SNMP Protocol Analysis: Network Management, Commands, and Applications
VerifiedAdded on 2023/06/03
|20
|4914
|153
Report
AI Summary
This report provides a comprehensive analysis of the Simple Network Management Protocol (SNMP), focusing on its role in network management, its various versions (SNMPv1, SNMPv2, and SNMPv3), and its architecture. It details why SNMP is popular in specific management areas due to built-in agents in network devices and its basic standards like Remote Network Monitoring (RMON). The report also explains different SNMP commands such as snmpget, snmpwalk, snmpbulkwalk, snmptable, snmpset, and snmptrapd, illustrating their usage with examples and highlighting their differences. Furthermore, the report includes an assessment of target hosts using SNMP, identifying network interfaces, datagrams received, ping messages, connected devices, and port statuses. It also addresses troubleshooting techniques for identifying and resolving port flapping issues. The document is a detailed resource for understanding SNMP and its practical applications in network management.

SNMP 1
SNMP
Name
Course
Date
SNMP
Name
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SNMP 2
Section A
Introduction
In general, network management is a service that uses different tools, devices, applications,
and protocols to help network administrators in controlling and monitoring network
resources, both software and hardware, to address network objectives and service
requirements (Jin and Lin, 2012). For instance, in the past when transmission control
protocol/internet protocol were created, network management was given the least priority.
Because of the high development cost before 1980, network management was mostly
proprietary. As the complexity and size of the network grew, it led to significant diffusion of
technologies for network management.
It was in 1988 when Simple Network Management Protocol (SNMP) was approved by the
Internet Architecture Board (IAB) as a short-term solution to address network management
issues that were on the rise. This became the focal point for offering network management
services and created a way for standardized network management and emergence of more
tools for managing the networks.
A network management system (NMS) can be described as a group of applications or
software that facilitates control and monitoring of the entire network infrastructure. The
figure below shows the basic structure of an NMS.
Figure 1: Basic Network Management System Architecture (Source: Zhang, et al., 2015)
Section A
Introduction
In general, network management is a service that uses different tools, devices, applications,
and protocols to help network administrators in controlling and monitoring network
resources, both software and hardware, to address network objectives and service
requirements (Jin and Lin, 2012). For instance, in the past when transmission control
protocol/internet protocol were created, network management was given the least priority.
Because of the high development cost before 1980, network management was mostly
proprietary. As the complexity and size of the network grew, it led to significant diffusion of
technologies for network management.
It was in 1988 when Simple Network Management Protocol (SNMP) was approved by the
Internet Architecture Board (IAB) as a short-term solution to address network management
issues that were on the rise. This became the focal point for offering network management
services and created a way for standardized network management and emergence of more
tools for managing the networks.
A network management system (NMS) can be described as a group of applications or
software that facilitates control and monitoring of the entire network infrastructure. The
figure below shows the basic structure of an NMS.
Figure 1: Basic Network Management System Architecture (Source: Zhang, et al., 2015)

SNMP 3
The architecture is made up of two primary elements: managed device and managing device.
The management station is used as an interface between the network management system and
the network administrator. It is also used by other network management tools to carry out
network management functions by interacting with the managed devices.
Due to the diversity and the difference between managed devices such as switches, hubs,
bridges, routers and many others, a wide variety of programming interfaces and operating
systems, it has become critical to have a network management protocol for the management
station to facilitate effective communication with the managed devices. SNMP is one of these
protocols. Many other protocols have been developed such as CMIP to replace SNMP but
SNMP still remain one of the most popular network management tools. This section seeks to
explain why SNMP is a popular management tool and not so prevalent in other
communication areas. Additionally, it will include details of traditional SNMP controlled
technologies and areas covered by alternative management system.
Simple Network Management Protocol (SNMP)
This part will discuss the different versions of SNMP and introduce other network
management protocols. The reason why SNMP is very popular in certain areas of network
management is because most of the network devices used in most enterprise networks have
built-in agents that support SNMP. This facilitates monitoring and controlling any new
device(s) added to the network. Besides, it has additional basic set of standards such as
Remote network monitoring (RMON) which provides very crucial information about the
network to the network administrator by defining the remote network monitoring
Management Information Base (MIB) that substitutes MIB-2 (Mauro and Schmidt, 2009).
SNMP version
The goal of a network managements system is to implement a single protocol that will
facilitate management of both TCP/IP and OSI networks. There exist three versions of
SNMP: SNMPv1, SNMPv2, and SNMPv3. Initially, SNMPv1 was considered a temporary
network management protocol while ISO CMIP over TCP/IP was considered as long-term
solution. SNMP is made up of three features: the MIB which defies the managed
components, the SMI which explains how managed components in the MIB are defined, and
the SNMP which describes the protocol used to manage these components.
SNMP Architecture
The architecture is made up of two primary elements: managed device and managing device.
The management station is used as an interface between the network management system and
the network administrator. It is also used by other network management tools to carry out
network management functions by interacting with the managed devices.
Due to the diversity and the difference between managed devices such as switches, hubs,
bridges, routers and many others, a wide variety of programming interfaces and operating
systems, it has become critical to have a network management protocol for the management
station to facilitate effective communication with the managed devices. SNMP is one of these
protocols. Many other protocols have been developed such as CMIP to replace SNMP but
SNMP still remain one of the most popular network management tools. This section seeks to
explain why SNMP is a popular management tool and not so prevalent in other
communication areas. Additionally, it will include details of traditional SNMP controlled
technologies and areas covered by alternative management system.
Simple Network Management Protocol (SNMP)
This part will discuss the different versions of SNMP and introduce other network
management protocols. The reason why SNMP is very popular in certain areas of network
management is because most of the network devices used in most enterprise networks have
built-in agents that support SNMP. This facilitates monitoring and controlling any new
device(s) added to the network. Besides, it has additional basic set of standards such as
Remote network monitoring (RMON) which provides very crucial information about the
network to the network administrator by defining the remote network monitoring
Management Information Base (MIB) that substitutes MIB-2 (Mauro and Schmidt, 2009).
SNMP version
The goal of a network managements system is to implement a single protocol that will
facilitate management of both TCP/IP and OSI networks. There exist three versions of
SNMP: SNMPv1, SNMPv2, and SNMPv3. Initially, SNMPv1 was considered a temporary
network management protocol while ISO CMIP over TCP/IP was considered as long-term
solution. SNMP is made up of three features: the MIB which defies the managed
components, the SMI which explains how managed components in the MIB are defined, and
the SNMP which describes the protocol used to manage these components.
SNMP Architecture
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
SNMP 4
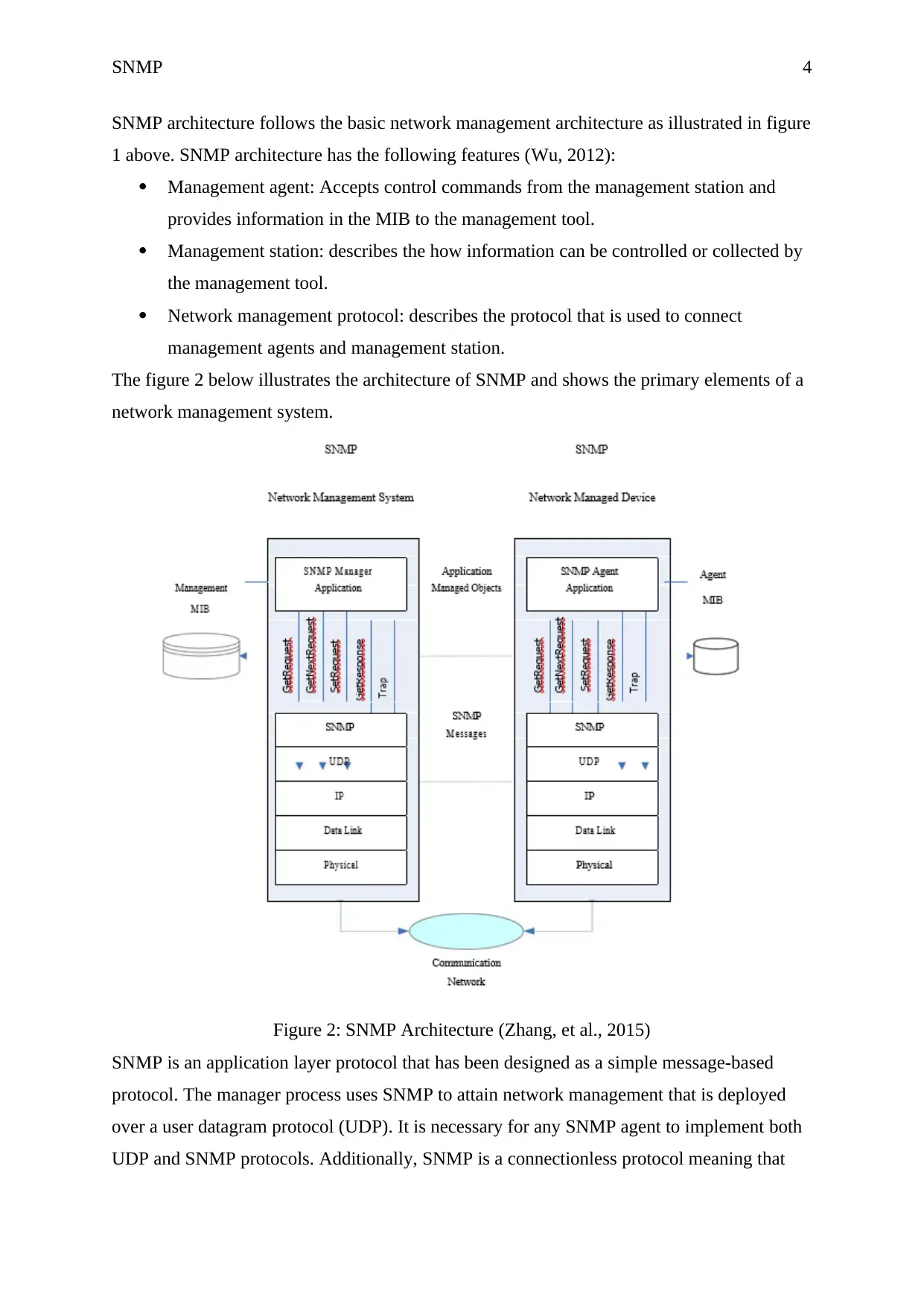
SNMP architecture follows the basic network management architecture as illustrated in figure
1 above. SNMP architecture has the following features (Wu, 2012):
Management agent: Accepts control commands from the management station and
provides information in the MIB to the management tool.
Management station: describes the how information can be controlled or collected by
the management tool.
Network management protocol: describes the protocol that is used to connect
management agents and management station.
The figure 2 below illustrates the architecture of SNMP and shows the primary elements of a
network management system.
Figure 2: SNMP Architecture (Zhang, et al., 2015)
SNMP is an application layer protocol that has been designed as a simple message-based
protocol. The manager process uses SNMP to attain network management that is deployed
over a user datagram protocol (UDP). It is necessary for any SNMP agent to implement both
UDP and SNMP protocols. Additionally, SNMP is a connectionless protocol meaning that
SNMP architecture follows the basic network management architecture as illustrated in figure
1 above. SNMP architecture has the following features (Wu, 2012):
Management agent: Accepts control commands from the management station and
provides information in the MIB to the management tool.
Management station: describes the how information can be controlled or collected by
the management tool.
Network management protocol: describes the protocol that is used to connect
management agents and management station.
The figure 2 below illustrates the architecture of SNMP and shows the primary elements of a
network management system.
Figure 2: SNMP Architecture (Zhang, et al., 2015)
SNMP is an application layer protocol that has been designed as a simple message-based
protocol. The manager process uses SNMP to attain network management that is deployed
over a user datagram protocol (UDP). It is necessary for any SNMP agent to implement both
UDP and SNMP protocols. Additionally, SNMP is a connectionless protocol meaning that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SNMP 5
communication between the agent and the management station is independent transaction.
Figure 2 also illustrates that the SNMP supports five types of protocol data units (PDU).
Three PDUs can be issued by the manager on behalf of a network application: SetRequest,
GetNExtRequest, and GetRequest. The agent acknowledges all the three messages using a
GetResponse message that is transmitted to the management application. An agent can also
generate a trap message which is an unwanted message that is produced when a triggered
event affects the normal functions of the MIB.
SNMP is still popular because it consumes less network resources and requires fewer
processing capabilities. This has led to SNMP being included and disseminated even in
simple components such as a printer. SNMP has the capability to monitor the number of
processes running on a particular device, information about memory of different devices and
CPU usage, charts and graphs with traffic statistics, and data on levels of printer toners.
Additionally, SNMP has the ability to allow one or more devices on the network to be used as
managers. The device will be configured to receive information from other components on
the network. It is easier to identify any defects or unusual activities by processing the
information generated by the manager device.
The protocol also describes how the data collected is transferred since the agents themselves
are responsible for storing the data. SNMP is both robust and simple apart from being
powerful enough and having the capacity to manage heterogenous networks (Colace, De
Santo and Ferrandino, 2010). Since it is a connectionless protocol, one does necessarily need
to take any action before or after sending the message. Additionally, since no connection is
required, the agent or manager does not require each other to operate. The network
administrator requires the information obtained from the SNMP to make decisions and define
network management strategies.
Section B
SNMP Command
This section will discuss the various SNMP commands. All the SNMP commands are
executed on the SNMP management station (Dubie, 2017). It is necessary that one has to
install ILOM MIBs files before using SNMP.
Snmpget command
This command returns an administratively given name for a particular node. For example
snpget -mall -v1 -cpublic agent_IP_address sysName.0
communication between the agent and the management station is independent transaction.
Figure 2 also illustrates that the SNMP supports five types of protocol data units (PDU).
Three PDUs can be issued by the manager on behalf of a network application: SetRequest,
GetNExtRequest, and GetRequest. The agent acknowledges all the three messages using a
GetResponse message that is transmitted to the management application. An agent can also
generate a trap message which is an unwanted message that is produced when a triggered
event affects the normal functions of the MIB.
SNMP is still popular because it consumes less network resources and requires fewer
processing capabilities. This has led to SNMP being included and disseminated even in
simple components such as a printer. SNMP has the capability to monitor the number of
processes running on a particular device, information about memory of different devices and
CPU usage, charts and graphs with traffic statistics, and data on levels of printer toners.
Additionally, SNMP has the ability to allow one or more devices on the network to be used as
managers. The device will be configured to receive information from other components on
the network. It is easier to identify any defects or unusual activities by processing the
information generated by the manager device.
The protocol also describes how the data collected is transferred since the agents themselves
are responsible for storing the data. SNMP is both robust and simple apart from being
powerful enough and having the capacity to manage heterogenous networks (Colace, De
Santo and Ferrandino, 2010). Since it is a connectionless protocol, one does necessarily need
to take any action before or after sending the message. Additionally, since no connection is
required, the agent or manager does not require each other to operate. The network
administrator requires the information obtained from the SNMP to make decisions and define
network management strategies.
Section B
SNMP Command
This section will discuss the various SNMP commands. All the SNMP commands are
executed on the SNMP management station (Dubie, 2017). It is necessary that one has to
install ILOM MIBs files before using SNMP.
Snmpget command
This command returns an administratively given name for a particular node. For example
snpget -mall -v1 -cpublic agent_IP_address sysName.0

SNMP 6
The output of this command is as shown below
Figure 3: SNMPGet Command
This command is also used to display sysObjectID.0 content and MIB objects for
ilomCtrlDateAndTime. As shown in the figure above, MIB file name is awarded for every
MIB object. The following MIB object descriptions are extracted from MIB files.
sysName- this is the name given to a managed node administratively. It is a fully qualified
domain name.
sysObjectID- authoritative identification of the vendor of the network management
subsystem held in the entity. This value is assigned in the SMI enterprise sub-tree and gives
an unambiguous and easy way of identifying what type of box is being managed.
ilomCtrlDataAndTime- time and date of the device.
Snmpwalk command
This command automatically executes an array of chained GetNext requests. It is basically a
command used to save work. Rather than executing several snmpgetnext commands, one for
every node in a sub-tree, one can just issue one snmpwalk command on the root node of the
sub-tree and the command gets the value for each sub-tree node. For instance:
The output of this command is as shown below
Figure 3: SNMPGet Command
This command is also used to display sysObjectID.0 content and MIB objects for
ilomCtrlDateAndTime. As shown in the figure above, MIB file name is awarded for every
MIB object. The following MIB object descriptions are extracted from MIB files.
sysName- this is the name given to a managed node administratively. It is a fully qualified
domain name.
sysObjectID- authoritative identification of the vendor of the network management
subsystem held in the entity. This value is assigned in the SMI enterprise sub-tree and gives
an unambiguous and easy way of identifying what type of box is being managed.
ilomCtrlDataAndTime- time and date of the device.
Snmpwalk command
This command automatically executes an array of chained GetNext requests. It is basically a
command used to save work. Rather than executing several snmpgetnext commands, one for
every node in a sub-tree, one can just issue one snmpwalk command on the root node of the
sub-tree and the command gets the value for each sub-tree node. For instance:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SNMP 7
Figure 4: SNMPWalk Command
Snmpbulkwalk command
This command employs the use of GETBULK SNMP protocol element to request
information of the entire network entity. Through repeater specification, the command can
pack many objects into the packets. As compared to snmpwalk command, snmpbulkwalk
command is faster.
The example below shows snmpwalk command with approximate begin and stop time
stamps.
Figure 5SNMPWalk Command with Approximate Start and Stop Time Stamps
The next example shows the same operation but this time using snmpbulkwalk command.
Figure 4: SNMPWalk Command
Snmpbulkwalk command
This command employs the use of GETBULK SNMP protocol element to request
information of the entire network entity. Through repeater specification, the command can
pack many objects into the packets. As compared to snmpwalk command, snmpbulkwalk
command is faster.
The example below shows snmpwalk command with approximate begin and stop time
stamps.
Figure 5SNMPWalk Command with Approximate Start and Stop Time Stamps
The next example shows the same operation but this time using snmpbulkwalk command.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SNMP 8
Figure 6: SNMPBulkWalk Command
From the two examples we can see that snmpbulk command is faster than snsmpwalk
command.
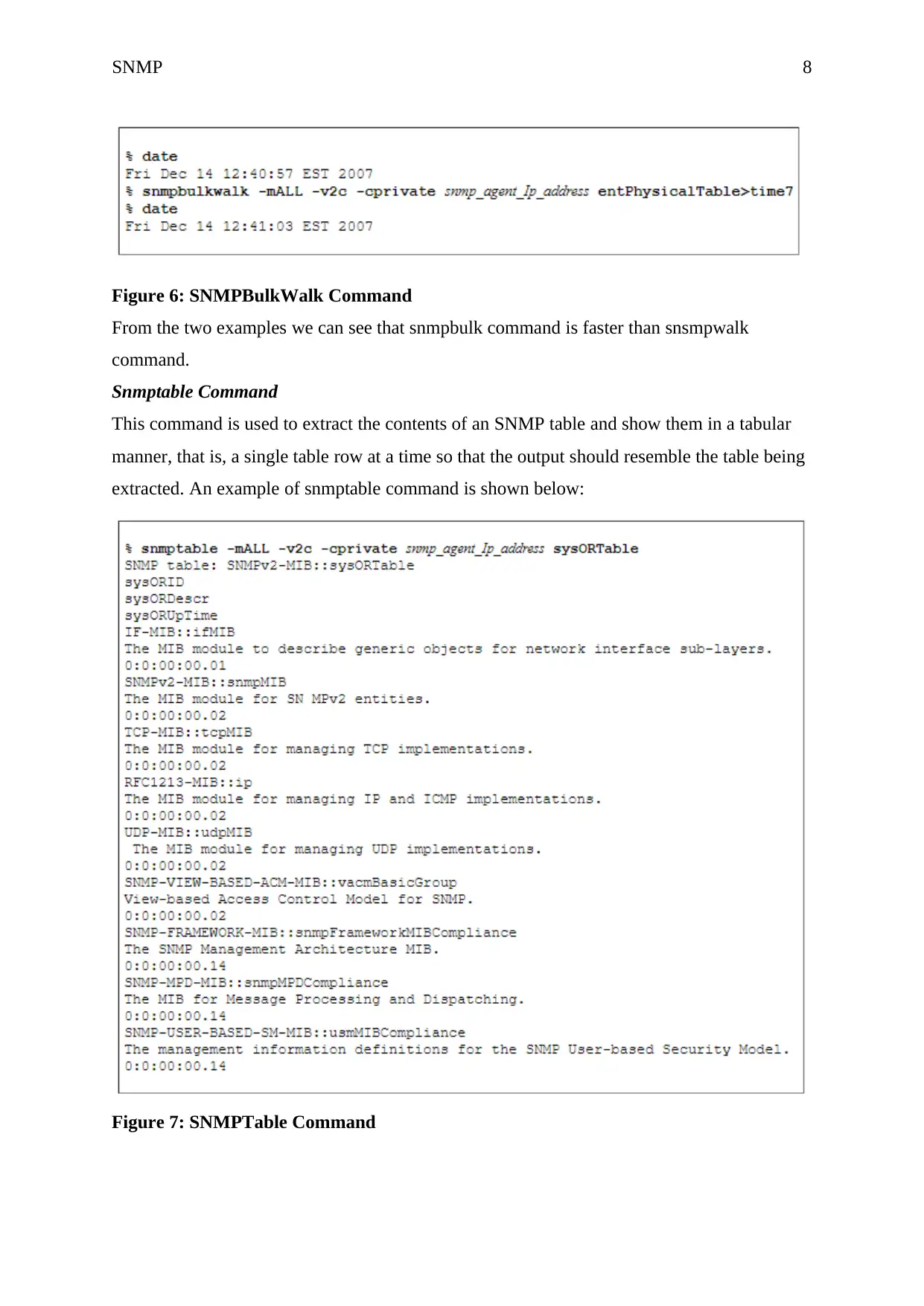
Snmptable Command
This command is used to extract the contents of an SNMP table and show them in a tabular
manner, that is, a single table row at a time so that the output should resemble the table being
extracted. An example of snmptable command is shown below:
Figure 7: SNMPTable Command
Figure 6: SNMPBulkWalk Command
From the two examples we can see that snmpbulk command is faster than snsmpwalk
command.
Snmptable Command
This command is used to extract the contents of an SNMP table and show them in a tabular
manner, that is, a single table row at a time so that the output should resemble the table being
extracted. An example of snmptable command is shown below:
Figure 7: SNMPTable Command

SNMP 9
Snmptable command is only relevant to MIB table objects unlike the rest of the commands
which can be used in any MIB object. -Ci and -Cb options are used in the snmptable
command example given above.
Snmpset command
Snmpset command has a syntax that is almost similar to that of snmpget command, but the
commands are relatively different. The snmpset command is used to write the value specified
to the object ID while snmpget command is used to read the values for the specified object
ID. The example below shows how snmpset and snmpget commands are used together.
Figure 8: SNMPSet and SNMPGet Commands
Snmptrapd Command
This command is used in SNMP application that logs and receives Inform messages and
SNMP Trap.
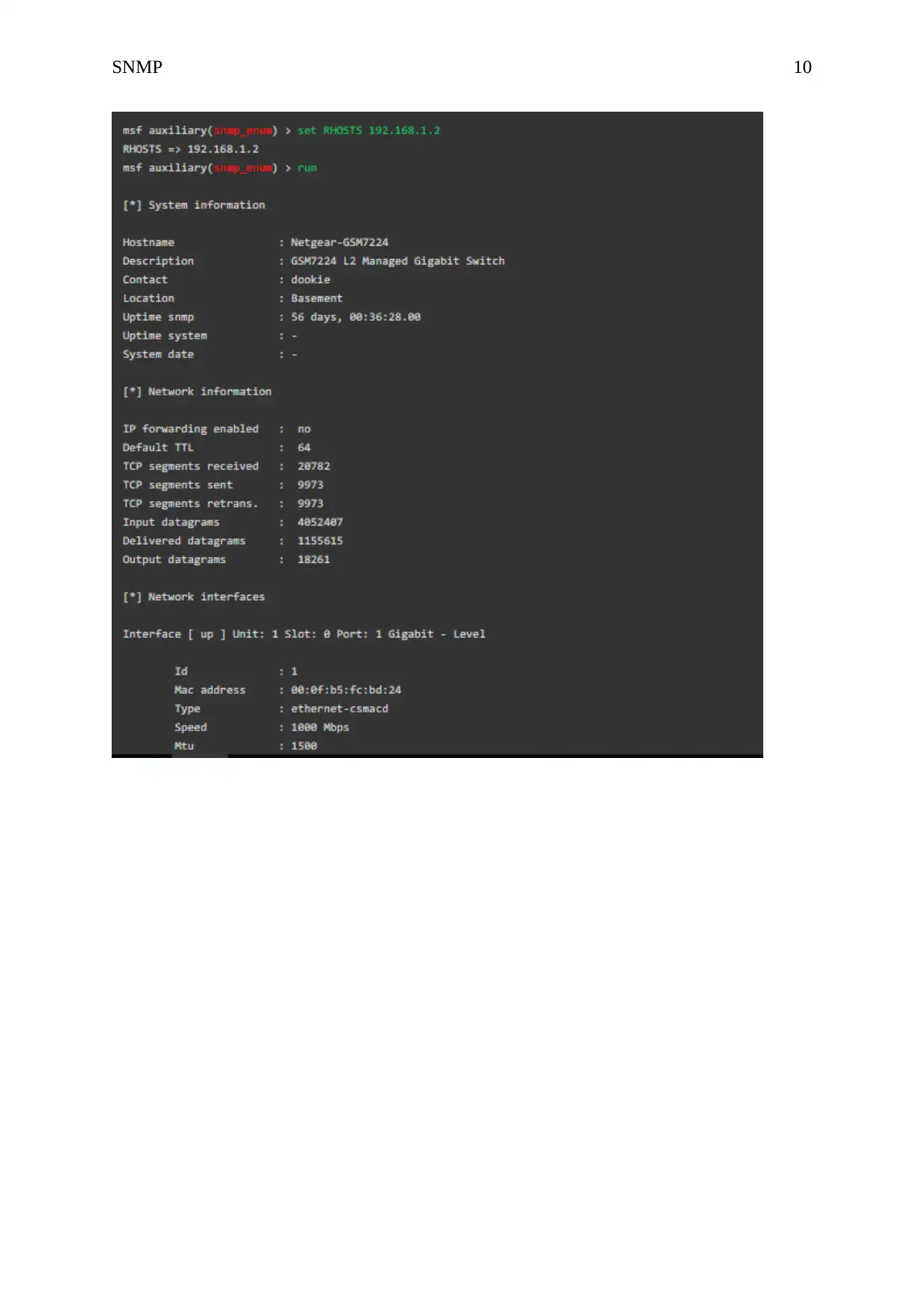
Assessing Target Hosts Using SNMP
The first host assessed using SNMP command is a switch. The following output was shown.
Snmptable command is only relevant to MIB table objects unlike the rest of the commands
which can be used in any MIB object. -Ci and -Cb options are used in the snmptable
command example given above.
Snmpset command
Snmpset command has a syntax that is almost similar to that of snmpget command, but the
commands are relatively different. The snmpset command is used to write the value specified
to the object ID while snmpget command is used to read the values for the specified object
ID. The example below shows how snmpset and snmpget commands are used together.
Figure 8: SNMPSet and SNMPGet Commands
Snmptrapd Command
This command is used in SNMP application that logs and receives Inform messages and
SNMP Trap.
Assessing Target Hosts Using SNMP
The first host assessed using SNMP command is a switch. The following output was shown.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
SNMP 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SNMP 11
a. Number of network interfaces 1
b. Number of datagrams/packets
received
4052407
c. Number of ping messages received
by the target host
64
d. Network Devices connected to the
switch
1
e. How long has the SNMP agent been
running?
56 days, 00:36:28.00
f. How many datagrams have been
sent by the target host?
18261
a. Number of network interfaces 1
b. Number of datagrams/packets
received
4052407
c. Number of ping messages received
by the target host
64
d. Network Devices connected to the
switch
1
e. How long has the SNMP agent been
running?
56 days, 00:36:28.00
f. How many datagrams have been
sent by the target host?
18261
SNMP 12
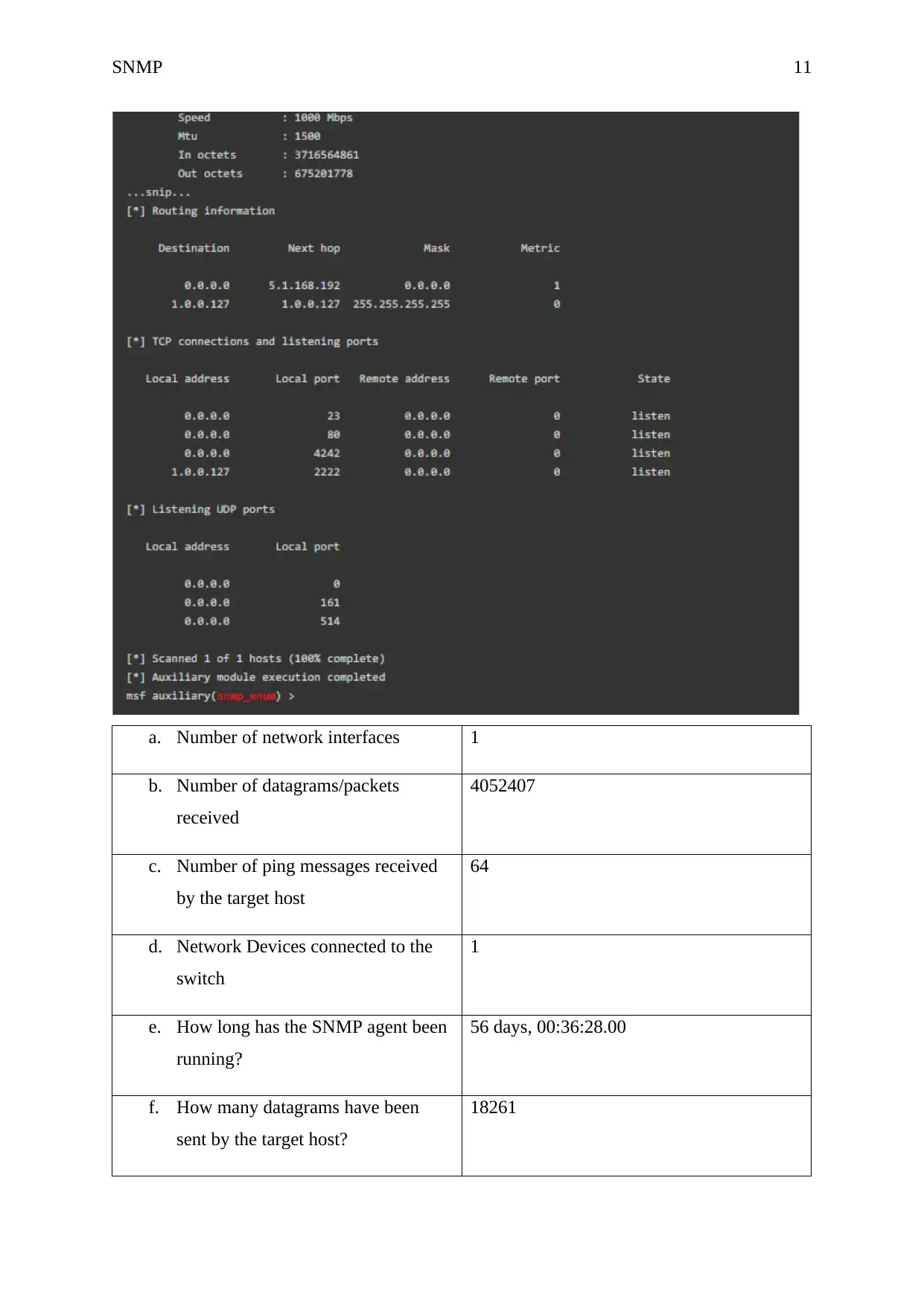
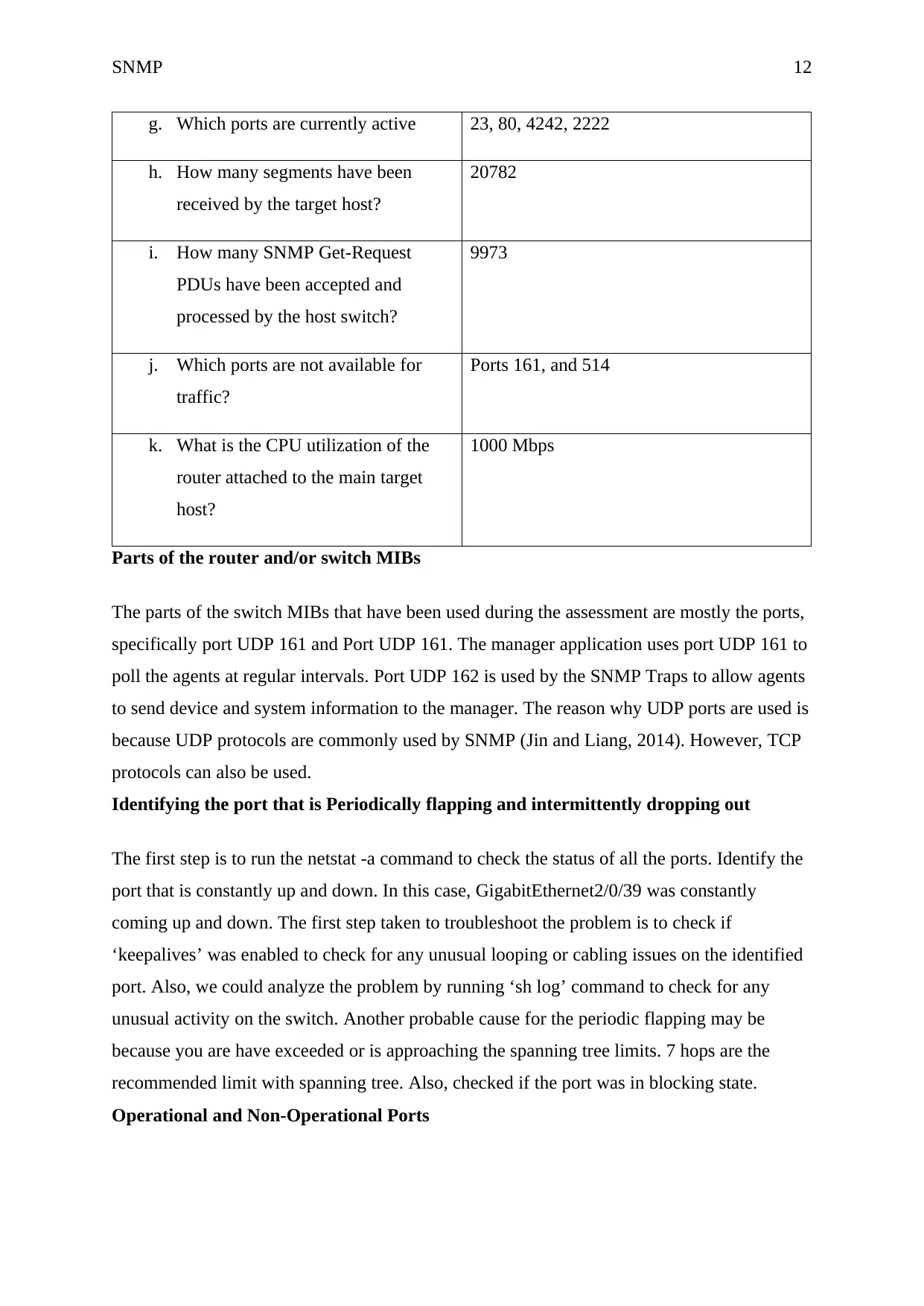
g. Which ports are currently active 23, 80, 4242, 2222
h. How many segments have been
received by the target host?
20782
i. How many SNMP Get-Request
PDUs have been accepted and
processed by the host switch?
9973
j. Which ports are not available for
traffic?
Ports 161, and 514
k. What is the CPU utilization of the
router attached to the main target
host?
1000 Mbps
Parts of the router and/or switch MIBs
The parts of the switch MIBs that have been used during the assessment are mostly the ports,
specifically port UDP 161 and Port UDP 161. The manager application uses port UDP 161 to
poll the agents at regular intervals. Port UDP 162 is used by the SNMP Traps to allow agents
to send device and system information to the manager. The reason why UDP ports are used is
because UDP protocols are commonly used by SNMP (Jin and Liang, 2014). However, TCP
protocols can also be used.
Identifying the port that is Periodically flapping and intermittently dropping out
The first step is to run the netstat -a command to check the status of all the ports. Identify the
port that is constantly up and down. In this case, GigabitEthernet2/0/39 was constantly
coming up and down. The first step taken to troubleshoot the problem is to check if
‘keepalives’ was enabled to check for any unusual looping or cabling issues on the identified
port. Also, we could analyze the problem by running ‘sh log’ command to check for any
unusual activity on the switch. Another probable cause for the periodic flapping may be
because you are have exceeded or is approaching the spanning tree limits. 7 hops are the
recommended limit with spanning tree. Also, checked if the port was in blocking state.
Operational and Non-Operational Ports
g. Which ports are currently active 23, 80, 4242, 2222
h. How many segments have been
received by the target host?
20782
i. How many SNMP Get-Request
PDUs have been accepted and
processed by the host switch?
9973
j. Which ports are not available for
traffic?
Ports 161, and 514
k. What is the CPU utilization of the
router attached to the main target
host?
1000 Mbps
Parts of the router and/or switch MIBs
The parts of the switch MIBs that have been used during the assessment are mostly the ports,
specifically port UDP 161 and Port UDP 161. The manager application uses port UDP 161 to
poll the agents at regular intervals. Port UDP 162 is used by the SNMP Traps to allow agents
to send device and system information to the manager. The reason why UDP ports are used is
because UDP protocols are commonly used by SNMP (Jin and Liang, 2014). However, TCP
protocols can also be used.
Identifying the port that is Periodically flapping and intermittently dropping out
The first step is to run the netstat -a command to check the status of all the ports. Identify the
port that is constantly up and down. In this case, GigabitEthernet2/0/39 was constantly
coming up and down. The first step taken to troubleshoot the problem is to check if
‘keepalives’ was enabled to check for any unusual looping or cabling issues on the identified
port. Also, we could analyze the problem by running ‘sh log’ command to check for any
unusual activity on the switch. Another probable cause for the periodic flapping may be
because you are have exceeded or is approaching the spanning tree limits. 7 hops are the
recommended limit with spanning tree. Also, checked if the port was in blocking state.
Operational and Non-Operational Ports
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





