SIT202 - Network Communication: Data Flow, IP Routing and Protocols
VerifiedAdded on 2023/06/04
|9
|2090
|356
Report
AI Summary
This report provides a detailed analysis of network communication, focusing on data flow from sender to recipient, IP routing, and the delivery of ICMP. It explains how packets are sent and received, how routers keep track of traffic, and the processes involved in protocols like EIGRP, OSPF, and RIP. The report also covers data acknowledgment exchange and the stop-and-wait ARQ protocol, including potential challenges and solutions. The report also includes a discussion of classful versus classless routing protocols, and the importance of subnet masks in network communication.

Network and Communication 1
Network and Communication
Name
Course Code and Name
Professor’s Name
City/State
Date
Network and Communication
Name
Course Code and Name
Professor’s Name
City/State
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network and Communication 2
Question One
Explanation of how data flows from sender to recipients
In network communication, the key elements needed for communication to get successfully
send it calls for a sender, communication medium, a protocol and the receiver (Alani &
Mohammed, 2014). Consequently, some of the activities that occur at the sender point (named
PC-1) include:
The message that is to be conveyed begins its journey at the application layer, for
example, a browser or an email which finds its path downwards.
The packet then proceeds to the TCP layer where it is assigned a port number. The
assigning of a port number is significant in the sense that here program uses TCP
stack while sending messages (Sriramoju, 2017). The assigning of port number allows
unique identification of the program whose port is listed. In this case, the port number
is assigned number 1020.
When the packet goes through the TCP protocol, it passes through the IP layer. The IP
layer then assigns this packet its destination. For instance, a packet passing through
PC-1 moving towards a remote server will have to be assigned both a port number
and an IP address. After the packet is assigned a port number and IP address, it is
ready to be conveyed over the Internet. The packet is then converted into electronic
waves using the data link and physical layer and then forwarded to the wide area
network (WAN) (White, 2015).
To the receiving end of the WAN link, an IPS router does routing activities to
determine the destination address and then forward the packet to the right final device.
Lastly but not least, in the final stage, the packet arrives at a remote server where it is
received at the lower end of the TCP stack where it has to move uphill (Goransson, et
Question One
Explanation of how data flows from sender to recipients
In network communication, the key elements needed for communication to get successfully
send it calls for a sender, communication medium, a protocol and the receiver (Alani &
Mohammed, 2014). Consequently, some of the activities that occur at the sender point (named
PC-1) include:
The message that is to be conveyed begins its journey at the application layer, for
example, a browser or an email which finds its path downwards.
The packet then proceeds to the TCP layer where it is assigned a port number. The
assigning of a port number is significant in the sense that here program uses TCP
stack while sending messages (Sriramoju, 2017). The assigning of port number allows
unique identification of the program whose port is listed. In this case, the port number
is assigned number 1020.
When the packet goes through the TCP protocol, it passes through the IP layer. The IP
layer then assigns this packet its destination. For instance, a packet passing through
PC-1 moving towards a remote server will have to be assigned both a port number
and an IP address. After the packet is assigned a port number and IP address, it is
ready to be conveyed over the Internet. The packet is then converted into electronic
waves using the data link and physical layer and then forwarded to the wide area
network (WAN) (White, 2015).
To the receiving end of the WAN link, an IPS router does routing activities to
determine the destination address and then forward the packet to the right final device.
Lastly but not least, in the final stage, the packet arrives at a remote server where it is
received at the lower end of the TCP stack where it has to move uphill (Goransson, et
Network and Communication 3
al., 2014). During this period of moving up the rioting information attached to the
packet is extracted. Therefore, when the packets arrive at the TCP stack top, they are
assembled into the original message.
The router follows the following process to keep on track the incoming and outgoing
traffic
Once the packet has arrived at the router from the switch, the router removes layer two
header information such as the MAC address which is contained in the packet and then
determines the destination IP address for the packet. Consequently, the router then finds a
route for the destination prefix by looking for a prefix which matches by assigning it an
interface as the exit MAC address which appears at the source address. After that, the packet
is forwarded to the exit interface (Grimes, 2016). When there is no route found in the routing
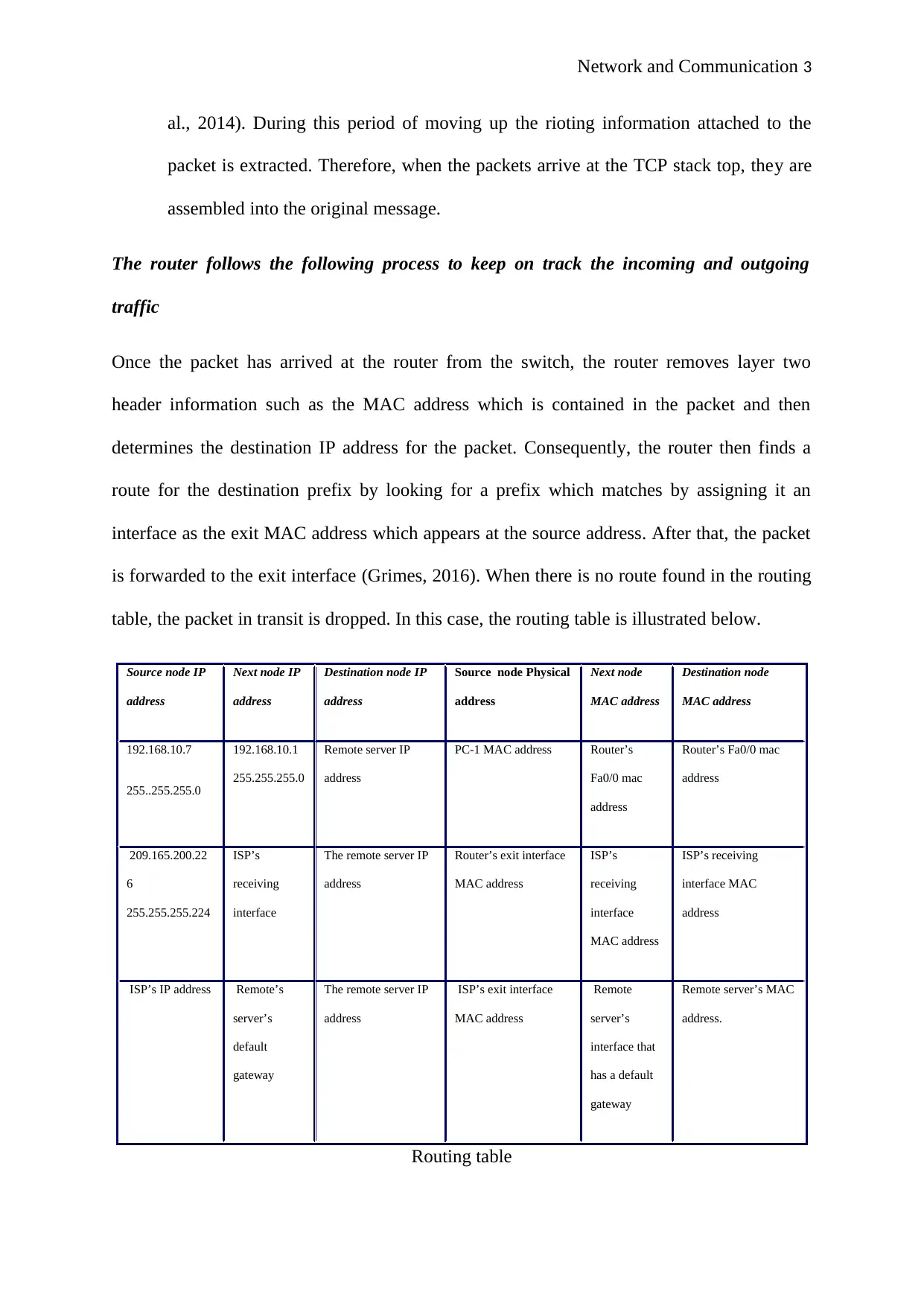
table, the packet in transit is dropped. In this case, the routing table is illustrated below.
Source node IP
address
Next node IP
address
Destination node IP
address
Source node Physical
address
Next node
MAC address
Destination node
MAC address
192.168.10.7
255..255.255.0
192.168.10.1
255.255.255.0
Remote server IP
address
PC-1 MAC address Router’s
Fa0/0 mac
address
Router’s Fa0/0 mac
address
209.165.200.22
6
255.255.255.224
ISP’s
receiving
interface
The remote server IP
address
Router’s exit interface
MAC address
ISP’s
receiving
interface
MAC address
ISP’s receiving
interface MAC
address
ISP’s IP address Remote’s
server’s
default
gateway
The remote server IP
address
ISP’s exit interface
MAC address
Remote
server’s
interface that
has a default
gateway
Remote server’s MAC
address.
Routing table
al., 2014). During this period of moving up the rioting information attached to the
packet is extracted. Therefore, when the packets arrive at the TCP stack top, they are
assembled into the original message.
The router follows the following process to keep on track the incoming and outgoing
traffic
Once the packet has arrived at the router from the switch, the router removes layer two
header information such as the MAC address which is contained in the packet and then
determines the destination IP address for the packet. Consequently, the router then finds a
route for the destination prefix by looking for a prefix which matches by assigning it an
interface as the exit MAC address which appears at the source address. After that, the packet
is forwarded to the exit interface (Grimes, 2016). When there is no route found in the routing
table, the packet in transit is dropped. In this case, the routing table is illustrated below.
Source node IP
address
Next node IP
address
Destination node IP
address
Source node Physical
address
Next node
MAC address
Destination node
MAC address
192.168.10.7
255..255.255.0
192.168.10.1
255.255.255.0
Remote server IP
address
PC-1 MAC address Router’s
Fa0/0 mac
address
Router’s Fa0/0 mac
address
209.165.200.22
6
255.255.255.224
ISP’s
receiving
interface
The remote server IP
address
Router’s exit interface
MAC address
ISP’s
receiving
interface
MAC address
ISP’s receiving
interface MAC
address
ISP’s IP address Remote’s
server’s
default
gateway
The remote server IP
address
ISP’s exit interface
MAC address
Remote
server’s
interface that
has a default
gateway
Remote server’s MAC
address.
Routing table
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network and Communication 4
Question Two
IP routing and frame forwarding process that delivers ICMP. The process goes through
the following stages:
PC-A send a ping request to 200.10.4.59 255.255.255.224
The address resolution protocol works together with the IP to come up with a decision
that ping request shall be forwarded, which is attained through identifying the IP
address and providing a mask to PC-A workstation (Lammle & Swartz, 2013). The
packet is then conveyed to the router for it to be directed to the right remote network
workstation.
When PC-A has been assigned a packet to the router, it has to identify the MAC
address of the interface of the router which is directly linked to the network.
The router has to distinguish the sent IP address for it to be able to respond to it.
Afterward, the router will then send back a response to PC-A. This takes some time
for ARP to deliver the information and ask the receiving device to give a response
(Carrell et al., 2013). At a given point, TTL decrements to zero which means that the
ping request time has expired.
The router will then give a response with its physical address interface that links the
network segment. The PC then complete the needed to be transmitted to the local
router externally. The network layer will then assign the packet to the data link layer
where at this point the packet containing ICMP will create a request (Pyles et al.,
2016). Indeed, this packet comprises a destination address, ping ECHO request, and
an IP for the source.
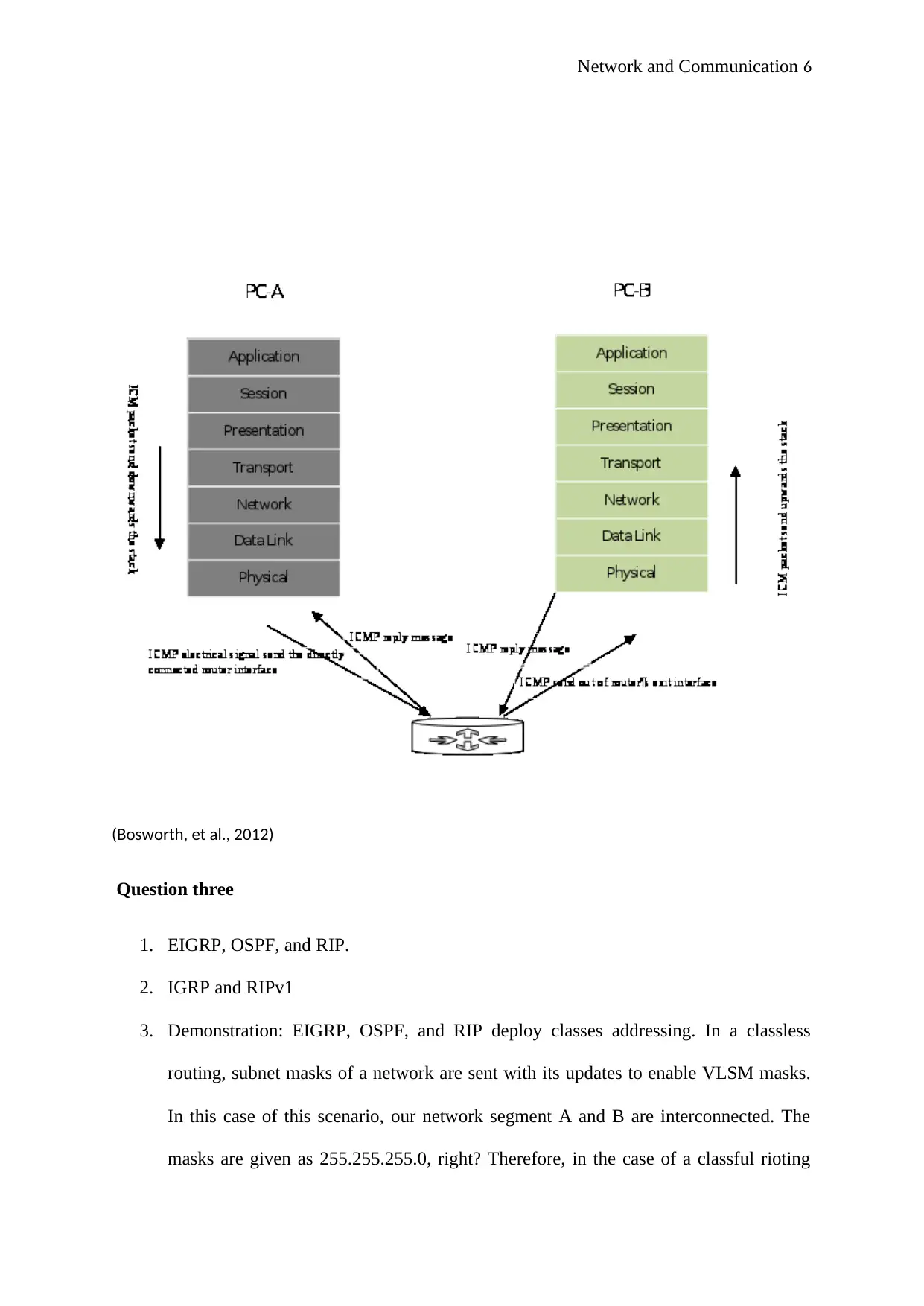
Question Two
IP routing and frame forwarding process that delivers ICMP. The process goes through
the following stages:
PC-A send a ping request to 200.10.4.59 255.255.255.224
The address resolution protocol works together with the IP to come up with a decision
that ping request shall be forwarded, which is attained through identifying the IP
address and providing a mask to PC-A workstation (Lammle & Swartz, 2013). The
packet is then conveyed to the router for it to be directed to the right remote network
workstation.
When PC-A has been assigned a packet to the router, it has to identify the MAC
address of the interface of the router which is directly linked to the network.
The router has to distinguish the sent IP address for it to be able to respond to it.
Afterward, the router will then send back a response to PC-A. This takes some time
for ARP to deliver the information and ask the receiving device to give a response
(Carrell et al., 2013). At a given point, TTL decrements to zero which means that the
ping request time has expired.
The router will then give a response with its physical address interface that links the
network segment. The PC then complete the needed to be transmitted to the local
router externally. The network layer will then assign the packet to the data link layer
where at this point the packet containing ICMP will create a request (Pyles et al.,
2016). Indeed, this packet comprises a destination address, ping ECHO request, and
an IP for the source.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network and Communication 5
The data link layer for PC-A will create a frame which comprises a source MAC
address, and destination address. A Cyclic redundancy check is attached to ascertain
that the destination workstation drops the frame in case it is destroyed.
The physical layer receives the frame from the data link layer and then convert the
frame from zeros to ones which are referred to as a digital signal to enable it to leave
the physical layer.
The physical layer router then receives the frame and check it to determine if there are
any errors in the frame.
At this point, the destination for the physical address has been established. Therefore,
the router will have to submit the packet to the IP. The PC-A’s MAC address is then
stored in the router’s memory routing table.
The IP search for the destination IP address to decide if the packet belongs to a
destination router.
The router shall be required to construct a frame which forwards it to PC-B, in this
case, the destination.
The destiny device will the reply using its physical address and the ARP response for
the router to have acquired all the necessities for it to respond.
The destination PC-B collects the frame where the PC carry out CRC checks to
determine whether there are any forms of errors. If the frame matches with the PC-B
frame, it indicates that there are no errors (Bosworth, et al., 2012), therefore, the
protocol can decide the following packet.
The destiny PC-B generate a new response PING response packet. Certainly, the
response echo will comprise the destination address and source address enabling for
the protocol to begin its journey all the way towards the other end.
The data link layer for PC-A will create a frame which comprises a source MAC
address, and destination address. A Cyclic redundancy check is attached to ascertain
that the destination workstation drops the frame in case it is destroyed.
The physical layer receives the frame from the data link layer and then convert the
frame from zeros to ones which are referred to as a digital signal to enable it to leave
the physical layer.
The physical layer router then receives the frame and check it to determine if there are
any errors in the frame.
At this point, the destination for the physical address has been established. Therefore,
the router will have to submit the packet to the IP. The PC-A’s MAC address is then
stored in the router’s memory routing table.
The IP search for the destination IP address to decide if the packet belongs to a
destination router.
The router shall be required to construct a frame which forwards it to PC-B, in this
case, the destination.
The destiny device will the reply using its physical address and the ARP response for
the router to have acquired all the necessities for it to respond.
The destination PC-B collects the frame where the PC carry out CRC checks to
determine whether there are any forms of errors. If the frame matches with the PC-B
frame, it indicates that there are no errors (Bosworth, et al., 2012), therefore, the
protocol can decide the following packet.
The destiny PC-B generate a new response PING response packet. Certainly, the
response echo will comprise the destination address and source address enabling for
the protocol to begin its journey all the way towards the other end.
Network and Communication 6
(Bosworth, et al., 2012)
Question three
1. EIGRP, OSPF, and RIP.
2. IGRP and RIPv1
3. Demonstration: EIGRP, OSPF, and RIP deploy classes addressing. In a classless
routing, subnet masks of a network are sent with its updates to enable VLSM masks.
In this case of this scenario, our network segment A and B are interconnected. The
masks are given as 255.255.255.0, right? Therefore, in the case of a classful rioting
(Bosworth, et al., 2012)
Question three
1. EIGRP, OSPF, and RIP.
2. IGRP and RIPv1
3. Demonstration: EIGRP, OSPF, and RIP deploy classes addressing. In a classless
routing, subnet masks of a network are sent with its updates to enable VLSM masks.
In this case of this scenario, our network segment A and B are interconnected. The
masks are given as 255.255.255.0, right? Therefore, in the case of a classful rioting
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network and Communication 7
protocol being adopted, these network segments have to take their default subnet
masks as 255.255.0.0 while the other will take 255.0.0. The subnet mask, which
interprets that wrong information will be routed. When using a classful protocol, it is
advisable to ensure that the subnet mask remains consistent throughout the entire
network.
4. The network address could be 10.10.10.0 in the WAN interface and 172.16.10.0 on
the Fa0/0 interface of the router on the left-hand side and 172.16.20.0 on the right-
hand side.
5. A merging parameter is essential at the time of routing. In the case of the case
mentioned above, OSPF will merge faster than to other routing protocols because
OSPF aspects allow small areas to assemble as individuals and their groups are taken
as a spate network by its own (Clarke, 2012).
Question Four
Data acknowledgment exchange of information
(Carrell, et al., 2013)
protocol being adopted, these network segments have to take their default subnet
masks as 255.255.0.0 while the other will take 255.0.0. The subnet mask, which
interprets that wrong information will be routed. When using a classful protocol, it is
advisable to ensure that the subnet mask remains consistent throughout the entire
network.
4. The network address could be 10.10.10.0 in the WAN interface and 172.16.10.0 on
the Fa0/0 interface of the router on the left-hand side and 172.16.20.0 on the right-
hand side.
5. A merging parameter is essential at the time of routing. In the case of the case
mentioned above, OSPF will merge faster than to other routing protocols because
OSPF aspects allow small areas to assemble as individuals and their groups are taken
as a spate network by its own (Clarke, 2012).
Question Four
Data acknowledgment exchange of information
(Carrell, et al., 2013)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network and Communication 8
The stop and wait to work together using automatic repeat query is defined as a control
procedure that is integrated to stop and wait for control flow protocol. In case of experiencing
an error at the receiving end, the message is discarded and send a NAK requesting to resend
the message again (Oriyano, 2014). When the message fails to reach the recipient, the
sending will often set a timer whereby at any point a frame is sent, a timer clock is set despite
the any NAK acknowledgment received or not, a frame is automatically resent once more.
Nonetheless, the timer introduces a challenge. For instance, the sending end can do
retransmission yet the recipient has already received the frame, which results in a duplicate to
the receiving end. Thus, to avoid such cases, frames and acknowledgments are put into
groups for instance frame as zeros and acknowledgment as ones (Viswanathan, et al., 2014).
The stop and wait to work together using automatic repeat query is defined as a control
procedure that is integrated to stop and wait for control flow protocol. In case of experiencing
an error at the receiving end, the message is discarded and send a NAK requesting to resend
the message again (Oriyano, 2014). When the message fails to reach the recipient, the
sending will often set a timer whereby at any point a frame is sent, a timer clock is set despite
the any NAK acknowledgment received or not, a frame is automatically resent once more.
Nonetheless, the timer introduces a challenge. For instance, the sending end can do
retransmission yet the recipient has already received the frame, which results in a duplicate to
the receiving end. Thus, to avoid such cases, frames and acknowledgments are put into
groups for instance frame as zeros and acknowledgment as ones (Viswanathan, et al., 2014).

Network and Communication 9
Bibliography
Alani & Mohammed, M., 2014. End-to-End Dataflow. In: Guide to OSI and TCP/IP Models. New York
City: Springer, pp. 15-17Carrell, J. L., Chappell, L. & Tittel, ., 2013. Internet Control Message Protocol.
In: Guide to TCP/IP. Boston: Cengage learning, pp. 293-295.
Clarke, G. E., 2012. CompTIA Network+ Certification Study Guide, 5th Edition (Exam N10-005). New
York: McGraw Hill Professional.
Goransson, Paul, Black & Chuck, 2014. Software Defined Networks: A Comprehensive Approach.
Edinburgh: Elsevier.
Grimes, B., 22 Apr 2016. CTS-D Certified Technology Specialist-Design Exam Guide. Pennsylvania
Plaza New York City: McGraw Hill Professional.
Lammle, T. & Swartz, J., 2013. CCNA Data Center - Introducing Cisco Data Center Networking Study
Guide. Hoboken: John Wiley & Sons.
Oriyano, 2014. Dissecting the TCP/IP Suite. In: CEH: Certified Ethical Hacker Version 8 Study Guide.
Hoboken: John Wiley & Sons, pp. 33-34.
Pyles, J., Carrell, J. L. & Tittel, E., 2016. Testing and Troubleshooting Sequences for ICMP. In: Guide to
TCP/IP: IPv6 and IPv4. Boston: Cengage Learning, p. 286.
Sriramoju, S. B., 2017. Basic Dataflow. In: NTRODUCTION TO BIG DATA: INFRASTRUCTURE AND
NETWORKING CONSIDERATIONS. s.l.:Horizon Books ( A Division of Ignited Minds Edutech P Ltd, pp.
72-74.
Viswanathan, Hiagarajan, Bhatnagar & Manav, 2014. Telecommunication Switching Systems and
Networks. In: Telecommunication Switching Systems and Networks. s.l.:PHI Learning Pvt. Ltd, pp.
433-436.
White, C., 2015. Data Communications and Computer Networks: A Business User's Approach.
Belmont: Cengage Learning.
Bibliography
Alani & Mohammed, M., 2014. End-to-End Dataflow. In: Guide to OSI and TCP/IP Models. New York
City: Springer, pp. 15-17Carrell, J. L., Chappell, L. & Tittel, ., 2013. Internet Control Message Protocol.
In: Guide to TCP/IP. Boston: Cengage learning, pp. 293-295.
Clarke, G. E., 2012. CompTIA Network+ Certification Study Guide, 5th Edition (Exam N10-005). New
York: McGraw Hill Professional.
Goransson, Paul, Black & Chuck, 2014. Software Defined Networks: A Comprehensive Approach.
Edinburgh: Elsevier.
Grimes, B., 22 Apr 2016. CTS-D Certified Technology Specialist-Design Exam Guide. Pennsylvania
Plaza New York City: McGraw Hill Professional.
Lammle, T. & Swartz, J., 2013. CCNA Data Center - Introducing Cisco Data Center Networking Study
Guide. Hoboken: John Wiley & Sons.
Oriyano, 2014. Dissecting the TCP/IP Suite. In: CEH: Certified Ethical Hacker Version 8 Study Guide.
Hoboken: John Wiley & Sons, pp. 33-34.
Pyles, J., Carrell, J. L. & Tittel, E., 2016. Testing and Troubleshooting Sequences for ICMP. In: Guide to
TCP/IP: IPv6 and IPv4. Boston: Cengage Learning, p. 286.
Sriramoju, S. B., 2017. Basic Dataflow. In: NTRODUCTION TO BIG DATA: INFRASTRUCTURE AND
NETWORKING CONSIDERATIONS. s.l.:Horizon Books ( A Division of Ignited Minds Edutech P Ltd, pp.
72-74.
Viswanathan, Hiagarajan, Bhatnagar & Manav, 2014. Telecommunication Switching Systems and
Networks. In: Telecommunication Switching Systems and Networks. s.l.:PHI Learning Pvt. Ltd, pp.
433-436.
White, C., 2015. Data Communications and Computer Networks: A Business User's Approach.
Belmont: Cengage Learning.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





