Consolidation Security Project: Skillage IT Network Business Plan
VerifiedAdded on 2021/01/02
|20
|1570
|422
Project
AI Summary
This project report presents a comprehensive network security plan for Skillage IT, aiming to enhance operational control and improve data sharing. The report outlines a detailed business plan, specifying objectives such as securing the network and improving operational efficiency. It includes problem specifications, a work schedule with cost breakdowns for hardware and software, and pricing details. Technical aspects covered involve network design, directory structure, server specifications, and security policies. The project also addresses testing, maintenance, and user documentation. Furthermore, it includes a financial plan, project acceptance form, and discusses future enhancements. The conclusion emphasizes the importance of the networking plan for Skillage IT's business activities, supported by a comprehensive list of references from books, journals, and online resources. The project seeks to implement a secure and efficient network infrastructure to support Skillage IT's business objectives and future growth.

CONSOLIDATION
SECURITY PROJECT
SECURITY PROJECT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
EXECUTIVE SUMMARY.............................................................................................................1
INTRODUCTION...........................................................................................................................2
BUSINESS PLAN...........................................................................................................................2
Objective.................................................................................................................................2
Problem specification.............................................................................................................2
Work Schedule.......................................................................................................................2
Gantt chart:.............................................................................................................................3
A Network design and supporting documents........................................................................4
B. Directory structure.............................................................................................................5
C. Server Specification...........................................................................................................7
D. Server build task list template...........................................................................................9
E, Server test plan...................................................................................................................9
F. Maintenance plan of server..............................................................................................10
G. Router specification.........................................................................................................10
H. Security Policy and plan..................................................................................................11
I. User Documentation..........................................................................................................12
J. Project sign off..................................................................................................................13
Ongoing Maintenance Support.............................................................................................13
Financial plan.......................................................................................................................13
Pricing details.......................................................................................................................14
Professionals service fee.......................................................................................................14
Project acceptance form.......................................................................................................14
Testing..................................................................................................................................15
Further Enhancement............................................................................................................15
CONCLUSION..............................................................................................................................15
REFERENCES..............................................................................................................................17
EXECUTIVE SUMMARY.............................................................................................................1
INTRODUCTION...........................................................................................................................2
BUSINESS PLAN...........................................................................................................................2
Objective.................................................................................................................................2
Problem specification.............................................................................................................2
Work Schedule.......................................................................................................................2
Gantt chart:.............................................................................................................................3
A Network design and supporting documents........................................................................4
B. Directory structure.............................................................................................................5
C. Server Specification...........................................................................................................7
D. Server build task list template...........................................................................................9
E, Server test plan...................................................................................................................9
F. Maintenance plan of server..............................................................................................10
G. Router specification.........................................................................................................10
H. Security Policy and plan..................................................................................................11
I. User Documentation..........................................................................................................12
J. Project sign off..................................................................................................................13
Ongoing Maintenance Support.............................................................................................13
Financial plan.......................................................................................................................13
Pricing details.......................................................................................................................14
Professionals service fee.......................................................................................................14
Project acceptance form.......................................................................................................14
Testing..................................................................................................................................15
Further Enhancement............................................................................................................15
CONCLUSION..............................................................................................................................15
REFERENCES..............................................................................................................................17

EXECUTIVE SUMMARY
Better operational control as well as records of all the transactional activities are required to
have appropriate plan for the activities. In the present report there will be discussion based on
operational plans and the setting up and network system which will be helpful to have
appropriate business practices of Skillage IT.
1
Better operational control as well as records of all the transactional activities are required to
have appropriate plan for the activities. In the present report there will be discussion based on
operational plans and the setting up and network system which will be helpful to have
appropriate business practices of Skillage IT.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Connecting all units of business with a motive to have satisfactory information relevant
with activities and performance made during a period. Creating a network system will assist a
helpful approach which brings proper administration over industrial operations. Skillage IT is
planning to improve its networking system within organisation which requires an accurate
business plan. Application of various technical tools which will enhance networking and
communication framework in entity. Report consists of all the tasks and activities which are
needed to be implicated by professionals that will be used for proper monitoring and execution
of business activities.
BUSINESS PLAN
Objective
Motivation of business is for developing a networking system which is within premises
which will be highly secured and protected from external influences. It will be incorporated with
well versed techniques, VPN connection, Server, modem and upgraded technologies that will
bring enhancement to operational activities. Data sharing in Skillage IT will be improved will be
convenient to professionals in sharing data with proper confidentiality.
Problem specification
To manage the operation in manufacturing, warehousing and distribution of the
organisation which requires proper administration.
Controlling staff, agent’s offices with respect to bring increment in the efficiency of
business.
Raining the sales at the target of $25 million per annum.
Retaining the 5% growth every year for upcoming 5 years.
Configuration the network system which will help in balancing operations as well as
managing tasks.
Work Schedule
Task
Mode Task Name Duration Start Finish Predecessors
Auto
Scheduled User Configuration 2 days Mon 20-08-
18 Tue 21-08-18
Auto Network Configuration 4 days Wed 22-08- Mon 27-08- 1
2
Connecting all units of business with a motive to have satisfactory information relevant
with activities and performance made during a period. Creating a network system will assist a
helpful approach which brings proper administration over industrial operations. Skillage IT is
planning to improve its networking system within organisation which requires an accurate
business plan. Application of various technical tools which will enhance networking and
communication framework in entity. Report consists of all the tasks and activities which are
needed to be implicated by professionals that will be used for proper monitoring and execution
of business activities.
BUSINESS PLAN
Objective
Motivation of business is for developing a networking system which is within premises
which will be highly secured and protected from external influences. It will be incorporated with
well versed techniques, VPN connection, Server, modem and upgraded technologies that will
bring enhancement to operational activities. Data sharing in Skillage IT will be improved will be
convenient to professionals in sharing data with proper confidentiality.
Problem specification
To manage the operation in manufacturing, warehousing and distribution of the
organisation which requires proper administration.
Controlling staff, agent’s offices with respect to bring increment in the efficiency of
business.
Raining the sales at the target of $25 million per annum.
Retaining the 5% growth every year for upcoming 5 years.
Configuration the network system which will help in balancing operations as well as
managing tasks.
Work Schedule
Task
Mode Task Name Duration Start Finish Predecessors
Auto
Scheduled User Configuration 2 days Mon 20-08-
18 Tue 21-08-18
Auto Network Configuration 4 days Wed 22-08- Mon 27-08- 1
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
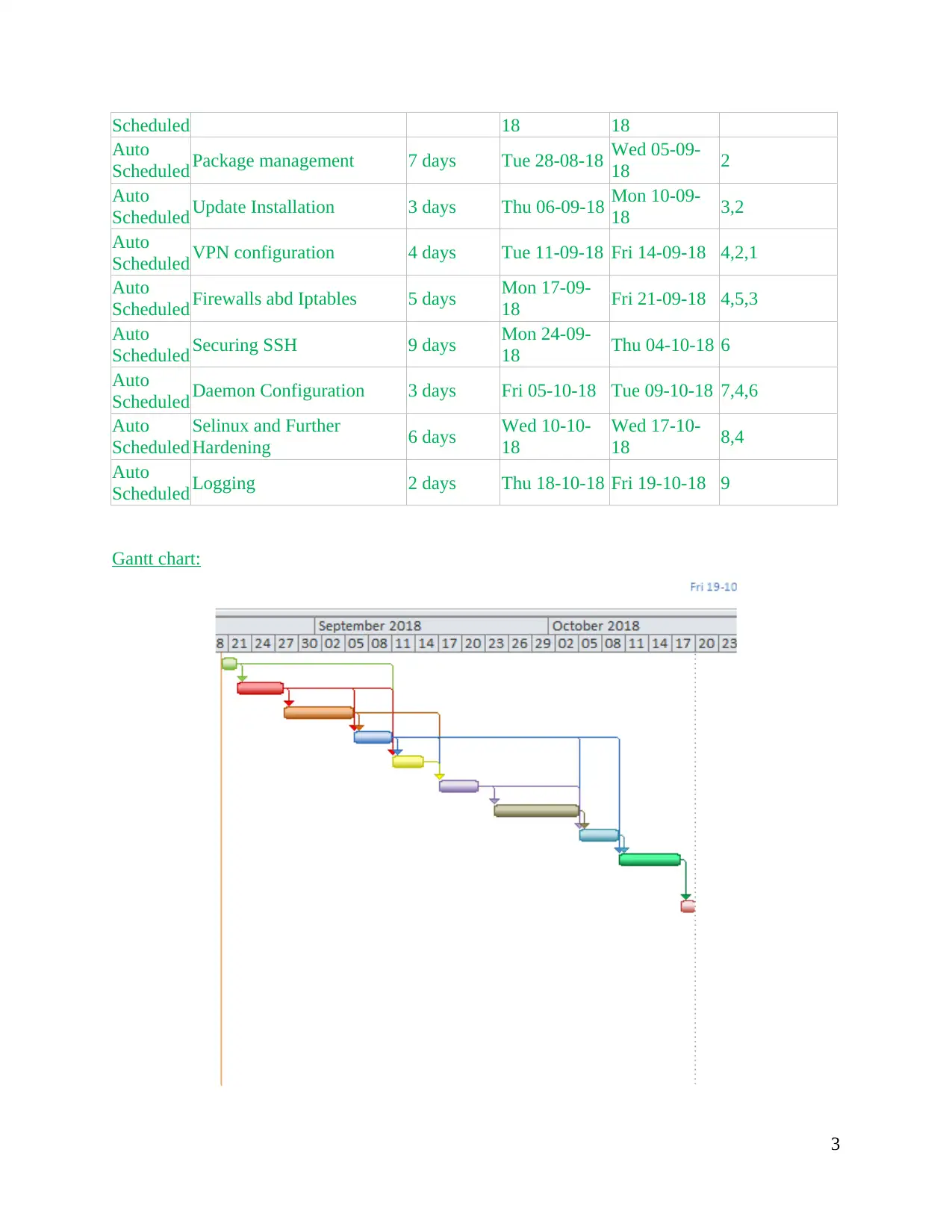
Scheduled 18 18
Auto
Scheduled Package management 7 days Tue 28-08-18 Wed 05-09-
18 2
Auto
Scheduled Update Installation 3 days Thu 06-09-18 Mon 10-09-
18 3,2
Auto
Scheduled VPN configuration 4 days Tue 11-09-18 Fri 14-09-18 4,2,1
Auto
Scheduled Firewalls abd Iptables 5 days Mon 17-09-
18 Fri 21-09-18 4,5,3
Auto
Scheduled Securing SSH 9 days Mon 24-09-
18 Thu 04-10-18 6
Auto
Scheduled Daemon Configuration 3 days Fri 05-10-18 Tue 09-10-18 7,4,6
Auto
Scheduled
Selinux and Further
Hardening 6 days Wed 10-10-
18
Wed 17-10-
18 8,4
Auto
Scheduled Logging 2 days Thu 18-10-18 Fri 19-10-18 9
Gantt chart:
3
Auto
Scheduled Package management 7 days Tue 28-08-18 Wed 05-09-
18 2
Auto
Scheduled Update Installation 3 days Thu 06-09-18 Mon 10-09-
18 3,2
Auto
Scheduled VPN configuration 4 days Tue 11-09-18 Fri 14-09-18 4,2,1
Auto
Scheduled Firewalls abd Iptables 5 days Mon 17-09-
18 Fri 21-09-18 4,5,3
Auto
Scheduled Securing SSH 9 days Mon 24-09-
18 Thu 04-10-18 6
Auto
Scheduled Daemon Configuration 3 days Fri 05-10-18 Tue 09-10-18 7,4,6
Auto
Scheduled
Selinux and Further
Hardening 6 days Wed 10-10-
18
Wed 17-10-
18 8,4
Auto
Scheduled Logging 2 days Thu 18-10-18 Fri 19-10-18 9
Gantt chart:
3

A Network design and supporting documents
Designing a suitable data set will require effective methods and techniques to implicate
proper transactional activities. Consisting all necessary information as well as physical and
network design which will circulate information all over offices and data centres. Skillage IT
needed to design routing protocols on which data transaction and communication among several
units must have confidentiality as well as there will be no chances of any manipulating
information. Developing networking chain in business environment requires speed and cabling
types which swift the transactional activities. Including an IP system brings control over
accessibility as well as it creates a proxy wall which protects network system from malware and
viruses (Network Documentation Best Practices: What to Create & Why, 2016). Similarly, IP
address allocation table will effectively control industrial operations. It consists of registering
network on private networking system such as IPV4 and IPV6. Moreover, there has been
requirement of various network documentation such as:
Wi-Fi diagram:
4
Designing a suitable data set will require effective methods and techniques to implicate
proper transactional activities. Consisting all necessary information as well as physical and
network design which will circulate information all over offices and data centres. Skillage IT
needed to design routing protocols on which data transaction and communication among several
units must have confidentiality as well as there will be no chances of any manipulating
information. Developing networking chain in business environment requires speed and cabling
types which swift the transactional activities. Including an IP system brings control over
accessibility as well as it creates a proxy wall which protects network system from malware and
viruses (Network Documentation Best Practices: What to Create & Why, 2016). Similarly, IP
address allocation table will effectively control industrial operations. It consists of registering
network on private networking system such as IPV4 and IPV6. Moreover, there has been
requirement of various network documentation such as:
Wi-Fi diagram:
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
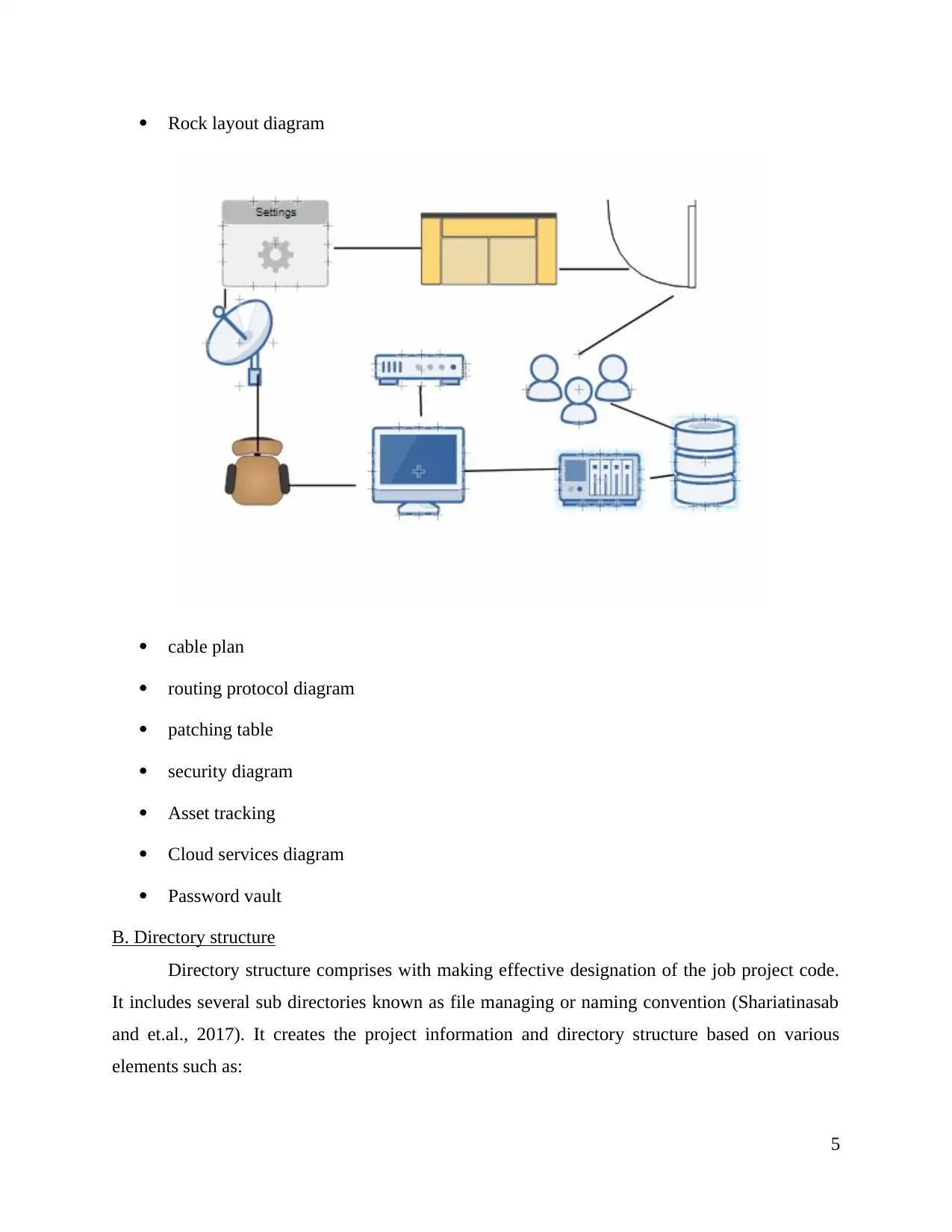
Rock layout diagram
cable plan
routing protocol diagram
patching table
security diagram
Asset tracking
Cloud services diagram
Password vault
B. Directory structure
Directory structure comprises with making effective designation of the job project code.
It includes several sub directories known as file managing or naming convention (Shariatinasab
and et.al., 2017). It creates the project information and directory structure based on various
elements such as:
5
cable plan
routing protocol diagram
patching table
security diagram
Asset tracking
Cloud services diagram
Password vault
B. Directory structure
Directory structure comprises with making effective designation of the job project code.
It includes several sub directories known as file managing or naming convention (Shariatinasab
and et.al., 2017). It creates the project information and directory structure based on various
elements such as:
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
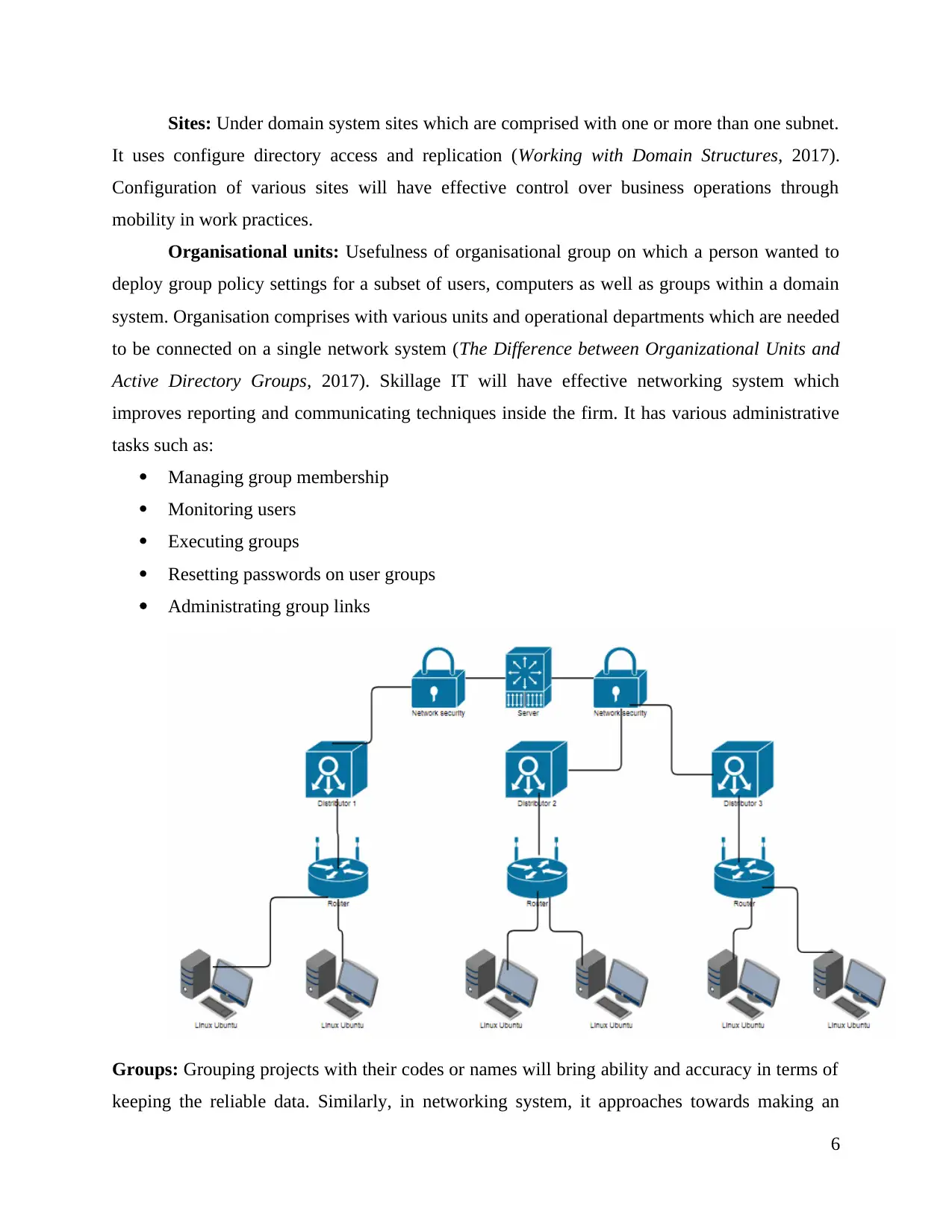
Sites: Under domain system sites which are comprised with one or more than one subnet.
It uses configure directory access and replication (Working with Domain Structures, 2017).
Configuration of various sites will have effective control over business operations through
mobility in work practices.
Organisational units: Usefulness of organisational group on which a person wanted to
deploy group policy settings for a subset of users, computers as well as groups within a domain
system. Organisation comprises with various units and operational departments which are needed
to be connected on a single network system (The Difference between Organizational Units and
Active Directory Groups, 2017). Skillage IT will have effective networking system which
improves reporting and communicating techniques inside the firm. It has various administrative
tasks such as:
Managing group membership
Monitoring users
Executing groups
Resetting passwords on user groups
Administrating group links
Groups: Grouping projects with their codes or names will bring ability and accuracy in terms of
keeping the reliable data. Similarly, in networking system, it approaches towards making an
6
It uses configure directory access and replication (Working with Domain Structures, 2017).
Configuration of various sites will have effective control over business operations through
mobility in work practices.
Organisational units: Usefulness of organisational group on which a person wanted to
deploy group policy settings for a subset of users, computers as well as groups within a domain
system. Organisation comprises with various units and operational departments which are needed
to be connected on a single network system (The Difference between Organizational Units and
Active Directory Groups, 2017). Skillage IT will have effective networking system which
improves reporting and communicating techniques inside the firm. It has various administrative
tasks such as:
Managing group membership
Monitoring users
Executing groups
Resetting passwords on user groups
Administrating group links
Groups: Grouping projects with their codes or names will bring ability and accuracy in terms of
keeping the reliable data. Similarly, in networking system, it approaches towards making an
6

effective and active directory group (El-Gheriani and et.al., 2017). Usefulness of this technique
in assigning permission to industrial resources for initiating operations. Putting users into small
group on which they will become able to imply with groups to an access control list (ACL).
Requiring the AD groups mirror as per organisational hierarchy such as finance group, legal,
marketing etc.
C. Server Specification
Demonstrating fruitful server location and specific information there are some factors
which are needed to be administered by professionals of Skillage IT. Server specification will
bring effective control over network system implications in business. Thus, there are several
components which are needed to be considered by professionals such as:
Number and location of virtual and physical servers: Physical servers are mainly
incorporated with physical devices such as operating system, windows and Linux which runs
through a device. Therefore, these are termed as Physical server. Skillage IT needed to have
appropriate operating system in each device as well as which consist security keys. It will be
remove chances of data break or losing confidential data (Physical server vs Virtual server,
2016). On the other side, virtual server is also known as virtual machines of VPA system.
Operation of a VPA through operating system that simulates an operating environment. It
virtually creates devices of machines and run them.
Roles of Servers: Configuring role of a server is for facilitating appropriate network
coverage in a premise (Mokhlespour Esfahani and et.al., 2017). It ascertains software
components that allows server in performing specific operations for users and relevant computer-
based networks.
Approval sign off a document:
7
in assigning permission to industrial resources for initiating operations. Putting users into small
group on which they will become able to imply with groups to an access control list (ACL).
Requiring the AD groups mirror as per organisational hierarchy such as finance group, legal,
marketing etc.
C. Server Specification
Demonstrating fruitful server location and specific information there are some factors
which are needed to be administered by professionals of Skillage IT. Server specification will
bring effective control over network system implications in business. Thus, there are several
components which are needed to be considered by professionals such as:
Number and location of virtual and physical servers: Physical servers are mainly
incorporated with physical devices such as operating system, windows and Linux which runs
through a device. Therefore, these are termed as Physical server. Skillage IT needed to have
appropriate operating system in each device as well as which consist security keys. It will be
remove chances of data break or losing confidential data (Physical server vs Virtual server,
2016). On the other side, virtual server is also known as virtual machines of VPA system.
Operation of a VPA through operating system that simulates an operating environment. It
virtually creates devices of machines and run them.
Roles of Servers: Configuring role of a server is for facilitating appropriate network
coverage in a premise (Mokhlespour Esfahani and et.al., 2017). It ascertains software
components that allows server in performing specific operations for users and relevant computer-
based networks.
Approval sign off a document:
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
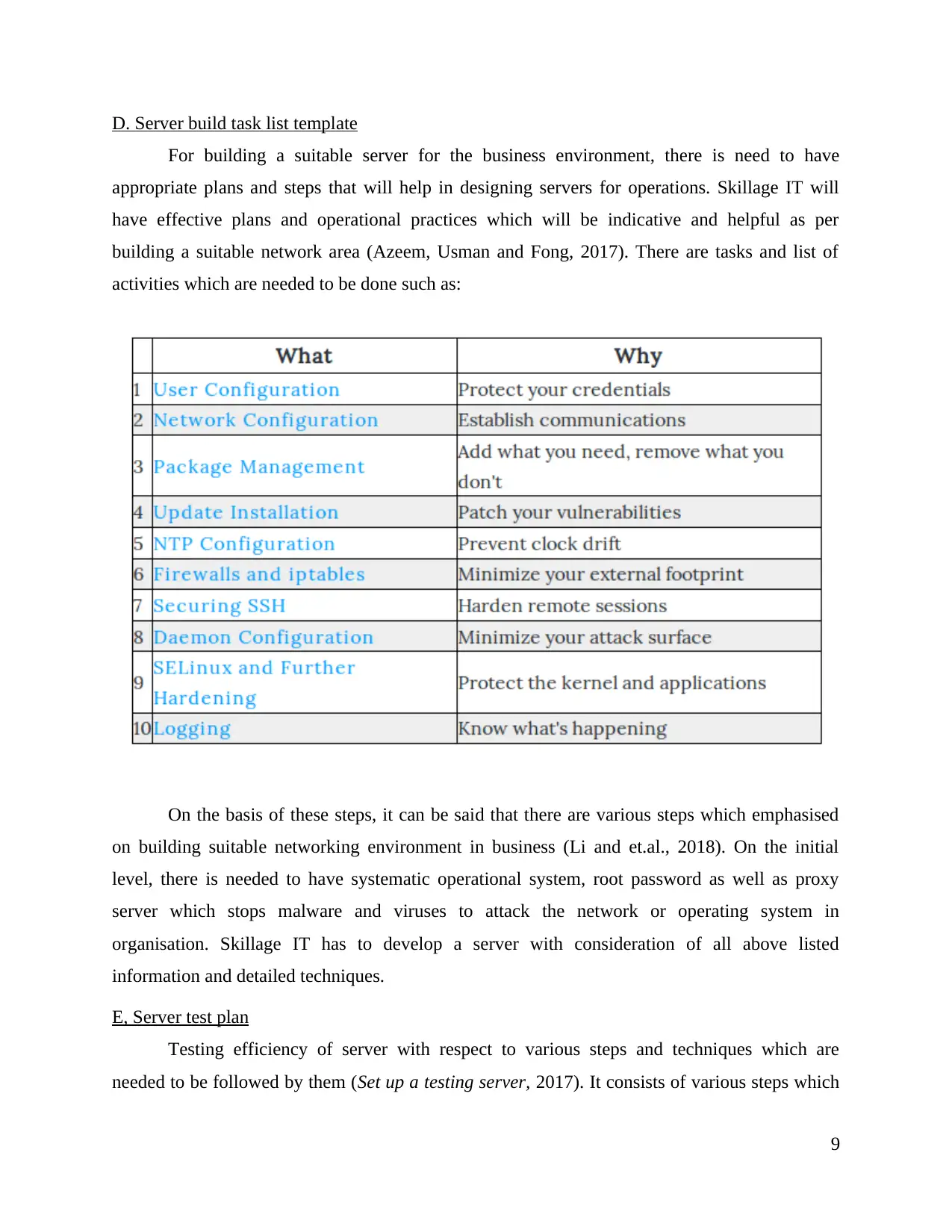
D. Server build task list template
For building a suitable server for the business environment, there is need to have
appropriate plans and steps that will help in designing servers for operations. Skillage IT will
have effective plans and operational practices which will be indicative and helpful as per
building a suitable network area (Azeem, Usman and Fong, 2017). There are tasks and list of
activities which are needed to be done such as:
On the basis of these steps, it can be said that there are various steps which emphasised
on building suitable networking environment in business (Li and et.al., 2018). On the initial
level, there is needed to have systematic operational system, root password as well as proxy
server which stops malware and viruses to attack the network or operating system in
organisation. Skillage IT has to develop a server with consideration of all above listed
information and detailed techniques.
E, Server test plan
Testing efficiency of server with respect to various steps and techniques which are
needed to be followed by them (Set up a testing server, 2017). It consists of various steps which
9
For building a suitable server for the business environment, there is need to have
appropriate plans and steps that will help in designing servers for operations. Skillage IT will
have effective plans and operational practices which will be indicative and helpful as per
building a suitable network area (Azeem, Usman and Fong, 2017). There are tasks and list of
activities which are needed to be done such as:
On the basis of these steps, it can be said that there are various steps which emphasised
on building suitable networking environment in business (Li and et.al., 2018). On the initial
level, there is needed to have systematic operational system, root password as well as proxy
server which stops malware and viruses to attack the network or operating system in
organisation. Skillage IT has to develop a server with consideration of all above listed
information and detailed techniques.
E, Server test plan
Testing efficiency of server with respect to various steps and techniques which are
needed to be followed by them (Set up a testing server, 2017). It consists of various steps which
9

are needed to be followed by professionals of Skillage IT as to have appropriate network
development plan. It ascertains various steps and techniques that will be helpful and appropriate
as per testing the existing severe plan of business. These steps can be demonstrated as:
Selecting site>manage site-specific
Click new for setting up a new site/ selecting and Dreamweaver site and clicking edit
icon.
Select a server category as per clicking on site setup dialogue box such as click add new server
button / edit existing server button
For the remote server connection there is must be click on an advanced button.
Selecting severe model as per web application by considering the testing server (Zhao,
Wang and Wu, 2017).
To save the advanced screen it requires a click to save, then all the changes were
automatically saved which were edited as well as newly designed.
F. Maintenance plan of server
Administrating and managing the severe of then organisation there is need to set up plans
for analysing data set. Thus, it comprises with creating a maintenance plan for existing server of
business such as:
Initiate the plan with object explorer than click plus sign which will expand severe where
the maintenance plan will be created (Create a Maintenance Plan, 2017).
For expanding managements folder click on plus sign
Selecting new maintenance plan as per clicking right click on maintenance plans folder
In new maintenance plan dialogue box, need to type name, type of plans and then OK.
G. Router specification
Implementing plan: there has been various plans and operations which will be effective
and helpful for developing the business networking system. For setting up most reliable as well
as helpful network system in the organisation Skillage IT needed to have development of various
plans and operations. Motive of industry for setting up an appropriate plan which will be helpful
10
development plan. It ascertains various steps and techniques that will be helpful and appropriate
as per testing the existing severe plan of business. These steps can be demonstrated as:
Selecting site>manage site-specific
Click new for setting up a new site/ selecting and Dreamweaver site and clicking edit
icon.
Select a server category as per clicking on site setup dialogue box such as click add new server
button / edit existing server button
For the remote server connection there is must be click on an advanced button.
Selecting severe model as per web application by considering the testing server (Zhao,
Wang and Wu, 2017).
To save the advanced screen it requires a click to save, then all the changes were
automatically saved which were edited as well as newly designed.
F. Maintenance plan of server
Administrating and managing the severe of then organisation there is need to set up plans
for analysing data set. Thus, it comprises with creating a maintenance plan for existing server of
business such as:
Initiate the plan with object explorer than click plus sign which will expand severe where
the maintenance plan will be created (Create a Maintenance Plan, 2017).
For expanding managements folder click on plus sign
Selecting new maintenance plan as per clicking right click on maintenance plans folder
In new maintenance plan dialogue box, need to type name, type of plans and then OK.
G. Router specification
Implementing plan: there has been various plans and operations which will be effective
and helpful for developing the business networking system. For setting up most reliable as well
as helpful network system in the organisation Skillage IT needed to have development of various
plans and operations. Motive of industry for setting up an appropriate plan which will be helpful
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





