Cybersecurity Challenges and Solutions in Smart Grid Systems: Review
VerifiedAdded on 2020/04/15
|49
|4696
|40
Report
AI Summary
This report presents a literature review focused on cybersecurity within smart grid systems, synthesizing key findings from several research papers. The review begins with an examination of the impact of cyberattacks on microgrid frequency control, analyzing the use of testing and analysis techniques, and the utilization of the Canadian urban benchmark frequency control system to identify and mitigate the effects of communication channel cyberattacks. The second section of the review delves into the security challenges and methods for protecting critical infrastructure cyber-physical systems, highlighting the vulnerabilities created by the interconnection between CPS and IT systems, and exploring the use of information assurance and machine learning techniques. The third paper investigates the systems-based cybersecurity in the supply chain, discussing the application of hierarchical holographic modeling and risk management tools to address risks in the supply chain. The review also includes a discussion on the cybersecurity of smart grid infrastructure, outlining the risks and vulnerabilities associated with cyber-physical control systems. The research emphasizes the importance of addressing these cybersecurity issues to ensure the reliability and security of smart grid operations.
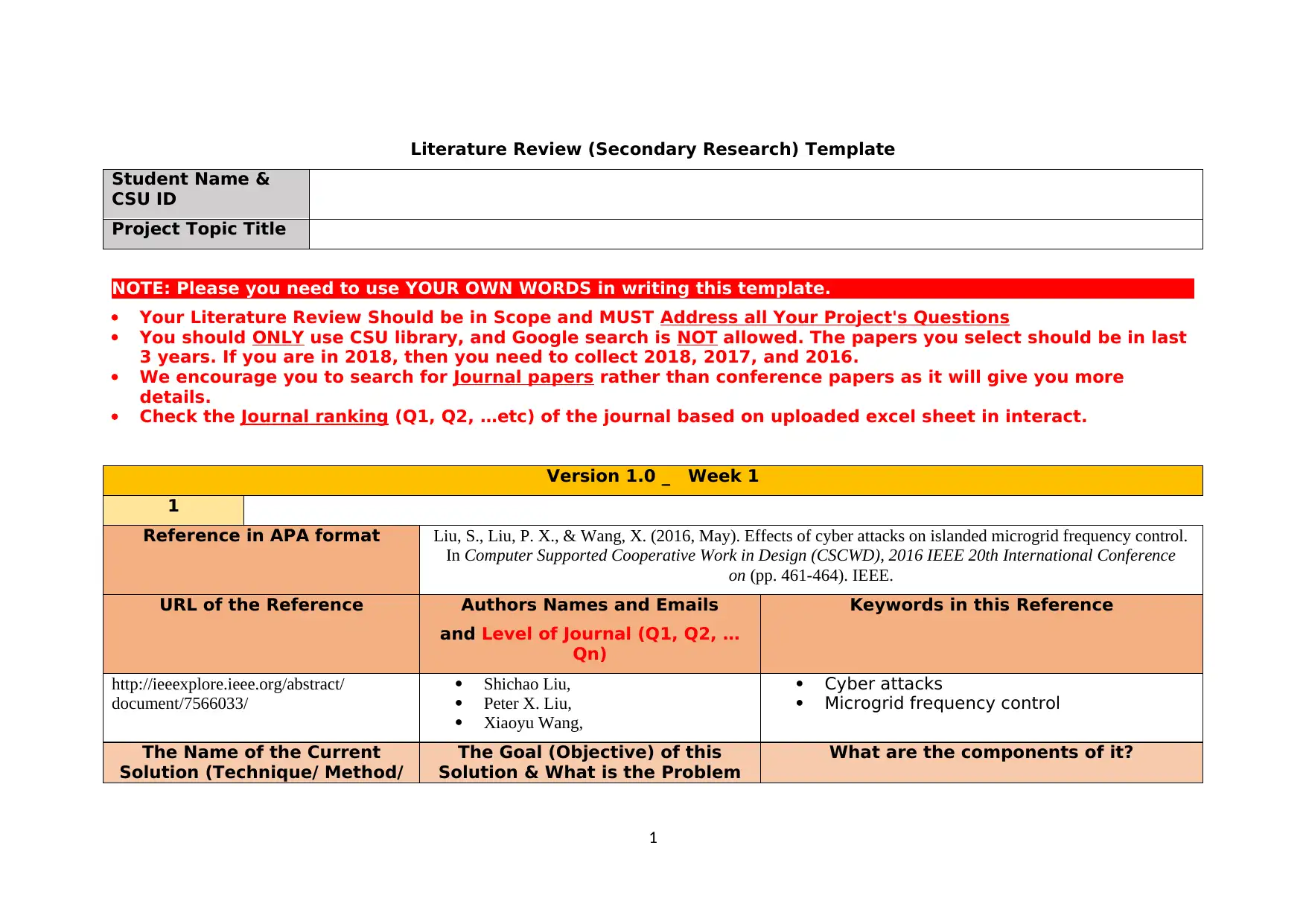
Literature Review (Secondary Research) Template
Student Name &
CSU ID
Project Topic Title
NOTE: Please you need to use YOUR OWN WORDS in writing this template.
Your Literature Review Should be in Scope and MUST Address all Your Project's Questions
You should ONLY use CSU library, and Google search is NOT allowed. The papers you select should be in last
3 years. If you are in 2018, then you need to collect 2018, 2017, and 2016.
We encourage you to search for Journal papers rather than conference papers as it will give you more
details.
Check the Journal ranking (Q1, Q2, …etc) of the journal based on uploaded excel sheet in interact.
Version 1.0 _ Week 1
1
Reference in APA format Liu, S., Liu, P. X., & Wang, X. (2016, May). Effects of cyber attacks on islanded microgrid frequency control.
In Computer Supported Cooperative Work in Design (CSCWD), 2016 IEEE 20th International Conference
on (pp. 461-464). IEEE.
URL of the Reference Authors Names and Emails
and Level of Journal (Q1, Q2, …
Qn)
Keywords in this Reference
http://ieeexplore.ieee.org/abstract/
document/7566033/
Shichao Liu,
Peter X. Liu,
Xiaoyu Wang,
Cyber attacks
Microgrid frequency control
The Name of the Current
Solution (Technique/ Method/
The Goal (Objective) of this
Solution & What is the Problem
What are the components of it?
1
Student Name &
CSU ID
Project Topic Title
NOTE: Please you need to use YOUR OWN WORDS in writing this template.
Your Literature Review Should be in Scope and MUST Address all Your Project's Questions
You should ONLY use CSU library, and Google search is NOT allowed. The papers you select should be in last
3 years. If you are in 2018, then you need to collect 2018, 2017, and 2016.
We encourage you to search for Journal papers rather than conference papers as it will give you more
details.
Check the Journal ranking (Q1, Q2, …etc) of the journal based on uploaded excel sheet in interact.
Version 1.0 _ Week 1
1
Reference in APA format Liu, S., Liu, P. X., & Wang, X. (2016, May). Effects of cyber attacks on islanded microgrid frequency control.
In Computer Supported Cooperative Work in Design (CSCWD), 2016 IEEE 20th International Conference
on (pp. 461-464). IEEE.
URL of the Reference Authors Names and Emails
and Level of Journal (Q1, Q2, …
Qn)
Keywords in this Reference
http://ieeexplore.ieee.org/abstract/
document/7566033/
Shichao Liu,
Peter X. Liu,
Xiaoyu Wang,
Cyber attacks
Microgrid frequency control
The Name of the Current
Solution (Technique/ Method/
The Goal (Objective) of this
Solution & What is the Problem
What are the components of it?
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
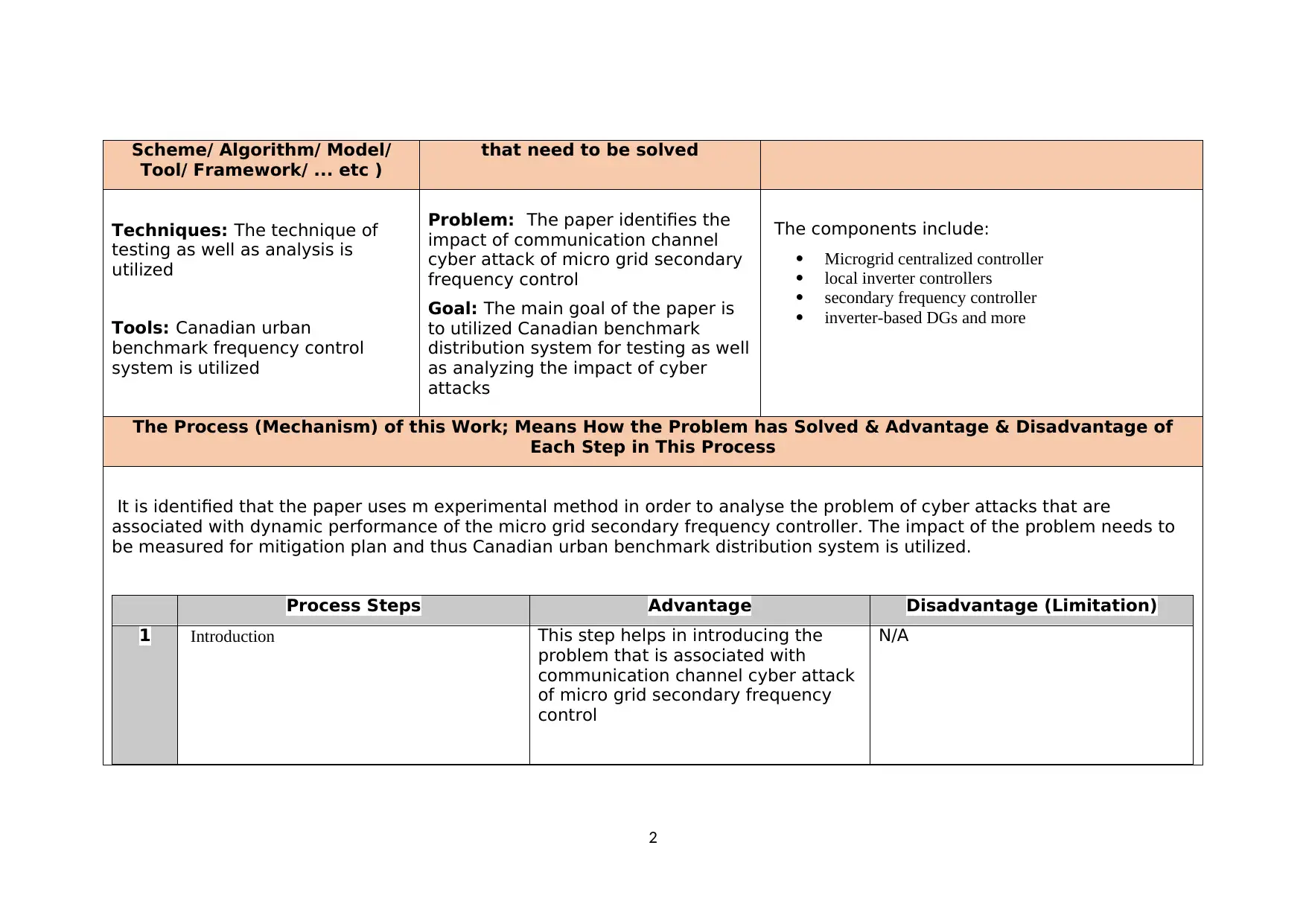
Scheme/ Algorithm/ Model/
Tool/ Framework/ ... etc )
that need to be solved
Techniques: The technique of
testing as well as analysis is
utilized
Tools: Canadian urban
benchmark frequency control
system is utilized
Problem: The paper identifies the
impact of communication channel
cyber attack of micro grid secondary
frequency control
Goal: The main goal of the paper is
to utilized Canadian benchmark
distribution system for testing as well
as analyzing the impact of cyber
attacks
The components include:
Microgrid centralized controller
local inverter controllers
secondary frequency controller
inverter-based DGs and more
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
It is identified that the paper uses m experimental method in order to analyse the problem of cyber attacks that are
associated with dynamic performance of the micro grid secondary frequency controller. The impact of the problem needs to
be measured for mitigation plan and thus Canadian urban benchmark distribution system is utilized.
Process Steps Advantage Disadvantage (Limitation)
1 Introduction This step helps in introducing the
problem that is associated with
communication channel cyber attack
of micro grid secondary frequency
control
N/A
2
Tool/ Framework/ ... etc )
that need to be solved
Techniques: The technique of
testing as well as analysis is
utilized
Tools: Canadian urban
benchmark frequency control
system is utilized
Problem: The paper identifies the
impact of communication channel
cyber attack of micro grid secondary
frequency control
Goal: The main goal of the paper is
to utilized Canadian benchmark
distribution system for testing as well
as analyzing the impact of cyber
attacks
The components include:
Microgrid centralized controller
local inverter controllers
secondary frequency controller
inverter-based DGs and more
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
It is identified that the paper uses m experimental method in order to analyse the problem of cyber attacks that are
associated with dynamic performance of the micro grid secondary frequency controller. The impact of the problem needs to
be measured for mitigation plan and thus Canadian urban benchmark distribution system is utilized.
Process Steps Advantage Disadvantage (Limitation)
1 Introduction This step helps in introducing the
problem that is associated with
communication channel cyber attack
of micro grid secondary frequency
control
N/A
2
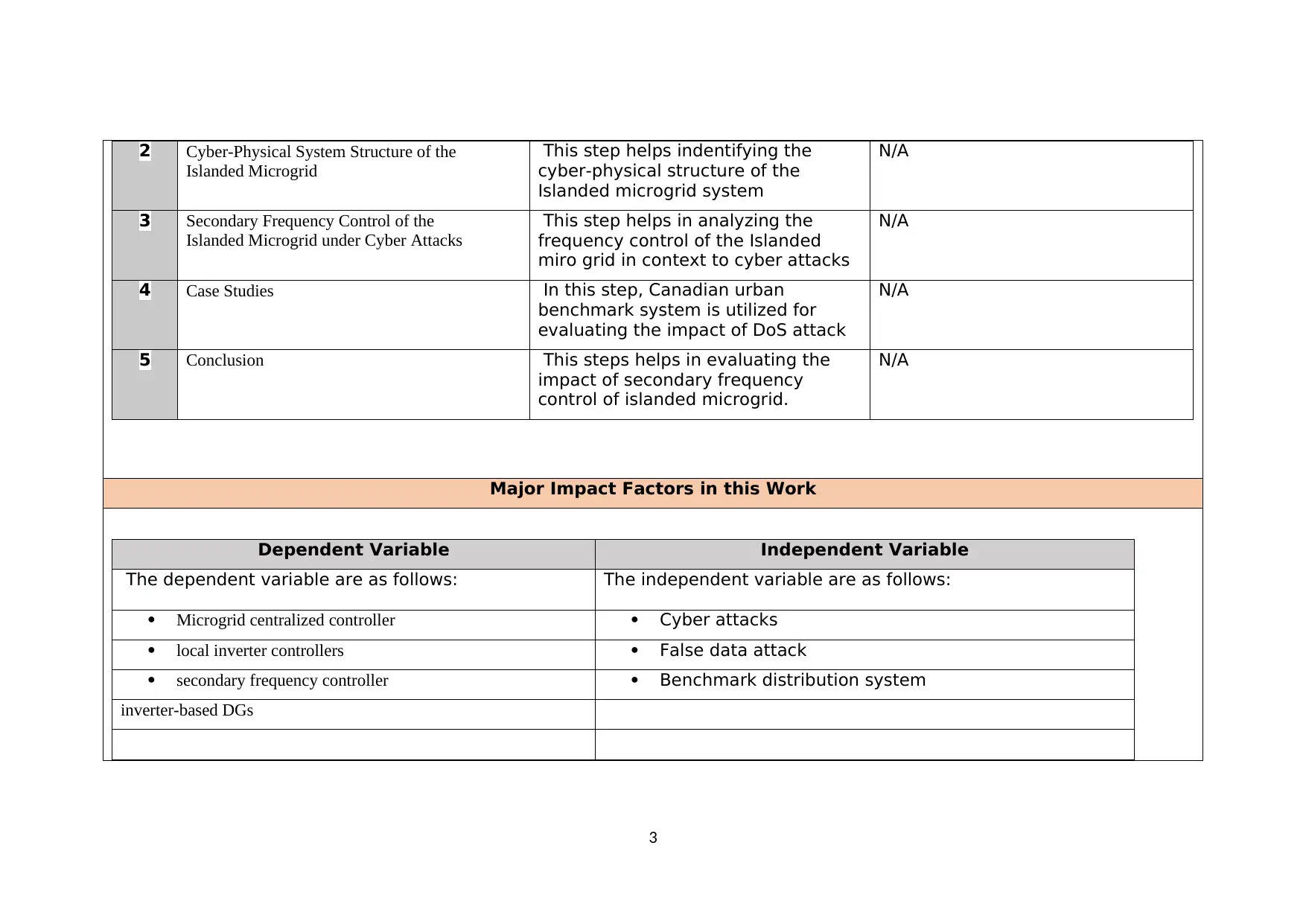
2 Cyber-Physical System Structure of the
Islanded Microgrid
This step helps indentifying the
cyber-physical structure of the
Islanded microgrid system
N/A
3 Secondary Frequency Control of the
Islanded Microgrid under Cyber Attacks
This step helps in analyzing the
frequency control of the Islanded
miro grid in context to cyber attacks
N/A
4 Case Studies In this step, Canadian urban
benchmark system is utilized for
evaluating the impact of DoS attack
N/A
5 Conclusion This steps helps in evaluating the
impact of secondary frequency
control of islanded microgrid.
N/A
Major Impact Factors in this Work
Dependent Variable Independent Variable
The dependent variable are as follows: The independent variable are as follows:
Microgrid centralized controller Cyber attacks
local inverter controllers False data attack
secondary frequency controller Benchmark distribution system
inverter-based DGs
3
Islanded Microgrid
This step helps indentifying the
cyber-physical structure of the
Islanded microgrid system
N/A
3 Secondary Frequency Control of the
Islanded Microgrid under Cyber Attacks
This step helps in analyzing the
frequency control of the Islanded
miro grid in context to cyber attacks
N/A
4 Case Studies In this step, Canadian urban
benchmark system is utilized for
evaluating the impact of DoS attack
N/A
5 Conclusion This steps helps in evaluating the
impact of secondary frequency
control of islanded microgrid.
N/A
Major Impact Factors in this Work
Dependent Variable Independent Variable
The dependent variable are as follows: The independent variable are as follows:
Microgrid centralized controller Cyber attacks
local inverter controllers False data attack
secondary frequency controller Benchmark distribution system
inverter-based DGs
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
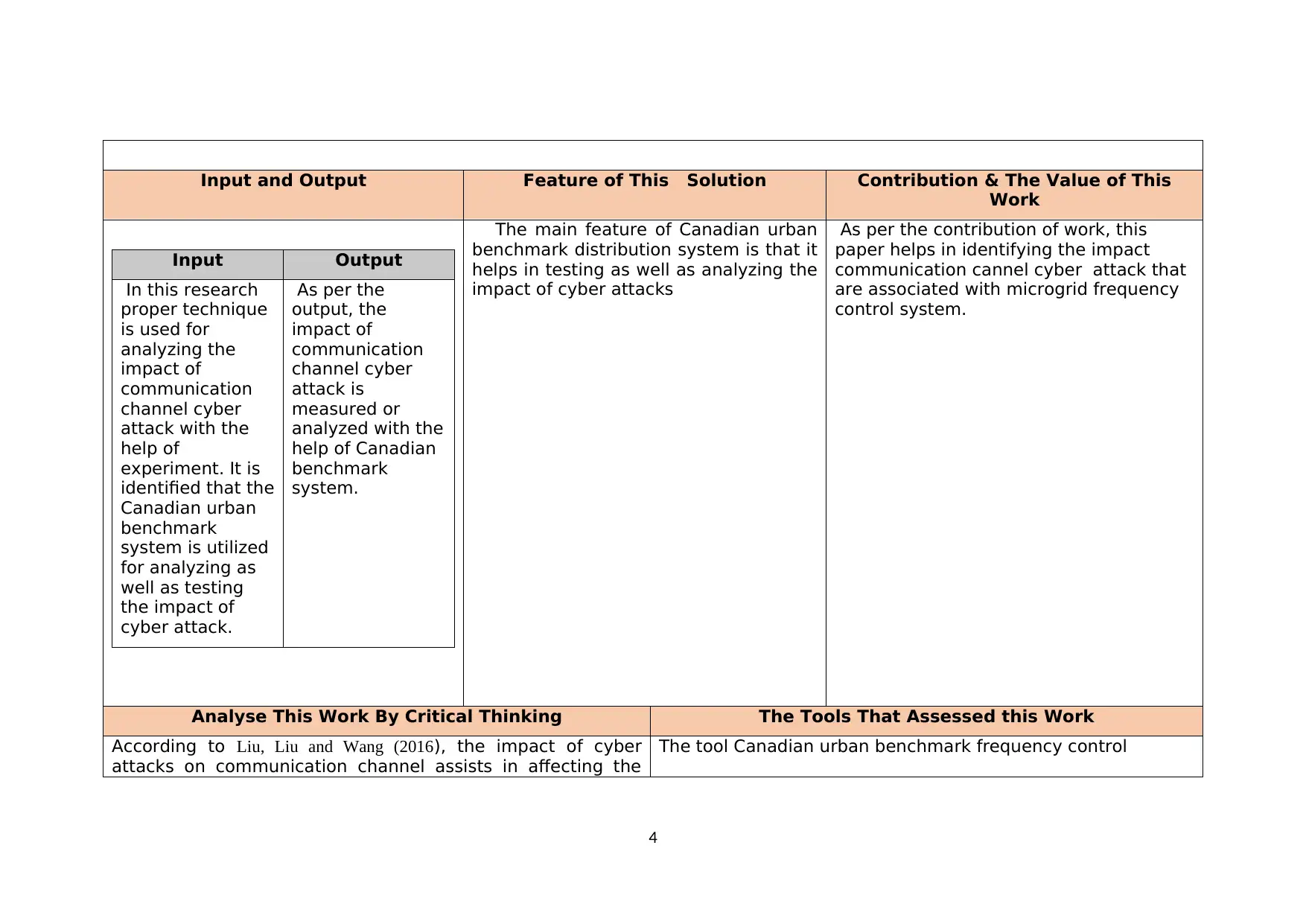
Input and Output Feature of This Solution Contribution & The Value of This
Work
Input Output
In this research
proper technique
is used for
analyzing the
impact of
communication
channel cyber
attack with the
help of
experiment. It is
identified that the
Canadian urban
benchmark
system is utilized
for analyzing as
well as testing
the impact of
cyber attack.
As per the
output, the
impact of
communication
channel cyber
attack is
measured or
analyzed with the
help of Canadian
benchmark
system.
The main feature of Canadian urban
benchmark distribution system is that it
helps in testing as well as analyzing the
impact of cyber attacks
As per the contribution of work, this
paper helps in identifying the impact
communication cannel cyber attack that
are associated with microgrid frequency
control system.
Analyse This Work By Critical Thinking The Tools That Assessed this Work
According to Liu, Liu and Wang (2016), the impact of cyber
attacks on communication channel assists in affecting the
The tool Canadian urban benchmark frequency control
4
Work
Input Output
In this research
proper technique
is used for
analyzing the
impact of
communication
channel cyber
attack with the
help of
experiment. It is
identified that the
Canadian urban
benchmark
system is utilized
for analyzing as
well as testing
the impact of
cyber attack.
As per the
output, the
impact of
communication
channel cyber
attack is
measured or
analyzed with the
help of Canadian
benchmark
system.
The main feature of Canadian urban
benchmark distribution system is that it
helps in testing as well as analyzing the
impact of cyber attacks
As per the contribution of work, this
paper helps in identifying the impact
communication cannel cyber attack that
are associated with microgrid frequency
control system.
Analyse This Work By Critical Thinking The Tools That Assessed this Work
According to Liu, Liu and Wang (2016), the impact of cyber
attacks on communication channel assists in affecting the
The tool Canadian urban benchmark frequency control
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
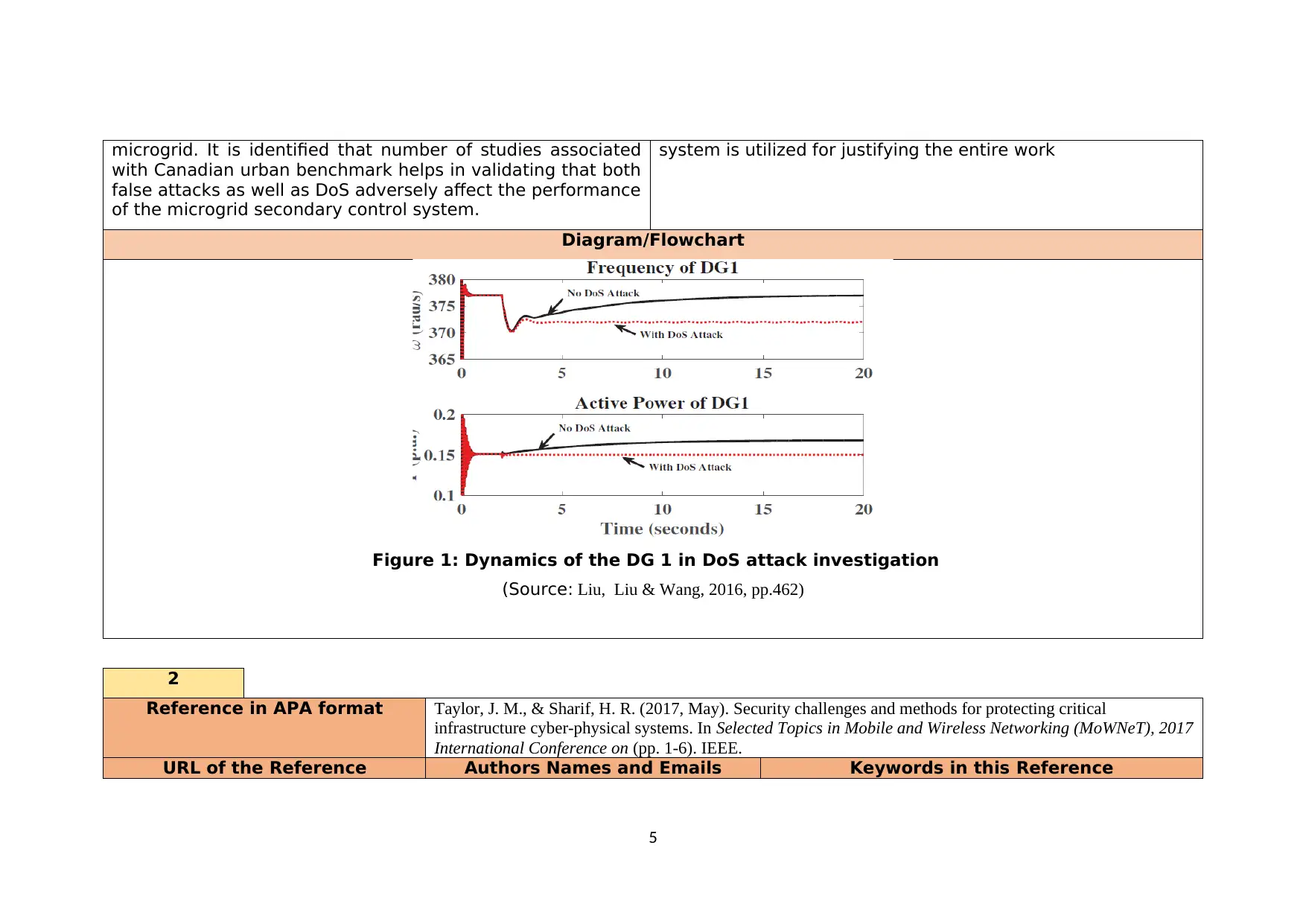
microgrid. It is identified that number of studies associated
with Canadian urban benchmark helps in validating that both
false attacks as well as DoS adversely affect the performance
of the microgrid secondary control system.
system is utilized for justifying the entire work
Diagram/Flowchart
Figure 1: Dynamics of the DG 1 in DoS attack investigation
(Source: Liu, Liu & Wang, 2016, pp.462)
2
Reference in APA format Taylor, J. M., & Sharif, H. R. (2017, May). Security challenges and methods for protecting critical
infrastructure cyber-physical systems. In Selected Topics in Mobile and Wireless Networking (MoWNeT), 2017
International Conference on (pp. 1-6). IEEE.
URL of the Reference Authors Names and Emails Keywords in this Reference
5
with Canadian urban benchmark helps in validating that both
false attacks as well as DoS adversely affect the performance
of the microgrid secondary control system.
system is utilized for justifying the entire work
Diagram/Flowchart
Figure 1: Dynamics of the DG 1 in DoS attack investigation
(Source: Liu, Liu & Wang, 2016, pp.462)
2
Reference in APA format Taylor, J. M., & Sharif, H. R. (2017, May). Security challenges and methods for protecting critical
infrastructure cyber-physical systems. In Selected Topics in Mobile and Wireless Networking (MoWNeT), 2017
International Conference on (pp. 1-6). IEEE.
URL of the Reference Authors Names and Emails Keywords in this Reference
5
and Level of Journal (Q1, Q2, …
Qn)
http://ieeexplore.ieee.org/
abstract/document/8045959/
James M. Taylor
Hamid R. Sharif
Security challenges
Cyber-physical system
Critical infrastructure
The Name of the Current
Solution (Technique/ Method/
Scheme/ Algorithm/ Model/
Tool/ Framework/ ... etc )
The Goal (Objective) of this
Solution & What is the problem
that need to be solved
What are the components of it?
Techniques: Information
assurance technique as well as
machine learning technique is used
Tools: Cyber physical system as
well as industrial control system is
utilized.
Problem: It is identified that the
interconnection between CPS as well
as IT systems created number of
security vulnerabilities including
cyber attacks, denial of service and
more
Goal: The main goal of this paper is
to identifies approaches that are
helpful in minimizing the complexity
of the security methods
The components include:
Cyber physical system
Industrial control system
Cyber physical adversary
CPS security and more
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
It is identified that the risks as well as challenges that are associated with CPS as well as IT system can be resolved by
utilizing methods that include industrial control system, as well as performance system.
6
Qn)
http://ieeexplore.ieee.org/
abstract/document/8045959/
James M. Taylor
Hamid R. Sharif
Security challenges
Cyber-physical system
Critical infrastructure
The Name of the Current
Solution (Technique/ Method/
Scheme/ Algorithm/ Model/
Tool/ Framework/ ... etc )
The Goal (Objective) of this
Solution & What is the problem
that need to be solved
What are the components of it?
Techniques: Information
assurance technique as well as
machine learning technique is used
Tools: Cyber physical system as
well as industrial control system is
utilized.
Problem: It is identified that the
interconnection between CPS as well
as IT systems created number of
security vulnerabilities including
cyber attacks, denial of service and
more
Goal: The main goal of this paper is
to identifies approaches that are
helpful in minimizing the complexity
of the security methods
The components include:
Cyber physical system
Industrial control system
Cyber physical adversary
CPS security and more
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
It is identified that the risks as well as challenges that are associated with CPS as well as IT system can be resolved by
utilizing methods that include industrial control system, as well as performance system.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Process Steps Advantage Disadvantage (Limitation)
1 Introduction This step helps in providing an
overview about the risks that are
associated with CPS as well as IT
system
N/A
2 Overview of CPS and security This step provides overview about
CPS and its security.
N/A
3 CPS security challenges This step elaborates the challenges
that are associated with CPS
N/A
4 Security methods for CPS This step provides security methods
for CPS
N/A
5 Conclusion This step develops proper
approaches for enhancing
confidentiality protection.
N/A
Major Impact Factors in this Work
Dependent Variable Independent Variable
Confidentiality IT system
Cyber attack CPS system
Availability Industrial control system
Integrity
7
1 Introduction This step helps in providing an
overview about the risks that are
associated with CPS as well as IT
system
N/A
2 Overview of CPS and security This step provides overview about
CPS and its security.
N/A
3 CPS security challenges This step elaborates the challenges
that are associated with CPS
N/A
4 Security methods for CPS This step provides security methods
for CPS
N/A
5 Conclusion This step develops proper
approaches for enhancing
confidentiality protection.
N/A
Major Impact Factors in this Work
Dependent Variable Independent Variable
Confidentiality IT system
Cyber attack CPS system
Availability Industrial control system
Integrity
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Relationship Among The Above 4 Variables in This article
Input and Output Feature of This Solution Contribution in This Work
Input Output
As an input,
proper analysis
on the security
issues of CPS
system is done.
As an out, the
issues of CPS
system can be
resolved by
utilizing
appropriate
approaches
The paper is quite helpful in resolving
the issue that is associated with the
CPS as well as IT system. Proper
approaches are utilized in order to
resolve the security issue.
It is identified that this research paper
is helpful in identifying methods as well
as approaches that are quite helpful in
mitigating the challenges that re
associated with the CPS system.
Analyse This Work By Critical Thinking The Tools That Assessed this Work
According to Taylor and Sharif (2017), cyber physical system
helps in representing a fundamental link between the
devices as well as information system for control as well as
maintaining the services. However it is found that the
linkage among CPS as well as IT system create number of
security related challenges.
It is found that utilization of industrial control system is
helpful in satisfying the work.
8
Input and Output Feature of This Solution Contribution in This Work
Input Output
As an input,
proper analysis
on the security
issues of CPS
system is done.
As an out, the
issues of CPS
system can be
resolved by
utilizing
appropriate
approaches
The paper is quite helpful in resolving
the issue that is associated with the
CPS as well as IT system. Proper
approaches are utilized in order to
resolve the security issue.
It is identified that this research paper
is helpful in identifying methods as well
as approaches that are quite helpful in
mitigating the challenges that re
associated with the CPS system.
Analyse This Work By Critical Thinking The Tools That Assessed this Work
According to Taylor and Sharif (2017), cyber physical system
helps in representing a fundamental link between the
devices as well as information system for control as well as
maintaining the services. However it is found that the
linkage among CPS as well as IT system create number of
security related challenges.
It is found that utilization of industrial control system is
helpful in satisfying the work.
8
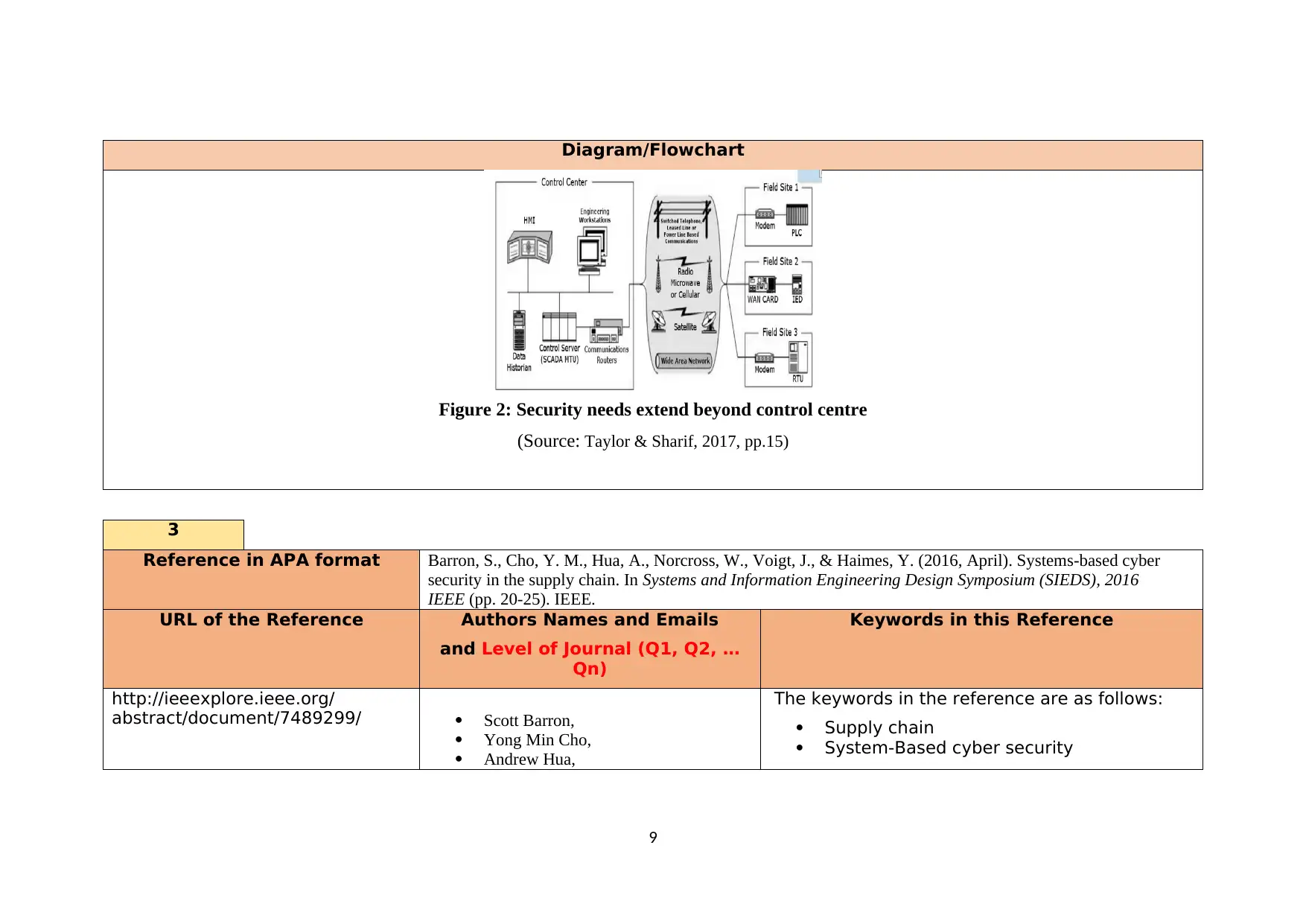
Diagram/Flowchart
Figure 2: Security needs extend beyond control centre
(Source: Taylor & Sharif, 2017, pp.15)
3
Reference in APA format Barron, S., Cho, Y. M., Hua, A., Norcross, W., Voigt, J., & Haimes, Y. (2016, April). Systems-based cyber
security in the supply chain. In Systems and Information Engineering Design Symposium (SIEDS), 2016
IEEE (pp. 20-25). IEEE.
URL of the Reference Authors Names and Emails
and Level of Journal (Q1, Q2, …
Qn)
Keywords in this Reference
http://ieeexplore.ieee.org/
abstract/document/7489299/ Scott Barron,
Yong Min Cho,
Andrew Hua,
The keywords in the reference are as follows:
Supply chain
System-Based cyber security
9
Figure 2: Security needs extend beyond control centre
(Source: Taylor & Sharif, 2017, pp.15)
3
Reference in APA format Barron, S., Cho, Y. M., Hua, A., Norcross, W., Voigt, J., & Haimes, Y. (2016, April). Systems-based cyber
security in the supply chain. In Systems and Information Engineering Design Symposium (SIEDS), 2016
IEEE (pp. 20-25). IEEE.
URL of the Reference Authors Names and Emails
and Level of Journal (Q1, Q2, …
Qn)
Keywords in this Reference
http://ieeexplore.ieee.org/
abstract/document/7489299/ Scott Barron,
Yong Min Cho,
Andrew Hua,
The keywords in the reference are as follows:
Supply chain
System-Based cyber security
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
William Norcross,
Jack Voigt, and
Yacov Haimes
The Name of the Current
Solution (Technique/ Method/
Scheme/ Algorithm/ Model/
Tool/ Framework/ ... etc )
The Goal (Objective) of this
Solution & What is the problem
that need to be solved
What are the components of it?
Techniques: Hierarchical Holographic
Modeling technique is utilized.
Tools: Proper risk filtering as well
as risk management tools must be
used.
Problem: The paper highlights the
risks that are associated with the
supply chain.
Goal: The main goal of the paper is
to utilize proper risk filtering as well
as management method for reducing
the number of risk scenarios. In
addition to this, proper modelling as
well as skills are utilized examining
the impact of malevolent medium for
decimating the safety critical supply
chain system.
The components include:
Supervisory Control and Data Acquisition (SCADA)
systems.
Hierarchical Holographic modelling
Risk Filtering
Risk management
Global supply chain
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
Process Steps Advantage Disadvantage (Limitation)
1 Introduction The step elaborates about supply
chain, risk management as well as
N/A
10
Jack Voigt, and
Yacov Haimes
The Name of the Current
Solution (Technique/ Method/
Scheme/ Algorithm/ Model/
Tool/ Framework/ ... etc )
The Goal (Objective) of this
Solution & What is the problem
that need to be solved
What are the components of it?
Techniques: Hierarchical Holographic
Modeling technique is utilized.
Tools: Proper risk filtering as well
as risk management tools must be
used.
Problem: The paper highlights the
risks that are associated with the
supply chain.
Goal: The main goal of the paper is
to utilize proper risk filtering as well
as management method for reducing
the number of risk scenarios. In
addition to this, proper modelling as
well as skills are utilized examining
the impact of malevolent medium for
decimating the safety critical supply
chain system.
The components include:
Supervisory Control and Data Acquisition (SCADA)
systems.
Hierarchical Holographic modelling
Risk Filtering
Risk management
Global supply chain
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
Process Steps Advantage Disadvantage (Limitation)
1 Introduction The step elaborates about supply
chain, risk management as well as
N/A
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3D printing
2 System Methodology This steps discuses risk assessment,
management as well as
communication procedures
N/A
3 Risk Filtering and risk monitoring
methodology
This steps illustrates risk filtering as
well as risk management
methodology
N/A
4 3D printing experiment The step discusses the importance
of 3D printing experiment
N/A
5 Conclusion The conclusion reflects that N/A
Major Impact Factors in this Work
Dependent Variable Independent Variable
Risk filtering Hierarchical Holographic Modelling
Risk assessment Global supply chain
Communication Three-dimensional printing (3D).
Risk management
Relationship Among The Above 4 Variables in This article
11
2 System Methodology This steps discuses risk assessment,
management as well as
communication procedures
N/A
3 Risk Filtering and risk monitoring
methodology
This steps illustrates risk filtering as
well as risk management
methodology
N/A
4 3D printing experiment The step discusses the importance
of 3D printing experiment
N/A
5 Conclusion The conclusion reflects that N/A
Major Impact Factors in this Work
Dependent Variable Independent Variable
Risk filtering Hierarchical Holographic Modelling
Risk assessment Global supply chain
Communication Three-dimensional printing (3D).
Risk management
Relationship Among The Above 4 Variables in This article
11
Input and Output Feature of This Solution Contribution in This Work
Input Output
As an input,
Hierarchical
holographic
modelling is
utilized
As an output the
proper as well as
safe supply chain
modelling is
present
The main feature is that the problem
of cyber security that is associated with
supply chain can be easily resolved by
utilizing proper modeling as well as risk
management method.
The research is quite helpful in
resolving the cyber security issue that is
mainly associated with supply chain
management system
Analyse This Work By Critical Thinking The Tools That Assessed this Work
According to Barron et al. (2016), in order to have proper
understanding of the risk needs in the supply chain it is
quite important to develop proper foundation of system
risks
Hierarchical holographic modelling is utilized for assessing the
entire research work
Diagram/Flowchart
12
Input Output
As an input,
Hierarchical
holographic
modelling is
utilized
As an output the
proper as well as
safe supply chain
modelling is
present
The main feature is that the problem
of cyber security that is associated with
supply chain can be easily resolved by
utilizing proper modeling as well as risk
management method.
The research is quite helpful in
resolving the cyber security issue that is
mainly associated with supply chain
management system
Analyse This Work By Critical Thinking The Tools That Assessed this Work
According to Barron et al. (2016), in order to have proper
understanding of the risk needs in the supply chain it is
quite important to develop proper foundation of system
risks
Hierarchical holographic modelling is utilized for assessing the
entire research work
Diagram/Flowchart
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 49
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
