Victorian Institute of Technology: IT NE 2005 Smurf Attack Report
VerifiedAdded on 2022/10/16
|9
|1080
|4
Report
AI Summary
This report provides an in-depth analysis of the Smurf attack, a type of Distributed Denial of Service (DDoS) attack that emerged in the 1990s. The report explains the working method of the Smurf attack, which involves spoofing ICMP echo requests to flood a target server with responses, thereby causing a denial of service. It details how attackers exploit IP broadcast networks to amplify the traffic. The report also outlines various mitigation options, such as disabling IP-directed broadcasts, reconfiguring the OS to restrict ICMP responses, and filtering outbound traffic. Furthermore, the report discusses the Nmap tool, a versatile network mapper used for tasks like network discovery, port scanning, and vulnerability assessment. The report emphasizes the importance of security audits and proactive measures to protect against network attacks, including installing firewalls, anti-spyware programs, and using strong passwords. The report concludes by highlighting the impact of network attacks and the necessity of comprehensive security practices to safeguard against such threats.

Name: Smurf attack
Type: Distributed Denial of Service
Date: In the 1990s
The affected organizations/computers: Businesses and ISPs
Working method and the impact:
The attack is particular in the way it is carried out. During the attack, host 1 sends ICMP Echo to
another host 2 and triggers an automatic response1. The time taken for the response to be received
from the other host is used to determine the virtual distance between the two hosts. In a normal
situation of IP broadcast network, every host is supposed to receive the ping request and thus
prompting each recipient to respond. This is the vulnerability that Smurf attackers take advantage
of to increase their traffic.
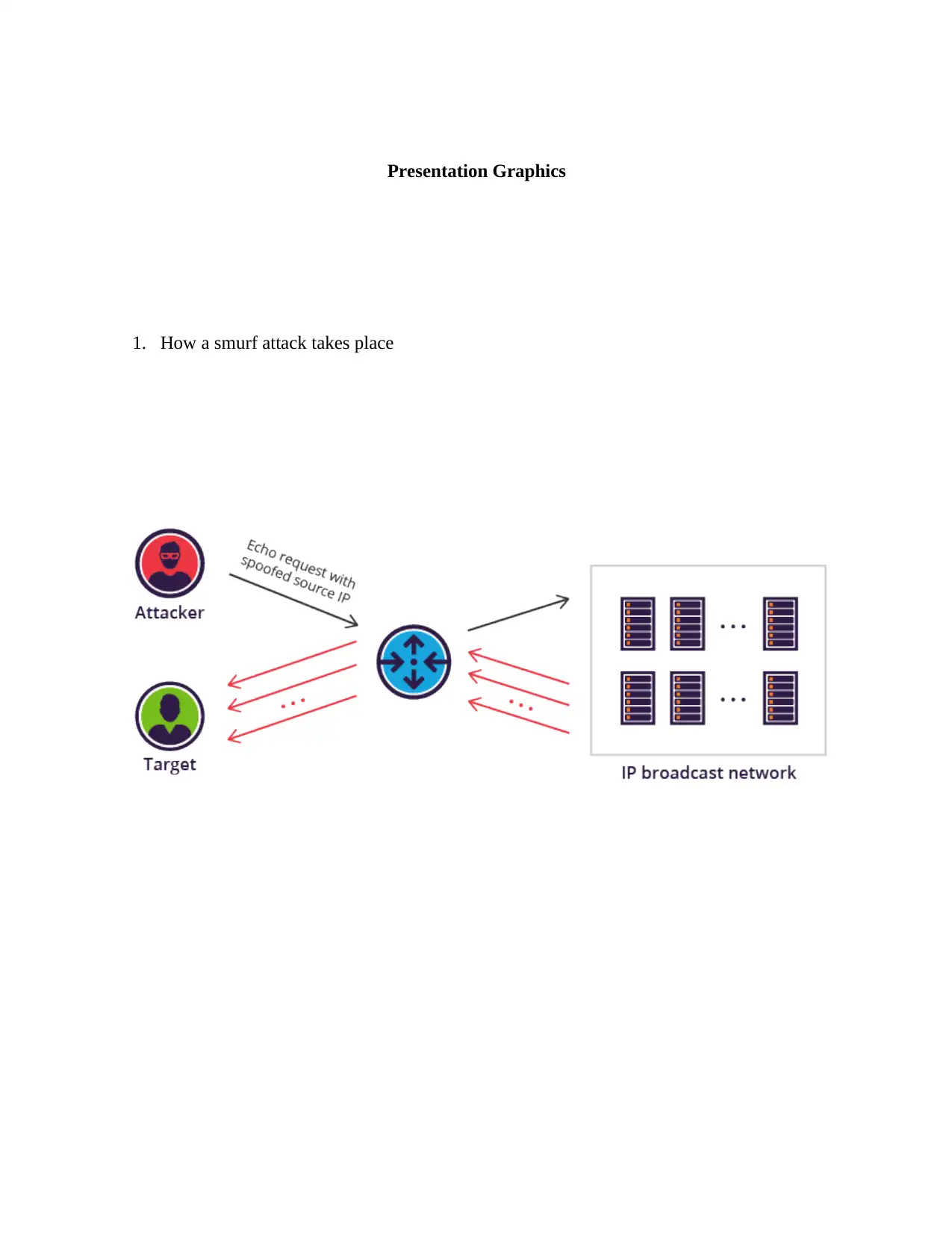
Basically, a Smurf attack follows the following steps2;
A fake Echo request is generated by Smurf malware and contains a source IP which is
spoofed to hide the fact that it the address of the target server.
The request then advances to an IP broadcast network which lies in between the sender and
the receiver after which it is transmitted equally to all the hosts found within the network
An ICMP response is then received from each host and sent to the spoofed source address.
This makes it possible for the target server to be brought down if a significant number of
responses are forwarded.
____________________________________________________________________________
1. Wiki.cas.mcmaster.ca. (2008). Smurfing - Computing and Software Wiki. [online] Available at:
http://wiki.cas.mcmaster.ca/index.php/Smurfing [Accessed 22 Sep. 2019].
2. Cert.org. (2017). 1998 CERT Advisories. [online] Available at: http://www.cert.org/historical/advisories/CA-
1998-01.cfm [Accessed 22 Sep. 2019].
Type: Distributed Denial of Service
Date: In the 1990s
The affected organizations/computers: Businesses and ISPs
Working method and the impact:
The attack is particular in the way it is carried out. During the attack, host 1 sends ICMP Echo to
another host 2 and triggers an automatic response1. The time taken for the response to be received
from the other host is used to determine the virtual distance between the two hosts. In a normal
situation of IP broadcast network, every host is supposed to receive the ping request and thus
prompting each recipient to respond. This is the vulnerability that Smurf attackers take advantage
of to increase their traffic.
Basically, a Smurf attack follows the following steps2;
A fake Echo request is generated by Smurf malware and contains a source IP which is
spoofed to hide the fact that it the address of the target server.
The request then advances to an IP broadcast network which lies in between the sender and
the receiver after which it is transmitted equally to all the hosts found within the network
An ICMP response is then received from each host and sent to the spoofed source address.
This makes it possible for the target server to be brought down if a significant number of
responses are forwarded.
____________________________________________________________________________
1. Wiki.cas.mcmaster.ca. (2008). Smurfing - Computing and Software Wiki. [online] Available at:
http://wiki.cas.mcmaster.ca/index.php/Smurfing [Accessed 22 Sep. 2019].
2. Cert.org. (2017). 1998 CERT Advisories. [online] Available at: http://www.cert.org/historical/advisories/CA-
1998-01.cfm [Accessed 22 Sep. 2019].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The critical factor that determines the extent and success of a Smurf attack is usually the number of
hosts that are available within the intermediate network3. The responses received from fake Echo
requests is directly proportional to the number of hosts in the network.
Mitigation Options
There are various methods that can be used to mitigate Smurf attacks. Such include;
Disabling broadcasts on the router that are IP-directed
Reconfiguring the OS to forbid giving ICMP responses to requests that are IP broadcast
Reconfiguration of the perimeter firewall such that the pings whose origin is outside the
network are disallowed.
Filtering the outbound traffic
_______________________________________________________________________________
3. Usa.kaspersky.com. (n.d.). [online] Available at: https://usa.kaspersky.com/internet-
security-center/definitions/smurf-attack#.U_61zWPp-ZQ [Accessed 22 Sep. 2019].
hosts that are available within the intermediate network3. The responses received from fake Echo
requests is directly proportional to the number of hosts in the network.
Mitigation Options
There are various methods that can be used to mitigate Smurf attacks. Such include;
Disabling broadcasts on the router that are IP-directed
Reconfiguring the OS to forbid giving ICMP responses to requests that are IP broadcast
Reconfiguration of the perimeter firewall such that the pings whose origin is outside the
network are disallowed.
Filtering the outbound traffic
_______________________________________________________________________________
3. Usa.kaspersky.com. (n.d.). [online] Available at: https://usa.kaspersky.com/internet-
security-center/definitions/smurf-attack#.U_61zWPp-ZQ [Accessed 22 Sep. 2019].
Presentation Graphics
1. How a smurf attack takes place
1. How a smurf attack takes place
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
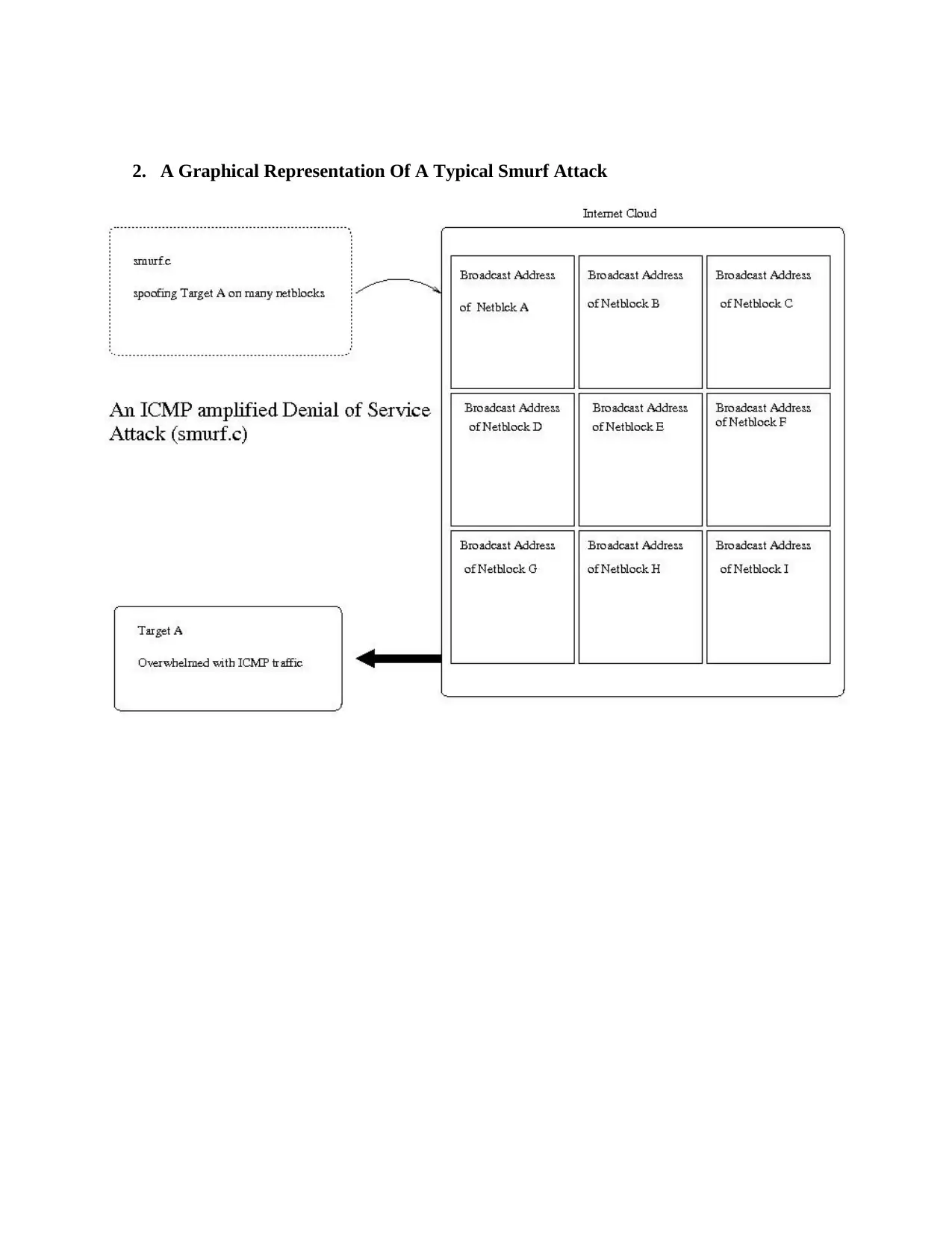
2. A Graphical Representation Of A Typical Smurf Attack
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
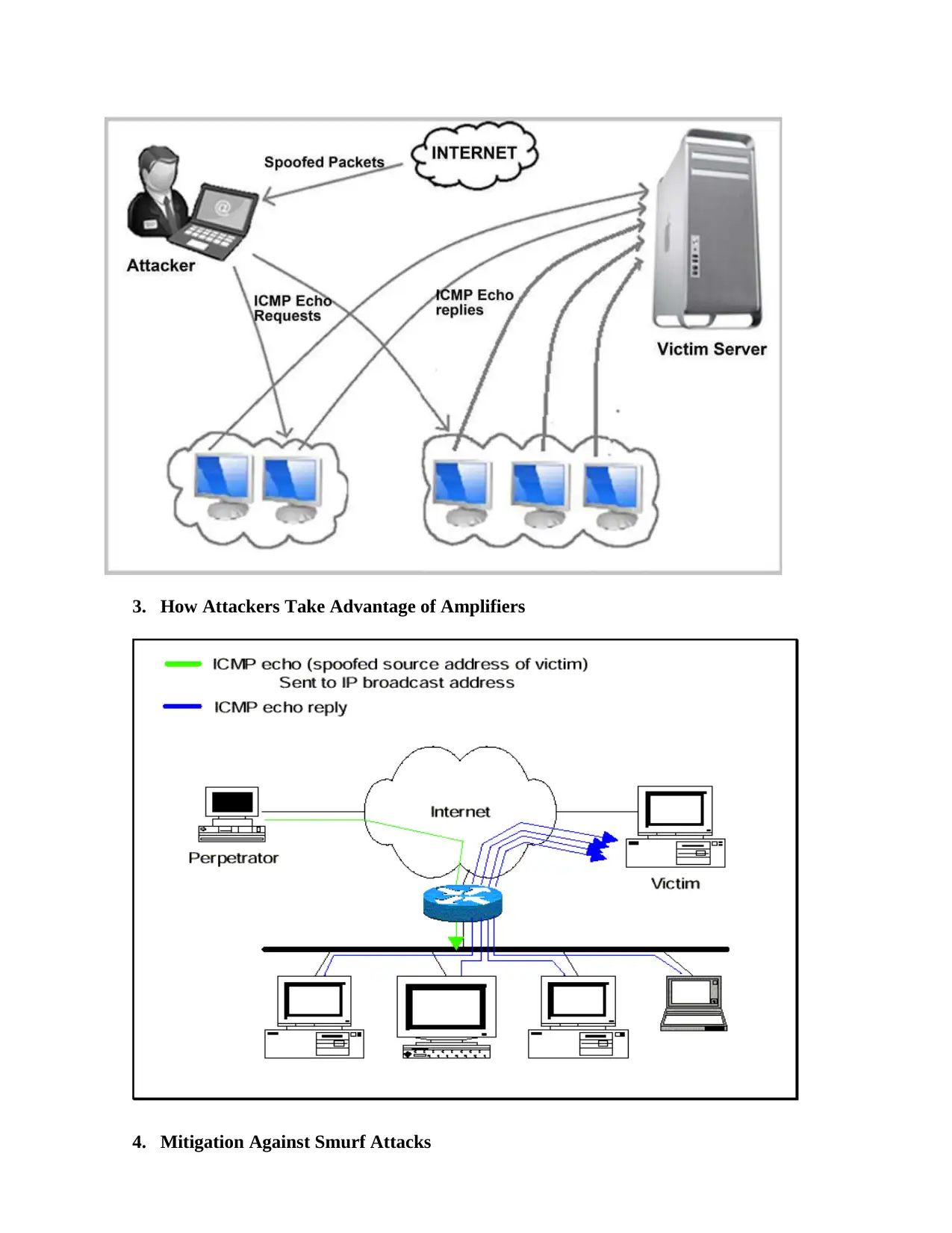
3. How Attackers Take Advantage of Amplifiers
4. Mitigation Against Smurf Attacks
4. Mitigation Against Smurf Attacks
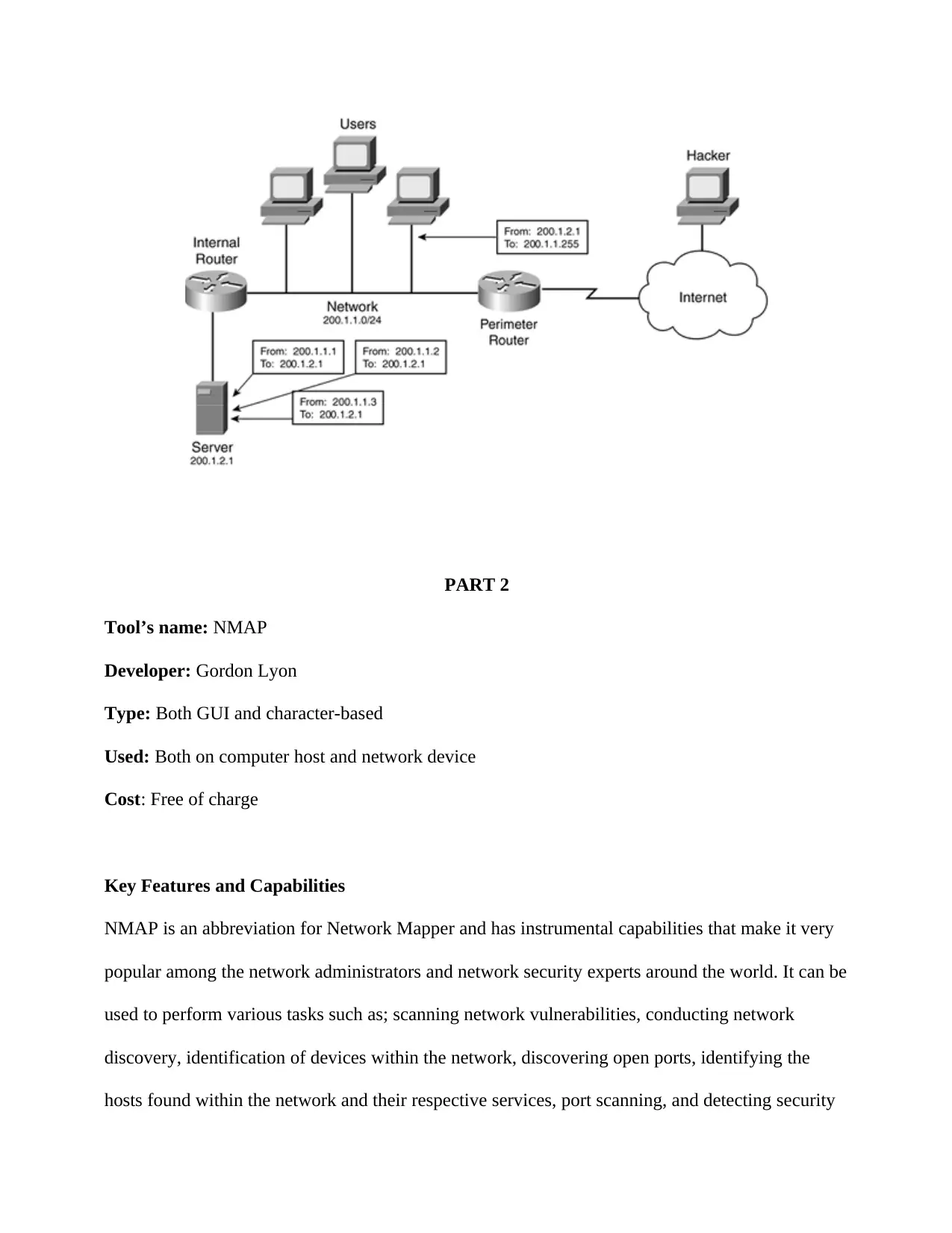
PART 2
Tool’s name: NMAP
Developer: Gordon Lyon
Type: Both GUI and character-based
Used: Both on computer host and network device
Cost: Free of charge
Key Features and Capabilities
NMAP is an abbreviation for Network Mapper and has instrumental capabilities that make it very
popular among the network administrators and network security experts around the world. It can be
used to perform various tasks such as; scanning network vulnerabilities, conducting network
discovery, identification of devices within the network, discovering open ports, identifying the
hosts found within the network and their respective services, port scanning, and detecting security
Tool’s name: NMAP
Developer: Gordon Lyon
Type: Both GUI and character-based
Used: Both on computer host and network device
Cost: Free of charge
Key Features and Capabilities
NMAP is an abbreviation for Network Mapper and has instrumental capabilities that make it very
popular among the network administrators and network security experts around the world. It can be
used to perform various tasks such as; scanning network vulnerabilities, conducting network
discovery, identification of devices within the network, discovering open ports, identifying the
hosts found within the network and their respective services, port scanning, and detecting security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

threats 4
Nmap is hugely flexible and has significantly improved over the years, but its key features have
remained intact. One of these original features is the port-scan tool which is used to gather
information through sending the raw packets to system ports. It then listens for any response from
the ports to determine which of them are closed, open or having some of filtering such as firewalls.
This is commonly referred to as port scanning or enumeration5.
Reflection
Network attacks are very prevalent and are responsible for a lot of damage known to the public.
The impact of these network attacks varies depending on how severe the attack is. For example,
less impact will be felt if the attack was recognized during the early stages before damage was
done. However, if the attack had managed to go deeper then the operation of the organization
might suffer a tremendous impact. For instance, if the attacker managed to gain access to personal
information may cause customers to lose confidence in the organization as well as affecting other
company’s operations.
_______________________________________________________________________________
4. Nmap.org. (n.d.). Nmap: the Network Mapper - Free Security Scanner. [online] Available at: http://nmap.org/
[Accessed 22 Sep. 2019].
5. Docs.ruckuswireless.com. (n.d.). Protecting against smurf attacks. [online] Available at:
http://docs.ruckuswireless.com/fastiron/08.0.70/fastiron-08070-securityguide/GUID-FE25CD5B-FFA5-4A77-
B864-E606BFB2BB8A.html [Accessed 22 Sep. 2019].
It is therefore imperative that all the efforts are done to curb all the network attacks. One of the
Nmap is hugely flexible and has significantly improved over the years, but its key features have
remained intact. One of these original features is the port-scan tool which is used to gather
information through sending the raw packets to system ports. It then listens for any response from
the ports to determine which of them are closed, open or having some of filtering such as firewalls.
This is commonly referred to as port scanning or enumeration5.
Reflection
Network attacks are very prevalent and are responsible for a lot of damage known to the public.
The impact of these network attacks varies depending on how severe the attack is. For example,
less impact will be felt if the attack was recognized during the early stages before damage was
done. However, if the attack had managed to go deeper then the operation of the organization
might suffer a tremendous impact. For instance, if the attacker managed to gain access to personal
information may cause customers to lose confidence in the organization as well as affecting other
company’s operations.
_______________________________________________________________________________
4. Nmap.org. (n.d.). Nmap: the Network Mapper - Free Security Scanner. [online] Available at: http://nmap.org/
[Accessed 22 Sep. 2019].
5. Docs.ruckuswireless.com. (n.d.). Protecting against smurf attacks. [online] Available at:
http://docs.ruckuswireless.com/fastiron/08.0.70/fastiron-08070-securityguide/GUID-FE25CD5B-FFA5-4A77-
B864-E606BFB2BB8A.html [Accessed 22 Sep. 2019].
It is therefore imperative that all the efforts are done to curb all the network attacks. One of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

most efficient ways organizations use for protection against network attacks is performing security
audits on both the personnel who work there and the network itself to identify any possible
vulnerabilities. This helps very much in finding out if there is any weakness available that an
attacker can use and help mitigate the impact of an attack if it occurs.
What steps can you take to protect your PC or laptop computer?
Firewall installation
Installing antispyware programs
Installation of updated antivirus
Using passwords that are too complex
Connecting to only secure networks
Ensuring that the security settings in the browser are checked.
Bibliography
audits on both the personnel who work there and the network itself to identify any possible
vulnerabilities. This helps very much in finding out if there is any weakness available that an
attacker can use and help mitigate the impact of an attack if it occurs.
What steps can you take to protect your PC or laptop computer?
Firewall installation
Installing antispyware programs
Installation of updated antivirus
Using passwords that are too complex
Connecting to only secure networks
Ensuring that the security settings in the browser are checked.
Bibliography

Cert.org. (2017). 1998 CERT Advisories. [online] Available at:
http://www.cert.org/historical/advisories/CA-1998-01.cfm [Accessed 22 Sep. 2019].
Docs.ruckuswireless.com. (n.d.). Protecting against smurf attacks. [online] Available at:
http://docs.ruckuswireless.com/fastiron/08.0.70/fastiron-08070-securityguide/GUID-
FE25CD5B-FFA5-4A77-B864-E606BFB2BB8A.html [Accessed 22 Sep. 2019].
Nmap.org. (n.d.). Nmap: the Network Mapper - Free Security Scanner. [online] Available at:
http://nmap.org/ [Accessed 22 Sep. 2019].
Usa.kaspersky.com. (n.d.). [online] Available at: https://usa.kaspersky.com/internet-security-
center/definitions/smurf-attack#.U_61zWPp-ZQ [Accessed 22 Sep. 2019].
Wiki.cas.mcmaster.ca. (2008). Smurfing - Computing and Software Wiki. [online] Available at:
http://wiki.cas.mcmaster.ca/index.php/Smurfing [Accessed 22 Sep. 2019].
http://www.cert.org/historical/advisories/CA-1998-01.cfm [Accessed 22 Sep. 2019].
Docs.ruckuswireless.com. (n.d.). Protecting against smurf attacks. [online] Available at:
http://docs.ruckuswireless.com/fastiron/08.0.70/fastiron-08070-securityguide/GUID-
FE25CD5B-FFA5-4A77-B864-E606BFB2BB8A.html [Accessed 22 Sep. 2019].
Nmap.org. (n.d.). Nmap: the Network Mapper - Free Security Scanner. [online] Available at:
http://nmap.org/ [Accessed 22 Sep. 2019].
Usa.kaspersky.com. (n.d.). [online] Available at: https://usa.kaspersky.com/internet-security-
center/definitions/smurf-attack#.U_61zWPp-ZQ [Accessed 22 Sep. 2019].
Wiki.cas.mcmaster.ca. (2008). Smurfing - Computing and Software Wiki. [online] Available at:
http://wiki.cas.mcmaster.ca/index.php/Smurfing [Accessed 22 Sep. 2019].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



