Social Engineering: Phishing for a Solution: A Comprehensive Report
VerifiedAdded on 2020/04/15
|5
|2170
|343
Report
AI Summary
This research paper delves into the vulnerabilities associated with social engineering phishing attacks. It critically examines phishing attacks, presenting current trends and relevant facts. The report explores various preventive measures to mitigate the threats and risks of phishing attacks, offering several solutions to minimize their vulnerabilities, including DNS cache poisoning, user education, and legal aspects. The paper aims to assess end-user vulnerabilities, analyze the impact of phishing, and identify strategies for mitigation and future cybersecurity trends. The research includes a review of existing literature, a discussion of proposed solutions, and recommendations for future work to combat phishing attacks. The report underscores the importance of user awareness, security protocols, and the need for continuous vigilance in the face of evolving cyber threats, concluding with recommendations for future research and practical implementation of the strategies.
Running head: SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
Name of the Student
Name of the University
Author’s Note
ABSTRACT
This research paper discusses vulnerabilities involved in
social engineering phishing attacks. Phishing attack has
been critically discussed in the paper. The use of trends in
phishing attacks has been provided in the paper. Facts
related to phishing attacks have been included in the paper.
Preventive measures regarding threats and risks of phishing
attacks have been explained in the report. This paper deals
with several solutions to phishing attack to minimize its
vulnerabilities.
Keywords: Social Engineering, Phishing attacks and
DNS cache poisoning
INTRODUCTION
Social Engineering describes non-technical
intrusion for relying upon and manipulating people for
divulging into confidential information and performing
illegal activities. The effectiveness of social engineering is
high as it contains low risks activity by in directing an
attack on human loved ones. These tactics allow a social
engineer for avoiding suspicion [1]. However, this paper
will focus on Phishing attack. Phishing is a form of
deception by which social engineer makes an attempt for
acquiring sensitive information from the potential victim of
illegal activities.
Phishing started with attacking America Online
(AOL) users, which has become a common problem in the
current cyber world. Social engineering has been occurring
over the Internet after its existence [2]. Hackers steal
personal and private data of users by different methods.
The unawareness of keeping personal information of a user
is the weak point for phishing. Various countries are
suffering from cyber-attacks over the internet. According to
IBM’s X-Force researchers, the number of spam emails has
been increasing rapidly. The number of emails containing
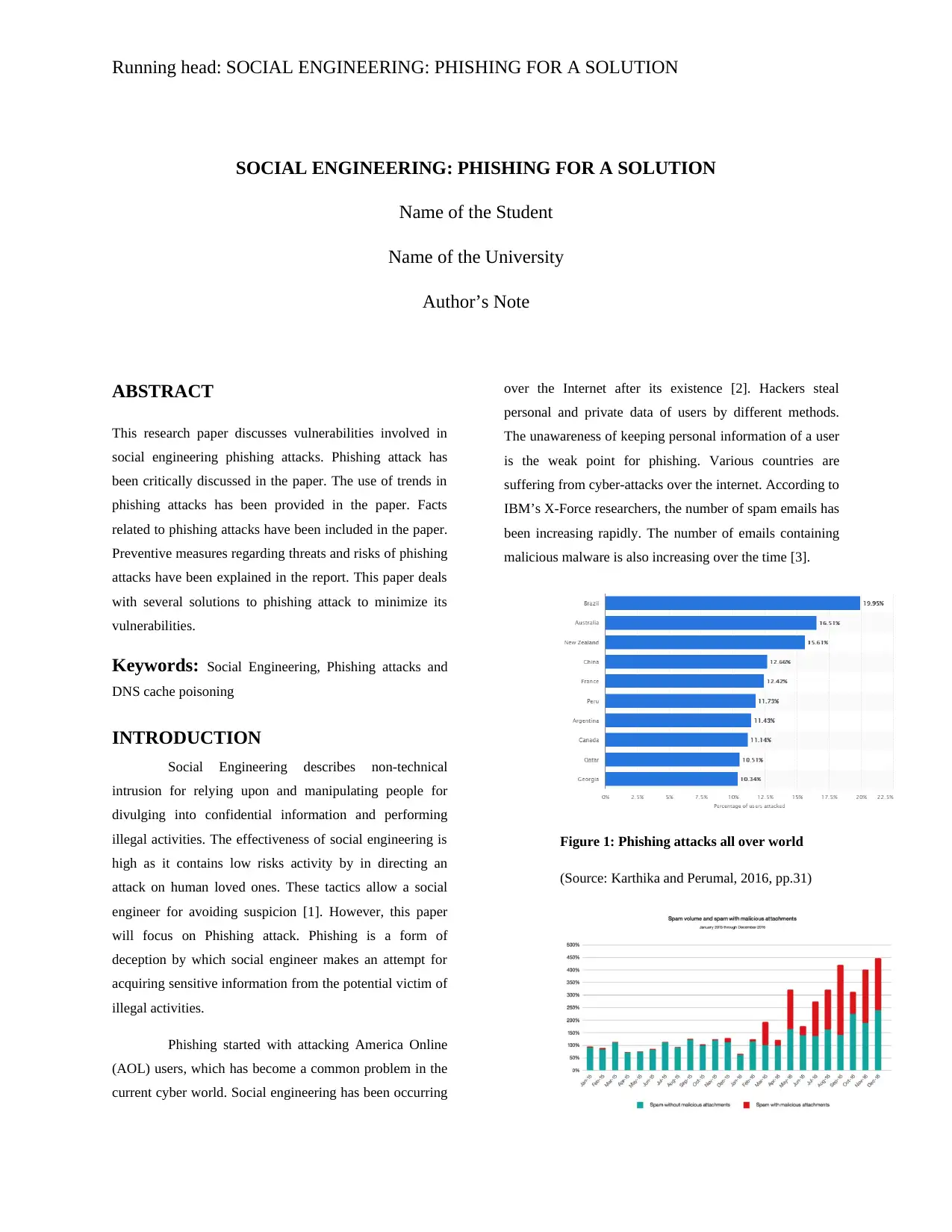
malicious malware is also increasing over the time [3].
Figure 1: Phishing attacks all over world
(Source: Karthika and Perumal, 2016, pp.31)
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
Name of the Student
Name of the University
Author’s Note
ABSTRACT
This research paper discusses vulnerabilities involved in
social engineering phishing attacks. Phishing attack has
been critically discussed in the paper. The use of trends in
phishing attacks has been provided in the paper. Facts
related to phishing attacks have been included in the paper.
Preventive measures regarding threats and risks of phishing
attacks have been explained in the report. This paper deals
with several solutions to phishing attack to minimize its
vulnerabilities.
Keywords: Social Engineering, Phishing attacks and
DNS cache poisoning
INTRODUCTION
Social Engineering describes non-technical
intrusion for relying upon and manipulating people for
divulging into confidential information and performing
illegal activities. The effectiveness of social engineering is
high as it contains low risks activity by in directing an
attack on human loved ones. These tactics allow a social
engineer for avoiding suspicion [1]. However, this paper
will focus on Phishing attack. Phishing is a form of
deception by which social engineer makes an attempt for
acquiring sensitive information from the potential victim of
illegal activities.
Phishing started with attacking America Online
(AOL) users, which has become a common problem in the
current cyber world. Social engineering has been occurring
over the Internet after its existence [2]. Hackers steal
personal and private data of users by different methods.
The unawareness of keeping personal information of a user
is the weak point for phishing. Various countries are
suffering from cyber-attacks over the internet. According to
IBM’s X-Force researchers, the number of spam emails has
been increasing rapidly. The number of emails containing
malicious malware is also increasing over the time [3].
Figure 1: Phishing attacks all over world
(Source: Karthika and Perumal, 2016, pp.31)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
Figure 2: Email including malicious malware
(Source: Ahn et al. 2016, pp. 2403)
The number of phishing reports has been 40,621
in August 2009 that has surpassed 38,514 by September
2007 [4]. The phishing attack has caused financial loss of
$3.2 billion to the government.
This research will deal with assessing
vulnerabilities of end users related to phishing based social
engineering attacks. The trends in phishing attacks will be
discussed in this paper. The factors responsible for phishing
attacks will be provided here. A proper previous literature
will be reviewed in this paper. This paper will use an online
survey-based research focusing on email aspect of
phishing. A proper analysis of collected data will be
analyzed during the research. The future recommendation
will be provided for mitigating issues related to phishing
attacks and further research will be done in future.
Research Aim
The aim of the research is to assess the vulnerabilities of
end users in relation to phishing based social engineering
attacks.
Research Objectives
The research objectives are discussed below:
To identify vulnerabilities in cyber world related
to phishing social engineering attacks
To critically analyze impact of phishing attack on
end users
To identify strategies for mitigating phishing
social engineering attacks
To recommend strategies for future work and
trends in cybersecurity
Research questions
The research questions are mentioned below:
What are the vulnerabilities in a cyber world
related to phishing social engineering attacks?
What is impact of the phishing attack on end
users?
What are strategies for mitigating phishing social
engineering attacks?
What are recommended strategies required for
future work and trends in cybersecurity?
LITERATURE REVIEW
Phishing is a type of social engineering in which
an attacker tries to fraudulently track data and information
of users over the internet. The use of spam emails and other
spam images are used for initiating phishing attacks. A
complete phishing attack contain three phases including
sending a large number of spam emails that direct users to
fake websites, collectors set up fake websites that track
private information of users and cashers extracts financial
data and information and misuse it.
Figure 3: Phishing information flow
(Source: Ahmed et al. 2017, pp.189))
Banks, financial institutions, social media users
and gaming sites users are a focus of phishers. Hackers are
targeting these users for getting her private information
along with bank account number for payment [5]. This has
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
Figure 2: Email including malicious malware
(Source: Ahn et al. 2016, pp. 2403)
The number of phishing reports has been 40,621
in August 2009 that has surpassed 38,514 by September
2007 [4]. The phishing attack has caused financial loss of
$3.2 billion to the government.
This research will deal with assessing
vulnerabilities of end users related to phishing based social
engineering attacks. The trends in phishing attacks will be
discussed in this paper. The factors responsible for phishing
attacks will be provided here. A proper previous literature
will be reviewed in this paper. This paper will use an online
survey-based research focusing on email aspect of
phishing. A proper analysis of collected data will be
analyzed during the research. The future recommendation
will be provided for mitigating issues related to phishing
attacks and further research will be done in future.
Research Aim
The aim of the research is to assess the vulnerabilities of
end users in relation to phishing based social engineering
attacks.
Research Objectives
The research objectives are discussed below:
To identify vulnerabilities in cyber world related
to phishing social engineering attacks
To critically analyze impact of phishing attack on
end users
To identify strategies for mitigating phishing
social engineering attacks
To recommend strategies for future work and
trends in cybersecurity
Research questions
The research questions are mentioned below:
What are the vulnerabilities in a cyber world
related to phishing social engineering attacks?
What is impact of the phishing attack on end
users?
What are strategies for mitigating phishing social
engineering attacks?
What are recommended strategies required for
future work and trends in cybersecurity?
LITERATURE REVIEW
Phishing is a type of social engineering in which
an attacker tries to fraudulently track data and information
of users over the internet. The use of spam emails and other
spam images are used for initiating phishing attacks. A
complete phishing attack contain three phases including
sending a large number of spam emails that direct users to
fake websites, collectors set up fake websites that track
private information of users and cashers extracts financial
data and information and misuse it.
Figure 3: Phishing information flow
(Source: Ahmed et al. 2017, pp.189))
Banks, financial institutions, social media users
and gaming sites users are a focus of phishers. Hackers are
targeting these users for getting her private information
along with bank account number for payment [5]. This has

2
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
created various threats and risks in the cyber world. The
U.S. remains the largest host of phishing, accounting for
43% of phishing sites reported in January 2012. Next was
Germany at 6%, followed by Australia, Spain, Brazil,
Canada, the U.K., France, Netherlands, and Russia [6].
On the other hand, phishing can be done for
checking security protocols of companies and security
organizations. However, this technique is mostly used for
illegal attacks over the internet [9]. IT-related course is
provided online that helps in maintaining the security of
data and information of users. This also prevents phishing
attacks by educating users about different attacks.
PROPOSED SOLUTION
Various strategies are made for preventing users
form phishing attacks. These strategies might help in
maintaining a secure internet browsing for a user. Based on
limitations and vulnerabilities, some strategies are made for
mitigating threats of phishing attacks over the internet.
DNS Cache Poisoning
Domain Name System (DNS) is used for
converting IP addresses into a name of website and vice
versa. This help in a proper understanding of the user. It
helps in improving the performance of local ISPs and
client-side server [7]. The DNS cache poisoning tries to
feed cache of local DNS with incorrect records. This help
in hiding original record and address of a server. It provides
three services including key distribution, data origin
authentication and transaction.
User Education
Phishing creates several vulnerabilities including
technical solutions that can block phishing websites. The
use of firewalls, encryption and certificates by users help in
securing data and information over the server. The user has
to be educated with preventive measures from phishing
attacks. General information about phishing has to be
circulated to employees and another user in the company.
This helps in maintaining a secure look at spam emails and
websites [8]. The details of spam mails and messages and
fake websites have to be provided to employees that help
secure browsing of the internet. The threats and risks
involved in phishing attacks have to be educated to
employees of companies that help in maintaining a close
look at their messages and spam emails.
Legal aspects
Legislations against phishing have been
strengthening in the UK. The UK Fraud Act of 2005 deals
with various fraud cases over the internet [10]. It focuses
on several types of cyber-attacks including phishing
attacks. The Anti-Phishing Act of 2005 is a bill that was
initiated to minimize internet frauds involving fraudulently
for gathering personal information and financial data [11].
The bill proposed five-year jail for person or group caught.
Strong Authentication and authorization
Two-factor authentication is a security factor that
requires two or more authenticators. A security factor is
necessary for the online commerce company that is always
connected to the internet; therefore, the details of the
business and products have to be secured properly with the
help of two-factor authentication technique [12].
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
created various threats and risks in the cyber world. The
U.S. remains the largest host of phishing, accounting for
43% of phishing sites reported in January 2012. Next was
Germany at 6%, followed by Australia, Spain, Brazil,
Canada, the U.K., France, Netherlands, and Russia [6].
On the other hand, phishing can be done for
checking security protocols of companies and security
organizations. However, this technique is mostly used for
illegal attacks over the internet [9]. IT-related course is
provided online that helps in maintaining the security of
data and information of users. This also prevents phishing
attacks by educating users about different attacks.
PROPOSED SOLUTION
Various strategies are made for preventing users
form phishing attacks. These strategies might help in
maintaining a secure internet browsing for a user. Based on
limitations and vulnerabilities, some strategies are made for
mitigating threats of phishing attacks over the internet.
DNS Cache Poisoning
Domain Name System (DNS) is used for
converting IP addresses into a name of website and vice
versa. This help in a proper understanding of the user. It
helps in improving the performance of local ISPs and
client-side server [7]. The DNS cache poisoning tries to
feed cache of local DNS with incorrect records. This help
in hiding original record and address of a server. It provides
three services including key distribution, data origin
authentication and transaction.
User Education
Phishing creates several vulnerabilities including
technical solutions that can block phishing websites. The
use of firewalls, encryption and certificates by users help in
securing data and information over the server. The user has
to be educated with preventive measures from phishing
attacks. General information about phishing has to be
circulated to employees and another user in the company.
This helps in maintaining a secure look at spam emails and
websites [8]. The details of spam mails and messages and
fake websites have to be provided to employees that help
secure browsing of the internet. The threats and risks
involved in phishing attacks have to be educated to
employees of companies that help in maintaining a close
look at their messages and spam emails.
Legal aspects
Legislations against phishing have been
strengthening in the UK. The UK Fraud Act of 2005 deals
with various fraud cases over the internet [10]. It focuses
on several types of cyber-attacks including phishing
attacks. The Anti-Phishing Act of 2005 is a bill that was
initiated to minimize internet frauds involving fraudulently
for gathering personal information and financial data [11].
The bill proposed five-year jail for person or group caught.
Strong Authentication and authorization
Two-factor authentication is a security factor that
requires two or more authenticators. A security factor is
necessary for the online commerce company that is always
connected to the internet; therefore, the details of the
business and products have to be secured properly with the
help of two-factor authentication technique [12].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
RECOMMENDATIONS
The increase in the phishing attacks all over the
world have created an alarming situation for users and
organizations. It is recommended that company needs to
aware their employees and other users about the phishing
attack. The awareness campaign needs to be initiated by the
company and society related to cyber-attacks including
phishing. This helps in minimizing attacks in the world.
Customers need to be aware of vulnerabilities of phishing
attack over the internet. The company needs to have
security protocols that help in securing databases over the
internet. The user must know about various types of spam
emails and messages and do not share their personal and
private information over the internet, therefore, this might
help in minimizing phishing attacks over the internet.
CONCLUSION
It can be concluded that social engineering
phishing attack has been common all over the world that
has been damaging financial status of several companies
uses of the spam emails and messages has been increased in
the work. The users are not safe over the internet without
any security protocols. The hackers have been targeting
banks. Financial situation and social media users for the
phishing attack. The vulnerabilities of phishing attack have
been increased in few years. The use of various strategies
for mitigating vulnerabilities and limitations of phishing
attacks has been provided. The recommended strategies for
minimizing threats and risks of phishing attacks has been
provided in the research paper.
FUTURE WORK
The current research will focus on various vulnerabilities of
phishing attacks in social engineering. Different factors will
be discussed in this research based on phishing attack and
its impact on a business organization. The future research
might focus on practical implementation of these strategies
in the market for minimizing phishing attacks over the
internet. The future research might focus on improving
models to detect phishing websites and spam emails.
Several multi-factor and multi-channel authentication
methods might be discussed in future.
REFERENCES
[1] Vishwanath, Arun. "Examining the Distinct
Antecedents of E‐Mail Habits and its Influence
on the Outcomes of a Phishing Attack." Journal
of Computer‐Mediated Communication 20, no. 5
(2015): 570-584.
[2] Gupta, Surbhi, Abhishek Singhal, and Akanksha
Kapoor. "A literature survey on social
engineering attacks: Phishing attack."
In Computing, Communication and Automation
(ICCCA), 2016 International Conference on, pp.
537-540. IEEE, 2016.
[3] Ahmed, N. Syed Siraj, D. P. Acharjya, and
Sugata Sanyal. "A framework for phishing attack
identification using rough set and formal concept
analysis." International Journal of
Communication Networks and Distributed
Systems 18, no. 2 (2017): 186-212.
[4] Arachchilage, Nalin Asanka Gamagedara, and
Steve Love. "Security awareness of computer
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
RECOMMENDATIONS
The increase in the phishing attacks all over the
world have created an alarming situation for users and
organizations. It is recommended that company needs to
aware their employees and other users about the phishing
attack. The awareness campaign needs to be initiated by the
company and society related to cyber-attacks including
phishing. This helps in minimizing attacks in the world.
Customers need to be aware of vulnerabilities of phishing
attack over the internet. The company needs to have
security protocols that help in securing databases over the
internet. The user must know about various types of spam
emails and messages and do not share their personal and
private information over the internet, therefore, this might
help in minimizing phishing attacks over the internet.
CONCLUSION
It can be concluded that social engineering
phishing attack has been common all over the world that
has been damaging financial status of several companies
uses of the spam emails and messages has been increased in
the work. The users are not safe over the internet without
any security protocols. The hackers have been targeting
banks. Financial situation and social media users for the
phishing attack. The vulnerabilities of phishing attack have
been increased in few years. The use of various strategies
for mitigating vulnerabilities and limitations of phishing
attacks has been provided. The recommended strategies for
minimizing threats and risks of phishing attacks has been
provided in the research paper.
FUTURE WORK
The current research will focus on various vulnerabilities of
phishing attacks in social engineering. Different factors will
be discussed in this research based on phishing attack and
its impact on a business organization. The future research
might focus on practical implementation of these strategies
in the market for minimizing phishing attacks over the
internet. The future research might focus on improving
models to detect phishing websites and spam emails.
Several multi-factor and multi-channel authentication
methods might be discussed in future.
REFERENCES
[1] Vishwanath, Arun. "Examining the Distinct
Antecedents of E‐Mail Habits and its Influence
on the Outcomes of a Phishing Attack." Journal
of Computer‐Mediated Communication 20, no. 5
(2015): 570-584.
[2] Gupta, Surbhi, Abhishek Singhal, and Akanksha
Kapoor. "A literature survey on social
engineering attacks: Phishing attack."
In Computing, Communication and Automation
(ICCCA), 2016 International Conference on, pp.
537-540. IEEE, 2016.
[3] Ahmed, N. Syed Siraj, D. P. Acharjya, and
Sugata Sanyal. "A framework for phishing attack
identification using rough set and formal concept
analysis." International Journal of
Communication Networks and Distributed
Systems 18, no. 2 (2017): 186-212.
[4] Arachchilage, Nalin Asanka Gamagedara, and
Steve Love. "Security awareness of computer
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
users: A phishing threat avoidance
perspective." Computers in Human Behavior 38
(2014): 304-312.
[5] Karthika, L., and V. Perumal. "A study on
phishing attack in internet
banking." International journal of
Interdisciplinary in Engineering Science and
Technology 1, no. 2 (2016): 29-32.
[6] Arachchilage, Nalin Asanka Gamagedara, and
Steve Love. "A game design framework for
avoiding phishing attacks." Computers in Human
Behavior 29, no. 3 (2013): 706-714.
[7] Gupta, Surbhi, Abhishek Singhal, and Akanksha
Kapoor. "A literature survey on social
engineering attacks: Phishing attack."
In Computing, Communication and Automation
(ICCCA), 2016 International Conference on, pp.
537-540. IEEE, 2016.
[8] Ahmed, N. Syed Siraj, D. P. Acharjya, and
Sugata Sanyal. "A framework for phishing attack
identification using rough set and formal concept
analysis." International Journal of
Communication Networks and Distributed
Systems 18, no. 2 (2017): 186-212.
[9] Karthika, L., and V. Perumal. "A study on
phishing attack in internet
banking." International journal of
Interdisciplinary in Engineering Science and
Technology 1, no. 2 (2016): 29-32.
[10] Ahn, Woo Hyun, Sanghyeon Park, Jaewon Oh,
and Seung-Ho Lim. "Inishing: A UI phishing
attack to exploit the vulnerability of inotify in
Android smartphones." IEICE TRANSACTIONS
on Information and Systems 99, no. 9 (2016):
2404-2409.
[11] Kumar, J. Dileep, V. Srikanth, and L. Tejeswini.
"Email phishing attack mitigation using server
side email addon." Indian Journal of Science and
Technology 9, no. 19 (2016).
[12] Ekawade, Shalaka, Snehal Mule, and Uday
Patkar. "Phishing Attacks and Its
Preventions." Imperial Journal of
Interdisciplinary Research 2, no. 12 (2016).
SOCIAL ENGINEERING: PHISHING FOR A SOLUTION
users: A phishing threat avoidance
perspective." Computers in Human Behavior 38
(2014): 304-312.
[5] Karthika, L., and V. Perumal. "A study on
phishing attack in internet
banking." International journal of
Interdisciplinary in Engineering Science and
Technology 1, no. 2 (2016): 29-32.
[6] Arachchilage, Nalin Asanka Gamagedara, and
Steve Love. "A game design framework for
avoiding phishing attacks." Computers in Human
Behavior 29, no. 3 (2013): 706-714.
[7] Gupta, Surbhi, Abhishek Singhal, and Akanksha
Kapoor. "A literature survey on social
engineering attacks: Phishing attack."
In Computing, Communication and Automation
(ICCCA), 2016 International Conference on, pp.
537-540. IEEE, 2016.
[8] Ahmed, N. Syed Siraj, D. P. Acharjya, and
Sugata Sanyal. "A framework for phishing attack
identification using rough set and formal concept
analysis." International Journal of
Communication Networks and Distributed
Systems 18, no. 2 (2017): 186-212.
[9] Karthika, L., and V. Perumal. "A study on
phishing attack in internet
banking." International journal of
Interdisciplinary in Engineering Science and
Technology 1, no. 2 (2016): 29-32.
[10] Ahn, Woo Hyun, Sanghyeon Park, Jaewon Oh,
and Seung-Ho Lim. "Inishing: A UI phishing
attack to exploit the vulnerability of inotify in
Android smartphones." IEICE TRANSACTIONS
on Information and Systems 99, no. 9 (2016):
2404-2409.
[11] Kumar, J. Dileep, V. Srikanth, and L. Tejeswini.
"Email phishing attack mitigation using server
side email addon." Indian Journal of Science and
Technology 9, no. 19 (2016).
[12] Ekawade, Shalaka, Snehal Mule, and Uday
Patkar. "Phishing Attacks and Its
Preventions." Imperial Journal of
Interdisciplinary Research 2, no. 12 (2016).
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




