Ethical Considerations: Risks in Social and Behavioral Research
VerifiedAdded on 2022/01/27
|9
|2513
|37
Homework Assignment
AI Summary
This assignment delves into the crucial topic of identifying, assessing, and minimizing risks of harm in social and behavioral science research. It highlights that these risks, unlike those in biomedical research, can be ambiguous and unpredictable, often involving social, psychological, economic, or legal consequences, and in rare cases, physical harm. The assignment outlines three main categories of risk: invasion of privacy, breach of confidentiality, and study procedures, illustrating them with examples. It emphasizes the importance of considering both the probability and magnitude of harm when assessing risk, while also acknowledging that risks are specific to time, situation, and subject population. The document stresses the need for researchers to objectively assess risk, balance risks against potential benefits, and minimize harm through measures like anonymous data collection, secure data storage, and Certificates of Confidentiality. The assignment underscores the role of Institutional Review Boards (IRBs) in providing independent risk assessments and ensuring ethical research practices.
One of the most important and challenging tasks researchers and Institutional
Review Boards (IRBs) face is identifying and evaluating risks of harm associated
with participation in research. Unlike biomedical research studies and clinical
trials in which the sources of risk may be more readily identifiable and
quantifiable, potential harms associated with taking part in social and behavioral
science research may be more ambiguous and less predictable, such as
individual reactions to certain events or questions. However, identifying and
assessing risks in such situations should be informed by a growing body of
research literature on risks associated with research participation.
The risks of harm typically associated with social and behavioral research are
social, psychological, economic, and legal in nature. However, in rare
circumstances, the risks may involve physical harm. For example, those who
study victims of domestic violence need to consider that individuals taking part in
the study may become the victims of retaliatory violence if the subjects'
involvement in the research is discovered.
It also is possible that when groups or communities rather than individuals are
the focus of a study, the group as a whole may be at risk of harm. For example,
research on the prevalence of individuals with HIV in communities may
stigmatize the community being studied.
Identification, assessment, and minimization of risk are paramount to the conduct
of ethical social and behavioral research.
Learning Objectives
By the end of this module, you should be able to:
Identify risks of harm associated with participation in social and behavioral
sciences research.
Distinguish between probability and magnitude of harm when assessing risk.
Apply the concepts of minimizing and managing risk.
Identifying Risks Associated with Participation in Social and
Behavioral Sciences Research
Review Boards (IRBs) face is identifying and evaluating risks of harm associated
with participation in research. Unlike biomedical research studies and clinical
trials in which the sources of risk may be more readily identifiable and
quantifiable, potential harms associated with taking part in social and behavioral
science research may be more ambiguous and less predictable, such as
individual reactions to certain events or questions. However, identifying and
assessing risks in such situations should be informed by a growing body of
research literature on risks associated with research participation.
The risks of harm typically associated with social and behavioral research are
social, psychological, economic, and legal in nature. However, in rare
circumstances, the risks may involve physical harm. For example, those who
study victims of domestic violence need to consider that individuals taking part in
the study may become the victims of retaliatory violence if the subjects'
involvement in the research is discovered.
It also is possible that when groups or communities rather than individuals are
the focus of a study, the group as a whole may be at risk of harm. For example,
research on the prevalence of individuals with HIV in communities may
stigmatize the community being studied.
Identification, assessment, and minimization of risk are paramount to the conduct
of ethical social and behavioral research.
Learning Objectives
By the end of this module, you should be able to:
Identify risks of harm associated with participation in social and behavioral
sciences research.
Distinguish between probability and magnitude of harm when assessing risk.
Apply the concepts of minimizing and managing risk.
Identifying Risks Associated with Participation in Social and
Behavioral Sciences Research
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
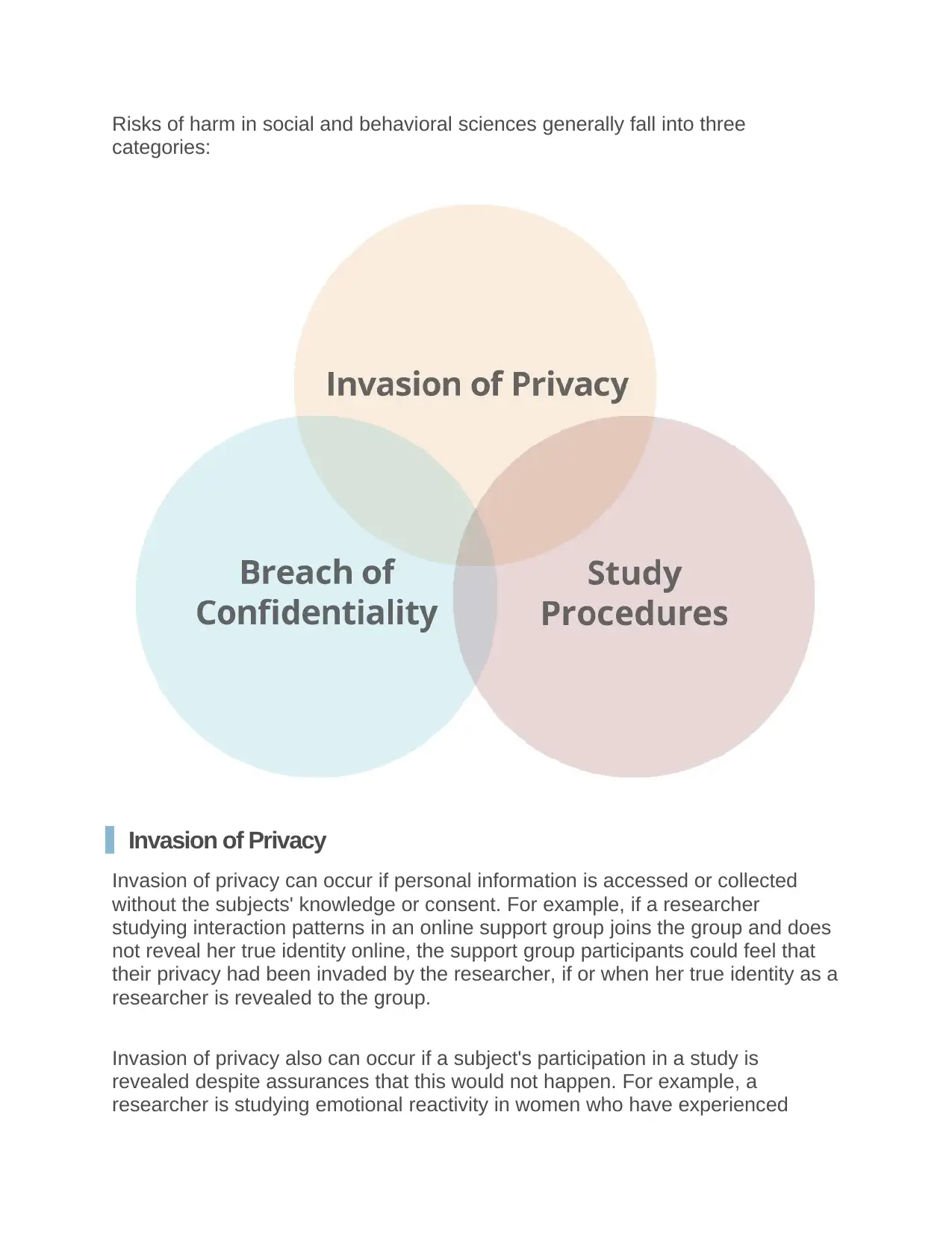
Risks of harm in social and behavioral sciences generally fall into three
categories:
Invasion of Privacy
Invasion of privacy can occur if personal information is accessed or collected
without the subjects' knowledge or consent. For example, if a researcher
studying interaction patterns in an online support group joins the group and does
not reveal her true identity online, the support group participants could feel that
their privacy had been invaded by the researcher, if or when her true identity as a
researcher is revealed to the group.
Invasion of privacy also can occur if a subject's participation in a study is
revealed despite assurances that this would not happen. For example, a
researcher is studying emotional reactivity in women who have experienced
categories:
Invasion of Privacy
Invasion of privacy can occur if personal information is accessed or collected
without the subjects' knowledge or consent. For example, if a researcher
studying interaction patterns in an online support group joins the group and does
not reveal her true identity online, the support group participants could feel that
their privacy had been invaded by the researcher, if or when her true identity as a
researcher is revealed to the group.
Invasion of privacy also can occur if a subject's participation in a study is
revealed despite assurances that this would not happen. For example, a
researcher is studying emotional reactivity in women who have experienced

sexual abuse. The research is conducted in a designated university lab on a
particular day each week. Another university staff person sees an acquaintance
entering the meeting room and therefore discovers that the acquaintance has
experienced sexual abuse.
Breach of Confidentiality
Perhaps the primary source of potential harm in
the social and behavioral sciences is that
information obtained by researchers could
adversely affect subjects if disclosed outside the
research setting. Confidentiality can be
compromised through an unauthorized release
of data, which could have a negative impact on
the subjects' psychological, social, or economic
status. For example:
Study Procedures
In some cases, simply taking part in research
can put subjects at risk. For example, if a researcher is conducting interviews
with individual gang members, it may be necessary to find places to meet where
other gang members could not observe the interaction.
Another situation in which merely taking part in research might pose some risk to
subjects is when there is a potential for a breach of confidentiality, not because of
inadequate confidentiality procedures on the part of the research team, but from
subjects themselves when data are collected in a group setting such as a focus
group. Even though participants typically are cautioned not to share information
outside the data collection setting, subjects should be made aware that the
researcher cannot guarantee confidentiality.
Often it is assumed that the very nature of the research inquiry can pose risk of
harm to subjects. For instance, when reviewing research plans that involve
asking subjects questions about trauma or abuse, IRB members may be
concerned about re-traumatization. However, current research findings indicate
that when appropriate protections are built into the study design, such as
ensuring that interviewers are trained to ask questions in a supportive, respectful
manner and respond to subjects' reactions appropriately, very few subjects were
particular day each week. Another university staff person sees an acquaintance
entering the meeting room and therefore discovers that the acquaintance has
experienced sexual abuse.
Breach of Confidentiality
Perhaps the primary source of potential harm in
the social and behavioral sciences is that
information obtained by researchers could
adversely affect subjects if disclosed outside the
research setting. Confidentiality can be
compromised through an unauthorized release
of data, which could have a negative impact on
the subjects' psychological, social, or economic
status. For example:
Study Procedures
In some cases, simply taking part in research
can put subjects at risk. For example, if a researcher is conducting interviews
with individual gang members, it may be necessary to find places to meet where
other gang members could not observe the interaction.
Another situation in which merely taking part in research might pose some risk to
subjects is when there is a potential for a breach of confidentiality, not because of
inadequate confidentiality procedures on the part of the research team, but from
subjects themselves when data are collected in a group setting such as a focus
group. Even though participants typically are cautioned not to share information
outside the data collection setting, subjects should be made aware that the
researcher cannot guarantee confidentiality.
Often it is assumed that the very nature of the research inquiry can pose risk of
harm to subjects. For instance, when reviewing research plans that involve
asking subjects questions about trauma or abuse, IRB members may be
concerned about re-traumatization. However, current research findings indicate
that when appropriate protections are built into the study design, such as
ensuring that interviewers are trained to ask questions in a supportive, respectful
manner and respond to subjects' reactions appropriately, very few subjects were
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

upset. In fact, most subjects, including those who may have experienced fleeting
negative emotions, reported feeling good about taking part in the study (Cromer
and Newman 2011). Thus, it is important to review the literature in a given field to
determine what, if any, risk of harm the research topic or design might pose to
the participant and what additional protections may be necessary.
Assessing Risk
Probability and Magnitude of Harm
When assessing risks of harm associated with participation in a research study,
there are two distinct elements of risk that must be considered. One is the
probability of harm - the likelihood that a specific harm might occur. The fact that
not all possible harms are equally probable should be taken into consideration
when assessing risk. The second element of risk is the magnitude or severity of
harm should it occur. The interaction between these two elements is a crucial
factor in determining the level of risk of harm in a study.
Often there is disparity between the probability and the magnitude of risk of harm
in a study. For example, a researcher wants to do a web-based survey of college
students to collect information about their sexual behavior and drug use. Direct
identifiers will not be collected; however, Internet Protocol (IP) addresses may be
present in the data set. Although the probability that an individual subject could
be identified is low, the magnitude of the possible risk of harm is high given the
sensitivity of the information.
Situation and Time
Risks of harm in research participation are specific to time, situation, and culture.
What may be a socially sensitive issue or topic at one time or place may not be
so at another time or place. For example, asking women if they have had an
abortion would carry very different risks in a country where abortion is a routine
negative emotions, reported feeling good about taking part in the study (Cromer
and Newman 2011). Thus, it is important to review the literature in a given field to
determine what, if any, risk of harm the research topic or design might pose to
the participant and what additional protections may be necessary.
Assessing Risk
Probability and Magnitude of Harm
When assessing risks of harm associated with participation in a research study,
there are two distinct elements of risk that must be considered. One is the
probability of harm - the likelihood that a specific harm might occur. The fact that
not all possible harms are equally probable should be taken into consideration
when assessing risk. The second element of risk is the magnitude or severity of
harm should it occur. The interaction between these two elements is a crucial
factor in determining the level of risk of harm in a study.
Often there is disparity between the probability and the magnitude of risk of harm
in a study. For example, a researcher wants to do a web-based survey of college
students to collect information about their sexual behavior and drug use. Direct
identifiers will not be collected; however, Internet Protocol (IP) addresses may be
present in the data set. Although the probability that an individual subject could
be identified is low, the magnitude of the possible risk of harm is high given the
sensitivity of the information.
Situation and Time
Risks of harm in research participation are specific to time, situation, and culture.
What may be a socially sensitive issue or topic at one time or place may not be
so at another time or place. For example, asking women if they have had an
abortion would carry very different risks in a country where abortion is a routine
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

medical practice, a country where it is illegal, or a country in which it is legal but
the issue is fraught with religious and political controversy.
Subject Population
Risks of harm will differ according to the subject population, too. Consider this
case: A study on the efficacy of a behavioral intervention for smoking cessation
involves both adults and teenagers. Purchasing tobacco products is generally
illegal for persons under 18 years of age. For adults, however, it is a health
hazard, but not an illegal activity. Thus, any assessment of the risk for teenagers
will have to consider that the research focuses on an illegal activity.
Similarly, a survey about sexually transmitted diseases may carry different risks
for different subject populations.
Assessing Risk Objectively
It may be challenging for researchers or potential subjects to assess risk
objectively.
Researchers
People, including researchers, may underestimate risks involved in activities with
which they are familiar and overestimate the benefit of things that are important
to them.
Potential Subjects
Regardless of the true probability of harm, research indicates that when potential
harms are severe, people tend to overestimate the probability. When potential
harms are less severe, such as embarrassment, people tend to underestimate
the probability.
An independent assessment of risk is critical. One function of IRBs is to provide
this independent assessment.
Balancing Risks and Potential Benefits
the issue is fraught with religious and political controversy.
Subject Population
Risks of harm will differ according to the subject population, too. Consider this
case: A study on the efficacy of a behavioral intervention for smoking cessation
involves both adults and teenagers. Purchasing tobacco products is generally
illegal for persons under 18 years of age. For adults, however, it is a health
hazard, but not an illegal activity. Thus, any assessment of the risk for teenagers
will have to consider that the research focuses on an illegal activity.
Similarly, a survey about sexually transmitted diseases may carry different risks
for different subject populations.
Assessing Risk Objectively
It may be challenging for researchers or potential subjects to assess risk
objectively.
Researchers
People, including researchers, may underestimate risks involved in activities with
which they are familiar and overestimate the benefit of things that are important
to them.
Potential Subjects
Regardless of the true probability of harm, research indicates that when potential
harms are severe, people tend to overestimate the probability. When potential
harms are less severe, such as embarrassment, people tend to underestimate
the probability.
An independent assessment of risk is critical. One function of IRBs is to provide
this independent assessment.
Balancing Risks and Potential Benefits
Federal regulations, based on the ethical principle of beneficence, require that
risks of harm associated with research are reasonable in relation to the potential
benefits (Protection of Human Subjects 2018).
A great deal of research in the social and behavioral sciences offers little
potential for direct benefits to the subjects themselves. The benefits of the
research often lie in the importance of the knowledge to be gained, the
contributions it makes to science, or the contributions to society in general. There
also might be cases in which a specific community, rather than individual
subjects, benefits from the research. This should be balanced with the fact that
most research in the social and behavioral sciences poses little or no risk of harm
to the individual subject.
In addition, regulations stipulate that risks of harm must be minimized to the
extent possible, consistent with sound research design (Protection of Human
Subjects 2018).
In order to minimize risk, potential research subjects need to be given sufficient
information to make a decision about whether they are willing to accept risks and
participate in the research. If research questions will be of a sensitive nature,
subjects need to be forewarned. Subjects also need to know what steps will be
taken to protect confidential information, including disposition of recorded
material. Any limits to the extent to which a researcher can protect identifiable
personal information should be clearly explained. State and local laws may limit
risks of harm associated with research are reasonable in relation to the potential
benefits (Protection of Human Subjects 2018).
A great deal of research in the social and behavioral sciences offers little
potential for direct benefits to the subjects themselves. The benefits of the
research often lie in the importance of the knowledge to be gained, the
contributions it makes to science, or the contributions to society in general. There
also might be cases in which a specific community, rather than individual
subjects, benefits from the research. This should be balanced with the fact that
most research in the social and behavioral sciences poses little or no risk of harm
to the individual subject.
In addition, regulations stipulate that risks of harm must be minimized to the
extent possible, consistent with sound research design (Protection of Human
Subjects 2018).
In order to minimize risk, potential research subjects need to be given sufficient
information to make a decision about whether they are willing to accept risks and
participate in the research. If research questions will be of a sensitive nature,
subjects need to be forewarned. Subjects also need to know what steps will be
taken to protect confidential information, including disposition of recorded
material. Any limits to the extent to which a researcher can protect identifiable
personal information should be clearly explained. State and local laws may limit
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

confidentiality, such as reporting requirements for child and elder abuse.
Confidentiality cannot be guaranteed for information shared in a focus group.
Minimizing and Managing Risk
It is important to minimize and manage the risks of harm in the research study.
Researchers and IRBs should assess the potential risks of harm in the study to
determine the best minimization and management plan.
When the Primary Source of Risk Is the Data
When a possible disclosure of subject
responses is the primary source of potential
harm, collecting data anonymously may provide
the best protection. For example, a mailed
survey can be constructed without a follow up
procedure, thereby negating the need for
identifiers.
If, however, the study design makes the
collection of identifiers necessary, for example a
longitudinal study, safeguarding the data from
unauthorized access can be accomplished in various ways, including:
Use of as few direct identifiers as practical.
Remove all direct identifiers as soon as possible.
Substitute codes for identifiers.
Maintain code lists and data files in separate secure locations.
Use accepted methods to protect against indirect identification, such as
aggregate reporting or pseudonyms.
Use and protect computer passwords.
Encrypt transmitted and stored data.
Access and store data on computers without internet connections.
Minimize procedures involving transferring direct identifiers between
persons.
Obtain a Certificate of Confidentiality.
In the past, when data were usually recorded and stored on paper and/or devices
such as floppy disks, researchers restricted access to data by storing the records
in locked file cabinets, in locked offices. With increasing use of digital
technologies to acquire, transmit, analyze, and store data, data security has
Confidentiality cannot be guaranteed for information shared in a focus group.
Minimizing and Managing Risk
It is important to minimize and manage the risks of harm in the research study.
Researchers and IRBs should assess the potential risks of harm in the study to
determine the best minimization and management plan.
When the Primary Source of Risk Is the Data
When a possible disclosure of subject
responses is the primary source of potential
harm, collecting data anonymously may provide
the best protection. For example, a mailed
survey can be constructed without a follow up
procedure, thereby negating the need for
identifiers.
If, however, the study design makes the
collection of identifiers necessary, for example a
longitudinal study, safeguarding the data from
unauthorized access can be accomplished in various ways, including:
Use of as few direct identifiers as practical.
Remove all direct identifiers as soon as possible.
Substitute codes for identifiers.
Maintain code lists and data files in separate secure locations.
Use accepted methods to protect against indirect identification, such as
aggregate reporting or pseudonyms.
Use and protect computer passwords.
Encrypt transmitted and stored data.
Access and store data on computers without internet connections.
Minimize procedures involving transferring direct identifiers between
persons.
Obtain a Certificate of Confidentiality.
In the past, when data were usually recorded and stored on paper and/or devices
such as floppy disks, researchers restricted access to data by storing the records
in locked file cabinets, in locked offices. With increasing use of digital
technologies to acquire, transmit, analyze, and store data, data security has
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

become much more complex. Researchers are not often information technology
(IT) experts. Therefore, research teams should consult with their institutional IT
security contacts for guidance regarding the most secure means of obtaining,
transferring, analyzing, and storing data when the primary source of risk stems
from a security breach.
Certificates of Confidentiality
Certificates of Confidentiality are issued by the National Institutes of Health (NIH)
to protect identifiable research information from compelled disclosure.
Certificates of Confidentiality may be obtained for any research, regardless of
funding, so long as the research is relevant to the mission of the NIH (an agency
of the U.S. Department of Health and Human Services [HHS]).
Certificates of Confidentiality may be granted for studies collecting information
that, if disclosed, could have adverse consequences for subjects or damage their
financial standing, employability, insurability, or reputation.
A Certificate of Confidentiality will allow the researcher, and others who have
access to research records, to be protected from required disclosure of
identifying information on research participants in: civil, criminal, administrative,
legislative, or other proceedings, whether at the federal, state, or local level.
The kinds of information that can be protected include:
Substance abuse or other illegal behaviors
Sexual attitudes, preferences, or practices
Genetic information
Psychological health
(IT) experts. Therefore, research teams should consult with their institutional IT
security contacts for guidance regarding the most secure means of obtaining,
transferring, analyzing, and storing data when the primary source of risk stems
from a security breach.
Certificates of Confidentiality
Certificates of Confidentiality are issued by the National Institutes of Health (NIH)
to protect identifiable research information from compelled disclosure.
Certificates of Confidentiality may be obtained for any research, regardless of
funding, so long as the research is relevant to the mission of the NIH (an agency
of the U.S. Department of Health and Human Services [HHS]).
Certificates of Confidentiality may be granted for studies collecting information
that, if disclosed, could have adverse consequences for subjects or damage their
financial standing, employability, insurability, or reputation.
A Certificate of Confidentiality will allow the researcher, and others who have
access to research records, to be protected from required disclosure of
identifying information on research participants in: civil, criminal, administrative,
legislative, or other proceedings, whether at the federal, state, or local level.
The kinds of information that can be protected include:
Substance abuse or other illegal behaviors
Sexual attitudes, preferences, or practices
Genetic information
Psychological health

Certificates of Confidentiality do not override the requirement to report the
suspicion of child abuse or neglect, or any other state-mandated reporting
requirements, such as elder abuse.
Other federal agencies, such as the Department of Justice, provide agency-
specific protections that apply to research conducted or funded by the agency.
Under a policy issued 7 September 2017 (effective 1 October 2017), NIH-funded
investigators do not need to apply for a Certificate of Confidentiality, nor will they
receive a document certificate. The NIH issues Certificates of Confidentiality
automatically for “NIH funded grants, cooperative agreements, contracts and
intramural research projects research funded wholly or in part by the NIH that
collects or uses identifiable, sensitive information” (NIH 2017). Certificates of
Confidentiality contain conditions for disclosure of the identifiable, sensitive
information that the investigator must comply with, including more restrictive
requirements for disclosure in the new policy.
The Certificates of Confidentiality policy remains the same for non-federally
funded research, in that investigators must apply for a Certificate of
Confidentiality from the NIH or other HHS agency for specific research studies.
Researchers must inform subjects about the protections and limitations provided
with a Certificate of Confidentiality.
When the Primary Source of Risk Is the Consent Document
Subjects may be placed at risk if others know
they are taking part in a study of a stigmatizing
or illegal activity. If the consent form is the only
document that links the participants to the study,
one way to diminish their risk of exposure is to
consider applying to the IRB for a waiver of the
requirement to document consent. A waiver of
documentation of consent does not imply that
any of the required elements of consent are
waived. The elements of consent must be
provided in some fashion such as in a cover letter, informational sheet, or verbal
script.
suspicion of child abuse or neglect, or any other state-mandated reporting
requirements, such as elder abuse.
Other federal agencies, such as the Department of Justice, provide agency-
specific protections that apply to research conducted or funded by the agency.
Under a policy issued 7 September 2017 (effective 1 October 2017), NIH-funded
investigators do not need to apply for a Certificate of Confidentiality, nor will they
receive a document certificate. The NIH issues Certificates of Confidentiality
automatically for “NIH funded grants, cooperative agreements, contracts and
intramural research projects research funded wholly or in part by the NIH that
collects or uses identifiable, sensitive information” (NIH 2017). Certificates of
Confidentiality contain conditions for disclosure of the identifiable, sensitive
information that the investigator must comply with, including more restrictive
requirements for disclosure in the new policy.
The Certificates of Confidentiality policy remains the same for non-federally
funded research, in that investigators must apply for a Certificate of
Confidentiality from the NIH or other HHS agency for specific research studies.
Researchers must inform subjects about the protections and limitations provided
with a Certificate of Confidentiality.
When the Primary Source of Risk Is the Consent Document
Subjects may be placed at risk if others know
they are taking part in a study of a stigmatizing
or illegal activity. If the consent form is the only
document that links the participants to the study,
one way to diminish their risk of exposure is to
consider applying to the IRB for a waiver of the
requirement to document consent. A waiver of
documentation of consent does not imply that
any of the required elements of consent are
waived. The elements of consent must be
provided in some fashion such as in a cover letter, informational sheet, or verbal
script.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





