Network Management Solution: Report on Design and Implementation
VerifiedAdded on 2021/04/16
|9
|1907
|53
Report
AI Summary
This report presents a network management solution, emphasizing the proactive management of network devices through the use of SNMP (Simple Network Management Protocol) and MIB (Management Information Base). The report outlines a scenario design based on the five areas of functionality defined by the International Organization of Standards, including fault, configuration, performance, security, and accounting management. It details the roles of network components such as routers, network management systems (NMS), printers, uninterruptible power supplies (UPS), and workstations, along with their respective IP addresses and functionalities. The implementation section covers essential prerequisites like MIB files, object identifiers (OIDs), and the hierarchical structure of MIB trees. The report further provides examples of SNMP commands and their usage to query data from network nodes. The conclusion highlights the utility of SNMP in managing large networks, sending alerts, and preventing device destruction. The report also provides a list of references used in the solution.

1
Running Head: Network Management Solution
A Report on Network Management Solution
Name
Course
Instructor
Date
Running Head: Network Management Solution
A Report on Network Management Solution
Name
Course
Instructor
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Running Head: Network Management Solution
Introduction
A network management solution facilitates the proactive management of devices found in a
network. It allows the devices in the network to be constantly queried for configuration and
performance. This can be done using SNMP (Simple Network Management Protocol) together
with MIB (Management Information Base). SNMP refers to an application layer protocol that
allows information to be exchanged between devices in a network (Rufus P. Credle Jr., Uma
Maheswari Kumaraguru, Gilson Cesar de Oliveira, Micky Reichenberg, Georg Senfleben,
Rutsakon Techo, Maulide Xavier, IBM Redbooks, 2013). The MIB on the other hand refers to
a database that contains information describing the parameters of a device in the network. The
MIB contains standard control values for the hardware of the managed devices in the network
(Hele-Mai Haav; Ahto Kalja, 2009). The SNMP utilizes this database to request for information
about a managed device and translates this information as required by the network management
system. Below is a scenario design of a network management solution together with its
implementation that makes use of SNMP manager and MIB database for management of devices
in a network.
Scenario Design of a Network Management Solution
The design of a network management solution will largely be dependent on the five areas of
functionality as defined by the International Organization of Standards body. These areas include
fault management, configuration management, performance management, security management
and accounting management (Cisco, 2007).
Fault Management is concerned with the detection, notification, isolation and correction of
faults occurring within a managed device in a network.
Configuration Management deals with the settings aspect of a device in the network, such as
file management configuration and software management. This ensures the configuration
parameters are checked to avoid incompatibility issues.
Performance Management ensures the optimal levels of performance of a network. It is
required to perform a routine check of the quality service and performance level of each
networked device.
Security Management goal is to prevent and protect intentional or unintentional sabotage of the
network by controlling access by the users in that network.
Running Head: Network Management Solution
Introduction
A network management solution facilitates the proactive management of devices found in a
network. It allows the devices in the network to be constantly queried for configuration and
performance. This can be done using SNMP (Simple Network Management Protocol) together
with MIB (Management Information Base). SNMP refers to an application layer protocol that
allows information to be exchanged between devices in a network (Rufus P. Credle Jr., Uma
Maheswari Kumaraguru, Gilson Cesar de Oliveira, Micky Reichenberg, Georg Senfleben,
Rutsakon Techo, Maulide Xavier, IBM Redbooks, 2013). The MIB on the other hand refers to
a database that contains information describing the parameters of a device in the network. The
MIB contains standard control values for the hardware of the managed devices in the network
(Hele-Mai Haav; Ahto Kalja, 2009). The SNMP utilizes this database to request for information
about a managed device and translates this information as required by the network management
system. Below is a scenario design of a network management solution together with its
implementation that makes use of SNMP manager and MIB database for management of devices
in a network.
Scenario Design of a Network Management Solution
The design of a network management solution will largely be dependent on the five areas of
functionality as defined by the International Organization of Standards body. These areas include
fault management, configuration management, performance management, security management
and accounting management (Cisco, 2007).
Fault Management is concerned with the detection, notification, isolation and correction of
faults occurring within a managed device in a network.
Configuration Management deals with the settings aspect of a device in the network, such as
file management configuration and software management. This ensures the configuration
parameters are checked to avoid incompatibility issues.
Performance Management ensures the optimal levels of performance of a network. It is
required to perform a routine check of the quality service and performance level of each
networked device.
Security Management goal is to prevent and protect intentional or unintentional sabotage of the
network by controlling access by the users in that network.

3
Running Head: Network Management Solution
Accounting Management refers to the process of regulating the utilization parameters of a
network to maintain an optimal level of performance. This way, individuals and groups can be
allocated network resources according to their usage patterns.
The Design of a Network Management System will contain the following.
Router
Different functions will be performed by the router in this network infrastructure. Firstly, the
router will be handling all the addressing of other networked devices. In this case, a class C
addressing scheme is used where the available ip addresses range from 192.0.0.0 –
223.255.255.255. The router address is 192.0.0.1. The rest of the devices in the network will
take an ip address within the remaining range.
Secondly, the router will house the SNMP agent together with the MIB database. The SNMP
agent is a software that collects data from the devices in the network, stores it in the MIB and
makes it available for the manager. The SNMP interacts with the agents using different types of
commands, namely Read, Write, Notification. Using Read command, the SNMP manager reads
MIB objects availed by the SNMP agents. Using Write command, the SNMP manager can
modify the MIB objects and object instances stored the by the agents in the database. The read
and write access is achieved by a concept known as Community strings. Community Strings act
as passwords that allow authorized users only to get access to the agent. By default, the
community strings are set to public which only authorizes a read-only access. The Notification
command allows the SNMP manager to be issued with reports regarding a device state on the
network. The SNMP agent makes use of traps to send notifications. On the other hand, MIB will
contain the data from the devices that is shared between the networked device and the manager
software.
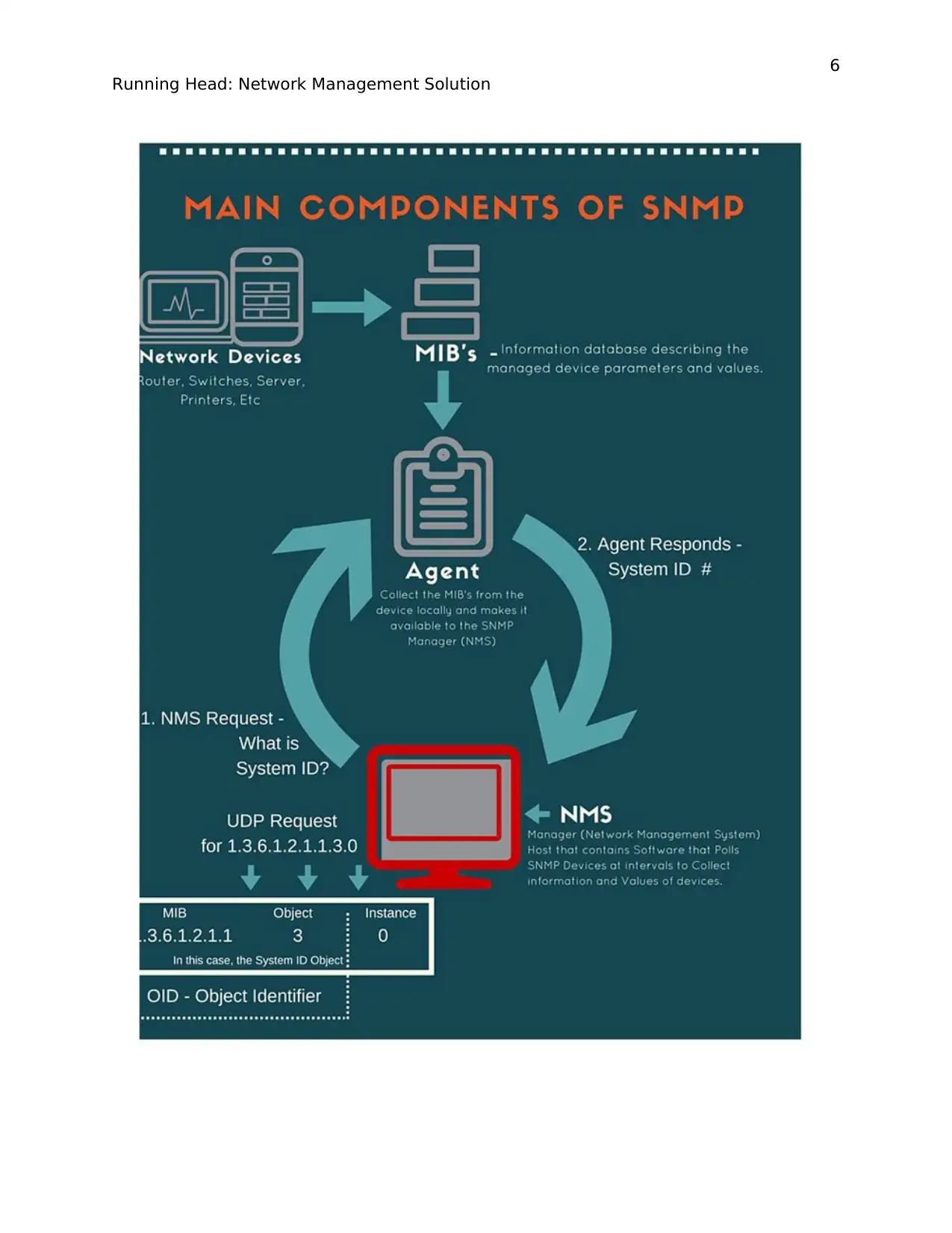
Network Management System (NMS)
The network management system is a management console installed with a network monitoring
software with built-in SNMP. The SNMP employs a client-server kind of communication where
a request is sent by the NMS to the managed devices which in turn return a response. The SNMP
uses four most common request operations. Get, GetNext, Trap and Set. Get is used to retrieve
an instance of an object from the agent. GetNext retrieves the next instance of an object from a
list or a table within the agent. GetNext operation reads through the table until all elements are
retrieved indicated when the request returns a value outside of the list. Set operation is used to
modify values of objects in the agent. Trap operation allows the agent to send notifications to the
SNMP manager asynchronously during the occurrence of some event. The NMS takes the ip
Running Head: Network Management Solution
Accounting Management refers to the process of regulating the utilization parameters of a
network to maintain an optimal level of performance. This way, individuals and groups can be
allocated network resources according to their usage patterns.
The Design of a Network Management System will contain the following.
Router
Different functions will be performed by the router in this network infrastructure. Firstly, the
router will be handling all the addressing of other networked devices. In this case, a class C
addressing scheme is used where the available ip addresses range from 192.0.0.0 –
223.255.255.255. The router address is 192.0.0.1. The rest of the devices in the network will
take an ip address within the remaining range.
Secondly, the router will house the SNMP agent together with the MIB database. The SNMP
agent is a software that collects data from the devices in the network, stores it in the MIB and
makes it available for the manager. The SNMP interacts with the agents using different types of
commands, namely Read, Write, Notification. Using Read command, the SNMP manager reads
MIB objects availed by the SNMP agents. Using Write command, the SNMP manager can
modify the MIB objects and object instances stored the by the agents in the database. The read
and write access is achieved by a concept known as Community strings. Community Strings act
as passwords that allow authorized users only to get access to the agent. By default, the
community strings are set to public which only authorizes a read-only access. The Notification
command allows the SNMP manager to be issued with reports regarding a device state on the
network. The SNMP agent makes use of traps to send notifications. On the other hand, MIB will
contain the data from the devices that is shared between the networked device and the manager
software.
Network Management System (NMS)
The network management system is a management console installed with a network monitoring
software with built-in SNMP. The SNMP employs a client-server kind of communication where
a request is sent by the NMS to the managed devices which in turn return a response. The SNMP
uses four most common request operations. Get, GetNext, Trap and Set. Get is used to retrieve
an instance of an object from the agent. GetNext retrieves the next instance of an object from a
list or a table within the agent. GetNext operation reads through the table until all elements are
retrieved indicated when the request returns a value outside of the list. Set operation is used to
modify values of objects in the agent. Trap operation allows the agent to send notifications to the
SNMP manager asynchronously during the occurrence of some event. The NMS takes the ip
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
Running Head: Network Management Solution
address 192.168.0.20 in the network. It communicates with the agent that provides data – either
performance or configuration data - from the devices in the network.
Printer
In this regard, a printer is a node on the network that can be queried by the network management
system to provide data about its state. At any time, the queried data can show the printer’s state
as available, idle or active. The printer takes the ip address 192.168.0.30 in the network.
Uninterruptible Power Supply
As a node in the network, the UPS can be queried on different objects of the SNMP. For
example, when queried, the UPS can return the battery system status (temperatures, charge) or
the device working mode (online, offline). The ip address of the UPS is 192.168.0.15.
WorkStation
A workstation can be any console device that is used by the user to interact with the network. A
workstation can provide data regarding its name, workgroup, status (online or offline),
performance and data usage level in the network. In this network design, the workstation takes
the ip address 192.168.0.25. Below is a description of the design of a network management
Running Head: Network Management Solution
address 192.168.0.20 in the network. It communicates with the agent that provides data – either
performance or configuration data - from the devices in the network.
Printer
In this regard, a printer is a node on the network that can be queried by the network management
system to provide data about its state. At any time, the queried data can show the printer’s state
as available, idle or active. The printer takes the ip address 192.168.0.30 in the network.
Uninterruptible Power Supply
As a node in the network, the UPS can be queried on different objects of the SNMP. For
example, when queried, the UPS can return the battery system status (temperatures, charge) or
the device working mode (online, offline). The ip address of the UPS is 192.168.0.15.
WorkStation
A workstation can be any console device that is used by the user to interact with the network. A
workstation can provide data regarding its name, workgroup, status (online or offline),
performance and data usage level in the network. In this network design, the workstation takes
the ip address 192.168.0.25. Below is a description of the design of a network management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
Running Head: Network Management Solution
solution (PCWDL, 2017).
Running Head: Network Management Solution
solution (PCWDL, 2017).
6
Running Head: Network Management Solution
Running Head: Network Management Solution
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
Running Head: Network Management Solution
Implementation
To effectively implement an SNMP, there are essential prerequisites to be considered. To start
with, an MIB file for the managed object should be made available. All Objects in the MIB are
defined using a common set of Abstract Syntax Notation(ASN) known as the Structure of
Management Information(SMI) that specifies the allowed data types and classes of management
information. There exist two types of object identifiers(OID) or managed objects, namely scalar
and tabular. Scalar objects return a single value or object instance. On the other hand, tabular
returns multiple object instance that are put together in the MIB table. For Example, the object
atInput is a scalar object because it contains a single integer value that shows the total input
packets on a router. CPU utilization query would return separate results for each CPU hence it is
a tabular object identifier.
MIB’s contain Object Identifiers (OID) that uniquely identify MIB’s, MIB tables, MIB objects
and object indices that the SNMP monitors. The organization of the MIB is hierarchical and is
represented as a tree with levels emanating from the root to the leaves. Each level has its own
OID presented as numbers. Each node along the path has a name and a number associated with
it. For Example, to get to the LAN Manager, the tree structure would look like this:
Iso(1).org(3).dod(6).internet(1).Private(4).Enterprise(1).LAN Manager(77). The OID object
number would be 1.3.6.1.4.1.77. The equivalent MIB tree structure is as explained below.
To start with, at the top of the tree is an organization concerned with standards:ISO(1). Under
Iso, there is a node known as org(3) which stands for organizations. Below this level, there is a
node called dod(6) which stands for the Department of Defence. Under dod, is the internet(1),
from which the internet community branches. The directory(1) is a subtree of the internet(1) and
contains the OSI directory. The management(2) represents the RFC standard objects. The
Running Head: Network Management Solution
Implementation
To effectively implement an SNMP, there are essential prerequisites to be considered. To start
with, an MIB file for the managed object should be made available. All Objects in the MIB are
defined using a common set of Abstract Syntax Notation(ASN) known as the Structure of
Management Information(SMI) that specifies the allowed data types and classes of management
information. There exist two types of object identifiers(OID) or managed objects, namely scalar
and tabular. Scalar objects return a single value or object instance. On the other hand, tabular
returns multiple object instance that are put together in the MIB table. For Example, the object
atInput is a scalar object because it contains a single integer value that shows the total input
packets on a router. CPU utilization query would return separate results for each CPU hence it is
a tabular object identifier.
MIB’s contain Object Identifiers (OID) that uniquely identify MIB’s, MIB tables, MIB objects
and object indices that the SNMP monitors. The organization of the MIB is hierarchical and is
represented as a tree with levels emanating from the root to the leaves. Each level has its own
OID presented as numbers. Each node along the path has a name and a number associated with
it. For Example, to get to the LAN Manager, the tree structure would look like this:
Iso(1).org(3).dod(6).internet(1).Private(4).Enterprise(1).LAN Manager(77). The OID object
number would be 1.3.6.1.4.1.77. The equivalent MIB tree structure is as explained below.
To start with, at the top of the tree is an organization concerned with standards:ISO(1). Under
Iso, there is a node known as org(3) which stands for organizations. Below this level, there is a
node called dod(6) which stands for the Department of Defence. Under dod, is the internet(1),
from which the internet community branches. The directory(1) is a subtree of the internet(1) and
contains the OSI directory. The management(2) represents the RFC standard objects. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
Running Head: Network Management Solution
experimental(3) represents internet experiments. Lastly, the private(4) is vendor specific and
contains those MIB’s from the vendor.
Printer
For the printer, the system up time can be queried using the following command, assuming the
printer’s ip address is 192.168.0.10.
%snmpget -v 2c -cpublic -mALL 192.168.0.10 system.systemUpTime.0
Ans: system.sysUpTime.0 =Timeticks: (586753771) 67 days, 21:58:06.70
The next command snmpgetnet returns the following OID in the tree sequence and its value.
%snmpgetnext -v2 2c -cpublic -mALL 192.168.0.10 system.systemUpTime.0
Ans: system. sysContact.0 = Peter Parker petepark@gmail.com.
The snmptranslate command converts a numeric OID and returns a corresponding MIB name in
text form.
%snmptranslate .1.3.6.1.2.1.1.3.0
Ans: SNMPv2-MIB: : sysUpTime.0
Conclusion
The SNMP offers numerous commands that can be utilized to query data from the nodes in a
network. Different network monitoring applications contain snmp that facilitates proactive
management of networked devices. By using snmptrap command, alerts can be sent from a
device to a network management software informing of a fault occurrence in the device. This
technique allows effective maintenance of big networks and prevents destruction of computing
devices in the network.
Running Head: Network Management Solution
experimental(3) represents internet experiments. Lastly, the private(4) is vendor specific and
contains those MIB’s from the vendor.
Printer
For the printer, the system up time can be queried using the following command, assuming the
printer’s ip address is 192.168.0.10.
%snmpget -v 2c -cpublic -mALL 192.168.0.10 system.systemUpTime.0
Ans: system.sysUpTime.0 =Timeticks: (586753771) 67 days, 21:58:06.70
The next command snmpgetnet returns the following OID in the tree sequence and its value.
%snmpgetnext -v2 2c -cpublic -mALL 192.168.0.10 system.systemUpTime.0
Ans: system. sysContact.0 = Peter Parker petepark@gmail.com.
The snmptranslate command converts a numeric OID and returns a corresponding MIB name in
text form.
%snmptranslate .1.3.6.1.2.1.1.3.0
Ans: SNMPv2-MIB: : sysUpTime.0
Conclusion
The SNMP offers numerous commands that can be utilized to query data from the nodes in a
network. Different network monitoring applications contain snmp that facilitates proactive
management of networked devices. By using snmptrap command, alerts can be sent from a
device to a network management software informing of a fault occurrence in the device. This
technique allows effective maintenance of big networks and prevents destruction of computing
devices in the network.

9
Running Head: Network Management Solution
References
Cisco. (2007, July 11). Network Management System: Best Practices White Paper.
Retrieved from A Cisco Corporation Website:
https://www.cisco.com/c/en/us/support/docs/availability/high-availability/15114-
NMS-bestpractice.html
Hele-Mai Haav; Ahto Kalja. (2009). Databases and Information Systems V: Selected
Papers from the Eighth International Baltic Conference, DB&IS 2008. Amsterdam:
IOS Press.
PCWDL. (2017). What is SNMP? Basic Tutorial on NMS, MIBs, OIDs, Traps & Agents.
Retrieved from PC&Network Website : https://www.pcwdld.com/what-is-snmp-
and-tutorial
Rufus P. Credle Jr., Uma Maheswari Kumaraguru, Gilson Cesar de Oliveira, Micky
Reichenberg, Georg Senfleben, Rutsakon Techo, Maulide Xavier, IBM Redbooks.
(2013). IBM z/OS V2R1 Communications Server TCP/IP Implementation Volume 2:
Standard Applications, Volume 2. Lampeter, UK: IBM Redbooks.
Running Head: Network Management Solution
References
Cisco. (2007, July 11). Network Management System: Best Practices White Paper.
Retrieved from A Cisco Corporation Website:
https://www.cisco.com/c/en/us/support/docs/availability/high-availability/15114-
NMS-bestpractice.html
Hele-Mai Haav; Ahto Kalja. (2009). Databases and Information Systems V: Selected
Papers from the Eighth International Baltic Conference, DB&IS 2008. Amsterdam:
IOS Press.
PCWDL. (2017). What is SNMP? Basic Tutorial on NMS, MIBs, OIDs, Traps & Agents.
Retrieved from PC&Network Website : https://www.pcwdld.com/what-is-snmp-
and-tutorial
Rufus P. Credle Jr., Uma Maheswari Kumaraguru, Gilson Cesar de Oliveira, Micky
Reichenberg, Georg Senfleben, Rutsakon Techo, Maulide Xavier, IBM Redbooks.
(2013). IBM z/OS V2R1 Communications Server TCP/IP Implementation Volume 2:
Standard Applications, Volume 2. Lampeter, UK: IBM Redbooks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





