BN305 - SME Network and VPN Services Design for Organizations
VerifiedAdded on 2023/06/04
|10
|1880
|415
Report
AI Summary
This report provides a detailed VPN network design tailored for Small and Medium Enterprises (SMEs), addressing the critical need for secure data transmission between remote sites. It begins by outlining the project's scope and limitations, emphasizing the importance of identifying current network frameworks and essential hardware/software requirements. The report highlights key requirements, including adherence to quality standards, network traffic subdivision through VLANs, restricted server access, server virtualization, IP addressing plan implementation, and the deployment of a RADIUS server for user authentication and authorization. The solution design encompasses logical and physical network layouts, hub and spoke topology selection, a comprehensive IP addressing scheme, robust security features and policies utilizing IPSec and multi-layer security models, redundancy and failover plans for enhanced network uptime, and VPN service implementation details including IPSEC, PPP, and MPPE protocol usage. The design also incorporates a DMZ zone for file and email servers to improve security and reliability. The report concludes by emphasizing the importance of analyzing SME requirements for VPN service selection, creating security policies for user access management, and establishing a VPN hub and spoke topology with failover planning to manage network complexity. Desklib offers a wealth of similar solved assignments and study resources for students.

Running head: VIRTUAL PRIVATE NETWORK
VPN Network Design for SME network and VPN services
Name of the Student
Name of the University
Author’s Note
VPN Network Design for SME network and VPN services
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
VIRTUAL PRIVATE NETWORK
Table of Contents
Introduction..............................................................................................................................2
Scopes and Limitations.............................................................................................................2
Requirements...........................................................................................................................2
Solution Design.........................................................................................................................3
a. Logical Design...................................................................................................................3
b. Physical Design.................................................................................................................4
c. Network Topologies..........................................................................................................4
d. IP Addressing....................................................................................................................4
e. Security features and policies...........................................................................................5
f. Redundancy and failover plans..........................................................................................5
g. VPN service implementation.............................................................................................5
Conclusion................................................................................................................................7
Bibliography..............................................................................................................................8
VIRTUAL PRIVATE NETWORK
Table of Contents
Introduction..............................................................................................................................2
Scopes and Limitations.............................................................................................................2
Requirements...........................................................................................................................2
Solution Design.........................................................................................................................3
a. Logical Design...................................................................................................................3
b. Physical Design.................................................................................................................4
c. Network Topologies..........................................................................................................4
d. IP Addressing....................................................................................................................4
e. Security features and policies...........................................................................................5
f. Redundancy and failover plans..........................................................................................5
g. VPN service implementation.............................................................................................5
Conclusion................................................................................................................................7
Bibliography..............................................................................................................................8

2
VIRTUAL PRIVATE NETWORK
Introduction
After a detailed investigation of the infrastructure of the organization and identification of
the needs of the network the report is prepared. The current needs of the organization is to
establish a VPN connection between remote sites of the same organization and securely
transmission of the data packets in the network. The success of the development of the network
depends on the successful implementation of the VPN. The VPN services that should be identified
that are needed by the organization and the scopes of the project should be defined for the
implementation of the new technology.
Scopes and Limitations
For the development of the VPN network the current network framework should be
identified and with the required number of hardware and software that are essential for the
development of the network. The network device should be configured according to the needs of
the organization and there should be used in future for the expansion of the current network. The
network should be connected with a wireless router such that the users with mobile devices can
connect with the wifi network for sending and receiving data packets in the network. A secure cloud
solution can be used for the storage of the data and allowing the access to the limited number of
users for the management of the information.
During the project development different barrier or constraint can rise that can affect the project
development such as the addition of extra cost during the progress of the project. The unavailability
of a hardware device and incompatibility of a device with the protocols and service required for the
configuration of the vpn network should be identified before the selection of the network hardware.
The skills and knowledge of the network engineer for configuration and troubleshooting the network
can also become a problem for the development of the network.
Requirements
For the analysis of the requirement the stakeholders must be involved and the service
required by them should be identified. The list of requirement for the development of the network
are listed below:
Quality of standards should be followed for the selection of the hardware device and
its installation in different parts of the network.
The traffic in the network should be sub divided by creating different vlan for each of
the department
VIRTUAL PRIVATE NETWORK
Introduction
After a detailed investigation of the infrastructure of the organization and identification of
the needs of the network the report is prepared. The current needs of the organization is to
establish a VPN connection between remote sites of the same organization and securely
transmission of the data packets in the network. The success of the development of the network
depends on the successful implementation of the VPN. The VPN services that should be identified
that are needed by the organization and the scopes of the project should be defined for the
implementation of the new technology.
Scopes and Limitations
For the development of the VPN network the current network framework should be
identified and with the required number of hardware and software that are essential for the
development of the network. The network device should be configured according to the needs of
the organization and there should be used in future for the expansion of the current network. The
network should be connected with a wireless router such that the users with mobile devices can
connect with the wifi network for sending and receiving data packets in the network. A secure cloud
solution can be used for the storage of the data and allowing the access to the limited number of
users for the management of the information.
During the project development different barrier or constraint can rise that can affect the project
development such as the addition of extra cost during the progress of the project. The unavailability
of a hardware device and incompatibility of a device with the protocols and service required for the
configuration of the vpn network should be identified before the selection of the network hardware.
The skills and knowledge of the network engineer for configuration and troubleshooting the network
can also become a problem for the development of the network.
Requirements
For the analysis of the requirement the stakeholders must be involved and the service
required by them should be identified. The list of requirement for the development of the network
are listed below:
Quality of standards should be followed for the selection of the hardware device and
its installation in different parts of the network.
The traffic in the network should be sub divided by creating different vlan for each of
the department
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
VIRTUAL PRIVATE NETWORK
The access of the servers connected in the network should be restricted such that
the employees cannot physically access the data.
The server should be virtualized for the management of the load and fulfill the
request of the user without any delay.
Use of Ip addressing plan should be prepared according to the number of user for
each of the department and configuration of the access network device according to
the addressing plan.
A RADIUS server should be installed for the management of the authentication and
authorization of the user connected with then network.
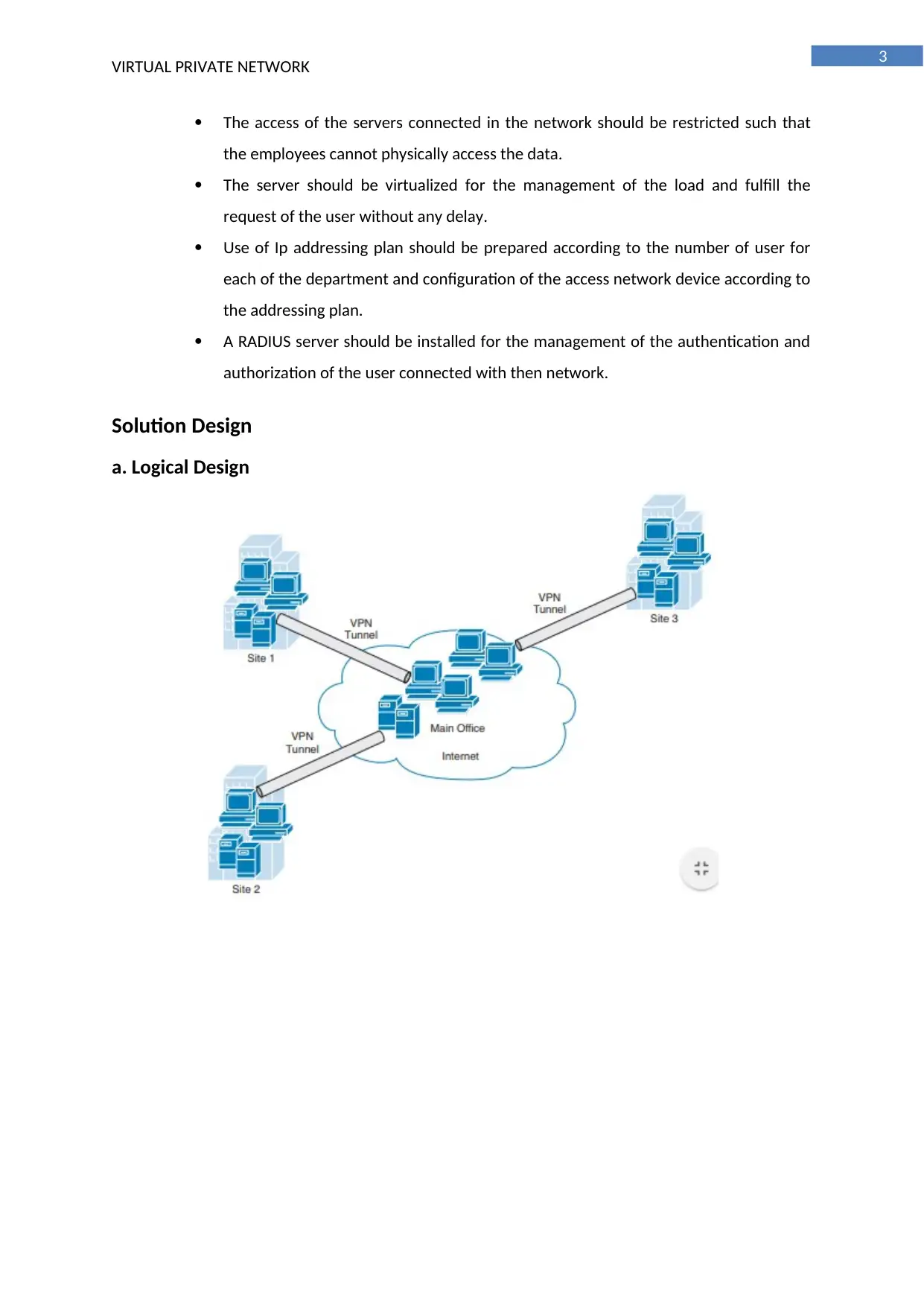
Solution Design
a. Logical Design
VIRTUAL PRIVATE NETWORK
The access of the servers connected in the network should be restricted such that
the employees cannot physically access the data.
The server should be virtualized for the management of the load and fulfill the
request of the user without any delay.
Use of Ip addressing plan should be prepared according to the number of user for
each of the department and configuration of the access network device according to
the addressing plan.
A RADIUS server should be installed for the management of the authentication and
authorization of the user connected with then network.
Solution Design
a. Logical Design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
VIRTUAL PRIVATE NETWORK
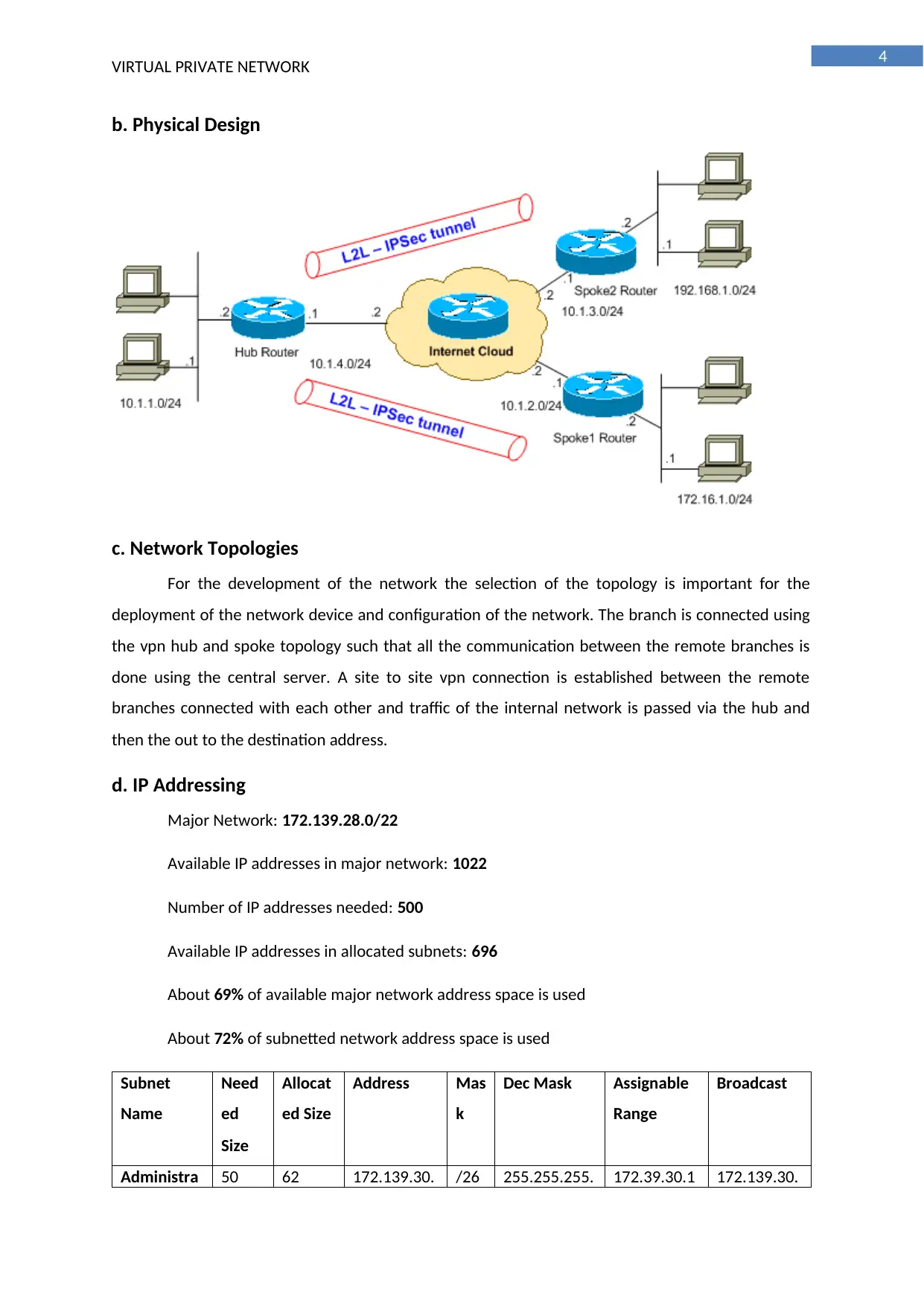
b. Physical Design
c. Network Topologies
For the development of the network the selection of the topology is important for the
deployment of the network device and configuration of the network. The branch is connected using
the vpn hub and spoke topology such that all the communication between the remote branches is
done using the central server. A site to site vpn connection is established between the remote
branches connected with each other and traffic of the internal network is passed via the hub and
then the out to the destination address.
d. IP Addressing
Major Network: 172.139.28.0/22
Available IP addresses in major network: 1022
Number of IP addresses needed: 500
Available IP addresses in allocated subnets: 696
About 69% of available major network address space is used
About 72% of subnetted network address space is used
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Administra 50 62 172.139.30. /26 255.255.255. 172.39.30.1 172.139.30.
VIRTUAL PRIVATE NETWORK
b. Physical Design
c. Network Topologies
For the development of the network the selection of the topology is important for the
deployment of the network device and configuration of the network. The branch is connected using
the vpn hub and spoke topology such that all the communication between the remote branches is
done using the central server. A site to site vpn connection is established between the remote
branches connected with each other and traffic of the internal network is passed via the hub and
then the out to the destination address.
d. IP Addressing
Major Network: 172.139.28.0/22
Available IP addresses in major network: 1022
Number of IP addresses needed: 500
Available IP addresses in allocated subnets: 696
About 69% of available major network address space is used
About 72% of subnetted network address space is used
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Administra 50 62 172.139.30. /26 255.255.255. 172.39.30.1 172.139.30.
5
VIRTUAL PRIVATE NETWORK
tive
network
128 192 29 -
172.39.30.1
90
191
Finance
Network
100 126 172.139.30.
0
/25 255.255.255.
128
172.39.30.1
-
172.39.30.1
26
172.139.30.
127
Sales
Network
200 254 172.139.28.
0
/24 255.255.255.
0
172.139.28.
1 -
172.139.28.
254
172.139.28.
255
Dispatch
Network
150 254 172.139.29.
0
/24 255.255.255.
0
172.139.29.
1 -
172.139.29.
254
172.39.29.2
55
e. Security features and policies
The application of the IPSec design between the routers can create an encrypted channel
with the spoke router. The A multi-layer security model is selected for the management of the
security of the network framework. The internal network is divided into different modules such that
a specific module can be provided with limited access. The use CHAP authentication and RADIUS
server help in maintaining the identity of the user.
f. Redundancy and failover plans
The fail over plan and the redundancy can be used for the creation of the back up link and
help in increasing the network uptime. The source can reach the destination via multiple path and if
one path is unavailable the other path is selected for successfully delivering the data packet.
g. VPN service implementation
For the implementation of the vpn service the router of the organization needs to be
configured with the ipsec policy and an encryption key should be used for the authentication of the
access of the remote user. For the implementation of the VPN service a research is done on
maintaining the confidentiality of data, tunneling, authentication, integration of data. The IPSEC,
PPP, MPPE protocols are used for the management of the authorization and encryption of the
channels to secure the network.
VIRTUAL PRIVATE NETWORK
tive
network
128 192 29 -
172.39.30.1
90
191
Finance
Network
100 126 172.139.30.
0
/25 255.255.255.
128
172.39.30.1
-
172.39.30.1
26
172.139.30.
127
Sales
Network
200 254 172.139.28.
0
/24 255.255.255.
0
172.139.28.
1 -
172.139.28.
254
172.139.28.
255
Dispatch
Network
150 254 172.139.29.
0
/24 255.255.255.
0
172.139.29.
1 -
172.139.29.
254
172.39.29.2
55
e. Security features and policies
The application of the IPSec design between the routers can create an encrypted channel
with the spoke router. The A multi-layer security model is selected for the management of the
security of the network framework. The internal network is divided into different modules such that
a specific module can be provided with limited access. The use CHAP authentication and RADIUS
server help in maintaining the identity of the user.
f. Redundancy and failover plans
The fail over plan and the redundancy can be used for the creation of the back up link and
help in increasing the network uptime. The source can reach the destination via multiple path and if
one path is unavailable the other path is selected for successfully delivering the data packet.
g. VPN service implementation
For the implementation of the vpn service the router of the organization needs to be
configured with the ipsec policy and an encryption key should be used for the authentication of the
access of the remote user. For the implementation of the VPN service a research is done on
maintaining the confidentiality of data, tunneling, authentication, integration of data. The IPSEC,
PPP, MPPE protocols are used for the management of the authorization and encryption of the
channels to secure the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
VIRTUAL PRIVATE NETWORK
VPN Network
For the development of the network the access of the security controls should be available
to the network administrator such that it is ensured that the data is sent and received using secure
communication tunnel. A proper authentication mechanism is followed for the authentication and
authorization of the users for creating a unique identification procedure. It is used for management
of the corporate resources and ensuring secure transmission of data.
Network Diagram for configuring IPsec Client VPN
Configuration of Crypto isakmp
VIRTUAL PRIVATE NETWORK
VPN Network
For the development of the network the access of the security controls should be available
to the network administrator such that it is ensured that the data is sent and received using secure
communication tunnel. A proper authentication mechanism is followed for the authentication and
authorization of the users for creating a unique identification procedure. It is used for management
of the corporate resources and ensuring secure transmission of data.
Network Diagram for configuring IPsec Client VPN
Configuration of Crypto isakmp
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
VIRTUAL PRIVATE NETWORK
DMZ Zone for file and Email Server
Installation of the Email and the file server in the DMZ zone improves the security and
reliability of the network and it creates a perimeter of the network where the internal resources are
secured from the external resources. The DMZ is configured such that an additional security layer is
imposed in the network and allows the network administrator to easily identify the breaches in the
network. The demilitarized zone is created for protecting the network from different types of
vulnerability and protect the network from the internal and the outside users.
Conclusion
It can be concluded that the requirement of a SME organization should be analyze for the
selection of the vpn service that would help the organization to meet their long term goals. It is
important to create an security policy for maintaining the access of the user to the different parts of
the network. For the establishment nt of the remote connection the VPN hub and spoke topology is
selected where a failover plan is also created for the management of the complexity of the network.
The network suitable for the small and medium sized organization should be identified for the
management of the current network capacity and management of the growth of the organization.
VIRTUAL PRIVATE NETWORK
DMZ Zone for file and Email Server
Installation of the Email and the file server in the DMZ zone improves the security and
reliability of the network and it creates a perimeter of the network where the internal resources are
secured from the external resources. The DMZ is configured such that an additional security layer is
imposed in the network and allows the network administrator to easily identify the breaches in the
network. The demilitarized zone is created for protecting the network from different types of
vulnerability and protect the network from the internal and the outside users.
Conclusion
It can be concluded that the requirement of a SME organization should be analyze for the
selection of the vpn service that would help the organization to meet their long term goals. It is
important to create an security policy for maintaining the access of the user to the different parts of
the network. For the establishment nt of the remote connection the VPN hub and spoke topology is
selected where a failover plan is also created for the management of the complexity of the network.
The network suitable for the small and medium sized organization should be identified for the
management of the current network capacity and management of the growth of the organization.

8
VIRTUAL PRIVATE NETWORK
Bibliography
[1]. R. Brewer, "Advanced persistent threats: minimising the damage", Network Security, vol.
2014, no. 4, pp. 5-9, 2014.
[2]. "IEEE/ACM Transactions on Networking society information", IEEE/ACM Transactions on
Networking, vol. 24, no. 5, pp. C3-C3, 2016.
[3]. D. Langenhan, VMware View Security Essentials. Packt Publishing, 2013.
[4]. "Optical Switching and Networking", Optical Switching and Networking, vol. 10, no. 4, pp.
463-464, 2013.
[5]. S. Subramaniam, M. Brandt-Pearce, P. Demeester and C. Vijaya Saradhi, Cross-Layer Design
in Optical Networks. Boston, MA: Springer US, 2013.
[6]. "Introduction to Information Security", Network Security, vol. 2013, no. 12, p. 4, 2013.
[7]. "The Practice of Network Security Monitoring", Network Security, vol. 2014, no. 10, p. 4,
2014.
[8]. J. Wang, "The Design of Improved Elman Network Intrusion Detection Algorithm in Digital
Campus Network", Advanced Materials Research, vol. 1049-1050, pp. 2096-2099, 2014.
[9]. S. Kermanshahi, Y. Shafahi and M. Bagherian, "Application of a new rapid transit network
design model to bus rapid transit network design: case study Isfahan metropolitan
area", Transport, vol. 30, no. 1, pp. 93-102, 2013.
[10]. E. Yadegari, M. Zandieh and H. Najmi, "A hybrid spanning tree-based
genetic/simulated annealing algorithm for a closed-loop logistics network design
problem", International Journal of Applied Decision Sciences, vol. 8, no. 4, p. 400, 2015.
[11]. F. Liu and W. Qu, "Design of Campus Network Database Access Based on
Encryption", Applied Mechanics and Materials, vol. 608-609, pp. 331-335, 2014.
VIRTUAL PRIVATE NETWORK
Bibliography
[1]. R. Brewer, "Advanced persistent threats: minimising the damage", Network Security, vol.
2014, no. 4, pp. 5-9, 2014.
[2]. "IEEE/ACM Transactions on Networking society information", IEEE/ACM Transactions on
Networking, vol. 24, no. 5, pp. C3-C3, 2016.
[3]. D. Langenhan, VMware View Security Essentials. Packt Publishing, 2013.
[4]. "Optical Switching and Networking", Optical Switching and Networking, vol. 10, no. 4, pp.
463-464, 2013.
[5]. S. Subramaniam, M. Brandt-Pearce, P. Demeester and C. Vijaya Saradhi, Cross-Layer Design
in Optical Networks. Boston, MA: Springer US, 2013.
[6]. "Introduction to Information Security", Network Security, vol. 2013, no. 12, p. 4, 2013.
[7]. "The Practice of Network Security Monitoring", Network Security, vol. 2014, no. 10, p. 4,
2014.
[8]. J. Wang, "The Design of Improved Elman Network Intrusion Detection Algorithm in Digital
Campus Network", Advanced Materials Research, vol. 1049-1050, pp. 2096-2099, 2014.
[9]. S. Kermanshahi, Y. Shafahi and M. Bagherian, "Application of a new rapid transit network
design model to bus rapid transit network design: case study Isfahan metropolitan
area", Transport, vol. 30, no. 1, pp. 93-102, 2013.
[10]. E. Yadegari, M. Zandieh and H. Najmi, "A hybrid spanning tree-based
genetic/simulated annealing algorithm for a closed-loop logistics network design
problem", International Journal of Applied Decision Sciences, vol. 8, no. 4, p. 400, 2015.
[11]. F. Liu and W. Qu, "Design of Campus Network Database Access Based on
Encryption", Applied Mechanics and Materials, vol. 608-609, pp. 331-335, 2014.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
VIRTUAL PRIVATE NETWORK
A. Hosapujari and A. Verma, "Development of a Hub and Spoke Model for Bus Transit
Route Network Design", Procedia - Social and Behavioral Sciences, vol. 104, pp. 835-
844, 2013.
[12]. "The Comprehensive Evaluation Research of Campus Network Security Based on the
Analytic Hierarchy Process (AHP)", INTERNATIONAL JOURNAL ON Advances in Information
Sciences and Service Sciences, vol. 5, no. 7, pp. 809-816, 2013.
VIRTUAL PRIVATE NETWORK
A. Hosapujari and A. Verma, "Development of a Hub and Spoke Model for Bus Transit
Route Network Design", Procedia - Social and Behavioral Sciences, vol. 104, pp. 835-
844, 2013.
[12]. "The Comprehensive Evaluation Research of Campus Network Security Based on the
Analytic Hierarchy Process (AHP)", INTERNATIONAL JOURNAL ON Advances in Information
Sciences and Service Sciences, vol. 5, no. 7, pp. 809-816, 2013.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





