Technical Report: Smart Campus System BYOD Policy for MTU, Semester 2
VerifiedAdded on 2022/10/17
|9
|2038
|10
Report
AI Summary
This report analyzes the implementation of a Bring Your Own Device (BYOD) policy within a Smart Campus system, specifically focusing on Melbourne Technology University (MTU). It begins by introducing the concept of BYOD and its relevance to modern educational institutions, highlighting the advantages such as student and employee comfort, ease of access to learning materials, and technological advancement. The report then delves into the disadvantages of BYOD, including heightened network insecurity and potential distractions, while proposing solutions such as updated system controls, strong password policies, device authentication, mobile device management software, and the use of anti-virus and malware protection. A comparison is made between BYOD, computer lab, and loaned computer policies. The report then discusses the network infrastructure required for a BYOD system, recommending a Wireless Local Area Network (WLAN) with switches, routers, and broadband receivers. The concept of virtualization is introduced as a solution to software management challenges. The report concludes that despite potential drawbacks, the BYOD policy offers significant benefits and recommends its adoption by MTU, emphasizing the importance of addressing security concerns. The report also includes references to relevant academic sources and a conceptual diagram of the proposed network.

Smart Campus System 1
Smart Campus System
Student Name
Student Number
Institution
Location of Institution
Professor’s Name
Date
Smart Campus System
Student Name
Student Number
Institution
Location of Institution
Professor’s Name
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Smart Campus System 2
Table of Contents
1.0 Introduction................................................................................................................................3
1.1 Bring your device (BYOD).......................................................................................................3
1.1.1 Advantages of bringing your device policy........................................................................3
1.1.2 Disadvantages of BYOD....................................................................................................4
1.2 BYOD network..........................................................................................................................7
1.3 Virtualization.............................................................................................................................7
1.4 Conclusion.................................................................................................................................8
Table of Contents
1.0 Introduction................................................................................................................................3
1.1 Bring your device (BYOD).......................................................................................................3
1.1.1 Advantages of bringing your device policy........................................................................3
1.1.2 Disadvantages of BYOD....................................................................................................4
1.2 BYOD network..........................................................................................................................7
1.3 Virtualization.............................................................................................................................7
1.4 Conclusion.................................................................................................................................8

Smart Campus System 3
1.0 Introduction
Information technology nowadays is very essential in every organization. Different
considerations are put in place to choose to decide on what form of technology to implement. It
can be a problem or can help you solve some organizational problems, depending on how you
implement it. A learning institution is a busy organization that needs ways of simplifying the
transactions. There must be a good understanding between tutors and students. Software
development came into place to help solve these problems. For an organization to change from
one mode of operation to another, it must get good reasons for doing so. Students using the
school computers in the computer lab, bring your device or loaning of computers to students both
have advantages and disadvantages but an organization can choose one depending on the reasons
they may be having. Computer networking, liability, user experience, how the system is designed
and managed are among the factors to be considered before shifting. The students' and
employees’ views should be taken before shifting.
1.1 Bring your device (BYOD).
BYOD is a policy that allows students or employees to use their computers in performing office
duties. Song & Kong. (2017). This has a lot of advantages to the organization over the
disadvantages. I recommend that Melbourne Technology University (MTU) should shift from
computer labs to BYOD policy.
1.1.1 Advantages of bringing your device policy. (Why BYOD should be implemented.)
The students and employees will be comfortable when using their own devices. The students will
be able to download, store and access learning materials from their laptops. It is easy for students
to install their own devices than the school installing computers for students.
Nowadays, everybody wants to keep their information private. Students will be able to store a lot
of information in their computers and use them later. This will make teaching effective since the
lessons will not be boring anymore Meske, Stieglitz, Brockmann & Ross. (2017).
Advancement in technology. Technology comes in with new things day by day. The students
will be free to explore more when using their own devices than when using an organization's
devices. This will not only make teaching easier but will also allow students to learn more.
1.0 Introduction
Information technology nowadays is very essential in every organization. Different
considerations are put in place to choose to decide on what form of technology to implement. It
can be a problem or can help you solve some organizational problems, depending on how you
implement it. A learning institution is a busy organization that needs ways of simplifying the
transactions. There must be a good understanding between tutors and students. Software
development came into place to help solve these problems. For an organization to change from
one mode of operation to another, it must get good reasons for doing so. Students using the
school computers in the computer lab, bring your device or loaning of computers to students both
have advantages and disadvantages but an organization can choose one depending on the reasons
they may be having. Computer networking, liability, user experience, how the system is designed
and managed are among the factors to be considered before shifting. The students' and
employees’ views should be taken before shifting.
1.1 Bring your device (BYOD).
BYOD is a policy that allows students or employees to use their computers in performing office
duties. Song & Kong. (2017). This has a lot of advantages to the organization over the
disadvantages. I recommend that Melbourne Technology University (MTU) should shift from
computer labs to BYOD policy.
1.1.1 Advantages of bringing your device policy. (Why BYOD should be implemented.)
The students and employees will be comfortable when using their own devices. The students will
be able to download, store and access learning materials from their laptops. It is easy for students
to install their own devices than the school installing computers for students.
Nowadays, everybody wants to keep their information private. Students will be able to store a lot
of information in their computers and use them later. This will make teaching effective since the
lessons will not be boring anymore Meske, Stieglitz, Brockmann & Ross. (2017).
Advancement in technology. Technology comes in with new things day by day. The students
will be free to explore more when using their own devices than when using an organization's
devices. This will not only make teaching easier but will also allow students to learn more.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Smart Campus System 4
It should set various security measures in order to provide security in the network
1.1.2 Disadvantages of BYOD.
Under the BYOD policy, the level of insecurity is very high due to high network traffic. Before
an organization implements this policy, its level of security must be high. Offices are the most
affected parts of this issue.
The teachers and students will face a lot of disturbance since apart from for learning purposes,
the computers can be used for other purposes like accessing social media and watching videos.
This becomes a source of distraction for both teachers and students. An organization can restrict
its own devices for learning purposes. Vignesh & Asha. (2015). So before shifting to bring your
devices policy, the organization should consider the ways of reducing destruction and
determining what can only be accessed from the internet. The following are some of the
strategies that will enable the success of BYOD policy;
i) Update and control the systems. The organization should help the students and
employees keep their computers' software updated. The software will be update
through continuous maintenance. This can be done by sending them notices whenever
an update arises. To ensure security there will be a chance to lock the system.
ii) Make a rule that every device should have a password. Passwords will protect
your device in case it gets into the wrong hands. Every owner of the system
should set a unique and strong password. Weak passwords can be hacked easily.
iii) The organization’s financial information should not be kept in personal
computers. The organization should set rules on where and how to access its
sensitive information. When kept in personal computers, it will be at a high risk of
falling in the hands of a third party.
iv) Come up with the ways to authenticate the devices into the organization's
network. This can be done by assigning the devices' unique IP addresses and
changing them after a while or giving every workstation a unique id. When these
authentication tools are not changed regularly, it becomes risky.
v) Encourage the use of mobile device management software.
It should set various security measures in order to provide security in the network
1.1.2 Disadvantages of BYOD.
Under the BYOD policy, the level of insecurity is very high due to high network traffic. Before
an organization implements this policy, its level of security must be high. Offices are the most
affected parts of this issue.
The teachers and students will face a lot of disturbance since apart from for learning purposes,
the computers can be used for other purposes like accessing social media and watching videos.
This becomes a source of distraction for both teachers and students. An organization can restrict
its own devices for learning purposes. Vignesh & Asha. (2015). So before shifting to bring your
devices policy, the organization should consider the ways of reducing destruction and
determining what can only be accessed from the internet. The following are some of the
strategies that will enable the success of BYOD policy;
i) Update and control the systems. The organization should help the students and
employees keep their computers' software updated. The software will be update
through continuous maintenance. This can be done by sending them notices whenever
an update arises. To ensure security there will be a chance to lock the system.
ii) Make a rule that every device should have a password. Passwords will protect
your device in case it gets into the wrong hands. Every owner of the system
should set a unique and strong password. Weak passwords can be hacked easily.
iii) The organization’s financial information should not be kept in personal
computers. The organization should set rules on where and how to access its
sensitive information. When kept in personal computers, it will be at a high risk of
falling in the hands of a third party.
iv) Come up with the ways to authenticate the devices into the organization's
network. This can be done by assigning the devices' unique IP addresses and
changing them after a while or giving every workstation a unique id. When these
authentication tools are not changed regularly, it becomes risky.
v) Encourage the use of mobile device management software.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Smart Campus System 5
This software allows IT organizations to add some other security measures into their devices.
MTU should employ the use of this software to be free from some advantages of BYOD police
when they chose to adapt.
vi) Encourage the use of antiviruses and malware.
Every type of internet connection can be controlled by an anti-virus. The organization should set
up certain anti-viruses suitable for their type of network to be installed on every computer. This
is because one computer might be infected by a virus or may get a virus from online, an anti-
virus will protect another computer in the network from being affected.
Comparison between brings your device, using computers in a computer lab and using loaned
computers by school policies.
Bring your device Using computer lab’s
computers
Giving computer to students
on loan
Encourages the comfort of
using computers
It does not have any comfort
as the students only use the
computer as restricted by the
organization.
There are is a comfort but the
burden of paying back the
loan denies the students peace
of mind
The insecurity issue can be
handled by employing
strategies like setting up a
strong password.
The rate of insecurity is very
low but the students may
misuse the devices in case
they get freedom since they
are monitored.
The insecurity issue can be
handled by employing
strategies like regularly
updating the software on the
devices.
Teaching is easy and the
students acquire knowledge at
any place since they can
move with the devices
anywhere even in their
rooms.
The use of computers is only
restricted to be only in the
computer labs hence denying
the students a chance of using
the devices in their free time.
The students may have fear of
using the devices anywhere
since it may get lost and yet
they got them through loans.
This software allows IT organizations to add some other security measures into their devices.
MTU should employ the use of this software to be free from some advantages of BYOD police
when they chose to adapt.
vi) Encourage the use of antiviruses and malware.
Every type of internet connection can be controlled by an anti-virus. The organization should set
up certain anti-viruses suitable for their type of network to be installed on every computer. This
is because one computer might be infected by a virus or may get a virus from online, an anti-
virus will protect another computer in the network from being affected.
Comparison between brings your device, using computers in a computer lab and using loaned
computers by school policies.
Bring your device Using computer lab’s
computers
Giving computer to students
on loan
Encourages the comfort of
using computers
It does not have any comfort
as the students only use the
computer as restricted by the
organization.
There are is a comfort but the
burden of paying back the
loan denies the students peace
of mind
The insecurity issue can be
handled by employing
strategies like setting up a
strong password.
The rate of insecurity is very
low but the students may
misuse the devices in case
they get freedom since they
are monitored.
The insecurity issue can be
handled by employing
strategies like regularly
updating the software on the
devices.
Teaching is easy and the
students acquire knowledge at
any place since they can
move with the devices
anywhere even in their
rooms.
The use of computers is only
restricted to be only in the
computer labs hence denying
the students a chance of using
the devices in their free time.
The students may have fear of
using the devices anywhere
since it may get lost and yet
they got them through loans.
Smart Campus System 6
1.2 BYOD network.
Since under this policy there will be many diverse devices, the wired network connection will
course commotion in the organization. Wireless Local Area Network is the most appropriate.
The institution will be required to buy switches to connect groups of devices and routers to
connect the switches to form a complete network. Because of the connection of a lot of devices,
a broadband receiver will be necessary to increase the speed at which data will be transferred.
Hong, Baykov, Xu, Nadimpalli & Gu. (2016, February).
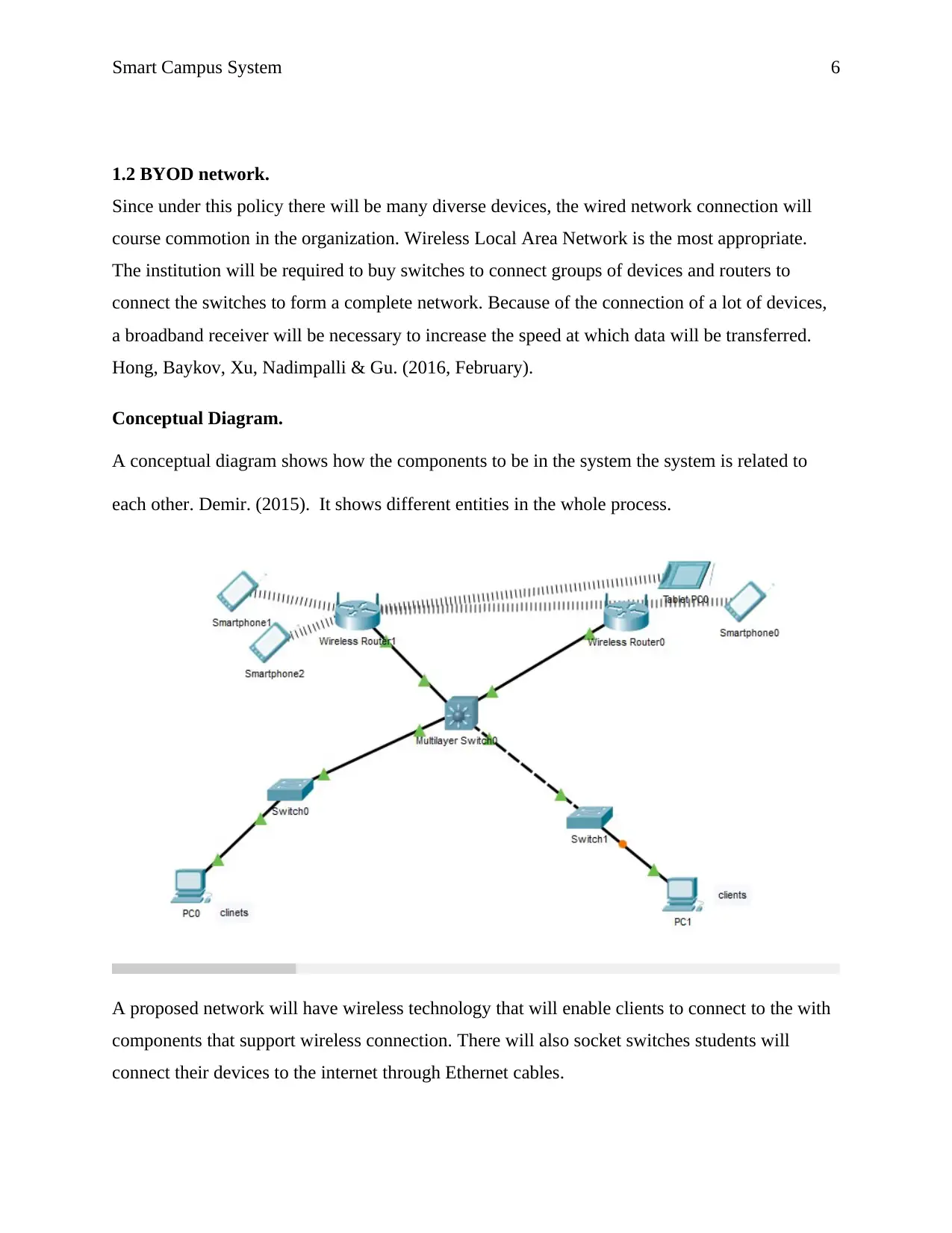
Conceptual Diagram.
A conceptual diagram shows how the components to be in the system the system is related to
each other. Demir. (2015). It shows different entities in the whole process.
A proposed network will have wireless technology that will enable clients to connect to the with
components that support wireless connection. There will also socket switches students will
connect their devices to the internet through Ethernet cables.
1.2 BYOD network.
Since under this policy there will be many diverse devices, the wired network connection will
course commotion in the organization. Wireless Local Area Network is the most appropriate.
The institution will be required to buy switches to connect groups of devices and routers to
connect the switches to form a complete network. Because of the connection of a lot of devices,
a broadband receiver will be necessary to increase the speed at which data will be transferred.
Hong, Baykov, Xu, Nadimpalli & Gu. (2016, February).
Conceptual Diagram.
A conceptual diagram shows how the components to be in the system the system is related to
each other. Demir. (2015). It shows different entities in the whole process.
A proposed network will have wireless technology that will enable clients to connect to the with
components that support wireless connection. There will also socket switches students will
connect their devices to the internet through Ethernet cables.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Smart Campus System 7
1.3 Solutions to the problems of BYOD policy.
Virtualization, as used in cloud computing, refers to formulating a version of something that is
not real. It can be database, hardware, software or computer networks. Ilyadis, Chen, Klein,
Hendel & Siva. (2017) Since MTU offers different courses and each course has different
software for facilitating teachers who teach, installing this software in all the computers is not
necessary as it will take longer and will be cumbersome. The organizers will have to employ
software as service. This is where they have to create a virtual framework and host it to the
server in the cloud where all the computers will be able to access. The notes to be shared by the
students can be updated to the central database where any student will be able to access them.
The central database has to be set in that no student can edit the data.
Devices used in setting up networks.
Bring your own devices Computers in a computer lab
Wireless network since the devices are in
diverse locations and need to be connected to
the internet.
Ethernet cables for connecting the computers
to the network since they are close to each
other and cables can connect them all.
Students are required to own their computers
as required by the policy.
Computers are owned by the organization.
Mobile device management software is used
to offer advanced security to the devices.
Anti-viruses are enough to control the
insecurity in data in the network since the
insecurity threat is very low.
Switches, broadband receivers, and routers
are used to set up the network.
Only routers are required since the network
connection is wired.
1.4 Conclusion
Despite having some disadvantages, bring your device policy should be considered the best.
Almost every learning institution is trying to implement technology in the classroom set up. And
mostly encouraging students to buy their devices to reduce running costs. Once all the security
issues are solved using the above-mentioned strategies, BYOD becomes the best policy. Its
disadvantages can be easily controlled as compared to the advantages of other policies.
1.3 Solutions to the problems of BYOD policy.
Virtualization, as used in cloud computing, refers to formulating a version of something that is
not real. It can be database, hardware, software or computer networks. Ilyadis, Chen, Klein,
Hendel & Siva. (2017) Since MTU offers different courses and each course has different
software for facilitating teachers who teach, installing this software in all the computers is not
necessary as it will take longer and will be cumbersome. The organizers will have to employ
software as service. This is where they have to create a virtual framework and host it to the
server in the cloud where all the computers will be able to access. The notes to be shared by the
students can be updated to the central database where any student will be able to access them.
The central database has to be set in that no student can edit the data.
Devices used in setting up networks.
Bring your own devices Computers in a computer lab
Wireless network since the devices are in
diverse locations and need to be connected to
the internet.
Ethernet cables for connecting the computers
to the network since they are close to each
other and cables can connect them all.
Students are required to own their computers
as required by the policy.
Computers are owned by the organization.
Mobile device management software is used
to offer advanced security to the devices.
Anti-viruses are enough to control the
insecurity in data in the network since the
insecurity threat is very low.
Switches, broadband receivers, and routers
are used to set up the network.
Only routers are required since the network
connection is wired.
1.4 Conclusion
Despite having some disadvantages, bring your device policy should be considered the best.
Almost every learning institution is trying to implement technology in the classroom set up. And
mostly encouraging students to buy their devices to reduce running costs. Once all the security
issues are solved using the above-mentioned strategies, BYOD becomes the best policy. Its
disadvantages can be easily controlled as compared to the advantages of other policies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Smart Campus System 8
Therefore, MTU should shift to the BYOD policy because as the trend goes, all the institutions
will employ this policy. This will enable it to fit in a competitive world.
Therefore, MTU should shift to the BYOD policy because as the trend goes, all the institutions
will employ this policy. This will enable it to fit in a competitive world.

Smart Campus System 9
References
Hong, S., Baykov, R., Xu, L., Nadimpalli, S., & Gu, G. (2016, February). Towards SDN-Defined
Programmable BYOD (Bring Your Device) Security. In NDSS.
Ilyadis, N., Chen, X., Klein, P., Hendel, A., & Siva, K. D. (2017). U.S. Patent Application No.
14/818,033.
Meske, C., Stieglitz, S., Brockmann, T., & Ross, B. (2017, July). Impact of mobile IT
consumerization on organizations–An empirical study on the adoption of BYOD
practices. In International Conference on HCI in Business, Government, and
Organizations (pp. 349-363). Springer, Cham.
Song, Y., & Kong, S. C. (2017). Affordances and constraints of BYOD (Bring Your Device) for
learning and teaching in higher education: Teachers' perspectives. The Internet and
Higher Education, 32(1), 39-46.
Vignesh, U., & Asha, S. (2015). Modifying security policies towards BYOD. Procedia
Computer Science, 50, 511-516.
Demir, K. A. (2015). Multi-View Software Architecture Design: Case Study of a Mission-Critical Defense
System. Computer and Information Science, 8(4), 12-31.
References
Hong, S., Baykov, R., Xu, L., Nadimpalli, S., & Gu, G. (2016, February). Towards SDN-Defined
Programmable BYOD (Bring Your Device) Security. In NDSS.
Ilyadis, N., Chen, X., Klein, P., Hendel, A., & Siva, K. D. (2017). U.S. Patent Application No.
14/818,033.
Meske, C., Stieglitz, S., Brockmann, T., & Ross, B. (2017, July). Impact of mobile IT
consumerization on organizations–An empirical study on the adoption of BYOD
practices. In International Conference on HCI in Business, Government, and
Organizations (pp. 349-363). Springer, Cham.
Song, Y., & Kong, S. C. (2017). Affordances and constraints of BYOD (Bring Your Device) for
learning and teaching in higher education: Teachers' perspectives. The Internet and
Higher Education, 32(1), 39-46.
Vignesh, U., & Asha, S. (2015). Modifying security policies towards BYOD. Procedia
Computer Science, 50, 511-516.
Demir, K. A. (2015). Multi-View Software Architecture Design: Case Study of a Mission-Critical Defense
System. Computer and Information Science, 8(4), 12-31.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





