SIT202 Computer Networks: NAT Configuration and Protocols
VerifiedAdded on 2023/06/07
|8
|1411
|461
Report
AI Summary
This report provides a detailed analysis of Network Address Translation (NAT) and various routing protocols within computer networks. It explains how NAT enables multiple users to access the internet using a single public IP address, detailing the packet flow and router operations involved. The report further explores the Address Resolution Protocol (ARP) and its role in discovering layer two addresses. It discusses the functionality of Routing Information Protocol (RIP), Open Shortest Path First (OSPF), and Border Gateway Protocol (BGP), comparing their characteristics and suitability for different network scenarios. The report also touches on selective acknowledgement in TCP to identify and retransmit lost packets, enhancing the reliability of network communication. Desklib offers a wealth of study tools and solved assignments for students seeking to deepen their understanding of computer networks.

NETWORK ASSIGNMENT
Name :
Course Code :
Date of Submission :
Name :
Course Code :
Date of Submission :
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
QUESTION 1:
Overall Explanation
NAT is a property in a router which allow clients to access services through public IP address in
a network. This eliminates the need of having a separate domain name for a network
If a packet is sent from PC-1 (192.168.10.7/24) connected to the switch through port 1020, the
packet will be routed to the default gateway (192.168.10.1/24) of the router. A router with a
NAT loopback feature detects the incoming packet as 209.165.200.226/27 and is the interface of
its WAN network. It determines the destination of the packet depending on the port forwarding
rule. Data is then directed to the host address remote server that receives the packets. If the
DNAT rule is not applicable the router will drop the packet. An ICMP destination unreachable is
replied. If the rule is still there then the router rewrites the source IP address. The client
(192.168.10.7/24) sends the packets as incoming from (192.168.10.1/24) then the server receives
the packet as incoming from 209.165.200.226/27. When the request is replied by the server the
process is repeated. This process is identical for external senders. Thus this is a two way
communication.
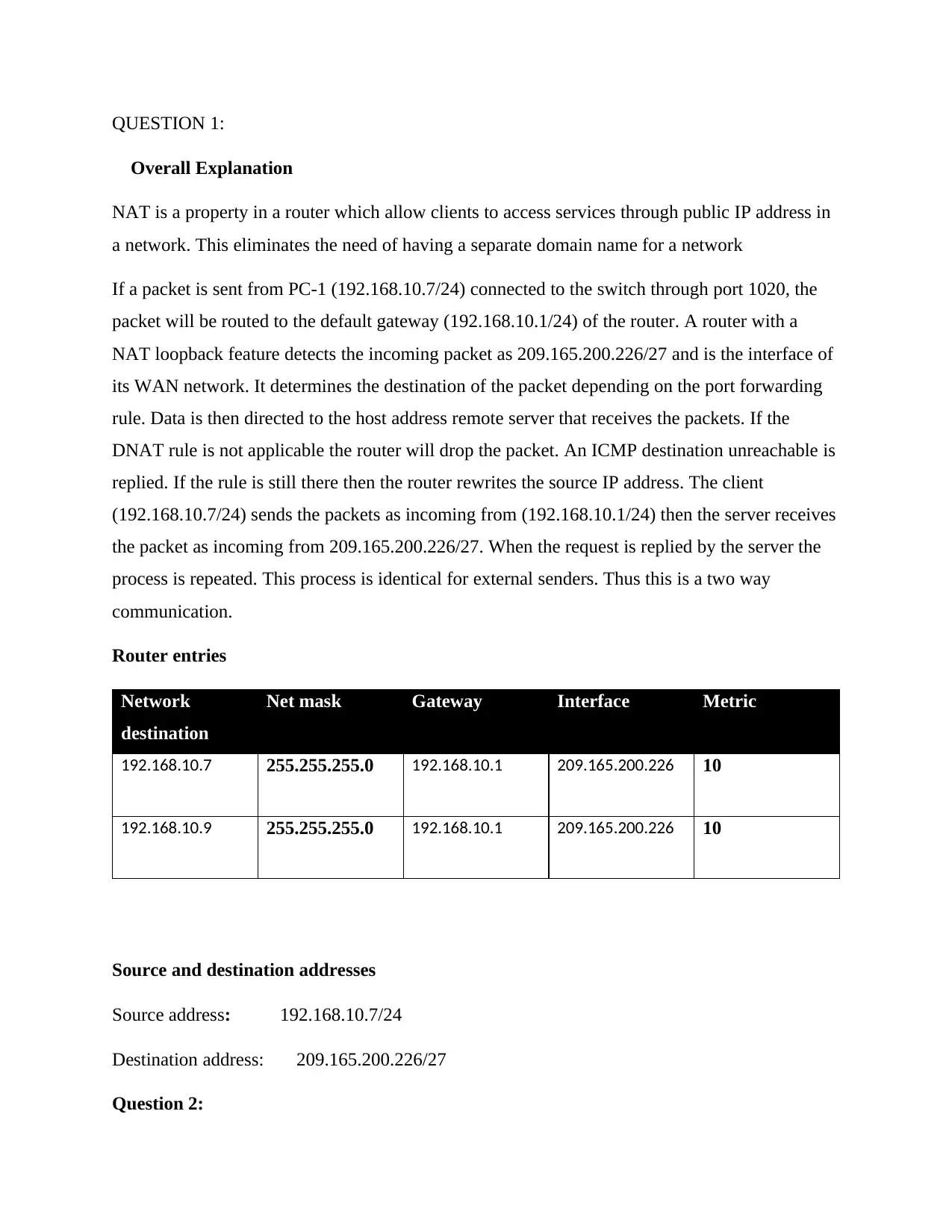
Router entries
Network
destination
Net mask Gateway Interface Metric
192.168.10.7 255.255.255.0 192.168.10.1 209.165.200.226 10
192.168.10.9 255.255.255.0 192.168.10.1 209.165.200.226 10
Source and destination addresses
Source address: 192.168.10.7/24
Destination address: 209.165.200.226/27
Question 2:
Overall Explanation
NAT is a property in a router which allow clients to access services through public IP address in
a network. This eliminates the need of having a separate domain name for a network
If a packet is sent from PC-1 (192.168.10.7/24) connected to the switch through port 1020, the
packet will be routed to the default gateway (192.168.10.1/24) of the router. A router with a
NAT loopback feature detects the incoming packet as 209.165.200.226/27 and is the interface of
its WAN network. It determines the destination of the packet depending on the port forwarding
rule. Data is then directed to the host address remote server that receives the packets. If the
DNAT rule is not applicable the router will drop the packet. An ICMP destination unreachable is
replied. If the rule is still there then the router rewrites the source IP address. The client
(192.168.10.7/24) sends the packets as incoming from (192.168.10.1/24) then the server receives
the packet as incoming from 209.165.200.226/27. When the request is replied by the server the
process is repeated. This process is identical for external senders. Thus this is a two way
communication.
Router entries
Network
destination
Net mask Gateway Interface Metric
192.168.10.7 255.255.255.0 192.168.10.1 209.165.200.226 10
192.168.10.9 255.255.255.0 192.168.10.1 209.165.200.226 10
Source and destination addresses
Source address: 192.168.10.7/24
Destination address: 209.165.200.226/27
Question 2:

1:
First PC-A (200.10.5.70/28) initiates the session by sending a broadcast ARP packet. The
address resolution packet is used in discovering the layer two address that is linked to layer three
addresses in the router. The broadcast then instructs the router to send the packet to all ports that
are connected to it. Computer PC-B (200.10.4.59/27) within layer three then responds with a
unicast ARP reply. The results are captured so that they can be looked up later. This makes the
ARP not to be sent frequently. This creates an ICMP request that is crafted. The source PC-A
(200.10.5.70/28) address will be originating computers’ ether address. The destination addresses
in the router and PC-B (200.10.4.59/27) will then be revealed from ARP. The packet is then sent
to the router through a cable Fa0/0 (200.10.5.70/28). The router then examines the destination
address of PC-B (200.10.4.59/27) and looks for it from the CAM table, this specifies the physical
port in the ether address. The packet is then transmitted through the wire to the correct physical
ports. When PC-B (200.10.4.59/27) computer receives the packet, it first examines the address
and makes sure that it is similar as that one in the physical interface. If the address is similar it
then checks if PC-B (200.10.4.59/27) matches with the address in layer 3 of the router as
assigned in the physical interface. If the packet matches, it is handled by upper layer protocols
(Pigeon, 2014) and if there is no match the packet is then dropped. For the ICMP reply, things
work in the same way, except that the responding computer doesn't need to send an ARP request.
The source computer receives reply from the connected computer if the pinging process is
successful.
2:
When PC-A (200.10.5.70/28) sends packet with the local network, PC-B (200.10.4.59/27) listens
to the incoming signal MAC address. If there is no answer within the network then the packet is
directed to the default gateway and configured in IP stack of the sending host. If the destination
address has not found any MAC address then the network is remote. If an address exits then the
network is local.
First PC-A (200.10.5.70/28) initiates the session by sending a broadcast ARP packet. The
address resolution packet is used in discovering the layer two address that is linked to layer three
addresses in the router. The broadcast then instructs the router to send the packet to all ports that
are connected to it. Computer PC-B (200.10.4.59/27) within layer three then responds with a
unicast ARP reply. The results are captured so that they can be looked up later. This makes the
ARP not to be sent frequently. This creates an ICMP request that is crafted. The source PC-A
(200.10.5.70/28) address will be originating computers’ ether address. The destination addresses
in the router and PC-B (200.10.4.59/27) will then be revealed from ARP. The packet is then sent
to the router through a cable Fa0/0 (200.10.5.70/28). The router then examines the destination
address of PC-B (200.10.4.59/27) and looks for it from the CAM table, this specifies the physical
port in the ether address. The packet is then transmitted through the wire to the correct physical
ports. When PC-B (200.10.4.59/27) computer receives the packet, it first examines the address
and makes sure that it is similar as that one in the physical interface. If the address is similar it
then checks if PC-B (200.10.4.59/27) matches with the address in layer 3 of the router as
assigned in the physical interface. If the packet matches, it is handled by upper layer protocols
(Pigeon, 2014) and if there is no match the packet is then dropped. For the ICMP reply, things
work in the same way, except that the responding computer doesn't need to send an ARP request.
The source computer receives reply from the connected computer if the pinging process is
successful.
2:
When PC-A (200.10.5.70/28) sends packet with the local network, PC-B (200.10.4.59/27) listens
to the incoming signal MAC address. If there is no answer within the network then the packet is
directed to the default gateway and configured in IP stack of the sending host. If the destination
address has not found any MAC address then the network is remote. If an address exits then the
network is local.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3:
The source machine MAC address is used in encapsulation. This is because at the source
machine, the domain name is converted into IP number. The target IP number is loaded in the
packet from the routing table. Then the MAC address of the next router is obtained through the
Arp request. The frame is then moved to the MAC address. This process continues until the last
router gets data. The router then identifies the address of the destination host. The last router of
the network is the one that knows the MAC address of the target machine.
4: Once the last router finds the MAC address of the destination computer, it determines the
shortest distance that it will use to send data to the destination host. The router then uses the
public IP address to transmit data to the host computer.
The source machine MAC address is used in encapsulation. This is because at the source
machine, the domain name is converted into IP number. The target IP number is loaded in the
packet from the routing table. Then the MAC address of the next router is obtained through the
Arp request. The frame is then moved to the MAC address. This process continues until the last
router gets data. The router then identifies the address of the destination host. The last router of
the network is the one that knows the MAC address of the target machine.
4: Once the last router finds the MAC address of the destination computer, it determines the
shortest distance that it will use to send data to the destination host. The router then uses the
public IP address to transmit data to the host computer.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 3
1:
Routing protocols
Routing information protocol (RIP)
Open Shortest Path First (OSPF)
2: Border Gateway protocol (BGP).
3:
RIP - this dynamic routing protocol adds policies to the system and selects the best route in the
network for packets to flow in. The routing protocol employs use of hop-count metric. This
prevents routing loops during packet transmission. It also implements route poisoning. This
prevents packets from being transmitted in incorrect paths (Thorenoor, 2010). The tables are
also updated after thirty seconds. This improves the working speed of the router. It is most
perfect because it can easily be configured
OSPF - This tests status of the links of its neighbors before it sends the packets. It stabilizes the
networked before it is used. It uses the IP addresses directly, does not rely on the TCP. It also
calculates the shortest route to be used in the network basing on the cost of the route, not living
behind bandwidth. It is a more reliable routing protocol that can easily be implemented (Black,
2013).
BGP - it uses the TCP protocol while the network requires usage of IP protocols. It is mostly
used in autonomous system, this makes it unfavorable to be used in the network. The routing
protocol also does not allow automatic configuration of the routers thus they are configured
manually
4:
10.10.10.1/24
10.10.10.5/24
1:
Routing protocols
Routing information protocol (RIP)
Open Shortest Path First (OSPF)
2: Border Gateway protocol (BGP).
3:
RIP - this dynamic routing protocol adds policies to the system and selects the best route in the
network for packets to flow in. The routing protocol employs use of hop-count metric. This
prevents routing loops during packet transmission. It also implements route poisoning. This
prevents packets from being transmitted in incorrect paths (Thorenoor, 2010). The tables are
also updated after thirty seconds. This improves the working speed of the router. It is most
perfect because it can easily be configured
OSPF - This tests status of the links of its neighbors before it sends the packets. It stabilizes the
networked before it is used. It uses the IP addresses directly, does not rely on the TCP. It also
calculates the shortest route to be used in the network basing on the cost of the route, not living
behind bandwidth. It is a more reliable routing protocol that can easily be implemented (Black,
2013).
BGP - it uses the TCP protocol while the network requires usage of IP protocols. It is mostly
used in autonomous system, this makes it unfavorable to be used in the network. The routing
protocol also does not allow automatic configuration of the routers thus they are configured
manually
4:
10.10.10.1/24
10.10.10.5/24
5:
RIP is set to use two IP addresses with 32 bit while OSPF uses routes that are based on the
telnet. OSPF uses multicasting while RIP uses commands in the transfer of network signals.
BGP uses TCP to transfer the signals while OSPF and RIP uses IP address for communication
between the routers. This makes OSPF and RIP suitable for the network
Question 4:
RIP is set to use two IP addresses with 32 bit while OSPF uses routes that are based on the
telnet. OSPF uses multicasting while RIP uses commands in the transfer of network signals.
BGP uses TCP to transfer the signals while OSPF and RIP uses IP address for communication
between the routers. This makes OSPF and RIP suitable for the network
Question 4:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

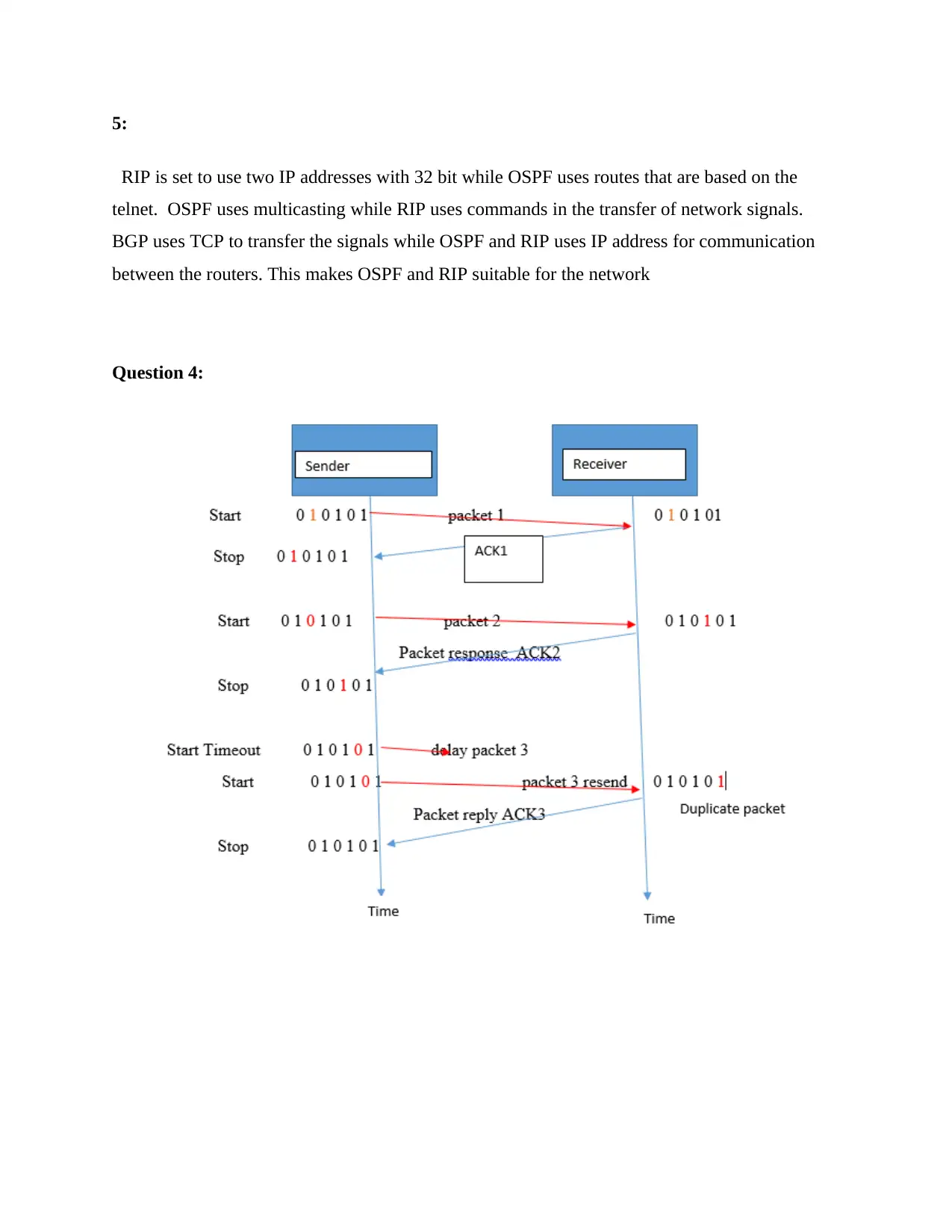
d.
As in the above figure, selective acknowledgement will use ACK values in TCP to show packet
loss. The packets that are lost during transmission are shown by suck TCP heads. Typically,
duplicate acknowledgements means one or more packets have been lost during the
communication process. They always show the symptoms of packet loss. Mostly when three
duplicate acknowledgements are received by the receiver, it retransmit the missing packet before
the timer expires (Campbell, 2014). This can be called faster transmission. Several duplicate
acknowledgment are used for single packet.
As in the above figure, selective acknowledgement will use ACK values in TCP to show packet
loss. The packets that are lost during transmission are shown by suck TCP heads. Typically,
duplicate acknowledgements means one or more packets have been lost during the
communication process. They always show the symptoms of packet loss. Mostly when three
duplicate acknowledgements are received by the receiver, it retransmit the missing packet before
the timer expires (Campbell, 2014). This can be called faster transmission. Several duplicate
acknowledgment are used for single packet.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Black, U.D., 2013. IP routing protocols: RIP, OSPF, BGP, PNNI, and Cisco routing protocols.
Prentice Hall Professional.
Campbell, M.J., Finn, D.J., Tucker, G.K., Vahey, M.D. and Vedder, R.W., Hughes Aircraft Co,
2014. Data-flow multiprocessor architecture with three dimensional multistage interconnection
network for efficient signal and data processing. U.S. Patent 5,021,947.
Pigeon, N., Sagem Communications SAS, 2014. Method and device for allocating MAC
addresses in a carrier-current communication network. U.S. Patent 8,842,697.
Thorenoor, S.G., 2010, April. Dynamic routing protocol implementation decision between
EIGRP, OSPF and RIP based on technical background using OPNET modeler. In Computer and
Network Technology (ICCNT), 2010 Second International Conference on (pp. 191-195). IEEE.
Black, U.D., 2013. IP routing protocols: RIP, OSPF, BGP, PNNI, and Cisco routing protocols.
Prentice Hall Professional.
Campbell, M.J., Finn, D.J., Tucker, G.K., Vahey, M.D. and Vedder, R.W., Hughes Aircraft Co,
2014. Data-flow multiprocessor architecture with three dimensional multistage interconnection
network for efficient signal and data processing. U.S. Patent 5,021,947.
Pigeon, N., Sagem Communications SAS, 2014. Method and device for allocating MAC
addresses in a carrier-current communication network. U.S. Patent 8,842,697.
Thorenoor, S.G., 2010, April. Dynamic routing protocol implementation decision between
EIGRP, OSPF and RIP based on technical background using OPNET modeler. In Computer and
Network Technology (ICCNT), 2010 Second International Conference on (pp. 191-195). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





