Seven Star Motors (SSM) Network Design and Implementation Project
VerifiedAdded on 2020/05/11
|66
|9319
|59
Project
AI Summary
This project details the network design for Seven Star Motors (SSM), an Australian company with multiple branches. The design focuses on creating a secure and efficient network using VLANs to segment departments and WLANs to connect branches, including a head office in Sydney and other branches in Melbourne, Brisbane, and Perth. The project covers network requirements, design phases (analysis, planning, design, implementation, testing, and maintenance), security policies, and a disaster recovery plan. It also includes configurations for ACLs and VLANs, ping tests, network diagrams, and a discussion of the equipment used. Furthermore, the project addresses company policies regarding internet and computer usage, worm protection, and wireless communication rules. The goal is to establish a robust and scalable network infrastructure to support SSM's business operations and growth, ensuring secure data management and access control across all departments and branches.
project 2-ssm network design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The network will be designed for the Seven Star Motors Company for all the departments with
Virtual Local Area Network (VLAN) by following the access rules given. The network will be
designed in order to develop the company’s business. An advance security will be used for
designing the network. Each and every department of the company will control and manage the
network by giving access to all other departments. There are four branches and a head office for
the company connected via Wireless Local Area Network (WLAN).
1
The network will be designed for the Seven Star Motors Company for all the departments with
Virtual Local Area Network (VLAN) by following the access rules given. The network will be
designed in order to develop the company’s business. An advance security will be used for
designing the network. Each and every department of the company will control and manage the
network by giving access to all other departments. There are four branches and a head office for
the company connected via Wireless Local Area Network (WLAN).
1

Table of Contents
1. Introduction 3
2. Requirements 3
3. Design 3
3.1 Security Policies 8
3.2 Disaster Recovery Plan 12
3.3 Disaster Recovery Policies 12
4. Network diagram and implementation 17
5. Configurations 17
ACL Configuration 36
VLAN configuration 42
Ping test 46
6. Tables 51
7. Equipment used 53
8. Conclusions 60
References 61
2
1. Introduction 3
2. Requirements 3
3. Design 3
3.1 Security Policies 8
3.2 Disaster Recovery Plan 12
3.3 Disaster Recovery Policies 12
4. Network diagram and implementation 17
5. Configurations 17
ACL Configuration 36
VLAN configuration 42
Ping test 46
6. Tables 51
7. Equipment used 53
8. Conclusions 60
References 61
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Introduction
Seven Star Motors company located in Australia and they have six branches in Melbourne,
Brisbane, Perth, Sydney and just started. The company has a head office located in Sydney and it
has two branches. The four branches and a head office of the company will be connected through
WLAN. All the branches will be designed by LAN network and WAN network will be used for
connecting all the departments. All the departments and branches will be designed by VLAN.
The security to all the branches of network will be provided by the device called Firewall. More
devices will be used for completing overall network design with the security. The network
configuration will be made by the following devices such as ISP, DHCP, Router, SSH server,
NAT server and switch etc.
2. Requirements
SSM Company spreads its branches all over the world and has six branches having many
departments. Six LAN configuration is provided to each branch of the network. WAN
configuration is provided for the connection between all the branches. One of the branch which
is in Sydney has two buildings named as Sydney-A and Sydney-B. Seventeen VLAN
connections are given since seventeen departments are there for whole branches. We need
seventeen printers for the branches since seventeen VLANs are present for seventeen
departments. Firewall is the security system used by all the systems for site security. An internet
standard named Network address translation (NAT) is the used for enabling LAN to use one set
of IP addresses for internal traffic and another set of IP addresses for external traffic used for
limiting the count of public IP addresses. All the system of the branches are provided with
technical support and a server is provided for all department each. Router, switch hub and more
required devices are used in the project as per the network requirement provided.
3. Design
Designing phase considers the development of lifecycle for designing large network.
Using this lifecycle, it is possible to design a network to improve the network security and
network maintenance. The development lifecycle contains the following phases:
i. Analysis requirement
3
Seven Star Motors company located in Australia and they have six branches in Melbourne,
Brisbane, Perth, Sydney and just started. The company has a head office located in Sydney and it
has two branches. The four branches and a head office of the company will be connected through
WLAN. All the branches will be designed by LAN network and WAN network will be used for
connecting all the departments. All the departments and branches will be designed by VLAN.
The security to all the branches of network will be provided by the device called Firewall. More
devices will be used for completing overall network design with the security. The network
configuration will be made by the following devices such as ISP, DHCP, Router, SSH server,
NAT server and switch etc.
2. Requirements
SSM Company spreads its branches all over the world and has six branches having many
departments. Six LAN configuration is provided to each branch of the network. WAN
configuration is provided for the connection between all the branches. One of the branch which
is in Sydney has two buildings named as Sydney-A and Sydney-B. Seventeen VLAN
connections are given since seventeen departments are there for whole branches. We need
seventeen printers for the branches since seventeen VLANs are present for seventeen
departments. Firewall is the security system used by all the systems for site security. An internet
standard named Network address translation (NAT) is the used for enabling LAN to use one set
of IP addresses for internal traffic and another set of IP addresses for external traffic used for
limiting the count of public IP addresses. All the system of the branches are provided with
technical support and a server is provided for all department each. Router, switch hub and more
required devices are used in the project as per the network requirement provided.
3. Design
Designing phase considers the development of lifecycle for designing large network.
Using this lifecycle, it is possible to design a network to improve the network security and
network maintenance. The development lifecycle contains the following phases:
i. Analysis requirement
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
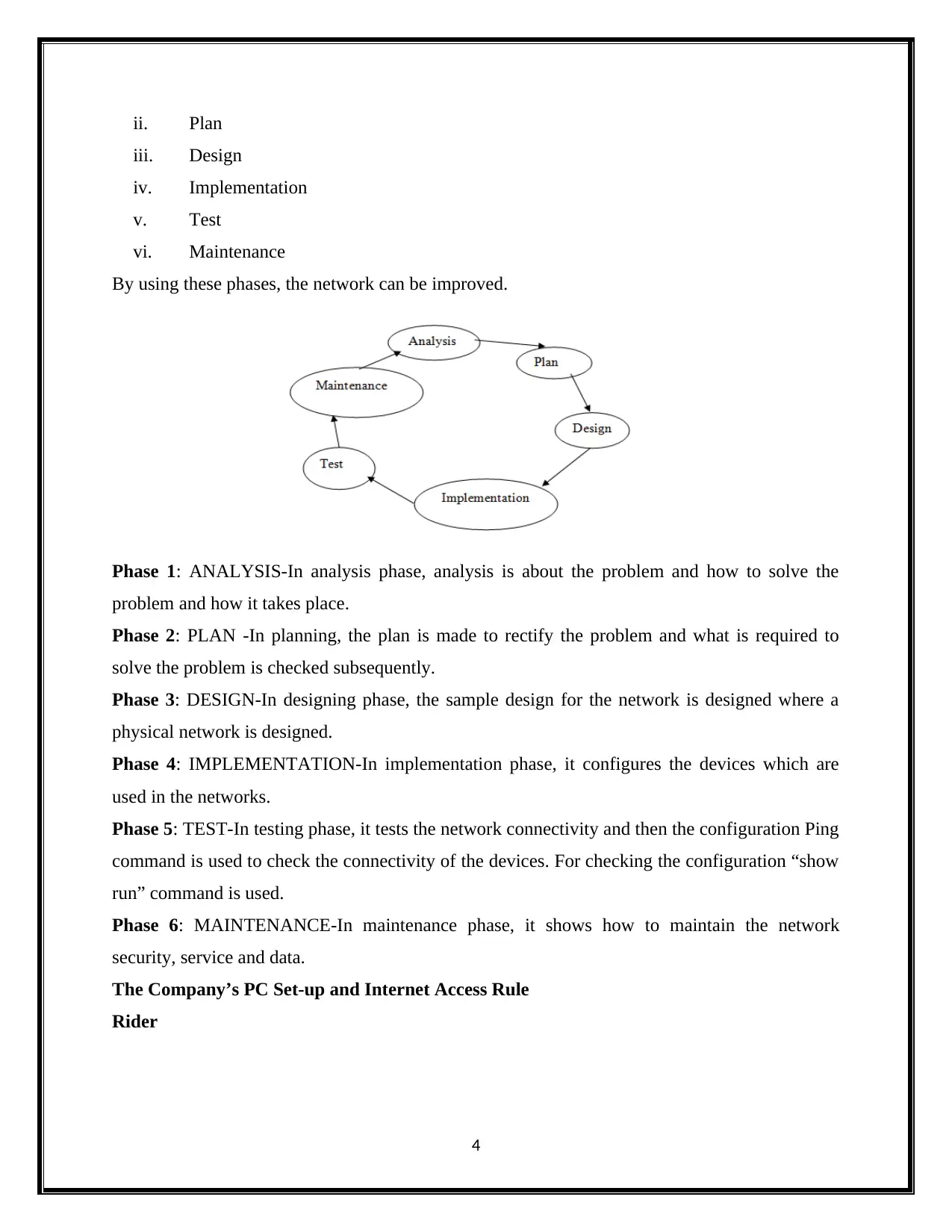
ii. Plan
iii. Design
iv. Implementation
v. Test
vi. Maintenance
By using these phases, the network can be improved.
Phase 1: ANALYSIS-In analysis phase, analysis is about the problem and how to solve the
problem and how it takes place.
Phase 2: PLAN -In planning, the plan is made to rectify the problem and what is required to
solve the problem is checked subsequently.
Phase 3: DESIGN-In designing phase, the sample design for the network is designed where a
physical network is designed.
Phase 4: IMPLEMENTATION-In implementation phase, it configures the devices which are
used in the networks.
Phase 5: TEST-In testing phase, it tests the network connectivity and then the configuration Ping
command is used to check the connectivity of the devices. For checking the configuration “show
run” command is used.
Phase 6: MAINTENANCE-In maintenance phase, it shows how to maintain the network
security, service and data.
The Company’s PC Set-up and Internet Access Rule
Rider
4
iii. Design
iv. Implementation
v. Test
vi. Maintenance
By using these phases, the network can be improved.
Phase 1: ANALYSIS-In analysis phase, analysis is about the problem and how to solve the
problem and how it takes place.
Phase 2: PLAN -In planning, the plan is made to rectify the problem and what is required to
solve the problem is checked subsequently.
Phase 3: DESIGN-In designing phase, the sample design for the network is designed where a
physical network is designed.
Phase 4: IMPLEMENTATION-In implementation phase, it configures the devices which are
used in the networks.
Phase 5: TEST-In testing phase, it tests the network connectivity and then the configuration Ping
command is used to check the connectivity of the devices. For checking the configuration “show
run” command is used.
Phase 6: MAINTENANCE-In maintenance phase, it shows how to maintain the network
security, service and data.
The Company’s PC Set-up and Internet Access Rule
Rider
4

The internet is a universal system and it contains million pages. It is caused by offensive,
and inappropriate materials. It avoids some unwanted pages and materials. It provides internet
connection to company.
Use of Internet and Company Computer Network
It uses legitimate business purposes and it provides computer network jobs. It allows
internet through the computer network. It includes possible termination and criminal liability. It
uses company’s PC properties, internet, legal and moral mode.
PC Setup Usage Boundaries
Forbidden Usage
In the organization, previously the printed agreement was lagging, an organization’s PC
setup did not distribute, vision or collection personal and profitable information like virus, self-
replicating programs and political materials. Employees should not download games and
entertaining software using organization’s networks. Employee’s should not store or send
computer network materials through email or chat room. If employee is encountered doing such
things, the materials will alert their supervisor instantly.
Illegal Copying
People should not copy or make duplicate of protected material illegally. People are
responsible for making copyright law and apply license for software, graphics, message and
documents. Other thing user can download or copy it easily. User can download the file easily
which is a license free version.
Communication of Trade Secrets
Employees are banned from sending and transmitting or distributing other private
information of the organization, but there is an exception for certain authorized individual. If an
employee shares those banned information, it is taken as a disciplinary action or criminal penalty
under the “Economic Espionage laws”.
PC Resources
Make sure safety, so employees using setup via a PC connected through the
organization’s setup should compulsory switch on the firewall or other security software from
computer. Organizations restrict network connector devices like modem which belongs to
employees.
Frivolous Use
5
and inappropriate materials. It avoids some unwanted pages and materials. It provides internet
connection to company.
Use of Internet and Company Computer Network
It uses legitimate business purposes and it provides computer network jobs. It allows
internet through the computer network. It includes possible termination and criminal liability. It
uses company’s PC properties, internet, legal and moral mode.
PC Setup Usage Boundaries
Forbidden Usage
In the organization, previously the printed agreement was lagging, an organization’s PC
setup did not distribute, vision or collection personal and profitable information like virus, self-
replicating programs and political materials. Employees should not download games and
entertaining software using organization’s networks. Employee’s should not store or send
computer network materials through email or chat room. If employee is encountered doing such
things, the materials will alert their supervisor instantly.
Illegal Copying
People should not copy or make duplicate of protected material illegally. People are
responsible for making copyright law and apply license for software, graphics, message and
documents. Other thing user can download or copy it easily. User can download the file easily
which is a license free version.
Communication of Trade Secrets
Employees are banned from sending and transmitting or distributing other private
information of the organization, but there is an exception for certain authorized individual. If an
employee shares those banned information, it is taken as a disciplinary action or criminal penalty
under the “Economic Espionage laws”.
PC Resources
Make sure safety, so employees using setup via a PC connected through the
organization’s setup should compulsory switch on the firewall or other security software from
computer. Organizations restrict network connector devices like modem which belongs to
employees.
Frivolous Use
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

An organization provides limited resources. Network bandwidth and system storage
capacity are limited. Networks have responsibility to keep those resources. Some range of
resources are allocated to each employee, if employees are over using the resources then it will
notify the same to the network administrator.
Anticipation of Secrecy
Each organization provides computer and internet access to employees for improving the
presentation of their jobs. Workers would not take any secrecy to send, make or save any
information using organization’s equipment.
Relinquishment of Secrecy Privileges
Consumer particularly surrenders to claim some privileges of secrecy like share, save,
and make by organization’s tools. The users agree to allow organizations personal access, where
the materials created, shared or are saved through employee via any computer networks
otherwise through a setup construction.
Watching PC Setup Usage.
An organization has rights toward monitoring the computers including internet sites that
are visited by the employees. Monitoring employee activities like downloads newsgroup and
chat.
Delaying Places by Unsuitable Information
An organization takes rights toward using the software for identifying the employee’s
activity and blocks the internet access of particular employees.
Strategies Happening Worm Protection Events
The following events are recommended for stopping the worm difficulties:
Continuously track the organization’s rules and reinforce worm protection software
which is obtainable in the company websites. Take that software then track the latest
types.
NEVER open unknown or unauthorized source in company’s system. If macros files or
any other files are opened just close it immediately.
Delete junk file and spam and chain from Emails do not have promoting with the
Hospital’s message rule.
Never transfer records from unidentified, unauthorized websites and sources.
Avoid disk sharing with Read/Write rights directly.
6
capacity are limited. Networks have responsibility to keep those resources. Some range of
resources are allocated to each employee, if employees are over using the resources then it will
notify the same to the network administrator.
Anticipation of Secrecy
Each organization provides computer and internet access to employees for improving the
presentation of their jobs. Workers would not take any secrecy to send, make or save any
information using organization’s equipment.
Relinquishment of Secrecy Privileges
Consumer particularly surrenders to claim some privileges of secrecy like share, save,
and make by organization’s tools. The users agree to allow organizations personal access, where
the materials created, shared or are saved through employee via any computer networks
otherwise through a setup construction.
Watching PC Setup Usage.
An organization has rights toward monitoring the computers including internet sites that
are visited by the employees. Monitoring employee activities like downloads newsgroup and
chat.
Delaying Places by Unsuitable Information
An organization takes rights toward using the software for identifying the employee’s
activity and blocks the internet access of particular employees.
Strategies Happening Worm Protection Events
The following events are recommended for stopping the worm difficulties:
Continuously track the organization’s rules and reinforce worm protection software
which is obtainable in the company websites. Take that software then track the latest
types.
NEVER open unknown or unauthorized source in company’s system. If macros files or
any other files are opened just close it immediately.
Delete junk file and spam and chain from Emails do not have promoting with the
Hospital’s message rule.
Never transfer records from unidentified, unauthorized websites and sources.
Avoid disk sharing with Read/Write rights directly.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Before using floppy disk from unknown source, ensure to scan always. After scanning
the disk employee can use it.
In regular basis, backup the critical information and system configuration files. Finally,
keep this in a safe location.
Doubt laboratory challenging differences with virus protection software, then track the
virus protection software and clean the machine or system. After that, stop the software
and perform the lab test. Permit virus protection software to function. If virus protection
software is not permitted, don’t run any applications. Because, it can transfer virus into
the system (Example: File sharing and Email).
Latest viruses are noticed in each diurnal. Check the Laboratory virus protection rule
regularly, then update the advised process.
Message Rule in Wireless
Outline
The determination of wireless communication rule stands to keep the data resources that
belong to the company. The company offers computers, nets then additional electric data system
toward see assignments, initiatives and its goals. This permits admission toward properties
upholds the privacy, honesty and obtainability of information. WC rule includes that the
circumstances of wireless substructure device should convince to join to the company.
Possibility
In the company, all the employees, consultants, temporary workers and contractors and
third party groups are connected, with a Wireless Infrastructure device and holds on this
Wireless Communication rule. The rule smears to every Wireless Substructure plans connected
in this l network. This network includes all types of wireless communication devices like cellular
phones, PDA, and desktops that are able to transfer the data packets.
Rule Statement
General Network Access Requirements
Every wireless device infrastructure devices located in company site and for providing
internet access company must deny the following:
1) An approved supported team must install and maintain the system.
2) Apply hospital accepted authentication protocols and infrastructure.
3) Apply encryption protocols which are approved by the company.
7
the disk employee can use it.
In regular basis, backup the critical information and system configuration files. Finally,
keep this in a safe location.
Doubt laboratory challenging differences with virus protection software, then track the
virus protection software and clean the machine or system. After that, stop the software
and perform the lab test. Permit virus protection software to function. If virus protection
software is not permitted, don’t run any applications. Because, it can transfer virus into
the system (Example: File sharing and Email).
Latest viruses are noticed in each diurnal. Check the Laboratory virus protection rule
regularly, then update the advised process.
Message Rule in Wireless
Outline
The determination of wireless communication rule stands to keep the data resources that
belong to the company. The company offers computers, nets then additional electric data system
toward see assignments, initiatives and its goals. This permits admission toward properties
upholds the privacy, honesty and obtainability of information. WC rule includes that the
circumstances of wireless substructure device should convince to join to the company.
Possibility
In the company, all the employees, consultants, temporary workers and contractors and
third party groups are connected, with a Wireless Infrastructure device and holds on this
Wireless Communication rule. The rule smears to every Wireless Substructure plans connected
in this l network. This network includes all types of wireless communication devices like cellular
phones, PDA, and desktops that are able to transfer the data packets.
Rule Statement
General Network Access Requirements
Every wireless device infrastructure devices located in company site and for providing
internet access company must deny the following:
1) An approved supported team must install and maintain the system.
2) Apply hospital accepted authentication protocols and infrastructure.
3) Apply encryption protocols which are approved by the company.
7

4) Manage MAC address of the devices for tracking.
Home Wireless Device Requirements
WI devices offers direct connection to the business network, and must match with the
home wireless devices requirements. WI device is not successful to follow the home-based
wireless scheme. So, it should be located in ways that provide straight connection toward the
business network.
Enforcement
A worker originates to break this rule, as it might be issued to punitive act and comprises
activation of worker. Abusing this rule through a short term employer, servicer will lose their
contract with the company.
Definitions
Company Network: Company network is a network that can be either wired or wireless
network, including interior, and the outside setups offer internet toward business facilities.
Business Construction: A construction gives admission toward the company setup.
Data Benefits: Data is met and generated from the fundamental hardware, software, facilities,
schemes, and knowledge. It is used for gaining, saving, spending, and safeguarding the
information and it identified to be significant and helpful for the group.
Physical Address – The physical address like the hardware address, it uses unique identification
of the devices.
3.1 Security Policies
The Company provides the huge range of information assert like systems, interconnected
nodes with regional connection, groupware databases and wireless devices for the normal usage
of the assists working there. All of these asserts are monitored by the administrative sector who
carry out the appropriate trade of the office related jobs in the care center. Legitimate trading of
the computerized resources includes scientific work and office related jobs. In acceptance with
the world wide range which provides interaction between the different facilities provided through
out. It manages the same way on the new technology. It is hard to believe that technology takes
care of all the amount of work carried out like taking care of databases and security of stored
data. The guidelines being followed by the system should be appropriate and the needs should be
satisfactory (Iyengar, 2011).
User Access
8
Home Wireless Device Requirements
WI devices offers direct connection to the business network, and must match with the
home wireless devices requirements. WI device is not successful to follow the home-based
wireless scheme. So, it should be located in ways that provide straight connection toward the
business network.
Enforcement
A worker originates to break this rule, as it might be issued to punitive act and comprises
activation of worker. Abusing this rule through a short term employer, servicer will lose their
contract with the company.
Definitions
Company Network: Company network is a network that can be either wired or wireless
network, including interior, and the outside setups offer internet toward business facilities.
Business Construction: A construction gives admission toward the company setup.
Data Benefits: Data is met and generated from the fundamental hardware, software, facilities,
schemes, and knowledge. It is used for gaining, saving, spending, and safeguarding the
information and it identified to be significant and helpful for the group.
Physical Address – The physical address like the hardware address, it uses unique identification
of the devices.
3.1 Security Policies
The Company provides the huge range of information assert like systems, interconnected
nodes with regional connection, groupware databases and wireless devices for the normal usage
of the assists working there. All of these asserts are monitored by the administrative sector who
carry out the appropriate trade of the office related jobs in the care center. Legitimate trading of
the computerized resources includes scientific work and office related jobs. In acceptance with
the world wide range which provides interaction between the different facilities provided through
out. It manages the same way on the new technology. It is hard to believe that technology takes
care of all the amount of work carried out like taking care of databases and security of stored
data. The guidelines being followed by the system should be appropriate and the needs should be
satisfactory (Iyengar, 2011).
User Access
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The authorized users have all the rights to access the profiles from any units of Company.
The overview about this is to tell people about the new technologies being introduced. All these
resources of the center should be connected locally. This is one of most important policy.
Account Management
Few conditions are to be followed like only official account can be operated and no one
can do any type of editing in the particular files. Any electronic devices used by the staffs are
prohibited to stop the sting operations and it may also lead to degrade the name and fame of the
center. They should prohibit the excessive use of data from the organization (Sá Silva,
Krishnamachari & Boavida, 2010).
Identifying Protocols
The unique identification number will be generated and handed over to the staff, so that
only they can access it which comes under the facilities of the center. To maintain the password
follow the normal b asic rules like strong alphanumeric and symbols. At any condition, it should
not be exchanged through mails to anyone.
Interconnected Nodes
The regional field connection is established for the care center in such a way that all the
sectors interact within itself. For the higher securities make sure that personal devices are not
used for interacting with the management staffs.
Device Authorization
All the electronic devices being used should be authorized with legal contracts, licenses
and notices. Firewall is a groupware which provides high security inside the care center systems
and reduces the traffic and keeps track of all the connected nodes.
Firewall for Precaution
Always check the authorities for any alteration of data and stay updated.
Should be able to differentiate between the authorized and unauthorized connection on
the nodes.
Block the unwanted traffic while accessing the signals and hide the system’s names.
Inscription
Inscription is mainly done in order to encode the data into an unknown sequence so that it
is not utilized by anyone to decrease the name and fame of the CWM healthcare center.
9
The overview about this is to tell people about the new technologies being introduced. All these
resources of the center should be connected locally. This is one of most important policy.
Account Management
Few conditions are to be followed like only official account can be operated and no one
can do any type of editing in the particular files. Any electronic devices used by the staffs are
prohibited to stop the sting operations and it may also lead to degrade the name and fame of the
center. They should prohibit the excessive use of data from the organization (Sá Silva,
Krishnamachari & Boavida, 2010).
Identifying Protocols
The unique identification number will be generated and handed over to the staff, so that
only they can access it which comes under the facilities of the center. To maintain the password
follow the normal b asic rules like strong alphanumeric and symbols. At any condition, it should
not be exchanged through mails to anyone.
Interconnected Nodes
The regional field connection is established for the care center in such a way that all the
sectors interact within itself. For the higher securities make sure that personal devices are not
used for interacting with the management staffs.
Device Authorization
All the electronic devices being used should be authorized with legal contracts, licenses
and notices. Firewall is a groupware which provides high security inside the care center systems
and reduces the traffic and keeps track of all the connected nodes.
Firewall for Precaution
Always check the authorities for any alteration of data and stay updated.
Should be able to differentiate between the authorized and unauthorized connection on
the nodes.
Block the unwanted traffic while accessing the signals and hide the system’s names.
Inscription
Inscription is mainly done in order to encode the data into an unknown sequence so that it
is not utilized by anyone to decrease the name and fame of the CWM healthcare center.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

It is necessary to check the encrypted keys every now and then so that the intruder do not
make any kind of changes. The management should see that the secret keys are not
altered.
Each individual is responsible if any problem occurs.
Chunk Path
Almost all the files saved here can be used only for limited a purpose, after which it gets
expired. So all the old data which is not needed for the center will get deleted after the required
time period.
Uncertainty Estimation
Uncertainty is actually analytical and delicate to handle various resources. It may cause
problems in tracking the visual and interactive data which may lead to face loss of honesty from
the company. As a whole reliability is lost between the Company and employee. Thus,
assessment center should exist, who looks after the corresponding data. A group of people looks
after this problem and immediately answers if any complaints are made based on the Company
Regulatory Administrator
Once the websites beings to run, then the admin should know what type of malicious
groupware may affect the sites in different aspects. Thus, SSM may have separate login page
where authorities can post the details if any malfunction occurs. As a result, immediately
previous list will be checked and made sure that what type of changes are required. It should also
verify that the staffs who are using the sites are verified or not. So that, it will check the relevant
Email IDs, and corresponding passwords or the related birthdays.
Liability
Educating the staffs about the usage of their own credentials to login into the page.
It is always necessary to inform the staff about the new techniques involved.
Make sure that none of the staff share SSM's credentials to any outsider, which may lead
to future problems.
Instruct the staff to keep changing their password often, so that no one can make any
changes, especially if they think something is unusual in the login page.
Also tell them to correctly login to the page and then logout.
Event Broadcasting
10
make any kind of changes. The management should see that the secret keys are not
altered.
Each individual is responsible if any problem occurs.
Chunk Path
Almost all the files saved here can be used only for limited a purpose, after which it gets
expired. So all the old data which is not needed for the center will get deleted after the required
time period.
Uncertainty Estimation
Uncertainty is actually analytical and delicate to handle various resources. It may cause
problems in tracking the visual and interactive data which may lead to face loss of honesty from
the company. As a whole reliability is lost between the Company and employee. Thus,
assessment center should exist, who looks after the corresponding data. A group of people looks
after this problem and immediately answers if any complaints are made based on the Company
Regulatory Administrator
Once the websites beings to run, then the admin should know what type of malicious
groupware may affect the sites in different aspects. Thus, SSM may have separate login page
where authorities can post the details if any malfunction occurs. As a result, immediately
previous list will be checked and made sure that what type of changes are required. It should also
verify that the staffs who are using the sites are verified or not. So that, it will check the relevant
Email IDs, and corresponding passwords or the related birthdays.
Liability
Educating the staffs about the usage of their own credentials to login into the page.
It is always necessary to inform the staff about the new techniques involved.
Make sure that none of the staff share SSM's credentials to any outsider, which may lead
to future problems.
Instruct the staff to keep changing their password often, so that no one can make any
changes, especially if they think something is unusual in the login page.
Also tell them to correctly login to the page and then logout.
Event Broadcasting
10

One who is the administrator of the page keeps the record of all the breaches, spam and any
other unrelated things happening on to the site. Each sector should have its own security so that
they supervise their own work. If any such thing happens, then make sure that new ideas are
generated in which suspecting the files will be very easy and is helpful for the main
administrator. Thus, if any unusual thing happens, immediately it can be notified and corrected
from where it is generated.
Certification
Only if the technical sites and the scheme provided are satisfied, the SSM Company will
be awarded with good support and ethics. All the new technologies being used should be correct
to use and authorize. Anyone using the heavy equipment should have experience to use it, in the
specified connection. All outdated products should be replaced.
Wi-Fi Surveillance
Wireless connection is used in order to build the care center local field connection strong
enough to continue the services as long as possible. It contains the certification of the wireless
technologies being used in the center and the admin keeps track of the signal’s bandwidth.
Anyone who is using this facilities should make sure that all the give guidelines should be
strictly followed. Any devices used for personal usage and intentionally misused are strictly not
allowed. It should satisfy the rules belonging from all the states. As the internet services are
provided, it is must to ask the authentication number for permission to use it. The internet
protocol address should be encrypted so that no one can easily obtain it and miss use it. The
connection should be established in such a way that new technology equipment can easily be
connected. Since the connection is divided, if any part displays some uncertain data, then
immediately it should be eradicated from the server.
Negligence and Prosecution
If any staff is committing any unusual thing then the access will be denied for the
temporary purposes as per the mistake being committed. An additional payment can be asked to
be given as a penalty and all the authorized rights can be banned. Provided facilitates would be
stopped completely and it should be made sure that in future all the data are not let out to anyone.
Thus, if anything leads to decreasing the fame of healthcare center, then the organization may
also take extreme step, for the legal violations of the norms.
11
other unrelated things happening on to the site. Each sector should have its own security so that
they supervise their own work. If any such thing happens, then make sure that new ideas are
generated in which suspecting the files will be very easy and is helpful for the main
administrator. Thus, if any unusual thing happens, immediately it can be notified and corrected
from where it is generated.
Certification
Only if the technical sites and the scheme provided are satisfied, the SSM Company will
be awarded with good support and ethics. All the new technologies being used should be correct
to use and authorize. Anyone using the heavy equipment should have experience to use it, in the
specified connection. All outdated products should be replaced.
Wi-Fi Surveillance
Wireless connection is used in order to build the care center local field connection strong
enough to continue the services as long as possible. It contains the certification of the wireless
technologies being used in the center and the admin keeps track of the signal’s bandwidth.
Anyone who is using this facilities should make sure that all the give guidelines should be
strictly followed. Any devices used for personal usage and intentionally misused are strictly not
allowed. It should satisfy the rules belonging from all the states. As the internet services are
provided, it is must to ask the authentication number for permission to use it. The internet
protocol address should be encrypted so that no one can easily obtain it and miss use it. The
connection should be established in such a way that new technology equipment can easily be
connected. Since the connection is divided, if any part displays some uncertain data, then
immediately it should be eradicated from the server.
Negligence and Prosecution
If any staff is committing any unusual thing then the access will be denied for the
temporary purposes as per the mistake being committed. An additional payment can be asked to
be given as a penalty and all the authorized rights can be banned. Provided facilitates would be
stopped completely and it should be made sure that in future all the data are not let out to anyone.
Thus, if anything leads to decreasing the fame of healthcare center, then the organization may
also take extreme step, for the legal violations of the norms.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 66
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




