Smith Security's Hybrid Cloud: Architecture, Security, and Continuity
VerifiedAdded on 2023/06/04
|23
|6238
|113
Report
AI Summary
This report explores cloud computing architectures suitable for Smith Security Ltd, which is considering migrating its IT infrastructure to a hybrid cloud environment. It details various architectures like Resource Pooling, Workload Distribution, and Dynamic Scalability, highlighting their benefits and issues. The report provides a risk assessment of hybrid cloud, focusing on DaaS, including mitigation strategies for risks like lack of encryption, inadequate security assessment, poor compliance, data redundancy, and failure to authenticate. Furthermore, it proposes information security controls, emphasizing strategic planning and self-awareness, and stresses the importance of a robust security business continuity plan. The report also touches on requirements for remote server administration, SLA management, and resource management for PaaS and IaaS.

Running head: CLOUD COMPUTING 1
Cloud Computing
Student Name
Institutional Affiliation
Cloud Computing
Student Name
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING 2
Introduction
In the recent years, cloud computing has gained popularity because of enabling on-
demand network access which is convenient, easily manageable, and share computer resources
that are provided for rapidly. From this description we can deduce five features of cloud
computing including wide network access, rapid elasticity, resource pooling, on-demand self-
service, and measured services (Gai, Qiu, Zhao, Tao & Zong, 2016). Adopting cloud computing
services has several benefits, however, there are barriers making it challenging to adopt. One
major setback associated with cloud computing is security and thus migrating sensitive data
and essential applications raises security concerns for the companies and businesses
considering cloud computing options. Since the emergence of cloud computing a lot of reviews
have been written but no systematic work has been published on cloud computing risk analysis
(Ghobaei-Arani, Jabbehdari & Pourmina, 2018). Cloud computing has facilitated organization to
host their servers remotely without having on-premise data centers.
Smith Security LTD have been relying on on-premise data centers distributed
independently in its various office branches. However, the company is considering to upgrade
their IT infrastructure and migrate to cloud computing. Smith Security is considering hybrid
cloud computing but would like to retain the data center in Sydney for sensitive data and
critical systems. They are considering this particular strategy as a way to enhance
responsiveness and flexibility of the business processes (Weinman, 2016). This report will focus
on the various cloud architecture that the company can employ, risks associated with hybrid
cloud computing, information security steps and control, security business continuity plan,
among other requirements required for the company to conduct remote server administration,
SLA management, and management of resources for its proposed PaaS and IaaS.
Proposed Architectures for a Hybrid Cloud
The following are some of the various cloud architectures that can be employed by
Smiths Security to their objectives:
Resource Pooling Architecture- In this particular architecture resources that are the
same are grouped together and controlled. It further ensures automation of synchronization
Introduction
In the recent years, cloud computing has gained popularity because of enabling on-
demand network access which is convenient, easily manageable, and share computer resources
that are provided for rapidly. From this description we can deduce five features of cloud
computing including wide network access, rapid elasticity, resource pooling, on-demand self-
service, and measured services (Gai, Qiu, Zhao, Tao & Zong, 2016). Adopting cloud computing
services has several benefits, however, there are barriers making it challenging to adopt. One
major setback associated with cloud computing is security and thus migrating sensitive data
and essential applications raises security concerns for the companies and businesses
considering cloud computing options. Since the emergence of cloud computing a lot of reviews
have been written but no systematic work has been published on cloud computing risk analysis
(Ghobaei-Arani, Jabbehdari & Pourmina, 2018). Cloud computing has facilitated organization to
host their servers remotely without having on-premise data centers.
Smith Security LTD have been relying on on-premise data centers distributed
independently in its various office branches. However, the company is considering to upgrade
their IT infrastructure and migrate to cloud computing. Smith Security is considering hybrid
cloud computing but would like to retain the data center in Sydney for sensitive data and
critical systems. They are considering this particular strategy as a way to enhance
responsiveness and flexibility of the business processes (Weinman, 2016). This report will focus
on the various cloud architecture that the company can employ, risks associated with hybrid
cloud computing, information security steps and control, security business continuity plan,
among other requirements required for the company to conduct remote server administration,
SLA management, and management of resources for its proposed PaaS and IaaS.
Proposed Architectures for a Hybrid Cloud
The following are some of the various cloud architectures that can be employed by
Smiths Security to their objectives:
Resource Pooling Architecture- In this particular architecture resources that are the
same are grouped together and controlled. It further ensures automation of synchronization

CLOUD COMPUTING 3
process. During the runtime several monitors of the cloud usage are included to help in
synchronizing and tracking the needed elements to be used by the pooled IT resources (Choi,
Choi & Kim, 2013). The reason for using this architecture is because it allows the cloud
providers to develop a sense of immediate or infinite resource availability by controlling
adjustments of resources at meta level. This enables Smiths Security to adjust service levels at
will without being limited by virtual or physical resources.
Workload Distribution Architecture- This architecture ensures that the IT resources are
not overused and that there is a balance on their utilization. This architecture depends on load-
balancing algorithms and runtime logics capabilities. The key feature in this architecture is the
inclusion of cloud usage monitor to track runtime workload. Additionally, it is useful for
information processing (Al-Rashedi, 2017). The reason for proposing this architecture for
Smiths Security is to minimize under-utilization and over-utilization of IT resources to a level
which depends on the sophistication of runtime logic and load balancing algorithms. This will
greatly benefit the company by ensuring optimum resource utilization.
Dynamic Scalability Architecture- This architecture lies of scaling systems that are
predefined and triggers resource allocations automatically (Cheng & Qu, 2014). This is achieved
through resource pools because of the dynamic fluctuations associated with this model. This
architecture will best work for Smiths Security because it enables dynamic allocation of
resources depending on the usage demand fluctuations resulting in efficient and effective IT
resource reclamation without the need of interacting with them manually (Sood, 2013).
Issues and Benefits of Implementing the Architectures
Scalability- the architecture supports elasticity and flexibility and facilitates growth of
the network (Chen, Zhang, Hu, Taleb & Sheng, 2015). Additionally, it enables the IT
management team to move applications from private cloud to public cloud for the purpose of
application testing.
Cost- there company will not have to but any hardware infrastructure resources
because they cloud providers handles the IT infrastructure. The capability of the architectures
to dynamically monitor and adjust usage capacity utilized in the cloud environment ensure cost-
process. During the runtime several monitors of the cloud usage are included to help in
synchronizing and tracking the needed elements to be used by the pooled IT resources (Choi,
Choi & Kim, 2013). The reason for using this architecture is because it allows the cloud
providers to develop a sense of immediate or infinite resource availability by controlling
adjustments of resources at meta level. This enables Smiths Security to adjust service levels at
will without being limited by virtual or physical resources.
Workload Distribution Architecture- This architecture ensures that the IT resources are
not overused and that there is a balance on their utilization. This architecture depends on load-
balancing algorithms and runtime logics capabilities. The key feature in this architecture is the
inclusion of cloud usage monitor to track runtime workload. Additionally, it is useful for
information processing (Al-Rashedi, 2017). The reason for proposing this architecture for
Smiths Security is to minimize under-utilization and over-utilization of IT resources to a level
which depends on the sophistication of runtime logic and load balancing algorithms. This will
greatly benefit the company by ensuring optimum resource utilization.
Dynamic Scalability Architecture- This architecture lies of scaling systems that are
predefined and triggers resource allocations automatically (Cheng & Qu, 2014). This is achieved
through resource pools because of the dynamic fluctuations associated with this model. This
architecture will best work for Smiths Security because it enables dynamic allocation of
resources depending on the usage demand fluctuations resulting in efficient and effective IT
resource reclamation without the need of interacting with them manually (Sood, 2013).
Issues and Benefits of Implementing the Architectures
Scalability- the architecture supports elasticity and flexibility and facilitates growth of
the network (Chen, Zhang, Hu, Taleb & Sheng, 2015). Additionally, it enables the IT
management team to move applications from private cloud to public cloud for the purpose of
application testing.
Cost- there company will not have to but any hardware infrastructure resources
because they cloud providers handles the IT infrastructure. The capability of the architectures
to dynamically monitor and adjust usage capacity utilized in the cloud environment ensure cost-
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CLOUD COMPUTING 4
effectiveness (Linthicum, 2016). Several cloud providers offer their customers pay-per-use
strategy enhancing more cost effectiveness.
Agility- when the business requires heavy application usage they can quickly get more
resources from the public cloud and transfer some tasks to the public systems leading to better
performance, less downtime, and reduced outages. The architecture further offers quick,
secure, and easy access of the SQL databases and analytical requirements to help the business
identify new trends and opportunities (Linthicum, 2016).
Risk report for Hybrid Cloud DaaS
Most critics have argued that hybrid cloud computing is disruptive but it actually is not
because the problem is entirely dependent on the security protocol and controls, poor network
management and execution. The major challenges to hybrid cloud computing are insufficient
risk assessment, data leakage, inadequate compliance, data redundancy, and lack of
encryption. However, this section will discuss the various risks associated with hybrid cloud
computing with focus of DaaS and the physical monitoring center. The table below describes
the various risks and mitigation strategies.
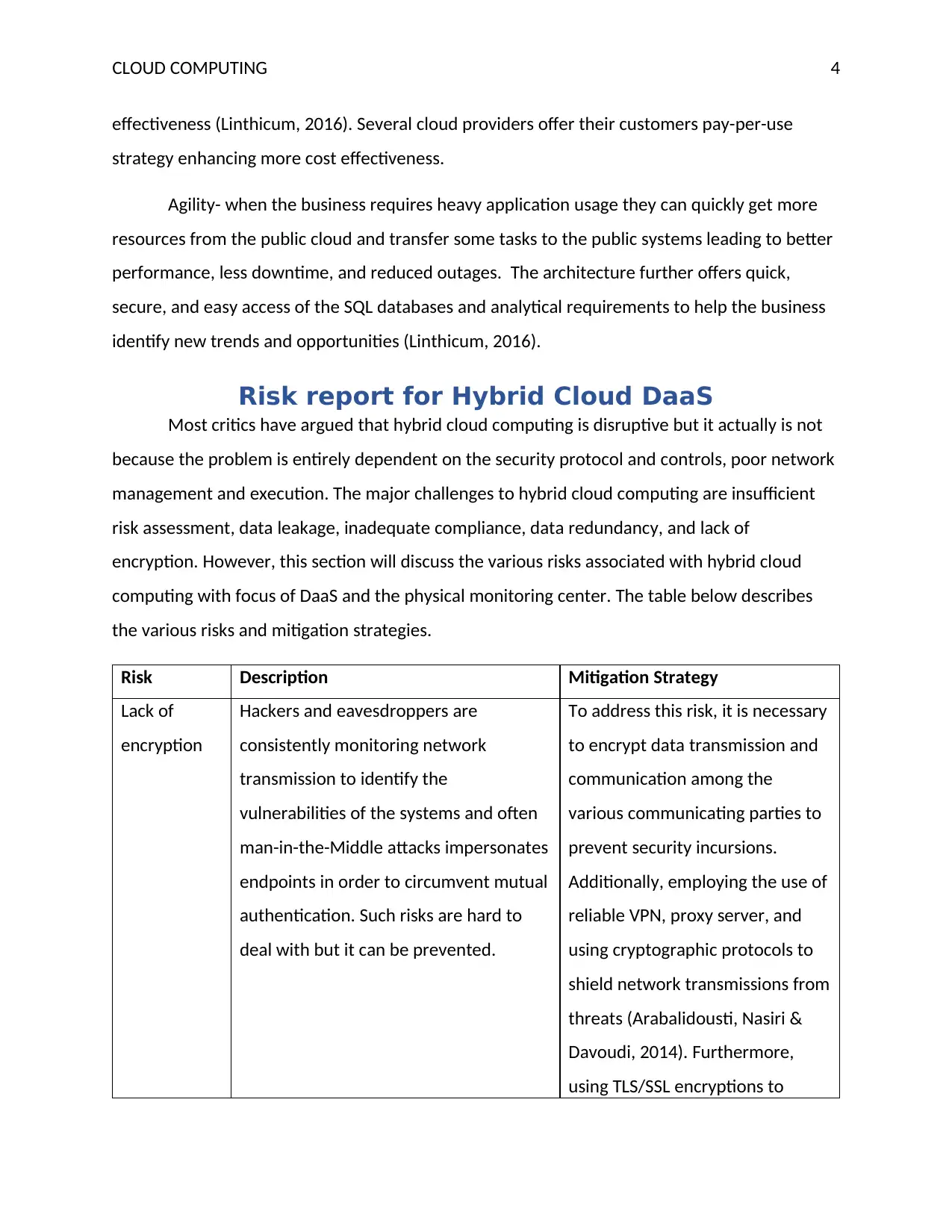
Risk Description Mitigation Strategy
Lack of
encryption
Hackers and eavesdroppers are
consistently monitoring network
transmission to identify the
vulnerabilities of the systems and often
man-in-the-Middle attacks impersonates
endpoints in order to circumvent mutual
authentication. Such risks are hard to
deal with but it can be prevented.
To address this risk, it is necessary
to encrypt data transmission and
communication among the
various communicating parties to
prevent security incursions.
Additionally, employing the use of
reliable VPN, proxy server, and
using cryptographic protocols to
shield network transmissions from
threats (Arabalidousti, Nasiri &
Davoudi, 2014). Furthermore,
using TLS/SSL encryptions to
effectiveness (Linthicum, 2016). Several cloud providers offer their customers pay-per-use
strategy enhancing more cost effectiveness.
Agility- when the business requires heavy application usage they can quickly get more
resources from the public cloud and transfer some tasks to the public systems leading to better
performance, less downtime, and reduced outages. The architecture further offers quick,
secure, and easy access of the SQL databases and analytical requirements to help the business
identify new trends and opportunities (Linthicum, 2016).
Risk report for Hybrid Cloud DaaS
Most critics have argued that hybrid cloud computing is disruptive but it actually is not
because the problem is entirely dependent on the security protocol and controls, poor network
management and execution. The major challenges to hybrid cloud computing are insufficient
risk assessment, data leakage, inadequate compliance, data redundancy, and lack of
encryption. However, this section will discuss the various risks associated with hybrid cloud
computing with focus of DaaS and the physical monitoring center. The table below describes
the various risks and mitigation strategies.
Risk Description Mitigation Strategy
Lack of
encryption
Hackers and eavesdroppers are
consistently monitoring network
transmission to identify the
vulnerabilities of the systems and often
man-in-the-Middle attacks impersonates
endpoints in order to circumvent mutual
authentication. Such risks are hard to
deal with but it can be prevented.
To address this risk, it is necessary
to encrypt data transmission and
communication among the
various communicating parties to
prevent security incursions.
Additionally, employing the use of
reliable VPN, proxy server, and
using cryptographic protocols to
shield network transmissions from
threats (Arabalidousti, Nasiri &
Davoudi, 2014). Furthermore,
using TLS/SSL encryptions to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CLOUD COMPUTING 5
prevent data interception and
server authentication can further
prevent this risk.
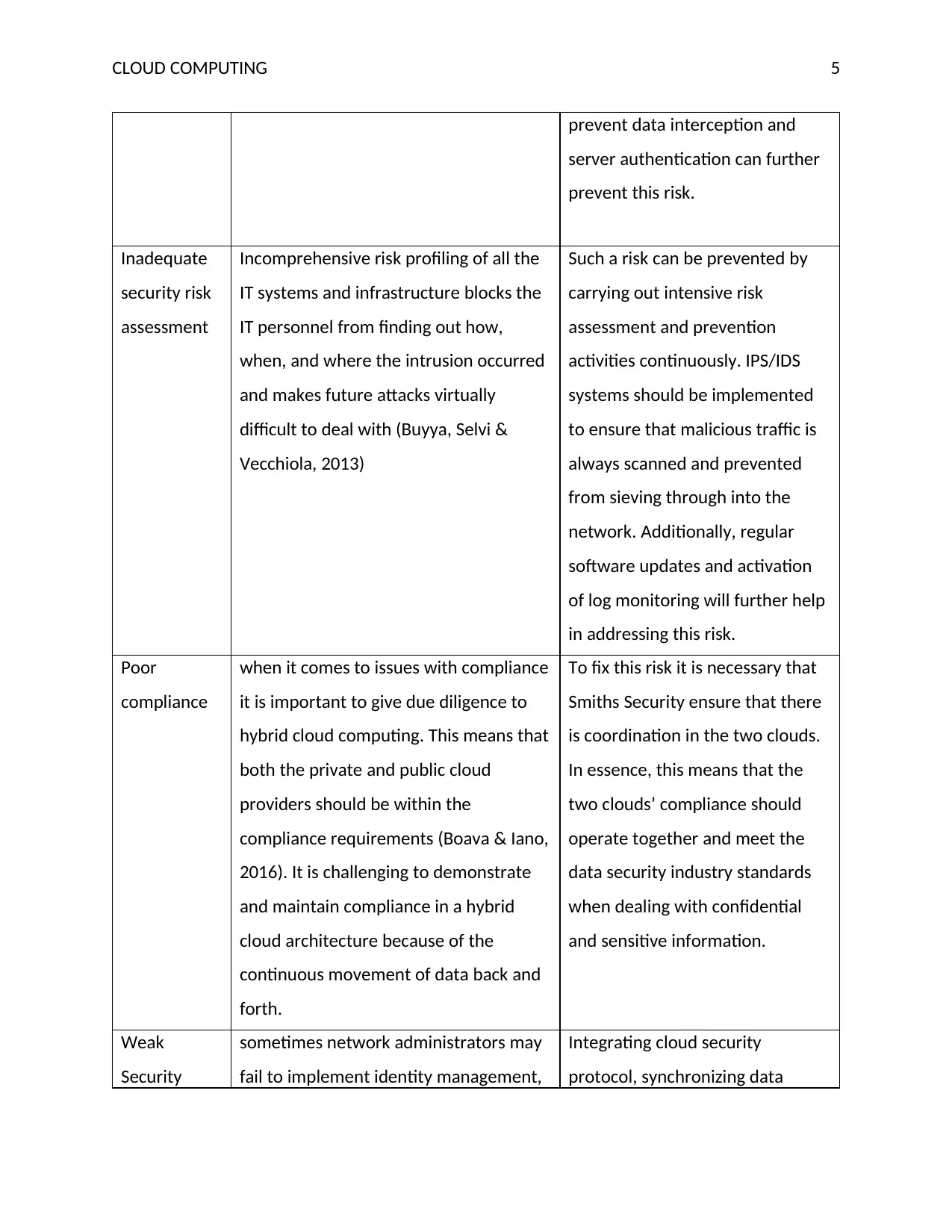
Inadequate
security risk
assessment
Incomprehensive risk profiling of all the
IT systems and infrastructure blocks the
IT personnel from finding out how,
when, and where the intrusion occurred
and makes future attacks virtually
difficult to deal with (Buyya, Selvi &
Vecchiola, 2013)
Such a risk can be prevented by
carrying out intensive risk
assessment and prevention
activities continuously. IPS/IDS
systems should be implemented
to ensure that malicious traffic is
always scanned and prevented
from sieving through into the
network. Additionally, regular
software updates and activation
of log monitoring will further help
in addressing this risk.
Poor
compliance
when it comes to issues with compliance
it is important to give due diligence to
hybrid cloud computing. This means that
both the private and public cloud
providers should be within the
compliance requirements (Boava & Iano,
2016). It is challenging to demonstrate
and maintain compliance in a hybrid
cloud architecture because of the
continuous movement of data back and
forth.
To fix this risk it is necessary that
Smiths Security ensure that there
is coordination in the two clouds.
In essence, this means that the
two clouds’ compliance should
operate together and meet the
data security industry standards
when dealing with confidential
and sensitive information.
Weak
Security
sometimes network administrators may
fail to implement identity management,
Integrating cloud security
protocol, synchronizing data
prevent data interception and
server authentication can further
prevent this risk.
Inadequate
security risk
assessment
Incomprehensive risk profiling of all the
IT systems and infrastructure blocks the
IT personnel from finding out how,
when, and where the intrusion occurred
and makes future attacks virtually
difficult to deal with (Buyya, Selvi &
Vecchiola, 2013)
Such a risk can be prevented by
carrying out intensive risk
assessment and prevention
activities continuously. IPS/IDS
systems should be implemented
to ensure that malicious traffic is
always scanned and prevented
from sieving through into the
network. Additionally, regular
software updates and activation
of log monitoring will further help
in addressing this risk.
Poor
compliance
when it comes to issues with compliance
it is important to give due diligence to
hybrid cloud computing. This means that
both the private and public cloud
providers should be within the
compliance requirements (Boava & Iano,
2016). It is challenging to demonstrate
and maintain compliance in a hybrid
cloud architecture because of the
continuous movement of data back and
forth.
To fix this risk it is necessary that
Smiths Security ensure that there
is coordination in the two clouds.
In essence, this means that the
two clouds’ compliance should
operate together and meet the
data security industry standards
when dealing with confidential
and sensitive information.
Weak
Security
sometimes network administrators may
fail to implement identity management,
Integrating cloud security
protocol, synchronizing data
CLOUD COMPUTING 6
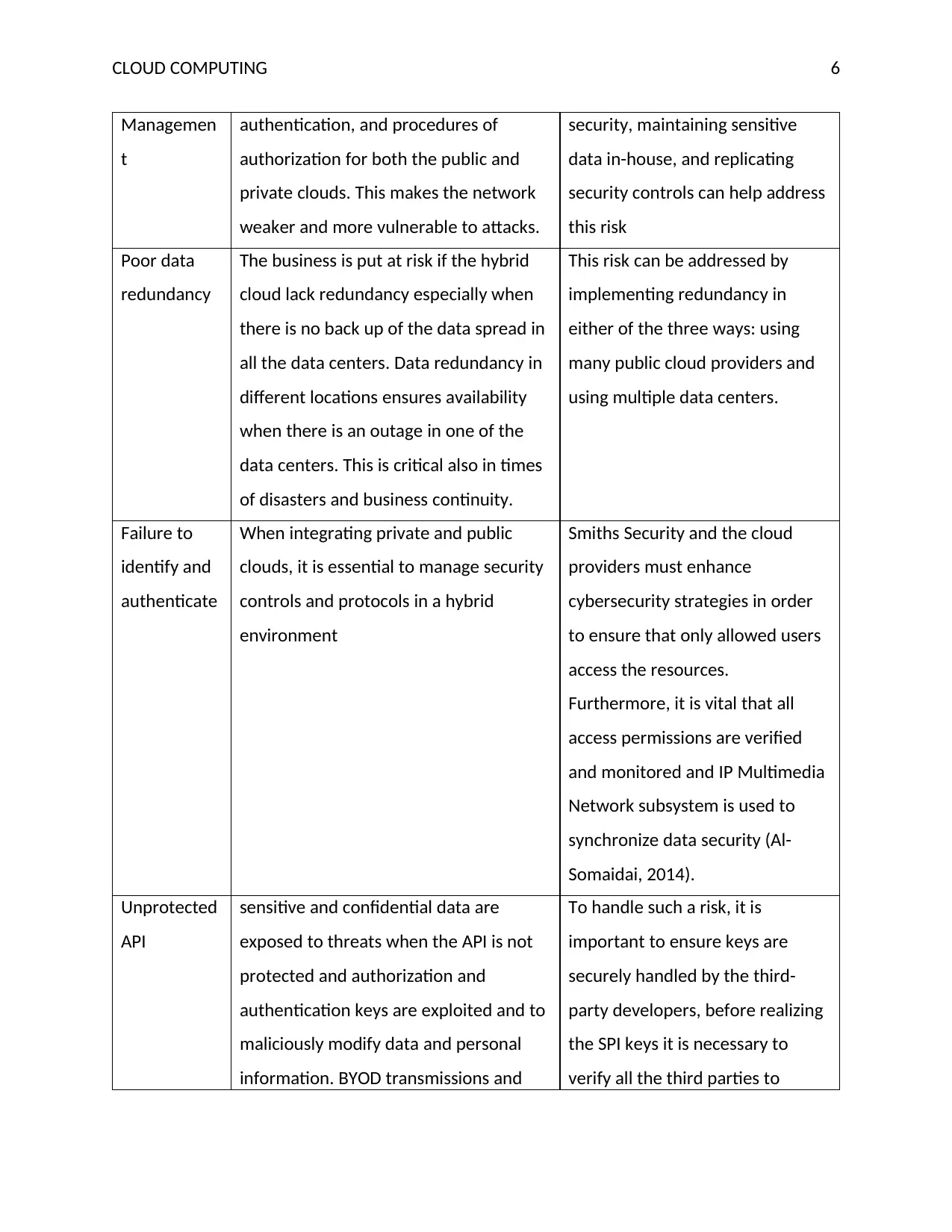
Managemen
t
authentication, and procedures of
authorization for both the public and
private clouds. This makes the network
weaker and more vulnerable to attacks.
security, maintaining sensitive
data in-house, and replicating
security controls can help address
this risk
Poor data
redundancy
The business is put at risk if the hybrid
cloud lack redundancy especially when
there is no back up of the data spread in
all the data centers. Data redundancy in
different locations ensures availability
when there is an outage in one of the
data centers. This is critical also in times
of disasters and business continuity.
This risk can be addressed by
implementing redundancy in
either of the three ways: using
many public cloud providers and
using multiple data centers.
Failure to
identify and
authenticate
When integrating private and public
clouds, it is essential to manage security
controls and protocols in a hybrid
environment
Smiths Security and the cloud
providers must enhance
cybersecurity strategies in order
to ensure that only allowed users
access the resources.
Furthermore, it is vital that all
access permissions are verified
and monitored and IP Multimedia
Network subsystem is used to
synchronize data security (Al-
Somaidai, 2014).
Unprotected
API
sensitive and confidential data are
exposed to threats when the API is not
protected and authorization and
authentication keys are exploited and to
maliciously modify data and personal
information. BYOD transmissions and
To handle such a risk, it is
important to ensure keys are
securely handled by the third-
party developers, before realizing
the SPI keys it is necessary to
verify all the third parties to
Managemen
t
authentication, and procedures of
authorization for both the public and
private clouds. This makes the network
weaker and more vulnerable to attacks.
security, maintaining sensitive
data in-house, and replicating
security controls can help address
this risk
Poor data
redundancy
The business is put at risk if the hybrid
cloud lack redundancy especially when
there is no back up of the data spread in
all the data centers. Data redundancy in
different locations ensures availability
when there is an outage in one of the
data centers. This is critical also in times
of disasters and business continuity.
This risk can be addressed by
implementing redundancy in
either of the three ways: using
many public cloud providers and
using multiple data centers.
Failure to
identify and
authenticate
When integrating private and public
clouds, it is essential to manage security
controls and protocols in a hybrid
environment
Smiths Security and the cloud
providers must enhance
cybersecurity strategies in order
to ensure that only allowed users
access the resources.
Furthermore, it is vital that all
access permissions are verified
and monitored and IP Multimedia
Network subsystem is used to
synchronize data security (Al-
Somaidai, 2014).
Unprotected
API
sensitive and confidential data are
exposed to threats when the API is not
protected and authorization and
authentication keys are exploited and to
maliciously modify data and personal
information. BYOD transmissions and
To handle such a risk, it is
important to ensure keys are
securely handled by the third-
party developers, before realizing
the SPI keys it is necessary to
verify all the third parties to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
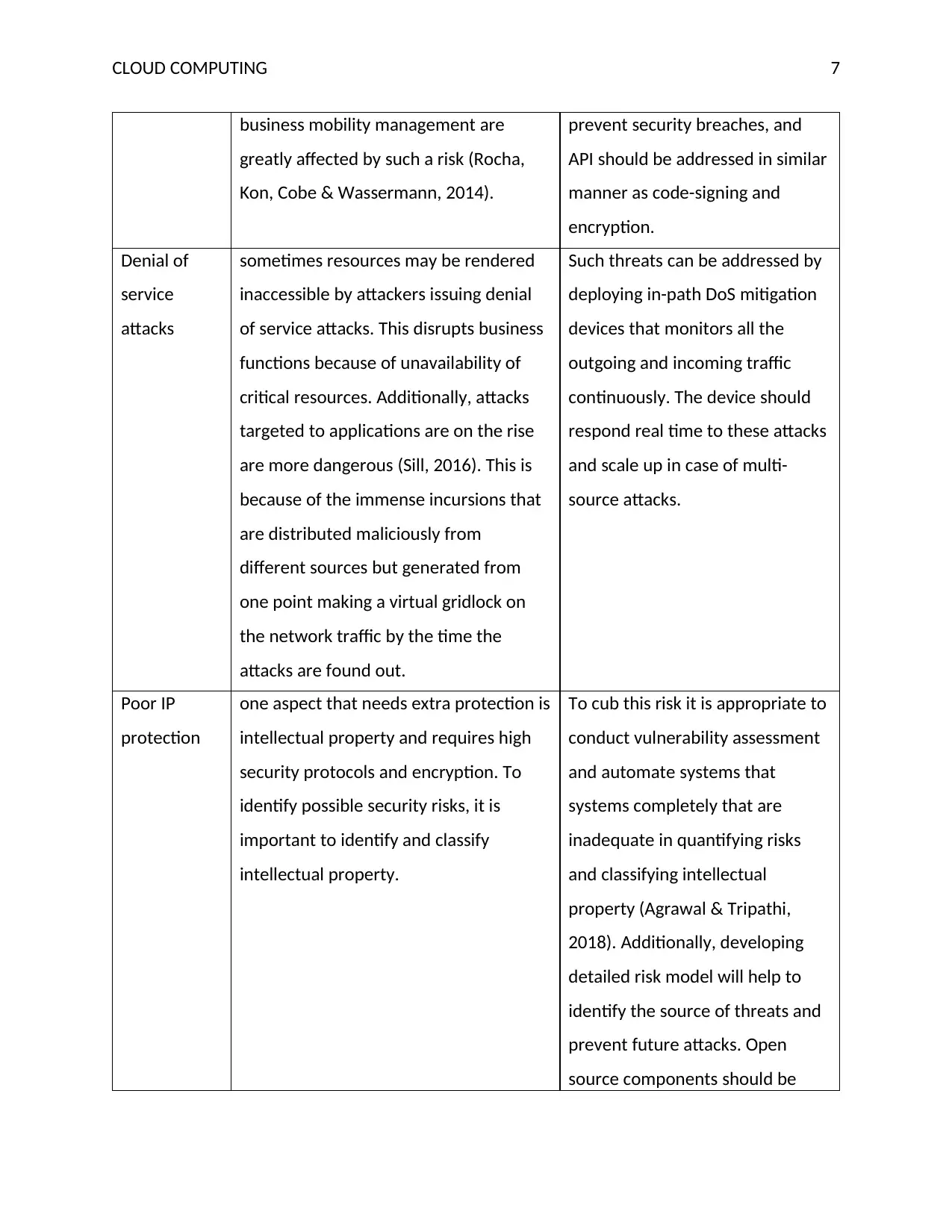
CLOUD COMPUTING 7
business mobility management are
greatly affected by such a risk (Rocha,
Kon, Cobe & Wassermann, 2014).
prevent security breaches, and
API should be addressed in similar
manner as code-signing and
encryption.
Denial of
service
attacks
sometimes resources may be rendered
inaccessible by attackers issuing denial
of service attacks. This disrupts business
functions because of unavailability of
critical resources. Additionally, attacks
targeted to applications are on the rise
are more dangerous (Sill, 2016). This is
because of the immense incursions that
are distributed maliciously from
different sources but generated from
one point making a virtual gridlock on
the network traffic by the time the
attacks are found out.
Such threats can be addressed by
deploying in-path DoS mitigation
devices that monitors all the
outgoing and incoming traffic
continuously. The device should
respond real time to these attacks
and scale up in case of multi-
source attacks.
Poor IP
protection
one aspect that needs extra protection is
intellectual property and requires high
security protocols and encryption. To
identify possible security risks, it is
important to identify and classify
intellectual property.
To cub this risk it is appropriate to
conduct vulnerability assessment
and automate systems that
systems completely that are
inadequate in quantifying risks
and classifying intellectual
property (Agrawal & Tripathi,
2018). Additionally, developing
detailed risk model will help to
identify the source of threats and
prevent future attacks. Open
source components should be
business mobility management are
greatly affected by such a risk (Rocha,
Kon, Cobe & Wassermann, 2014).
prevent security breaches, and
API should be addressed in similar
manner as code-signing and
encryption.
Denial of
service
attacks
sometimes resources may be rendered
inaccessible by attackers issuing denial
of service attacks. This disrupts business
functions because of unavailability of
critical resources. Additionally, attacks
targeted to applications are on the rise
are more dangerous (Sill, 2016). This is
because of the immense incursions that
are distributed maliciously from
different sources but generated from
one point making a virtual gridlock on
the network traffic by the time the
attacks are found out.
Such threats can be addressed by
deploying in-path DoS mitigation
devices that monitors all the
outgoing and incoming traffic
continuously. The device should
respond real time to these attacks
and scale up in case of multi-
source attacks.
Poor IP
protection
one aspect that needs extra protection is
intellectual property and requires high
security protocols and encryption. To
identify possible security risks, it is
important to identify and classify
intellectual property.
To cub this risk it is appropriate to
conduct vulnerability assessment
and automate systems that
systems completely that are
inadequate in quantifying risks
and classifying intellectual
property (Agrawal & Tripathi,
2018). Additionally, developing
detailed risk model will help to
identify the source of threats and
prevent future attacks. Open
source components should be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CLOUD COMPUTING 8
hardened and develop permission
matrix to prevent incursions.
Lack of data
ownership
Before choosing a particular cloud
vendor it is important to vet cloud
providers fully for security controls when
dealing with data (Wang, 2015). The
business will lose the some right to
manage its own data once it has been
deployed to the cloud.
business managers should be
aware of the levels of security
provided by the cloud to avoid
surprises. Moreover, verification
of data security and ownership is
required to prevent providers who
cannot offer agreed ownership
rights. Finally, should provide a
well-structured, defined, and
inclusive service level agreement
will cover the business while using
hybrid cloud.
Proposed Information Security controls
Smiths Security are expecting to get the best out of the hybrid cloud. However, it is
important to take some few precautionary information security steps and controls. With the
increasing use and adoption of hybrid cloud environment, it will be essential for businesses and
organizations to take effective security measures to secure sensitive and confidential data at all
times in order to minimize threats and attacks. It is quite a challenge to secure the hybrid cloud
but with proper strategies, and effective security plan can be developed. The following are
some of the steps that the Smiths Security Board can employ in order to secure the hybrid
cloud:
Develop a strategic plan- it is essential to come up with a comprehensive data security
plan before migrating the data. The business ca be able to avoid worst case scenarios by doing
so and also it would be of help when faced with future threats. Identify the services and
resources that you need from the cloud provider and have an in-depth understanding of how
the cloud provider will secure such resources and data.
hardened and develop permission
matrix to prevent incursions.
Lack of data
ownership
Before choosing a particular cloud
vendor it is important to vet cloud
providers fully for security controls when
dealing with data (Wang, 2015). The
business will lose the some right to
manage its own data once it has been
deployed to the cloud.
business managers should be
aware of the levels of security
provided by the cloud to avoid
surprises. Moreover, verification
of data security and ownership is
required to prevent providers who
cannot offer agreed ownership
rights. Finally, should provide a
well-structured, defined, and
inclusive service level agreement
will cover the business while using
hybrid cloud.
Proposed Information Security controls
Smiths Security are expecting to get the best out of the hybrid cloud. However, it is
important to take some few precautionary information security steps and controls. With the
increasing use and adoption of hybrid cloud environment, it will be essential for businesses and
organizations to take effective security measures to secure sensitive and confidential data at all
times in order to minimize threats and attacks. It is quite a challenge to secure the hybrid cloud
but with proper strategies, and effective security plan can be developed. The following are
some of the steps that the Smiths Security Board can employ in order to secure the hybrid
cloud:
Develop a strategic plan- it is essential to come up with a comprehensive data security
plan before migrating the data. The business ca be able to avoid worst case scenarios by doing
so and also it would be of help when faced with future threats. Identify the services and
resources that you need from the cloud provider and have an in-depth understanding of how
the cloud provider will secure such resources and data.

CLOUD COMPUTING 9
Be Self-aware- one major security measures that the company can take is by knowing
the environment of operation by having insights of the measures that the cloud provider has in
place to mitigate risks, incident reporting, and plans for data backup and recovery (Gordon,
2016). Additionally, it is essential to know the type of applications and data that you are moving
to the cloud and making sure that the platform you are choosing is convenient and suitable for
all aspects.
Know your environment- understanding the kind of space you operate in is also crucial
because you will be able to easily identify the breaches and threats associated with such space
and if they have occurred in your industry. Have the knowledge of how such data was
compromised so as to avoid making similar mistakes.
Do not depend on industry standards alone- many businesses have been compromised
because of relying on the fact that the cloud vendor complies with all the industry standards.
This alone is not enough to ensure effective data security because some of these standards
have become obsolete because of the fast-evolving technological trends around the world (Jula,
Sundararajan & Othman, 2014). It is important to continuously monitor the compliance
standards.
Embrace Transparency- Smiths should ensure that the cloud provider keep them open
and upfront on the emerging threats and risks facing the industry. It is necessary to know that
your data is secured, emerging risks and threats and the mitigation strategies being taken to
mitigate such threats and risks.
Be one step ahead- both the cloud provider’s and your security tools should be
continuous to determine any changes or weaknesses providing real-time look of how the
business data is secured in the cloud (Hwang, Dongarra & Fox, 2013). Continuously identify
weak points and security vulnerabilities and take necessary measures before attackers make
use of them.
Prioritize management of risks- any cloud platform has vulnerabilities and risks
associated with them. As such, it is necessary to always give it a priority and identify the
vulnerabilities that brings the biggest risk and mitigate them first. You don’t have to fix
Be Self-aware- one major security measures that the company can take is by knowing
the environment of operation by having insights of the measures that the cloud provider has in
place to mitigate risks, incident reporting, and plans for data backup and recovery (Gordon,
2016). Additionally, it is essential to know the type of applications and data that you are moving
to the cloud and making sure that the platform you are choosing is convenient and suitable for
all aspects.
Know your environment- understanding the kind of space you operate in is also crucial
because you will be able to easily identify the breaches and threats associated with such space
and if they have occurred in your industry. Have the knowledge of how such data was
compromised so as to avoid making similar mistakes.
Do not depend on industry standards alone- many businesses have been compromised
because of relying on the fact that the cloud vendor complies with all the industry standards.
This alone is not enough to ensure effective data security because some of these standards
have become obsolete because of the fast-evolving technological trends around the world (Jula,
Sundararajan & Othman, 2014). It is important to continuously monitor the compliance
standards.
Embrace Transparency- Smiths should ensure that the cloud provider keep them open
and upfront on the emerging threats and risks facing the industry. It is necessary to know that
your data is secured, emerging risks and threats and the mitigation strategies being taken to
mitigate such threats and risks.
Be one step ahead- both the cloud provider’s and your security tools should be
continuous to determine any changes or weaknesses providing real-time look of how the
business data is secured in the cloud (Hwang, Dongarra & Fox, 2013). Continuously identify
weak points and security vulnerabilities and take necessary measures before attackers make
use of them.
Prioritize management of risks- any cloud platform has vulnerabilities and risks
associated with them. As such, it is necessary to always give it a priority and identify the
vulnerabilities that brings the biggest risk and mitigate them first. You don’t have to fix
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CLOUD COMPUTING 10
everything at the same time. Implement tools that will continuously assess the cloud resources
for any potential risks.
BCP Changes
With the exciting advancement in the information sector and the increasing number of
businesses globally, a massive business data has been considered as the key for the global
business connections, as such protecting data gets to be specifically important. Smiths Security
would like to improve their opportunity of recovering data loss and system failures, specifically
to protect themselves from man-made and natural disasters. Smiths Security relies on the
existence of the internet. Continuity is an essential element to the company, as unpredicted
service interference can, without doubt, affect company goals resulting to significant losses
with regards to business status, income and losses connected to the market share. As an
outlook in Smiths Security, data has a huge measure of interest from both mechanical and
scholastic views. As data grows, making sure that it is securely and safely set aside is
challenging.
In Smiths Security there are a substantial amount of information in digital format that
need safe storage services. Business continuity and data backup matters have become
important in networks as the need and the benefit for electronic information is frequently
increasing (Sohal, 2013). Smiths Security needs a DRP (disaster recovery plan) or BCP (business
continuity plan) and data backup that comes within cost restraints, at the same time getting the
goal recovery requirements with regards to RPO (recovery point objective) and RTO (recovery
time objective). The levels of data recovery are categorized through RPO and RTO which are the
underlying goals that should be met anytime while analyzing an excellent choice in a specific
capital and operating costs. Besides, RPO report the data that a company might afford to lose.
The total cost of maintaining the actual recover infrastructure environment is high when the
RPO is low.
DRP (disaster recovery planning) is connected with the recovery of major set of
infrastructure elements and IT systems, while the BCP is connected to business as a complete
part managing the processes of business. The ICT role in disaster management is increasing
everything at the same time. Implement tools that will continuously assess the cloud resources
for any potential risks.
BCP Changes
With the exciting advancement in the information sector and the increasing number of
businesses globally, a massive business data has been considered as the key for the global
business connections, as such protecting data gets to be specifically important. Smiths Security
would like to improve their opportunity of recovering data loss and system failures, specifically
to protect themselves from man-made and natural disasters. Smiths Security relies on the
existence of the internet. Continuity is an essential element to the company, as unpredicted
service interference can, without doubt, affect company goals resulting to significant losses
with regards to business status, income and losses connected to the market share. As an
outlook in Smiths Security, data has a huge measure of interest from both mechanical and
scholastic views. As data grows, making sure that it is securely and safely set aside is
challenging.
In Smiths Security there are a substantial amount of information in digital format that
need safe storage services. Business continuity and data backup matters have become
important in networks as the need and the benefit for electronic information is frequently
increasing (Sohal, 2013). Smiths Security needs a DRP (disaster recovery plan) or BCP (business
continuity plan) and data backup that comes within cost restraints, at the same time getting the
goal recovery requirements with regards to RPO (recovery point objective) and RTO (recovery
time objective). The levels of data recovery are categorized through RPO and RTO which are the
underlying goals that should be met anytime while analyzing an excellent choice in a specific
capital and operating costs. Besides, RPO report the data that a company might afford to lose.
The total cost of maintaining the actual recover infrastructure environment is high when the
RPO is low.
DRP (disaster recovery planning) is connected with the recovery of major set of
infrastructure elements and IT systems, while the BCP is connected to business as a complete
part managing the processes of business. The ICT role in disaster management is increasing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CLOUD COMPUTING 11
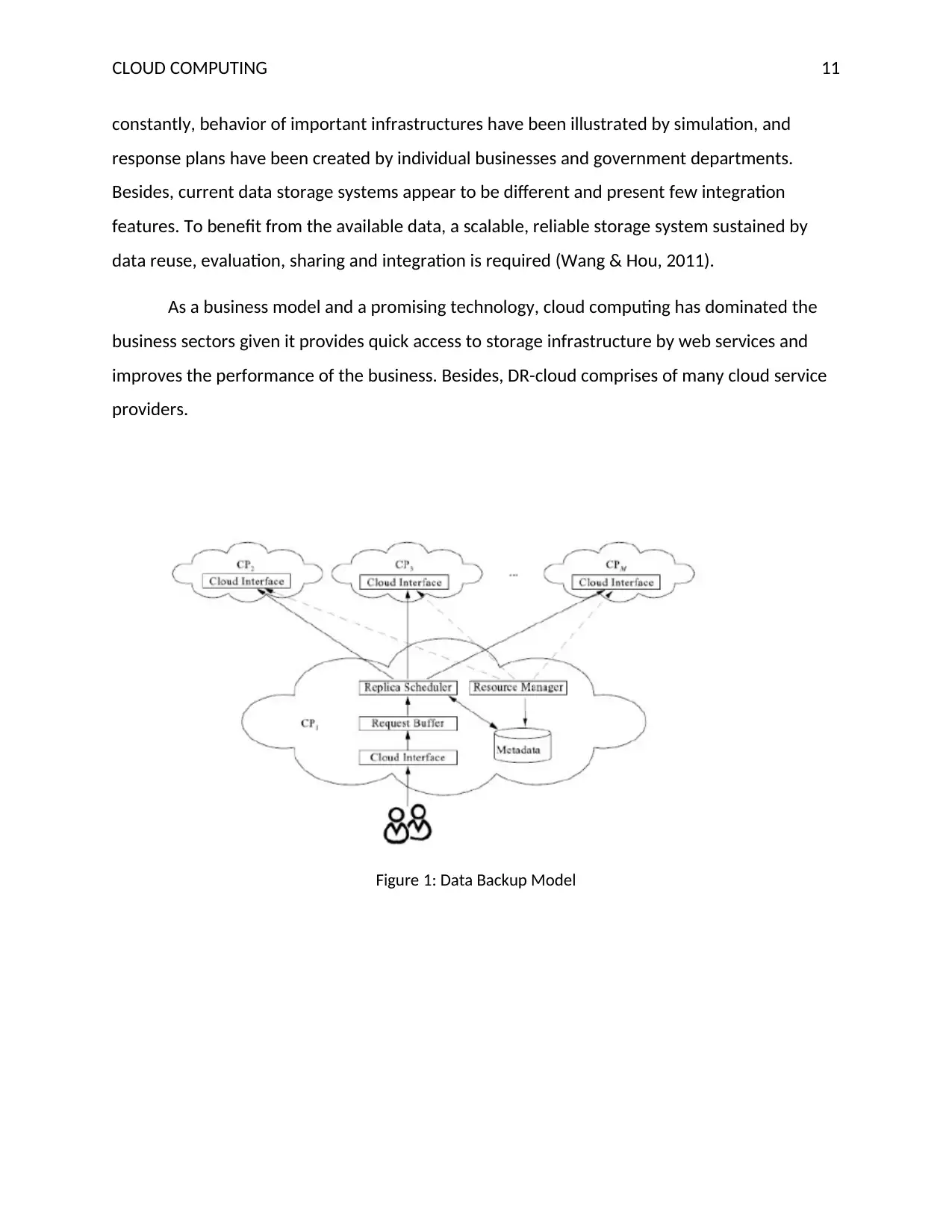
constantly, behavior of important infrastructures have been illustrated by simulation, and
response plans have been created by individual businesses and government departments.
Besides, current data storage systems appear to be different and present few integration
features. To benefit from the available data, a scalable, reliable storage system sustained by
data reuse, evaluation, sharing and integration is required (Wang & Hou, 2011).
As a business model and a promising technology, cloud computing has dominated the
business sectors given it provides quick access to storage infrastructure by web services and
improves the performance of the business. Besides, DR-cloud comprises of many cloud service
providers.
Figure 1: Data Backup Model
constantly, behavior of important infrastructures have been illustrated by simulation, and
response plans have been created by individual businesses and government departments.
Besides, current data storage systems appear to be different and present few integration
features. To benefit from the available data, a scalable, reliable storage system sustained by
data reuse, evaluation, sharing and integration is required (Wang & Hou, 2011).
As a business model and a promising technology, cloud computing has dominated the
business sectors given it provides quick access to storage infrastructure by web services and
improves the performance of the business. Besides, DR-cloud comprises of many cloud service
providers.
Figure 1: Data Backup Model
CLOUD COMPUTING 12
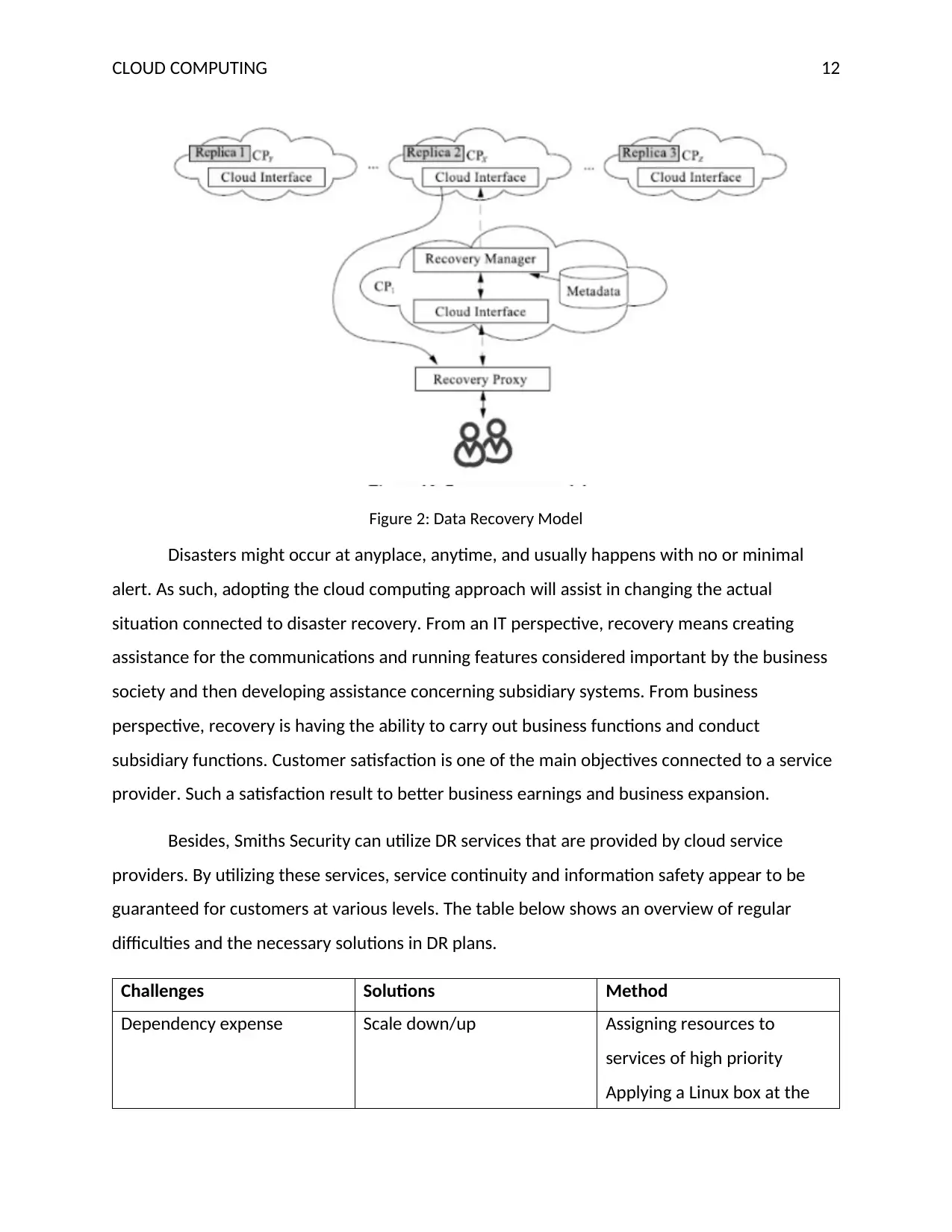
Figure 2: Data Recovery Model
Disasters might occur at anyplace, anytime, and usually happens with no or minimal
alert. As such, adopting the cloud computing approach will assist in changing the actual
situation connected to disaster recovery. From an IT perspective, recovery means creating
assistance for the communications and running features considered important by the business
society and then developing assistance concerning subsidiary systems. From business
perspective, recovery is having the ability to carry out business functions and conduct
subsidiary functions. Customer satisfaction is one of the main objectives connected to a service
provider. Such a satisfaction result to better business earnings and business expansion.
Besides, Smiths Security can utilize DR services that are provided by cloud service
providers. By utilizing these services, service continuity and information safety appear to be
guaranteed for customers at various levels. The table below shows an overview of regular
difficulties and the necessary solutions in DR plans.
Challenges Solutions Method
Dependency expense Scale down/up Assigning resources to
services of high priority
Applying a Linux box at the
Figure 2: Data Recovery Model
Disasters might occur at anyplace, anytime, and usually happens with no or minimal
alert. As such, adopting the cloud computing approach will assist in changing the actual
situation connected to disaster recovery. From an IT perspective, recovery means creating
assistance for the communications and running features considered important by the business
society and then developing assistance concerning subsidiary systems. From business
perspective, recovery is having the ability to carry out business functions and conduct
subsidiary functions. Customer satisfaction is one of the main objectives connected to a service
provider. Such a satisfaction result to better business earnings and business expansion.
Besides, Smiths Security can utilize DR services that are provided by cloud service
providers. By utilizing these services, service continuity and information safety appear to be
guaranteed for customers at various levels. The table below shows an overview of regular
difficulties and the necessary solutions in DR plans.
Challenges Solutions Method
Dependency expense Scale down/up Assigning resources to
services of high priority
Applying a Linux box at the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





