Strategic Information System Report: Business Process Analysis
VerifiedAdded on 2022/08/27
|12
|2492
|25
Report
AI Summary
This report provides a comprehensive analysis of the Giant Eggplant organization's current business processes and proposes strategic improvements through the implementation of IT controls. The report begins with an introduction highlighting the inefficiencies of the current manual systems, which struggle to manage a growing customer base and lack adequate data security. The discussion section includes data flow diagrams of the revenue and expenditure cycles, illustrating the flow of information within the company. A critical analysis of internal control weaknesses identifies issues such as manual data entry errors, slow service times, and inadequate inventory management. The report then outlines a series of IT controls to address these weaknesses, including IT governance, continuous monitoring and incident management, information security, data privacy, and identity and access management. The conclusion emphasizes the importance of automation and IT implementation to increase efficiency and revenue, providing recommendations for improvement. The report concludes with a list of relevant references supporting the analysis and recommendations.

Running head: STRATEGIC INFORMATION SYSTEM
STRATEGIC INFORMATION SYSTEM
Name of student
Name of university
Author’s note:
STRATEGIC INFORMATION SYSTEM
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
STRATEGIC INFORMATION SYSTEM
Table of Contents
1. Introduction..........................................................................................................2
2. Discussion............................................................................................................3
3. Diagrams..............................................................................................................3
3.1 Data flow diagram of revenue cycle.................................................................3
3.2 Data flow diagram of expenditure cycle..........................................................4
3.3 Analysis of internal control weaknesses...........................................................4
3.4 Description of the IT controls...........................................................................6
4. Conclusion............................................................................................................8
5. References..........................................................................................................10
STRATEGIC INFORMATION SYSTEM
Table of Contents
1. Introduction..........................................................................................................2
2. Discussion............................................................................................................3
3. Diagrams..............................................................................................................3
3.1 Data flow diagram of revenue cycle.................................................................3
3.2 Data flow diagram of expenditure cycle..........................................................4
3.3 Analysis of internal control weaknesses...........................................................4
3.4 Description of the IT controls...........................................................................6
4. Conclusion............................................................................................................8
5. References..........................................................................................................10

2
STRATEGIC INFORMATION SYSTEM
1. Introduction
It is being analysed among the modern organisation that the implementation of
automation technology helps in increasing the efficiency of various processes of the
organisation. The Giant Eggplant organisation presently executes their business using the
manual methods that is not able to provide services to the increased customer base. The
organisation is observed to manage several registers that does not provide extensive security
to all the data of transactions done by the customers. The aim of this report is to analyse the
present business methods of giant eggplant and then determine the areas in the business
where the business is lacking behind. The flow of information in the company is illustrated
using the data flow diagrams.
STRATEGIC INFORMATION SYSTEM
1. Introduction
It is being analysed among the modern organisation that the implementation of
automation technology helps in increasing the efficiency of various processes of the
organisation. The Giant Eggplant organisation presently executes their business using the
manual methods that is not able to provide services to the increased customer base. The
organisation is observed to manage several registers that does not provide extensive security
to all the data of transactions done by the customers. The aim of this report is to analyse the
present business methods of giant eggplant and then determine the areas in the business
where the business is lacking behind. The flow of information in the company is illustrated
using the data flow diagrams.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
STRATEGIC INFORMATION SYSTEM
2. Discussion
3. Diagrams
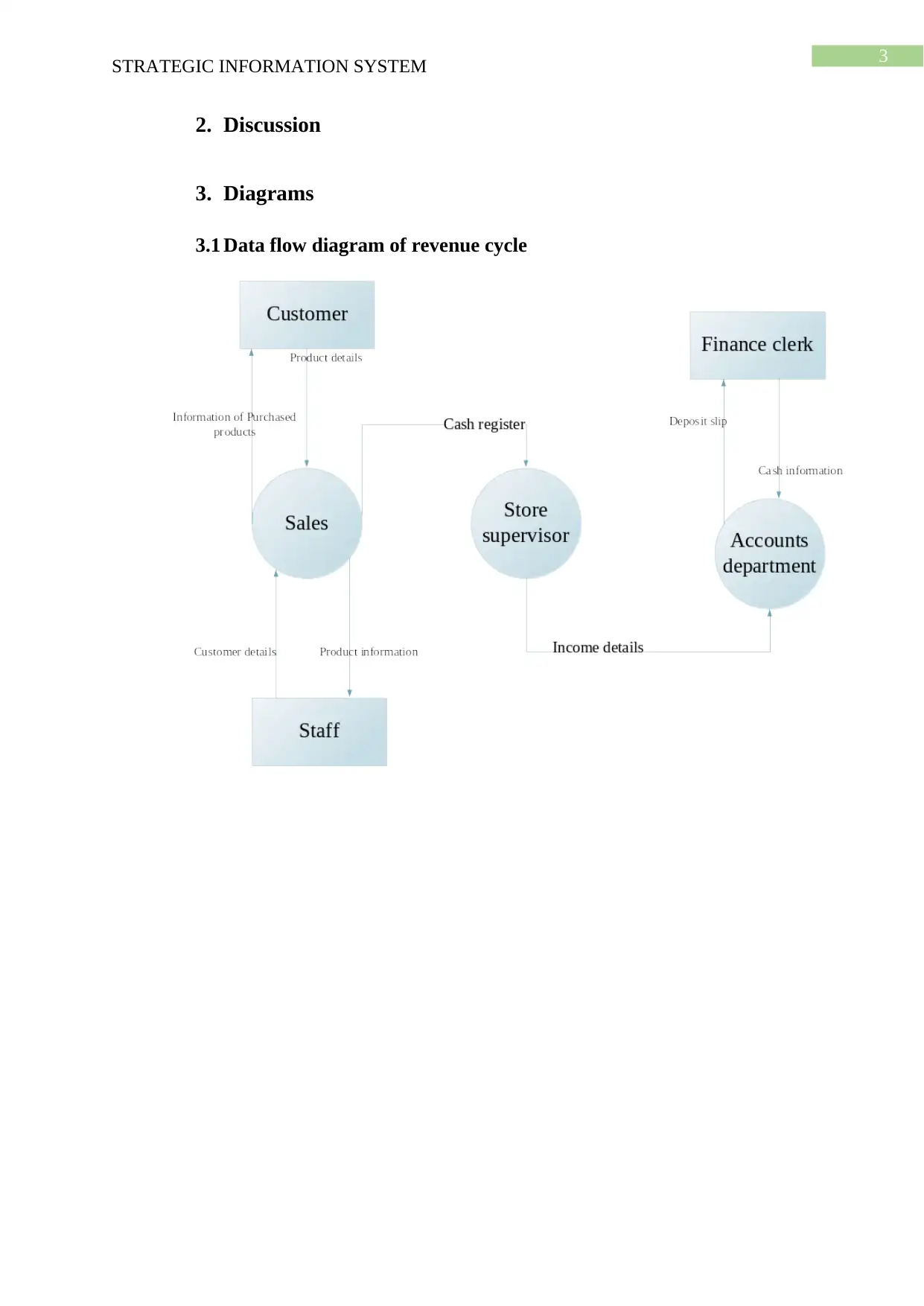
3.1 Data flow diagram of revenue cycle
STRATEGIC INFORMATION SYSTEM
2. Discussion
3. Diagrams
3.1 Data flow diagram of revenue cycle
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
STRATEGIC INFORMATION SYSTEM
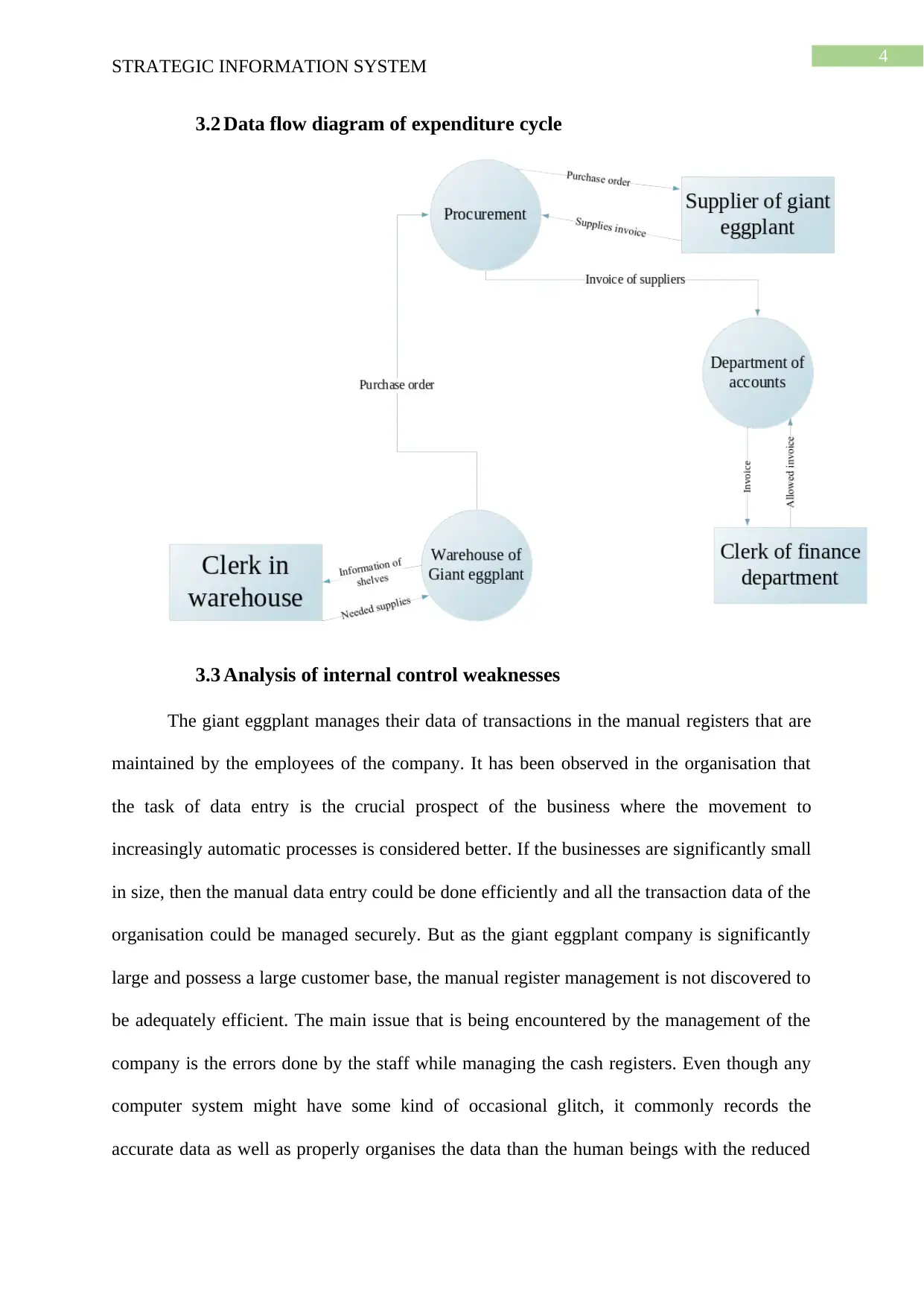
3.2 Data flow diagram of expenditure cycle
3.3 Analysis of internal control weaknesses
The giant eggplant manages their data of transactions in the manual registers that are
maintained by the employees of the company. It has been observed in the organisation that
the task of data entry is the crucial prospect of the business where the movement to
increasingly automatic processes is considered better. If the businesses are significantly small
in size, then the manual data entry could be done efficiently and all the transaction data of the
organisation could be managed securely. But as the giant eggplant company is significantly
large and possess a large customer base, the manual register management is not discovered to
be adequately efficient. The main issue that is being encountered by the management of the
company is the errors done by the staff while managing the cash registers. Even though any
computer system might have some kind of occasional glitch, it commonly records the
accurate data as well as properly organises the data than the human beings with the reduced
STRATEGIC INFORMATION SYSTEM
3.2 Data flow diagram of expenditure cycle
3.3 Analysis of internal control weaknesses
The giant eggplant manages their data of transactions in the manual registers that are
maintained by the employees of the company. It has been observed in the organisation that
the task of data entry is the crucial prospect of the business where the movement to
increasingly automatic processes is considered better. If the businesses are significantly small
in size, then the manual data entry could be done efficiently and all the transaction data of the
organisation could be managed securely. But as the giant eggplant company is significantly
large and possess a large customer base, the manual register management is not discovered to
be adequately efficient. The main issue that is being encountered by the management of the
company is the errors done by the staff while managing the cash registers. Even though any
computer system might have some kind of occasional glitch, it commonly records the
accurate data as well as properly organises the data than the human beings with the reduced

5
STRATEGIC INFORMATION SYSTEM
requirement of error checking. The manual ledger maintaining needs significantly more
employees to check as well as double check for the appropriate accuracy.
One more issue faced in the organisation is the speed of providing the services as well
as the products to the customers. With the manual register maintaining, the data entry process
takes significantly more time of the employees that could been otherwise be invested in some
other work. The computers as well as the machines are commonly observed to be faster than
the human that frees up time for the employees for focussing on the other things. Rather than
typing in the numbers all day, the employees could spend increased time on the review of
inventory, developing charts or even drawing up the projections for the future growth. The
investment done by the company is observed to be comparatively more than the revenue
gained. The company has to hire significantly more employees for managing the manual cash
registers and it also keeps the employees from investing increased time on the point of
biggest contribution towards mission as well as the vision of the company.
The company do not possess the required inventory management system for
managing the adequate amount of inventory in the company. The employees of the
warehouse are required to manually check the shelves for determining the products that are
required to be restocked in the company. The manual inventory management system in the
company needs an employee to note down all the products that are required to be restocked
and if the employee forgets to note down any particular product, then that product would not
be available in the company. The manual inventory management system does not allow the
complete information flow regarding the products available in the company. With the
introduction of automated inventory management system, the transparency among the various
departments would be significantly increased as the information of the available products in
the company would be available for all the departments. The manual inventory system in the
company does not offer a number, as all the numbers from inventory are obtained from the
STRATEGIC INFORMATION SYSTEM
requirement of error checking. The manual ledger maintaining needs significantly more
employees to check as well as double check for the appropriate accuracy.
One more issue faced in the organisation is the speed of providing the services as well
as the products to the customers. With the manual register maintaining, the data entry process
takes significantly more time of the employees that could been otherwise be invested in some
other work. The computers as well as the machines are commonly observed to be faster than
the human that frees up time for the employees for focussing on the other things. Rather than
typing in the numbers all day, the employees could spend increased time on the review of
inventory, developing charts or even drawing up the projections for the future growth. The
investment done by the company is observed to be comparatively more than the revenue
gained. The company has to hire significantly more employees for managing the manual cash
registers and it also keeps the employees from investing increased time on the point of
biggest contribution towards mission as well as the vision of the company.
The company do not possess the required inventory management system for
managing the adequate amount of inventory in the company. The employees of the
warehouse are required to manually check the shelves for determining the products that are
required to be restocked in the company. The manual inventory management system in the
company needs an employee to note down all the products that are required to be restocked
and if the employee forgets to note down any particular product, then that product would not
be available in the company. The manual inventory management system does not allow the
complete information flow regarding the products available in the company. With the
introduction of automated inventory management system, the transparency among the various
departments would be significantly increased as the information of the available products in
the company would be available for all the departments. The manual inventory system in the
company does not offer a number, as all the numbers from inventory are obtained from the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
STRATEGIC INFORMATION SYSTEM
physical counts of inventory. The main difficulty of executing the manual inventory system
could be observed that the physical inventory counts are required to be performed often for
controlling all the items in inventory. This task has been observed to be extensively time-
consuming and it could cost significant money to the business, if any employee is required to
provide assistance outside of the business hours. The manual inventory system in the
company do not update at end of the data with the real-time counts of inventory. It denotes
that the company is required to analyse the items in the inventory each time any product is
required to be ordered. For placing the order of any new raw materials, supplies or even the
products in the company, the employees are required to analyse the present inventory for
ordering the accurate number of products. This could be considered as significantly time
consuming process as the employees in the warehouse is required to go through the items
before ordering products.
3.4 Description of the IT controls
The list of IT controls that are required to be introduced in the organisation are:
IT governance: The IT governance could be described as the processes that are used
for monitoring as well as controlling the crucial decisions of information technology
capability for ensuring the appropriate delivery of the value to the key stakeholders in the
organisation (Van Grembergen & De Haes, 2018). The main objective of the IT governance
is ensuring the delivery of the business results and not IT risk management or IT systems
performance, which would reinforce of the notion of IT as the end in itself. To contrary, IT
governance is regarding the decisions of IT that have significant impact on the business value
(Gregory et al., 2018). The process could be efficiently used for monitoring as well as
controlling the crucial IT decisions that might have the negative or positive impact on the
business results (Joshi et al., 2018). The main concept of the governance is considered
meaningless deprived of the recognition of both the responsibility as well as the ownership.
STRATEGIC INFORMATION SYSTEM
physical counts of inventory. The main difficulty of executing the manual inventory system
could be observed that the physical inventory counts are required to be performed often for
controlling all the items in inventory. This task has been observed to be extensively time-
consuming and it could cost significant money to the business, if any employee is required to
provide assistance outside of the business hours. The manual inventory system in the
company do not update at end of the data with the real-time counts of inventory. It denotes
that the company is required to analyse the items in the inventory each time any product is
required to be ordered. For placing the order of any new raw materials, supplies or even the
products in the company, the employees are required to analyse the present inventory for
ordering the accurate number of products. This could be considered as significantly time
consuming process as the employees in the warehouse is required to go through the items
before ordering products.
3.4 Description of the IT controls
The list of IT controls that are required to be introduced in the organisation are:
IT governance: The IT governance could be described as the processes that are used
for monitoring as well as controlling the crucial decisions of information technology
capability for ensuring the appropriate delivery of the value to the key stakeholders in the
organisation (Van Grembergen & De Haes, 2018). The main objective of the IT governance
is ensuring the delivery of the business results and not IT risk management or IT systems
performance, which would reinforce of the notion of IT as the end in itself. To contrary, IT
governance is regarding the decisions of IT that have significant impact on the business value
(Gregory et al., 2018). The process could be efficiently used for monitoring as well as
controlling the crucial IT decisions that might have the negative or positive impact on the
business results (Joshi et al., 2018). The main concept of the governance is considered
meaningless deprived of the recognition of both the responsibility as well as the ownership.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
STRATEGIC INFORMATION SYSTEM
The crucial stakeholders in the organisation have the ownership stake in that organisation
(Khouja et al., 2018).
Continuous Monitoring and Incident Management: The organisation needs
technologies that delivers complete visibility into their network as well as the effective
understanding of the core components (Thompson, 2018). For detecting the attacks easily, for
making sure that proper understanding of the attack is gained as well mitigated and for
preventing similar kinds of attacks in future, the organisation needs constant approach of
incident response (Miloslavskaya, 2019). There are several technologies available in the
modern times that proactively detects the threats as well as provides the remedies for the
attacks (Miloslavskaya, 2016). With the introduction of these technology, not only the real-
time visibility is obtained into the endpoint systems but it also helps in reducing the
probability of any incident by efficiently preventing the attacks from successfully executing
(Wahlgren & Kowalski, 2019).
Information Security: The information security aspect is mainly associated with the
protection of information from any kind of unauthorised access (Peltier, 2016). It is the
section of the risk management and it mainly involves the prevention or reduction of the
probability of any unauthorised access, disruption, disclosure, modification, recording or
inspection (Safa, Von Solms & Furnell, 2016). While main focus of the information security
programs is the protection of the CIA triad or Confidentiality, Integrity and Availability of
the information in organisation, managing the productivity of the organisation is frequently
the crucial consideration (Johnston et al., 2016).
Data Privacy: The information privacy or data privacy is considered as the aspect of
information technology in the organisations that mainly deals with ability of the organisation
or any individual to determine what kind of data present in the computer system of the
STRATEGIC INFORMATION SYSTEM
The crucial stakeholders in the organisation have the ownership stake in that organisation
(Khouja et al., 2018).
Continuous Monitoring and Incident Management: The organisation needs
technologies that delivers complete visibility into their network as well as the effective
understanding of the core components (Thompson, 2018). For detecting the attacks easily, for
making sure that proper understanding of the attack is gained as well mitigated and for
preventing similar kinds of attacks in future, the organisation needs constant approach of
incident response (Miloslavskaya, 2019). There are several technologies available in the
modern times that proactively detects the threats as well as provides the remedies for the
attacks (Miloslavskaya, 2016). With the introduction of these technology, not only the real-
time visibility is obtained into the endpoint systems but it also helps in reducing the
probability of any incident by efficiently preventing the attacks from successfully executing
(Wahlgren & Kowalski, 2019).
Information Security: The information security aspect is mainly associated with the
protection of information from any kind of unauthorised access (Peltier, 2016). It is the
section of the risk management and it mainly involves the prevention or reduction of the
probability of any unauthorised access, disruption, disclosure, modification, recording or
inspection (Safa, Von Solms & Furnell, 2016). While main focus of the information security
programs is the protection of the CIA triad or Confidentiality, Integrity and Availability of
the information in organisation, managing the productivity of the organisation is frequently
the crucial consideration (Johnston et al., 2016).
Data Privacy: The information privacy or data privacy is considered as the aspect of
information technology in the organisations that mainly deals with ability of the organisation
or any individual to determine what kind of data present in the computer system of the

8
STRATEGIC INFORMATION SYSTEM
organisation could be shared with the third parties (Martin & Murphy, 2017). It also deals
with the methods by which any piece of information is required to be managed on the basis of
the relative significance (He, Cai & Yu, 2017). In the modern times, the concept of the data
privacy is applied to crucial personal information that is stored in the database of any
organisation.
Identity and Access Management: Identity and Access Management could be
described as the framework of the business policies, processes as well as the technologies that
permits the management of the digital or electronic identities (Indu, Anand & Bhaskar, 2018).
With the introduction of Identity and Access Management framework in the organisation, the
managers of information technology could effectively control the user access to the crucial
information in the organisation (Hummer et al., 2018). The products of Identity and Access
Management provides the role-based control to access that allows the system administrators
with regulating the access to their systems or the networks on the basis of role of the
individual users in the organisation. Within this concept, the access could be described as the
capability of any particular user of performing any particular task, like create, view or even
modify any particular role (Sharma, Dhote & Potey, 2016). The roles could be defined as per
the competency of job, authority as well as the accountability of the individual in the
organisation. The systems that could be used in the Giant eggplant organisation for Identity
and Access Management includes the single sign-on systems, privileged access management
as well as multi-factor authentication.
4. Conclusion
From the above, the most appropriate conclusion that could be drawn is that the
manual present manual process is the main reason for the decrease in revenue gained. With
the introduction of the modern technologies and systems, the efficiency of the organisation
STRATEGIC INFORMATION SYSTEM
organisation could be shared with the third parties (Martin & Murphy, 2017). It also deals
with the methods by which any piece of information is required to be managed on the basis of
the relative significance (He, Cai & Yu, 2017). In the modern times, the concept of the data
privacy is applied to crucial personal information that is stored in the database of any
organisation.
Identity and Access Management: Identity and Access Management could be
described as the framework of the business policies, processes as well as the technologies that
permits the management of the digital or electronic identities (Indu, Anand & Bhaskar, 2018).
With the introduction of Identity and Access Management framework in the organisation, the
managers of information technology could effectively control the user access to the crucial
information in the organisation (Hummer et al., 2018). The products of Identity and Access
Management provides the role-based control to access that allows the system administrators
with regulating the access to their systems or the networks on the basis of role of the
individual users in the organisation. Within this concept, the access could be described as the
capability of any particular user of performing any particular task, like create, view or even
modify any particular role (Sharma, Dhote & Potey, 2016). The roles could be defined as per
the competency of job, authority as well as the accountability of the individual in the
organisation. The systems that could be used in the Giant eggplant organisation for Identity
and Access Management includes the single sign-on systems, privileged access management
as well as multi-factor authentication.
4. Conclusion
From the above, the most appropriate conclusion that could be drawn is that the
manual present manual process is the main reason for the decrease in revenue gained. With
the introduction of the modern technologies and systems, the efficiency of the organisation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
STRATEGIC INFORMATION SYSTEM
could be increased significantly and increased revenue could be gained. The main sectors of
the business where the efficiency is lacking, has been discussed briefly and proper IT controls
have been recommended to the organisation that could be introduced for ensuring the
increase of efficiency.
STRATEGIC INFORMATION SYSTEM
could be increased significantly and increased revenue could be gained. The main sectors of
the business where the efficiency is lacking, has been discussed briefly and proper IT controls
have been recommended to the organisation that could be introduced for ensuring the
increase of efficiency.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
STRATEGIC INFORMATION SYSTEM
5. References
Gregory, R. W., Kaganer, E., Henfridsson, O., & Ruch, T. J. (2018). IT Consumerization and
the Transformation of IT Governance. MIS Quarterly, 42(4), 1225-1253.
He, Z., Cai, Z., & Yu, J. (2017). Latent-data privacy preserving with customized data utility
for social network data. IEEE Transactions on Vehicular Technology, 67(1), 665-673.
Hummer, M., Groll, S., Kunz, M., Fuchs, L., & Pernul, G. (2018). Measuring Identity and
Access Management Performance-An Expert Survey on Possible Performance
Indicators. In ICISSP (pp. 233-240).
Indu, I., Anand, P. R., & Bhaskar, V. (2018). Identity and access management in cloud
environment: Mechanisms and challenges. Engineering science and technology, an
international journal, 21(4), 574-588.
Johnston, A. C., Warkentin, M., McBride, M., & Carter, L. (2016). Dispositional and
situational factors: influences on information security policy violations. European
Journal of Information Systems, 25(3), 231-251.
Joshi, A., Bollen, L., Hassink, H., De Haes, S., & Van Grembergen, W. (2018). Explaining IT
governance disclosure through the constructs of IT governance maturity and IT
strategic role. Information & Management, 55(3), 368-380.
Khouja, M., Rodriguez, I. B., Halima, Y. B., & Moalla, S. (2018). IT Governance in Higher
education Institutions: A systematic Literature review. International Journal of
Human Capital and Information Technology Professionals (IJHCITP), 9(2), 52-67.
Martin, K. D., & Murphy, P. E. (2017). The role of data privacy in marketing. Journal of the
Academy of Marketing Science, 45(2), 135-155.
STRATEGIC INFORMATION SYSTEM
5. References
Gregory, R. W., Kaganer, E., Henfridsson, O., & Ruch, T. J. (2018). IT Consumerization and
the Transformation of IT Governance. MIS Quarterly, 42(4), 1225-1253.
He, Z., Cai, Z., & Yu, J. (2017). Latent-data privacy preserving with customized data utility
for social network data. IEEE Transactions on Vehicular Technology, 67(1), 665-673.
Hummer, M., Groll, S., Kunz, M., Fuchs, L., & Pernul, G. (2018). Measuring Identity and
Access Management Performance-An Expert Survey on Possible Performance
Indicators. In ICISSP (pp. 233-240).
Indu, I., Anand, P. R., & Bhaskar, V. (2018). Identity and access management in cloud
environment: Mechanisms and challenges. Engineering science and technology, an
international journal, 21(4), 574-588.
Johnston, A. C., Warkentin, M., McBride, M., & Carter, L. (2016). Dispositional and
situational factors: influences on information security policy violations. European
Journal of Information Systems, 25(3), 231-251.
Joshi, A., Bollen, L., Hassink, H., De Haes, S., & Van Grembergen, W. (2018). Explaining IT
governance disclosure through the constructs of IT governance maturity and IT
strategic role. Information & Management, 55(3), 368-380.
Khouja, M., Rodriguez, I. B., Halima, Y. B., & Moalla, S. (2018). IT Governance in Higher
education Institutions: A systematic Literature review. International Journal of
Human Capital and Information Technology Professionals (IJHCITP), 9(2), 52-67.
Martin, K. D., & Murphy, P. E. (2017). The role of data privacy in marketing. Journal of the
Academy of Marketing Science, 45(2), 135-155.

11
STRATEGIC INFORMATION SYSTEM
Miloslavskaya, N. (2016, August). Security operations centers for information security
incident management. In 2016 IEEE 4th International Conference on Future Internet
of Things and Cloud (FiCloud) (pp. 131-136). IEEE.
Miloslavskaya, N. (2019). Network Security Intelligence Centres for Information Security
Incident Management (Doctoral dissertation, University of Plymouth).
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. computers & security, 56, 70-82.
Sharma, D. H., Dhote, C. A., & Potey, M. M. (2016). Identity and access management as
security-as-a-service from clouds. Procedia Computer Science, 79, 170-174.
Thompson, E. C. (2018). Continuous Monitoring of Incident Response Program.
In Cybersecurity Incident Response (pp. 125-135). Apress, Berkeley, CA.
Van Grembergen, W., & De Haes, S. (2018). Introduction to the Minitrack on IT Governance
and its Mechanisms.
Wahlgren, G., & Kowalski, S. (2019, June). A Maturity Model for IT-Related Security
Incident Management. In International Conference on Business Information
Systems (pp. 203-217). Springer, Cham.
STRATEGIC INFORMATION SYSTEM
Miloslavskaya, N. (2016, August). Security operations centers for information security
incident management. In 2016 IEEE 4th International Conference on Future Internet
of Things and Cloud (FiCloud) (pp. 131-136). IEEE.
Miloslavskaya, N. (2019). Network Security Intelligence Centres for Information Security
Incident Management (Doctoral dissertation, University of Plymouth).
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. computers & security, 56, 70-82.
Sharma, D. H., Dhote, C. A., & Potey, M. M. (2016). Identity and access management as
security-as-a-service from clouds. Procedia Computer Science, 79, 170-174.
Thompson, E. C. (2018). Continuous Monitoring of Incident Response Program.
In Cybersecurity Incident Response (pp. 125-135). Apress, Berkeley, CA.
Van Grembergen, W., & De Haes, S. (2018). Introduction to the Minitrack on IT Governance
and its Mechanisms.
Wahlgren, G., & Kowalski, S. (2019, June). A Maturity Model for IT-Related Security
Incident Management. In International Conference on Business Information
Systems (pp. 203-217). Springer, Cham.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





