SIT703 Advanced Digital Forensics: A Detailed Case Investigation
VerifiedAdded on 2023/06/07
|35
|2867
|282
Case Study
AI Summary
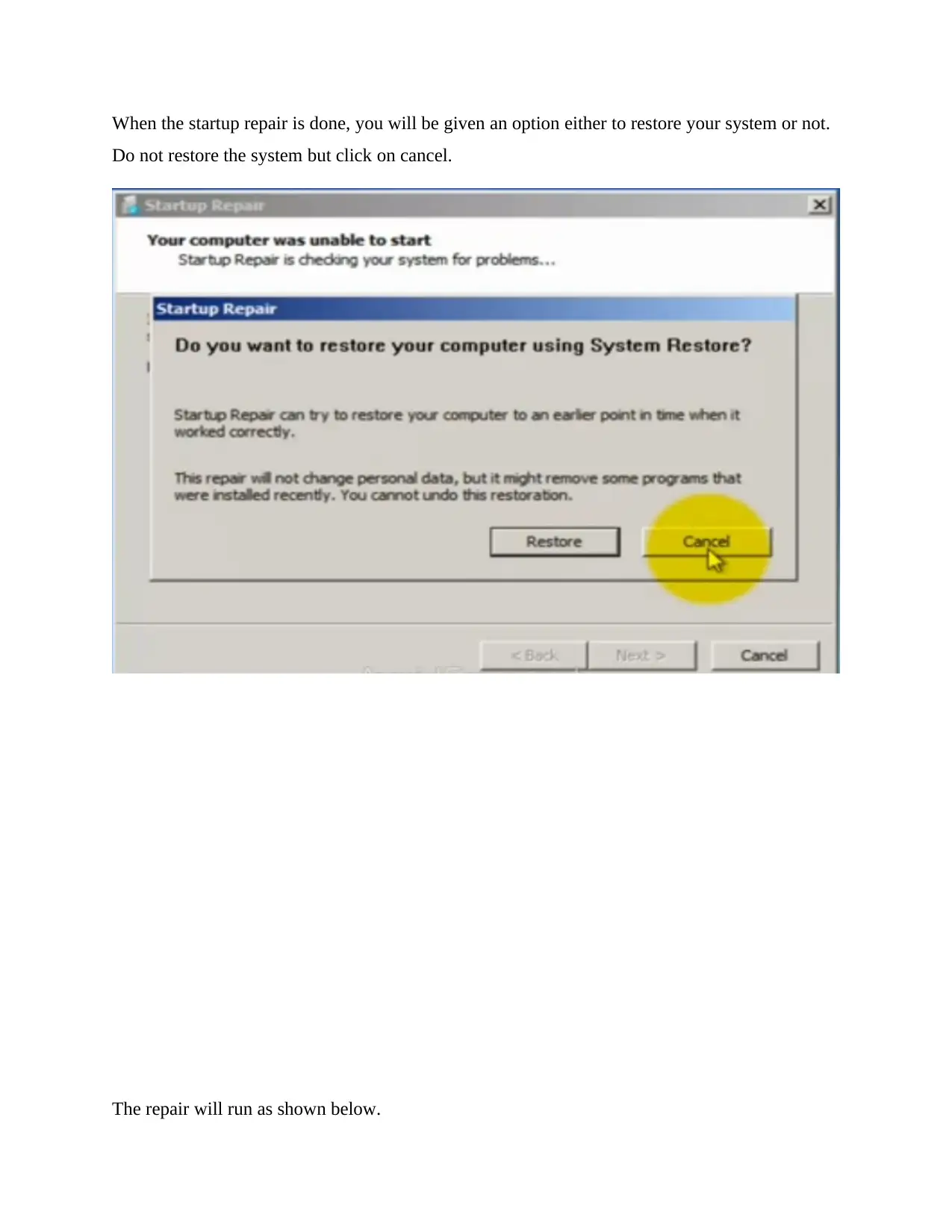
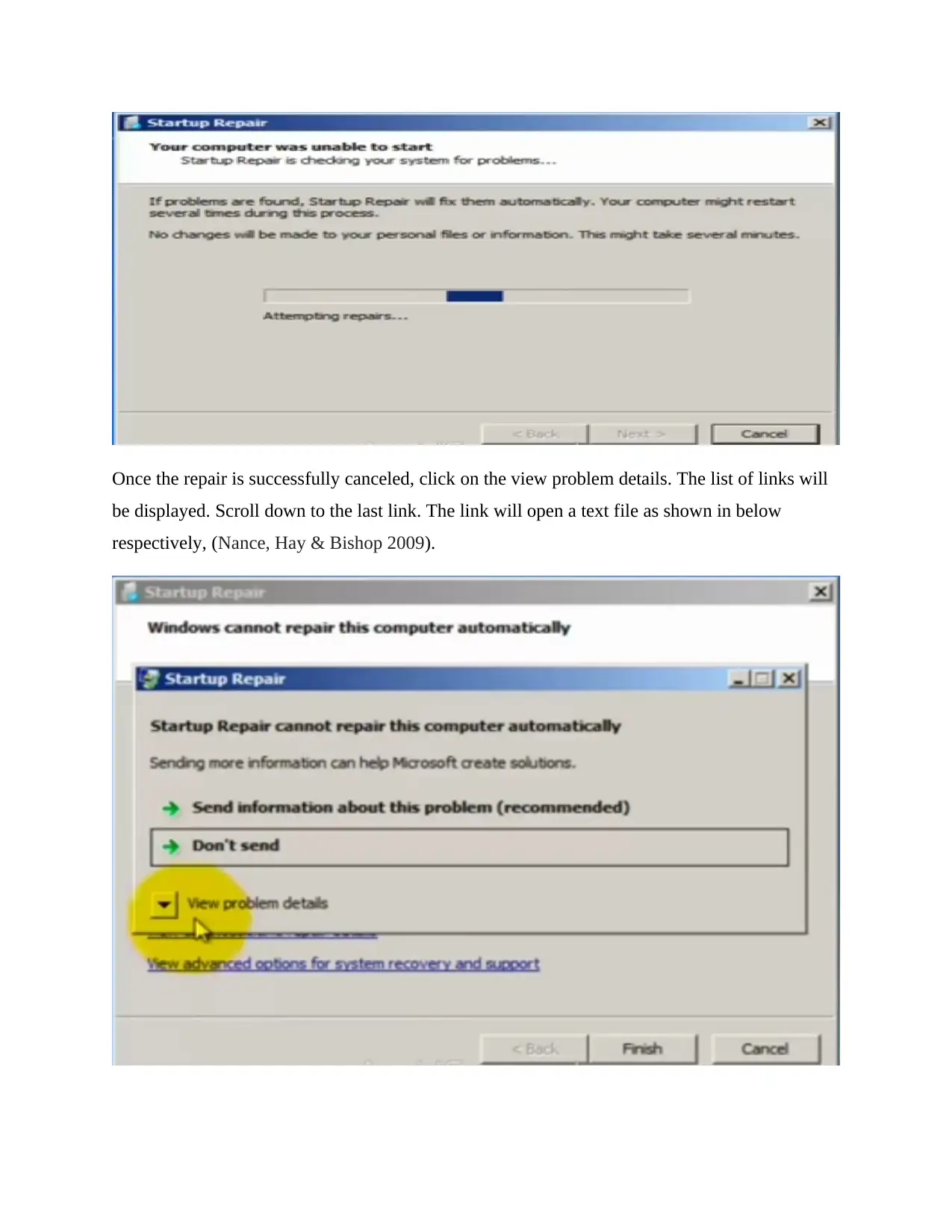
This case study delves into a computer crime involving unauthorized access to a user's laptop. It explores methods of password cracking, including physical access techniques and the use of tools like Ettercap for sniffing credentials. The investigation covers the identification of suspicious programs through registry analysis and the utilization of tools like Ophcrack with rainbow tables to crack password hashes. Analysis of Windows event logs, including security, application, setup, system, and forwarded event logs, is crucial in determining the timeline of unauthorized access, identifying created accounts, and understanding actions performed. The report also discusses techniques for scanning rootkits, repairing log files, and securing Windows systems against unauthorized access, highlighting the importance of log file analysis in tracking events and rectifying security breaches. Finally, the study concludes by emphasizing the critical role of digital forensics in investigating computer crimes and utilizing stored information in log files to track events and rectify problems.
1 out of 35









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)