things properly. It has included audit process to know about the vulnerability and threats in the
system. Moreover, it is necessary to identify the vulnerabilities of the system and reduce them
for overcoming the losses of the system.
In addition, sometimes doctors have required remote desktop services to create notes about the
patients before making a report. Therefore, it is necessary to provide remote desktop service to
them to access the system from their home PCs.
The maximum tough undertaking in cyber safety is the ever-evolving nature of protection risks
themselves. Traditionally, companies and the government have centered most in their cyber
safety assets on perimeter protection to shield the simplest their maximum important system
The company makes a backup in magnetic tape, which is stored in the fireproof safe that is
situated at Bradford. The company has used GoDaddy to provide web and email services to their
clients. That division uses different types of systems, which are having Windows XP operating
systems as well as Windows 10 operating systems. All the staff members are using email
services though personal computer systems and few are accessing on their mobile devices as
well.
In addition, ISO/IEC 27001 framework is highly used at the international level to secure all
things properly. It has included audit process to know about the vulnerability and threats in the
system. Moreover, it is necessary to identify the vulnerabilities of the system and reduce them
for overcoming the losses of the system.
In addition, sometimes doctors have required remote desktop services to create notes about the
patients before making a report. Therefore, it is necessary to provide remote desktop service to
them to access the system from their home PCs.
The maximum tough undertaking in cyber safety is the ever-evolving nature of protection risks
themselves. Traditionally, companies and the government have centered most in their cyber
safety assets on perimeter protection to shield the simplest their maximum important system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Security of Network 9
components and shield against regarded treats. These days, this approach is inadequate, because
the threats develop and change speedier than groups can preserve up with. As a result, advisory
companies sell greater proactive and adaptive methods of cyber safety ( Dosal, 2018).
The issue is that ECHRS believes that data of the company has been breach from the third party
using any unofficial method. The company has suffered an intrusion. According to the General
Data Protection Regulation (GDPR), this type of condition is not good for the company because
personal and payroll data is highly sensitive for the company and its employees as well as
customers. Therefore, the company should make a decision to stop such type of issues on high
priority. In addition, the company has been found that some details of external clients' employees
with health reports.
Vulnerabilities in the company
The company has much vulnerability because of old systems and lack of update devices and
software. These are the vulnerabilities of the company:
Lack of updated in systems:
Computer systems are not properly updated with the advanced operating systems, such as
Windows 10, and others. Those systems are able to handle various types of security issues based
on their program definitions. Therefore, all the systems should update with Windows 10
operating systems with the latest patch (Yadav, 2018).
components and shield against regarded treats. These days, this approach is inadequate, because
the threats develop and change speedier than groups can preserve up with. As a result, advisory
companies sell greater proactive and adaptive methods of cyber safety ( Dosal, 2018).
The issue is that ECHRS believes that data of the company has been breach from the third party
using any unofficial method. The company has suffered an intrusion. According to the General
Data Protection Regulation (GDPR), this type of condition is not good for the company because
personal and payroll data is highly sensitive for the company and its employees as well as
customers. Therefore, the company should make a decision to stop such type of issues on high
priority. In addition, the company has been found that some details of external clients' employees
with health reports.
Vulnerabilities in the company
The company has much vulnerability because of old systems and lack of update devices and
software. These are the vulnerabilities of the company:
Lack of updated in systems:
Computer systems are not properly updated with the advanced operating systems, such as
Windows 10, and others. Those systems are able to handle various types of security issues based
on their program definitions. Therefore, all the systems should update with Windows 10
operating systems with the latest patch (Yadav, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security of Network 10
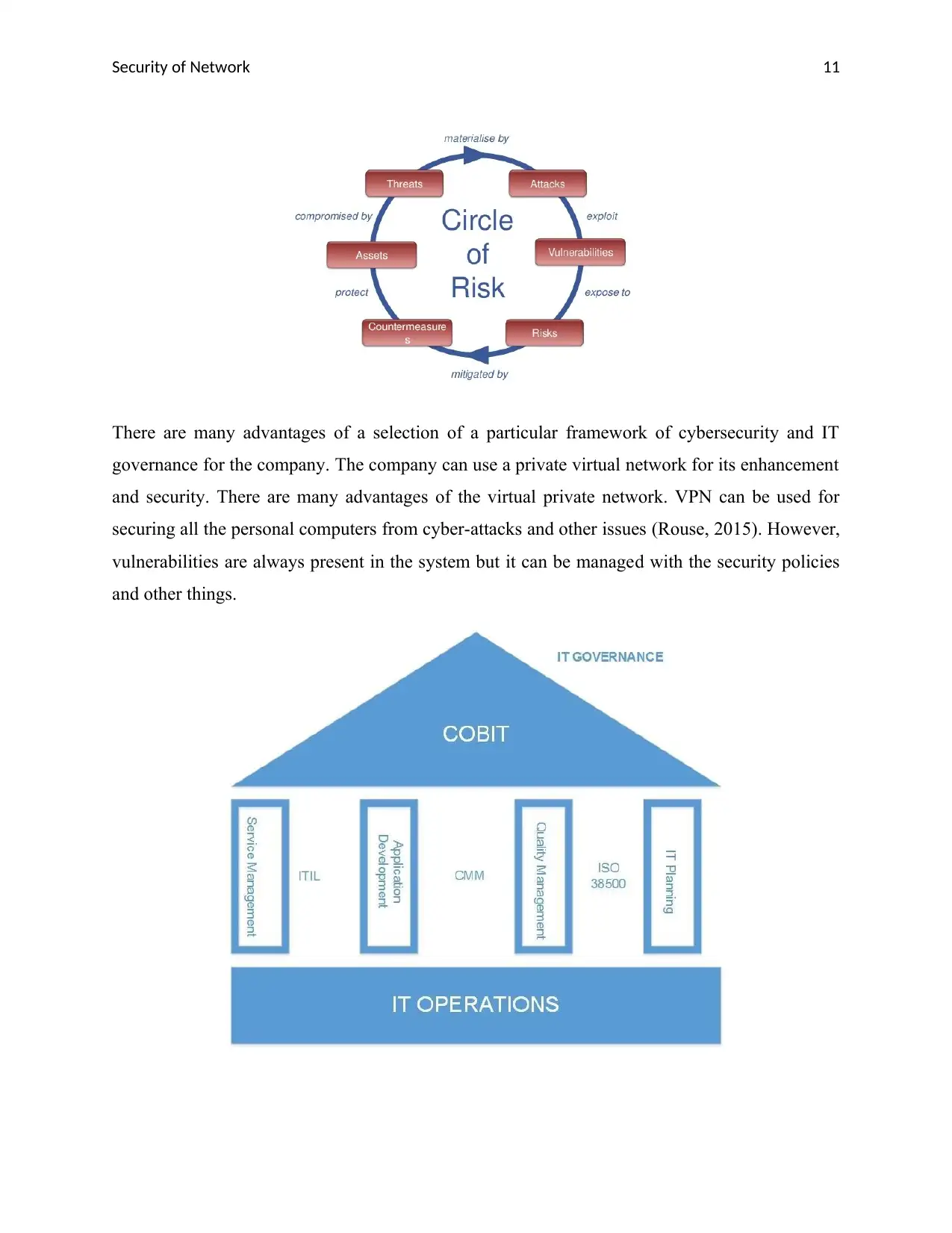
The threat is always finding a vulnerability to break the protection of the system or assets of the
organization. In addition, all those vulnerabilities make a way for threats to enter in the whole
system. Therefore, it is necessary to reduce the vulnerabilities of the system (Techdonut, 2018).
No framework:
The company should use the IT governance framework to monitor all the threats and
vulnerabilities of the system to reduce risks from the system. In addition, the IT governance
framework will provide full protection to the systems as well as the client’s data as well. There
are various types of IT governance frameworks are available in the market to secure the whole
system from cyber-attacks, such as COBIT, ISO/IEC 27001, ITIL, and many others (Subashini
& Kavitha, 2011).
Firewall configuration:
The company must configure their firewalls and other IDS and IPS systems to secure the whole
network of the company as well as different sites of the company. It will provide a high level of
network security to the company (Security-trails, 2018). Firewalls can reduce the chances of
cyber-attacks, as it secures all the incoming connection and other outgoing packets as well
(Tanenbaum, 2014).
Selection, justification, and Evaluation
Cybersecurity is a necessary thing for the company because the company has many personal data
of its clients as well as their employees. Therefore, the company is responsible for all data and
information of their clients because they stored all the data in their systems and databases. In
addition, there are many other issues of an organization, which are related to the security of the
data and information (Mukherjee, et al., 2014).
In addition, the company can manage a cybersecurity team to observe various types of issues in
the infrastructure related to IT assets. Moreover, many other things matter a lot for security of the
system, such as knowledge about a data breach, and other things.
The threat is always finding a vulnerability to break the protection of the system or assets of the
organization. In addition, all those vulnerabilities make a way for threats to enter in the whole
system. Therefore, it is necessary to reduce the vulnerabilities of the system (Techdonut, 2018).
No framework:
The company should use the IT governance framework to monitor all the threats and
vulnerabilities of the system to reduce risks from the system. In addition, the IT governance
framework will provide full protection to the systems as well as the client’s data as well. There
are various types of IT governance frameworks are available in the market to secure the whole
system from cyber-attacks, such as COBIT, ISO/IEC 27001, ITIL, and many others (Subashini
& Kavitha, 2011).
Firewall configuration:
The company must configure their firewalls and other IDS and IPS systems to secure the whole
network of the company as well as different sites of the company. It will provide a high level of
network security to the company (Security-trails, 2018). Firewalls can reduce the chances of
cyber-attacks, as it secures all the incoming connection and other outgoing packets as well
(Tanenbaum, 2014).
Selection, justification, and Evaluation
Cybersecurity is a necessary thing for the company because the company has many personal data
of its clients as well as their employees. Therefore, the company is responsible for all data and
information of their clients because they stored all the data in their systems and databases. In
addition, there are many other issues of an organization, which are related to the security of the
data and information (Mukherjee, et al., 2014).
In addition, the company can manage a cybersecurity team to observe various types of issues in
the infrastructure related to IT assets. Moreover, many other things matter a lot for security of the
system, such as knowledge about a data breach, and other things.
Security of Network 11
There are many advantages of a selection of a particular framework of cybersecurity and IT
governance for the company. The company can use a private virtual network for its enhancement
and security. There are many advantages of the virtual private network. VPN can be used for
securing all the personal computers from cyber-attacks and other issues (Rouse, 2015). However,
vulnerabilities are always present in the system but it can be managed with the security policies
and other things.
There are many advantages of a selection of a particular framework of cybersecurity and IT
governance for the company. The company can use a private virtual network for its enhancement
and security. There are many advantages of the virtual private network. VPN can be used for
securing all the personal computers from cyber-attacks and other issues (Rouse, 2015). However,
vulnerabilities are always present in the system but it can be managed with the security policies
and other things.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




