Report on the Shellshock Vulnerability: Impact and Exploitation
VerifiedAdded on 2020/05/11
|4
|486
|182
Report
AI Summary
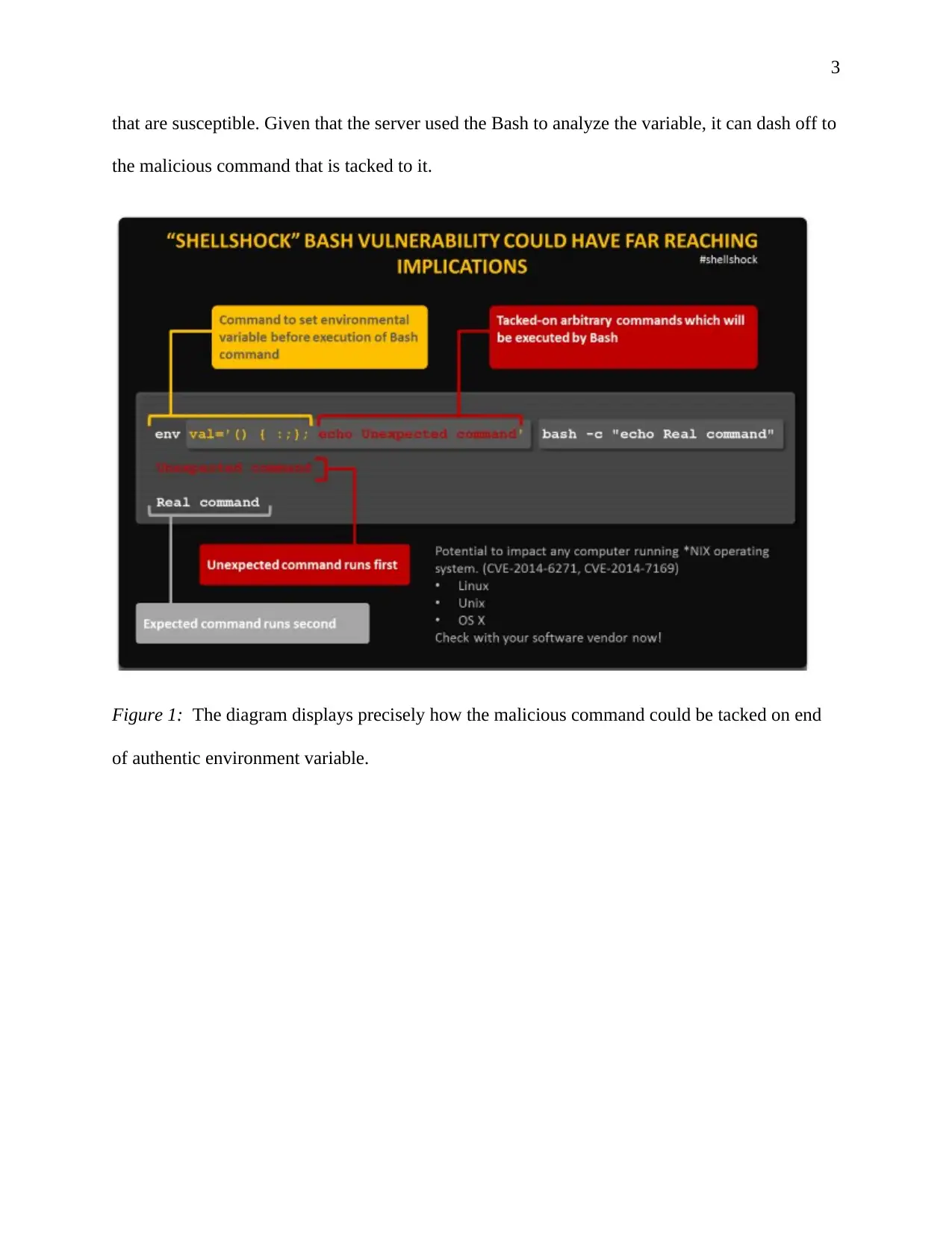
This report provides an overview of the Shellshock vulnerability, a critical security flaw affecting Linux and Unix systems, including macOS. The vulnerability impacts the bash shell, used to interpret commands. The report details the vulnerability's potential for exploitation, particularly through web servers using the Common Gateway Interface (CGI). Attackers can inject malicious commands via malformed environment variables. The report highlights the mechanisms of exploitation and emphasizes the need for security measures to mitigate the risks. References to relevant research papers are also provided to support the analysis.
1 out of 4









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)