Smart Grids and Associated Security Protocols: Comprehensive Analysis
VerifiedAdded on 2022/11/14
|17
|4603
|302
Report
AI Summary
This report provides a comprehensive overview of smart grids and their associated security protocols. It begins with an introduction to smart grid technology, highlighting its characteristics, domains, and the role of the Internet of Things (IoT). The report then delves into the challenges faced by smart grids, particularly those related to interoperability, awareness, and technical complexities. A significant portion is dedicated to discussing security and privacy issues, including vulnerabilities and potential attack vectors. The core of the report focuses on various standards and protocols used in smart grids, such as IEC 61970, IEC 61850, IEEE C37.118, and DNP3, categorizing them based on their application in different areas like enterprise, substation automation, and wide-area monitoring. The report also provides a comparison of these protocols, assessing their suitability for smart grid environments. The report concludes by emphasizing the importance of robust security measures to ensure the reliability and integrity of smart grid systems.

Running head: SMART GRIDS AND THE ASSOCIATED SECURITY PROTOCOLS
SMART GRIDS AND THE ASSOCIATED SECURITY PROTOCOLS
Name of the Student
Name of the university
Author note
SMART GRIDS AND THE ASSOCIATED SECURITY PROTOCOLS
Name of the Student
Name of the university
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
Table of Contents
Introduction................................................................................................................................2
Characteristics of the Smart Grid System..............................................................................2
Generation of Smart Grid Domains...........................................................................................3
Transmission of Smart Grid Domains........................................................................................4
Distribution of Smart Grid Domains..........................................................................................5
Operations of Smart Grid Domains............................................................................................5
Security and Privacy Issues related to Smart Grids...................................................................6
Standards and protocols related to Smart Grids.........................................................................7
Comparison between the protocols and assessing the best for Smart Grids............................12
Conclusion................................................................................................................................13
References................................................................................................................................14
Table of Contents
Introduction................................................................................................................................2
Characteristics of the Smart Grid System..............................................................................2
Generation of Smart Grid Domains...........................................................................................3
Transmission of Smart Grid Domains........................................................................................4
Distribution of Smart Grid Domains..........................................................................................5
Operations of Smart Grid Domains............................................................................................5
Security and Privacy Issues related to Smart Grids...................................................................6
Standards and protocols related to Smart Grids.........................................................................7
Comparison between the protocols and assessing the best for Smart Grids............................12
Conclusion................................................................................................................................13
References................................................................................................................................14

2SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
Introduction
Smart grid is a modern technology that aids bidirectional flow of the energy and
makes use of both way communication and also controls the capabilities that leads to a range
of new applications and various functionalities. It is considered as “System of Systems” and
in smart grids each of the functional domains consist of three different layers that are the
communication layer, power and energy layer and the IT computer layer (Hurtado, Nguyen &
Kling 2015). The communication and the IT computer layer are the two infrastructures which
make the present power and the energy structure smarter. The technology has evolved in the
market to enhance the power generation and to help in maximizing production. These grids
help are effective in delivering in a two way process controlling the home appliances. The
smart model helps save energy and has the potential to reduce the costs thereby increasing the
transparency and the reliability of the network (Tsai & Lo, 2015). The major target of the
system is to decrease loss in power and inculcate advance monitoring systems. It is an
advanced version of the traditional power grid that helps to enhance intelligent decisions thus
making the system stable and reliable. The performance of the smart grid technology has
maintained desirous approach in the sphere of development in generating power, the most
sustainable way.
IoT in Smart Grids:
IoT or the Internet of Things is the concept which can be addressed in an unique
manner and is associated with including the physical objects which are connected to the
internet for the purpose of identifying themselves to the other devices based upon the TCP/IP
stacks (Akinsomi et al., 2016). Besides this the identifiable, along with the autonomous,
adaptive responsive and the self-configurable entities are capable of interacting with one
another along with cooperating in a continuous manner with one another for the purpose of
Introduction
Smart grid is a modern technology that aids bidirectional flow of the energy and
makes use of both way communication and also controls the capabilities that leads to a range
of new applications and various functionalities. It is considered as “System of Systems” and
in smart grids each of the functional domains consist of three different layers that are the
communication layer, power and energy layer and the IT computer layer (Hurtado, Nguyen &
Kling 2015). The communication and the IT computer layer are the two infrastructures which
make the present power and the energy structure smarter. The technology has evolved in the
market to enhance the power generation and to help in maximizing production. These grids
help are effective in delivering in a two way process controlling the home appliances. The
smart model helps save energy and has the potential to reduce the costs thereby increasing the
transparency and the reliability of the network (Tsai & Lo, 2015). The major target of the
system is to decrease loss in power and inculcate advance monitoring systems. It is an
advanced version of the traditional power grid that helps to enhance intelligent decisions thus
making the system stable and reliable. The performance of the smart grid technology has
maintained desirous approach in the sphere of development in generating power, the most
sustainable way.
IoT in Smart Grids:
IoT or the Internet of Things is the concept which can be addressed in an unique
manner and is associated with including the physical objects which are connected to the
internet for the purpose of identifying themselves to the other devices based upon the TCP/IP
stacks (Akinsomi et al., 2016). Besides this the identifiable, along with the autonomous,
adaptive responsive and the self-configurable entities are capable of interacting with one
another along with cooperating in a continuous manner with one another for the purpose of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
ensuring the ubiquitous communication to the peers as well as to the servers in the internet
(Suleiman et al., 2015). This particular automated form of communication model devices
have been associated with becoming aware of eth context along with being associated with
organizing themselves, transferring of the information and responding to the changes taking
place in circumstances which are dynamic.
The power Internet of Things or the PIoT is the application of the internet of things
upon the smart grids (Kalalas, Thrybom & Alonso-Zarate, 2016). The power Internet of
things is capable of achieving a reliable form of transmission of the information by means of
wired or wireless communication network along with smart processing of information in the
power grid systems. Besides this the PIoT is also seen to be widely applied in each and every
aspect of the smart grids which includes the generation of power, power transmission,
transformation of information, distribution of power and power consumption (Aghajani,
Shayanfar & Shayeghi, 2017). The power internet of things are divided into three layers and
this is associated with including the perception layer, the network layer and the application
layer.
Challenges faced by Smart grids:
The IoT has been deployed in eth smart grids so as to enable the two way
communication by having an aim of making the electricity girds become smarter. One of the
fundamental attribute which is seen to be very vital in the process of integrating with the
other smart devices for the purpose of enabling the applications of the smart grids which
includes the interoperability amongst the various devices and platforms (Yoldaş et al., 2017).
Despite of the progress which has been made with respect to the deployment of the Power
internet of things in the smart grids along with the implementation, there still exists many
challenges which are faced by the smart grids related to the standards and the protocols which
ensuring the ubiquitous communication to the peers as well as to the servers in the internet
(Suleiman et al., 2015). This particular automated form of communication model devices
have been associated with becoming aware of eth context along with being associated with
organizing themselves, transferring of the information and responding to the changes taking
place in circumstances which are dynamic.
The power Internet of Things or the PIoT is the application of the internet of things
upon the smart grids (Kalalas, Thrybom & Alonso-Zarate, 2016). The power Internet of
things is capable of achieving a reliable form of transmission of the information by means of
wired or wireless communication network along with smart processing of information in the
power grid systems. Besides this the PIoT is also seen to be widely applied in each and every
aspect of the smart grids which includes the generation of power, power transmission,
transformation of information, distribution of power and power consumption (Aghajani,
Shayanfar & Shayeghi, 2017). The power internet of things are divided into three layers and
this is associated with including the perception layer, the network layer and the application
layer.
Challenges faced by Smart grids:
The IoT has been deployed in eth smart grids so as to enable the two way
communication by having an aim of making the electricity girds become smarter. One of the
fundamental attribute which is seen to be very vital in the process of integrating with the
other smart devices for the purpose of enabling the applications of the smart grids which
includes the interoperability amongst the various devices and platforms (Yoldaş et al., 2017).
Despite of the progress which has been made with respect to the deployment of the Power
internet of things in the smart grids along with the implementation, there still exists many
challenges which are faced by the smart grids related to the standards and the protocols which
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
needs to be addressed. Amongst the major challenge is the interoperability of the devices and
platforms (Arasteh et al., 2016). Interoperability generally refers to the ability of the different
kind of devices and the platforms to exchange the information along with the work in a
cooperative manner so as to accomplish the smart applications. The second challenge which
is faced is the lack of awareness. even after the existence of the fact that many of the
standards are existing which are related to the smart grids there still exists a lack with respect
to the awareness of the availability of the smart grid standards as well as protocols along with
the lack in proper guidelines related to the application of the standards in the smart grid
deployments. Followed by this the third major challenge includes the technical challenges.
The electrical power grids are seen to be compromising of a large number of electric
components which are seen to be tightly coupled together and are operating in a dependent
manner. The forth challenge which is faced by the smart grids is associated with including the
complexity challenges (Wang et al., 2017). The Power Internet of Things based smart grids
are considered to be an extremely complex system which is associated with including many
subsystems. Many of the smart grid projects are associated with the smart grid standards
which are developed for the purpose of overcoming the challenges and in the later section of
eth report some of the major security protocols have been discussed along with selecting the
most appropriate standard.
Security and Privacy Issues related to Smart Grids
The main aim of the smart grid system is to make improvements in the security and
the reliability of the grid. There are some privacy and security implications with this
technology as well. They are exposed to the computer vulnerabilities and the increasing
number of attackers with the incentives related to it (Yi, Qin & Li, 2015). The smart devices
that have been deployed in smart grid systems are supported by commodity software and
hardware and are vulnerable to the other networks’ security vulnerabilities. The researches
needs to be addressed. Amongst the major challenge is the interoperability of the devices and
platforms (Arasteh et al., 2016). Interoperability generally refers to the ability of the different
kind of devices and the platforms to exchange the information along with the work in a
cooperative manner so as to accomplish the smart applications. The second challenge which
is faced is the lack of awareness. even after the existence of the fact that many of the
standards are existing which are related to the smart grids there still exists a lack with respect
to the awareness of the availability of the smart grid standards as well as protocols along with
the lack in proper guidelines related to the application of the standards in the smart grid
deployments. Followed by this the third major challenge includes the technical challenges.
The electrical power grids are seen to be compromising of a large number of electric
components which are seen to be tightly coupled together and are operating in a dependent
manner. The forth challenge which is faced by the smart grids is associated with including the
complexity challenges (Wang et al., 2017). The Power Internet of Things based smart grids
are considered to be an extremely complex system which is associated with including many
subsystems. Many of the smart grid projects are associated with the smart grid standards
which are developed for the purpose of overcoming the challenges and in the later section of
eth report some of the major security protocols have been discussed along with selecting the
most appropriate standard.
Security and Privacy Issues related to Smart Grids
The main aim of the smart grid system is to make improvements in the security and
the reliability of the grid. There are some privacy and security implications with this
technology as well. They are exposed to the computer vulnerabilities and the increasing
number of attackers with the incentives related to it (Yi, Qin & Li, 2015). The smart devices
that have been deployed in smart grid systems are supported by commodity software and
hardware and are vulnerable to the other networks’ security vulnerabilities. The researches
5SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
that have been conducted demonstrate a worm which spreads in between the smart meters.
Meter based injected viruses, meter bots, usage loggers, denial of service attacks and other
possible malwares are possible in the future (Jokar, Arianpoo & Leung, 2016). To add to
these vulnerabilities, there is high possibility of attacks through the enormous entry points
that are opened in case of deploying the smart devices. The similar characteristics of the
devices installed means that a fault in one device could be exploited in all the other devices
connected thus making it easy for the attackers to disrupt the system. The old ways of attacks
involve the inversion attacks that are responsible for turning the meter backward and the
reading is counted backwards, using of magnets having high intensity power to lower the rate
that has been recorded and some simple destructions that are made physically (Han & Xiao,
2016). The new ways of attacks will require just attacking a single smart meter by making
use of a low-tech mechanical instrument and could disrupt many meters at a stretch.
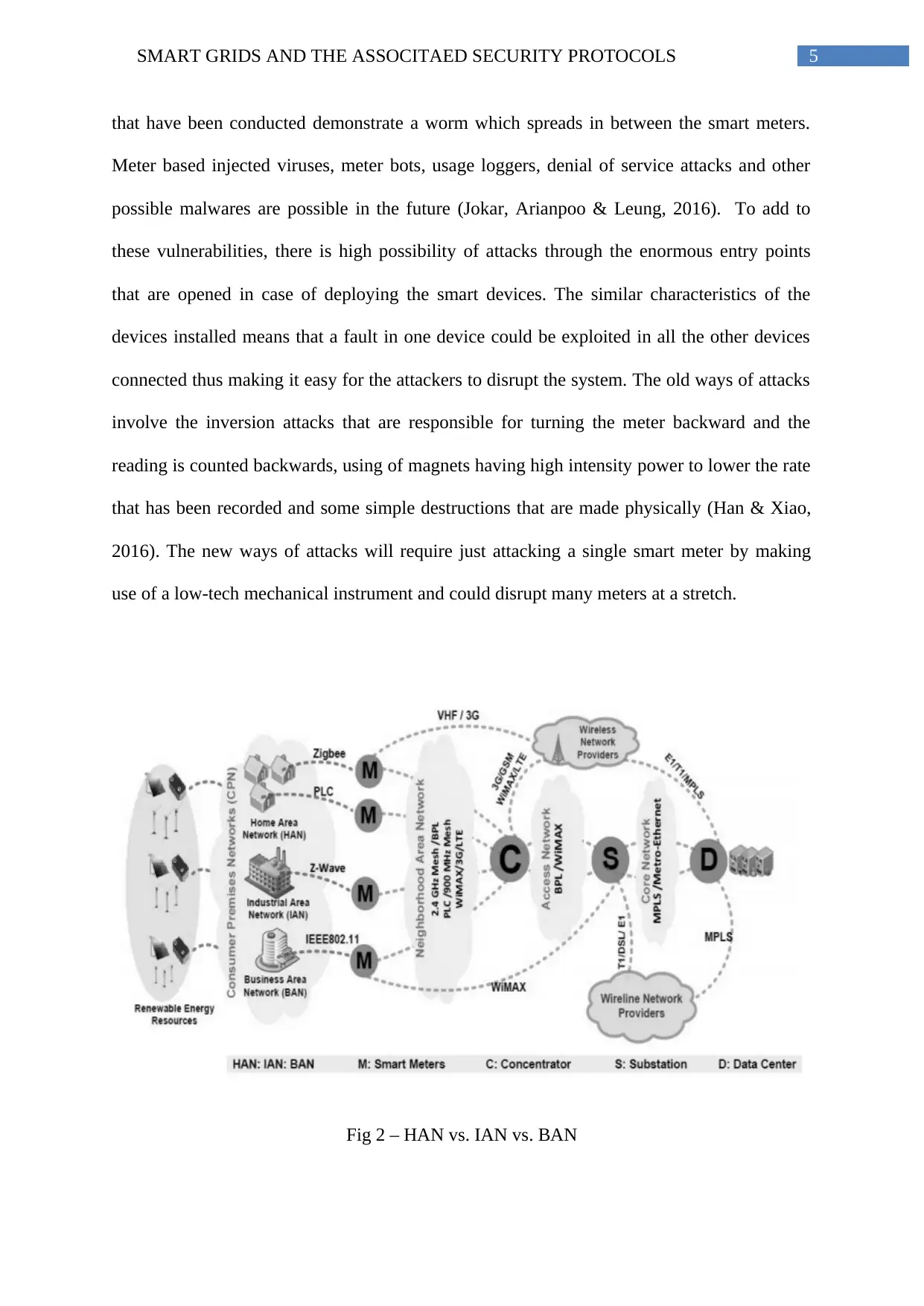
Fig 2 – HAN vs. IAN vs. BAN
that have been conducted demonstrate a worm which spreads in between the smart meters.
Meter based injected viruses, meter bots, usage loggers, denial of service attacks and other
possible malwares are possible in the future (Jokar, Arianpoo & Leung, 2016). To add to
these vulnerabilities, there is high possibility of attacks through the enormous entry points
that are opened in case of deploying the smart devices. The similar characteristics of the
devices installed means that a fault in one device could be exploited in all the other devices
connected thus making it easy for the attackers to disrupt the system. The old ways of attacks
involve the inversion attacks that are responsible for turning the meter backward and the
reading is counted backwards, using of magnets having high intensity power to lower the rate
that has been recorded and some simple destructions that are made physically (Han & Xiao,
2016). The new ways of attacks will require just attacking a single smart meter by making
use of a low-tech mechanical instrument and could disrupt many meters at a stretch.
Fig 2 – HAN vs. IAN vs. BAN
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
Reference: (Arasteh et al., 2016).
Standards and protocols related to Smart Grids
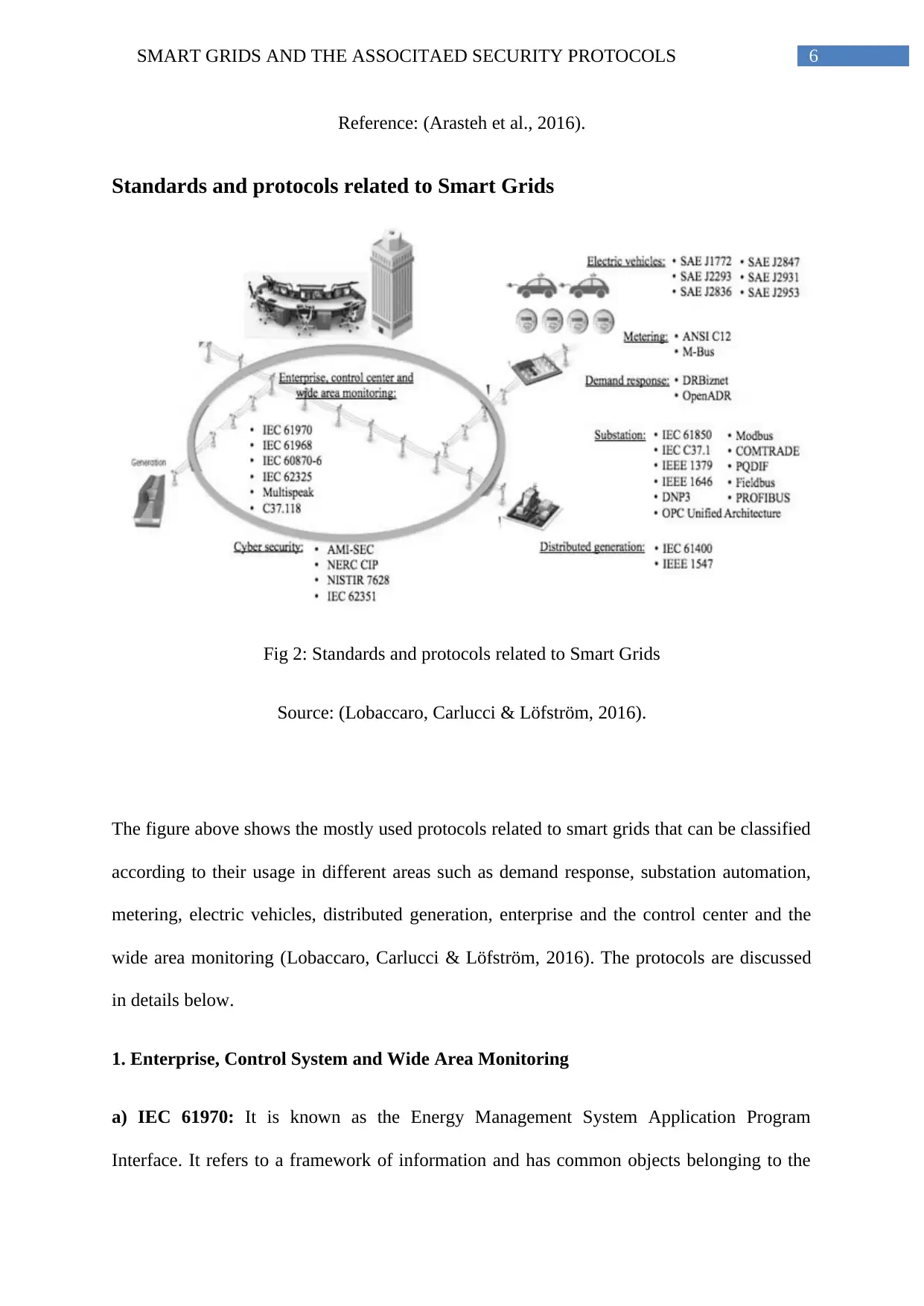
Fig 2: Standards and protocols related to Smart Grids
Source: (Lobaccaro, Carlucci & Löfström, 2016).
The figure above shows the mostly used protocols related to smart grids that can be classified
according to their usage in different areas such as demand response, substation automation,
metering, electric vehicles, distributed generation, enterprise and the control center and the
wide area monitoring (Lobaccaro, Carlucci & Löfström, 2016). The protocols are discussed
in details below.
1. Enterprise, Control System and Wide Area Monitoring
a) IEC 61970: It is known as the Energy Management System Application Program
Interface. It refers to a framework of information and has common objects belonging to the
Reference: (Arasteh et al., 2016).
Standards and protocols related to Smart Grids
Fig 2: Standards and protocols related to Smart Grids
Source: (Lobaccaro, Carlucci & Löfström, 2016).
The figure above shows the mostly used protocols related to smart grids that can be classified
according to their usage in different areas such as demand response, substation automation,
metering, electric vehicles, distributed generation, enterprise and the control center and the
wide area monitoring (Lobaccaro, Carlucci & Löfström, 2016). The protocols are discussed
in details below.
1. Enterprise, Control System and Wide Area Monitoring
a) IEC 61970: It is known as the Energy Management System Application Program
Interface. It refers to a framework of information and has common objects belonging to the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
region of transmission systems of electricity in order to provide a model that is semantic (Lu
et al., 2016). It provides an abstract Application Program Interface for enabling exchange of
data and is independent of the platform and the technology (Yoo & Shon, 2016). IEC 61970
can be run on different operating systems having distinct programming languages and
database systems.
b) IEC 60870-6: This protocol defines the systems that are used in tele-control that is the
Supervisory Control and Data Acquisition with regard to the power applications of power
systems (Schlegel, R., Obermeier & Schneider, 2015). In IEC 60870-6 a standard profile for
the purpose of data transfer has been defined that allows monitoring and controlling the wide
area networks amidst the control centers.
c) IEC 62325: This protocol provides a standard protocol that serves as general guidelines in
the use of eXtensible Markup language technology and is a base for the architecture of the
communication in the energy markets. The main target of IEC 62325 is enabling integration
of the designed market-based software applications by distinct vendors that run
independently.
d) Multispeak: The National Rural Electric Cooperative Association developed Multispeak
and this addresses the domain responsible for electric distribution focusing on the market
based at U.S. It helps providing interoperability in the different application software that is
used by the electric utilities.
e) IEEE C37.118: It is a set standard for the synchrophasors used for the power systems that
define the requirements on the measurement of phasor’s data exchange. This protocol is
based on IP and Ethernet and has been developed for reporting the synchronized
measurement data of the phasor (Khan et al., 2016). It is a protocol that specifies the methods
to quantify the measurement of the phasor and the test procedures.
region of transmission systems of electricity in order to provide a model that is semantic (Lu
et al., 2016). It provides an abstract Application Program Interface for enabling exchange of
data and is independent of the platform and the technology (Yoo & Shon, 2016). IEC 61970
can be run on different operating systems having distinct programming languages and
database systems.
b) IEC 60870-6: This protocol defines the systems that are used in tele-control that is the
Supervisory Control and Data Acquisition with regard to the power applications of power
systems (Schlegel, R., Obermeier & Schneider, 2015). In IEC 60870-6 a standard profile for
the purpose of data transfer has been defined that allows monitoring and controlling the wide
area networks amidst the control centers.
c) IEC 62325: This protocol provides a standard protocol that serves as general guidelines in
the use of eXtensible Markup language technology and is a base for the architecture of the
communication in the energy markets. The main target of IEC 62325 is enabling integration
of the designed market-based software applications by distinct vendors that run
independently.
d) Multispeak: The National Rural Electric Cooperative Association developed Multispeak
and this addresses the domain responsible for electric distribution focusing on the market
based at U.S. It helps providing interoperability in the different application software that is
used by the electric utilities.
e) IEEE C37.118: It is a set standard for the synchrophasors used for the power systems that
define the requirements on the measurement of phasor’s data exchange. This protocol is
based on IP and Ethernet and has been developed for reporting the synchronized
measurement data of the phasor (Khan et al., 2016). It is a protocol that specifies the methods
to quantify the measurement of the phasor and the test procedures.

8SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
2. Substations Automation
a) IEC 61850: This protocol specifies the communication network and systems in the
substations. The aim of this is to present interoperability to the intelligent electronic
appliances and enables these to perform control, automation, protection and monitoring the
functions in the substations (Zapata et al., 2016). It is compatible with CIM for serving its
purpose and thus is able to differentiate from the various applications and prioritizes the flow
of the traffic.
b) IEEE C37.1: This specifies the application, definition and specification for the
supervisory control and the system automations for the substations. It defines the architecture
of the system and the related functions in a specific substation that includes implementation
issues, human machine interfaces and protocol selections.
c) IEEE 1379: It provides guidelines for implementation of IEDs and the remote terminal
units in electric substation. It deals in recommended practice required to add data elements
and the message structures. This helps in eliminating the time consuming and expensive
efforts that are been made to interface equipments to one another in the substations.
d) IEEE 1646: It defines the communication delivery time involved in the exchange of the
informations among the internal and the external equipments of the substation (Liu et al.,
2016). This protocol signifies the delay in the communication as per the time taken in the
networks between the runnings of the applications at both the ends of the system.
e) DNP3: DNP is the full form of Distributed Network Protocol and is defined as a
communication protocol that is open, mostly used in the SCADA systems in order to specify
the communication protocols existing among the various other components. It is used in the
substations for monitoring the equipments and gaining control on them.
f) Modbus: It is a communication protocol that is open serial that is used in the applications
such as substation automation, building automation and the system energy management.
2. Substations Automation
a) IEC 61850: This protocol specifies the communication network and systems in the
substations. The aim of this is to present interoperability to the intelligent electronic
appliances and enables these to perform control, automation, protection and monitoring the
functions in the substations (Zapata et al., 2016). It is compatible with CIM for serving its
purpose and thus is able to differentiate from the various applications and prioritizes the flow
of the traffic.
b) IEEE C37.1: This specifies the application, definition and specification for the
supervisory control and the system automations for the substations. It defines the architecture
of the system and the related functions in a specific substation that includes implementation
issues, human machine interfaces and protocol selections.
c) IEEE 1379: It provides guidelines for implementation of IEDs and the remote terminal
units in electric substation. It deals in recommended practice required to add data elements
and the message structures. This helps in eliminating the time consuming and expensive
efforts that are been made to interface equipments to one another in the substations.
d) IEEE 1646: It defines the communication delivery time involved in the exchange of the
informations among the internal and the external equipments of the substation (Liu et al.,
2016). This protocol signifies the delay in the communication as per the time taken in the
networks between the runnings of the applications at both the ends of the system.
e) DNP3: DNP is the full form of Distributed Network Protocol and is defined as a
communication protocol that is open, mostly used in the SCADA systems in order to specify
the communication protocols existing among the various other components. It is used in the
substations for monitoring the equipments and gaining control on them.
f) Modbus: It is a communication protocol that is open serial that is used in the applications
such as substation automation, building automation and the system energy management.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
Modbus SCADA serve as a master station to the RTUs. It defines a framework related to
messaging that is based on client-server communications (Good, Elli & Mancarella, 2017).
g) OPC Unified Architecture: It is a series of standard protocols for interface that provide
interoperability in the automation and the control applications and the enterprise applications.
It defines the infrastructure of the communication and the information model of the smart
grids. It also provides mapping to web services that are based on HTTP or SOAP.
3. Distributed Resources and Demand Response
a) IEC 61400: It defines the standards for the information exchange along with the design
requirements that are required to monitor and control the wind power plants. The protocol
specifies a series of the designs that are required to ensure the robustness in the designs of the
wind turbines.
b) IEEE 1547: This protocol specifies the standards for establishing interconnection between
the distributed resources along with the electric power systems. It addresses the vital issue of
interoperability of the energy resources and interconnections in between the physical and the
electrical parts (Silva, 2018).
c) OpenADR: It is a communication protocol that provides standards of information models
in the domain of demand response. It depends on the web services and the Web Service
Definition Language. The protocol was designed to enable a common information exchange
among the utilities and the independent operators of the system and the customers.
d) DRBiznet: This serves as a reliable platform that supports the DR applications. It has an
architecture that is service oriented and has a standardized version of the web services
interface. It enables the operators of the market and the utilities to manage the DR process
efficiently. The protocol manages the custom DR programs related to any market. The
customers are automatically notified and the aggregators and the grid operators are notified as
well.
Modbus SCADA serve as a master station to the RTUs. It defines a framework related to
messaging that is based on client-server communications (Good, Elli & Mancarella, 2017).
g) OPC Unified Architecture: It is a series of standard protocols for interface that provide
interoperability in the automation and the control applications and the enterprise applications.
It defines the infrastructure of the communication and the information model of the smart
grids. It also provides mapping to web services that are based on HTTP or SOAP.
3. Distributed Resources and Demand Response
a) IEC 61400: It defines the standards for the information exchange along with the design
requirements that are required to monitor and control the wind power plants. The protocol
specifies a series of the designs that are required to ensure the robustness in the designs of the
wind turbines.
b) IEEE 1547: This protocol specifies the standards for establishing interconnection between
the distributed resources along with the electric power systems. It addresses the vital issue of
interoperability of the energy resources and interconnections in between the physical and the
electrical parts (Silva, 2018).
c) OpenADR: It is a communication protocol that provides standards of information models
in the domain of demand response. It depends on the web services and the Web Service
Definition Language. The protocol was designed to enable a common information exchange
among the utilities and the independent operators of the system and the customers.
d) DRBiznet: This serves as a reliable platform that supports the DR applications. It has an
architecture that is service oriented and has a standardized version of the web services
interface. It enables the operators of the market and the utilities to manage the DR process
efficiently. The protocol manages the custom DR programs related to any market. The
customers are automatically notified and the aggregators and the grid operators are notified as
well.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
4. Metering
a) ANSI C12: ANSI C12 suite provides guidelines for the metering applications. It gives
certain requirements for the specification of the protocols for the optical ports and electric
meter accuracy classes.
b) M-bus: M-Bus also named as Meter Bus. The protocol is in wide use for the remote utility
reading of the meters for example electricity and gas. It design focuses on low lost and
battery powered devices (Kuzlu, Pipattanasompom & Rahman, 2017). It is used for creating
energy managing applications for example alarm systems and the control lighting system.
5. Electric vehicles
a) SAE J2293: It provides the needs for the EV and the off-board electric vehicle supply
equipment (EVSE). It also covers the basic requirements and the system architectures, along
with the requirements regarding communication and various network architectures for the
transferring of electrical energy to the EV from the electrical utility in North America.
b) SAE J2836: It specifies the cases that can be used for communications between the plug-
in electric vehicles (PEV) and the electric power grid in between the PEV and the off-board
DC chargers as well as the customers and the PEV. It uses the cases for the diagnostic
communication and the wireless communication charging. The protocol also defines the use
cases for that PEV communicating as the distributed sources of energy.
6. Cyber Security
a) IEC 6235-1: IEC 62351 defines the requirements of the security for the management of
the power systems along with the linked information exchange. It introduces the meter
4. Metering
a) ANSI C12: ANSI C12 suite provides guidelines for the metering applications. It gives
certain requirements for the specification of the protocols for the optical ports and electric
meter accuracy classes.
b) M-bus: M-Bus also named as Meter Bus. The protocol is in wide use for the remote utility
reading of the meters for example electricity and gas. It design focuses on low lost and
battery powered devices (Kuzlu, Pipattanasompom & Rahman, 2017). It is used for creating
energy managing applications for example alarm systems and the control lighting system.
5. Electric vehicles
a) SAE J2293: It provides the needs for the EV and the off-board electric vehicle supply
equipment (EVSE). It also covers the basic requirements and the system architectures, along
with the requirements regarding communication and various network architectures for the
transferring of electrical energy to the EV from the electrical utility in North America.
b) SAE J2836: It specifies the cases that can be used for communications between the plug-
in electric vehicles (PEV) and the electric power grid in between the PEV and the off-board
DC chargers as well as the customers and the PEV. It uses the cases for the diagnostic
communication and the wireless communication charging. The protocol also defines the use
cases for that PEV communicating as the distributed sources of energy.
6. Cyber Security
a) IEC 6235-1: IEC 62351 defines the requirements of the security for the management of
the power systems along with the linked information exchange. It introduces the meter

11SMART GRIDS AND THE ASSOCITAED SECURITY PROTOCOLS
reading agent to the wide aspects of the communication network and the system security that
is linked to the operations of the power system. IEC 62351-3 defines messages and
algorithms for manufacturing message specification that are based on applications.
b) NERC CIP: The protocol consists of certain requirements that are to provide security to
the assets needed for operating the bulk electric power systems. It covers a range of subjects
that include personal and training in cyber security, electronic security perimeters and
recovery plans for the critical cyber assets.
c) NISTIR 7628: It provides guidelines for the smart grid related to cyber security that
consists of three volumes and the volumes include smart grid cyber security strategy, privacy
and the smart grid and references (Clausen et al., 2018). NISTIR 7628 provides a compact
framework that helps in guiding the rate of development of cyber security strategies that are
effective.
d) AMI System Security Requirements: AMISEC provides a certain set of security
essentials for AMI that is beneficial for the utility industry as well as the vendors. These are
aimed for being used during the procurement process related to the AMI and the smart
meters.
Comparison between the protocols and assessing the best for Smart Grids
The Smart Grid applies to utilities that are dedicated to provide services for the
betterment of the public good that includes taking care of the society’s electricity
requirements by maintaining building and operating added electric infrastructure. The costs
associated with the implementation of smart grids can be a hindrance in the way added to the
other challenges. A smarter grid depends on the protocols it is based on and this need to
reduce the cost of the utilities’ capital and the expenditure on the operations. The protocols
can be compared on the basis of the intelligence, efficiency, accommodating power and the
opportunities the smart gird system acquires. On the basis of the protocols discussed and the
reading agent to the wide aspects of the communication network and the system security that
is linked to the operations of the power system. IEC 62351-3 defines messages and
algorithms for manufacturing message specification that are based on applications.
b) NERC CIP: The protocol consists of certain requirements that are to provide security to
the assets needed for operating the bulk electric power systems. It covers a range of subjects
that include personal and training in cyber security, electronic security perimeters and
recovery plans for the critical cyber assets.
c) NISTIR 7628: It provides guidelines for the smart grid related to cyber security that
consists of three volumes and the volumes include smart grid cyber security strategy, privacy
and the smart grid and references (Clausen et al., 2018). NISTIR 7628 provides a compact
framework that helps in guiding the rate of development of cyber security strategies that are
effective.
d) AMI System Security Requirements: AMISEC provides a certain set of security
essentials for AMI that is beneficial for the utility industry as well as the vendors. These are
aimed for being used during the procurement process related to the AMI and the smart
meters.
Comparison between the protocols and assessing the best for Smart Grids
The Smart Grid applies to utilities that are dedicated to provide services for the
betterment of the public good that includes taking care of the society’s electricity
requirements by maintaining building and operating added electric infrastructure. The costs
associated with the implementation of smart grids can be a hindrance in the way added to the
other challenges. A smarter grid depends on the protocols it is based on and this need to
reduce the cost of the utilities’ capital and the expenditure on the operations. The protocols
can be compared on the basis of the intelligence, efficiency, accommodating power and the
opportunities the smart gird system acquires. On the basis of the protocols discussed and the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




