DAS and SaaS: Security, Privacy in Shared Service Implementation
VerifiedAdded on 2022/11/18
|20
|1852
|194
Report
AI Summary
This report evaluates the Department of Administrative Services (DAS) in Australia's transition to a shared service model using SaaS solutions. It examines the security threats and contingency plans before and after SaaS implementation, focusing on risks like password loss, phishing, and unauthorized installations. The report assesses how SaaS impacts the security posture of DAS, addressing issues such as immature identification management, weak cloud infrastructure, and data security. It further explores the severity of risks to employee data, discussing how the operational solution and its location mitigate or increase threats to security and privacy. The report identifies new privacy threats post-implementation, including data breaches and software misconfiguration, and concludes by discussing data sensitivity issues, particularly employee data privacy, in relation to the chosen SaaS solution. Desklib provides access to this and other solved assignments to aid students in their studies.

DAS AND SHARED
SERVICE
APPROACH
SERVICE
APPROACH
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction:
The report aims in discussing and evaluating the case study
scenario of the the Department of Administrative Services (DAS) in
Australia, where it delivers several services to the departments
that are undertaken by the Australian Government. The main
service that is been delivered by them comprises of HR and
personal management, contract tendering, payroll, contractor
management and procurement. The services are dependent on the
data centers of the DAS department (Rittinghouse & Ransome,
2017).
According to the revised policy change that has been done by the
Australian government, the department working under the system
is forced to come down under the shared Service system.
According to the specific system, all the services under the
government that are looked at after by the DAS are commanded to
get combined under one centralized system under the government.
The report aims in discussing and evaluating the case study
scenario of the the Department of Administrative Services (DAS) in
Australia, where it delivers several services to the departments
that are undertaken by the Australian Government. The main
service that is been delivered by them comprises of HR and
personal management, contract tendering, payroll, contractor
management and procurement. The services are dependent on the
data centers of the DAS department (Rittinghouse & Ransome,
2017).
According to the revised policy change that has been done by the
Australian government, the department working under the system
is forced to come down under the shared Service system.
According to the specific system, all the services under the
government that are looked at after by the DAS are commanded to
get combined under one centralized system under the government.

For achieving the motive of centralizing the system under one unit, the
government has declared and suggested the implementation of the new
approach which is known as the CLOUD FIRST process. The changes that
need to be done by the governmental organization needs the assistance of
the SAAS solution and implementation t5hat has been discussed to be
bought form a US undertaking company.
The previous report where the development procedure and the utilization
factors of the SaaS technology for the management of the HR personal
within the DAS infrastructure has been stated, it has been evaluated that
the implementation of the SaaS technology was one of the vital process
that has been used for achieving the desired outcome (Lewandowski,
Salako & Garcia-Perez, 2013).
The SaaS Solutions is known as the Software as a Security solution. It
deals with the type of the model which develops the applications or
software for the security implementation of the organization . This is
developed by a third party who creates and hosts the software applications
which is available to tne users in a form of online web browser page.
government has declared and suggested the implementation of the new
approach which is known as the CLOUD FIRST process. The changes that
need to be done by the governmental organization needs the assistance of
the SAAS solution and implementation t5hat has been discussed to be
bought form a US undertaking company.
The previous report where the development procedure and the utilization
factors of the SaaS technology for the management of the HR personal
within the DAS infrastructure has been stated, it has been evaluated that
the implementation of the SaaS technology was one of the vital process
that has been used for achieving the desired outcome (Lewandowski,
Salako & Garcia-Perez, 2013).
The SaaS Solutions is known as the Software as a Security solution. It
deals with the type of the model which develops the applications or
software for the security implementation of the organization . This is
developed by a third party who creates and hosts the software applications
which is available to tne users in a form of online web browser page.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY THREATS AND THE
CONTINGENCY PLANS BEFORE THE
IMPLEMENTATION OF SAAS:
Password loosing risk by employees: This has a
Very High Likelihood along with Very High
Impact and the priority has been set Very High.
The preventing Actions are Implementation of
SaaS technology (Bildosola et al., 2015).
Security threats caused by emails: This has a
High likelihood and High impact which has a
High priority. The preventive measures
comprise of allocation of efficient access
controls on the emails.
CONTINGENCY PLANS BEFORE THE
IMPLEMENTATION OF SAAS:
Password loosing risk by employees: This has a
Very High Likelihood along with Very High
Impact and the priority has been set Very High.
The preventing Actions are Implementation of
SaaS technology (Bildosola et al., 2015).
Security threats caused by emails: This has a
High likelihood and High impact which has a
High priority. The preventive measures
comprise of allocation of efficient access
controls on the emails.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Unauthenticated connection risks: This has Medium likelihood to
happen with a medium range of impact and a very high priority
standard for the mitigation of the problem. Implementing SaaS
technology to keep observation on the practice of
unauthenticated connections is the preventive measure for the
problem (Alkalbani et al., 2015 ).
PHISHING risk: this has very high likelihood of happening with a
Very High range of impact and a very high priority standard for
the mitigation of the problem. Again the implementation of the
SaaS technology can be the preventive measure for the problem.
Unauthorized installation of applications: this has medium
likelihood of happening with a medium range of impact and a
high priority standard. The implementation of the SaaS
technology can be the preventive measure for the problem.
happen with a medium range of impact and a very high priority
standard for the mitigation of the problem. Implementing SaaS
technology to keep observation on the practice of
unauthenticated connections is the preventive measure for the
problem (Alkalbani et al., 2015 ).
PHISHING risk: this has very high likelihood of happening with a
Very High range of impact and a very high priority standard for
the mitigation of the problem. Again the implementation of the
SaaS technology can be the preventive measure for the problem.
Unauthorized installation of applications: this has medium
likelihood of happening with a medium range of impact and a
high priority standard. The implementation of the SaaS
technology can be the preventive measure for the problem.

THE OPERATIONAL SOLUTION USING AN SAAS
APPLICATION, AND THE LOCATION(S) OF THE
SAAS PROVIDER FOR HR MANAGEMENT MAY
AFFECT THE SECURITY POSTURE OF DAS.
Security posture of an organization refers to the
strengths or the overall strengths of the cyber security
attributes of the organization of the department.
The security posture of the DAS has been affected in
both positive and negative aspects as the security
posture refers to the relative security of the firm
especially when it is data centric and has implemented
the SaaS technology for the CLOUD FIRST technology.
APPLICATION, AND THE LOCATION(S) OF THE
SAAS PROVIDER FOR HR MANAGEMENT MAY
AFFECT THE SECURITY POSTURE OF DAS.
Security posture of an organization refers to the
strengths or the overall strengths of the cyber security
attributes of the organization of the department.
The security posture of the DAS has been affected in
both positive and negative aspects as the security
posture refers to the relative security of the firm
especially when it is data centric and has implemented
the SaaS technology for the CLOUD FIRST technology.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Operational solution using SaaS application affects
the security posture:
Immature identification management: This has
Medium likelihood assessed by the organization or
the organization that has implemented in the
solution in the DAS. The impact that has been
recorded is high and the priority is also kept high.
Weak cloud infrastructure: This has High likelihood
assessed by the organization that has implemented
in the solution in the DAS. The impact that has been
recorded is Very High and the priority is also kept
high.
the security posture:
Immature identification management: This has
Medium likelihood assessed by the organization or
the organization that has implemented in the
solution in the DAS. The impact that has been
recorded is high and the priority is also kept high.
Weak cloud infrastructure: This has High likelihood
assessed by the organization that has implemented
in the solution in the DAS. The impact that has been
recorded is Very High and the priority is also kept
high.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Data security issues: this has very high
likelihood of happening with a Very High range
of impact and high priority standard for the
mitigation of the problem. The security issues
regarding the software for the cloud has been
implemented by the DAS
Risky access from everywhere: this has very
high likelihood of happening with a High range
of impact and high priority standard. The DFAS
vcan implement Cisco Web Gateway
appliances.
likelihood of happening with a Very High range
of impact and high priority standard for the
mitigation of the problem. The security issues
regarding the software for the cloud has been
implemented by the DAS
Risky access from everywhere: this has very
high likelihood of happening with a High range
of impact and high priority standard. The DFAS
vcan implement Cisco Web Gateway
appliances.

Unknown data location: this has very high likelihood of
happening with a High range of impact and high priority
standard has been set by the organization. The DAS can
execute the Google Apps specialized by FISMA. Therefore,
the implementation of the data can be completed.
Data logging and monitoring lack: this has Low likelihood
of happening with a Low range of impact and high priority
standard has been set by the organization. The
management of logging and checking of employees needs
to be implemented by DAS (Tiwari, Kumar & Mishra,
2013). The major issue that has been put in the
contingency plan comprises of the data safety which is the
major issue.
happening with a High range of impact and high priority
standard has been set by the organization. The DAS can
execute the Google Apps specialized by FISMA. Therefore,
the implementation of the data can be completed.
Data logging and monitoring lack: this has Low likelihood
of happening with a Low range of impact and high priority
standard has been set by the organization. The
management of logging and checking of employees needs
to be implemented by DAS (Tiwari, Kumar & Mishra,
2013). The major issue that has been put in the
contingency plan comprises of the data safety which is the
major issue.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
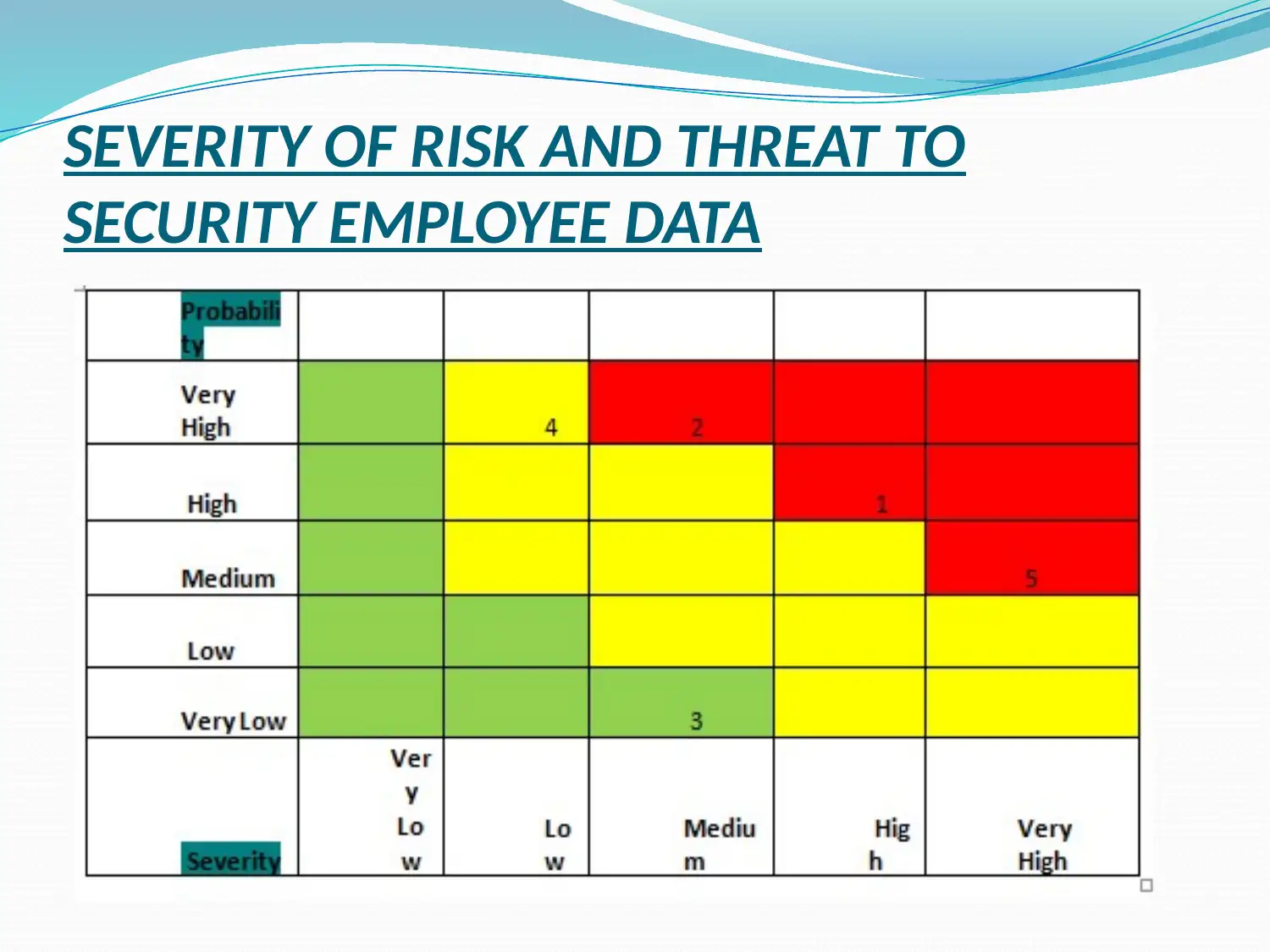
SEVERITY OF RISK AND THREAT TO
SECURITY EMPLOYEE DATA
SECURITY EMPLOYEE DATA
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

EXPLAIN IF EITHER THE OPERATIONAL SOLUTION, OR THE
OPERATIONAL LOCATION(S), OR BOTH, INCREASE OR MITIGATE
THE THREATS AND RISKS IDENTIFIED FOR THE SECURITY AND
PRIVACY OF EMPLOYEE DATA?
The threats that were identified before the application of
the new operational solution or operational location or both
which is the implementation of the SaaS technology in the
DAS systems regarding the privacy of employee data were
mitigated by the implementation of the new technology.
The threats that existed in the old model were the,
Requirement of internet connectivity with high speed,
Freedom loss of the employee, Security and control of data,
Lack of software control of the employees and Lack of idea
of employees of software version. All the threats were
mitigated. However, after the implementation of the SaaS
system new threats to the employee data security were
found.
OPERATIONAL LOCATION(S), OR BOTH, INCREASE OR MITIGATE
THE THREATS AND RISKS IDENTIFIED FOR THE SECURITY AND
PRIVACY OF EMPLOYEE DATA?
The threats that were identified before the application of
the new operational solution or operational location or both
which is the implementation of the SaaS technology in the
DAS systems regarding the privacy of employee data were
mitigated by the implementation of the new technology.
The threats that existed in the old model were the,
Requirement of internet connectivity with high speed,
Freedom loss of the employee, Security and control of data,
Lack of software control of the employees and Lack of idea
of employees of software version. All the threats were
mitigated. However, after the implementation of the SaaS
system new threats to the employee data security were
found.

The new privacy threats:
Data breach: this has high likelihood of happening
with a medium range of impact and very high priority
standard has been set by the organization. The
preventive actions can be stated as, for cyber Security
suitable mechanism must be implemented and suitable
method in business data loss should be implemented.
Software miss-configuration: this has medium
likelihood of happening with a very large range of
impact and very high priority standard has been set by
the organization. The preventive actions can be
defined as implementing correct methods for avoiding
miss-configuration.
Data breach: this has high likelihood of happening
with a medium range of impact and very high priority
standard has been set by the organization. The
preventive actions can be stated as, for cyber Security
suitable mechanism must be implemented and suitable
method in business data loss should be implemented.
Software miss-configuration: this has medium
likelihood of happening with a very large range of
impact and very high priority standard has been set by
the organization. The preventive actions can be
defined as implementing correct methods for avoiding
miss-configuration.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





