Murdoch University: Smartphone User Security Behavior Analysis
VerifiedAdded on 2022/11/15
|11
|2584
|337
Report
AI Summary
This report analyzes smartphone user security behavior, drawing upon a literature review of ten research articles. It explores the impact of user perceptions, attitudes, and understanding on smartphone security, including discussions on malware attacks, authentication methods, and the role of human psychology. The report examines findings related to user behavior across different age groups and the influence of third-party applications on security risks. It highlights key insights from various studies, including the importance of developer focus on user behavior, the impact of social networking, and the need for effective security measures. The report also includes a table summarizing the research findings of the selected papers. The assignment, completed for Murdoch University's BSC203 course, aims to synthesize and critically analyze the existing knowledge on the topic.

Running Head: Smart Phone user Security Behavior
0
Smartphone User Security Behavior
July 16
2019
0
Smartphone User Security Behavior
July 16
2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Smartphone User Security Behavior 1
Table of Contents
Introduction.........................................................................................................................................2
Summary.............................................................................................................................................2
Literature Review...............................................................................................................................3
Findings of Article..............................................................................................................................6
Conclusion..........................................................................................................................................8
References...........................................................................................................................................9
Table of Contents
Introduction.........................................................................................................................................2
Summary.............................................................................................................................................2
Literature Review...............................................................................................................................3
Findings of Article..............................................................................................................................6
Conclusion..........................................................................................................................................8
References...........................................................................................................................................9
Smartphone User Security Behavior 2
Introduction
In this analysis the topic is chosen for the review is Smartphone user security behavior.
Today it is the era of technology where every task is getting performed by using gadgets and
applications. Communication is the most important medium to exchange of information and data.
In this assignment different articles are chosen, their perception and their ideas are described
briefly. The statistics reports are also analyzed. The assignment is totally based upon the behavior
of smartphone users on which the security and breaching depends. In the assignment the findings
of journal article are also defined.
Summary
In human society cellular phones become the important and large part, it becomes a very
useful device in the digital age for communication. Smartphones are the mobile computing devices
which are featured with the good hardware power and an operating system which controls the
software functions like web-browsing, internet, multimedia functionality i.e. Videos, Music,
camera, games etc. These phones are comprises of distinct sensors such as proximity sensors,
gyroscope, barometer, accelerometer etc. all of their functions are hold by their own software. By
the end of the year 2014 1.76 million people approximately using smartphones which was
increased by 25 percent from year 2013...
Introduction
In this analysis the topic is chosen for the review is Smartphone user security behavior.
Today it is the era of technology where every task is getting performed by using gadgets and
applications. Communication is the most important medium to exchange of information and data.
In this assignment different articles are chosen, their perception and their ideas are described
briefly. The statistics reports are also analyzed. The assignment is totally based upon the behavior
of smartphone users on which the security and breaching depends. In the assignment the findings
of journal article are also defined.
Summary
In human society cellular phones become the important and large part, it becomes a very
useful device in the digital age for communication. Smartphones are the mobile computing devices
which are featured with the good hardware power and an operating system which controls the
software functions like web-browsing, internet, multimedia functionality i.e. Videos, Music,
camera, games etc. These phones are comprises of distinct sensors such as proximity sensors,
gyroscope, barometer, accelerometer etc. all of their functions are hold by their own software. By
the end of the year 2014 1.76 million people approximately using smartphones which was
increased by 25 percent from year 2013...
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Smartphone User Security Behavior 3
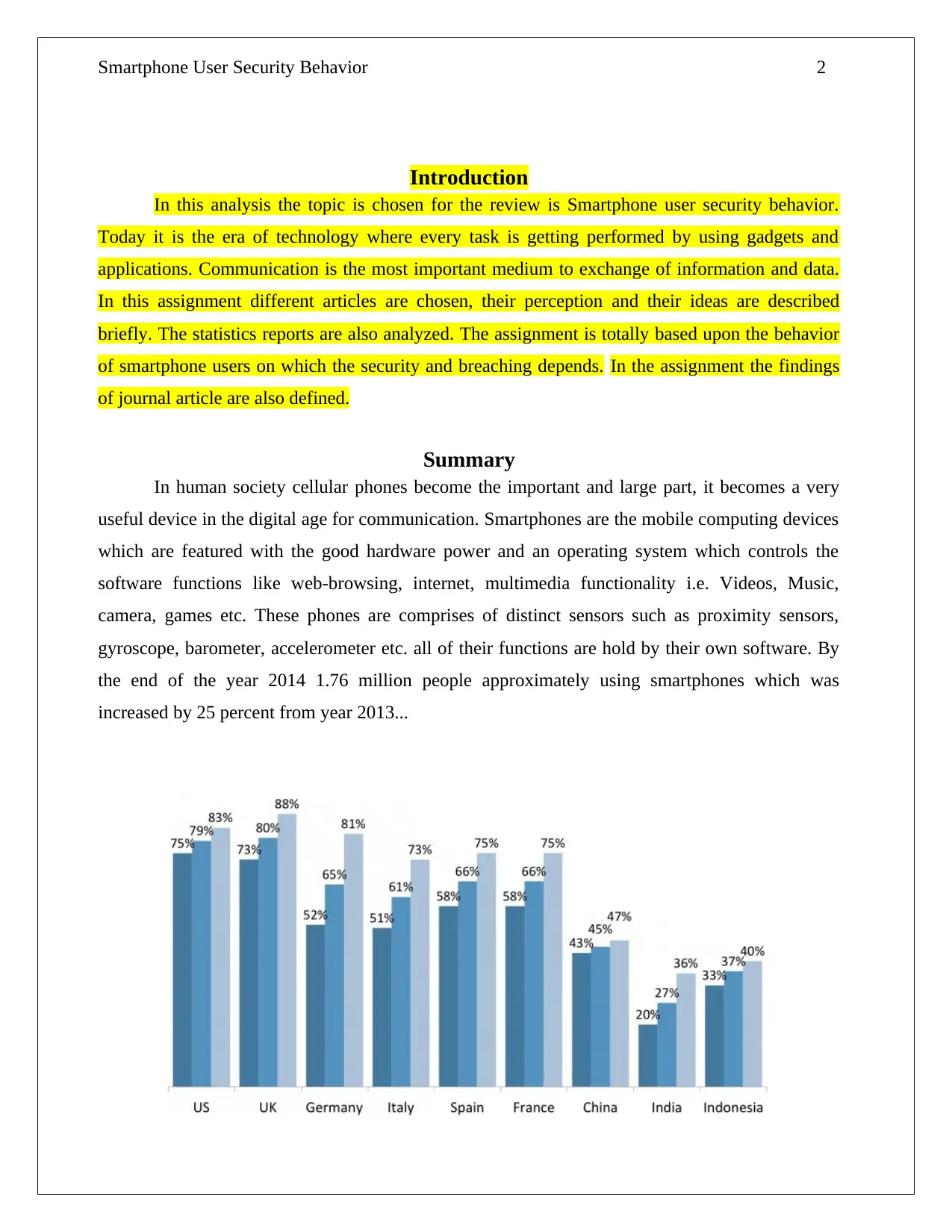
Image Source: (Meola , 2016)
Literature Review
According to the article which is written by Mansour Alsaleh, Noura Alomar and
Addulrahman Alarifi security threat of smartphone in human community is an important
technological factor. They explained that security of the smartphone is totally affected by the
perception, attitude and understanding of users. According to their research in 2014 Symantec
examined that over 15% of the application out of 6 million mobile applications were included with
malicious content. For the article and its conclusion researchers performed approximately thirty
qualitative observations to examine the correlation between the behavior and security threat of the
smartphone users and they found youth population preferred to behave securely when they using
their smartphones. According to the statement provided in the article by the authors that
applications developers are much capable of make innovation while developing smartphone
applications so they should focus on these behaviors of users which plays significant role in
security risk of smartphones (Alsaleh , Alomar , & Alarifi , 2017 ).
In the other article written by Amit Das and Habib Ullah Khan the description was based
upon the analysis of various surveys which were performed by different organizations concerning
the use of smartphones and security. According to study of the authors the behavior for the security
of smartphones is comfortable in Middle East countries with the usage of 75% of smartphone. The
studies conducted by the authors are conducted upon the existed theory of behavior for information
security relating to new domains of smartphone security (Das & Khan , 2016). They conclude that
security threats get upgrade with the time hence every smartphone users also have to focus on their
perceptions or behaviors towards the security.
An article which was published by Murat Koyuncu and Tolga Pustali defines the level of
awareness on the security of the smartphone by the population amongst different age groups. For
this they analyzed various theoretical research papers and surveys conducted by well-known
organization. They concluded that the behavior of users is responsible about the security of
Smartphone. Authors of the article provided a statement that the proper education of an individual
also affects the security concerns if any person has the complete knowledge than it develop a
positive effect positively on security concerns (Koyuncu & Pusatli , 2019).
Image Source: (Meola , 2016)
Literature Review
According to the article which is written by Mansour Alsaleh, Noura Alomar and
Addulrahman Alarifi security threat of smartphone in human community is an important
technological factor. They explained that security of the smartphone is totally affected by the
perception, attitude and understanding of users. According to their research in 2014 Symantec
examined that over 15% of the application out of 6 million mobile applications were included with
malicious content. For the article and its conclusion researchers performed approximately thirty
qualitative observations to examine the correlation between the behavior and security threat of the
smartphone users and they found youth population preferred to behave securely when they using
their smartphones. According to the statement provided in the article by the authors that
applications developers are much capable of make innovation while developing smartphone
applications so they should focus on these behaviors of users which plays significant role in
security risk of smartphones (Alsaleh , Alomar , & Alarifi , 2017 ).
In the other article written by Amit Das and Habib Ullah Khan the description was based
upon the analysis of various surveys which were performed by different organizations concerning
the use of smartphones and security. According to study of the authors the behavior for the security
of smartphones is comfortable in Middle East countries with the usage of 75% of smartphone. The
studies conducted by the authors are conducted upon the existed theory of behavior for information
security relating to new domains of smartphone security (Das & Khan , 2016). They conclude that
security threats get upgrade with the time hence every smartphone users also have to focus on their
perceptions or behaviors towards the security.
An article which was published by Murat Koyuncu and Tolga Pustali defines the level of
awareness on the security of the smartphone by the population amongst different age groups. For
this they analyzed various theoretical research papers and surveys conducted by well-known
organization. They concluded that the behavior of users is responsible about the security of
Smartphone. Authors of the article provided a statement that the proper education of an individual
also affects the security concerns if any person has the complete knowledge than it develop a
positive effect positively on security concerns (Koyuncu & Pusatli , 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Smartphone User Security Behavior 4
In an article which was published in 2016 by two authors Abdulaziz alzubaidi and Jugal
Kalita performed their research on the authentication of Smartphone users through behavior.
According to both of the authors each smartphones are installed with many application and each of
them has their own specific functionality. So developers should implement feature which can
identify the usage time of the application through differentiate can be made between authorized
person and non-authorized person by the application. It would help users in breaching the security
of their smartphone (Alzubaidi & Kalita , 2015 ).
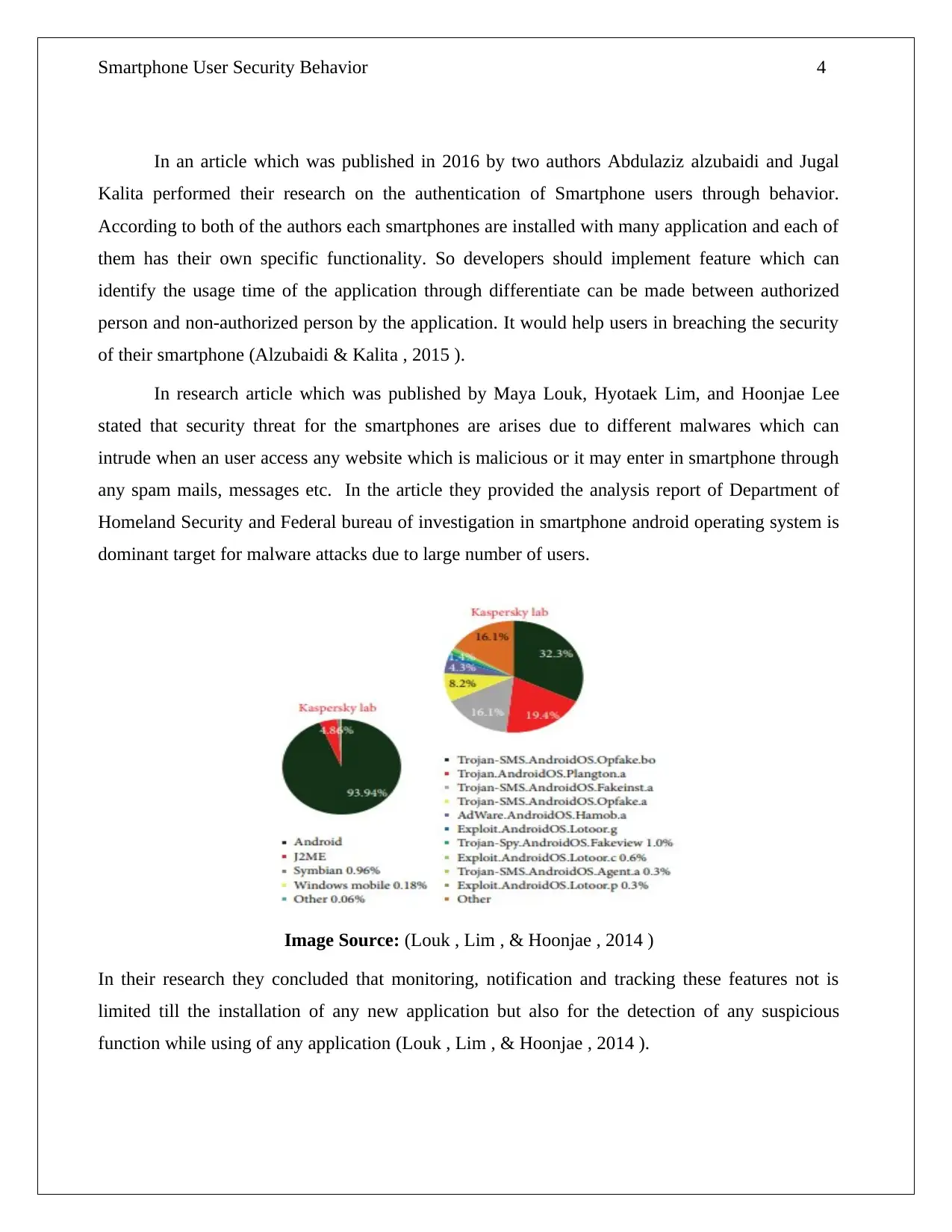
In research article which was published by Maya Louk, Hyotaek Lim, and Hoonjae Lee
stated that security threat for the smartphones are arises due to different malwares which can
intrude when an user access any website which is malicious or it may enter in smartphone through
any spam mails, messages etc. In the article they provided the analysis report of Department of
Homeland Security and Federal bureau of investigation in smartphone android operating system is
dominant target for malware attacks due to large number of users.
Image Source: (Louk , Lim , & Hoonjae , 2014 )
In their research they concluded that monitoring, notification and tracking these features not is
limited till the installation of any new application but also for the detection of any suspicious
function while using of any application (Louk , Lim , & Hoonjae , 2014 ).
In an article which was published in 2016 by two authors Abdulaziz alzubaidi and Jugal
Kalita performed their research on the authentication of Smartphone users through behavior.
According to both of the authors each smartphones are installed with many application and each of
them has their own specific functionality. So developers should implement feature which can
identify the usage time of the application through differentiate can be made between authorized
person and non-authorized person by the application. It would help users in breaching the security
of their smartphone (Alzubaidi & Kalita , 2015 ).
In research article which was published by Maya Louk, Hyotaek Lim, and Hoonjae Lee
stated that security threat for the smartphones are arises due to different malwares which can
intrude when an user access any website which is malicious or it may enter in smartphone through
any spam mails, messages etc. In the article they provided the analysis report of Department of
Homeland Security and Federal bureau of investigation in smartphone android operating system is
dominant target for malware attacks due to large number of users.
Image Source: (Louk , Lim , & Hoonjae , 2014 )
In their research they concluded that monitoring, notification and tracking these features not is
limited till the installation of any new application but also for the detection of any suspicious
function while using of any application (Louk , Lim , & Hoonjae , 2014 ).

Smartphone User Security Behavior 5
However in article which was published by Multidisciplinary Scientific Journal the
discussion was made on access of the technological devices in which smartphone was also
included. Authors of the journal articles find in their studies that due to rise in the usage of these
technologies lead to the introduction of IoT where every device is interconnected with each other.
They concluded the results that further steps for the development in smartphones to avoid the
security risks are voice sensing features, implementing interfaces for expanding the bio-
psychological devices. Authors were totally link the relation of security of smartphones with the
biological activity of human body (Montag, Baumeister, & Christopher, 2019).
In the journal of information security and application authors performed their research
areas where the smartphones are used. According to them users prefer their smartphones for
accessing social networks, for the banking transactions, sharing pictures and videos with the family
and friends. They found that 70% of smart phone users not prefer any security method in their
phones. Authors proposed the modal which was based upon the biometric system for the
authentication of smartphone user (Kranikiotis , Symeonidis, & Saripalle, 2019). Every
smartphone user should select the security patterns which are available in their device for the
security of their own data and information. It will protect them from getting access their device by
any unauthorized person.
Rather than all the above theories in the article which was published in May 2019 gives the
explanation that with the increase in the usage of the smartphones the penetration is also increased
the risk the security. The applications which are installed in smart phone exchange the data all over
web which may raise the security and privacy concerns these applications may access the
confidential data of users can be compromised easily. So it should be ensured by the developer
team that all the data of users remain safe and without any breaching (Gupta , Buriro, & Crispo ,
2019 ). There should be some parameter has to be decided by the authorities or by the management
of user interface. If any application is getting listed with them than it should be analyzed that if
there is no any malicious or suspicious file or terms are not available. Every day almost hundreds
of applications are listed with the user interface or with the operating system software. Most of
them are developed by illegal ways and methods which lead to risk of the smartphones.
In the article which was presented by Silas Formunyuy Verijika connectivity are
maintained in better way through smartphones which is the possible reason people are tending
towards smartphones. According to the research conducted by the authors they provide the
However in article which was published by Multidisciplinary Scientific Journal the
discussion was made on access of the technological devices in which smartphone was also
included. Authors of the journal articles find in their studies that due to rise in the usage of these
technologies lead to the introduction of IoT where every device is interconnected with each other.
They concluded the results that further steps for the development in smartphones to avoid the
security risks are voice sensing features, implementing interfaces for expanding the bio-
psychological devices. Authors were totally link the relation of security of smartphones with the
biological activity of human body (Montag, Baumeister, & Christopher, 2019).
In the journal of information security and application authors performed their research
areas where the smartphones are used. According to them users prefer their smartphones for
accessing social networks, for the banking transactions, sharing pictures and videos with the family
and friends. They found that 70% of smart phone users not prefer any security method in their
phones. Authors proposed the modal which was based upon the biometric system for the
authentication of smartphone user (Kranikiotis , Symeonidis, & Saripalle, 2019). Every
smartphone user should select the security patterns which are available in their device for the
security of their own data and information. It will protect them from getting access their device by
any unauthorized person.
Rather than all the above theories in the article which was published in May 2019 gives the
explanation that with the increase in the usage of the smartphones the penetration is also increased
the risk the security. The applications which are installed in smart phone exchange the data all over
web which may raise the security and privacy concerns these applications may access the
confidential data of users can be compromised easily. So it should be ensured by the developer
team that all the data of users remain safe and without any breaching (Gupta , Buriro, & Crispo ,
2019 ). There should be some parameter has to be decided by the authorities or by the management
of user interface. If any application is getting listed with them than it should be analyzed that if
there is no any malicious or suspicious file or terms are not available. Every day almost hundreds
of applications are listed with the user interface or with the operating system software. Most of
them are developed by illegal ways and methods which lead to risk of the smartphones.
In the article which was presented by Silas Formunyuy Verijika connectivity are
maintained in better way through smartphones which is the possible reason people are tending
towards smartphones. According to the research conducted by the authors they provide the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Smartphone User Security Behavior 6
outcome in which it was concluded that by using or installing third party applications lead to the
security risk of the personal information and confidential data. In the study the author lastly stated
that regret and security intentions are the major factors which predict the security behavior of
smartphone (Verkijika , 2018 ).
Another journal states that the smartphone become the assistant of an individual who is
creating connection and working. If compared to Personal computer smartphones are becoming
more private devices. Even the cybercriminals prefer to attack on smartphones to steal the private
information. All of cybercriminals are aware that with the increase in the use of the smartphones
people store their personal and important information in their phones so by attacking on
smartphones these cybercriminals steal their all credential information including their card details,
information of bank accounts and other confidential data. They use these information to blackmail
the victim. Hence every smartphone user must ensure before installing the application if it verified
or not because when the user is installing the application he/she has to accept the agreement
through which user allow the access of the information with the owner or manufacturer of
application. (Meng , Li, & Jiang , 2019).
Findings of Article
S. No. Journal Name Finding
1. Smartphone users:
Understanding how
security mechanisms are
perceived and new
persuasive methods
In the article authors concluded that smartphones and their
security is totally depend upon the application and their
designing. Developers should consider all the security
measures while the developing any application.
2. Smartphone behaviors of
smartphone users
According to the article the smartphone users are worried
about security of their smartphones. Overall level of the
security behavior is very low.
3. Security Awareness Level
of Smartphone Users: An
This article focused on the usage of the smartphone
according to age groups, it is identified that young people
outcome in which it was concluded that by using or installing third party applications lead to the
security risk of the personal information and confidential data. In the study the author lastly stated
that regret and security intentions are the major factors which predict the security behavior of
smartphone (Verkijika , 2018 ).
Another journal states that the smartphone become the assistant of an individual who is
creating connection and working. If compared to Personal computer smartphones are becoming
more private devices. Even the cybercriminals prefer to attack on smartphones to steal the private
information. All of cybercriminals are aware that with the increase in the use of the smartphones
people store their personal and important information in their phones so by attacking on
smartphones these cybercriminals steal their all credential information including their card details,
information of bank accounts and other confidential data. They use these information to blackmail
the victim. Hence every smartphone user must ensure before installing the application if it verified
or not because when the user is installing the application he/she has to accept the agreement
through which user allow the access of the information with the owner or manufacturer of
application. (Meng , Li, & Jiang , 2019).
Findings of Article
S. No. Journal Name Finding
1. Smartphone users:
Understanding how
security mechanisms are
perceived and new
persuasive methods
In the article authors concluded that smartphones and their
security is totally depend upon the application and their
designing. Developers should consider all the security
measures while the developing any application.
2. Smartphone behaviors of
smartphone users
According to the article the smartphone users are worried
about security of their smartphones. Overall level of the
security behavior is very low.
3. Security Awareness Level
of Smartphone Users: An
This article focused on the usage of the smartphone
according to age groups, it is identified that young people
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Smartphone User Security Behavior 7
Exploratory Case Study are more cautious for the security of their smartphones.
4. Authentication of
Smartphone Users Using
Behavioral Biometrics
This article was mainly focused on the methods or type of
passwords implemented in smartphones.
5. An Analysis of Security
System for Intrusion in
Smartphone Environment
The article defines about the malware attacks which are
performed on smartphones and which are totally depends
upon the behavior of people.
6. A Study of User
Perception on Features
Used in Behavior-Based
Authentication
The article represents the concept on the security of the
smartphone varies on the type of user some users are not
much aware about the security of their data while some
cares a lot for the security of their smartphone.
7. Concept, Possibilities and
Pilot-Testing of a New
Smartphone Application
for the Social and Life
Sciences to Study Human
Behavior Including
Validation Data from
Personality Psychology
This article explains that human psychology and other
factors which are related to the human mental health are
responsible for the security risk of smartphones.
8. SocialAuth: Designing
Touch Behavioral
Smartphone User
Authentication Based on
Social Networking
Applications
The article describes about the threats of smartphone
security. As per the article there are many ways from
where the security of a smartphone can be breached. In
these ways the social networking and other application
plays the role of mediator
9. Understanding
smartphone security
This article explains and based upon the Protection
Motivation Theory and its core variable which is used
Exploratory Case Study are more cautious for the security of their smartphones.
4. Authentication of
Smartphone Users Using
Behavioral Biometrics
This article was mainly focused on the methods or type of
passwords implemented in smartphones.
5. An Analysis of Security
System for Intrusion in
Smartphone Environment
The article defines about the malware attacks which are
performed on smartphones and which are totally depends
upon the behavior of people.
6. A Study of User
Perception on Features
Used in Behavior-Based
Authentication
The article represents the concept on the security of the
smartphone varies on the type of user some users are not
much aware about the security of their data while some
cares a lot for the security of their smartphone.
7. Concept, Possibilities and
Pilot-Testing of a New
Smartphone Application
for the Social and Life
Sciences to Study Human
Behavior Including
Validation Data from
Personality Psychology
This article explains that human psychology and other
factors which are related to the human mental health are
responsible for the security risk of smartphones.
8. SocialAuth: Designing
Touch Behavioral
Smartphone User
Authentication Based on
Social Networking
Applications
The article describes about the threats of smartphone
security. As per the article there are many ways from
where the security of a smartphone can be breached. In
these ways the social networking and other application
plays the role of mediator
9. Understanding
smartphone security
This article explains and based upon the Protection
Motivation Theory and its core variable which is used
Smartphone User Security Behavior 8
behaviors: An extension
of the protection
motivation theory with
anticipated regret
widely for the security intentions. There are different
dimensions where the security behavior is measured
including the organizations and personal computing.
10. DriverAuth: Behavioral
biometric-based driver
authentication mechanism
for on-demand ride and
ridesharing infrastructure
The article deal with the type of security methods which
are currently implemented in the smartphones, the article
explains that these method selections are totally depends
upon user and their attitude or the way in which they use
their smartphone.
Conclusion
The literature review consists of the different journal articles which are based upon the
security behavior of smartphone user. These articles consist of the different theory and explain their
perception about the usage of the smartphone and the factors which are responsible for different
risks for the smartphone security. Security of every smartphone may get breach due to distinct
reasons in which malwares, spam messages and other activity which get accessed by the
applications get compromised; these all methods and ways are explained in the above articles which
are described above. Further in the analysis the findings of each article are concluded.
behaviors: An extension
of the protection
motivation theory with
anticipated regret
widely for the security intentions. There are different
dimensions where the security behavior is measured
including the organizations and personal computing.
10. DriverAuth: Behavioral
biometric-based driver
authentication mechanism
for on-demand ride and
ridesharing infrastructure
The article deal with the type of security methods which
are currently implemented in the smartphones, the article
explains that these method selections are totally depends
upon user and their attitude or the way in which they use
their smartphone.
Conclusion
The literature review consists of the different journal articles which are based upon the
security behavior of smartphone user. These articles consist of the different theory and explain their
perception about the usage of the smartphone and the factors which are responsible for different
risks for the smartphone security. Security of every smartphone may get breach due to distinct
reasons in which malwares, spam messages and other activity which get accessed by the
applications get compromised; these all methods and ways are explained in the above articles which
are described above. Further in the analysis the findings of each article are concluded.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Smartphone User Security Behavior 9
References
Alsaleh , M., Alomar , N., & Alarifi , A. (2017 ). Smartphone users: Understanding how security
mechanisms are perceived and new persuasive methods. Plos One.
Alzubaidi, A., & Kalita , J. (2015 ). Authentication of Smartphone Users Behavioral Biometrics.
Journal of IEEE Communications Surveys and Tutorials,, 27-28.
Das , A., & Khan , U. H. (2016). Security behaviors ofsmartphone users. Journal of Information
Management & Computer Security , 116.
Gupta , S., Buriro, A., & Crispo , B. (2019 ). DriverAuth: Behavioral biometric-based driver
authentication mechanism for on-demand ride and ridesharing infrastructure. The Korean
institue of communication and information science, 16-20.
Koyuncu, M., & Pusatli , T. (2019). Security Awareness Level of Smartphone Users: An
Exploratory Case Study. Mobile Information Systems, 11.
Kranikiotis , T., Symeonidis, A. L., & Saripalle, S. K. (2019). A Behavioral Biometrics Dataset
towards Continuous Implicit Authentication. Journal of Department of Electrical and
Computer Engineering, Aristotle University of Thessaloniki.
Louk , M., Lim , H., & Hoonjae , L. (2014 ). An Analysis of Security System for Intrusion in
Smartphone Environment. The Scientific World Journal, 1-12.
Meng , W., Li, W., & Jiang , L. (2019). SocialAuth: Designing Touch Behavioral Smartphone
User Authentication Based on Social Networking Applications. IFIP Advances in
Information and Communication Technology , 180-193.
Meola , A. (2016). Global smartphone shipments hit a turning point. New York: Business Insider
Intelligence.
Montag, C., Baumeister, H., & Christopher, K. (2019). Concept, Possibilities and Pilot-Testing of
a New Smartphone Application for the Social and Life Sciences to Study Human Behavior
Including Validation Data from Personality Psychology. Multidisciplinary Scientific
Journal .
Verkijika , S. F. (2018 ). Understanding smartphone security behaviors: An extension of the
protection motivation theory with anticipated regret. Journal of Computer and Secirtiy ,
860-870.
References
Alsaleh , M., Alomar , N., & Alarifi , A. (2017 ). Smartphone users: Understanding how security
mechanisms are perceived and new persuasive methods. Plos One.
Alzubaidi, A., & Kalita , J. (2015 ). Authentication of Smartphone Users Behavioral Biometrics.
Journal of IEEE Communications Surveys and Tutorials,, 27-28.
Das , A., & Khan , U. H. (2016). Security behaviors ofsmartphone users. Journal of Information
Management & Computer Security , 116.
Gupta , S., Buriro, A., & Crispo , B. (2019 ). DriverAuth: Behavioral biometric-based driver
authentication mechanism for on-demand ride and ridesharing infrastructure. The Korean
institue of communication and information science, 16-20.
Koyuncu, M., & Pusatli , T. (2019). Security Awareness Level of Smartphone Users: An
Exploratory Case Study. Mobile Information Systems, 11.
Kranikiotis , T., Symeonidis, A. L., & Saripalle, S. K. (2019). A Behavioral Biometrics Dataset
towards Continuous Implicit Authentication. Journal of Department of Electrical and
Computer Engineering, Aristotle University of Thessaloniki.
Louk , M., Lim , H., & Hoonjae , L. (2014 ). An Analysis of Security System for Intrusion in
Smartphone Environment. The Scientific World Journal, 1-12.
Meng , W., Li, W., & Jiang , L. (2019). SocialAuth: Designing Touch Behavioral Smartphone
User Authentication Based on Social Networking Applications. IFIP Advances in
Information and Communication Technology , 180-193.
Meola , A. (2016). Global smartphone shipments hit a turning point. New York: Business Insider
Intelligence.
Montag, C., Baumeister, H., & Christopher, K. (2019). Concept, Possibilities and Pilot-Testing of
a New Smartphone Application for the Social and Life Sciences to Study Human Behavior
Including Validation Data from Personality Psychology. Multidisciplinary Scientific
Journal .
Verkijika , S. F. (2018 ). Understanding smartphone security behaviors: An extension of the
protection motivation theory with anticipated regret. Journal of Computer and Secirtiy ,
860-870.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Smartphone User Security Behavior 10
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





