NEF6002 Research Project B: Smart Home Automation via Biometrics
VerifiedAdded on 2022/09/08
|10
|2303
|26
Report
AI Summary
This research paper, submitted as part of the NEF6002 Research Project B, investigates the application of biometric authentication in smart home environments. The report begins with an introduction to biometrics, defining key terminology and highlighting the increasing use of biometric technologies. It outlines the research project's background, objectives, and research problems, focusing on security concerns related to biometric authentication such as fingerprint and facial recognition vulnerabilities. The literature review explores various biometric methods like face recognition, iris recognition, and hand geometry, and their role in smart home automation, discussing the advantages and disadvantages of each. The research methodology adopts a mixed design, combining qualitative and quantitative methods, including the use of questionnaires and data processing techniques. The report also discusses the significance of the research, which aims to develop and implement a biometric system for smart home automation and evaluate security concerns. The conclusion summarizes the findings, emphasizing the importance of privacy and the potential of biometric systems to enhance security in smart homes.

RESEARCH PAPER 0
Smart home automation using
Biometrics
Smart home automation using
Biometrics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH PAPER 1
Table of Contents
Introduction.................................................................................................................................................2
Research project background.......................................................................................................................2
Objectives of research.............................................................................................................................2
Literature review.....................................................................................................................................2
Introduction.........................................................................................................................................2
Biometric authentication......................................................................................................................3
Types of biometrics.............................................................................................................................3
Biometric in smart home automation...................................................................................................3
Research problems......................................................................................................................................4
Research methodology, modeling, and implementation..............................................................................5
Research design.......................................................................................................................................5
Data sets and data processing approach...................................................................................................5
Research significance..................................................................................................................................6
Conclusion...................................................................................................................................................6
Research planning.......................................................................................................................................6
References...................................................................................................................................................8
Table of Contents
Introduction.................................................................................................................................................2
Research project background.......................................................................................................................2
Objectives of research.............................................................................................................................2
Literature review.....................................................................................................................................2
Introduction.........................................................................................................................................2
Biometric authentication......................................................................................................................3
Types of biometrics.............................................................................................................................3
Biometric in smart home automation...................................................................................................3
Research problems......................................................................................................................................4
Research methodology, modeling, and implementation..............................................................................5
Research design.......................................................................................................................................5
Data sets and data processing approach...................................................................................................5
Research significance..................................................................................................................................6
Conclusion...................................................................................................................................................6
Research planning.......................................................................................................................................6
References...................................................................................................................................................8

RESEARCH PAPER 2
Introduction
Biometric is defined as a process for identifying and authenticating consumers in a reliable
manner by the utilization of unique biological characteristics. It has the capability to collect and
evaluate reliable information from consumers. Biometric is an advanced technology that can be
used in smart home automation due to its capability to enhance the performance of the systems
(Awasthi, and Srivastava, 2013). The major terminology behind biometrics is that it takes data
from the consumers and identifies the authenticity of the consumers effectively. The area of
biometric is important for the research as the uses of biometric technologies are increasing
quickly for which it is necessary to understand the working and key aspects of biometric and
evaluate their role in home automation. It is observed that biometric is mainly used in the
business communities for handling security issues and the authenticity of the employees. The
smart home automation using biometric is a current trend that has the potential to control and
access home appliances through biometric networks.
Research project background
Objectives of research
This report aims to analyze the applicability of biometric system of authentication for the
purpose of rendering security to the residential complex and dwellings to combat the
unauthorized access of the intruders, trespassing in the properties of others. To conduct the above
analysis, the researcher will adopt a thematic analysis of the findings from the literature review,
with specific goal of developing a framework for applying biometric systems in residential
complex and dwellings.
Literature review
Introduction
Biometric is a key topic for the investigation and there are numerous papers were published in
the last five years which will be discussed in this section. The significance of this literature is to
review the findings of previous studies and evaluate the importance of biometrics in smart home
automation. It is argued that biometric is an effective technology that has the capability to control
Introduction
Biometric is defined as a process for identifying and authenticating consumers in a reliable
manner by the utilization of unique biological characteristics. It has the capability to collect and
evaluate reliable information from consumers. Biometric is an advanced technology that can be
used in smart home automation due to its capability to enhance the performance of the systems
(Awasthi, and Srivastava, 2013). The major terminology behind biometrics is that it takes data
from the consumers and identifies the authenticity of the consumers effectively. The area of
biometric is important for the research as the uses of biometric technologies are increasing
quickly for which it is necessary to understand the working and key aspects of biometric and
evaluate their role in home automation. It is observed that biometric is mainly used in the
business communities for handling security issues and the authenticity of the employees. The
smart home automation using biometric is a current trend that has the potential to control and
access home appliances through biometric networks.
Research project background
Objectives of research
This report aims to analyze the applicability of biometric system of authentication for the
purpose of rendering security to the residential complex and dwellings to combat the
unauthorized access of the intruders, trespassing in the properties of others. To conduct the above
analysis, the researcher will adopt a thematic analysis of the findings from the literature review,
with specific goal of developing a framework for applying biometric systems in residential
complex and dwellings.
Literature review
Introduction
Biometric is a key topic for the investigation and there are numerous papers were published in
the last five years which will be discussed in this section. The significance of this literature is to
review the findings of previous studies and evaluate the importance of biometrics in smart home
automation. It is argued that biometric is an effective technology that has the capability to control
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RESEARCH PAPER 3
and address unauthorized access from the systems and lead security of data in a reliable manner
(Awasthi, and Srivastava, 2013). This section provides a way to understand the opinions of other
experts and enhance knowledge in the area of smart home automation and biometric.
It is observed that biometric is an attractive topic for the investigation as many companies are
using biometric systems for protecting data against hackers due to which many investigators
highlighted biometric advantages and disadvantages along with the security concerns. Therefore,
the biometric is an attractive topic for the investigation and this paper will help the readers to
understand the concept of biometric authentication.
Biometric authentication
Bhatt and Santhanam, (2013) examined that biometric authentication is a process of verifying the
identity of individuals with other unique characteristics of the human body system. It is a kind of
secure network that measures and matches biometric features of a consumer to verify that a
consumer trying to access a specific device is authorized to do so. Therefore, using biometric
authentication companies can enhance the privacy of data and lead the performance of the
system effectively.
Types of biometrics
Chantal, Lee, and Kim, (2017) reported that there are numerous kinds of biometric systems
involved in home automation, for example, face recognition, hand geometry, iris recognition and
so on. In which iris recognition is an advanced technology used in the companies to protect data
from the third parties and hackers effectively. The major advantage of biometric technology is
that it is capable to address unauthorized access from the systems and lead effectiveness of
developed systems in a reliable manner.
From a recent investigation conducted by Chen, Pande, and Mohapatra, (2014) it is examined
that face recognition scan facial expression of the consumers and match with the stored database.
Hand geometry is a technique that helps the consumers to scan the hand of victims and enhance
the privacy of data in a reliable manner. It is reported that iris recognition can be used for various
security applications including identity cards, passports, prison security, and database access.
and address unauthorized access from the systems and lead security of data in a reliable manner
(Awasthi, and Srivastava, 2013). This section provides a way to understand the opinions of other
experts and enhance knowledge in the area of smart home automation and biometric.
It is observed that biometric is an attractive topic for the investigation as many companies are
using biometric systems for protecting data against hackers due to which many investigators
highlighted biometric advantages and disadvantages along with the security concerns. Therefore,
the biometric is an attractive topic for the investigation and this paper will help the readers to
understand the concept of biometric authentication.
Biometric authentication
Bhatt and Santhanam, (2013) examined that biometric authentication is a process of verifying the
identity of individuals with other unique characteristics of the human body system. It is a kind of
secure network that measures and matches biometric features of a consumer to verify that a
consumer trying to access a specific device is authorized to do so. Therefore, using biometric
authentication companies can enhance the privacy of data and lead the performance of the
system effectively.
Types of biometrics
Chantal, Lee, and Kim, (2017) reported that there are numerous kinds of biometric systems
involved in home automation, for example, face recognition, hand geometry, iris recognition and
so on. In which iris recognition is an advanced technology used in the companies to protect data
from the third parties and hackers effectively. The major advantage of biometric technology is
that it is capable to address unauthorized access from the systems and lead effectiveness of
developed systems in a reliable manner.
From a recent investigation conducted by Chen, Pande, and Mohapatra, (2014) it is examined
that face recognition scan facial expression of the consumers and match with the stored database.
Hand geometry is a technique that helps the consumers to scan the hand of victims and enhance
the privacy of data in a reliable manner. It is reported that iris recognition can be used for various
security applications including identity cards, passports, prison security, and database access.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH PAPER 4
Biometric in smart home automation
El-Basioni, El-Kader, and Abdelmonim, (2013) proposed research and determined that in smart
home automation biometric system plays a major character that helps consumers to enhance the
performance of security systems in an effective manner. It is true that using the biometric system
the complexity of home automation can be reduced and users can protect their data from
criminals. Most of the consumers use the facial recognition system at the front door which helps
to manage unauthorized activities and signals from the home. The smart home automation can be
managed using biometric systems including fingerprint, iris recognition and other systems.
Lu, Li, Peng, and Yang, (2015) examined that the key advantage of biometric in home
automation is that it is capable to connect numerous home appliances with biometric networks
and reduce privacy risks that affect private details of the users. In which there are numerous
hardware and software tools involve, for example, computing devices, databases for storing
identity, wireless networks, sensors and many more. All these networks and servers are
interconnected in a way where consumers can perform smart home automation and link with the
biometric system. The future research will develop and implement an effective biometric system
for designing smart home automation and will explore security risks associated with the
biometric authentication.
Research problems
There are numerous research problems identified which are described below:
Security is a major issue related to the biometric authentication that directly impacts on
the private data of the consumers. It is observed that fingerprint and facial recognition of
consumers are unique properties but cyber predators are able to gain such properties
effectively that access the personal information easily (Martin, and Donovan, 2015).
The vulnerability of the voice recognition system lies in the fact that the voice can be
imitated through the recording activities and can be used for the purpose of forgery
thereby gaining unauthorized access over the restricted property of the individuals.
The fingerprint of an individual can be easily replicated through the prototyping
techniques as fingerprint gets recorded in certain devices when it comes to physical
contact with the fingerprint of the individuals (Tome, et al., 2015). The software
Biometric in smart home automation
El-Basioni, El-Kader, and Abdelmonim, (2013) proposed research and determined that in smart
home automation biometric system plays a major character that helps consumers to enhance the
performance of security systems in an effective manner. It is true that using the biometric system
the complexity of home automation can be reduced and users can protect their data from
criminals. Most of the consumers use the facial recognition system at the front door which helps
to manage unauthorized activities and signals from the home. The smart home automation can be
managed using biometric systems including fingerprint, iris recognition and other systems.
Lu, Li, Peng, and Yang, (2015) examined that the key advantage of biometric in home
automation is that it is capable to connect numerous home appliances with biometric networks
and reduce privacy risks that affect private details of the users. In which there are numerous
hardware and software tools involve, for example, computing devices, databases for storing
identity, wireless networks, sensors and many more. All these networks and servers are
interconnected in a way where consumers can perform smart home automation and link with the
biometric system. The future research will develop and implement an effective biometric system
for designing smart home automation and will explore security risks associated with the
biometric authentication.
Research problems
There are numerous research problems identified which are described below:
Security is a major issue related to the biometric authentication that directly impacts on
the private data of the consumers. It is observed that fingerprint and facial recognition of
consumers are unique properties but cyber predators are able to gain such properties
effectively that access the personal information easily (Martin, and Donovan, 2015).
The vulnerability of the voice recognition system lies in the fact that the voice can be
imitated through the recording activities and can be used for the purpose of forgery
thereby gaining unauthorized access over the restricted property of the individuals.
The fingerprint of an individual can be easily replicated through the prototyping
techniques as fingerprint gets recorded in certain devices when it comes to physical
contact with the fingerprint of the individuals (Tome, et al., 2015). The software

RESEARCH PAPER 5
deployed for the purpose of imitating the fingerprint of the individuals is the VeriFinger
software.
From the conducted literature it is reported that this research will resolve all these problems and
provide depth examination about security concerns along with with with the mitigation
techniques for handling such issues (Sayed, et al., 2013).
Research methodology, modeling, and implementation
The research problem for this investigation is security risks associated with the biometric
authentication and home automation. There are numerous methodologies will be used for these
investigations which are described below:
Research design
This investigation will adopt a mixed design that contains qualitative and quantitative methods. It
is argued that qualitative research will help to deliver theoretical information related to the
biometric system while quantitative research will deliver numerical facts and data to the
researcher (Soni, Somani, and Shete, 2016). This approach will help to obtain reliable
information and resolve the research problems in an effective way. There are numerous variables
in this research, for example, biometric, the identity of the consumers, home appliances and so
on. In which a usability evaluation model will be used for managing the authenticity of the
consumers and evaluating security concerns linked with biometric systems.
Data sets and data processing approach
It is reported that a close-ended questionnaire will be included for finding the opinions of others
in the relation of the biometric system. For collecting secondary data various resources will be
adopted such as literature review, journal articles, and online books. All these sources will help
to obtain effective data related to biometric authentication. For processing collected data
descriptive statistics and inductive approaches will be used due to their capability to deliver
effective points related to research concerns (Trojahn, and Ortmeier, 2012). The simulation
process will cover numerous phases such as initialization of authenticity, interfacing process
through microcontrollers, programming software like Arduino IDE and Keil software,
developing an approach, configuration process, and final evaluation process. These steps are able
to simulate and perform biometric authenticity in home automation.
deployed for the purpose of imitating the fingerprint of the individuals is the VeriFinger
software.
From the conducted literature it is reported that this research will resolve all these problems and
provide depth examination about security concerns along with with with the mitigation
techniques for handling such issues (Sayed, et al., 2013).
Research methodology, modeling, and implementation
The research problem for this investigation is security risks associated with the biometric
authentication and home automation. There are numerous methodologies will be used for these
investigations which are described below:
Research design
This investigation will adopt a mixed design that contains qualitative and quantitative methods. It
is argued that qualitative research will help to deliver theoretical information related to the
biometric system while quantitative research will deliver numerical facts and data to the
researcher (Soni, Somani, and Shete, 2016). This approach will help to obtain reliable
information and resolve the research problems in an effective way. There are numerous variables
in this research, for example, biometric, the identity of the consumers, home appliances and so
on. In which a usability evaluation model will be used for managing the authenticity of the
consumers and evaluating security concerns linked with biometric systems.
Data sets and data processing approach
It is reported that a close-ended questionnaire will be included for finding the opinions of others
in the relation of the biometric system. For collecting secondary data various resources will be
adopted such as literature review, journal articles, and online books. All these sources will help
to obtain effective data related to biometric authentication. For processing collected data
descriptive statistics and inductive approaches will be used due to their capability to deliver
effective points related to research concerns (Trojahn, and Ortmeier, 2012). The simulation
process will cover numerous phases such as initialization of authenticity, interfacing process
through microcontrollers, programming software like Arduino IDE and Keil software,
developing an approach, configuration process, and final evaluation process. These steps are able
to simulate and perform biometric authenticity in home automation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
RESEARCH PAPER 6
Research significance
The major significance of this research is to develop and implement a biometric system for smart
home automation and review the security concerns related to biometric that impact on society,
business and enterprise systems. This research is different from others as it provides depth
examination about the biometric system and proposed an evaluation process for security issues
by which readers can understand privacy issues and enhance the security of biometrics by
evaluating proposed mitigation techniques.
Conclusion
From the above findings, it can be concluded that security is a major issue associated with the
biometric system that impacts on the networks and private data. This research reviewed the
significance of biometrics in smart home automation and the proposed literature review for
evaluating the findings of recent papers. The adopted methodologies helped to solve research
problems and enhanced the quality of research in a reliable manner. Therefore, it is stated that
companies should focus on privacy while implementing biometric authentication and in smart
home automation biometric systems can be used for managing authenticity.
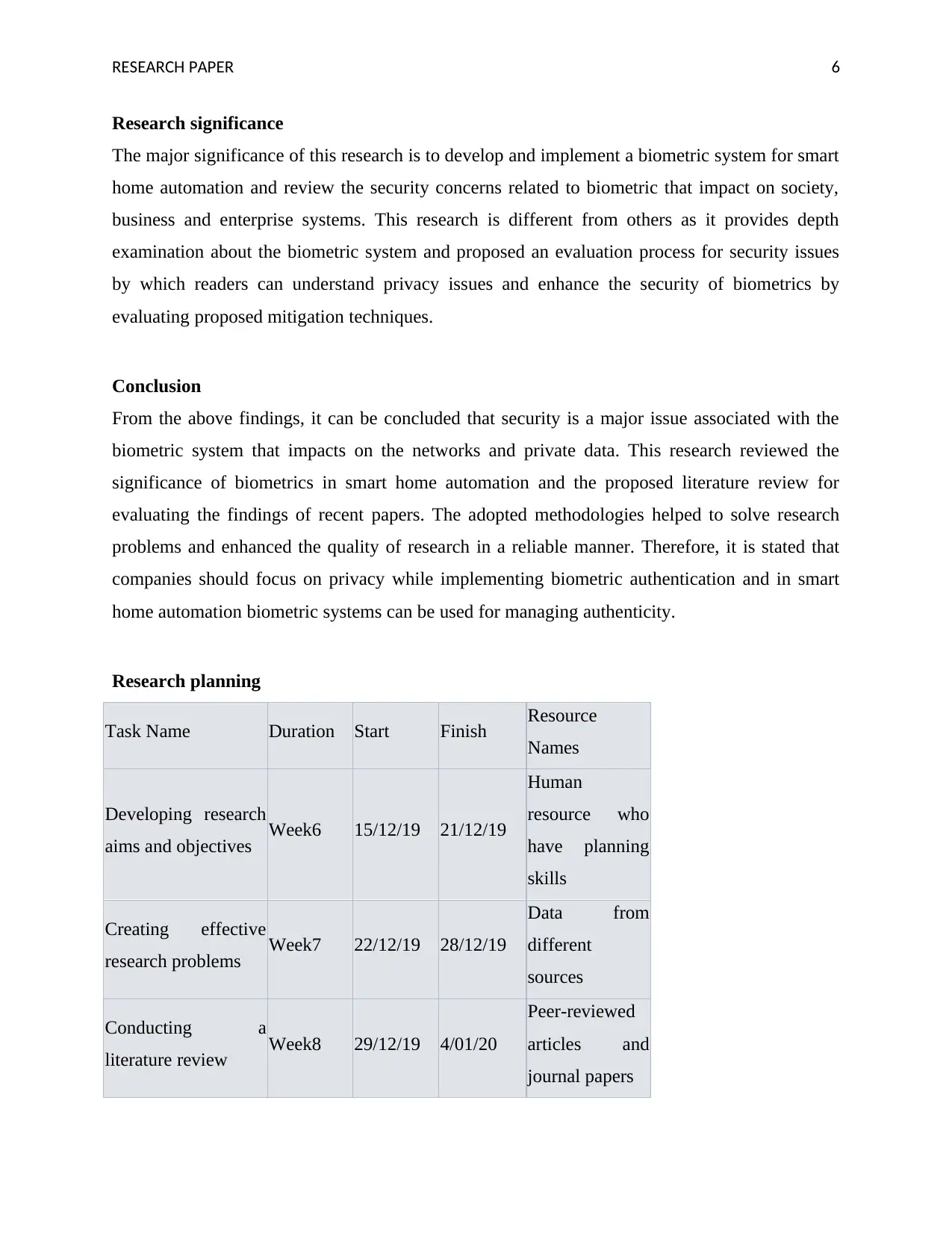
Research planning
Task Name Duration Start Finish Resource
Names
Developing research
aims and objectives Week6 15/12/19 21/12/19
Human
resource who
have planning
skills
Creating effective
research problems Week7 22/12/19 28/12/19
Data from
different
sources
Conducting a
literature review Week8 29/12/19 4/01/20
Peer-reviewed
articles and
journal papers
Research significance
The major significance of this research is to develop and implement a biometric system for smart
home automation and review the security concerns related to biometric that impact on society,
business and enterprise systems. This research is different from others as it provides depth
examination about the biometric system and proposed an evaluation process for security issues
by which readers can understand privacy issues and enhance the security of biometrics by
evaluating proposed mitigation techniques.
Conclusion
From the above findings, it can be concluded that security is a major issue associated with the
biometric system that impacts on the networks and private data. This research reviewed the
significance of biometrics in smart home automation and the proposed literature review for
evaluating the findings of recent papers. The adopted methodologies helped to solve research
problems and enhanced the quality of research in a reliable manner. Therefore, it is stated that
companies should focus on privacy while implementing biometric authentication and in smart
home automation biometric systems can be used for managing authenticity.
Research planning
Task Name Duration Start Finish Resource
Names
Developing research
aims and objectives Week6 15/12/19 21/12/19
Human
resource who
have planning
skills
Creating effective
research problems Week7 22/12/19 28/12/19
Data from
different
sources
Conducting a
literature review Week8 29/12/19 4/01/20
Peer-reviewed
articles and
journal papers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
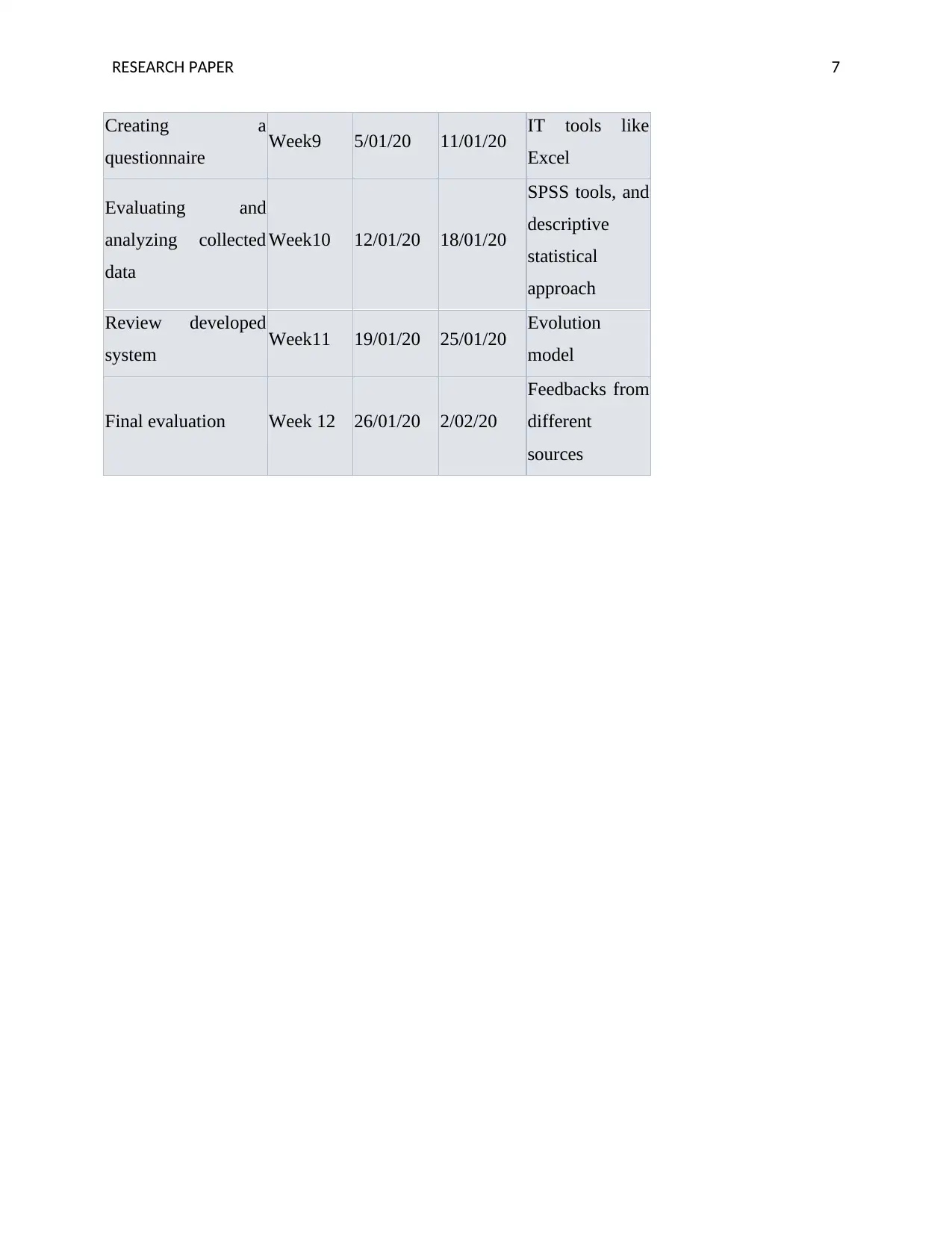
RESEARCH PAPER 7
Creating a
questionnaire Week9 5/01/20 11/01/20 IT tools like
Excel
Evaluating and
analyzing collected
data
Week10 12/01/20 18/01/20
SPSS tools, and
descriptive
statistical
approach
Review developed
system Week11 19/01/20 25/01/20 Evolution
model
Final evaluation Week 12 26/01/20 2/02/20
Feedbacks from
different
sources
Creating a
questionnaire Week9 5/01/20 11/01/20 IT tools like
Excel
Evaluating and
analyzing collected
data
Week10 12/01/20 18/01/20
SPSS tools, and
descriptive
statistical
approach
Review developed
system Week11 19/01/20 25/01/20 Evolution
model
Final evaluation Week 12 26/01/20 2/02/20
Feedbacks from
different
sources

RESEARCH PAPER 8
References
Awasthi, A.K. and Srivastava, K., (2013) A biometric authentication scheme for telecare
medicine information systems with a nonce. Journal of medical systems, 37(5), p.9964.
Bhatt, S. and Santhanam, T., (2013) Keystroke dynamics for biometric authentication—A
survey. In 2013 International Conference on Pattern Recognition, Informatics and Mobile
Engineering, 12(5), pp. 17-23.
Chantal, M., Lee, S.W. and Kim, K.H., (2017) A security analysis and reinforcement design
adopting fingerprints over drawbacks of passwords based authentication in the remote home
automation control system. In Proceedings of the 6th International Conference on Informatics,
Environment, Energy, and Applications, 12(6), pp. 71-75.
Chen, S., Pande, A. and Mohapatra, P., (2014) Sensor-assisted facial recognition: an enhanced
biometric authentication system for smartphones. In Proceedings of the 12th annual
international conference on Mobile systems, applications, and services, 12(6), pp. 109-122.
El-Basioni, B.M.M., El-Kader, S.M.A. and Abdelmonim, M., (2013) Smart home design using
wireless sensor network and biometric technologies. information technology, 1(2), p.2.
Lu, Y., Li, L., Peng, H. and Yang, Y., (2015) An enhanced biometric-based authentication
scheme for telecare medicine information systems using elliptic curve cryptosystem. Journal of
medical systems, 39(3), p.32.
Martin, A.K. and Donovan, K.P., (2015) New surveillance technologies and their publics: A case
of biometrics. Public Understanding of Science, 24(7), pp.842-857.
Sayed, B., Traore, I., Woungang, I. and Obaidat, M.S., (2013) Biometric authentication using
mouse gesture dynamics. IEEE Systems Journal, 7(2), pp.262-274.
Soni, Y.S., Somani, S.B. and Shete, V.V., (2016) Biometric user authentication using brain
waves. In 2016 International Conference on Inventive Computation Technologies (ICICT), 2(1),
pp. 1-6.
References
Awasthi, A.K. and Srivastava, K., (2013) A biometric authentication scheme for telecare
medicine information systems with a nonce. Journal of medical systems, 37(5), p.9964.
Bhatt, S. and Santhanam, T., (2013) Keystroke dynamics for biometric authentication—A
survey. In 2013 International Conference on Pattern Recognition, Informatics and Mobile
Engineering, 12(5), pp. 17-23.
Chantal, M., Lee, S.W. and Kim, K.H., (2017) A security analysis and reinforcement design
adopting fingerprints over drawbacks of passwords based authentication in the remote home
automation control system. In Proceedings of the 6th International Conference on Informatics,
Environment, Energy, and Applications, 12(6), pp. 71-75.
Chen, S., Pande, A. and Mohapatra, P., (2014) Sensor-assisted facial recognition: an enhanced
biometric authentication system for smartphones. In Proceedings of the 12th annual
international conference on Mobile systems, applications, and services, 12(6), pp. 109-122.
El-Basioni, B.M.M., El-Kader, S.M.A. and Abdelmonim, M., (2013) Smart home design using
wireless sensor network and biometric technologies. information technology, 1(2), p.2.
Lu, Y., Li, L., Peng, H. and Yang, Y., (2015) An enhanced biometric-based authentication
scheme for telecare medicine information systems using elliptic curve cryptosystem. Journal of
medical systems, 39(3), p.32.
Martin, A.K. and Donovan, K.P., (2015) New surveillance technologies and their publics: A case
of biometrics. Public Understanding of Science, 24(7), pp.842-857.
Sayed, B., Traore, I., Woungang, I. and Obaidat, M.S., (2013) Biometric authentication using
mouse gesture dynamics. IEEE Systems Journal, 7(2), pp.262-274.
Soni, Y.S., Somani, S.B. and Shete, V.V., (2016) Biometric user authentication using brain
waves. In 2016 International Conference on Inventive Computation Technologies (ICICT), 2(1),
pp. 1-6.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RESEARCH PAPER 9
Tome, P., Vera-Rodriguez, R., Fierrez, J. and Ortega-Garcia, J., (2015) Facial soft biometric
features for forensic face recognition. Forensic science international, 257(5), pp.271-284.
Trojahn, M., and Ortmeier, F., (2012) Biometric authentication through a virtual keyboard for
smartphones. International Journal of Computer Science & Information Technology, 4(5), p.1.
Tome, P., Vera-Rodriguez, R., Fierrez, J. and Ortega-Garcia, J., (2015) Facial soft biometric
features for forensic face recognition. Forensic science international, 257(5), pp.271-284.
Trojahn, M., and Ortmeier, F., (2012) Biometric authentication through a virtual keyboard for
smartphones. International Journal of Computer Science & Information Technology, 4(5), p.1.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





