IT Infrastructure for SmartDefence: A Network Design Project
VerifiedAdded on 2023/05/29
|12
|2261
|457
Project
AI Summary
This document presents an IT infrastructure project for SmartDefence, a software development company with offices in Toronto, Waterloo, and Brampton. The project details the LAN setup for each location using a tree topology for scalability and security. It includes an IP address solution utilizing DHCP for dynamic assignment and static IPs for servers and printers. Security measures for LAN servers are outlined, including network mapping, auditing, physical security, and VLAN implementation. The project also addresses remote secure connections using VPNs and data loss prevention strategies. A DMZ server setup is described to protect the internal network, and fiber optic cable is recommended for inter-office connectivity. The solution concludes by advocating for VPNs to ensure secure remote access. Desklib provides access to this and other solved assignments for students.

IT INFRASTRUCTURE 1
IT infrastructure
Student Name
Institutional Affiliation
IT infrastructure
Student Name
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT INFRASTRUCTURE 2
Table of Contents
Introduction.................................................................................................................................................3
LAN Solution..............................................................................................................................................3
Toronto LAN...........................................................................................................................................3
Waterloo LAN.........................................................................................................................................4
Brampton LAN........................................................................................................................................5
IP Address Solution.....................................................................................................................................6
Securing LAN Servers.................................................................................................................................7
Remote Secure Connection.........................................................................................................................7
DMZ Servers...............................................................................................................................................8
Transmission Medium.................................................................................................................................9
Remote connectivity solution using VPN....................................................................................................9
Conclusion...................................................................................................................................................9
Reference List...........................................................................................................................................10
Table of Contents
Introduction.................................................................................................................................................3
LAN Solution..............................................................................................................................................3
Toronto LAN...........................................................................................................................................3
Waterloo LAN.........................................................................................................................................4
Brampton LAN........................................................................................................................................5
IP Address Solution.....................................................................................................................................6
Securing LAN Servers.................................................................................................................................7
Remote Secure Connection.........................................................................................................................7
DMZ Servers...............................................................................................................................................8
Transmission Medium.................................................................................................................................9
Remote connectivity solution using VPN....................................................................................................9
Conclusion...................................................................................................................................................9
Reference List...........................................................................................................................................10
IT INFRASTRUCTURE 3
Introduction
SmartDefence is a company that is located in three cities, Toronto, Waterloo, and Brampton. The
company deals with development of software solution for different clients. The company wants
to upgrade it network to meet the new requirements. The company has three offices in three
building located in Toronto, two office in Waterloo, two offices in Brampton. The head office is
located in Toronto.
LAN Solution
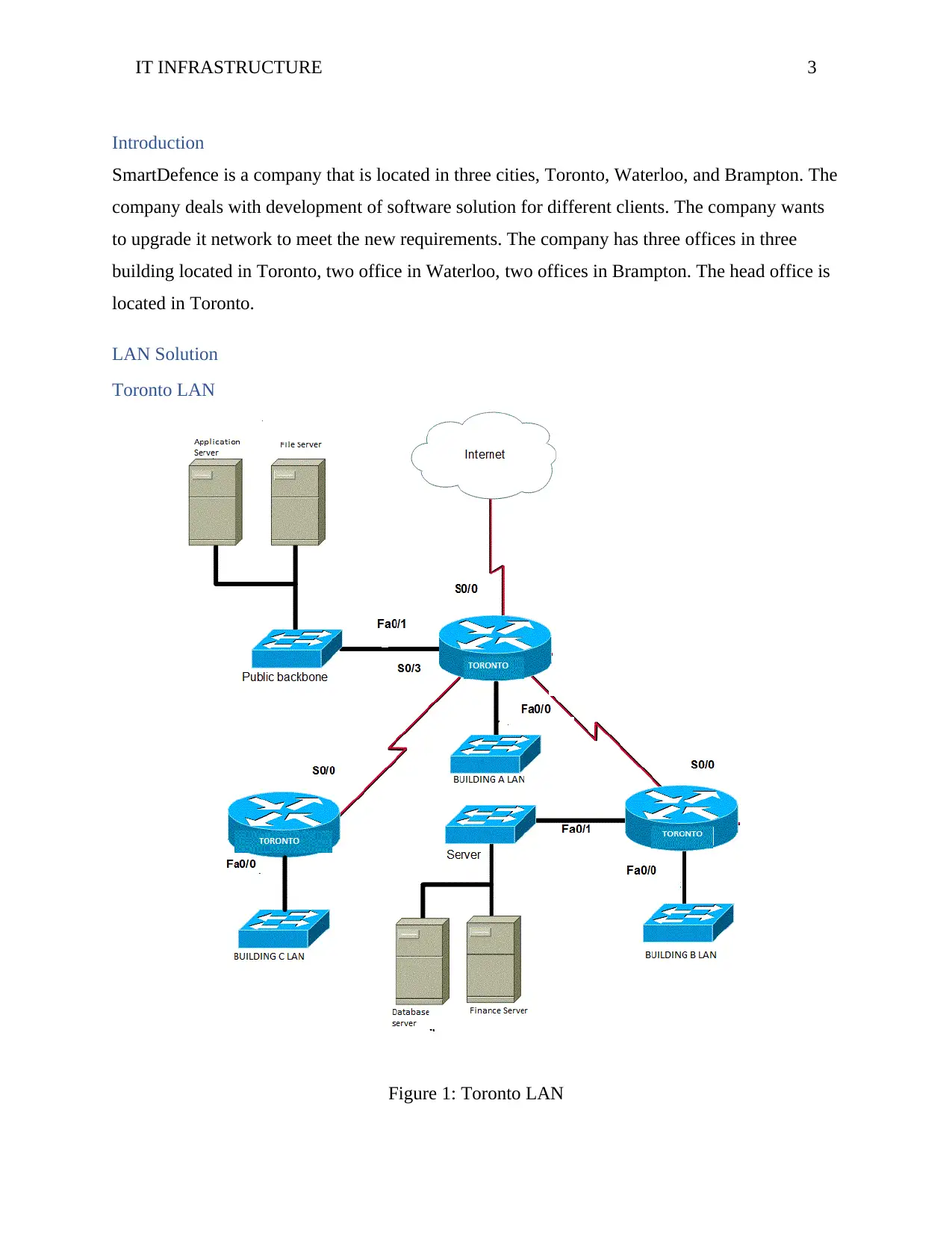
Toronto LAN
Figure 1: Toronto LAN
Introduction
SmartDefence is a company that is located in three cities, Toronto, Waterloo, and Brampton. The
company deals with development of software solution for different clients. The company wants
to upgrade it network to meet the new requirements. The company has three offices in three
building located in Toronto, two office in Waterloo, two offices in Brampton. The head office is
located in Toronto.
LAN Solution
Toronto LAN
Figure 1: Toronto LAN
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT INFRASTRUCTURE 4
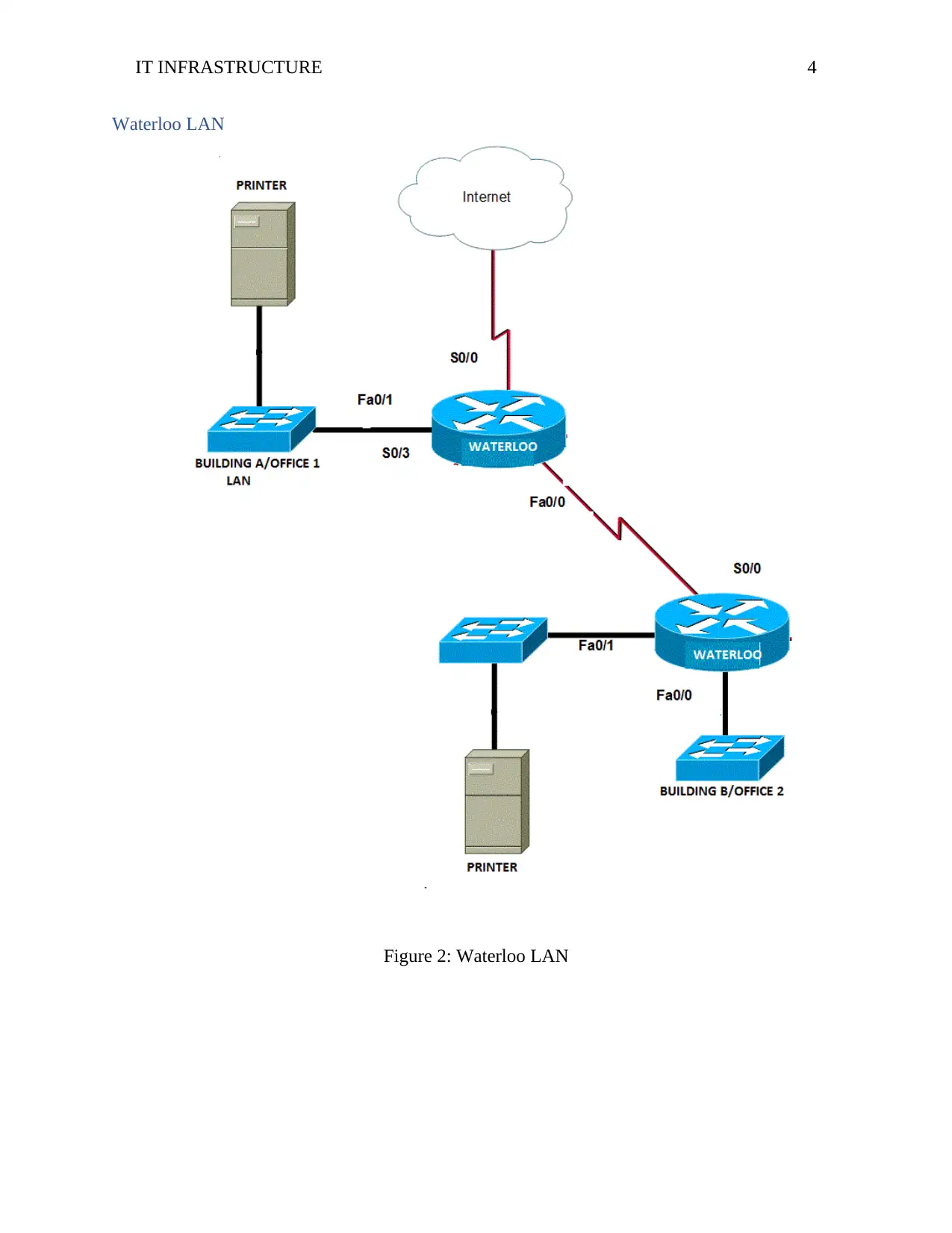
Waterloo LAN
Figure 2: Waterloo LAN
Waterloo LAN
Figure 2: Waterloo LAN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT INFRASTRUCTURE 5
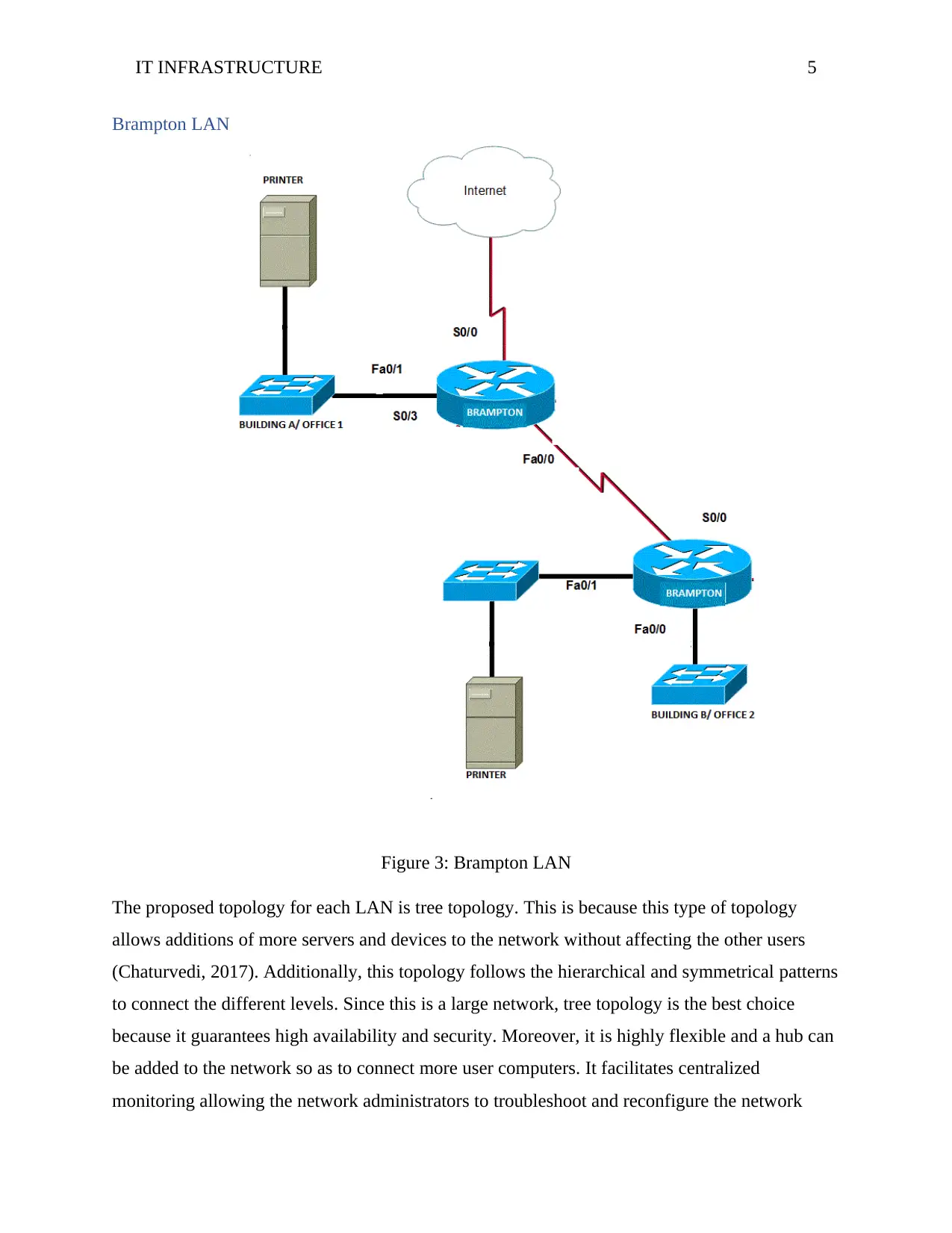
Brampton LAN
Figure 3: Brampton LAN
The proposed topology for each LAN is tree topology. This is because this type of topology
allows additions of more servers and devices to the network without affecting the other users
(Chaturvedi, 2017). Additionally, this topology follows the hierarchical and symmetrical patterns
to connect the different levels. Since this is a large network, tree topology is the best choice
because it guarantees high availability and security. Moreover, it is highly flexible and a hub can
be added to the network so as to connect more user computers. It facilitates centralized
monitoring allowing the network administrators to troubleshoot and reconfigure the network
Brampton LAN
Figure 3: Brampton LAN
The proposed topology for each LAN is tree topology. This is because this type of topology
allows additions of more servers and devices to the network without affecting the other users
(Chaturvedi, 2017). Additionally, this topology follows the hierarchical and symmetrical patterns
to connect the different levels. Since this is a large network, tree topology is the best choice
because it guarantees high availability and security. Moreover, it is highly flexible and a hub can
be added to the network so as to connect more user computers. It facilitates centralized
monitoring allowing the network administrators to troubleshoot and reconfigure the network
IT INFRASTRUCTURE 6
easily. Tree topology enables better access to the network because of the point to point
connection (Shekhar, 2016). The devices that will be used in this topology include routers,
hubs/switches, and wireless access points. The router will be used to connect the LAN to the
internet, the hub/switch will be used to extend the network, while the wireless access point will
be used to provide wireless connection.
IP Address Solution
IP addresses are vital to any network because it allows the computers on the network to send and
receive data and files. It identifies the specific computers uniquely on a network. Overlooking on
how important IP addresses are can cause major network problems and may bring about
communication breakdown. Since it is a critical resource, it should be managed because every
device or application on the network from web connectivity, to networked printers, emails, and
file storage requires assignment of IP addresses (Shapiro, 2013).
It is important for SmartDefence to have an IP address solution. Because of the wide network
requirements within the company that requires servers, printers, and quite a large number of end
users, this means that some devices will require static IP addresses while others dynamic. The
servers and the printers will be assigned static IP addresses. The end user devices such as
desktops, laptops, phones, tablets will be assigned IP addresses using a DHCP server.
DHCP server is works with both internet protocol and transmission control protocol to manage
the network. The primary function of DHCP server is to configure and manage IP addresses on
the network automatically and this addresses the challenge of having to assign IP addresses
manually to every device that is connected to the network (Hopping, 2018). Some of the benefits
of DHCP server include IP address management, centralized network client configuration, and
large network support. The table below represent the IP address for each subnet and how they are
assigned by DHCP. The first 20 IP addresses are reserved for management purposes and for
devices that requires static IP.
Subnet name Subnet
address
Subnet
mask
First
useable
address
Last
useable
address
Broadcast
address
DHCP
address range
Toronto
(Mangers’
office)
172.16.0
.0 /24 172.16.0.1
172.16.0.25
4
172.16.0.2
55
172.16.0.20 -
176.16.0.254
easily. Tree topology enables better access to the network because of the point to point
connection (Shekhar, 2016). The devices that will be used in this topology include routers,
hubs/switches, and wireless access points. The router will be used to connect the LAN to the
internet, the hub/switch will be used to extend the network, while the wireless access point will
be used to provide wireless connection.
IP Address Solution
IP addresses are vital to any network because it allows the computers on the network to send and
receive data and files. It identifies the specific computers uniquely on a network. Overlooking on
how important IP addresses are can cause major network problems and may bring about
communication breakdown. Since it is a critical resource, it should be managed because every
device or application on the network from web connectivity, to networked printers, emails, and
file storage requires assignment of IP addresses (Shapiro, 2013).
It is important for SmartDefence to have an IP address solution. Because of the wide network
requirements within the company that requires servers, printers, and quite a large number of end
users, this means that some devices will require static IP addresses while others dynamic. The
servers and the printers will be assigned static IP addresses. The end user devices such as
desktops, laptops, phones, tablets will be assigned IP addresses using a DHCP server.
DHCP server is works with both internet protocol and transmission control protocol to manage
the network. The primary function of DHCP server is to configure and manage IP addresses on
the network automatically and this addresses the challenge of having to assign IP addresses
manually to every device that is connected to the network (Hopping, 2018). Some of the benefits
of DHCP server include IP address management, centralized network client configuration, and
large network support. The table below represent the IP address for each subnet and how they are
assigned by DHCP. The first 20 IP addresses are reserved for management purposes and for
devices that requires static IP.
Subnet name Subnet
address
Subnet
mask
First
useable
address
Last
useable
address
Broadcast
address
DHCP
address range
Toronto
(Mangers’
office)
172.16.0
.0 /24 172.16.0.1
172.16.0.25
4
172.16.0.2
55
172.16.0.20 -
176.16.0.254
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT INFRASTRUCTURE 7
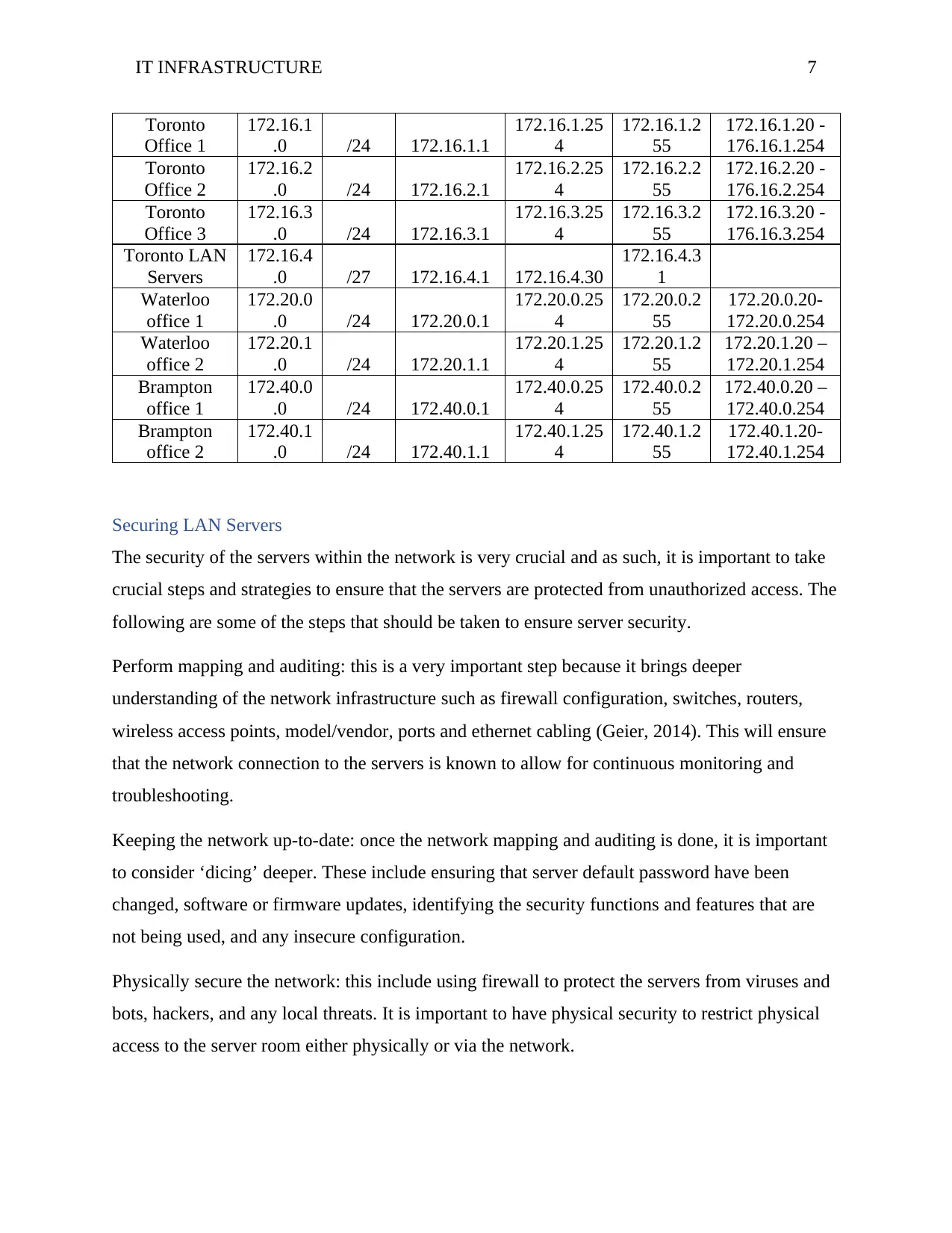
Toronto
Office 1
172.16.1
.0 /24 172.16.1.1
172.16.1.25
4
172.16.1.2
55
172.16.1.20 -
176.16.1.254
Toronto
Office 2
172.16.2
.0 /24 172.16.2.1
172.16.2.25
4
172.16.2.2
55
172.16.2.20 -
176.16.2.254
Toronto
Office 3
172.16.3
.0 /24 172.16.3.1
172.16.3.25
4
172.16.3.2
55
172.16.3.20 -
176.16.3.254
Toronto LAN
Servers
172.16.4
.0 /27 172.16.4.1 172.16.4.30
172.16.4.3
1
Waterloo
office 1
172.20.0
.0 /24 172.20.0.1
172.20.0.25
4
172.20.0.2
55
172.20.0.20-
172.20.0.254
Waterloo
office 2
172.20.1
.0 /24 172.20.1.1
172.20.1.25
4
172.20.1.2
55
172.20.1.20 –
172.20.1.254
Brampton
office 1
172.40.0
.0 /24 172.40.0.1
172.40.0.25
4
172.40.0.2
55
172.40.0.20 –
172.40.0.254
Brampton
office 2
172.40.1
.0 /24 172.40.1.1
172.40.1.25
4
172.40.1.2
55
172.40.1.20-
172.40.1.254
Securing LAN Servers
The security of the servers within the network is very crucial and as such, it is important to take
crucial steps and strategies to ensure that the servers are protected from unauthorized access. The
following are some of the steps that should be taken to ensure server security.
Perform mapping and auditing: this is a very important step because it brings deeper
understanding of the network infrastructure such as firewall configuration, switches, routers,
wireless access points, model/vendor, ports and ethernet cabling (Geier, 2014). This will ensure
that the network connection to the servers is known to allow for continuous monitoring and
troubleshooting.
Keeping the network up-to-date: once the network mapping and auditing is done, it is important
to consider ‘dicing’ deeper. These include ensuring that server default password have been
changed, software or firmware updates, identifying the security functions and features that are
not being used, and any insecure configuration.
Physically secure the network: this include using firewall to protect the servers from viruses and
bots, hackers, and any local threats. It is important to have physical security to restrict physical
access to the server room either physically or via the network.
Toronto
Office 1
172.16.1
.0 /24 172.16.1.1
172.16.1.25
4
172.16.1.2
55
172.16.1.20 -
176.16.1.254
Toronto
Office 2
172.16.2
.0 /24 172.16.2.1
172.16.2.25
4
172.16.2.2
55
172.16.2.20 -
176.16.2.254
Toronto
Office 3
172.16.3
.0 /24 172.16.3.1
172.16.3.25
4
172.16.3.2
55
172.16.3.20 -
176.16.3.254
Toronto LAN
Servers
172.16.4
.0 /27 172.16.4.1 172.16.4.30
172.16.4.3
1
Waterloo
office 1
172.20.0
.0 /24 172.20.0.1
172.20.0.25
4
172.20.0.2
55
172.20.0.20-
172.20.0.254
Waterloo
office 2
172.20.1
.0 /24 172.20.1.1
172.20.1.25
4
172.20.1.2
55
172.20.1.20 –
172.20.1.254
Brampton
office 1
172.40.0
.0 /24 172.40.0.1
172.40.0.25
4
172.40.0.2
55
172.40.0.20 –
172.40.0.254
Brampton
office 2
172.40.1
.0 /24 172.40.1.1
172.40.1.25
4
172.40.1.2
55
172.40.1.20-
172.40.1.254
Securing LAN Servers
The security of the servers within the network is very crucial and as such, it is important to take
crucial steps and strategies to ensure that the servers are protected from unauthorized access. The
following are some of the steps that should be taken to ensure server security.
Perform mapping and auditing: this is a very important step because it brings deeper
understanding of the network infrastructure such as firewall configuration, switches, routers,
wireless access points, model/vendor, ports and ethernet cabling (Geier, 2014). This will ensure
that the network connection to the servers is known to allow for continuous monitoring and
troubleshooting.
Keeping the network up-to-date: once the network mapping and auditing is done, it is important
to consider ‘dicing’ deeper. These include ensuring that server default password have been
changed, software or firmware updates, identifying the security functions and features that are
not being used, and any insecure configuration.
Physically secure the network: this include using firewall to protect the servers from viruses and
bots, hackers, and any local threats. It is important to have physical security to restrict physical
access to the server room either physically or via the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT INFRASTRUCTURE 8
Another way to secure LAN servers is by implementing VLANs to segregate network traffic.
This can be done by using VLANs to group users, wireless access points, and ethernet ports
across the multiple virtual networks. By segregating the networks, the servers can be places in
one VLAN to ensure and enhance security (Liyanage and Gurtov, 2013).
Remote Secure Connection
When it comes to mobile working or working from home, it is necessary to have a policy in
place that is well understood by all the employees. This does not only refer to having a set of
written rules and policies but also conducting awareness and training to ensure that staff working
from home know what to do incase of a problem or what to look for. In order to facilitate the
employees to work remotely in a secure environment the following measures have to be taken:
All the mobile devices should be secured with password. This is to ensure that unauthorize
access to such device is prevented. Password are very vital when it comes working remotely.
Additionally, employees using devices such as phones and tablets to access critical information
should be installed with remote wipe application such that incase such a device is lost or stolen,
the information won’t fall into the wrong hands (Owais, 2018).
Secondly, it is important to ensure that the remote working environment is as secure as the
office. This is achieved by ensuring that endpoint security applications such as antiviruses are
installed and regularly updated. All the applications and software used by the employees should
be updated regularly.
To protect internet traffic the company should use virtual private network and ensure appropriate
policies have been applied. This can be achieved by routing the web traffic through secured
corporate gateways to filter the web traffic and ensure that all sites accessed by the employees
are secure and safe.
All the devices used by the employees should be backed-up securely so that incase information is
lost when staff is working remotely can be recovered. Additionally, it is important to deploy a
data loss prevention mechanism and should be used on endpoint and gateways. By using DLP
and security gateway, the company will be able to prevent staff from maliciously and
inadvertently sending critical information (Tyson and Crawford, 2016). By implementing clear
Another way to secure LAN servers is by implementing VLANs to segregate network traffic.
This can be done by using VLANs to group users, wireless access points, and ethernet ports
across the multiple virtual networks. By segregating the networks, the servers can be places in
one VLAN to ensure and enhance security (Liyanage and Gurtov, 2013).
Remote Secure Connection
When it comes to mobile working or working from home, it is necessary to have a policy in
place that is well understood by all the employees. This does not only refer to having a set of
written rules and policies but also conducting awareness and training to ensure that staff working
from home know what to do incase of a problem or what to look for. In order to facilitate the
employees to work remotely in a secure environment the following measures have to be taken:
All the mobile devices should be secured with password. This is to ensure that unauthorize
access to such device is prevented. Password are very vital when it comes working remotely.
Additionally, employees using devices such as phones and tablets to access critical information
should be installed with remote wipe application such that incase such a device is lost or stolen,
the information won’t fall into the wrong hands (Owais, 2018).
Secondly, it is important to ensure that the remote working environment is as secure as the
office. This is achieved by ensuring that endpoint security applications such as antiviruses are
installed and regularly updated. All the applications and software used by the employees should
be updated regularly.
To protect internet traffic the company should use virtual private network and ensure appropriate
policies have been applied. This can be achieved by routing the web traffic through secured
corporate gateways to filter the web traffic and ensure that all sites accessed by the employees
are secure and safe.
All the devices used by the employees should be backed-up securely so that incase information is
lost when staff is working remotely can be recovered. Additionally, it is important to deploy a
data loss prevention mechanism and should be used on endpoint and gateways. By using DLP
and security gateway, the company will be able to prevent staff from maliciously and
inadvertently sending critical information (Tyson and Crawford, 2016). By implementing clear

IT INFRASTRUCTURE 9
policies, educating employees, and ensuring that security systems are up to date, employees can
work comfortably remotely.
DMZ Servers
DMZ should be placed outside the internal network where servers that are supposed to be
accessed by the outsiders without getting into the internal network. This helps in fine tuning the
monitoring process and limiting access to the internal network. DMZ helps in ensuring that all
the traffic on going in and out of the public servers pass through a firewall. This is achieved by
creating rules that will facilitate outsiders to connect to the email, DNS, and web server through
the internet. The DMZ will ensure that any attempts by the outsiders to connect to other ports
other than the ones specified will be denied by the firewall (Taylor, 2018). There are several
methods to create DMZ; one is by putting a DMZ between two firewalls, this is a firewall
sandwich.
Transmission Medium
The recommended transmission medium to be used while connecting the branch offices is fiber
optic cable. This medium uses the concept of light reflection via a plastic or glass core. This
medium increases the bandwidth and capacity, is light weight, and has minimal signal
attenuation. Fiber optic covers longer distance while ensuring that signal quality is not affected
as it is being transmitted (Popov, 2018).
Remote connectivity solution using VPN
In order to provide secured remote connectivity solution, a VPN LAN-to-LAN will be used. A
remote-access VPN enable users to establish connections that are secured with remote computer
network. Individual users will be able to access secured resources on the company network as if
they were physically connected to the to the network (Broadview, 2018). Encrypted IP traffic is
received by centralized LAN-to-LAN VPN service using the internet. Having a virtual private
network will enable secure remote connectivity.
Conclusion
A network is a very critical resource to any business, as such, it should be protected and secured
at all times. There are several security strategies that can be employed to secure the network
including using firewall, VPN, endpoint security solutions, and many others. When working
policies, educating employees, and ensuring that security systems are up to date, employees can
work comfortably remotely.
DMZ Servers
DMZ should be placed outside the internal network where servers that are supposed to be
accessed by the outsiders without getting into the internal network. This helps in fine tuning the
monitoring process and limiting access to the internal network. DMZ helps in ensuring that all
the traffic on going in and out of the public servers pass through a firewall. This is achieved by
creating rules that will facilitate outsiders to connect to the email, DNS, and web server through
the internet. The DMZ will ensure that any attempts by the outsiders to connect to other ports
other than the ones specified will be denied by the firewall (Taylor, 2018). There are several
methods to create DMZ; one is by putting a DMZ between two firewalls, this is a firewall
sandwich.
Transmission Medium
The recommended transmission medium to be used while connecting the branch offices is fiber
optic cable. This medium uses the concept of light reflection via a plastic or glass core. This
medium increases the bandwidth and capacity, is light weight, and has minimal signal
attenuation. Fiber optic covers longer distance while ensuring that signal quality is not affected
as it is being transmitted (Popov, 2018).
Remote connectivity solution using VPN
In order to provide secured remote connectivity solution, a VPN LAN-to-LAN will be used. A
remote-access VPN enable users to establish connections that are secured with remote computer
network. Individual users will be able to access secured resources on the company network as if
they were physically connected to the to the network (Broadview, 2018). Encrypted IP traffic is
received by centralized LAN-to-LAN VPN service using the internet. Having a virtual private
network will enable secure remote connectivity.
Conclusion
A network is a very critical resource to any business, as such, it should be protected and secured
at all times. There are several security strategies that can be employed to secure the network
including using firewall, VPN, endpoint security solutions, and many others. When working
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT INFRASTRUCTURE 10
remotely, the company should ensure that employees working remotely are connecting to the
company network securely using VPNs.
remotely, the company should ensure that employees working remotely are connecting to the
company network securely using VPNs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT INFRASTRUCTURE 11
Reference List
Broadview, N. (2018). Remote Access Solutions: Why VPNs Aren’t Enough | Broadview
Networks. [online] Broadview Networks. Available at: https://broadviewnetworks.ca/remote-
access-solutions-why-vpns-arent-enough/ [Accessed 27 Nov. 2018].
Chaturvedi, B. (2017). What is Tree Topology? Advantages and Disadvantages. [online]
Pctechnicalpro.blogspot.com. Available at: https://pctechnicalpro.blogspot.com/2017/08/tree-
topology-advantages-disadvantages.html [Accessed 27 Nov. 2018].
Geier, E. (2014). 8 ways to improve wired network security. [online] Network World. Available
at: https://www.networkworld.com/article/2175048/wireless/8-ways-to-improve-wired-network-
security.html [Accessed 27 Nov. 2018].
Hopping, C. (2018). What is a DHCP server?. [online] IT PRO. Available at:
https://www.itpro.co.uk/network-access-control/30329/what-is-a-dhcp-server [Accessed 29 Nov.
2018].
Liyanage, M. and Gurtov, A. (2013). Securing virtual private LAN service by efficient key
management. Security and Communication Networks, 7(1), pp.1-13.
Owais, A. (2018). Remote Access VPN: Secure Your Access Point with PureVPN. [online]
PureVPN Blog. Available at: https://www.purevpn.com/blog/secure-remote-access-vpn-solution/
[Accessed 27 Nov. 2018].
Popov, S. (2018). FIBER OPTIC CABLE OF CONSISTENTLY HIGH QUALITY. LastMile,
(4), pp.18-20.
Shapiro, A. (2013). Why Do Unique IP Addresses Matter and What Is Their Importance?.
[online] Business 2 Community. Available at: https://www.business2community.com/tech-
gadgets/why-do-unique-ip-addresses-matter-and-what-is-their-importance-0474610 [Accessed
29 Nov. 2018].
Shekhar, A. (2016). What Is Tree Topology? Advantages And Disadvantages Of Tree Topology.
[online] Fossbytes. Available at: https://fossbytes.com/tree-topology-advantage-disadvantage/
[Accessed 27 Nov. 2018].
Reference List
Broadview, N. (2018). Remote Access Solutions: Why VPNs Aren’t Enough | Broadview
Networks. [online] Broadview Networks. Available at: https://broadviewnetworks.ca/remote-
access-solutions-why-vpns-arent-enough/ [Accessed 27 Nov. 2018].
Chaturvedi, B. (2017). What is Tree Topology? Advantages and Disadvantages. [online]
Pctechnicalpro.blogspot.com. Available at: https://pctechnicalpro.blogspot.com/2017/08/tree-
topology-advantages-disadvantages.html [Accessed 27 Nov. 2018].
Geier, E. (2014). 8 ways to improve wired network security. [online] Network World. Available
at: https://www.networkworld.com/article/2175048/wireless/8-ways-to-improve-wired-network-
security.html [Accessed 27 Nov. 2018].
Hopping, C. (2018). What is a DHCP server?. [online] IT PRO. Available at:
https://www.itpro.co.uk/network-access-control/30329/what-is-a-dhcp-server [Accessed 29 Nov.
2018].
Liyanage, M. and Gurtov, A. (2013). Securing virtual private LAN service by efficient key
management. Security and Communication Networks, 7(1), pp.1-13.
Owais, A. (2018). Remote Access VPN: Secure Your Access Point with PureVPN. [online]
PureVPN Blog. Available at: https://www.purevpn.com/blog/secure-remote-access-vpn-solution/
[Accessed 27 Nov. 2018].
Popov, S. (2018). FIBER OPTIC CABLE OF CONSISTENTLY HIGH QUALITY. LastMile,
(4), pp.18-20.
Shapiro, A. (2013). Why Do Unique IP Addresses Matter and What Is Their Importance?.
[online] Business 2 Community. Available at: https://www.business2community.com/tech-
gadgets/why-do-unique-ip-addresses-matter-and-what-is-their-importance-0474610 [Accessed
29 Nov. 2018].
Shekhar, A. (2016). What Is Tree Topology? Advantages And Disadvantages Of Tree Topology.
[online] Fossbytes. Available at: https://fossbytes.com/tree-topology-advantage-disadvantage/
[Accessed 27 Nov. 2018].

IT INFRASTRUCTURE 12
Taylor, L. (2018). DMZs for dummies | ZDNet. [online] ZDNet. Available at:
https://www.zdnet.com/article/dmzs-for-dummies-5000297743/ [Accessed 27 Nov. 2018].
Tyson, J. and Crawford, S. (2016). How VPNs Work. [online] HowStuffWorks. Available at:
https://computer.howstuffworks.com/vpn3.htm [Accessed 27 Nov. 2018].
Taylor, L. (2018). DMZs for dummies | ZDNet. [online] ZDNet. Available at:
https://www.zdnet.com/article/dmzs-for-dummies-5000297743/ [Accessed 27 Nov. 2018].
Tyson, J. and Crawford, S. (2016). How VPNs Work. [online] HowStuffWorks. Available at:
https://computer.howstuffworks.com/vpn3.htm [Accessed 27 Nov. 2018].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



