Comprehensive Report: Small Office Network Designing and Planning
VerifiedAdded on 2020/10/05
|14
|1850
|183
Report
AI Summary
This report details the design and planning of a small office network for Booksforyou, a retail book sale company. It begins with a gap analysis, identifying outdated technologies and security vulnerabilities, and then proposes a new network design incorporating switches, firewalls, wireless access points, and cloud services. The report outlines IP addressing solutions, including subnetting to conserve IP addresses. It provides lists of necessary hardware (switches, firewalls, desktops, WAPs, DHCP server, mail server, web server) and software (Windows, antivirus). Finally, the report includes network device configuration steps, such as setting hostnames, system clocks, and IP addresses, and displaying interface information. The aim is to modernize Booksforyou's network to enhance services and improve competitiveness.

Small Office Network
Designing and
Planning
Designing and
Planning
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
1. Creation of GAP report......................................................................................................1
2. Build a document which comprises of all network designs...............................................1
3. IP addressing solution.........................................................................................................4
4. List of software and hardware specification.......................................................................6
5. Network device configuration............................................................................................6
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10
INTRODUCTION...........................................................................................................................1
1. Creation of GAP report......................................................................................................1
2. Build a document which comprises of all network designs...............................................1
3. IP addressing solution.........................................................................................................4
4. List of software and hardware specification.......................................................................6
5. Network device configuration............................................................................................6
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Internetworking is term which is used by BBN, Cisco and other network providers of
services as a encompassing term for technologies, generic devices and concepts which allow
people to communicate across wide networks (Alem, Clark and Moreno, 2016). This report is
based on Booksforyou which is a retail book sale company as well as they possess small library.
To remain competitive within the market they need to make changes in their network or the way
they deliver their services. This report contain GAP report, documents for network design, IP
addressing solution, hardware and software specifications of devices and network device
configuration.
1. Creation of GAP report.
Booksforyou is making use of resources which are out dated and at present scenario people want
services where they have advanced options. Like Wi-fi services, as everyone has smart phones
and they want that their phone get connected to Wi-Fi rather than carrying laptop every time as it
is not feasible. Furthermore, they do not have any firewall which means that there can be issues
related with security of a system that is in the network (Vahdani and Mohammadi, 2015). Apart
from this they have windows XP in their systems, which can be easily broken up, means it can be
hacked and all the details related with customers, their business clients and books will be taken
out by them. They are also making use of Microsoft Office 2007 which is also outdated as, they
make use of Microsoft Office 2016 so that they can have advanced options. In case of
technology they are lacking behind and they need to update their systems by which they can
remain within a network for longer period of time. For remaining competitive within the market
they need to update their systems and make their information available from anywhere (Duffy,
Cave and Worthington, 2016).
2. Build a document which comprises of all network designs.
As per the above GAP report, it is necessary for Booksforyou to modify their existing
system and expand it to attain growth of 28% within 3 years. The existing network design is
present below, they have made use of switch, router but it is a wired network and as clients are
requesting for wireless network, then Booksforyou have to make changes accordingly.
1
Internetworking is term which is used by BBN, Cisco and other network providers of
services as a encompassing term for technologies, generic devices and concepts which allow
people to communicate across wide networks (Alem, Clark and Moreno, 2016). This report is
based on Booksforyou which is a retail book sale company as well as they possess small library.
To remain competitive within the market they need to make changes in their network or the way
they deliver their services. This report contain GAP report, documents for network design, IP
addressing solution, hardware and software specifications of devices and network device
configuration.
1. Creation of GAP report.
Booksforyou is making use of resources which are out dated and at present scenario people want
services where they have advanced options. Like Wi-fi services, as everyone has smart phones
and they want that their phone get connected to Wi-Fi rather than carrying laptop every time as it
is not feasible. Furthermore, they do not have any firewall which means that there can be issues
related with security of a system that is in the network (Vahdani and Mohammadi, 2015). Apart
from this they have windows XP in their systems, which can be easily broken up, means it can be
hacked and all the details related with customers, their business clients and books will be taken
out by them. They are also making use of Microsoft Office 2007 which is also outdated as, they
make use of Microsoft Office 2016 so that they can have advanced options. In case of
technology they are lacking behind and they need to update their systems by which they can
remain within a network for longer period of time. For remaining competitive within the market
they need to update their systems and make their information available from anywhere (Duffy,
Cave and Worthington, 2016).
2. Build a document which comprises of all network designs.
As per the above GAP report, it is necessary for Booksforyou to modify their existing
system and expand it to attain growth of 28% within 3 years. The existing network design is
present below, they have made use of switch, router but it is a wired network and as clients are
requesting for wireless network, then Booksforyou have to make changes accordingly.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
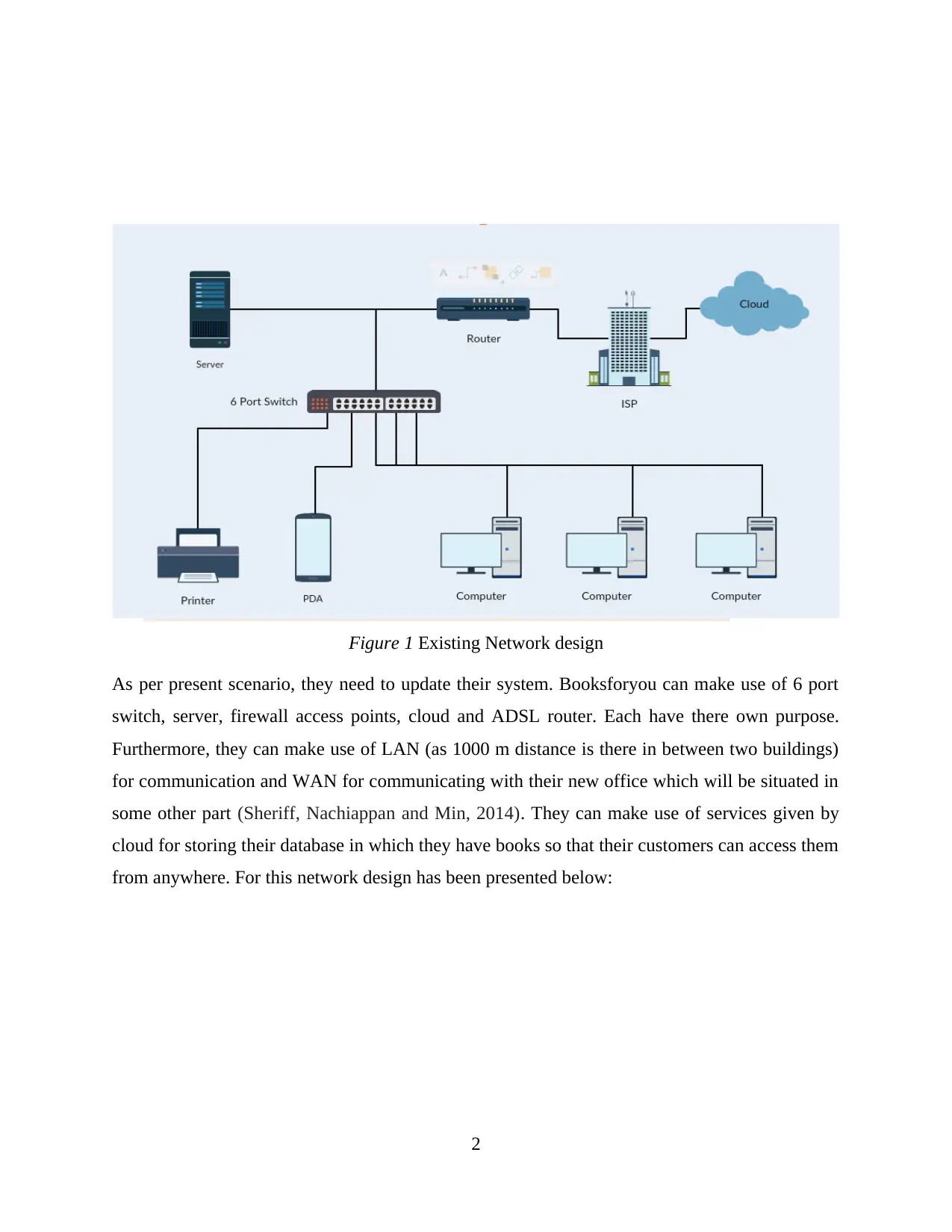
Figure 1 Existing Network design
As per present scenario, they need to update their system. Booksforyou can make use of 6 port
switch, server, firewall access points, cloud and ADSL router. Each have there own purpose.
Furthermore, they can make use of LAN (as 1000 m distance is there in between two buildings)
for communication and WAN for communicating with their new office which will be situated in
some other part (Sheriff, Nachiappan and Min, 2014). They can make use of services given by
cloud for storing their database in which they have books so that their customers can access them
from anywhere. For this network design has been presented below:
2
As per present scenario, they need to update their system. Booksforyou can make use of 6 port
switch, server, firewall access points, cloud and ADSL router. Each have there own purpose.
Furthermore, they can make use of LAN (as 1000 m distance is there in between two buildings)
for communication and WAN for communicating with their new office which will be situated in
some other part (Sheriff, Nachiappan and Min, 2014). They can make use of services given by
cloud for storing their database in which they have books so that their customers can access them
from anywhere. For this network design has been presented below:
2

They can update their systems and have window 8 or 8.1 in their systems. Steps are
mentioned below:
1. They can make use of either 802.11b, 802.11g, 802.11a or 802.11n. Prices will vary as
per data transfer rates. Ideally they can opt for 802.11b- 11 megabytes per seconds.
2. Wireless router can be used for sending information in between network and internet by
making use of radio signals rather than wires. Wireless access point can be used (WAP)
in central location (Set up your small business network. 2019). Like in office 1 they have
two floors so they can put router high on the shelf or wall of the first floor so that second
floor devices can also access internet.
3. Set up the modem by steps mentioned below:
i. Plug modem into the electrical outlet.
ii. Plug one end cable or phone cord into WAN port and other into wall jack.
iii. Restart device.
3
Figure 2 Network design
mentioned below:
1. They can make use of either 802.11b, 802.11g, 802.11a or 802.11n. Prices will vary as
per data transfer rates. Ideally they can opt for 802.11b- 11 megabytes per seconds.
2. Wireless router can be used for sending information in between network and internet by
making use of radio signals rather than wires. Wireless access point can be used (WAP)
in central location (Set up your small business network. 2019). Like in office 1 they have
two floors so they can put router high on the shelf or wall of the first floor so that second
floor devices can also access internet.
3. Set up the modem by steps mentioned below:
i. Plug modem into the electrical outlet.
ii. Plug one end cable or phone cord into WAN port and other into wall jack.
iii. Restart device.
3
Figure 2 Network design
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4. Wireless network has security key to protect from unauthorized access. It can be setup
by:
i. Click on the right side of screen, go to settings and then network icon.
ii. Select wireless network and click on connect, if window has WPS OR WCN then
push the button present on router and wait (Simmons, 2014).
iii. Enter the passphrase or security key if prompted and click on ok.
5. Firewall can be set up to protect devices from malicious software and hackers. This can
be attained by:
i. Swipe up on right edge of screen, and search firewall in search box.
ii. Click on settings and then on Windows Firewall, click turn on
iii. Turn on Windows Firewall for each network which they Booksfor you needs to
protect.
6. Enable printer and file sharing with firewall. Windows firewall will open ports for this
for devices which are on network. If it is being not used then, manually these ports can be
opened (Soleimani, Seyyed-Esfahani and Kannan, 2014).
7. To connect devices to a network, swipe up, click on settings, then network icon and select
network icon, then click on ok and enter.
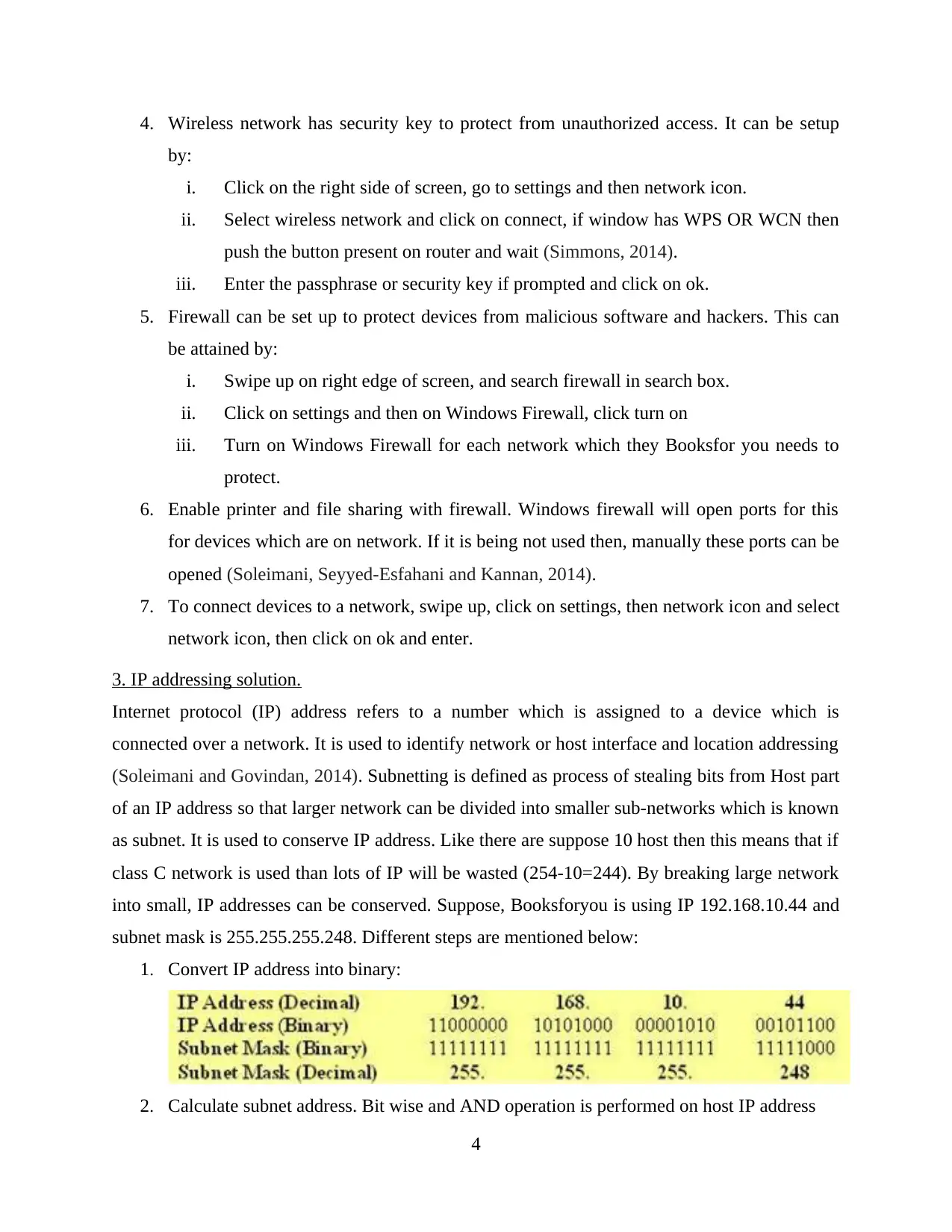
3. IP addressing solution.
Internet protocol (IP) address refers to a number which is assigned to a device which is
connected over a network. It is used to identify network or host interface and location addressing
(Soleimani and Govindan, 2014). Subnetting is defined as process of stealing bits from Host part
of an IP address so that larger network can be divided into smaller sub-networks which is known
as subnet. It is used to conserve IP address. Like there are suppose 10 host then this means that if
class C network is used than lots of IP will be wasted (254-10=244). By breaking large network
into small, IP addresses can be conserved. Suppose, Booksforyou is using IP 192.168.10.44 and
subnet mask is 255.255.255.248. Different steps are mentioned below:
1. Convert IP address into binary:
2. Calculate subnet address. Bit wise and AND operation is performed on host IP address
4
by:
i. Click on the right side of screen, go to settings and then network icon.
ii. Select wireless network and click on connect, if window has WPS OR WCN then
push the button present on router and wait (Simmons, 2014).
iii. Enter the passphrase or security key if prompted and click on ok.
5. Firewall can be set up to protect devices from malicious software and hackers. This can
be attained by:
i. Swipe up on right edge of screen, and search firewall in search box.
ii. Click on settings and then on Windows Firewall, click turn on
iii. Turn on Windows Firewall for each network which they Booksfor you needs to
protect.
6. Enable printer and file sharing with firewall. Windows firewall will open ports for this
for devices which are on network. If it is being not used then, manually these ports can be
opened (Soleimani, Seyyed-Esfahani and Kannan, 2014).
7. To connect devices to a network, swipe up, click on settings, then network icon and select
network icon, then click on ok and enter.
3. IP addressing solution.
Internet protocol (IP) address refers to a number which is assigned to a device which is
connected over a network. It is used to identify network or host interface and location addressing
(Soleimani and Govindan, 2014). Subnetting is defined as process of stealing bits from Host part
of an IP address so that larger network can be divided into smaller sub-networks which is known
as subnet. It is used to conserve IP address. Like there are suppose 10 host then this means that if
class C network is used than lots of IP will be wasted (254-10=244). By breaking large network
into small, IP addresses can be conserved. Suppose, Booksforyou is using IP 192.168.10.44 and
subnet mask is 255.255.255.248. Different steps are mentioned below:
1. Convert IP address into binary:
2. Calculate subnet address. Bit wise and AND operation is performed on host IP address
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
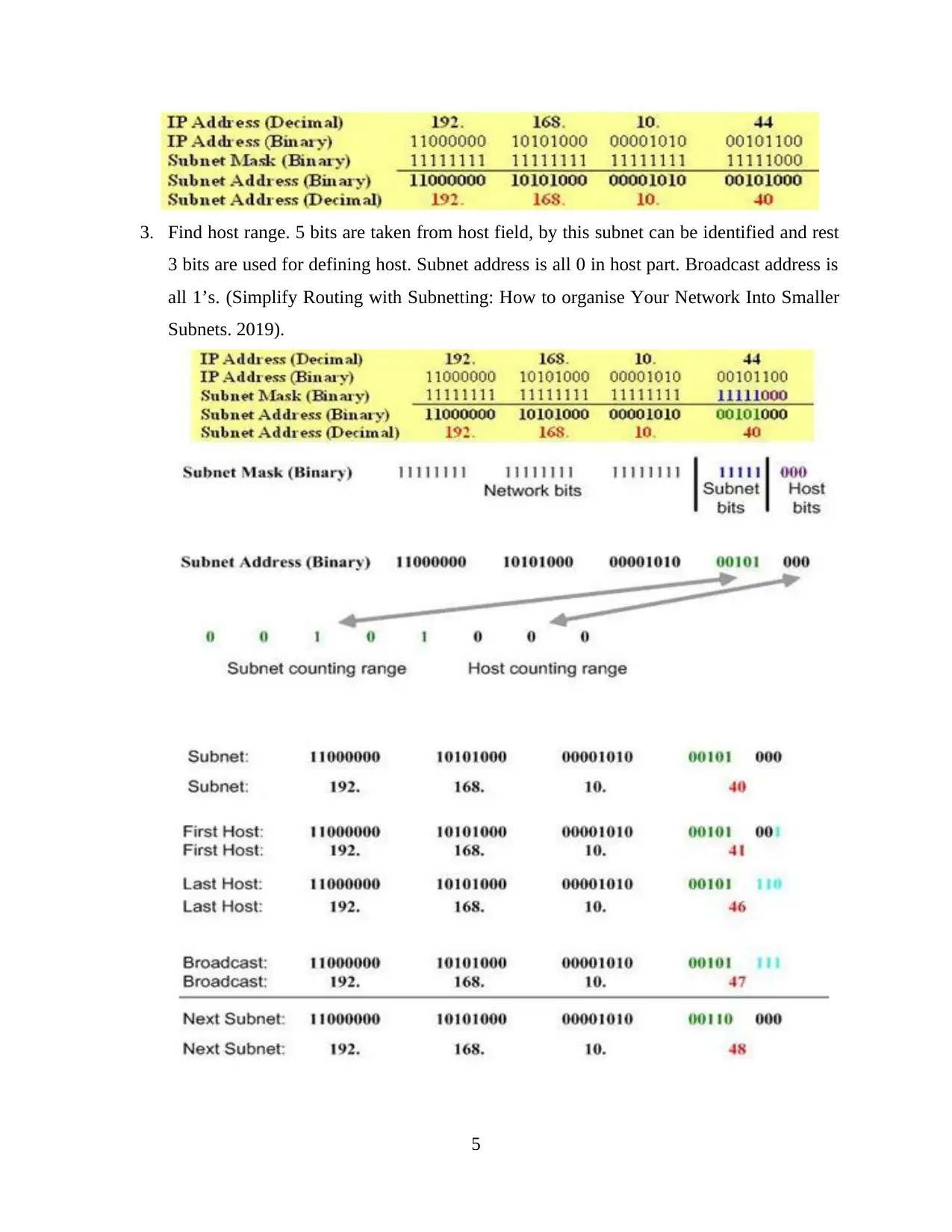
3. Find host range. 5 bits are taken from host field, by this subnet can be identified and rest
3 bits are used for defining host. Subnet address is all 0 in host part. Broadcast address is
all 1’s. (Simplify Routing with Subnetting: How to organise Your Network Into Smaller
Subnets. 2019).
5
3 bits are used for defining host. Subnet address is all 0 in host part. Broadcast address is
all 1’s. (Simplify Routing with Subnetting: How to organise Your Network Into Smaller
Subnets. 2019).
5
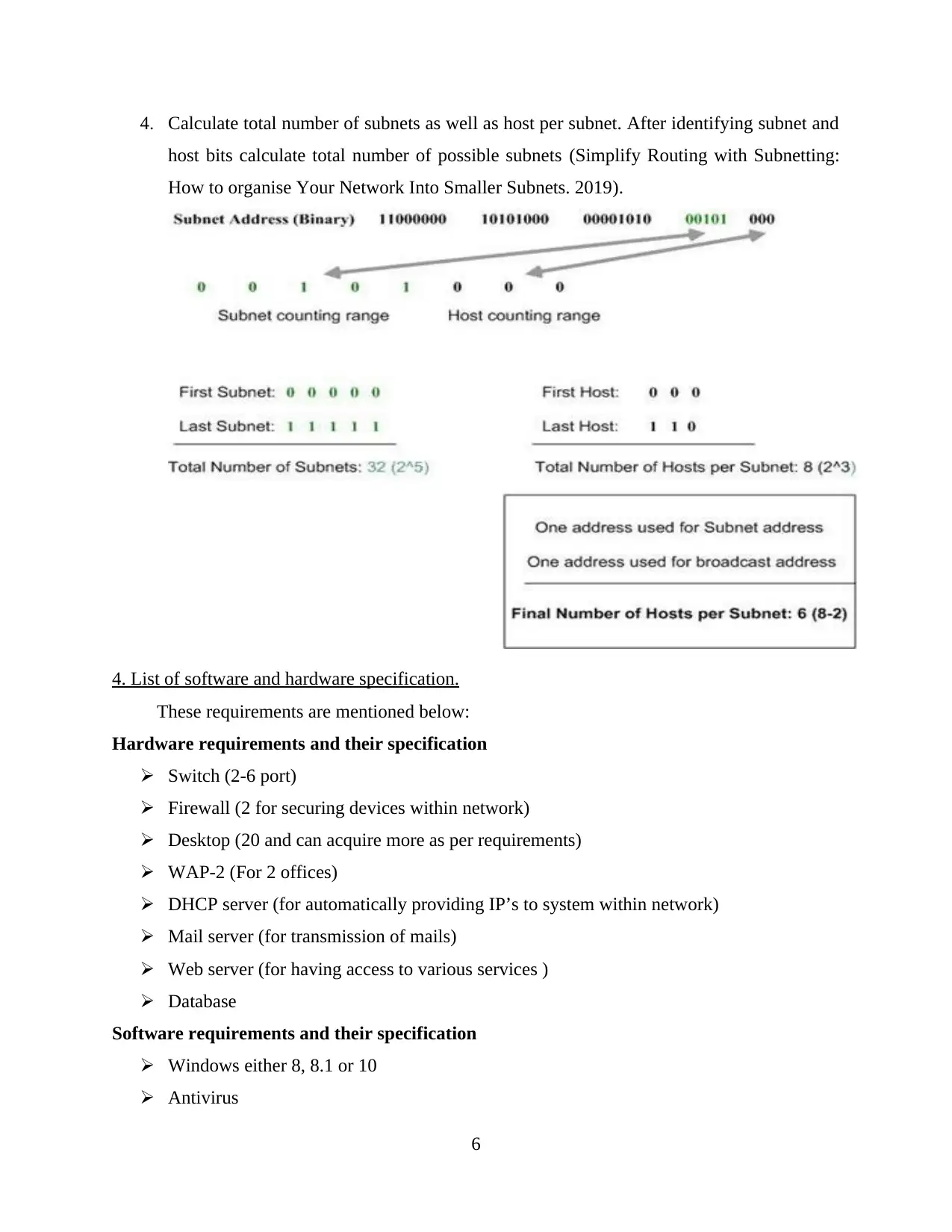
4. Calculate total number of subnets as well as host per subnet. After identifying subnet and
host bits calculate total number of possible subnets (Simplify Routing with Subnetting:
How to organise Your Network Into Smaller Subnets. 2019).
4. List of software and hardware specification.
These requirements are mentioned below:
Hardware requirements and their specification
Switch (2-6 port)
Firewall (2 for securing devices within network)
Desktop (20 and can acquire more as per requirements)
WAP-2 (For 2 offices)
DHCP server (for automatically providing IP’s to system within network)
Mail server (for transmission of mails)
Web server (for having access to various services )
Database
Software requirements and their specification
Windows either 8, 8.1 or 10
Antivirus
6
host bits calculate total number of possible subnets (Simplify Routing with Subnetting:
How to organise Your Network Into Smaller Subnets. 2019).
4. List of software and hardware specification.
These requirements are mentioned below:
Hardware requirements and their specification
Switch (2-6 port)
Firewall (2 for securing devices within network)
Desktop (20 and can acquire more as per requirements)
WAP-2 (For 2 offices)
DHCP server (for automatically providing IP’s to system within network)
Mail server (for transmission of mails)
Web server (for having access to various services )
Database
Software requirements and their specification
Windows either 8, 8.1 or 10
Antivirus
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Software required for accessing books
5. Network device configuration.
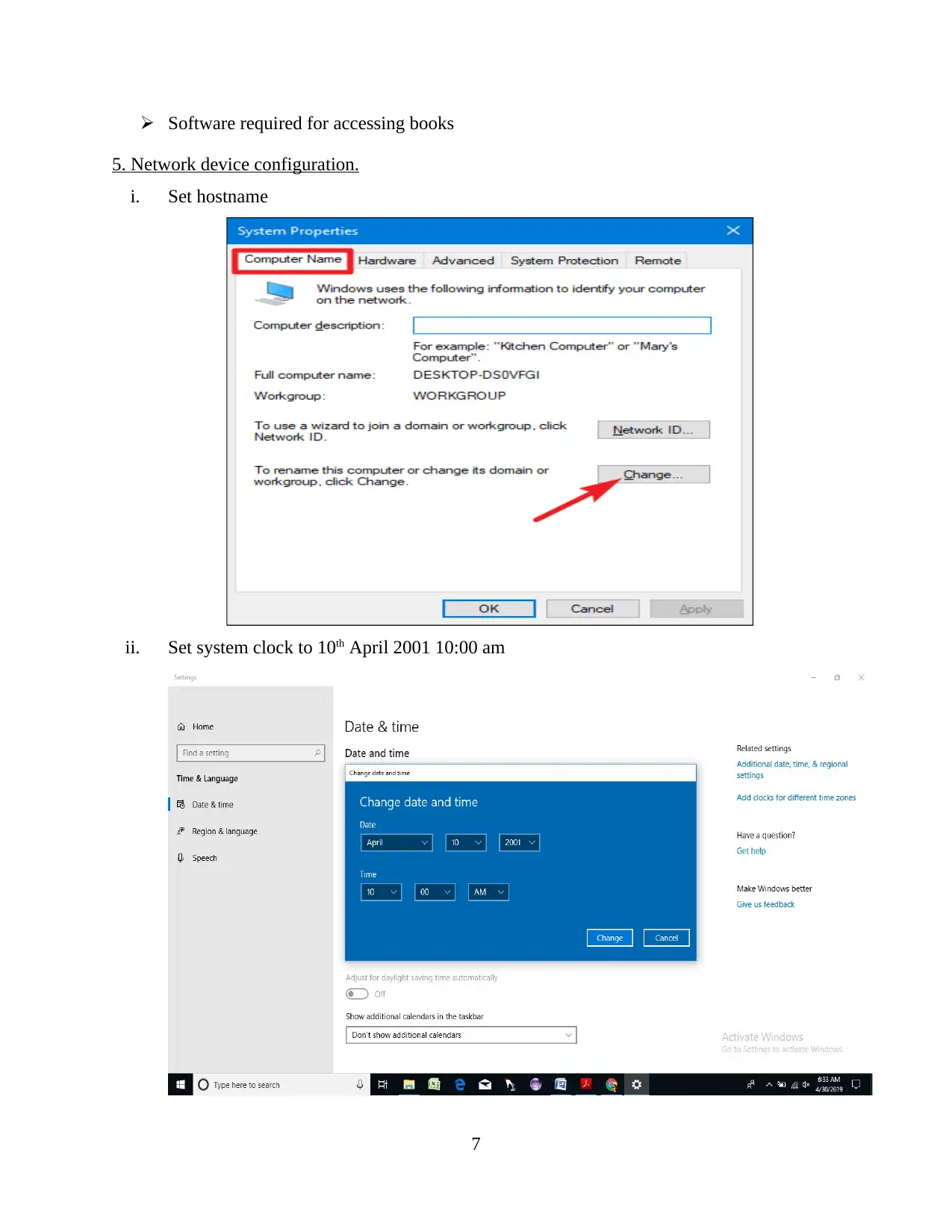
i. Set hostname
ii. Set system clock to 10th April 2001 10:00 am
7
5. Network device configuration.
i. Set hostname
ii. Set system clock to 10th April 2001 10:00 am
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
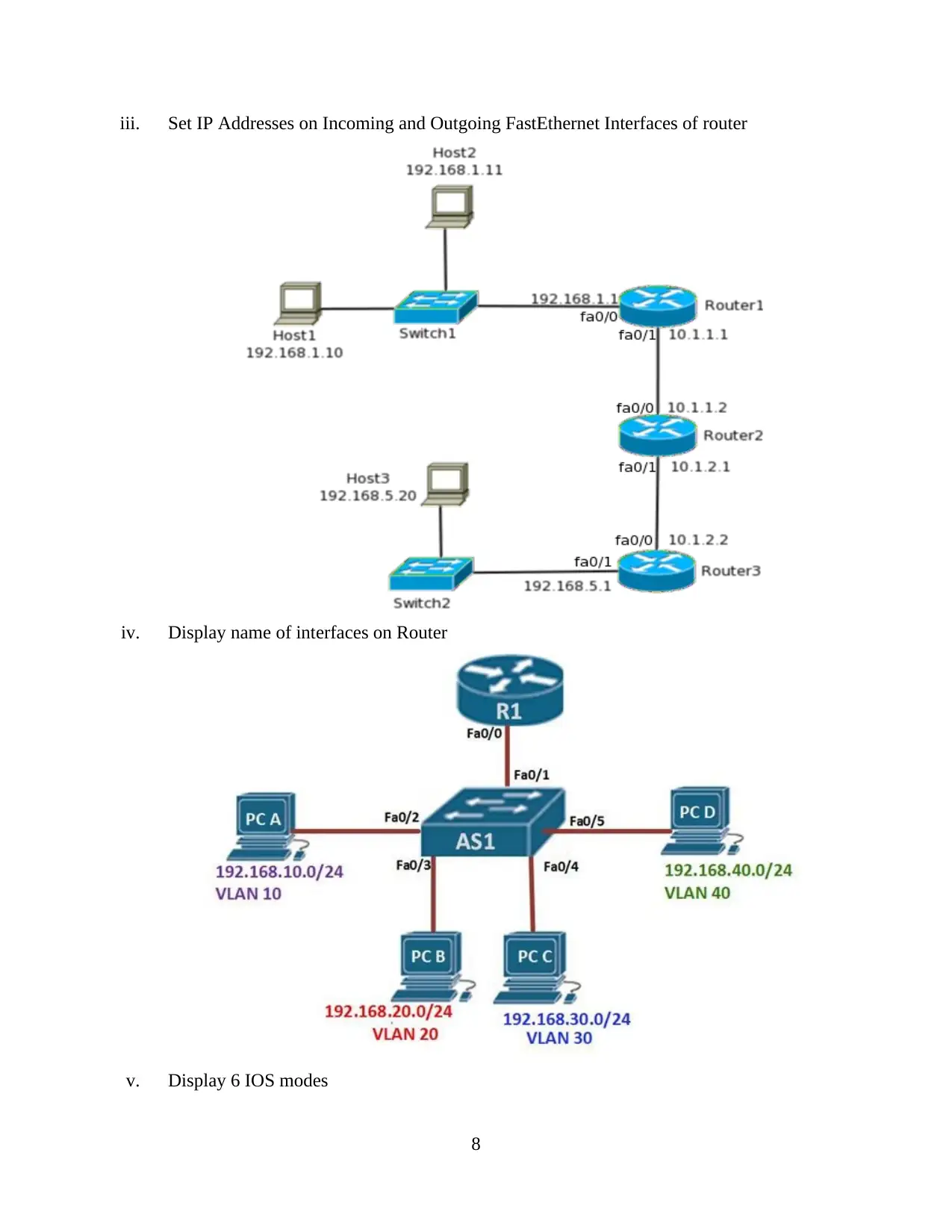
iii. Set IP Addresses on Incoming and Outgoing FastEthernet Interfaces of router
iv. Display name of interfaces on Router
v. Display 6 IOS modes
8
iv. Display name of interfaces on Router
v. Display 6 IOS modes
8
CONCLUSION
From above it has been concluded that internetworking refers to technique or process for
connecting different networks by making use of intermediary devices like switches, routers or
hubs. GAP analysis has been done for identification of gap between existing and current needs to
analyse what is required. A network design has been implemented to meet the current needs and
attain the desired results. Furthermore, concept of IP addresses has been used to give unique
number to each system within the network by making use of subnetting and major objective
behind subnetting is to save IP’s from wastage.
9
From above it has been concluded that internetworking refers to technique or process for
connecting different networks by making use of intermediary devices like switches, routers or
hubs. GAP analysis has been done for identification of gap between existing and current needs to
analyse what is required. A network design has been implemented to meet the current needs and
attain the desired results. Furthermore, concept of IP addresses has been used to give unique
number to each system within the network by making use of subnetting and major objective
behind subnetting is to save IP’s from wastage.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




