System Administration Assignment: Server Management Tools
VerifiedAdded on 2021/06/17
|13
|1578
|99
Homework Assignment
AI Summary
This assignment solution delves into the core concepts of system administration, emphasizing the importance of Command Line Interface (CLI) proficiency over Graphical User Interfaces (GUI) for server management, particularly for complex processes. It provides detailed explanations and examples of essential CLI tools such as `lsof`, `netstat`, and `mtr` for monitoring and diagnosing system and network activities. The solution further explores the use of Red Hat Enterprise Linux (RHEL) as a robust and secure platform for deploying critical applications, highlighting its features, advantages, and suitability for various server environments. The document covers the history, technical details, and security benefits of RHEL, including its high uptime, built-in security, and support for virtualization, making it a valuable resource for students studying system administration.

Running head: SYSTEM ADMINISTRATION
System Administration
Name of the student
Name of the University
Authors note
System Administration
Name of the student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1SYSTEM ADMINISTRATION
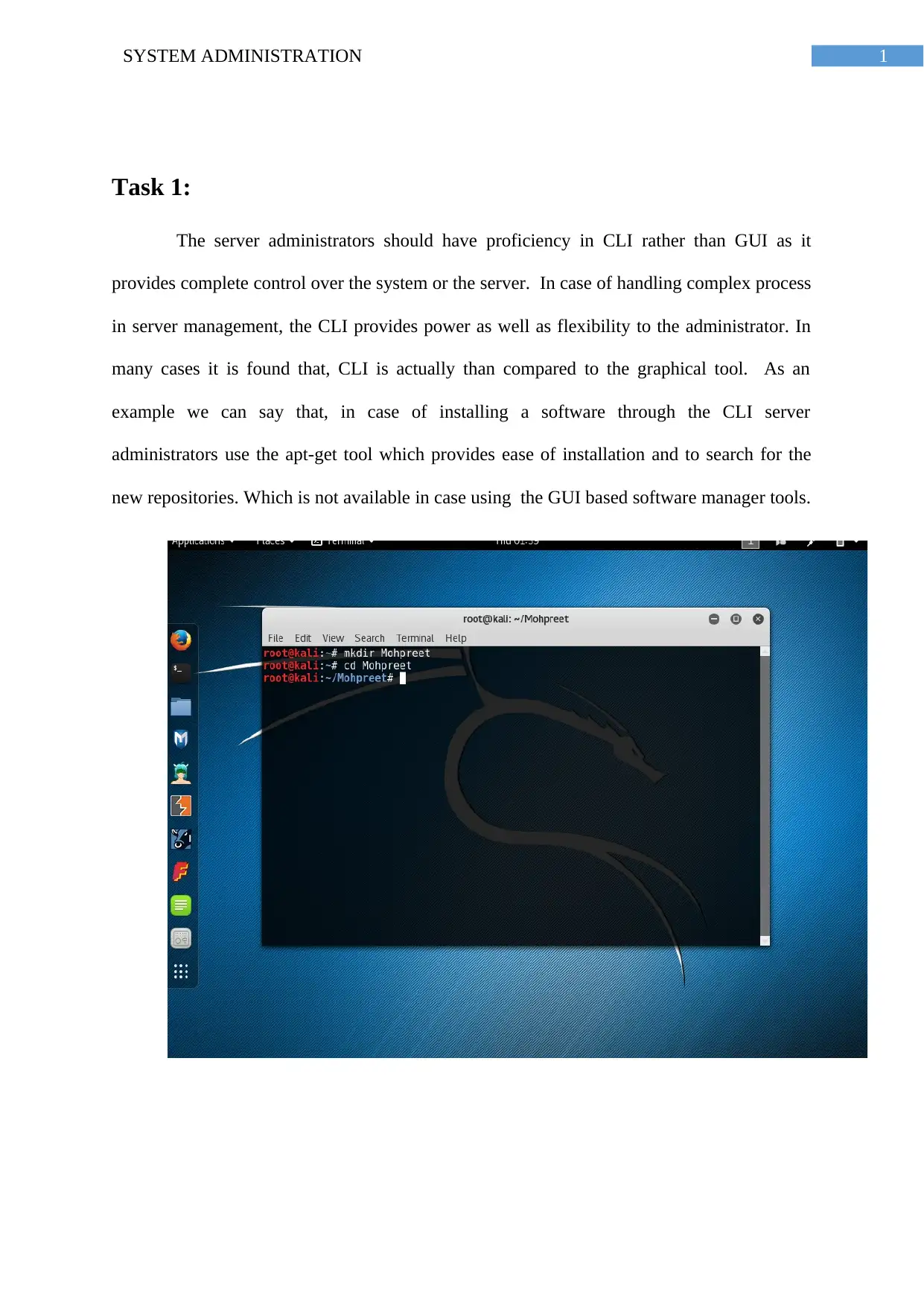
Task 1:
The server administrators should have proficiency in CLI rather than GUI as it
provides complete control over the system or the server. In case of handling complex process
in server management, the CLI provides power as well as flexibility to the administrator. In
many cases it is found that, CLI is actually than compared to the graphical tool. As an
example we can say that, in case of installing a software through the CLI server
administrators use the apt-get tool which provides ease of installation and to search for the
new repositories. Which is not available in case using the GUI based software manager tools.
Task 1:
The server administrators should have proficiency in CLI rather than GUI as it
provides complete control over the system or the server. In case of handling complex process
in server management, the CLI provides power as well as flexibility to the administrator. In
many cases it is found that, CLI is actually than compared to the graphical tool. As an
example we can say that, in case of installing a software through the CLI server
administrators use the apt-get tool which provides ease of installation and to search for the
new repositories. Which is not available in case using the GUI based software manager tools.

2SYSTEM ADMINISTRATION
Task 2:
lsof command:
usage: The lsof command is used to list the opened files used by the different
processes on the system.
syntax of the command: lsof
options that can be used with it,
[ -A A ]
[ -c c ]
[ +c c ]
[ +|-d d ]
[ +|-D D ]
[ +|-e s ]
[ +|-f [cfgGn] ]
[ -F [f] ] [ -g[s] ]
[ -i [i] ]
[ -k k ]
Task 2:
lsof command:
usage: The lsof command is used to list the opened files used by the different
processes on the system.
syntax of the command: lsof
options that can be used with it,
[ -A A ]
[ -c c ]
[ +c c ]
[ +|-d d ]
[ +|-D D ]
[ +|-e s ]
[ +|-f [cfgGn] ]
[ -F [f] ] [ -g[s] ]
[ -i [i] ]
[ -k k ]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SYSTEM ADMINISTRATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SYSTEM ADMINISTRATION
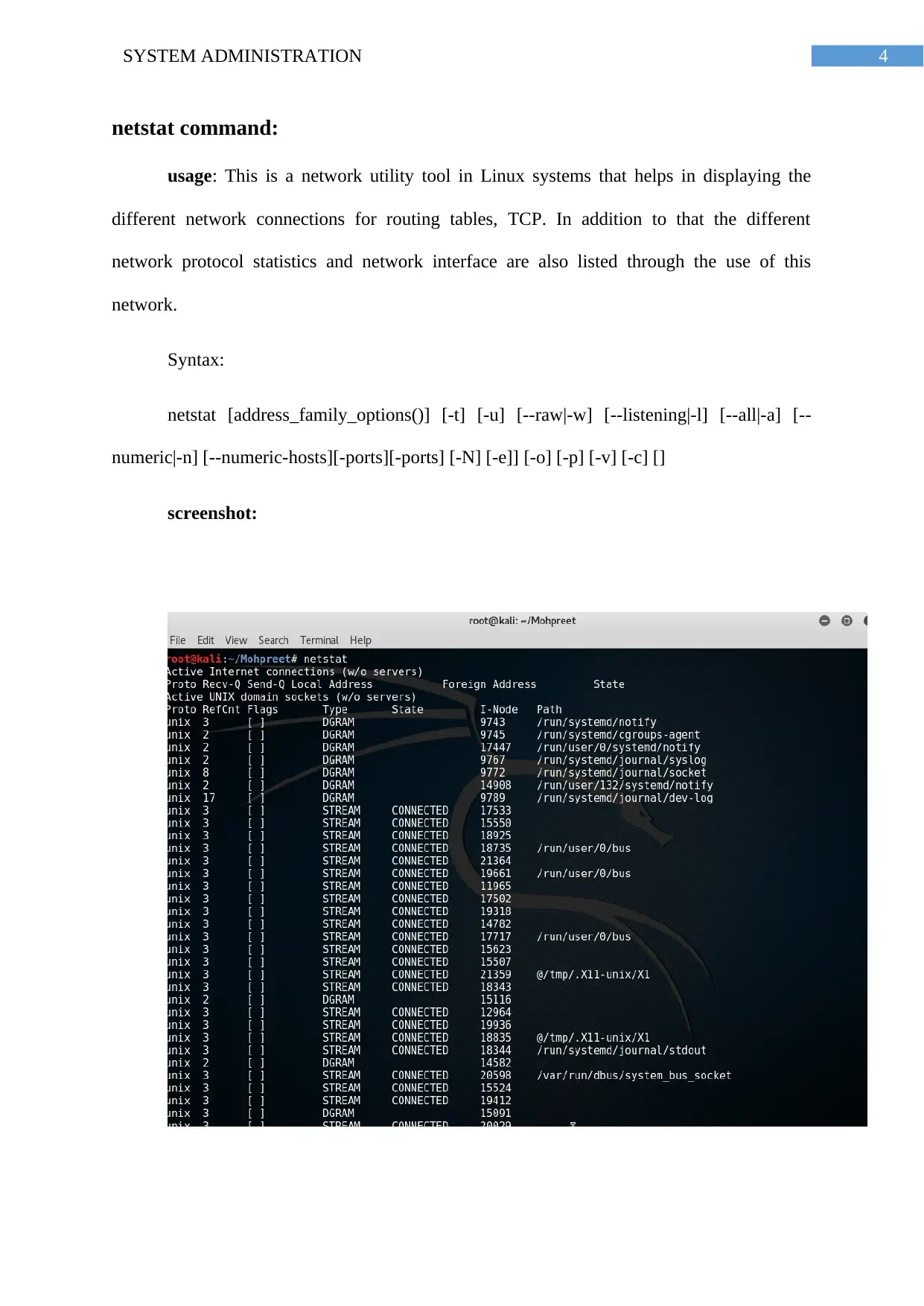
netstat command:
usage: This is a network utility tool in Linux systems that helps in displaying the
different network connections for routing tables, TCP. In addition to that the different
network protocol statistics and network interface are also listed through the use of this
network.
Syntax:
netstat [address_family_options()] [-t] [-u] [--raw|-w] [--listening|-l] [--all|-a] [--
numeric|-n] [--numeric-hosts][-ports][-ports] [-N] [-e]] [-o] [-p] [-v] [-c] []
screenshot:
netstat command:
usage: This is a network utility tool in Linux systems that helps in displaying the
different network connections for routing tables, TCP. In addition to that the different
network protocol statistics and network interface are also listed through the use of this
network.
Syntax:
netstat [address_family_options()] [-t] [-u] [--raw|-w] [--listening|-l] [--all|-a] [--
numeric|-n] [--numeric-hosts][-ports][-ports] [-N] [-e]] [-o] [-p] [-v] [-c] []
screenshot:

5SYSTEM ADMINISTRATION
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SYSTEM ADMINISTRATION
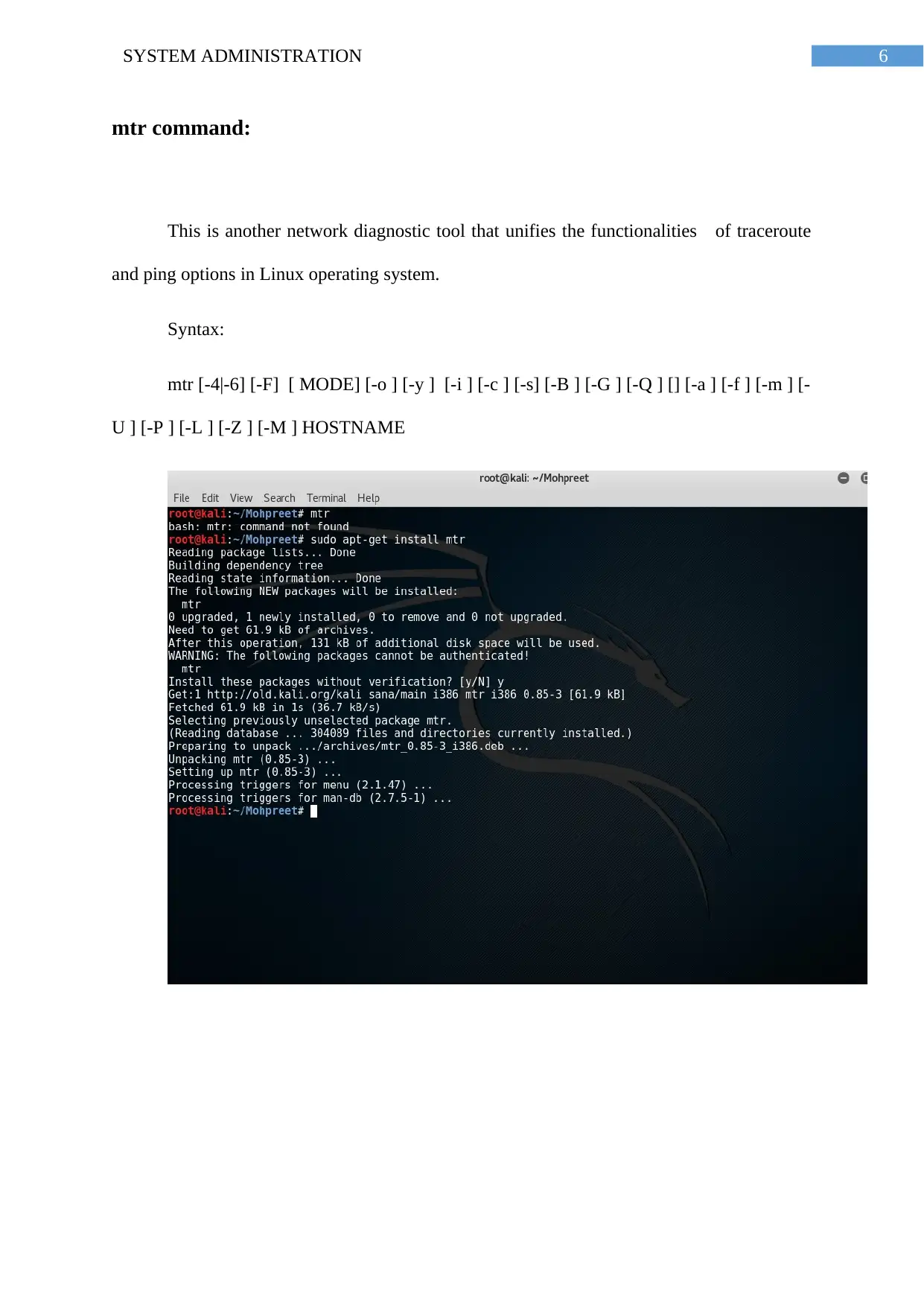
mtr command:
This is another network diagnostic tool that unifies the functionalities of traceroute
and ping options in Linux operating system.
Syntax:
mtr [-4|-6] [-F] [ MODE] [-o ] [-y ] [-i ] [-c ] [-s] [-B ] [-G ] [-Q ] [] [-a ] [-f ] [-m ] [-
U ] [-P ] [-L ] [-Z ] [-M ] HOSTNAME
mtr command:
This is another network diagnostic tool that unifies the functionalities of traceroute
and ping options in Linux operating system.
Syntax:
mtr [-4|-6] [-F] [ MODE] [-o ] [-y ] [-i ] [-c ] [-s] [-B ] [-G ] [-Q ] [] [-a ] [-f ] [-m ] [-
U ] [-P ] [-L ] [-Z ] [-M ] HOSTNAME
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SYSTEM ADMINISTRATION
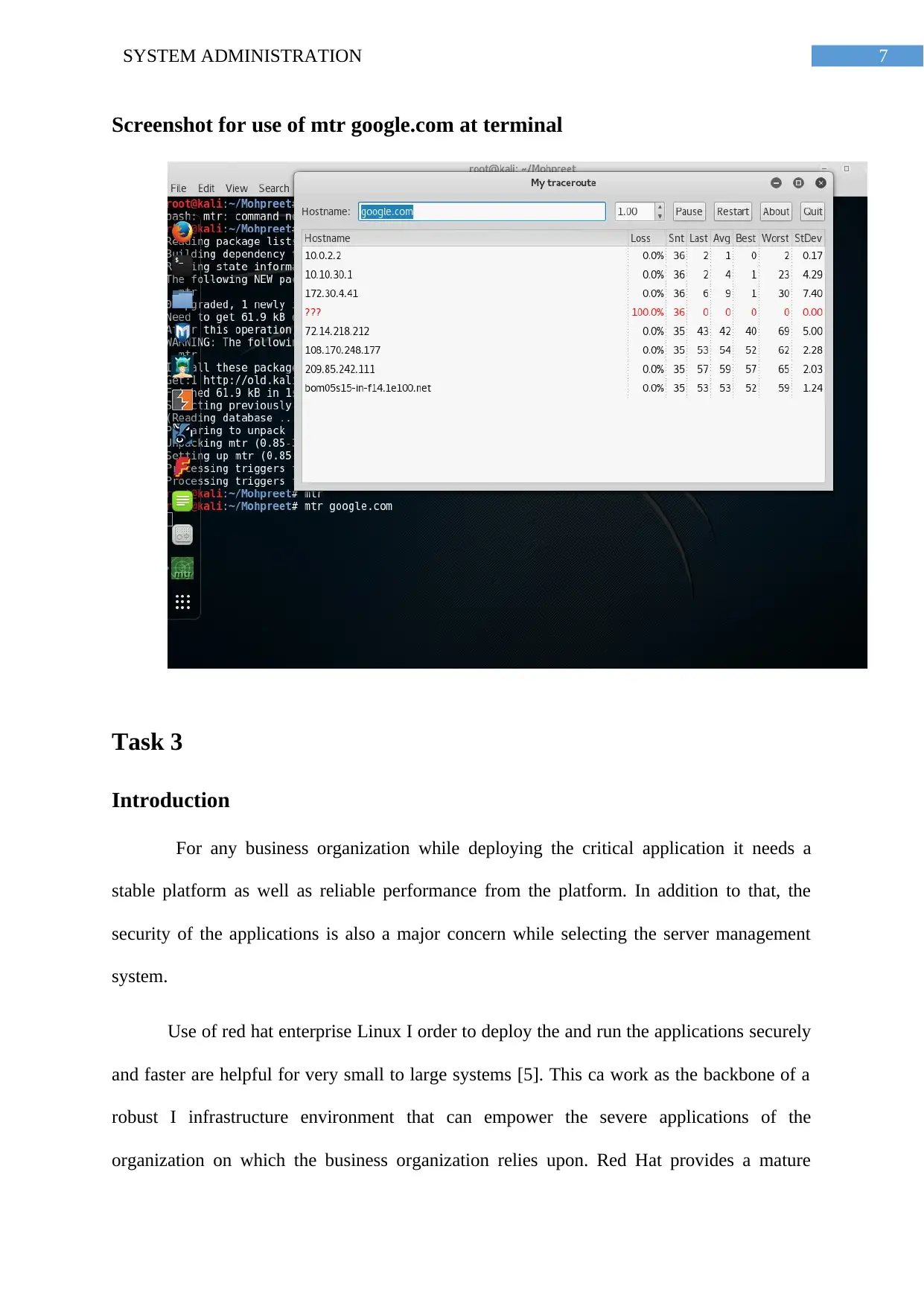
Screenshot for use of mtr google.com at terminal
Task 3
Introduction
For any business organization while deploying the critical application it needs a
stable platform as well as reliable performance from the platform. In addition to that, the
security of the applications is also a major concern while selecting the server management
system.
Use of red hat enterprise Linux I order to deploy the and run the applications securely
and faster are helpful for very small to large systems [5]. This ca work as the backbone of a
robust I infrastructure environment that can empower the severe applications of the
organization on which the business organization relies upon. Red Hat provides a mature
Screenshot for use of mtr google.com at terminal
Task 3
Introduction
For any business organization while deploying the critical application it needs a
stable platform as well as reliable performance from the platform. In addition to that, the
security of the applications is also a major concern while selecting the server management
system.
Use of red hat enterprise Linux I order to deploy the and run the applications securely
and faster are helpful for very small to large systems [5]. This ca work as the backbone of a
robust I infrastructure environment that can empower the severe applications of the
organization on which the business organization relies upon. Red Hat provides a mature

8SYSTEM ADMINISTRATION
software stack based on extensive research on technology in collaboration with numerous
developer which is tested and certified by them.
Background information/history of development
The first commercial version of Red hat Linux was first released in the year 2002
developed by Redhat and mainly targeted to commercial market. Presently, Red Hat
Enterprise Linux provides multiple variants for the users [1]. The available versions are
PowerPC, x86, x86-64, IBM Systems and Itanium. It also includes desktop versions (with
support to x86 and x86-64 architecture)
Technical details and features
The red hat Linux provides almost 99% uptime for the servers it is used for. In
addition to that, it also provides built in security. Other features include the following,
Provides provision for transactional use of a logical volume of the servers and mainly
roll-back of the transactions.
Provides high availability of used LVMs through the synchronization of the metadata
of the stored data.
• improved management of huge memory allocations for the applications while
providing substantial performance improvements for virtualized guest memory.
• improved dynamic control of DM-multipathing [5].
• Red hat Linux also provides support for large SAN-based storage connected with
the server.
software stack based on extensive research on technology in collaboration with numerous
developer which is tested and certified by them.
Background information/history of development
The first commercial version of Red hat Linux was first released in the year 2002
developed by Redhat and mainly targeted to commercial market. Presently, Red Hat
Enterprise Linux provides multiple variants for the users [1]. The available versions are
PowerPC, x86, x86-64, IBM Systems and Itanium. It also includes desktop versions (with
support to x86 and x86-64 architecture)
Technical details and features
The red hat Linux provides almost 99% uptime for the servers it is used for. In
addition to that, it also provides built in security. Other features include the following,
Provides provision for transactional use of a logical volume of the servers and mainly
roll-back of the transactions.
Provides high availability of used LVMs through the synchronization of the metadata
of the stored data.
• improved management of huge memory allocations for the applications while
providing substantial performance improvements for virtualized guest memory.
• improved dynamic control of DM-multipathing [5].
• Red hat Linux also provides support for large SAN-based storage connected with
the server.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SYSTEM ADMINISTRATION
For networks related performance, Red hat Linux provides innovative networking
stack that are helpful in meeting the complex networking requirements of the today’s
enterprises [2]. Features includes leveraging multi-core CPUs, performance improvements,
for efficient send and receive data packets through the outside network.
From the security aspect, File and process permissions can be systematically reduced
by the administrator whenever required in order to reduce the risk of privilege exploitation.
in addition to that newly added utilities in the latest versions provides better control over
process privileges. While using the RHEL in kiosks in banks, and other public domains etc
gain, it makes and implements additional protections in order to ensure secure public use and
prevent the exploits.
Target platform
The red hat Linux s intended for mainly servers but presently it also provides desktop
versions with different hardware compatibility. In addition to that presently the RHEL is also
used in the cloud platforms too in order to make the platforms more robust and secure for the
users.
Advantages and Disadvantages
Better security compared to other OS: Even though the source code of the RHEL
is available or in other words being open source does not make it vulnerable. On the contrary
as too many developers’ consistently evaluate the code of the available code and verifies the
robustness of the system [5]. Due to this constant review of the sources makes it one of the
best dependable and secure OS which makes it almost impossible to exploit the
vulnerabilities.
Stability: In case of Red hat Linux does not require frequent reboots periodically in
order to consistently maintain its performance level [3]. It provides very dependable uptime
For networks related performance, Red hat Linux provides innovative networking
stack that are helpful in meeting the complex networking requirements of the today’s
enterprises [2]. Features includes leveraging multi-core CPUs, performance improvements,
for efficient send and receive data packets through the outside network.
From the security aspect, File and process permissions can be systematically reduced
by the administrator whenever required in order to reduce the risk of privilege exploitation.
in addition to that newly added utilities in the latest versions provides better control over
process privileges. While using the RHEL in kiosks in banks, and other public domains etc
gain, it makes and implements additional protections in order to ensure secure public use and
prevent the exploits.
Target platform
The red hat Linux s intended for mainly servers but presently it also provides desktop
versions with different hardware compatibility. In addition to that presently the RHEL is also
used in the cloud platforms too in order to make the platforms more robust and secure for the
users.
Advantages and Disadvantages
Better security compared to other OS: Even though the source code of the RHEL
is available or in other words being open source does not make it vulnerable. On the contrary
as too many developers’ consistently evaluate the code of the available code and verifies the
robustness of the system [5]. Due to this constant review of the sources makes it one of the
best dependable and secure OS which makes it almost impossible to exploit the
vulnerabilities.
Stability: In case of Red hat Linux does not require frequent reboots periodically in
order to consistently maintain its performance level [3]. It provides very dependable uptime
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SYSTEM ADMINISTRATION
without freezing up or slowing down of the processes due to the reasons like memory leaks
and so on.
Power consumption optimization: In case of server administration the power
consumption by the servers makes it a very costly to maintain the infrastructure. Redhat
enterprise virtualization manager like add on are helpful in optimizing the usage of available
system resources.
Minimal cost: users does not have to spend too much time and economical resources
in order to get licenses as most of the Linux and related software comes with the GNU
licence[1]. Therefore, users can operate on it immediately without worrying about the trail
version of the software.
Virtualization support: Red Hat Linux comes with Smart Virtualization solution.
This is considered as one of the most cost-effective virtualization solutions available in the
market. Using this solution administrator can virtualize Linux workloads [5]. It provides a
virtualization management tools, enterprise-grade hypervisor, and support t different guest
operating system.
Conclusion
With all the above mentioned features one of the most important feature which is
access controls is provided in red hat Linux which makes it much more secure. It includes
Better coverage of the services provided by the by SELinux policies. It makes RHEL secure
compared to the other server management systems and better resistant to hacking exploits. In
this way RHEL protects system stored data. in addition to that SELinux sandboxing feature
also allows the administrators to execute untrusted applications in safe environment and
securely. In addition to that, due to ubiquitous concern about security of the operating
system community based loophole detections the red hat Linux does not require third-party
without freezing up or slowing down of the processes due to the reasons like memory leaks
and so on.
Power consumption optimization: In case of server administration the power
consumption by the servers makes it a very costly to maintain the infrastructure. Redhat
enterprise virtualization manager like add on are helpful in optimizing the usage of available
system resources.
Minimal cost: users does not have to spend too much time and economical resources
in order to get licenses as most of the Linux and related software comes with the GNU
licence[1]. Therefore, users can operate on it immediately without worrying about the trail
version of the software.
Virtualization support: Red Hat Linux comes with Smart Virtualization solution.
This is considered as one of the most cost-effective virtualization solutions available in the
market. Using this solution administrator can virtualize Linux workloads [5]. It provides a
virtualization management tools, enterprise-grade hypervisor, and support t different guest
operating system.
Conclusion
With all the above mentioned features one of the most important feature which is
access controls is provided in red hat Linux which makes it much more secure. It includes
Better coverage of the services provided by the by SELinux policies. It makes RHEL secure
compared to the other server management systems and better resistant to hacking exploits. In
this way RHEL protects system stored data. in addition to that SELinux sandboxing feature
also allows the administrators to execute untrusted applications in safe environment and
securely. In addition to that, due to ubiquitous concern about security of the operating
system community based loophole detections the red hat Linux does not require third-party

11SYSTEM ADMINISTRATION
tools which incurs additional extra costs to patch the security holes in the security of the
system.
tools which incurs additional extra costs to patch the security holes in the security of the
system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





