ITSA2005: Server Planning and Implementation Project Report
VerifiedAdded on 2023/01/11
|25
|2252
|23
Report
AI Summary
This report presents a comprehensive proposal for server planning and implementation, focusing on Contoso Corporation's expansion and acquisition of Adatum Corporation. The report outlines the requirements, including the need for domain controllers, automated installation strategies using Windows Deployment Services (WDS), and redesigning Adatum's network infrastructure. It details the proposed solution, which includes utilizing Windows Internal Database (WID) for data storage, implementing Active Directory for user management, and leveraging WDS for remote deployment and management of servers. The report addresses the integration of Adatum's existing systems and the rollout of new products, emphasizing the importance of a well-managed IT infrastructure. The executive summary provides an overview of the challenges and solutions, while the body of the report delves into specific technologies and strategies, supported by figures and appendices illustrating key processes like server and Active Directory installation. The report underscores the importance of planning, effective implementation, and stakeholder involvement to ensure a successful integration and deployment of the new systems.

Server 1
Planning and Implementing Server
Name
Course
Institution
Date
Planning and Implementing Server
Name
Course
Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Server 2
Executive summary
Contoso Corporation is a company offering smart devices to their customers. The company
provides home security monitoring and medical monitoring solutions. The company has also
acquired another company, Adatum Corporation. The paper written is a proposal to persuade the
management about the new products (product for home security monitoring and medical
monitoring) that are to be rolled out. The report also tries to address the issue of Adatum
Corporation (acquired by Contoso Corporation), how to improve their network system and make
it as simple as possible. This piece of paper is a proposal to advice on how ways to improve the
systems of both companies and also find ways to implement and integrate the existing systems.
The paper is a collaboration of various people from the information technology design team, to
the system developers and the information system administrator.
Executive summary
Contoso Corporation is a company offering smart devices to their customers. The company
provides home security monitoring and medical monitoring solutions. The company has also
acquired another company, Adatum Corporation. The paper written is a proposal to persuade the
management about the new products (product for home security monitoring and medical
monitoring) that are to be rolled out. The report also tries to address the issue of Adatum
Corporation (acquired by Contoso Corporation), how to improve their network system and make
it as simple as possible. This piece of paper is a proposal to advice on how ways to improve the
systems of both companies and also find ways to implement and integrate the existing systems.
The paper is a collaboration of various people from the information technology design team, to
the system developers and the information system administrator.

Server 3
Table of Contents
Executive summary.....................................................................................................................................2
Introduction.................................................................................................................................................5
Purpose of the project.................................................................................................................................5
Contoso Corporation...............................................................................................................................5
Adatum Corporation................................................................................................................................5
Requirements of the project.......................................................................................................................6
Servers.....................................................................................................................................................6
Domain controllers..............................................................................................................................6
Mail servers.........................................................................................................................................7
SQL server............................................................................................................................................7
Automated installation strategy..............................................................................................................7
Redesign the network infrastructure of Adatum Corporation.................................................................7
Proposed solution........................................................................................................................................8
Windows Internal Database....................................................................................................................8
Active Directory.....................................................................................................................................10
Windows Deployment Services (WDS)..................................................................................................10
Conclusion.................................................................................................................................................11
Works cited...............................................................................................................................................12
Appendixes................................................................................................................................................13
Appendix One: Installation of a Windows Server..................................................................................13
Appendix Two: Installing Active Directory.............................................................................................15
Appendix Three: Windows Deployment Service....................................................................................20
Table of Contents
Executive summary.....................................................................................................................................2
Introduction.................................................................................................................................................5
Purpose of the project.................................................................................................................................5
Contoso Corporation...............................................................................................................................5
Adatum Corporation................................................................................................................................5
Requirements of the project.......................................................................................................................6
Servers.....................................................................................................................................................6
Domain controllers..............................................................................................................................6
Mail servers.........................................................................................................................................7
SQL server............................................................................................................................................7
Automated installation strategy..............................................................................................................7
Redesign the network infrastructure of Adatum Corporation.................................................................7
Proposed solution........................................................................................................................................8
Windows Internal Database....................................................................................................................8
Active Directory.....................................................................................................................................10
Windows Deployment Services (WDS)..................................................................................................10
Conclusion.................................................................................................................................................11
Works cited...............................................................................................................................................12
Appendixes................................................................................................................................................13
Appendix One: Installation of a Windows Server..................................................................................13
Appendix Two: Installing Active Directory.............................................................................................15
Appendix Three: Windows Deployment Service....................................................................................20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Server 4
List of figures
Figure 1.1
Figure 2.1
Figure 3.1
Figure 4.1
List of figures
Figure 1.1
Figure 2.1
Figure 3.1
Figure 4.1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Server 5
Introduction
Contoso Corporation is a leading producer of smart devices for homes. Contoso
Corporation also designs medical monitoring equipment. Contoso Corporation has a design team
which has come up with a new product for home security monitoring and medical monitoring
equipment. These new products need to be rolled out. Therefore, necessary preparations (create
the necessary structures) are to be done for the new system to work as expected. In addition to
the new product, Contoso Corporation has also acquired a new company- Adutum Corporation.
The company acquired also have their infrastructure and systems in place. As the administrator,
it is my job to see that the new product is rolled out and the ground is set running.
Purpose of the project
The purpose of this proposal is to come up with the best practices for the products of
Contoso Corporation. Contoso, dealing with home monitoring security and medical monitoring
security systems, need a system to manage usage and to manage their infrastructure. The
products offered should be well “thought out” to see to it that the products developed by the
design team meet international standards. In addition to Contoso’s products, we are also going to
find a way to integrate Adatum’s systems into Contoso’s systems. Contoso will have to find a
way to control the resources of Adatum for easier management.
Contoso also has its systems that they run. These systems also need proper management
to see that they work perfectly so that the customers are served as required.As the administrator,
working with other team players, we need to come up with a solution for Contoso’s products and
an answer for Adatum Corporation’s systems. The solution provided also needs to address an
automatic installation strategy to support the installation of several new servers each month. The
proposal also has to address the issue of Windows Installation Database (WID) that will be used
to manage the home security and medical monitoring systems. Moving forward, we have
discussed briefly Contoso Corporation and Adatum Corporation in the next two paragraphs.
Contoso Corporation
Contoso Corporation is a leading producer of smart devices. They produce home
monitoring devices and medical monitoring devices They also provide installation services for
people. Contoso Corporation also acquired Adatum Corporation. The technology team will need
to come up with a strategy to control the systems available and incorporate the acquired
company so that they complement each other.
Adatum Corporation
Adatum Corporation has a Microsoft Exchange server to manage the emails of their staff.
They also have an SQL server that serves as their database. In addition, Adatum Corporation also
has twenty smaller sites with each consisting of between twenty and fifty employees. The
corporation has an internal network to manage their employees and a mail server to enable their
communications. They also have a database to help them manage their information. The
Introduction
Contoso Corporation is a leading producer of smart devices for homes. Contoso
Corporation also designs medical monitoring equipment. Contoso Corporation has a design team
which has come up with a new product for home security monitoring and medical monitoring
equipment. These new products need to be rolled out. Therefore, necessary preparations (create
the necessary structures) are to be done for the new system to work as expected. In addition to
the new product, Contoso Corporation has also acquired a new company- Adutum Corporation.
The company acquired also have their infrastructure and systems in place. As the administrator,
it is my job to see that the new product is rolled out and the ground is set running.
Purpose of the project
The purpose of this proposal is to come up with the best practices for the products of
Contoso Corporation. Contoso, dealing with home monitoring security and medical monitoring
security systems, need a system to manage usage and to manage their infrastructure. The
products offered should be well “thought out” to see to it that the products developed by the
design team meet international standards. In addition to Contoso’s products, we are also going to
find a way to integrate Adatum’s systems into Contoso’s systems. Contoso will have to find a
way to control the resources of Adatum for easier management.
Contoso also has its systems that they run. These systems also need proper management
to see that they work perfectly so that the customers are served as required.As the administrator,
working with other team players, we need to come up with a solution for Contoso’s products and
an answer for Adatum Corporation’s systems. The solution provided also needs to address an
automatic installation strategy to support the installation of several new servers each month. The
proposal also has to address the issue of Windows Installation Database (WID) that will be used
to manage the home security and medical monitoring systems. Moving forward, we have
discussed briefly Contoso Corporation and Adatum Corporation in the next two paragraphs.
Contoso Corporation
Contoso Corporation is a leading producer of smart devices. They produce home
monitoring devices and medical monitoring devices They also provide installation services for
people. Contoso Corporation also acquired Adatum Corporation. The technology team will need
to come up with a strategy to control the systems available and incorporate the acquired
company so that they complement each other.
Adatum Corporation
Adatum Corporation has a Microsoft Exchange server to manage the emails of their staff.
They also have an SQL server that serves as their database. In addition, Adatum Corporation also
has twenty smaller sites with each consisting of between twenty and fifty employees. The
corporation has an internal network to manage their employees and a mail server to enable their
communications. They also have a database to help them manage their information. The
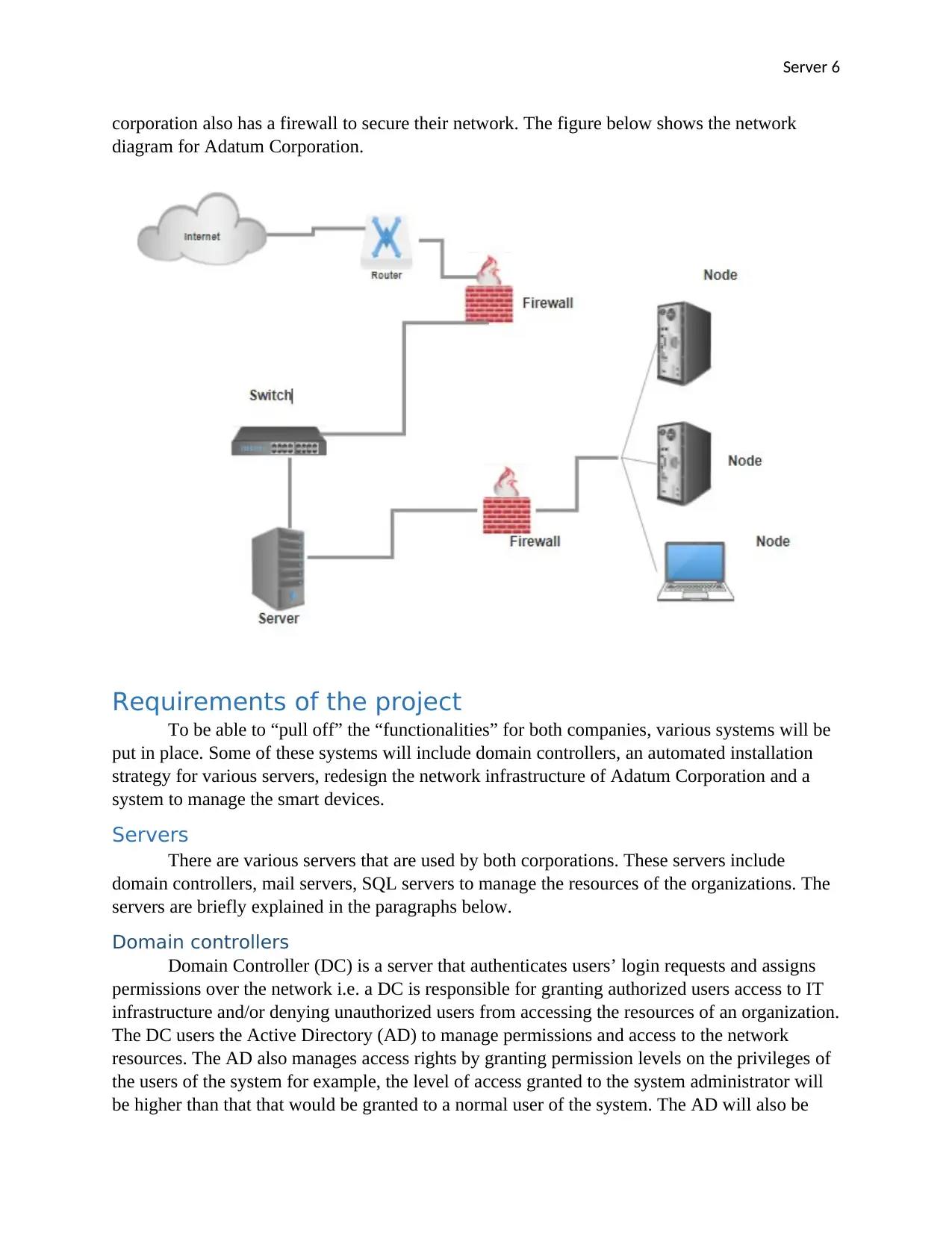
Server 6
corporation also has a firewall to secure their network. The figure below shows the network
diagram for Adatum Corporation.
Requirements of the project
To be able to “pull off” the “functionalities” for both companies, various systems will be
put in place. Some of these systems will include domain controllers, an automated installation
strategy for various servers, redesign the network infrastructure of Adatum Corporation and a
system to manage the smart devices.
Servers
There are various servers that are used by both corporations. These servers include
domain controllers, mail servers, SQL servers to manage the resources of the organizations. The
servers are briefly explained in the paragraphs below.
Domain controllers
Domain Controller (DC) is a server that authenticates users’ login requests and assigns
permissions over the network i.e. a DC is responsible for granting authorized users access to IT
infrastructure and/or denying unauthorized users from accessing the resources of an organization.
The DC users the Active Directory (AD) to manage permissions and access to the network
resources. The AD also manages access rights by granting permission levels on the privileges of
the users of the system for example, the level of access granted to the system administrator will
be higher than that that would be granted to a normal user of the system. The AD will also be
corporation also has a firewall to secure their network. The figure below shows the network
diagram for Adatum Corporation.
Requirements of the project
To be able to “pull off” the “functionalities” for both companies, various systems will be
put in place. Some of these systems will include domain controllers, an automated installation
strategy for various servers, redesign the network infrastructure of Adatum Corporation and a
system to manage the smart devices.
Servers
There are various servers that are used by both corporations. These servers include
domain controllers, mail servers, SQL servers to manage the resources of the organizations. The
servers are briefly explained in the paragraphs below.
Domain controllers
Domain Controller (DC) is a server that authenticates users’ login requests and assigns
permissions over the network i.e. a DC is responsible for granting authorized users access to IT
infrastructure and/or denying unauthorized users from accessing the resources of an organization.
The DC users the Active Directory (AD) to manage permissions and access to the network
resources. The AD also manages access rights by granting permission levels on the privileges of
the users of the system for example, the level of access granted to the system administrator will
be higher than that that would be granted to a normal user of the system. The AD will also be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Server 7
used to manage groups and group policies. For more information, you can refer to Appendix
Two.
Mail servers
Microsoft Exchange is a mail server. The Microsoft Exchange server is an email server
that can also be used to manage contacts, schedule events using the calendaring system
incorporated in it. Microsoft Exchange server serves to manage the business emails of the
company. Both Contoso and Adatum Corporations have an exchange server to manage their
emails. The server has a mailbox to manage the emails of the employees of the organizations.
The mailbox serves as an agent to deliver and receive the mails of its users. The mailbox also has
access roles to authenticate and handle security and messaging. The exchange server is designed
to give employees access to their messages easily through their phones, desktops, tablets and
ever through various web systems. To manage security of the exchange server, there is an edge
transport server (role that protects the organization from attacks like viruses and spam).
SQL server
SQL server is a database server whose main purpose is to store data and allow access to
the data whenever needed. The server enables for retrieval of stored data.
Automated installation strategy
An automated installation strategy is needed to manage the resources of both companies
i.e. using an automated installation strategy, it will be possible to deploy servers swiftly and
efficiently in line with the ever changing business landscape. Having an automated installation
strategy will also add redundancy to the organizations making it possible to deploy infrastructure
efficiently. To manage automated installation, the team may use Windows Deployment Service
(WDS). WDS allows for remote deployment and management of operating systems (Minasi,
2014). You can also use the Windows Assessment and Deployment Kit (Windows ADK) to
manage automatic installation. The Windows ADK contains various assessment and deployment
tools and technologies like Windows System Image Manager (Windows SIM), Volume
Activation Management Tool (VAMT), Deployment Image Servicing and Management (DSIM),
Windows Assessment Services, Windows Imaging and Configuration Designer (Windows ICD),
Windows Performance Toolkit (WPT), Application Compatibility Toolkit (ACT), User State
Management Tool (USTM).
All the automated installation tools mentioned above are meant to make the work of the
system administrators as easy as possible. Using various tools for example, DSIM, it will be
possible to capture, service and deploy boot images and operating system images. USMT can be
used to backup and restore user state, data, settings from one installation to another. The purpose
of the automated installation strategy is to enable easy management and deployment of services.
Redesign the network infrastructure of Adatum Corporation
Adatum Corporation’s network infrastructure needs streamlining to make it effective and
more efficient. For example, the use of one firewall will be enough to save on costs. Their mail
and SQL server will also be added to the domain controller of Contoso Corporation for easier
management.
used to manage groups and group policies. For more information, you can refer to Appendix
Two.
Mail servers
Microsoft Exchange is a mail server. The Microsoft Exchange server is an email server
that can also be used to manage contacts, schedule events using the calendaring system
incorporated in it. Microsoft Exchange server serves to manage the business emails of the
company. Both Contoso and Adatum Corporations have an exchange server to manage their
emails. The server has a mailbox to manage the emails of the employees of the organizations.
The mailbox serves as an agent to deliver and receive the mails of its users. The mailbox also has
access roles to authenticate and handle security and messaging. The exchange server is designed
to give employees access to their messages easily through their phones, desktops, tablets and
ever through various web systems. To manage security of the exchange server, there is an edge
transport server (role that protects the organization from attacks like viruses and spam).
SQL server
SQL server is a database server whose main purpose is to store data and allow access to
the data whenever needed. The server enables for retrieval of stored data.
Automated installation strategy
An automated installation strategy is needed to manage the resources of both companies
i.e. using an automated installation strategy, it will be possible to deploy servers swiftly and
efficiently in line with the ever changing business landscape. Having an automated installation
strategy will also add redundancy to the organizations making it possible to deploy infrastructure
efficiently. To manage automated installation, the team may use Windows Deployment Service
(WDS). WDS allows for remote deployment and management of operating systems (Minasi,
2014). You can also use the Windows Assessment and Deployment Kit (Windows ADK) to
manage automatic installation. The Windows ADK contains various assessment and deployment
tools and technologies like Windows System Image Manager (Windows SIM), Volume
Activation Management Tool (VAMT), Deployment Image Servicing and Management (DSIM),
Windows Assessment Services, Windows Imaging and Configuration Designer (Windows ICD),
Windows Performance Toolkit (WPT), Application Compatibility Toolkit (ACT), User State
Management Tool (USTM).
All the automated installation tools mentioned above are meant to make the work of the
system administrators as easy as possible. Using various tools for example, DSIM, it will be
possible to capture, service and deploy boot images and operating system images. USMT can be
used to backup and restore user state, data, settings from one installation to another. The purpose
of the automated installation strategy is to enable easy management and deployment of services.
Redesign the network infrastructure of Adatum Corporation
Adatum Corporation’s network infrastructure needs streamlining to make it effective and
more efficient. For example, the use of one firewall will be enough to save on costs. Their mail
and SQL server will also be added to the domain controller of Contoso Corporation for easier
management.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
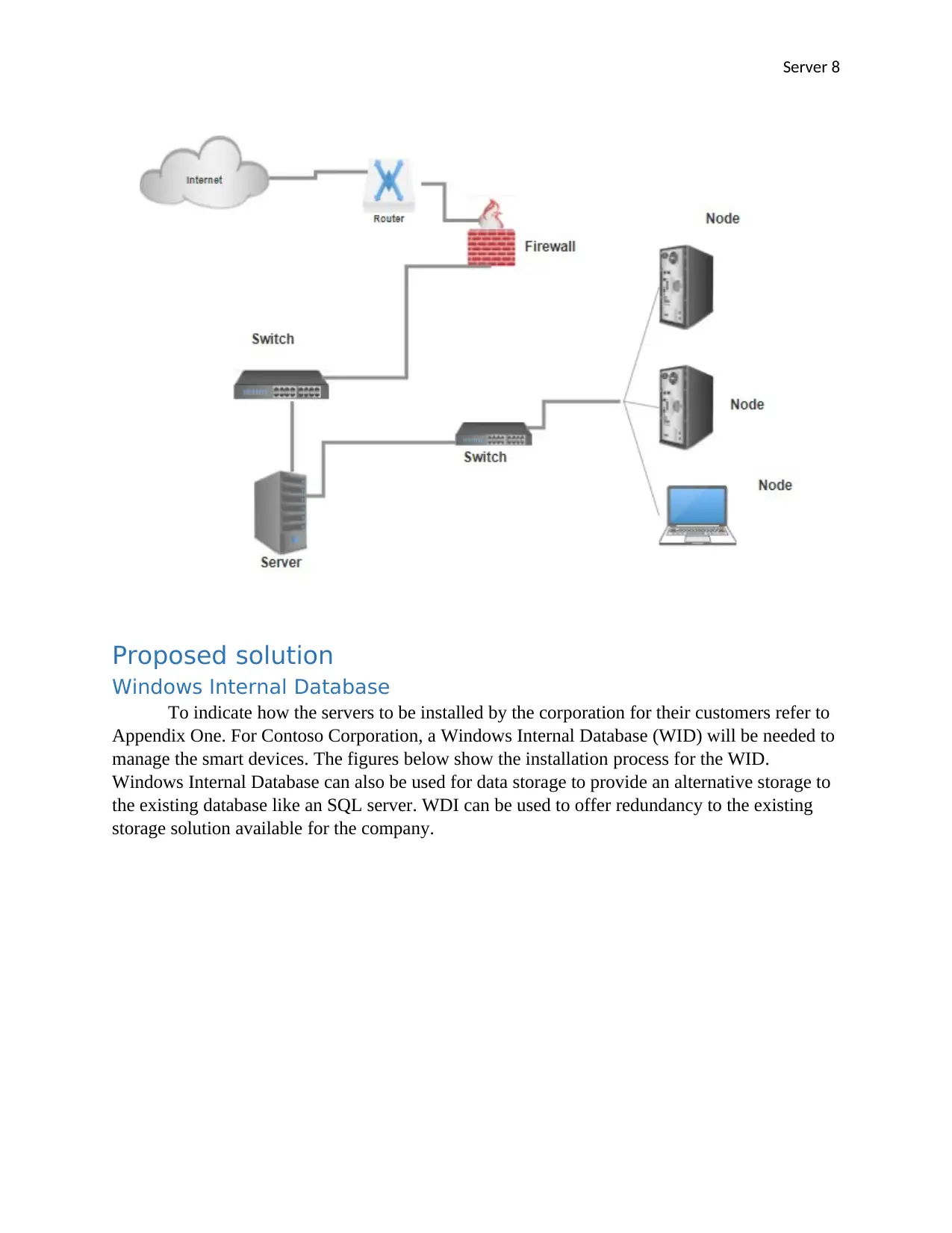
Server 8
Proposed solution
Windows Internal Database
To indicate how the servers to be installed by the corporation for their customers refer to
Appendix One. For Contoso Corporation, a Windows Internal Database (WID) will be needed to
manage the smart devices. The figures below show the installation process for the WID.
Windows Internal Database can also be used for data storage to provide an alternative storage to
the existing database like an SQL server. WDI can be used to offer redundancy to the existing
storage solution available for the company.
Proposed solution
Windows Internal Database
To indicate how the servers to be installed by the corporation for their customers refer to
Appendix One. For Contoso Corporation, a Windows Internal Database (WID) will be needed to
manage the smart devices. The figures below show the installation process for the WID.
Windows Internal Database can also be used for data storage to provide an alternative storage to
the existing database like an SQL server. WDI can be used to offer redundancy to the existing
storage solution available for the company.
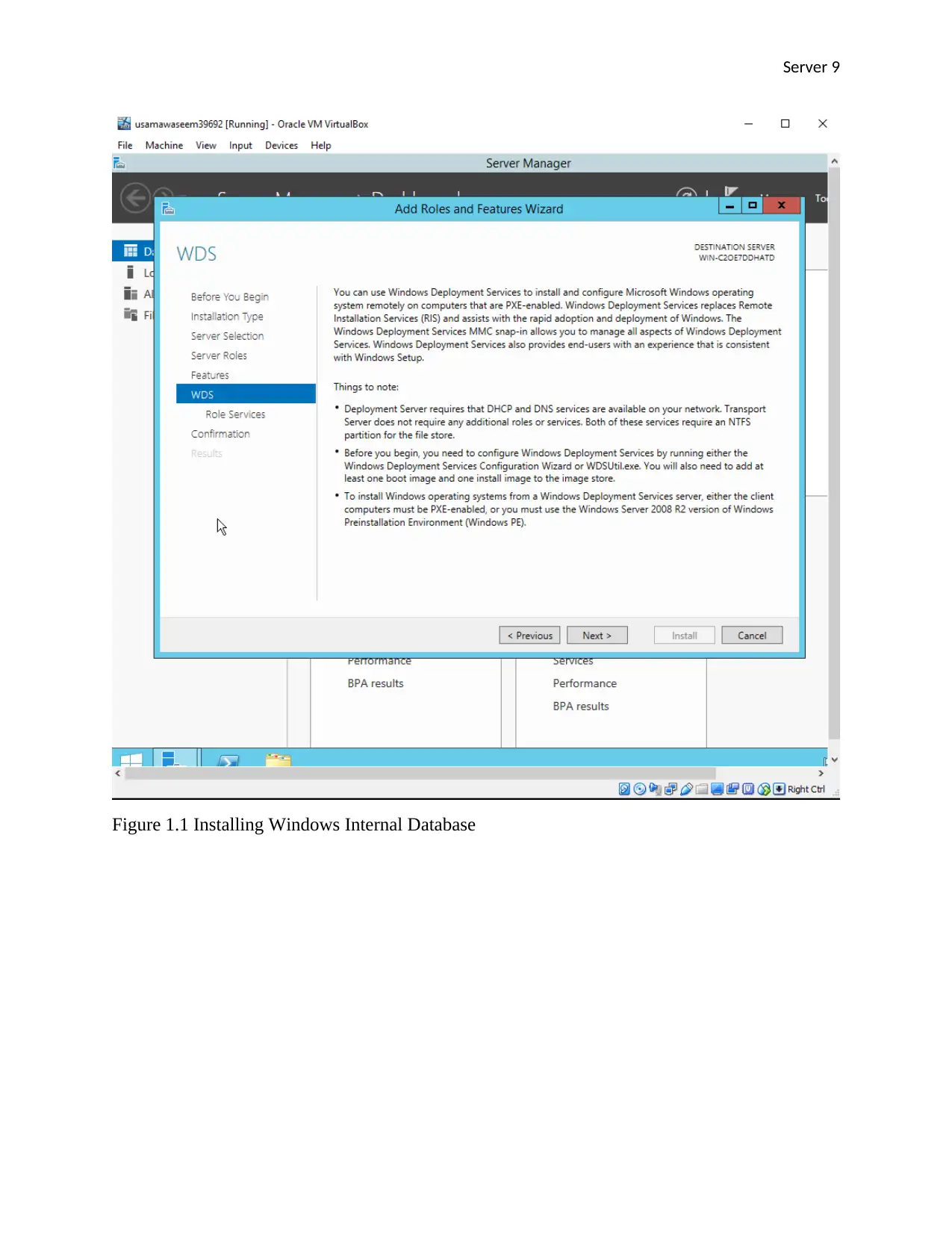
Server 9
Figure 1.1 Installing Windows Internal Database
Figure 1.1 Installing Windows Internal Database
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
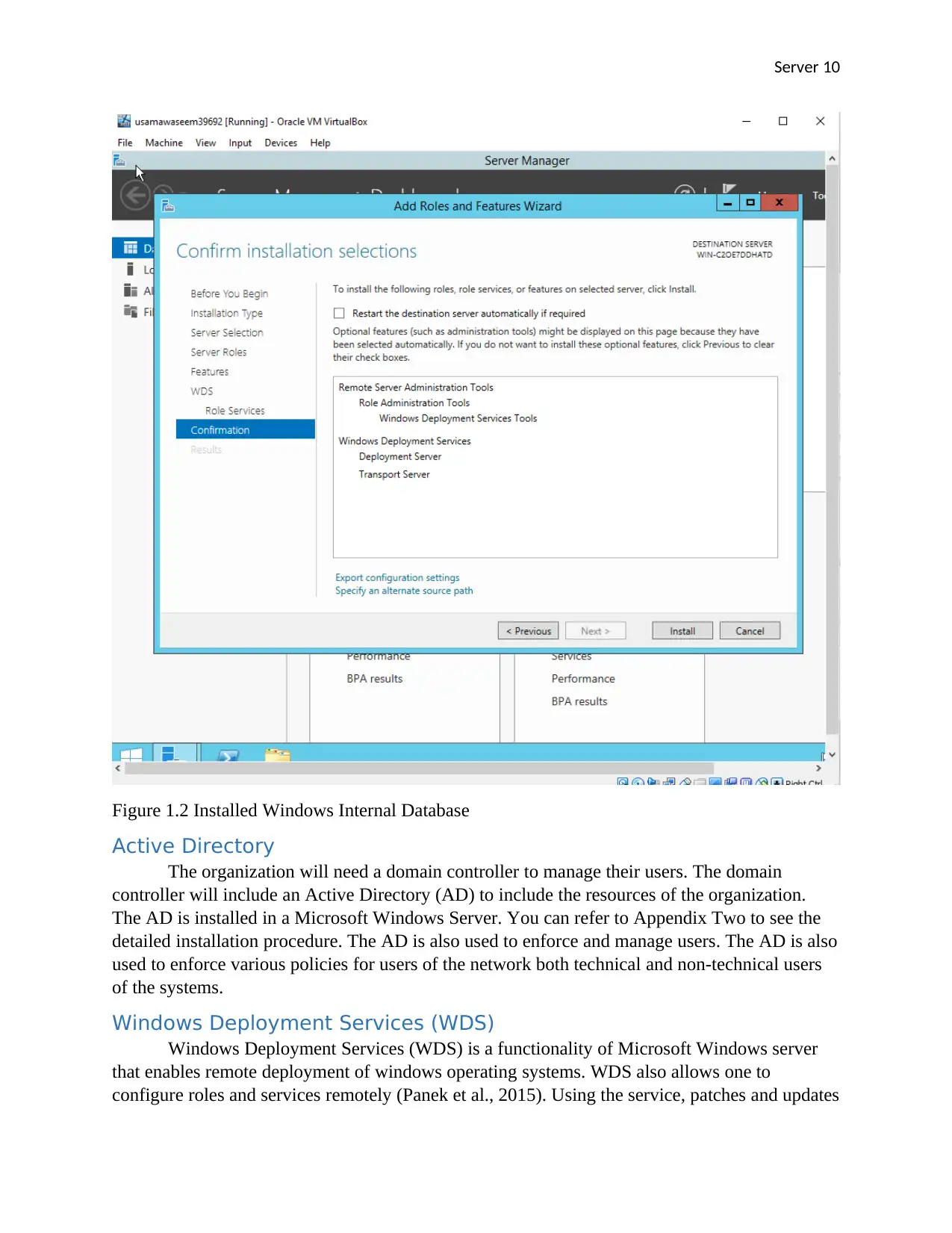
Server 10
Figure 1.2 Installed Windows Internal Database
Active Directory
The organization will need a domain controller to manage their users. The domain
controller will include an Active Directory (AD) to include the resources of the organization.
The AD is installed in a Microsoft Windows Server. You can refer to Appendix Two to see the
detailed installation procedure. The AD is also used to enforce and manage users. The AD is also
used to enforce various policies for users of the network both technical and non-technical users
of the systems.
Windows Deployment Services (WDS)
Windows Deployment Services (WDS) is a functionality of Microsoft Windows server
that enables remote deployment of windows operating systems. WDS also allows one to
configure roles and services remotely (Panek et al., 2015). Using the service, patches and updates
Figure 1.2 Installed Windows Internal Database
Active Directory
The organization will need a domain controller to manage their users. The domain
controller will include an Active Directory (AD) to include the resources of the organization.
The AD is installed in a Microsoft Windows Server. You can refer to Appendix Two to see the
detailed installation procedure. The AD is also used to enforce and manage users. The AD is also
used to enforce various policies for users of the network both technical and non-technical users
of the systems.
Windows Deployment Services (WDS)
Windows Deployment Services (WDS) is a functionality of Microsoft Windows server
that enables remote deployment of windows operating systems. WDS also allows one to
configure roles and services remotely (Panek et al., 2015). Using the service, patches and updates
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Server 11
can also be done remotely. The WDS will be used to manage the servers that will be deployed by
Contoso Corporation. The service will enable easy and convenient management of the several
servers that the organization will be planning to roll out for their customers. The WDS will be
used to manage the automatic installation of smart devices. To show the detailed installation of
the WDS you can refer to Appendix Three.
Conclusion
Contoso Corporation is a company dealing with smart devices. Having acquired Adatum
Corporation, they had to form the various structures to enable them control both businesses. A
good management strategy makes it easy to administer the IT infrastructure available. Expansion
of one’s business (acquisition of Adatum Corporation) also introduces various factors like
scalability. It is therefore necessary to have a plan in place to incorporate the new systems
without necessarily interfering with the existing systems. If planned correctly, developed
effectively and executed meticulously, the system will work out fine without giving the
implementers unnecessary headaches. All the stakeholders should also be involved all the way
when implementing the systems to enable compliance and informed use of the systems rolled
out.
can also be done remotely. The WDS will be used to manage the servers that will be deployed by
Contoso Corporation. The service will enable easy and convenient management of the several
servers that the organization will be planning to roll out for their customers. The WDS will be
used to manage the automatic installation of smart devices. To show the detailed installation of
the WDS you can refer to Appendix Three.
Conclusion
Contoso Corporation is a company dealing with smart devices. Having acquired Adatum
Corporation, they had to form the various structures to enable them control both businesses. A
good management strategy makes it easy to administer the IT infrastructure available. Expansion
of one’s business (acquisition of Adatum Corporation) also introduces various factors like
scalability. It is therefore necessary to have a plan in place to incorporate the new systems
without necessarily interfering with the existing systems. If planned correctly, developed
effectively and executed meticulously, the system will work out fine without giving the
implementers unnecessary headaches. All the stakeholders should also be involved all the way
when implementing the systems to enable compliance and informed use of the systems rolled
out.

Server 12
Works cited
Minasi, M. (2014). Mastering Windows server 2012 R2. Indianapolis, Ind.: John Wiley & Sons.
Panek, W., Rice, M., McMiller, W. and Stokes, J. (2015). MCSA Windows Server 2012 R2
complete study guide. [Indianapolis, Ind.]: Sybex, p.2.
Works cited
Minasi, M. (2014). Mastering Windows server 2012 R2. Indianapolis, Ind.: John Wiley & Sons.
Panek, W., Rice, M., McMiller, W. and Stokes, J. (2015). MCSA Windows Server 2012 R2
complete study guide. [Indianapolis, Ind.]: Sybex, p.2.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





