SIT182 - Malware Analysis of Dyre Trojan: Homework Assignment
VerifiedAdded on 2022/09/17
|9
|2288
|28
Homework Assignment
AI Summary
This assignment delves into the analysis of the Dyre Trojan, a sophisticated piece of malware. The analysis begins by exploring the security benefits of using a virtual machine (VM) to protect against potential risks during malware investigation, explaining memory segment handling in different operating modes, and the isolation provided by virtualization. The assignment then dissects the Dyre Trojan, detailing its capabilities, infection methods, and techniques for bypassing security measures like SSL encryption. It covers the Trojan's polymorphic nature, its use of social engineering, and the dynamic analysis approach required to understand its behavior. The analysis includes examination of the malware's hexadecimal code, identification of the MZ header, and discussion of the payload, which involves collecting credentials and manipulating browser content. Further, the assignment analyzes the malware's persistence mechanisms, such as the creation of a startup service, and compares the MD5 hashes of different files to identify the malware's components. The Windows Registry is examined to determine the malware's modifications, and finally, the assignment classifies the analysis as dynamic, justifying the approach with reference to the malware's runtime behavior and the tools used.

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MALWARE ANALYSIS
Q1, How does using a VM protect a malware engineer against possible security risks?
A general idea on how computers handle memory segments can be dated back to the DOS and early
16bit real mode systems. In these modes, there is no control over the size of segments and there are
no protection switches on any of those segments. Code can be loaded in any segment and run. It can
theoretically jump into other segments and run, also editing the contents of the given segment.
Basically there is absolutely no protection across these segments.
By the rise of the 32bit operating systems, came protected mode. The 32 bit Protected Mode allows
working with many virtual address areas, each of them contains a maximum of 4Giga Bytes of
addressable memory storage; and allows the system to enforce memory and hardware Input/Output
protection while also restricting the available instruction set via rings. Rings can be interpreted as
protection layers for programs. Paging is also used to provide virtual memory or simply a way to
load data out of RAM and onto disk.
Virtualization builds on the same concept used on the 32 bit protected mode. Virtual machines are
set up using a virtual machine control structure which dictates how their memory is mapped back to
actual host memory, which is similar to paging. In the event the virtual machine requires to make a
request to the host machine, it does so through the use of system-call-like events called VM exits
which are handled accordingly with the VM architecture. When that happens, control is transferred
back to the host.
In this structure it is extremely rare for code running in the VM’s memory segments to ‘jump’ into
the host computer memory, this is fundamentally because the VM does not ‘see’ the host’s memory.
The host maps memory required by the Virtual System. This includes everything from the BIOS all
the way up and as such the VM is isolated within the rules declared by the host. Malware running in
the VM cannot directly affect the host and hence the protection and freedom to experiment within
the VM machine.
Q1, How does using a VM protect a malware engineer against possible security risks?
A general idea on how computers handle memory segments can be dated back to the DOS and early
16bit real mode systems. In these modes, there is no control over the size of segments and there are
no protection switches on any of those segments. Code can be loaded in any segment and run. It can
theoretically jump into other segments and run, also editing the contents of the given segment.
Basically there is absolutely no protection across these segments.
By the rise of the 32bit operating systems, came protected mode. The 32 bit Protected Mode allows
working with many virtual address areas, each of them contains a maximum of 4Giga Bytes of
addressable memory storage; and allows the system to enforce memory and hardware Input/Output
protection while also restricting the available instruction set via rings. Rings can be interpreted as
protection layers for programs. Paging is also used to provide virtual memory or simply a way to
load data out of RAM and onto disk.
Virtualization builds on the same concept used on the 32 bit protected mode. Virtual machines are
set up using a virtual machine control structure which dictates how their memory is mapped back to
actual host memory, which is similar to paging. In the event the virtual machine requires to make a
request to the host machine, it does so through the use of system-call-like events called VM exits
which are handled accordingly with the VM architecture. When that happens, control is transferred
back to the host.
In this structure it is extremely rare for code running in the VM’s memory segments to ‘jump’ into
the host computer memory, this is fundamentally because the VM does not ‘see’ the host’s memory.
The host maps memory required by the Virtual System. This includes everything from the BIOS all
the way up and as such the VM is isolated within the rules declared by the host. Malware running in
the VM cannot directly affect the host and hence the protection and freedom to experiment within
the VM machine.

Q2 Dyre Malware
The Malware was discovered in early June 2014 by the Dell SecureWorks Counter Threat Unit
research team. The malware has all Trojan capabilities. An extra feature enables it to bypass a site’s
SSL encryption by rerouting the subject’s traffic as raw HTTP while still displaying the HTTPS
encrypted session mark on the victim’s web browser. Dyre uses different techniques to attack its
victims, such as impersonating invoices, faxes, and financial documents, mostly PDF’s.
Dyre is a polymorphic virus. Polymorphic viruses are complex file infecting malware that can
create different versions of themselves to avoid detection yet maintain the same routines after every
infection. Once it infects the targets machine, it duplicates and disburses itself out to everyone in the
contact list. Other targets in turn send out new variants of the virus. Anti-viruses are virtualy useless
against it. Dyre is a Trojan. This means its primarily spread by social engineering and misleads
users of its true purpose.
This virus is also can be considered to be dynamic virus in classification. This is because it is
categorized by the means used to detect and analyze it. Dynamic malware analysis involves running
the malware in a contained environment like a VM in order to determine its behavioral
characteristics. This type of analysis is more detailed and yields better results. Therefore it is
important to not that without a contained environment like a VM its is nearly impossible to detect a
polymorphic virus like Dyre since static means of detection cannot be reliable.
A payload is the section or code of a virus that performs the attackers intentions.
Some viruses copy themselves over and over again, others steal data ,eavesdrop or allow illegal
access, destroy data and cause other consequences.
Examples of payloads may include reverse shells or TCP shells which allow the remote computer to
open an ssh-like shell on your computer and execute commands with a possibility of elevating their
privileges. A payload in a reverse shell could be a bat script that performs a TCP 3 way handshake
with the attacker allowing them to spawn a shell remotely.
To understand how the virus executes its payload, we study its dynamic properties. Dyre collects
credentials, essentially aiming online payment sites. Similar to other banking Trojans, Dyre attaches
into the most used internet browsers to intercept data traffic coming from a subject's computer,
collecting data, information and manipulating browser content before it is displayed by the web
browser.
Dyre's injection software uses a distinct application than other Trojans. The process attaches code
into browsers like Mozilla Firefox, Chrome by google, and of course the old Microsoft Internet
Explorer, snatching subjects vital data and information when they enter into an online payment
system or other credit card service possibly using key loggers.
The Malware was discovered in early June 2014 by the Dell SecureWorks Counter Threat Unit
research team. The malware has all Trojan capabilities. An extra feature enables it to bypass a site’s
SSL encryption by rerouting the subject’s traffic as raw HTTP while still displaying the HTTPS
encrypted session mark on the victim’s web browser. Dyre uses different techniques to attack its
victims, such as impersonating invoices, faxes, and financial documents, mostly PDF’s.
Dyre is a polymorphic virus. Polymorphic viruses are complex file infecting malware that can
create different versions of themselves to avoid detection yet maintain the same routines after every
infection. Once it infects the targets machine, it duplicates and disburses itself out to everyone in the
contact list. Other targets in turn send out new variants of the virus. Anti-viruses are virtualy useless
against it. Dyre is a Trojan. This means its primarily spread by social engineering and misleads
users of its true purpose.
This virus is also can be considered to be dynamic virus in classification. This is because it is
categorized by the means used to detect and analyze it. Dynamic malware analysis involves running
the malware in a contained environment like a VM in order to determine its behavioral
characteristics. This type of analysis is more detailed and yields better results. Therefore it is
important to not that without a contained environment like a VM its is nearly impossible to detect a
polymorphic virus like Dyre since static means of detection cannot be reliable.
A payload is the section or code of a virus that performs the attackers intentions.
Some viruses copy themselves over and over again, others steal data ,eavesdrop or allow illegal
access, destroy data and cause other consequences.
Examples of payloads may include reverse shells or TCP shells which allow the remote computer to
open an ssh-like shell on your computer and execute commands with a possibility of elevating their
privileges. A payload in a reverse shell could be a bat script that performs a TCP 3 way handshake
with the attacker allowing them to spawn a shell remotely.
To understand how the virus executes its payload, we study its dynamic properties. Dyre collects
credentials, essentially aiming online payment sites. Similar to other banking Trojans, Dyre attaches
into the most used internet browsers to intercept data traffic coming from a subject's computer,
collecting data, information and manipulating browser content before it is displayed by the web
browser.
Dyre's injection software uses a distinct application than other Trojans. The process attaches code
into browsers like Mozilla Firefox, Chrome by google, and of course the old Microsoft Internet
Explorer, snatching subjects vital data and information when they enter into an online payment
system or other credit card service possibly using key loggers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
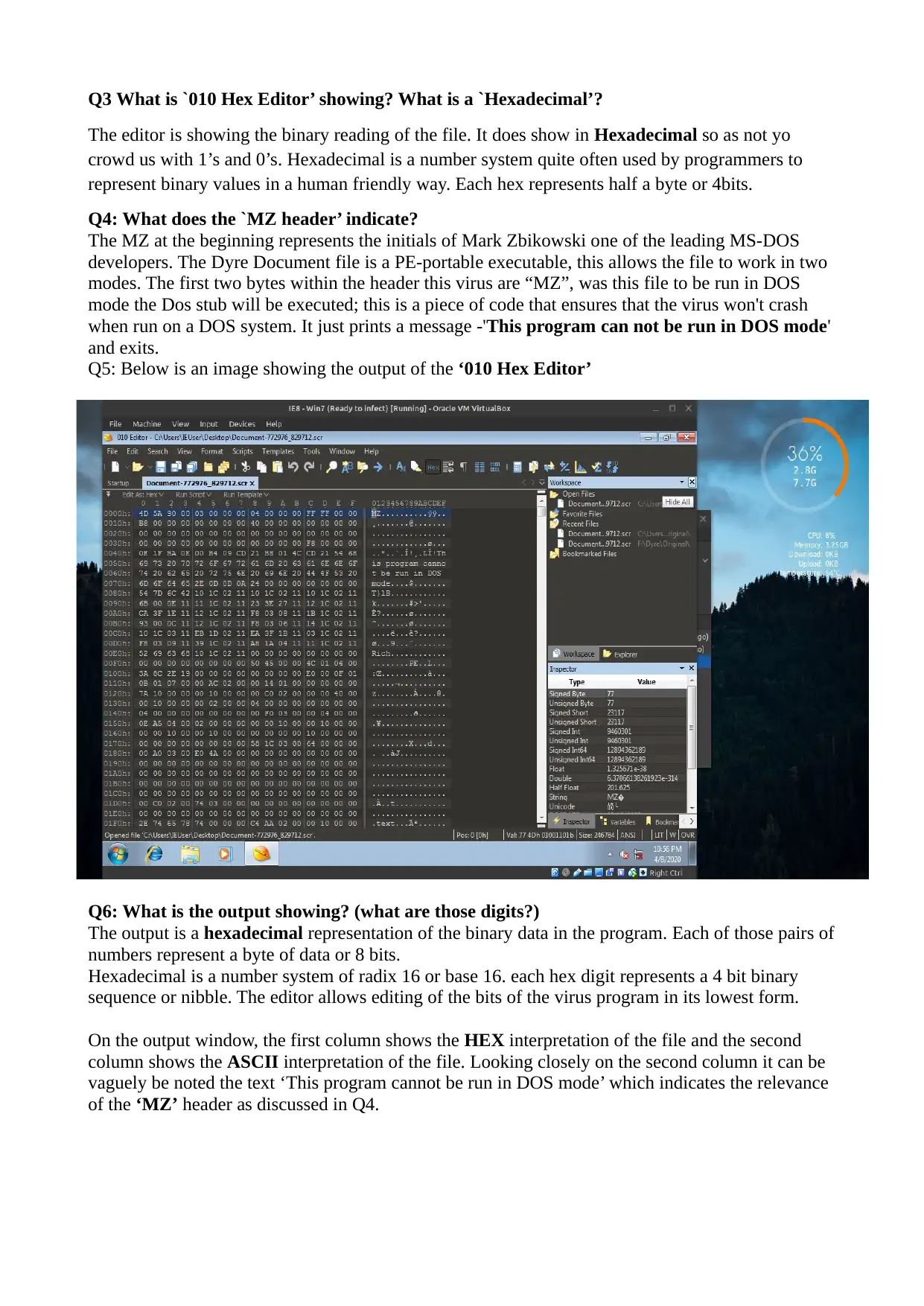
Q3 What is `010 Hex Editor’ showing? What is a `Hexadecimal’?
The editor is showing the binary reading of the file. It does show in Hexadecimal so as not yo
crowd us with 1’s and 0’s. Hexadecimal is a number system quite often used by programmers to
represent binary values in a human friendly way. Each hex represents half a byte or 4bits.
Q4: What does the `MZ header’ indicate?
The MZ at the beginning represents the initials of Mark Zbikowski one of the leading MS-DOS
developers. The Dyre Document file is a PE-portable executable, this allows the file to work in two
modes. The first two bytes within the header this virus are “MZ”, was this file to be run in DOS
mode the Dos stub will be executed; this is a piece of code that ensures that the virus won't crash
when run on a DOS system. It just prints a message -'This program can not be run in DOS mode'
and exits.
Q5: Below is an image showing the output of the ‘010 Hex Editor’
Q6: What is the output showing? (what are those digits?)
The output is a hexadecimal representation of the binary data in the program. Each of those pairs of
numbers represent a byte of data or 8 bits.
Hexadecimal is a number system of radix 16 or base 16. each hex digit represents a 4 bit binary
sequence or nibble. The editor allows editing of the bits of the virus program in its lowest form.
On the output window, the first column shows the HEX interpretation of the file and the second
column shows the ASCII interpretation of the file. Looking closely on the second column it can be
vaguely be noted the text ‘This program cannot be run in DOS mode’ which indicates the relevance
of the ‘MZ’ header as discussed in Q4.
The editor is showing the binary reading of the file. It does show in Hexadecimal so as not yo
crowd us with 1’s and 0’s. Hexadecimal is a number system quite often used by programmers to
represent binary values in a human friendly way. Each hex represents half a byte or 4bits.
Q4: What does the `MZ header’ indicate?
The MZ at the beginning represents the initials of Mark Zbikowski one of the leading MS-DOS
developers. The Dyre Document file is a PE-portable executable, this allows the file to work in two
modes. The first two bytes within the header this virus are “MZ”, was this file to be run in DOS
mode the Dos stub will be executed; this is a piece of code that ensures that the virus won't crash
when run on a DOS system. It just prints a message -'This program can not be run in DOS mode'
and exits.
Q5: Below is an image showing the output of the ‘010 Hex Editor’
Q6: What is the output showing? (what are those digits?)
The output is a hexadecimal representation of the binary data in the program. Each of those pairs of
numbers represent a byte of data or 8 bits.
Hexadecimal is a number system of radix 16 or base 16. each hex digit represents a 4 bit binary
sequence or nibble. The editor allows editing of the bits of the virus program in its lowest form.
On the output window, the first column shows the HEX interpretation of the file and the second
column shows the ASCII interpretation of the file. Looking closely on the second column it can be
vaguely be noted the text ‘This program cannot be run in DOS mode’ which indicates the relevance
of the ‘MZ’ header as discussed in Q4.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
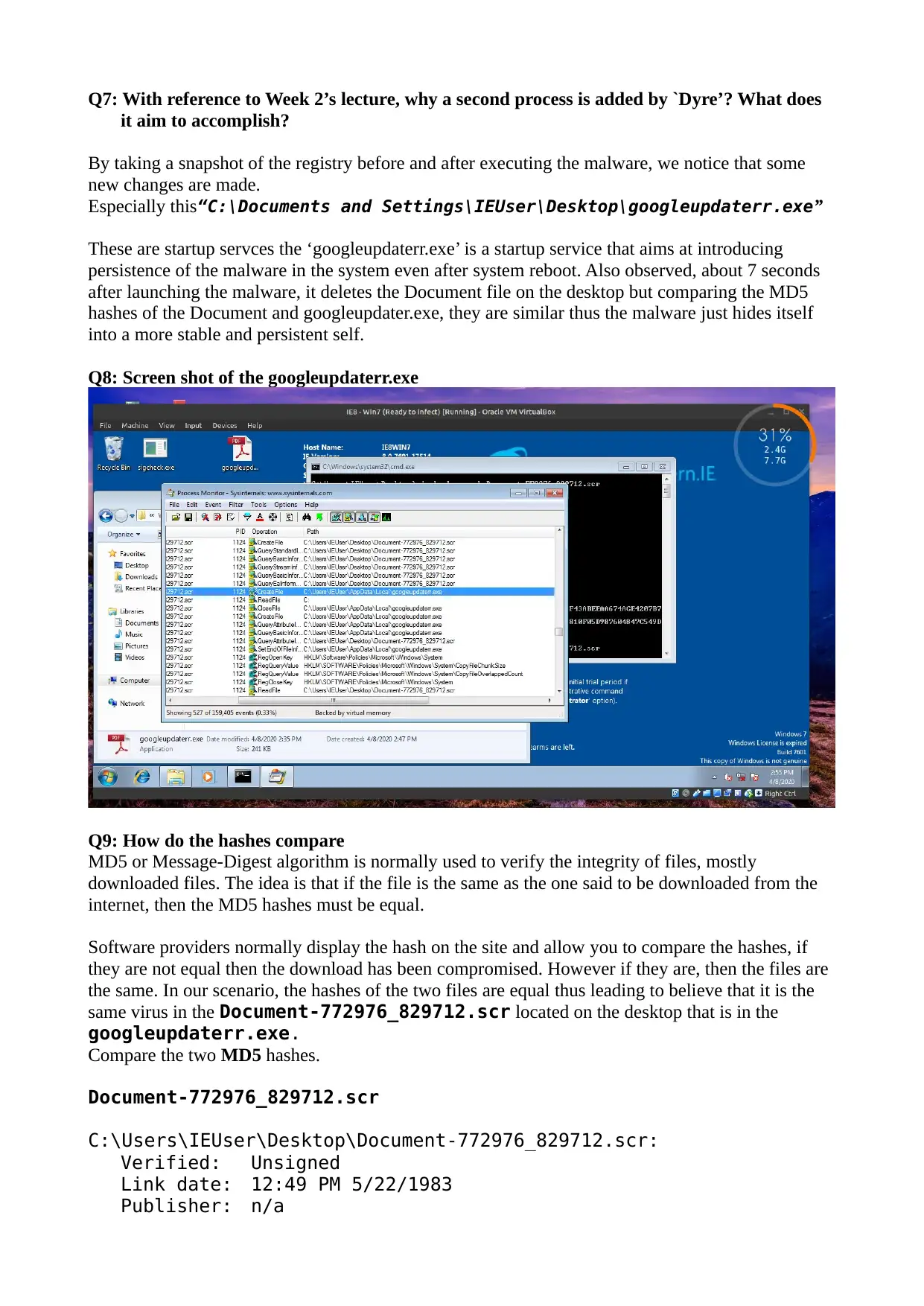
Q7: With reference to Week 2’s lecture, why a second process is added by `Dyre’? What does
it aim to accomplish?
By taking a snapshot of the registry before and after executing the malware, we notice that some
new changes are made.
Especially this“C:\Documents and Settings\IEUser\Desktop\googleupdaterr.exe”
These are startup servces the ‘googleupdaterr.exe’ is a startup service that aims at introducing
persistence of the malware in the system even after system reboot. Also observed, about 7 seconds
after launching the malware, it deletes the Document file on the desktop but comparing the MD5
hashes of the Document and googleupdater.exe, they are similar thus the malware just hides itself
into a more stable and persistent self.
Q8: Screen shot of the googleupdaterr.exe
Q9: How do the hashes compare
MD5 or Message-Digest algorithm is normally used to verify the integrity of files, mostly
downloaded files. The idea is that if the file is the same as the one said to be downloaded from the
internet, then the MD5 hashes must be equal.
Software providers normally display the hash on the site and allow you to compare the hashes, if
they are not equal then the download has been compromised. However if they are, then the files are
the same. In our scenario, the hashes of the two files are equal thus leading to believe that it is the
same virus in the Document-772976_829712.scr located on the desktop that is in the
googleupdaterr.exe.
Compare the two MD5 hashes.
Document-772976_829712.scr
C:\Users\IEUser\Desktop\Document-772976_829712.scr:
Verified: Unsigned
Link date: 12:49 PM 5/22/1983
Publisher: n/a
it aim to accomplish?
By taking a snapshot of the registry before and after executing the malware, we notice that some
new changes are made.
Especially this“C:\Documents and Settings\IEUser\Desktop\googleupdaterr.exe”
These are startup servces the ‘googleupdaterr.exe’ is a startup service that aims at introducing
persistence of the malware in the system even after system reboot. Also observed, about 7 seconds
after launching the malware, it deletes the Document file on the desktop but comparing the MD5
hashes of the Document and googleupdater.exe, they are similar thus the malware just hides itself
into a more stable and persistent self.
Q8: Screen shot of the googleupdaterr.exe
Q9: How do the hashes compare
MD5 or Message-Digest algorithm is normally used to verify the integrity of files, mostly
downloaded files. The idea is that if the file is the same as the one said to be downloaded from the
internet, then the MD5 hashes must be equal.
Software providers normally display the hash on the site and allow you to compare the hashes, if
they are not equal then the download has been compromised. However if they are, then the files are
the same. In our scenario, the hashes of the two files are equal thus leading to believe that it is the
same virus in the Document-772976_829712.scr located on the desktop that is in the
googleupdaterr.exe.
Compare the two MD5 hashes.
Document-772976_829712.scr
C:\Users\IEUser\Desktop\Document-772976_829712.scr:
Verified: Unsigned
Link date: 12:49 PM 5/22/1983
Publisher: n/a

Company: n/a
Description: n/a
Product: n/a
Prod version: n/a
File version: n/a
MachineType: 32-bit
MD5: C2D73485095EFDBD7AB625E469AFFB11
SHA1: A0A7B943B46979CC593474B94F14F2451B8AC3C0
PESHA1: F333CE0730B6B3088EE26667DB8CA343511CC675
PE256:
EAFEDAAD459E68E898EE90B27AE702E6211B893CD2BF43ABEEAA674ACE4207B7
SHA256:
523B9E8057EF0905E2C7D51B742D4BE9374CF2EEE5A810F05D987604847C549D
IMP: 8BCCA895CC1AAD9A2D2D4E9BA64A1EDA
googleupdaterr.exe
C:\Users\IEUser\Desktop\googleupdaterr.exe:
Verified: Unsigned
Link date: 12:49 PM 5/22/1983
Publisher: n/a
Company: n/a
Description: n/a
Product: n/a
Prod version: n/a
File version: n/a
MachineType: 32-bit
MD5: C2D73485095EFDBD7AB625E469AFFB11
SHA1: A0A7B943B46979CC593474B94F14F2451B8AC3C0
PESHA1: F333CE0730B6B3088EE26667DB8CA343511CC675
PE256:
EAFEDAAD459E68E898EE90B27AE702E6211B893CD2BF43ABEEAA674ACE4207B7
SHA256:
523B9E8057EF0905E2C7D51B742D4BE9374CF2EEE5A810F05D987604847C549D
IMP: 8BCCA895CC1AAD9A2D2D4E9BA64A1EDA
Given that the googleupdaterr.exe is a start up service, this shows that the virus made an
effort to obtain the ability to run even after the host machine shuts down
Description: n/a
Product: n/a
Prod version: n/a
File version: n/a
MachineType: 32-bit
MD5: C2D73485095EFDBD7AB625E469AFFB11
SHA1: A0A7B943B46979CC593474B94F14F2451B8AC3C0
PESHA1: F333CE0730B6B3088EE26667DB8CA343511CC675
PE256:
EAFEDAAD459E68E898EE90B27AE702E6211B893CD2BF43ABEEAA674ACE4207B7
SHA256:
523B9E8057EF0905E2C7D51B742D4BE9374CF2EEE5A810F05D987604847C549D
IMP: 8BCCA895CC1AAD9A2D2D4E9BA64A1EDA
googleupdaterr.exe
C:\Users\IEUser\Desktop\googleupdaterr.exe:
Verified: Unsigned
Link date: 12:49 PM 5/22/1983
Publisher: n/a
Company: n/a
Description: n/a
Product: n/a
Prod version: n/a
File version: n/a
MachineType: 32-bit
MD5: C2D73485095EFDBD7AB625E469AFFB11
SHA1: A0A7B943B46979CC593474B94F14F2451B8AC3C0
PESHA1: F333CE0730B6B3088EE26667DB8CA343511CC675
PE256:
EAFEDAAD459E68E898EE90B27AE702E6211B893CD2BF43ABEEAA674ACE4207B7
SHA256:
523B9E8057EF0905E2C7D51B742D4BE9374CF2EEE5A810F05D987604847C549D
IMP: 8BCCA895CC1AAD9A2D2D4E9BA64A1EDA
Given that the googleupdaterr.exe is a start up service, this shows that the virus made an
effort to obtain the ability to run even after the host machine shuts down
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Q10: What is `Windows Registry?’ What is it used for and why Windows has one?
The windows registry is a database of configurations used by Microsoft’s windows to control the
functionalities of files, hardware devices, programs and the O.S itself.
The registry gives a way of keeping settings for each Windows user.
The following table contains a list of the root keys found in the windows registry system.
Key About key
HKEY_CURRENT_USER Contains settings information for the user account that is
currently logged on.
HKEY_USERS
Has all active user accounts on the machine.
HKEY_CURRENT_USER is actually a sub-directory of
HKEY_USERS. HKEY_USERS
HKEY_LOCAL_MACHINE Has configurations specific to the machine for all the users
in that computer.
HKEY_CLASSES_ROOT
This is a sub-directory of the
HKEY_LOCAL_MACHINE\Software. This key ensures
that the correct program opens when you a file is launched
by the Windows Explorer.
HKEY_CURRENT_CONFIG Contains configuration settings about the hardware that is
currently being used by the computer
Q11. How do you open Windows Registry on the guest OS? Include screenshot of accessing
the
Windows Registry on guest OS.
To access the Registry, simply use the shortcut WIN + R and open the ‘run’ utility, on this type
‘regedit’ and press enter
The windows registry is a database of configurations used by Microsoft’s windows to control the
functionalities of files, hardware devices, programs and the O.S itself.
The registry gives a way of keeping settings for each Windows user.
The following table contains a list of the root keys found in the windows registry system.
Key About key
HKEY_CURRENT_USER Contains settings information for the user account that is
currently logged on.
HKEY_USERS
Has all active user accounts on the machine.
HKEY_CURRENT_USER is actually a sub-directory of
HKEY_USERS. HKEY_USERS
HKEY_LOCAL_MACHINE Has configurations specific to the machine for all the users
in that computer.
HKEY_CLASSES_ROOT
This is a sub-directory of the
HKEY_LOCAL_MACHINE\Software. This key ensures
that the correct program opens when you a file is launched
by the Windows Explorer.
HKEY_CURRENT_CONFIG Contains configuration settings about the hardware that is
currently being used by the computer
Q11. How do you open Windows Registry on the guest OS? Include screenshot of accessing
the
Windows Registry on guest OS.
To access the Registry, simply use the shortcut WIN + R and open the ‘run’ utility, on this type
‘regedit’ and press enter
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
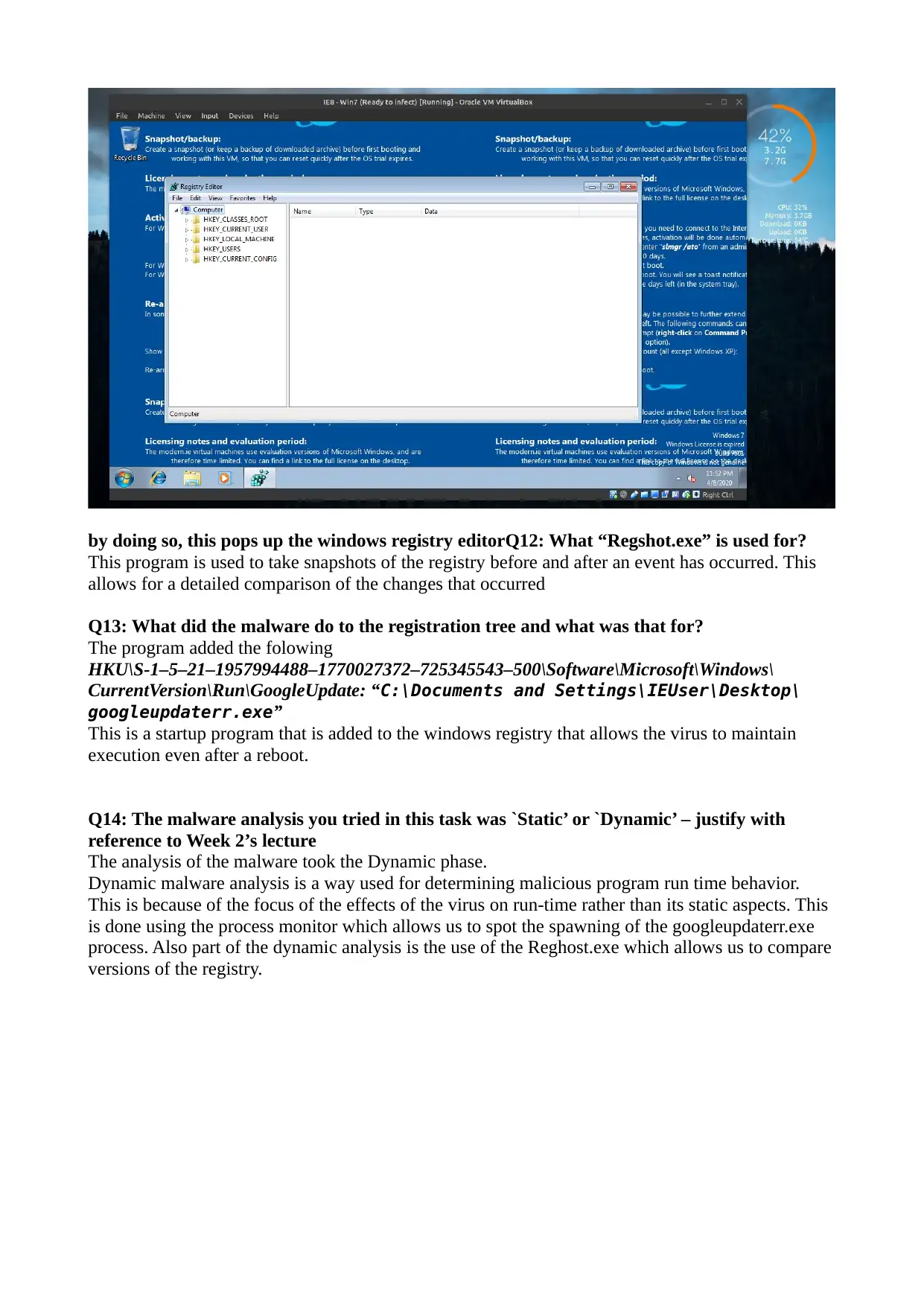
by doing so, this pops up the windows registry editorQ12: What “Regshot.exe” is used for?
This program is used to take snapshots of the registry before and after an event has occurred. This
allows for a detailed comparison of the changes that occurred
Q13: What did the malware do to the registration tree and what was that for?
The program added the folowing
HKU\S-1–5–21–1957994488–1770027372–725345543–500\Software\Microsoft\Windows\
CurrentVersion\Run\GoogleUpdate: “C:\Documents and Settings\IEUser\Desktop\
googleupdaterr.exe”
This is a startup program that is added to the windows registry that allows the virus to maintain
execution even after a reboot.
Q14: The malware analysis you tried in this task was `Static’ or `Dynamic’ – justify with
reference to Week 2’s lecture
The analysis of the malware took the Dynamic phase.
Dynamic malware analysis is a way used for determining malicious program run time behavior.
This is because of the focus of the effects of the virus on run-time rather than its static aspects. This
is done using the process monitor which allows us to spot the spawning of the googleupdaterr.exe
process. Also part of the dynamic analysis is the use of the Reghost.exe which allows us to compare
versions of the registry.
This program is used to take snapshots of the registry before and after an event has occurred. This
allows for a detailed comparison of the changes that occurred
Q13: What did the malware do to the registration tree and what was that for?
The program added the folowing
HKU\S-1–5–21–1957994488–1770027372–725345543–500\Software\Microsoft\Windows\
CurrentVersion\Run\GoogleUpdate: “C:\Documents and Settings\IEUser\Desktop\
googleupdaterr.exe”
This is a startup program that is added to the windows registry that allows the virus to maintain
execution even after a reboot.
Q14: The malware analysis you tried in this task was `Static’ or `Dynamic’ – justify with
reference to Week 2’s lecture
The analysis of the malware took the Dynamic phase.
Dynamic malware analysis is a way used for determining malicious program run time behavior.
This is because of the focus of the effects of the virus on run-time rather than its static aspects. This
is done using the process monitor which allows us to spot the spawning of the googleupdaterr.exe
process. Also part of the dynamic analysis is the use of the Reghost.exe which allows us to compare
versions of the registry.

REFERENCES
1. Edwards, G. Dyre Banking Trojan Explained. Retrieved April 9, 2020, from
https://blog.getcryptostopper.com/dyre-banking-trojan-explained
2. Protected Mode. Retrieved April 9, 2020, from https://wiki.osdev.org/Protected_Mode
3. Stone-Gross, B., Khandhar, P., & Dell. (2020, March 20). Dyre Banking Trojan Threat Analysis.
Retrieved April 9, 2020, from https://www.secureworks.com/research/dyre-banking-trojan
4.Thoma, M. T. M. (1961, September 1). Does a Virtual Machine stop malware from doing harm?
Retrieved April 9, 2020, from https://security.stackexchange.com/questions/9011/does-a-virtual-
machine-stop-malware-from-doing-harm
5.Trojan horse (computing). (2020, April 1). Retrieved April 9, 2020, from
https://en.wikipedia.org/wiki/Trojan_horse_(computing)
6.What is the Windows Registry? (2019, November 16). Retrieved April 9, 2020, from
https://www.computerhope.com/jargon/r/registry.html
1. Edwards, G. Dyre Banking Trojan Explained. Retrieved April 9, 2020, from
https://blog.getcryptostopper.com/dyre-banking-trojan-explained
2. Protected Mode. Retrieved April 9, 2020, from https://wiki.osdev.org/Protected_Mode
3. Stone-Gross, B., Khandhar, P., & Dell. (2020, March 20). Dyre Banking Trojan Threat Analysis.
Retrieved April 9, 2020, from https://www.secureworks.com/research/dyre-banking-trojan
4.Thoma, M. T. M. (1961, September 1). Does a Virtual Machine stop malware from doing harm?
Retrieved April 9, 2020, from https://security.stackexchange.com/questions/9011/does-a-virtual-
machine-stop-malware-from-doing-harm
5.Trojan horse (computing). (2020, April 1). Retrieved April 9, 2020, from
https://en.wikipedia.org/wiki/Trojan_horse_(computing)
6.What is the Windows Registry? (2019, November 16). Retrieved April 9, 2020, from
https://www.computerhope.com/jargon/r/registry.html
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.