Server Operating System: Design, Roles, and Functionality Report
VerifiedAdded on 2023/01/11
|14
|3184
|50
Report
AI Summary
This report addresses the server operating system needs of Tetrahedron Theatre in Sheffield, focusing on updating their network infrastructure. It identifies essential server roles, including Active Directory, DHCP, DNS, and Remote Access, and details their functionalities. The report justifies the necessity of each role, explaining how they contribute to user management, centralized control, and network security. It outlines a design for server configuration, emphasizing the importance of Active Directory for authentication and authorization, DHCP for dynamic IP allocation, DNS for domain name resolution, and Remote Access for remote connectivity. The justification for the design choices is provided, highlighting the skills required for critical thinking and problem-solving in implementing these solutions. The report emphasizes the configuration of Active Directory for user and group management, including different group scopes, and the importance of computer account management for auditing and security. Furthermore, it discusses the creation of storage pools and virtual disks for efficient file storage and management, and the need for skills in designing enterprise solutions, supporting storage and file services, and implementing network solutions.

Running head: SERVER OPERATING SYSTEM
Server Operating System
Name of the Student
Name of the University
Author’s Note
Server Operating System
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SERVER OPERATING SYSTEM
Table of Contents
Introduction................................................................................................................................2
Identification of server roles need..............................................................................................2
Identification of functions that the roles provides and justification of requirements................6
Design for server configuration.................................................................................................8
Justification of the decision for the design development...........................................................8
Skills for critical thinking and problem solving.........................................................................9
Conclusion..................................................................................................................................9
References................................................................................................................................11
SERVER OPERATING SYSTEM
Table of Contents
Introduction................................................................................................................................2
Identification of server roles need..............................................................................................2
Identification of functions that the roles provides and justification of requirements................6
Design for server configuration.................................................................................................8
Justification of the decision for the design development...........................................................8
Skills for critical thinking and problem solving.........................................................................9
Conclusion..................................................................................................................................9
References................................................................................................................................11

2
SERVER OPERATING SYSTEM
Introduction
The report is prepared for Tetrahedron Theatre located in Sheffield which have need
to update their current network infrastructure. For the development of the report the network
services are needed to be identified that can be implemented on the Windows Server for the
management of roles and responsibility of the user. The organization have the requirement to
centralize the management and allowing the user to access the network files easily from
remote location. A shared storage space is needed to be configured for each of the department
and the access right is needed to be provided to the members of the department by
configuring group policy. There is a need to configure the group policy and security settings
such that the unauthorised access is prevented and network is secured.
Identification of server roles need
The following four roles are needed to be deployed in the two servers available with
Tetrahedron theatre such as:
A. Active Directory –
Functionality
The main functionality of the active directory is to configure the server as a
domain controller and authenticate, authorize and manage the user groups centrally. It
acts as a distributed directory and user for controlling the domain (Sundar and Kumar
2016). The users are authorized and authenticated and security policies are enforced
for the management of authorization and authentication.
Roles
The active directory is used for checking the password for the determination of
the user if he is a normal user or have the administrative privilege. It is used for
managing and storing information for the establishment of framework and deploying
SERVER OPERATING SYSTEM
Introduction
The report is prepared for Tetrahedron Theatre located in Sheffield which have need
to update their current network infrastructure. For the development of the report the network
services are needed to be identified that can be implemented on the Windows Server for the
management of roles and responsibility of the user. The organization have the requirement to
centralize the management and allowing the user to access the network files easily from
remote location. A shared storage space is needed to be configured for each of the department
and the access right is needed to be provided to the members of the department by
configuring group policy. There is a need to configure the group policy and security settings
such that the unauthorised access is prevented and network is secured.
Identification of server roles need
The following four roles are needed to be deployed in the two servers available with
Tetrahedron theatre such as:
A. Active Directory –
Functionality
The main functionality of the active directory is to configure the server as a
domain controller and authenticate, authorize and manage the user groups centrally. It
acts as a distributed directory and user for controlling the domain (Sundar and Kumar
2016). The users are authorized and authenticated and security policies are enforced
for the management of authorization and authentication.
Roles
The active directory is used for checking the password for the determination of
the user if he is a normal user or have the administrative privilege. It is used for
managing and storing information for the establishment of framework and deploying
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SERVER OPERATING SYSTEM
related service. The information about each of the user are stored and the serving
running the service is also known as domain controller.
Justification
The active directory is configured such that authentication and authorization is
maintained for all the users who uses the computers. It also helps in enforcement of
security policy for the computers connected in the network and installation and
updating the software. The storage and management of information is important and it
also provide authorization and authentication mechanism for establishing a
framework and deployment of the related services such as Rights management,
lightweight directory, Domain services, etc.
B. DHCP –
Functionality
It is used for the simplification of administrative tasks with the assigning of IP
address, Subnet mask, default gateway to the hosts connected in the network. It is a
network management protocol used for the needs of network administration and
elimination of the needs of manually assigning IP address in the network (Alvarez et
al. 2017).
Roles
The DHCP service is enabled in the server for enabling dynamic allocation of
the IP address and having a centralized management on the network. A pool of Ip
address is maintained by the server with the client information and parameters used
for configuration (Xu et al. 2015). If there is a change in the network address it can be
managed centrally by changing the pools and automatically updating the IP address
for the client connected in the server.
Justification
SERVER OPERATING SYSTEM
related service. The information about each of the user are stored and the serving
running the service is also known as domain controller.
Justification
The active directory is configured such that authentication and authorization is
maintained for all the users who uses the computers. It also helps in enforcement of
security policy for the computers connected in the network and installation and
updating the software. The storage and management of information is important and it
also provide authorization and authentication mechanism for establishing a
framework and deployment of the related services such as Rights management,
lightweight directory, Domain services, etc.
B. DHCP –
Functionality
It is used for the simplification of administrative tasks with the assigning of IP
address, Subnet mask, default gateway to the hosts connected in the network. It is a
network management protocol used for the needs of network administration and
elimination of the needs of manually assigning IP address in the network (Alvarez et
al. 2017).
Roles
The DHCP service is enabled in the server for enabling dynamic allocation of
the IP address and having a centralized management on the network. A pool of Ip
address is maintained by the server with the client information and parameters used
for configuration (Xu et al. 2015). If there is a change in the network address it can be
managed centrally by changing the pools and automatically updating the IP address
for the client connected in the server.
Justification
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SERVER OPERATING SYSTEM
It is needed to be configured such that each of the branches of the organization
gets the subnetted address automatically from the DHCP pool configured in the
server. The DHCP service is needed to be installed and the pools for the different
subnet is needed to be configured such that the client connected in the network gets
the network parameters needed for proper communication with the other clients
automatically (Ram et al. 2016). It eliminates the needs of manually configuring the
IP address of each of the network device.
C. DNS –
Functionality
The functionality of the DNS is translating the domain names into the
corresponding IP address that is understandable by the computer (Rego et al. 2017). A
list of mail server is also provided for accepting emails for each of the domain and a
set of name servers is needed to be authoritative for the DNS.
Roles
The role of the DNS server is to store the small set of instruction which points
IP address to the domain name also named as zone file. A set of records are used for
the creation of the zone file and if the user needs CNAME record the URL is provided
to the user and thus it can be specified which email servers are responsible for the
domain name (Yamato 2017). There are other types of record such as MX record that
is used for setting the priority number and retiring information to the mail server
querrying and that is needed to be used first. When the highest priority is not available
the next entry is tried.
Justification
Configuring the server with DNS includes translating the domain name with
the respective Ip address when a request is generated by the client. A database is used
SERVER OPERATING SYSTEM
It is needed to be configured such that each of the branches of the organization
gets the subnetted address automatically from the DHCP pool configured in the
server. The DHCP service is needed to be installed and the pools for the different
subnet is needed to be configured such that the client connected in the network gets
the network parameters needed for proper communication with the other clients
automatically (Ram et al. 2016). It eliminates the needs of manually configuring the
IP address of each of the network device.
C. DNS –
Functionality
The functionality of the DNS is translating the domain names into the
corresponding IP address that is understandable by the computer (Rego et al. 2017). A
list of mail server is also provided for accepting emails for each of the domain and a
set of name servers is needed to be authoritative for the DNS.
Roles
The role of the DNS server is to store the small set of instruction which points
IP address to the domain name also named as zone file. A set of records are used for
the creation of the zone file and if the user needs CNAME record the URL is provided
to the user and thus it can be specified which email servers are responsible for the
domain name (Yamato 2017). There are other types of record such as MX record that
is used for setting the priority number and retiring information to the mail server
querrying and that is needed to be used first. When the highest priority is not available
the next entry is tried.
Justification
Configuring the server with DNS includes translating the domain name with
the respective Ip address when a request is generated by the client. A database is used

5
SERVER OPERATING SYSTEM
by the DNS for storing the domain name and the corresponding registered IP
addresses (Khodadadi, Calheiros and Buyya 2015). It works as an attendance register
that are available in the internet and that operates worldwide.
D. Remote Access –
Functionality
The remote access configuration is needed to be enabled from the server
manager and users are needed to be defined for providing permission to connect using
the remote desktop (Polenov et al. 2016). The configuration of the server with remote
access enables the users accessing the system that are required.
Roles
It is used for adding flexibility in the organization for promoting collaboration
between the location, offices and teams. It can be achieved with the application of
remote access VPN for the creation of encryption and safe connection using the less
secured network. The remote desktop application can also be used for connecting with
network and applications remotely (Carutasu et al. 2016). Application software are
used for enabling the application run remotely on the server and display in the local
computer parallelly. The people ate the branch office can access the shared files and
work on the project combinedly for improving the productivity.
Justification
The remote access is necessary for allowing the users to connect with the local
server from remote location and improve the performance. Remote desktops are used
by the organization for enabling the users to connect their application and network
from remote location.
SERVER OPERATING SYSTEM
by the DNS for storing the domain name and the corresponding registered IP
addresses (Khodadadi, Calheiros and Buyya 2015). It works as an attendance register
that are available in the internet and that operates worldwide.
D. Remote Access –
Functionality
The remote access configuration is needed to be enabled from the server
manager and users are needed to be defined for providing permission to connect using
the remote desktop (Polenov et al. 2016). The configuration of the server with remote
access enables the users accessing the system that are required.
Roles
It is used for adding flexibility in the organization for promoting collaboration
between the location, offices and teams. It can be achieved with the application of
remote access VPN for the creation of encryption and safe connection using the less
secured network. The remote desktop application can also be used for connecting with
network and applications remotely (Carutasu et al. 2016). Application software are
used for enabling the application run remotely on the server and display in the local
computer parallelly. The people ate the branch office can access the shared files and
work on the project combinedly for improving the productivity.
Justification
The remote access is necessary for allowing the users to connect with the local
server from remote location and improve the performance. Remote desktops are used
by the organization for enabling the users to connect their application and network
from remote location.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
SERVER OPERATING SYSTEM
Identification of functions that the roles provides and justification of
requirements
For the identification of the functionality the roles and service that is essential is
needed to be identified for the management of user accounts, groups, computer accounts,
configuration of storage and details and configuring the group policy. Gateway access role
definition is needed to be used for the management of gateway service and provide access
permission to the users for authenticating the gateway service (MVP et al. 2015). The active
directory is configured for controlling the access of the gateway and this is done by adding
security groups to the list of users and restrict the members to access those groups. New users
accounts can be added or deleted by using the windows server for the management of the
user. It can be done from the dashboard with the prompts for adding or deleting the user
account.
For the management of the groups the users are needed to be categorized according to
their needs and resources essential for the management of the task. There are different scopes
for the groups such as local, domain local, universal and global. The local groups are created
and defined for the specific computers and they may be users or administrators. The domain
local groups are created for the management of permission to the resources as the groups are
applied in the domain (Bensley et al. 2017). It consists of any types of members from the
trusted domain for example if there is a need of access management for multiple folders for
the single or the two servers containing different information, the group created should be of
domain local. There are universal groups created in the active directory that are used for
multi domain forest. It is used for defining roles and management of resources for multiple
domain. Foreach of the domain a universal group is created and the group membership is
stored as a global catalogue and replicated forest wide. There is no need of universal groups
since the organization would have a single domain (Moore 2016). The global groups are
SERVER OPERATING SYSTEM
Identification of functions that the roles provides and justification of
requirements
For the identification of the functionality the roles and service that is essential is
needed to be identified for the management of user accounts, groups, computer accounts,
configuration of storage and details and configuring the group policy. Gateway access role
definition is needed to be used for the management of gateway service and provide access
permission to the users for authenticating the gateway service (MVP et al. 2015). The active
directory is configured for controlling the access of the gateway and this is done by adding
security groups to the list of users and restrict the members to access those groups. New users
accounts can be added or deleted by using the windows server for the management of the
user. It can be done from the dashboard with the prompts for adding or deleting the user
account.
For the management of the groups the users are needed to be categorized according to
their needs and resources essential for the management of the task. There are different scopes
for the groups such as local, domain local, universal and global. The local groups are created
and defined for the specific computers and they may be users or administrators. The domain
local groups are created for the management of permission to the resources as the groups are
applied in the domain (Bensley et al. 2017). It consists of any types of members from the
trusted domain for example if there is a need of access management for multiple folders for
the single or the two servers containing different information, the group created should be of
domain local. There are universal groups created in the active directory that are used for
multi domain forest. It is used for defining roles and management of resources for multiple
domain. Foreach of the domain a universal group is created and the group membership is
stored as a global catalogue and replicated forest wide. There is no need of universal groups
since the organization would have a single domain (Moore 2016). The global groups are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SERVER OPERATING SYSTEM
created for defining the collection of domain objects such as users, computers and other
global groups. As an example of global group the groups that have role based groups of users
are defined. Marketing group or HR group is an example of global groups and the Marketing
Workstations is an example of role based group for computers.
The management of computer account is essential for auditing and maintaining the
system activity logs and identifying the errors in configuration and troubleshooting the
disruption in service for analysing the compromises that occurred and detecting the attacks.
The collection of the data helps in improvising the security of information assets and
detection of unexpected and suspicious behaviour (Karim et al. 2017). The events such as
renaming, deleting, changing, creating, enabling or disabling or computer accounts are
recorded under the computer account management.
More than one virtual disk can be created from a storage pool and this are also
referred as storage specs. For the creation of storage specs a storage pool is needed to be
created and it offers aggregation of storage, delegated administration and elastic capacity
expansion. There are some prerequisites that are needed for using storage spaces in the stand
alone Windows server 2012. For planning the needs of number of physical disks and
resiliency at least one physical disk is necessary and it should not be used for hosting
irreplaceable data and the simple spaces cannot be used for protecting the disk failures (Lynn
et al. 2017). It can also be used for hosting temporary or easily recreated data and is best
suited for high performance workloads.
SERVER OPERATING SYSTEM
created for defining the collection of domain objects such as users, computers and other
global groups. As an example of global group the groups that have role based groups of users
are defined. Marketing group or HR group is an example of global groups and the Marketing
Workstations is an example of role based group for computers.
The management of computer account is essential for auditing and maintaining the
system activity logs and identifying the errors in configuration and troubleshooting the
disruption in service for analysing the compromises that occurred and detecting the attacks.
The collection of the data helps in improvising the security of information assets and
detection of unexpected and suspicious behaviour (Karim et al. 2017). The events such as
renaming, deleting, changing, creating, enabling or disabling or computer accounts are
recorded under the computer account management.
More than one virtual disk can be created from a storage pool and this are also
referred as storage specs. For the creation of storage specs a storage pool is needed to be
created and it offers aggregation of storage, delegated administration and elastic capacity
expansion. There are some prerequisites that are needed for using storage spaces in the stand
alone Windows server 2012. For planning the needs of number of physical disks and
resiliency at least one physical disk is necessary and it should not be used for hosting
irreplaceable data and the simple spaces cannot be used for protecting the disk failures (Lynn
et al. 2017). It can also be used for hosting temporary or easily recreated data and is best
suited for high performance workloads.
8
SERVER OPERATING SYSTEM
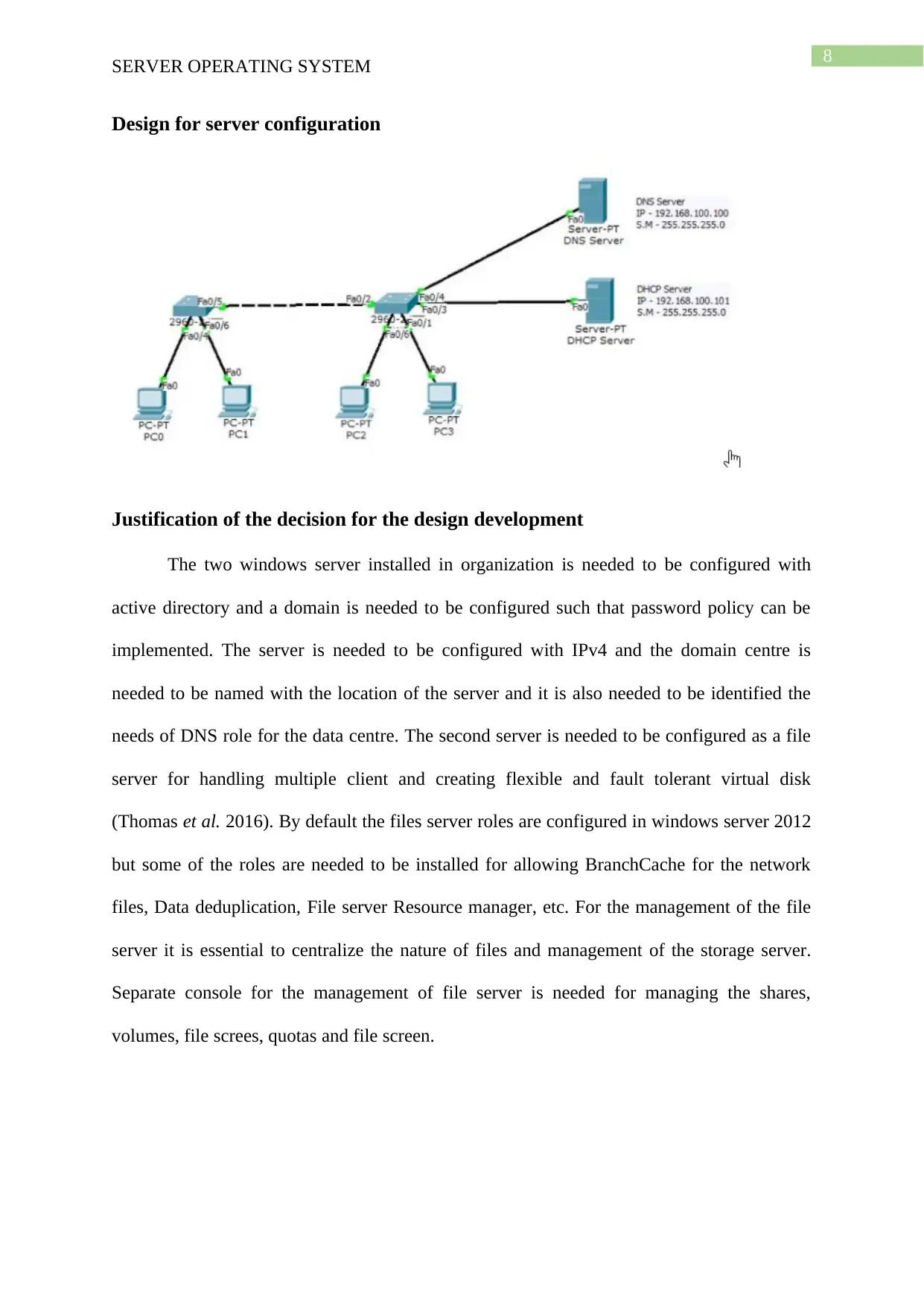
Design for server configuration
Justification of the decision for the design development
The two windows server installed in organization is needed to be configured with
active directory and a domain is needed to be configured such that password policy can be
implemented. The server is needed to be configured with IPv4 and the domain centre is
needed to be named with the location of the server and it is also needed to be identified the
needs of DNS role for the data centre. The second server is needed to be configured as a file
server for handling multiple client and creating flexible and fault tolerant virtual disk
(Thomas et al. 2016). By default the files server roles are configured in windows server 2012
but some of the roles are needed to be installed for allowing BranchCache for the network
files, Data deduplication, File server Resource manager, etc. For the management of the file
server it is essential to centralize the nature of files and management of the storage server.
Separate console for the management of file server is needed for managing the shares,
volumes, file screes, quotas and file screen.
SERVER OPERATING SYSTEM
Design for server configuration
Justification of the decision for the design development
The two windows server installed in organization is needed to be configured with
active directory and a domain is needed to be configured such that password policy can be
implemented. The server is needed to be configured with IPv4 and the domain centre is
needed to be named with the location of the server and it is also needed to be identified the
needs of DNS role for the data centre. The second server is needed to be configured as a file
server for handling multiple client and creating flexible and fault tolerant virtual disk
(Thomas et al. 2016). By default the files server roles are configured in windows server 2012
but some of the roles are needed to be installed for allowing BranchCache for the network
files, Data deduplication, File server Resource manager, etc. For the management of the file
server it is essential to centralize the nature of files and management of the storage server.
Separate console for the management of file server is needed for managing the shares,
volumes, file screes, quotas and file screen.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
SERVER OPERATING SYSTEM
Skills for critical thinking and problem solving
For designing and implementation of the active directory and server roles and service
it is essential to gain knowledge and skills for designing enterprise solution for supporting the
automated and manual server installation in virtual and physical environment. The knowledge
regarding support of storage and file services is needed to be gained and the skills that are
necessary for providing enterprise network solution such as DHCP, Remote Access is needed
to be gained and the server administrator should also be able to design and implement forest
and domain infrastructure containing multi domain for the scenario with an enterprise with
multiple branch (Tso, Jouet and Pezaros 2016). A certification is necessary such as Windows
2012 R2 MCSA for experiencing a good technical knowledge on both Windows Server 2012
R2, Active Directory and Domain Services.
Conclusion
From the above report it can be concluded that before the deployment of the Windows
server for updating the existing infrastructure it is important to identify the current problems
faced by Tetrahedon Theatre. The service that are needed to be implemented for mitigation of
the problem is needed to be identified for the configuration of server roles and responsibility.
A central management of the users accounts and configuration is needed to be maintained and
remote access is needed to be enabled such that files residing in the server can be access by
the authorised users. A file management server is needed to be deployed in the network and it
is needed to be configured with group policy and security settings such that the unauthorised
access is restricted and the network security is improved. A list of the user and their needs are
analysed for the configuration of the server with group policy and configuring roles and
service for management of the users. The requirement of the four server roles are explained in
the document along with their functionality. An analysis is made on the current system needs
for the management of user accounts, management of groups, computer accounts, storage
SERVER OPERATING SYSTEM
Skills for critical thinking and problem solving
For designing and implementation of the active directory and server roles and service
it is essential to gain knowledge and skills for designing enterprise solution for supporting the
automated and manual server installation in virtual and physical environment. The knowledge
regarding support of storage and file services is needed to be gained and the skills that are
necessary for providing enterprise network solution such as DHCP, Remote Access is needed
to be gained and the server administrator should also be able to design and implement forest
and domain infrastructure containing multi domain for the scenario with an enterprise with
multiple branch (Tso, Jouet and Pezaros 2016). A certification is necessary such as Windows
2012 R2 MCSA for experiencing a good technical knowledge on both Windows Server 2012
R2, Active Directory and Domain Services.
Conclusion
From the above report it can be concluded that before the deployment of the Windows
server for updating the existing infrastructure it is important to identify the current problems
faced by Tetrahedon Theatre. The service that are needed to be implemented for mitigation of
the problem is needed to be identified for the configuration of server roles and responsibility.
A central management of the users accounts and configuration is needed to be maintained and
remote access is needed to be enabled such that files residing in the server can be access by
the authorised users. A file management server is needed to be deployed in the network and it
is needed to be configured with group policy and security settings such that the unauthorised
access is restricted and the network security is improved. A list of the user and their needs are
analysed for the configuration of the server with group policy and configuring roles and
service for management of the users. The requirement of the four server roles are explained in
the document along with their functionality. An analysis is made on the current system needs
for the management of user accounts, management of groups, computer accounts, storage
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
SERVER OPERATING SYSTEM
details/ configuration and group policy settings. A justification is given for the decision taken
for selecting the roles and service for the development of the solution and identifying the
skills needed for development of the problem solution.
SERVER OPERATING SYSTEM
details/ configuration and group policy settings. A justification is given for the decision taken
for selecting the roles and service for the development of the solution and identifying the
skills needed for development of the problem solution.

11
SERVER OPERATING SYSTEM
References
Alvarez, R., Mirzoev, T., Gowan, A., Henderson, B. and Kruck, S.E., 2017. Learning
Laboratories as Services in Private Cloud Deployment. Journal of Computer Information
Systems, pp.1-9.
Bensley, S., Thaler, D., Balasubramanian, P., Eggert, L. and Judd, G., 2017. Data center
TCP (DCTCP): TCP congestion control for data centers (No. RFC 8257).
Carutasu, G., Botezatu, M.A., Botezatu, C. and Pirnau, M., 2016, June. Cloud computing and
windows azure. In 2016 8th International Conference on Electronics, Computers and
Artificial Intelligence (ECAI) (pp. 1-6). IEEE.
Karim, I., Vien, Q.T., Le, T. and Mapp, G., 2017. A comparative experimental design and
performance analysis of Snort-based Intrusion Detection System in practical computer
networks. Computers, 6(1), p.6.
Khodadadi, F., Calheiros, R.N. and Buyya, R., 2015, April. A data-centric framework for
development and deployment of internet of things applications in clouds. In 2015 IEEE Tenth
International Conference on Intelligent Sensors, Sensor Networks and Information
Processing (ISSNIP) (pp. 1-6). IEEE.
Lynn, R., Contis, D., Hossain, M., Huang, N., Tucker, T. and Kurfess, T., 2017. Voxel model
surface offsetting for computer-aided manufacturing using virtualized high-performance
computing. Journal of Manufacturing Systems, 43, pp.296-304.
Moore, C., 2016, August. Detecting ransomware with honeypot techniques. In 2016
Cybersecurity and Cyberforensics Conference (CCC) (pp. 77-81). IEEE.
MVP, S.B., Horner, J., Odika, C. and Ryan, R., 2015. Microsoft System Center 2012 R2
Operations Manager cookbook. Packt Publishing Ltd.
SERVER OPERATING SYSTEM
References
Alvarez, R., Mirzoev, T., Gowan, A., Henderson, B. and Kruck, S.E., 2017. Learning
Laboratories as Services in Private Cloud Deployment. Journal of Computer Information
Systems, pp.1-9.
Bensley, S., Thaler, D., Balasubramanian, P., Eggert, L. and Judd, G., 2017. Data center
TCP (DCTCP): TCP congestion control for data centers (No. RFC 8257).
Carutasu, G., Botezatu, M.A., Botezatu, C. and Pirnau, M., 2016, June. Cloud computing and
windows azure. In 2016 8th International Conference on Electronics, Computers and
Artificial Intelligence (ECAI) (pp. 1-6). IEEE.
Karim, I., Vien, Q.T., Le, T. and Mapp, G., 2017. A comparative experimental design and
performance analysis of Snort-based Intrusion Detection System in practical computer
networks. Computers, 6(1), p.6.
Khodadadi, F., Calheiros, R.N. and Buyya, R., 2015, April. A data-centric framework for
development and deployment of internet of things applications in clouds. In 2015 IEEE Tenth
International Conference on Intelligent Sensors, Sensor Networks and Information
Processing (ISSNIP) (pp. 1-6). IEEE.
Lynn, R., Contis, D., Hossain, M., Huang, N., Tucker, T. and Kurfess, T., 2017. Voxel model
surface offsetting for computer-aided manufacturing using virtualized high-performance
computing. Journal of Manufacturing Systems, 43, pp.296-304.
Moore, C., 2016, August. Detecting ransomware with honeypot techniques. In 2016
Cybersecurity and Cyberforensics Conference (CCC) (pp. 77-81). IEEE.
MVP, S.B., Horner, J., Odika, C. and Ryan, R., 2015. Microsoft System Center 2012 R2
Operations Manager cookbook. Packt Publishing Ltd.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





