CKIT519: Exploring SANS SIFT Tools for Forensic Analysis
VerifiedAdded on 2022/11/09
|13
|851
|96
Practical Assignment
AI Summary
This assignment details the use of SANS SIFT tools for forensic analysis on a remote Linux server. The student accessed the server via SSH and used various tools to analyze an E01 image file. The steps included mounting the image, checking operating system details, and using tools like ewfmount, vshadow, and log2timeline. Memory analysis was attempted, and registry examination was performed using tools like rip.pl, ShimCacheParser, amcache.py, reglookup, and strings. The assignment demonstrates a practical application of SIFT tools in a forensic investigation scenario, covering timeline creation, registry analysis, and data parsing to extract valuable information from the evidence file. The student successfully navigated the command-line interface and utilized the SIFT tools to extract and interpret data from the provided evidence.

SANS SIFT Tools
1
SANS SIFT TOOLS
By [Student Name]
Course name
Professor’s Name
Institution
Location of Institution
Date
1
SANS SIFT TOOLS
By [Student Name]
Course name
Professor’s Name
Institution
Location of Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SANS SIFT Tools
2
SANS SIFT Tools
The SANS SIFT tools are forensic programs that have been made available to perform
forensic analysis on various sets of images (Shrivastava, et al., 2018). It can be used both on the
Windows and Linux systems, either on a local computer or a remote server (Lucas, 2018). This
lab project required the exploration of tools that are available within the SIFT ensemble
(Altheide & Carvey, 2011).
It was required that the analysis be conducted on a remote server that has pre-installed
sift tools (Cerri, 2015). In order to begin the exercise, a successful connection to the remote
server had to be made through a secure shell.
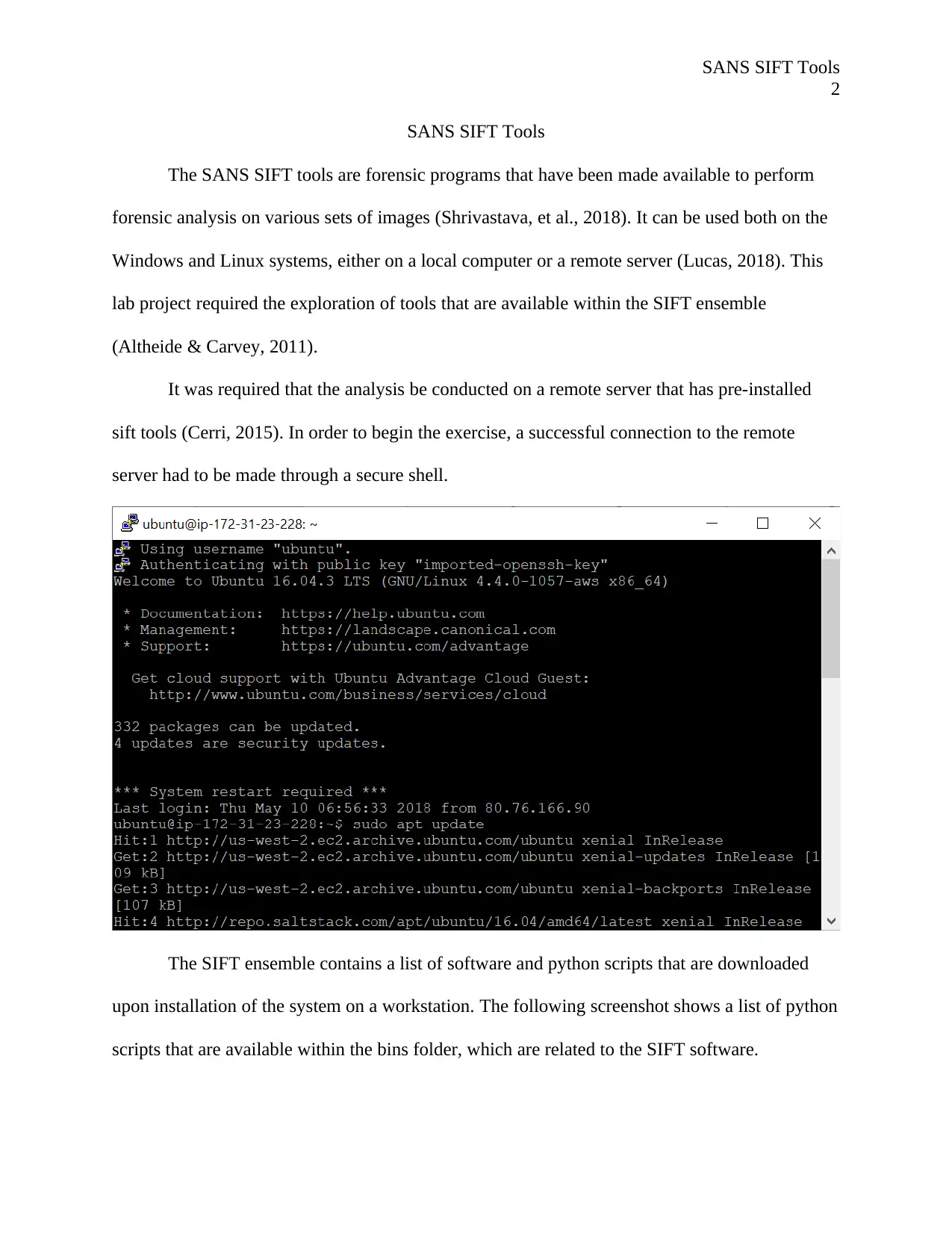
The SIFT ensemble contains a list of software and python scripts that are downloaded
upon installation of the system on a workstation. The following screenshot shows a list of python
scripts that are available within the bins folder, which are related to the SIFT software.
2
SANS SIFT Tools
The SANS SIFT tools are forensic programs that have been made available to perform
forensic analysis on various sets of images (Shrivastava, et al., 2018). It can be used both on the
Windows and Linux systems, either on a local computer or a remote server (Lucas, 2018). This
lab project required the exploration of tools that are available within the SIFT ensemble
(Altheide & Carvey, 2011).
It was required that the analysis be conducted on a remote server that has pre-installed
sift tools (Cerri, 2015). In order to begin the exercise, a successful connection to the remote
server had to be made through a secure shell.
The SIFT ensemble contains a list of software and python scripts that are downloaded
upon installation of the system on a workstation. The following screenshot shows a list of python
scripts that are available within the bins folder, which are related to the SIFT software.
SANS SIFT Tools
3
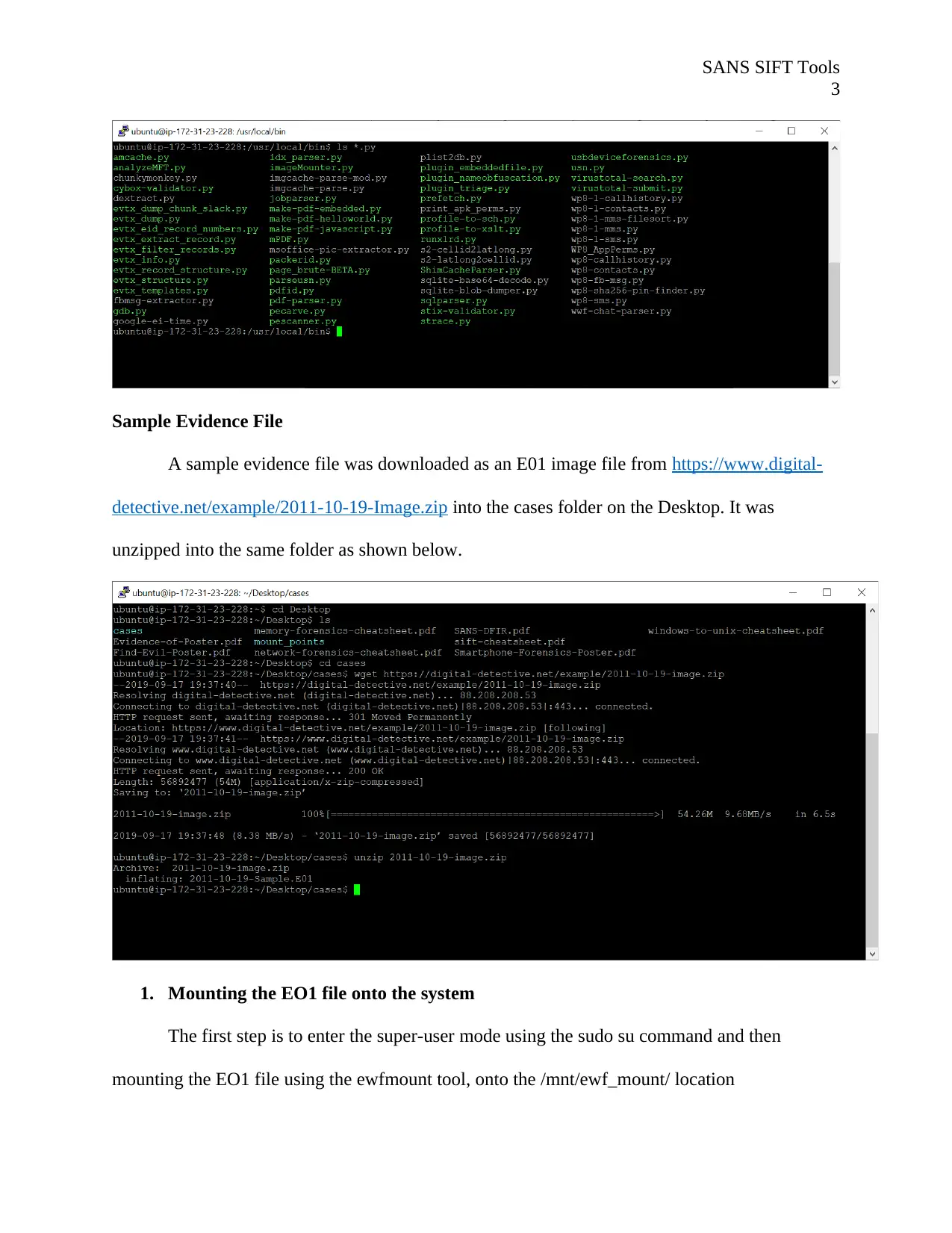
Sample Evidence File
A sample evidence file was downloaded as an E01 image file from https://www.digital-
detective.net/example/2011-10-19-Image.zip into the cases folder on the Desktop. It was
unzipped into the same folder as shown below.
1. Mounting the EO1 file onto the system
The first step is to enter the super-user mode using the sudo su command and then
mounting the EO1 file using the ewfmount tool, onto the /mnt/ewf_mount/ location
3
Sample Evidence File
A sample evidence file was downloaded as an E01 image file from https://www.digital-
detective.net/example/2011-10-19-Image.zip into the cases folder on the Desktop. It was
unzipped into the same folder as shown below.
1. Mounting the EO1 file onto the system
The first step is to enter the super-user mode using the sudo su command and then
mounting the EO1 file using the ewfmount tool, onto the /mnt/ewf_mount/ location
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
SANS SIFT Tools
4
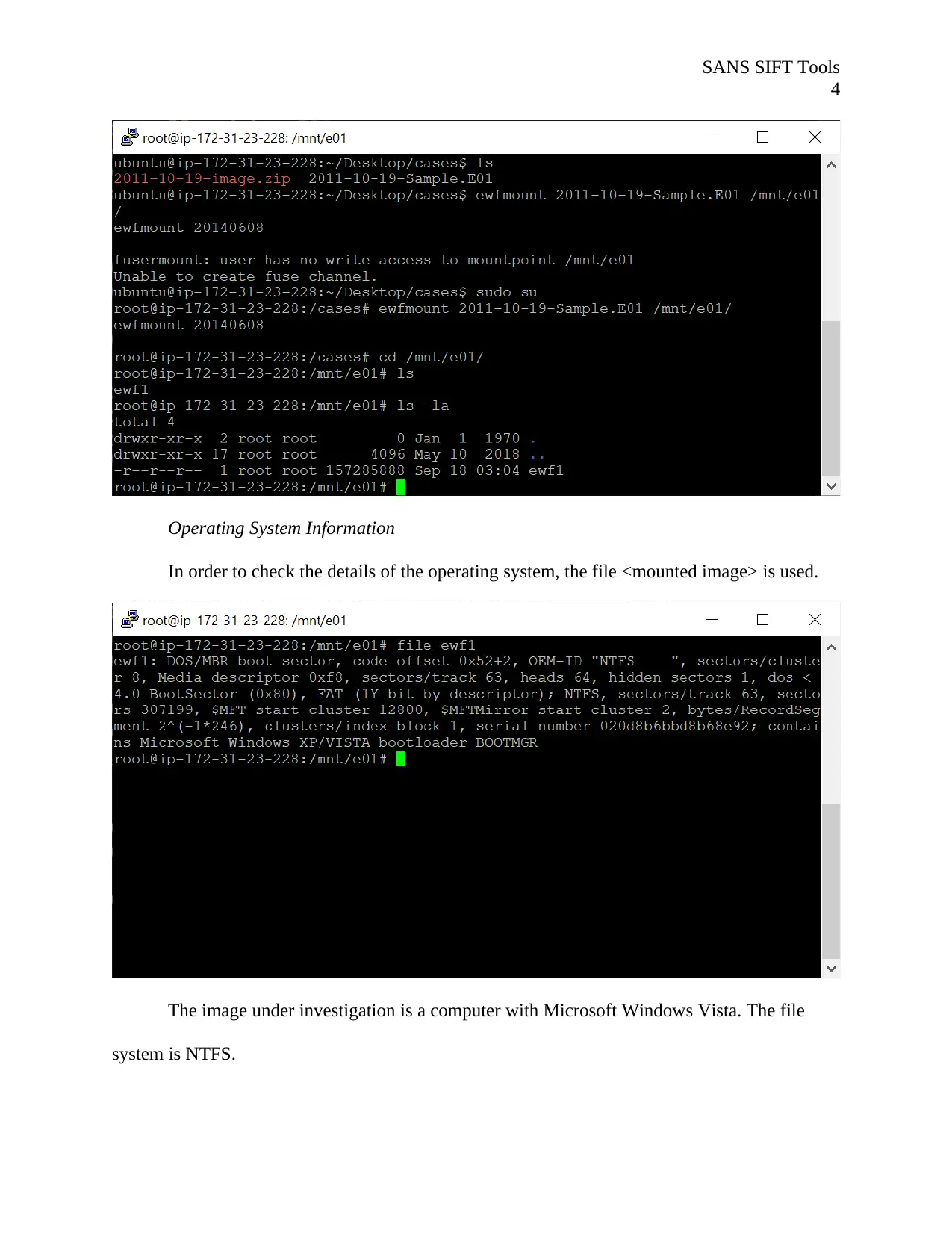
Operating System Information
In order to check the details of the operating system, the file <mounted image> is used.
The image under investigation is a computer with Microsoft Windows Vista. The file
system is NTFS.
4
Operating System Information
In order to check the details of the operating system, the file <mounted image> is used.
The image under investigation is a computer with Microsoft Windows Vista. The file
system is NTFS.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SANS SIFT Tools
5
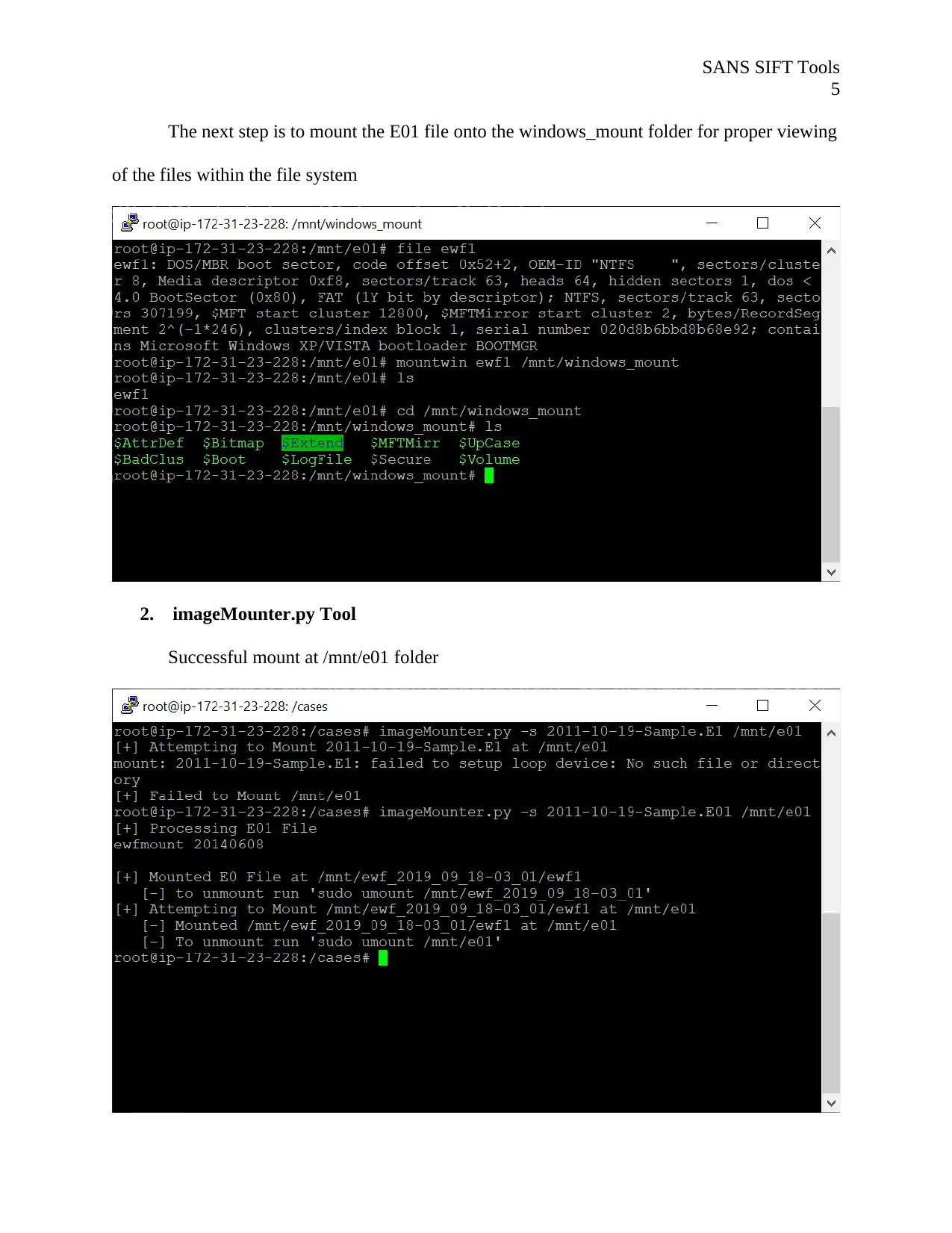
The next step is to mount the E01 file onto the windows_mount folder for proper viewing
of the files within the file system
2. imageMounter.py Tool
Successful mount at /mnt/e01 folder
5
The next step is to mount the E01 file onto the windows_mount folder for proper viewing
of the files within the file system
2. imageMounter.py Tool
Successful mount at /mnt/e01 folder
SANS SIFT Tools
6
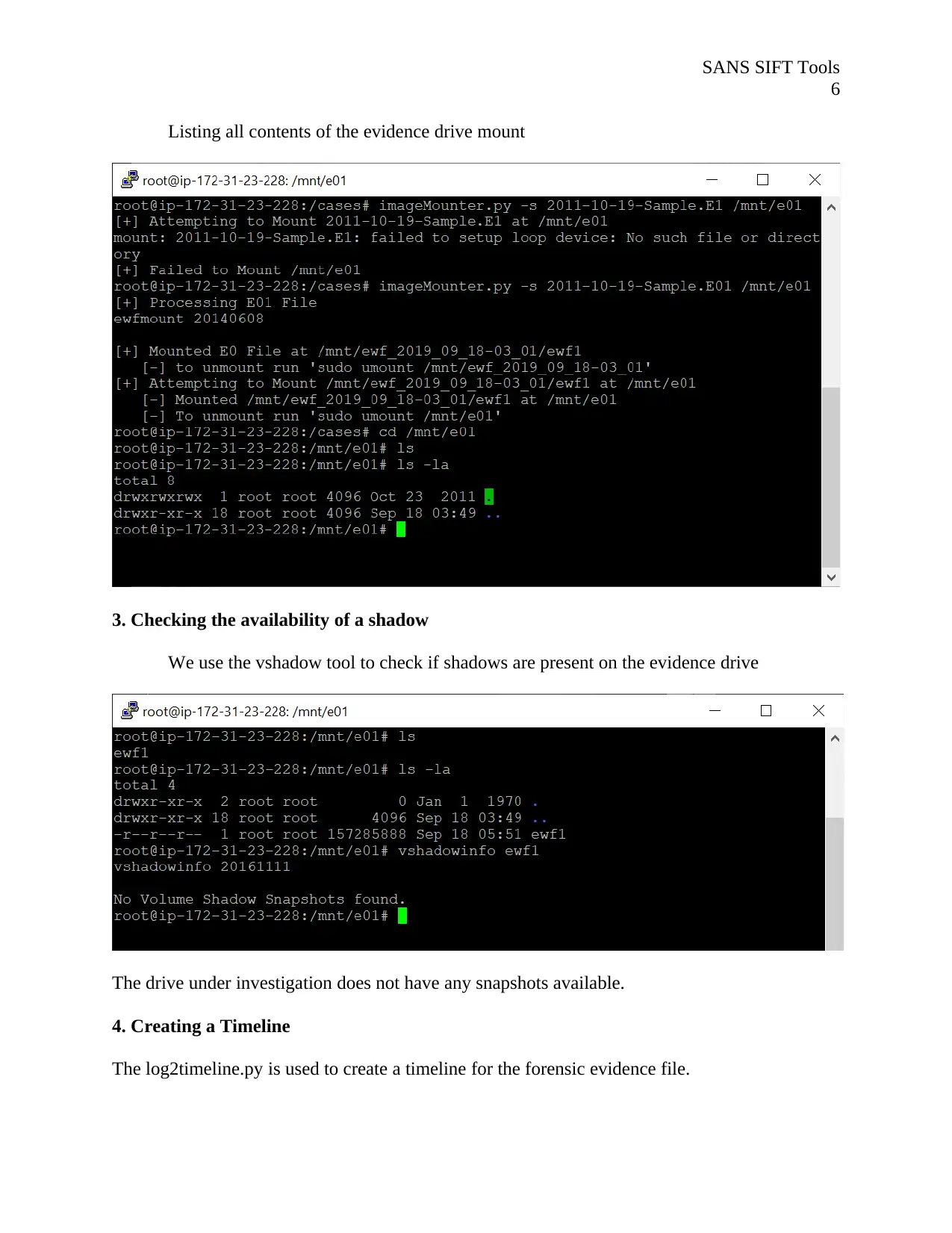
Listing all contents of the evidence drive mount
3. Checking the availability of a shadow
We use the vshadow tool to check if shadows are present on the evidence drive
The drive under investigation does not have any snapshots available.
4. Creating a Timeline
The log2timeline.py is used to create a timeline for the forensic evidence file.
6
Listing all contents of the evidence drive mount
3. Checking the availability of a shadow
We use the vshadow tool to check if shadows are present on the evidence drive
The drive under investigation does not have any snapshots available.
4. Creating a Timeline
The log2timeline.py is used to create a timeline for the forensic evidence file.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
SANS SIFT Tools
7
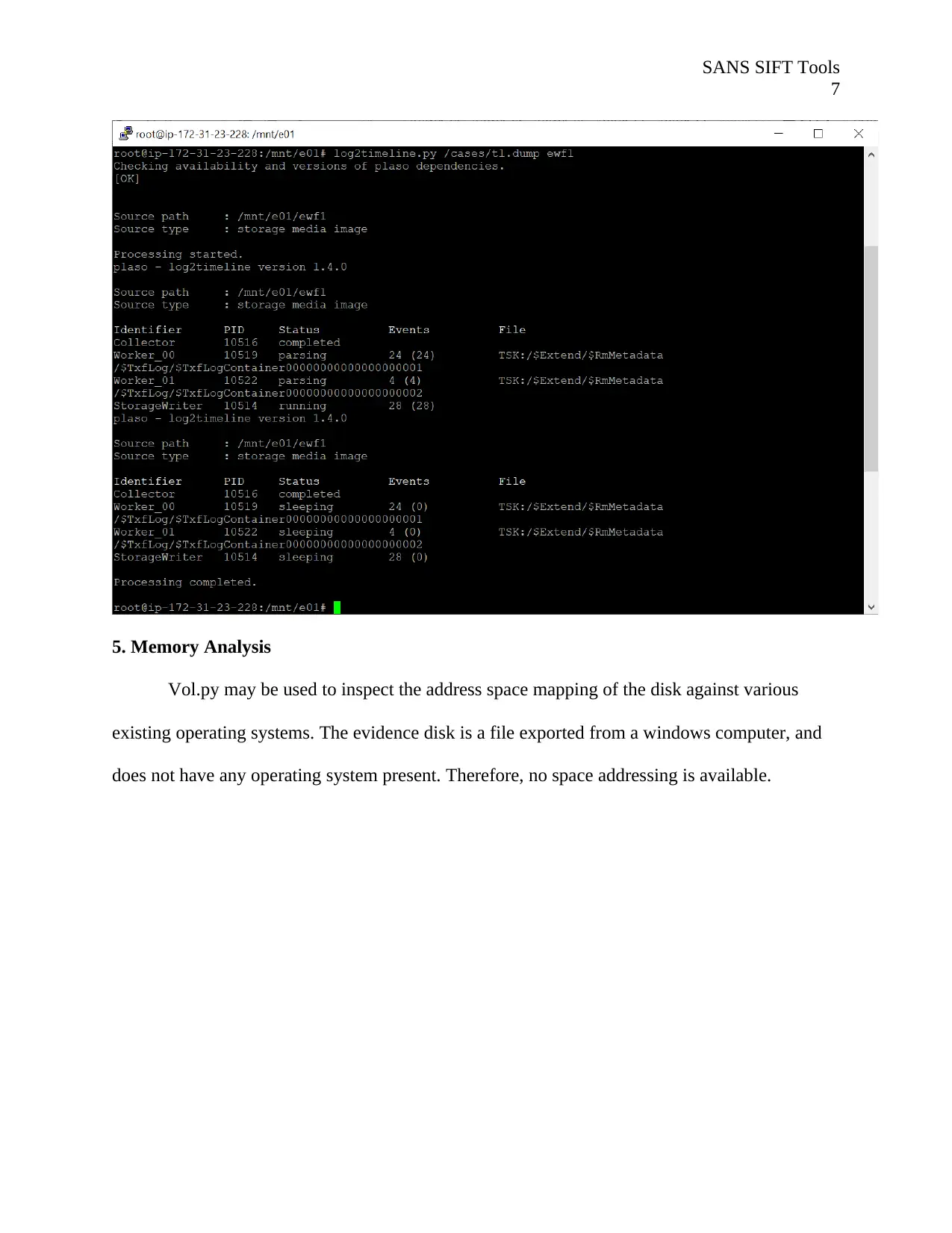
5. Memory Analysis
Vol.py may be used to inspect the address space mapping of the disk against various
existing operating systems. The evidence disk is a file exported from a windows computer, and
does not have any operating system present. Therefore, no space addressing is available.
7
5. Memory Analysis
Vol.py may be used to inspect the address space mapping of the disk against various
existing operating systems. The evidence disk is a file exported from a windows computer, and
does not have any operating system present. Therefore, no space addressing is available.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SANS SIFT Tools
8
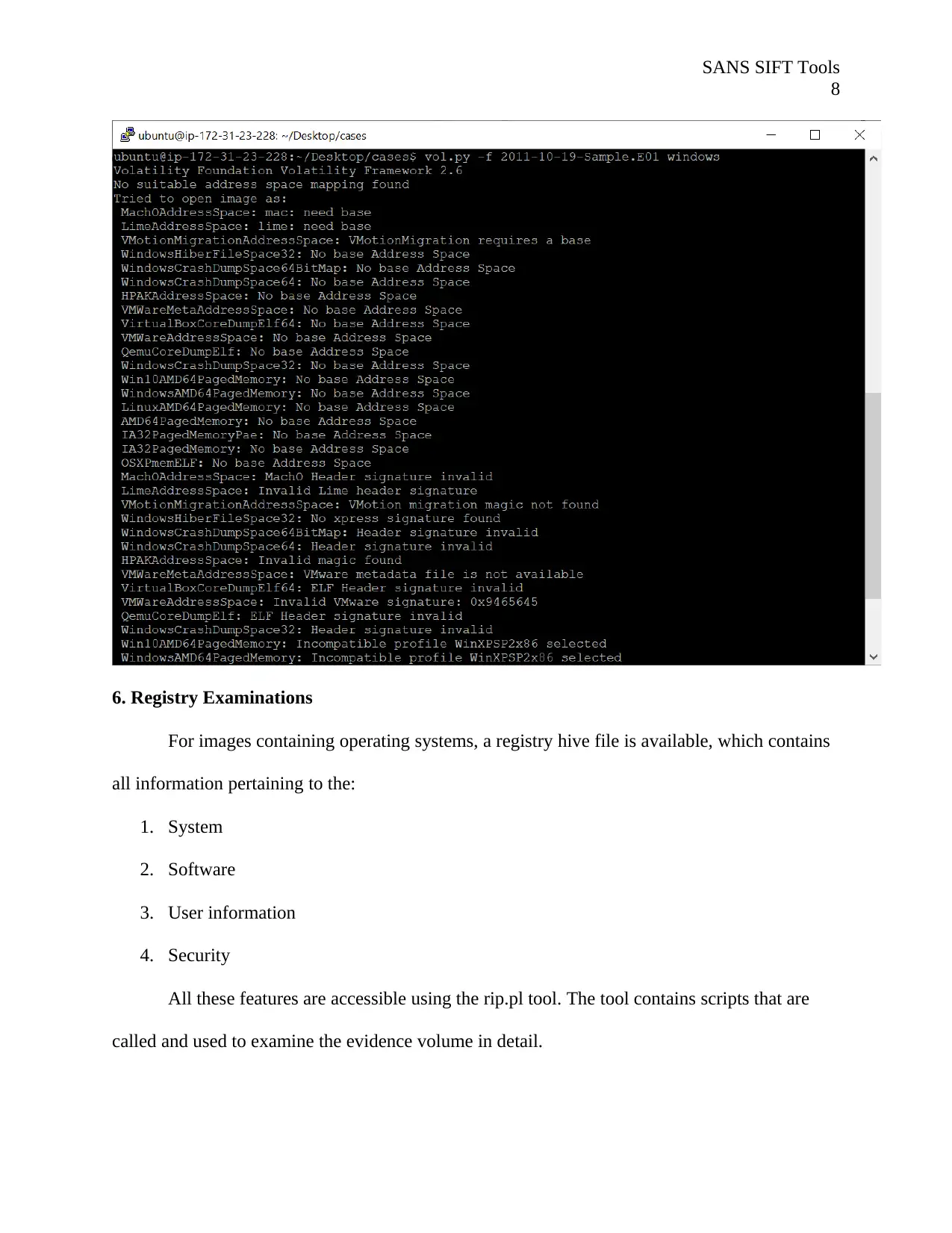
6. Registry Examinations
For images containing operating systems, a registry hive file is available, which contains
all information pertaining to the:
1. System
2. Software
3. User information
4. Security
All these features are accessible using the rip.pl tool. The tool contains scripts that are
called and used to examine the evidence volume in detail.
8
6. Registry Examinations
For images containing operating systems, a registry hive file is available, which contains
all information pertaining to the:
1. System
2. Software
3. User information
4. Security
All these features are accessible using the rip.pl tool. The tool contains scripts that are
called and used to examine the evidence volume in detail.
SANS SIFT Tools
9
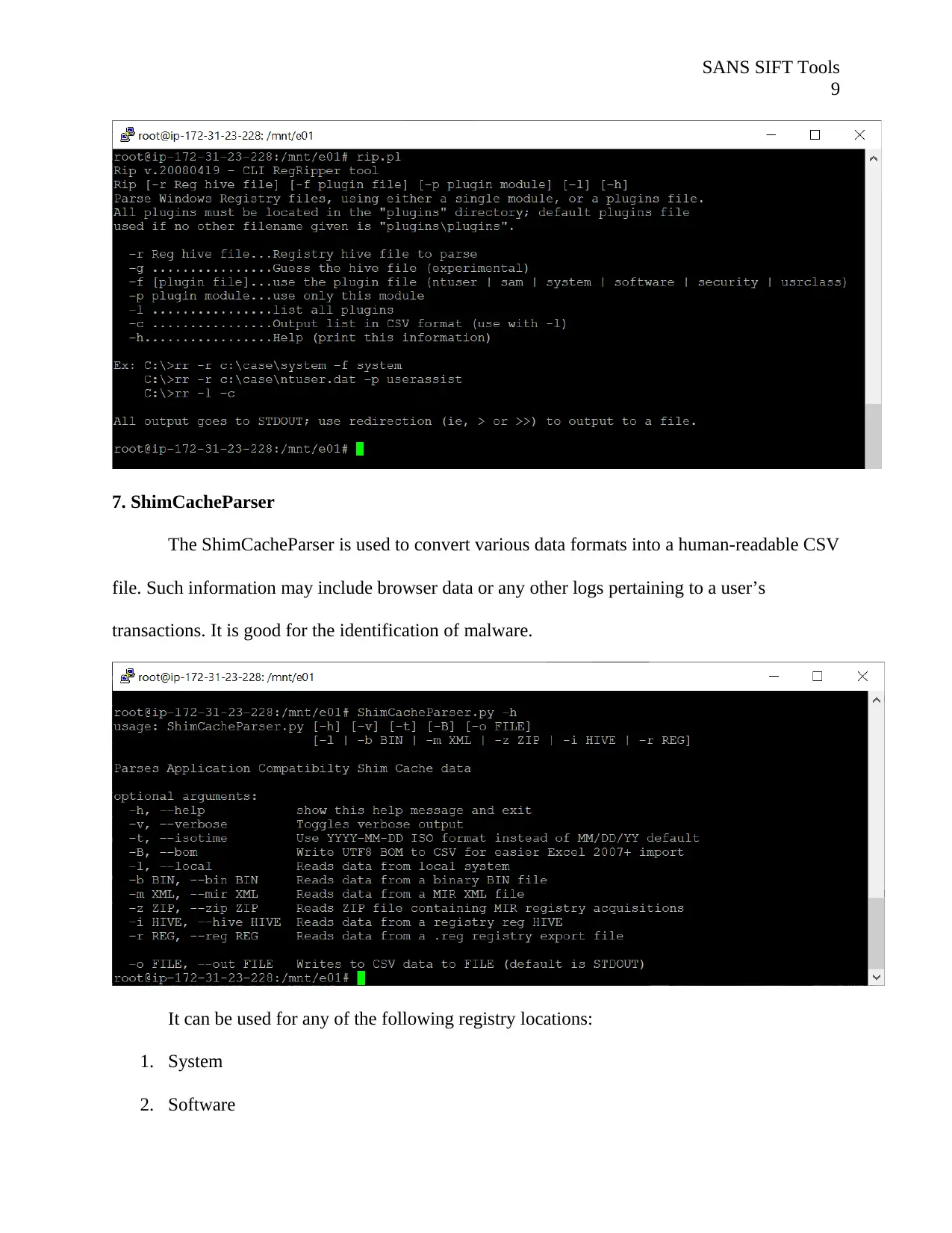
7. ShimCacheParser
The ShimCacheParser is used to convert various data formats into a human-readable CSV
file. Such information may include browser data or any other logs pertaining to a user’s
transactions. It is good for the identification of malware.
It can be used for any of the following registry locations:
1. System
2. Software
9
7. ShimCacheParser
The ShimCacheParser is used to convert various data formats into a human-readable CSV
file. Such information may include browser data or any other logs pertaining to a user’s
transactions. It is good for the identification of malware.
It can be used for any of the following registry locations:
1. System
2. Software
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
SANS SIFT Tools
10
3. User information
4. Security
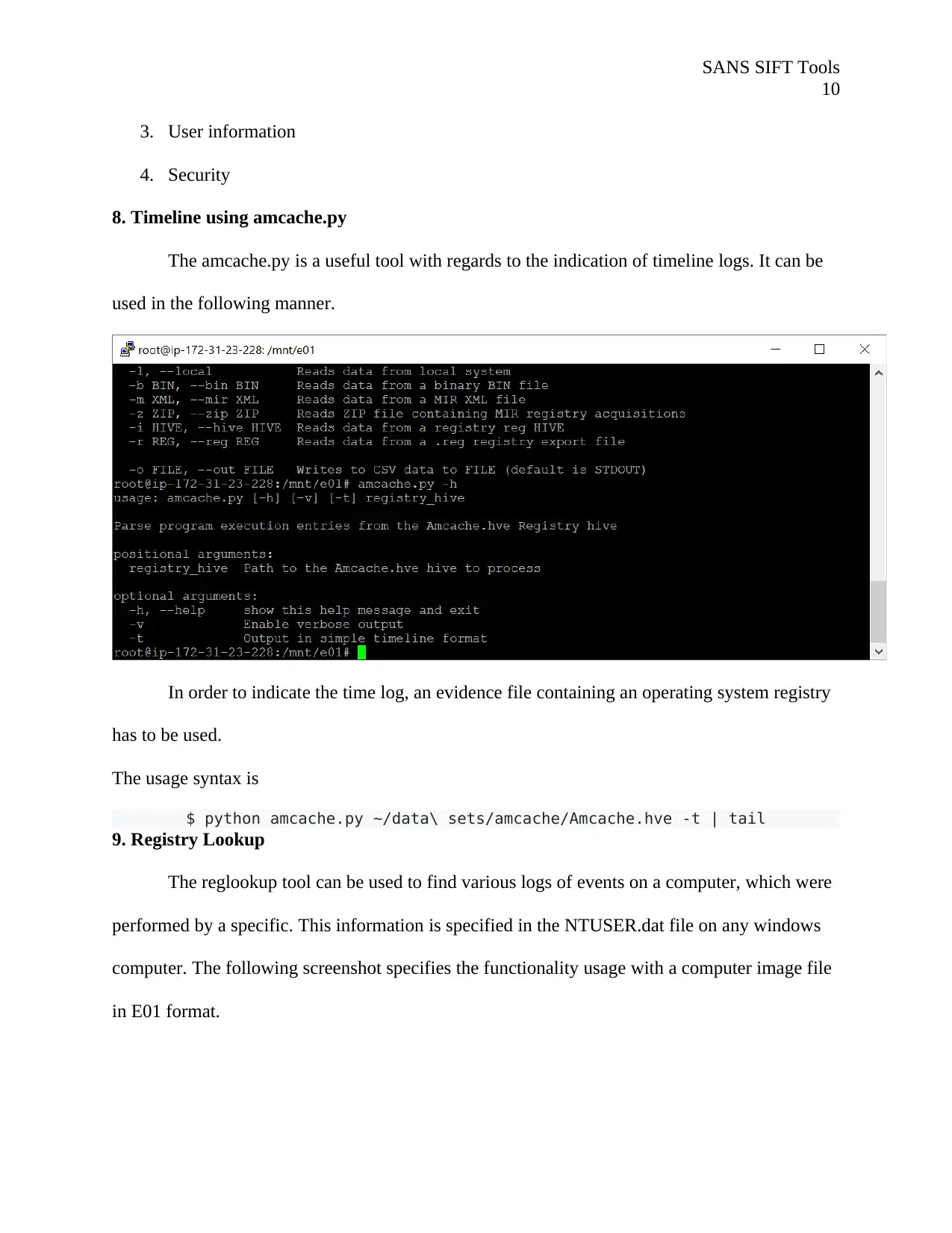
8. Timeline using amcache.py
The amcache.py is a useful tool with regards to the indication of timeline logs. It can be
used in the following manner.
In order to indicate the time log, an evidence file containing an operating system registry
has to be used.
The usage syntax is
$ python amcache.py ~/data\ sets/amcache/Amcache.hve -t | tail
9. Registry Lookup
The reglookup tool can be used to find various logs of events on a computer, which were
performed by a specific. This information is specified in the NTUSER.dat file on any windows
computer. The following screenshot specifies the functionality usage with a computer image file
in E01 format.
10
3. User information
4. Security
8. Timeline using amcache.py
The amcache.py is a useful tool with regards to the indication of timeline logs. It can be
used in the following manner.
In order to indicate the time log, an evidence file containing an operating system registry
has to be used.
The usage syntax is
$ python amcache.py ~/data\ sets/amcache/Amcache.hve -t | tail
9. Registry Lookup
The reglookup tool can be used to find various logs of events on a computer, which were
performed by a specific. This information is specified in the NTUSER.dat file on any windows
computer. The following screenshot specifies the functionality usage with a computer image file
in E01 format.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SANS SIFT Tools
11
10. Parsing Data with strings tool
The strings tool is used to read files from a mounted image and display the contents on
the command line interface.
The following output is produced.
11
10. Parsing Data with strings tool
The strings tool is used to read files from a mounted image and display the contents on
the command line interface.
The following output is produced.
SANS SIFT Tools
12
The strings tool can be used to verify inspect the text content of a file in its raw format or
as a mounted drive.
12
The strings tool can be used to verify inspect the text content of a file in its raw format or
as a mounted drive.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


