Service Oriented Software Engineering: Process Mining and Applications
VerifiedAdded on 2023/06/05
|10
|1705
|169
Report
AI Summary
This report provides an overview of service-oriented software engineering through the lens of process mining. It begins with a BPMN model for a bank's internal procedure for change of details, detailing the steps from initial request to data validation and storage, highlighting the importance of data integrity and audit logs. The report then presents an insurance claim process model, outlining the steps from claim receipt to payment, including claim evaluation, estimation, and approval stages. Furthermore, the report discusses process mining and its application scenarios, emphasizing its ability to extract significant information from event logs to improve business processes and support auditing. It also details the use of process mining in discovering actual processes versus perceived processes and its role in delta analysis, comparing real and predefined processes to identify inconsistencies and improve business process intelligence. The report concludes by highlighting the importance of process mining tools in business process intelligence and how it helps in extracting event data from databases.

Running head: SERVICE ORIENTED SOFTWARE ENGINEERING
Service Oriented Software Engineering
Name of the Student
Name of the University
Service Oriented Software Engineering
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SERVICE ORIENTED SOFTWARE ENGINEERING
Table of Contents
Part One:.....................................................................................................................................2
Part Two:....................................................................................................................................4
Part Three:..................................................................................................................................5
Bibliography:..............................................................................................................................8
Table of Contents
Part One:.....................................................................................................................................2
Part Two:....................................................................................................................................4
Part Three:..................................................................................................................................5
Bibliography:..............................................................................................................................8
2SERVICE ORIENTED SOFTWARE ENGINEERING
Part One:
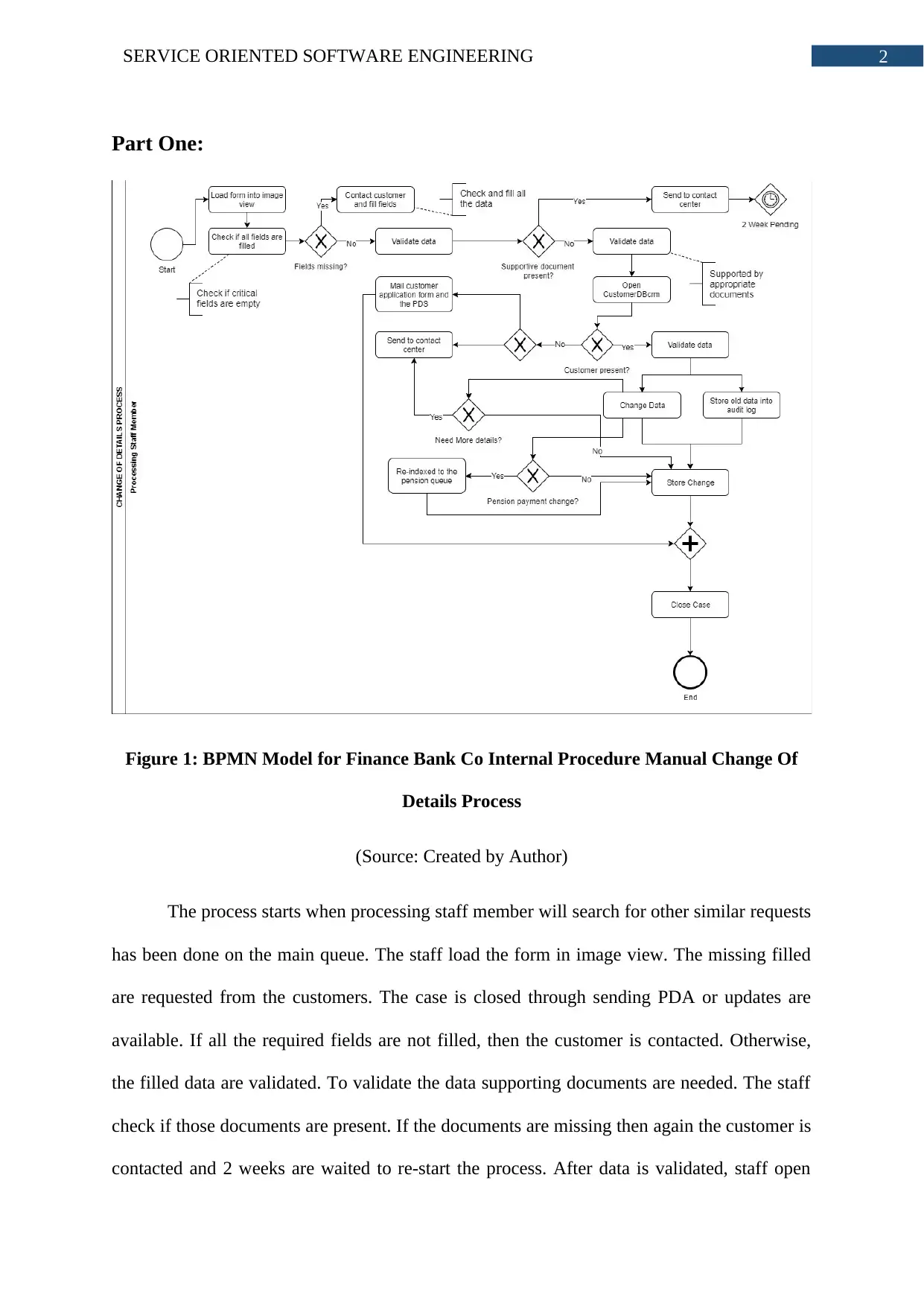
Figure 1: BPMN Model for Finance Bank Co Internal Procedure Manual Change Of
Details Process
(Source: Created by Author)
The process starts when processing staff member will search for other similar requests
has been done on the main queue. The staff load the form in image view. The missing filled
are requested from the customers. The case is closed through sending PDA or updates are
available. If all the required fields are not filled, then the customer is contacted. Otherwise,
the filled data are validated. To validate the data supporting documents are needed. The staff
check if those documents are present. If the documents are missing then again the customer is
contacted and 2 weeks are waited to re-start the process. After data is validated, staff open
Part One:
Figure 1: BPMN Model for Finance Bank Co Internal Procedure Manual Change Of
Details Process
(Source: Created by Author)
The process starts when processing staff member will search for other similar requests
has been done on the main queue. The staff load the form in image view. The missing filled
are requested from the customers. The case is closed through sending PDA or updates are
available. If all the required fields are not filled, then the customer is contacted. Otherwise,
the filled data are validated. To validate the data supporting documents are needed. The staff
check if those documents are present. If the documents are missing then again the customer is
contacted and 2 weeks are waited to re-start the process. After data is validated, staff open
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SERVICE ORIENTED SOFTWARE ENGINEERING
CustomerBDcrm. If the customer is not present in the system then PDS is sent to the
customer. If for changing data additional data is required then contact centre is instructed to
collect those required data. The organization strongly focuses on storing all the data.
Changing data does not mean old data must be deleted. Along with changing data, the old
data is stored in audit log. If the change is related to pension payment then re-indexed to
pension queue done. After all the data are properly validated and all data are present then data
are stored.
Annotations:
i. Check if critical fields are empty (Process: Check if all fields are filled)
ii. Check and fill all the data (Process: Contact customer and fill fields)
iii. Supported by appropriate documents (Process: Validate data)
CustomerBDcrm. If the customer is not present in the system then PDS is sent to the
customer. If for changing data additional data is required then contact centre is instructed to
collect those required data. The organization strongly focuses on storing all the data.
Changing data does not mean old data must be deleted. Along with changing data, the old
data is stored in audit log. If the change is related to pension payment then re-indexed to
pension queue done. After all the data are properly validated and all data are present then data
are stored.
Annotations:
i. Check if critical fields are empty (Process: Check if all fields are filled)
ii. Check and fill all the data (Process: Contact customer and fill fields)
iii. Supported by appropriate documents (Process: Validate data)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SERVICE ORIENTED SOFTWARE ENGINEERING
Part Two:
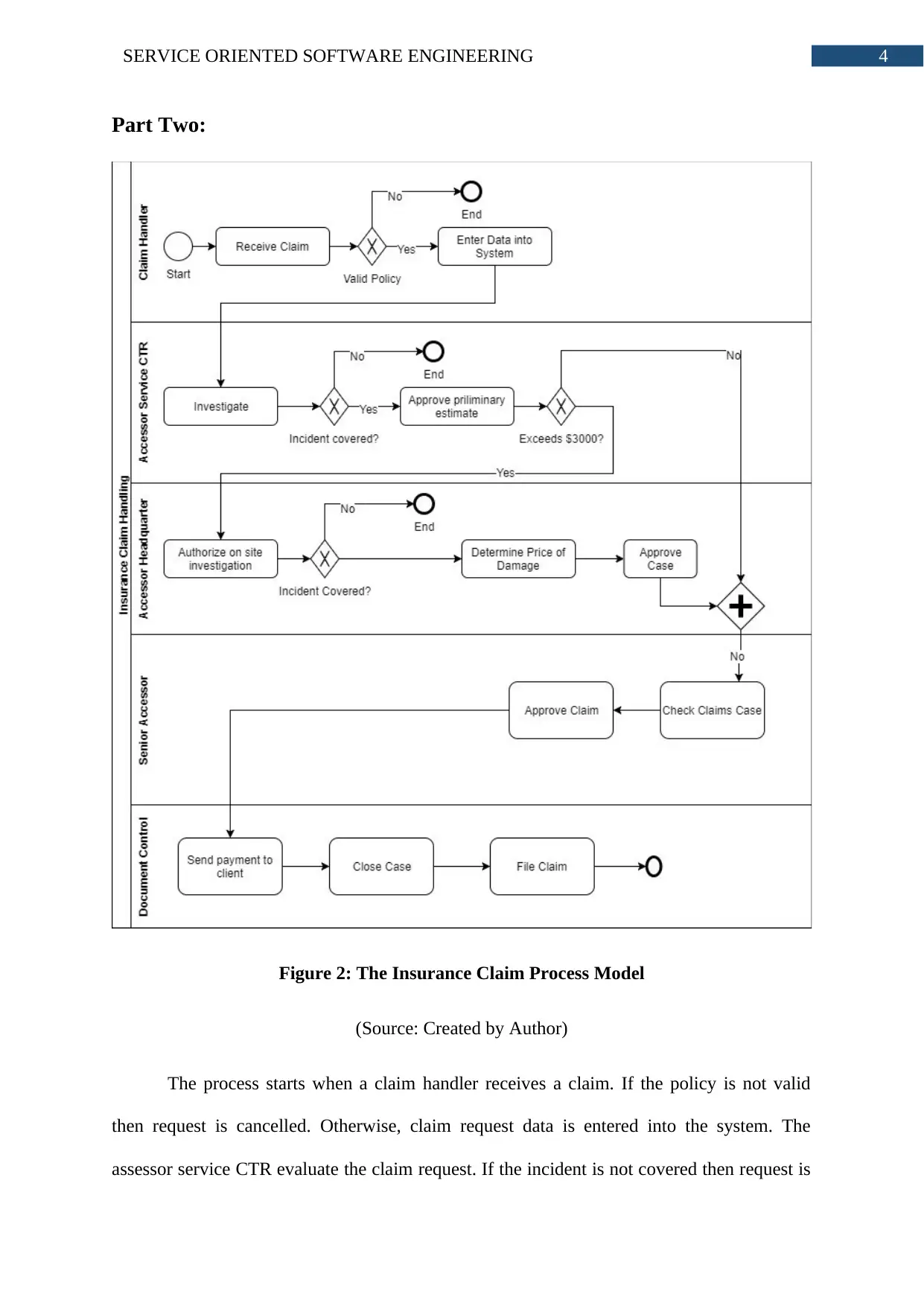
Figure 2: The Insurance Claim Process Model
(Source: Created by Author)
The process starts when a claim handler receives a claim. If the policy is not valid
then request is cancelled. Otherwise, claim request data is entered into the system. The
assessor service CTR evaluate the claim request. If the incident is not covered then request is
Part Two:
Figure 2: The Insurance Claim Process Model
(Source: Created by Author)
The process starts when a claim handler receives a claim. If the policy is not valid
then request is cancelled. Otherwise, claim request data is entered into the system. The
assessor service CTR evaluate the claim request. If the incident is not covered then request is

5SERVICE ORIENTED SOFTWARE ENGINEERING
cancelled. Otherwise, preliminary estimation of claim is done. If the primary estimate
exceeds $3000 then on-site investigation is authorized by Assessor Headquarter. If the report
says that incident was covered then price damage is calculated. Otherwise, the request is
cancelled. The case is approved and forward to Senior Assessor. The senior assessor check
claim case for both approved case and preliminary estimate under $3000. The senior assessor
approved the claim forward the request to Document Control Department. The payment is
sent to client. The case is finally closed and file is claimed by the document control office.
The claim handling is completely managed by internal staff. For investigation, organization
can hire third party but that is seen in very rare cases.
Part Three:
The process mining aims for discovering the significant information through an event
log very easily. The collected information through process mining can be later utilized to
implement an organization wide system or analytical method that assists in auditing. The
existing business process will then improve significantly and provide better chance for
business growth (Van der Aalst 2016). The collected information are objectively compiled in
process mining. At the end of the day, process mining procedures are useful on the grounds
that they accumulate data about what is really occurring as per an event log of a business, and
not what individuals believe is going on in this company.
cancelled. Otherwise, preliminary estimation of claim is done. If the primary estimate
exceeds $3000 then on-site investigation is authorized by Assessor Headquarter. If the report
says that incident was covered then price damage is calculated. Otherwise, the request is
cancelled. The case is approved and forward to Senior Assessor. The senior assessor check
claim case for both approved case and preliminary estimate under $3000. The senior assessor
approved the claim forward the request to Document Control Department. The payment is
sent to client. The case is finally closed and file is claimed by the document control office.
The claim handling is completely managed by internal staff. For investigation, organization
can hire third party but that is seen in very rare cases.
Part Three:
The process mining aims for discovering the significant information through an event
log very easily. The collected information through process mining can be later utilized to
implement an organization wide system or analytical method that assists in auditing. The
existing business process will then improve significantly and provide better chance for
business growth (Van der Aalst 2016). The collected information are objectively compiled in
process mining. At the end of the day, process mining procedures are useful on the grounds
that they accumulate data about what is really occurring as per an event log of a business, and
not what individuals believe is going on in this company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SERVICE ORIENTED SOFTWARE ENGINEERING
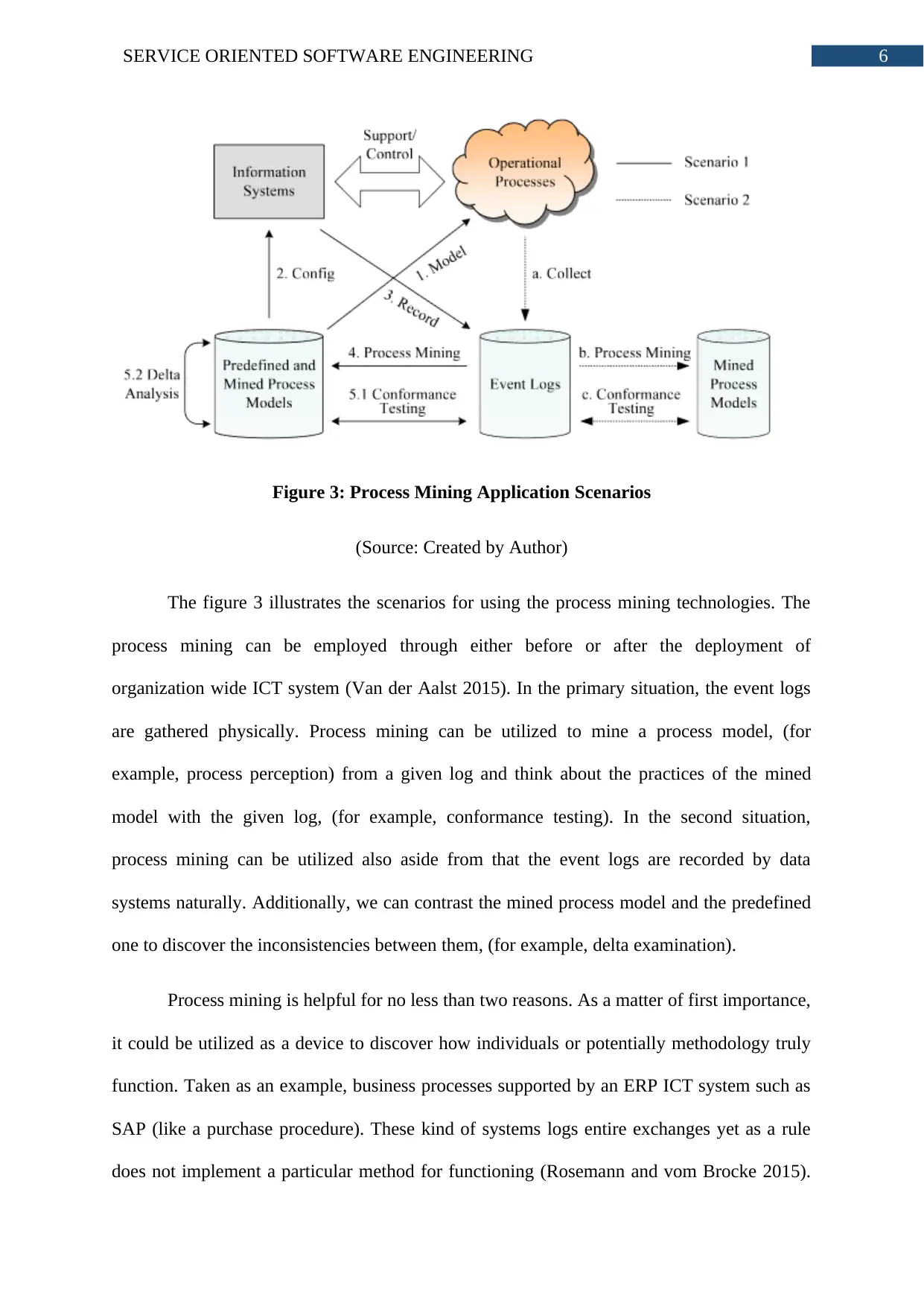
Figure 3: Process Mining Application Scenarios
(Source: Created by Author)
The figure 3 illustrates the scenarios for using the process mining technologies. The
process mining can be employed through either before or after the deployment of
organization wide ICT system (Van der Aalst 2015). In the primary situation, the event logs
are gathered physically. Process mining can be utilized to mine a process model, (for
example, process perception) from a given log and think about the practices of the mined
model with the given log, (for example, conformance testing). In the second situation,
process mining can be utilized also aside from that the event logs are recorded by data
systems naturally. Additionally, we can contrast the mined process model and the predefined
one to discover the inconsistencies between them, (for example, delta examination).
Process mining is helpful for no less than two reasons. As a matter of first importance,
it could be utilized as a device to discover how individuals or potentially methodology truly
function. Taken as an example, business processes supported by an ERP ICT system such as
SAP (like a purchase procedure). These kind of systems logs entire exchanges yet as a rule
does not implement a particular method for functioning (Rosemann and vom Brocke 2015).
Figure 3: Process Mining Application Scenarios
(Source: Created by Author)
The figure 3 illustrates the scenarios for using the process mining technologies. The
process mining can be employed through either before or after the deployment of
organization wide ICT system (Van der Aalst 2015). In the primary situation, the event logs
are gathered physically. Process mining can be utilized to mine a process model, (for
example, process perception) from a given log and think about the practices of the mined
model with the given log, (for example, conformance testing). In the second situation,
process mining can be utilized also aside from that the event logs are recorded by data
systems naturally. Additionally, we can contrast the mined process model and the predefined
one to discover the inconsistencies between them, (for example, delta examination).
Process mining is helpful for no less than two reasons. As a matter of first importance,
it could be utilized as a device to discover how individuals or potentially methodology truly
function. Taken as an example, business processes supported by an ERP ICT system such as
SAP (like a purchase procedure). These kind of systems logs entire exchanges yet as a rule
does not implement a particular method for functioning (Rosemann and vom Brocke 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SERVICE ORIENTED SOFTWARE ENGINEERING
Within like a domain, process mining may be utilized for picking up understanding within the
authenticated procedure. Alternative situation would be the number of patients in a Hospital
or Health Care Organization. It is to be noted that, taken as an instance, condition entire
exercises are logged however, data regarding the fundamental procedure is regularly absent.
Within this setting pressure that database administration systems give information regarding
key functioning pointers like asset usage, stream periods and management levels (Partington
et al. 2015). However, does not concern about the unknown business processes, taken as an
instance, fundamental relations, demanding of functions and that is only the bottom of the
concerned topic. Second, process mining may be employed regarding Delta Investigation,
taken as an instance, contrasting the real process and few of the predefined procedures. A
model this determines the functioning capability of individuals and associations based on
various anticipated factors. By looking at the inflexible or unique process model with the
freshly developed BPMN model, contradictions among both can be recognized and utilized
for improving the procedure (Nguyen et al. 2014). Taken for instance, the developed
reference models with regards to SAP. The developed models represent the utilization of the
system. Utilizing process mining it is conceivable to check whether this is the situation. Truth
be told, process mining could likewise be utilized to look at changed offices/associations
utilizing the same ERP system. In the context of business process intelligence or BPI, the
process mining is considered as one of the crucial tools.
Within like a domain, process mining may be utilized for picking up understanding within the
authenticated procedure. Alternative situation would be the number of patients in a Hospital
or Health Care Organization. It is to be noted that, taken as an instance, condition entire
exercises are logged however, data regarding the fundamental procedure is regularly absent.
Within this setting pressure that database administration systems give information regarding
key functioning pointers like asset usage, stream periods and management levels (Partington
et al. 2015). However, does not concern about the unknown business processes, taken as an
instance, fundamental relations, demanding of functions and that is only the bottom of the
concerned topic. Second, process mining may be employed regarding Delta Investigation,
taken as an instance, contrasting the real process and few of the predefined procedures. A
model this determines the functioning capability of individuals and associations based on
various anticipated factors. By looking at the inflexible or unique process model with the
freshly developed BPMN model, contradictions among both can be recognized and utilized
for improving the procedure (Nguyen et al. 2014). Taken for instance, the developed
reference models with regards to SAP. The developed models represent the utilization of the
system. Utilizing process mining it is conceivable to check whether this is the situation. Truth
be told, process mining could likewise be utilized to look at changed offices/associations
utilizing the same ERP system. In the context of business process intelligence or BPI, the
process mining is considered as one of the crucial tools.

8SERVICE ORIENTED SOFTWARE ENGINEERING
Bibliography:
Bose, R.J.C., Van Der Aalst, W.M., Zliobaite, I. and Pechenizkiy, M., 2014. Dealing with
concept drifts in process mining. IEEE transactions on neural networks and learning systems,
25(1), pp.154-171.
Nguyen, H., Dumas, M., La Rosa, M., Maggi, F.M. and Suriadi, S., 2014, October. Mining
business process deviance: a quest for accuracy. In OTM Confederated International
Conferences" On the Move to Meaningful Internet Systems" (pp. 436-445). Springer, Berlin,
Heidelberg.
Nguyen, H., Dumas, M., ter Hofstede, A.H., La Rosa, M. and Maggi, F.M., 2017, June.
Mining business process stages from event logs. In International Conference on Advanced
Information Systems Engineering (pp. 577-594). Springer, Cham.
Partington, A., Wynn, M., Suriadi, S., Ouyang, C. and Karnon, J., 2015. Process mining for
clinical processes: a comparative analysis of four Australian hospitals. ACM Transactions on
Management Information Systems (TMIS), 5(4), p.19.
Polyvyanyy, A., Smirnov, S. and Weske, M., 2015. Business process model abstraction. In
Handbook on Business Process Management 1 (pp. 147-165). Springer, Berlin, Heidelberg.
Rojas, E., Munoz-Gama, J., Sepúlveda, M. and Capurro, D., 2016. Process mining in
healthcare: A literature review. Journal of biomedical informatics, 61, pp.224-236.
Rosemann, M. and vom Brocke, J., 2015. The six core elements of business process
management. In Handbook on business process management 1 (pp. 105-122). Springer,
Berlin, Heidelberg.
Bibliography:
Bose, R.J.C., Van Der Aalst, W.M., Zliobaite, I. and Pechenizkiy, M., 2014. Dealing with
concept drifts in process mining. IEEE transactions on neural networks and learning systems,
25(1), pp.154-171.
Nguyen, H., Dumas, M., La Rosa, M., Maggi, F.M. and Suriadi, S., 2014, October. Mining
business process deviance: a quest for accuracy. In OTM Confederated International
Conferences" On the Move to Meaningful Internet Systems" (pp. 436-445). Springer, Berlin,
Heidelberg.
Nguyen, H., Dumas, M., ter Hofstede, A.H., La Rosa, M. and Maggi, F.M., 2017, June.
Mining business process stages from event logs. In International Conference on Advanced
Information Systems Engineering (pp. 577-594). Springer, Cham.
Partington, A., Wynn, M., Suriadi, S., Ouyang, C. and Karnon, J., 2015. Process mining for
clinical processes: a comparative analysis of four Australian hospitals. ACM Transactions on
Management Information Systems (TMIS), 5(4), p.19.
Polyvyanyy, A., Smirnov, S. and Weske, M., 2015. Business process model abstraction. In
Handbook on Business Process Management 1 (pp. 147-165). Springer, Berlin, Heidelberg.
Rojas, E., Munoz-Gama, J., Sepúlveda, M. and Capurro, D., 2016. Process mining in
healthcare: A literature review. Journal of biomedical informatics, 61, pp.224-236.
Rosemann, M. and vom Brocke, J., 2015. The six core elements of business process
management. In Handbook on business process management 1 (pp. 105-122). Springer,
Berlin, Heidelberg.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SERVICE ORIENTED SOFTWARE ENGINEERING
Sonnenberg, C. and Bannert, M., 2015. Discovering the effects of metacognitive prompts on
the sequential structure of SRL-processes using process mining techniques. Journal of
Learning Analytics, 2(1), pp.72-100.
Van der Aalst, W., 2016. Process discovery: An introduction. In Process Mining (pp. 163-
194). Springer, Berlin, Heidelberg.
Van Der Aalst, W.M., 2015. Business process simulation survival guide. In Handbook on
Business Process Management 1 (pp. 337-370). Springer, Berlin, Heidelberg.
Van der Aalst, W.M., 2015. Extracting event data from databases to unleash process mining.
In BPM-Driving innovation in a digital world (pp. 105-128). Springer, Cham.
Sonnenberg, C. and Bannert, M., 2015. Discovering the effects of metacognitive prompts on
the sequential structure of SRL-processes using process mining techniques. Journal of
Learning Analytics, 2(1), pp.72-100.
Van der Aalst, W., 2016. Process discovery: An introduction. In Process Mining (pp. 163-
194). Springer, Berlin, Heidelberg.
Van Der Aalst, W.M., 2015. Business process simulation survival guide. In Handbook on
Business Process Management 1 (pp. 337-370). Springer, Berlin, Heidelberg.
Van der Aalst, W.M., 2015. Extracting event data from databases to unleash process mining.
In BPM-Driving innovation in a digital world (pp. 105-128). Springer, Cham.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





