Social Media Analysis Using BYOD: Security and Recommendations
VerifiedAdded on 2020/05/01
|15
|4063
|339
Report
AI Summary
This report provides an analysis of social media using the Bring Your Own Device (BYOD) technology. It begins with an executive summary and table of contents, followed by an introduction to the topic. The report includes a literature review defining BYOD and its trends, alongside an analysis of social media platforms, discussing their advantages and disadvantages. The core of the report examines the impact of social media on BYOD, highlighting advantages such as increased productivity and disadvantages like security risks. It also details existing policies and concludes with recommendations for mitigating risks associated with BYOD implementation in a social media context. The report also references the various security threats associated with BYOD, and the various policies and measures that are being taken to mitigate them.

Running head: SOCIAL MEDIA ANALYSIS USING BYOD
Social media analysis using BYOD
Name of the student
Name of the University
Author Note
Social media analysis using BYOD
Name of the student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SOCIAL MEDIA ANALYSIS USING BYOD
Executive summary
The following report discusses about the topic of social media analysis by using the BYOD
technology. The BYOD stands for Bring Your Own device which will be later discussed in the
report. The report further includes the security problems associated with the use of this
technology in the social media platform. The analysis made in this report also includes the
various recommendations to be considered while going for an implementation of the social
media platform. Lastly, the issue associated with the BYOD technology is also discusses in this
report and the current measures that are being taken are also referenced in this report.
Page 1
Executive summary
The following report discusses about the topic of social media analysis by using the BYOD
technology. The BYOD stands for Bring Your Own device which will be later discussed in the
report. The report further includes the security problems associated with the use of this
technology in the social media platform. The analysis made in this report also includes the
various recommendations to be considered while going for an implementation of the social
media platform. Lastly, the issue associated with the BYOD technology is also discusses in this
report and the current measures that are being taken are also referenced in this report.
Page 1

2SOCIAL MEDIA ANALYSIS USING BYOD
Table of Contents
Introduction:....................................................................................................................................3
Literature review:.............................................................................................................................3
Definition of the BYOD (Bring Your Own Device) technology:...............................................3
Social media analysis:..................................................................................................................5
Impact of Social media on BYOD:..............................................................................................7
Recommendations:........................................................................................................................11
Conclusion:....................................................................................................................................11
References:....................................................................................................................................13
Page 2
Table of Contents
Introduction:....................................................................................................................................3
Literature review:.............................................................................................................................3
Definition of the BYOD (Bring Your Own Device) technology:...............................................3
Social media analysis:..................................................................................................................5
Impact of Social media on BYOD:..............................................................................................7
Recommendations:........................................................................................................................11
Conclusion:....................................................................................................................................11
References:....................................................................................................................................13
Page 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SOCIAL MEDIA ANALYSIS USING BYOD
Introduction:
Social media is used to represent a platform where people from all over the world are
used to increase their engagements on these platforms to connect to each other. This is a type of
technology used to facilitate better connection among people. The BYOD (Bring Your Own
Device) is used to define the practice of employment services where the staffs are allowed to
bring their own devices in their office premises. This report discusses about the implementation
of the BYOD concept in business applications for the use of a social media platform. The report
also includes the presence of the various issues regarding its use in this case. Lastly, the report
also includes a recommendation to be included for mitigating such requirements.
Literature review:
This section of the report discusses about the main topic of the assignment.
Definition of the BYOD (Bring Your Own Device) technology:
The technology BYOD, also known BYOT (Bring Your Own Technology), BYOP
(Bring Your Own Phone) or the BYOPC (Bring Your Own Personal Computer), is termed as the
policy or frameworks which are used in a company or business organization to permit the
employees to carry their own device for office works (Beckett 2014). These devices may include
their personal laptops, mobile phones or tablets which can be used for normal working with the
official data of the company or organization involved. This process is also known as the
consumerization of IT business process.
Trends in the technology:
In the year 2009, the BYOD technology was first introduced through the Intel
Corporation. This was mainly done to recognize the tendency of its employees to bring their own
devices to the office premises. This process was further implemented by the other companies like
the Citrix Systems in the year 2011 for addressing their business requirements.
In the modern times, the use of the personal devices has been adopted by almost all the
big multinational companies like the IBM. The main reason for the widespread adoption of the
Page 3
Introduction:
Social media is used to represent a platform where people from all over the world are
used to increase their engagements on these platforms to connect to each other. This is a type of
technology used to facilitate better connection among people. The BYOD (Bring Your Own
Device) is used to define the practice of employment services where the staffs are allowed to
bring their own devices in their office premises. This report discusses about the implementation
of the BYOD concept in business applications for the use of a social media platform. The report
also includes the presence of the various issues regarding its use in this case. Lastly, the report
also includes a recommendation to be included for mitigating such requirements.
Literature review:
This section of the report discusses about the main topic of the assignment.
Definition of the BYOD (Bring Your Own Device) technology:
The technology BYOD, also known BYOT (Bring Your Own Technology), BYOP
(Bring Your Own Phone) or the BYOPC (Bring Your Own Personal Computer), is termed as the
policy or frameworks which are used in a company or business organization to permit the
employees to carry their own device for office works (Beckett 2014). These devices may include
their personal laptops, mobile phones or tablets which can be used for normal working with the
official data of the company or organization involved. This process is also known as the
consumerization of IT business process.
Trends in the technology:
In the year 2009, the BYOD technology was first introduced through the Intel
Corporation. This was mainly done to recognize the tendency of its employees to bring their own
devices to the office premises. This process was further implemented by the other companies like
the Citrix Systems in the year 2011 for addressing their business requirements.
In the modern times, the use of the personal devices has been adopted by almost all the
big multinational companies like the IBM. The main reason for the widespread adoption of the
Page 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SOCIAL MEDIA ANALYSIS USING BYOD
BYOD program is that the use of this policy reduces the company’s requirement to stay updated
with the modern trends in the digital world.
Advantages:
The BYOD (Bring Your Own Device) has many advantages in the field of business and
applications. The program is considered to increase the productivity of the employees working in
the associated company. As an employee considers ease in working if they are allowed to operate
their own device in the company, the efficiency of doing increases which in turn increases the
productivity. Additionally, it is also considered that the morale of the employees is also increased
in case of BYOD adoption policies.
Furthermore, the use of the BYOD program is also considered to cause an increase in the
employee satisfaction (Afreen 2014). As a company policy involves an employee to use the
company device for professional works and the personal work using the personal devices, the
increase in strain to carry these two devices causes hindrance. Having one device for both the
professional and the personal work greatly increases the job satisfaction level of employees
which in turn is responsible for increasing the efficiency of the work.
This technology also removes the need for a company to upgrade their services to comply
with the modern trends in the market. As the employees already possess new types of devices for
their personal uses, the need for upgrading the present infrastructure is thus removed. This is also
another point for reducing the cost needed for installation and thus increases the profit margin of
a company or business organizations concerned.
Disadvantages:
Although the use of the BYOD program is essential for allowing the employees work
from anywhere, there are significant risks in the system which are to be addressed by the
company so as to ensure the safety of the information handling in the right hands.
The first disadvantage of the BYOD program is used to define the use of the personal
deices to get access to the information of the company (Berger 2013). The end node problem in
this case is the main problem of the program as the need to encrypt the connection is required.
Page 4
BYOD program is that the use of this policy reduces the company’s requirement to stay updated
with the modern trends in the digital world.
Advantages:
The BYOD (Bring Your Own Device) has many advantages in the field of business and
applications. The program is considered to increase the productivity of the employees working in
the associated company. As an employee considers ease in working if they are allowed to operate
their own device in the company, the efficiency of doing increases which in turn increases the
productivity. Additionally, it is also considered that the morale of the employees is also increased
in case of BYOD adoption policies.
Furthermore, the use of the BYOD program is also considered to cause an increase in the
employee satisfaction (Afreen 2014). As a company policy involves an employee to use the
company device for professional works and the personal work using the personal devices, the
increase in strain to carry these two devices causes hindrance. Having one device for both the
professional and the personal work greatly increases the job satisfaction level of employees
which in turn is responsible for increasing the efficiency of the work.
This technology also removes the need for a company to upgrade their services to comply
with the modern trends in the market. As the employees already possess new types of devices for
their personal uses, the need for upgrading the present infrastructure is thus removed. This is also
another point for reducing the cost needed for installation and thus increases the profit margin of
a company or business organizations concerned.
Disadvantages:
Although the use of the BYOD program is essential for allowing the employees work
from anywhere, there are significant risks in the system which are to be addressed by the
company so as to ensure the safety of the information handling in the right hands.
The first disadvantage of the BYOD program is used to define the use of the personal
deices to get access to the information of the company (Berger 2013). The end node problem in
this case is the main problem of the program as the need to encrypt the connection is required.
Page 4
5SOCIAL MEDIA ANALYSIS USING BYOD
Breaches are another prospect which has led to the emergence of various security
protocols to be addressed. In cases where an employee loses their personal device, the data
present in that phone can be hacked if the device falls in wrong hands. This is one point of
security issue present due to the emergence of the BYOD program. In addition, the use of these
company data in the personal devices of the employees are not checked when they leave the
premises. These can be used to get access to the system by unethical means.
Additionally, if an employee decides to sell their personal data, it must be done after
removing the presence of data from it (Boulianne 2015). If a person forgets to remove all data
present in it, unethical attackers may get access to the information of the company which is
another reason for occurrence of breaches and hacks in the system.
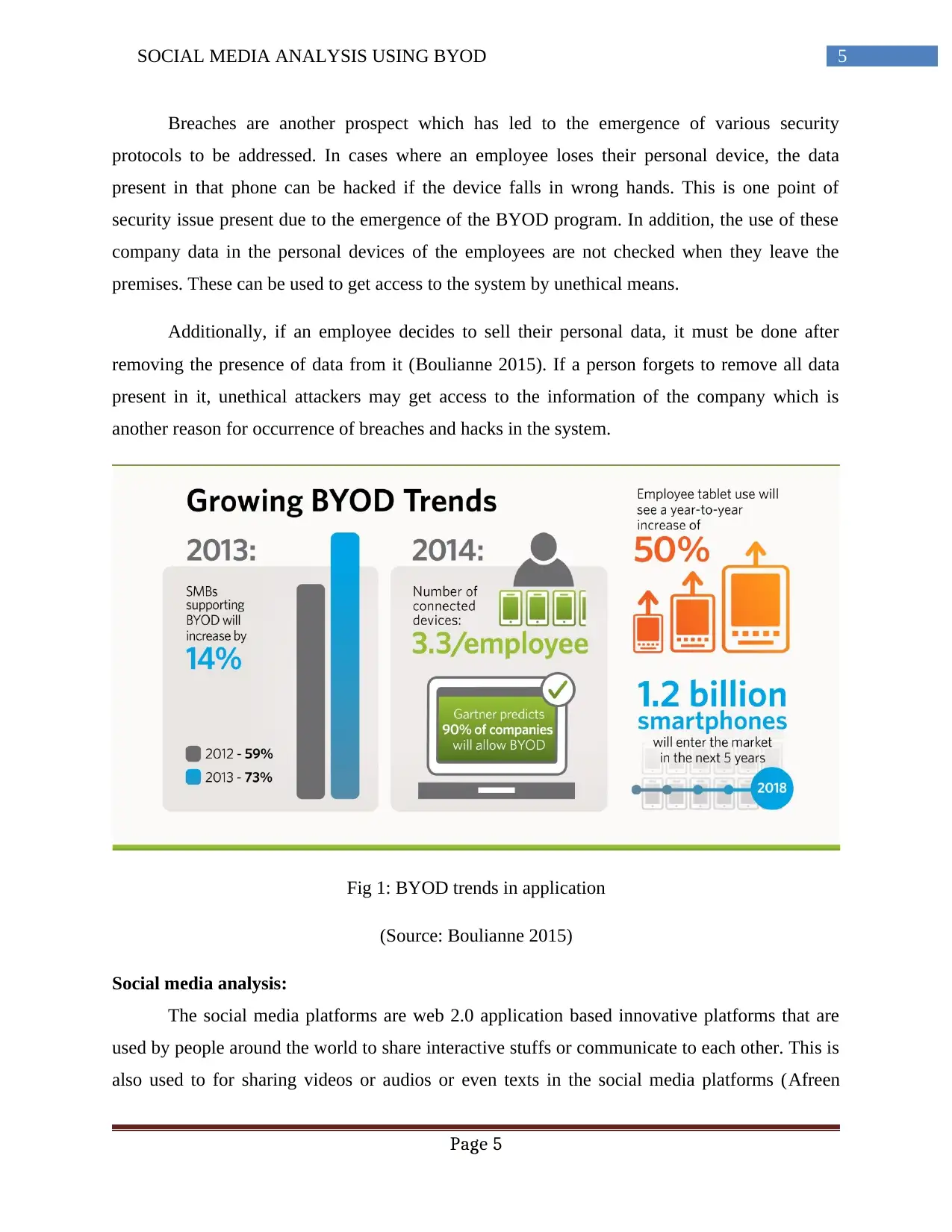
Fig 1: BYOD trends in application
(Source: Boulianne 2015)
Social media analysis:
The social media platforms are web 2.0 application based innovative platforms that are
used by people around the world to share interactive stuffs or communicate to each other. This is
also used to for sharing videos or audios or even texts in the social media platforms (Afreen
Page 5
Breaches are another prospect which has led to the emergence of various security
protocols to be addressed. In cases where an employee loses their personal device, the data
present in that phone can be hacked if the device falls in wrong hands. This is one point of
security issue present due to the emergence of the BYOD program. In addition, the use of these
company data in the personal devices of the employees are not checked when they leave the
premises. These can be used to get access to the system by unethical means.
Additionally, if an employee decides to sell their personal data, it must be done after
removing the presence of data from it (Boulianne 2015). If a person forgets to remove all data
present in it, unethical attackers may get access to the information of the company which is
another reason for occurrence of breaches and hacks in the system.
Fig 1: BYOD trends in application
(Source: Boulianne 2015)
Social media analysis:
The social media platforms are web 2.0 application based innovative platforms that are
used by people around the world to share interactive stuffs or communicate to each other. This is
also used to for sharing videos or audios or even texts in the social media platforms (Afreen
Page 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SOCIAL MEDIA ANALYSIS USING BYOD
2014). The people are then categorized into specific groups to create a social network that are
specifically designed for better advertising.
Advantages of social media platforms:
A social media platform is mainly used by the users around the world to make new
friends or engage on different posts. These people are then grouped according to their
engagement provided which makes up the social network. These are utilized as a tool for the
businesses to target them according to their engagement. This is the most advanced use of the
social media platforms.
Another main characteristic of the social media is the viral contents available. A viral
content is a post which has a deep significance and is mainly used to get the attention of users
quickly. These reach a very high level of engagement and are mainly used to target the people
around the world. An example of the viral content is the recent posts of Kim Kardashian. This is
another main advantage of the social media platforms (Brunty, Miller and Helenek 2014). A
website or any other blogs or forums will not be able to reach this type of engagements which
can be reached easily by using these media platforms. This is another reason for a business to
constantly create posts so that they also reach the viral engagement required.
Another great advantage for the social media platforms is their integration in the mobile
devices. This has made the rise of a new technology known as mobile applications (apps). These
mobile applications show a small portion of the desktop-friendly websites in an innovative way
to increase the interaction made. This has also made many businesses to target them with mobile
apps. Due to the use of the mobile devices, the social media apps run in a different way than the
desktop version. These include including the device features like the camera or the location apps.
This is another reason for businesses to get more engagement from the targeted demographics.
Disadvantages:
For businesses implementing the social media platform, there are certain disadvantages to
its use that are to be considered before running an ad campaign.
The first disadvantage is the presence of a feedback feature in the posts. These are mainly
done to present the users the opportunity to comment and engage on the posts made by the
Page 6
2014). The people are then categorized into specific groups to create a social network that are
specifically designed for better advertising.
Advantages of social media platforms:
A social media platform is mainly used by the users around the world to make new
friends or engage on different posts. These people are then grouped according to their
engagement provided which makes up the social network. These are utilized as a tool for the
businesses to target them according to their engagement. This is the most advanced use of the
social media platforms.
Another main characteristic of the social media is the viral contents available. A viral
content is a post which has a deep significance and is mainly used to get the attention of users
quickly. These reach a very high level of engagement and are mainly used to target the people
around the world. An example of the viral content is the recent posts of Kim Kardashian. This is
another main advantage of the social media platforms (Brunty, Miller and Helenek 2014). A
website or any other blogs or forums will not be able to reach this type of engagements which
can be reached easily by using these media platforms. This is another reason for a business to
constantly create posts so that they also reach the viral engagement required.
Another great advantage for the social media platforms is their integration in the mobile
devices. This has made the rise of a new technology known as mobile applications (apps). These
mobile applications show a small portion of the desktop-friendly websites in an innovative way
to increase the interaction made. This has also made many businesses to target them with mobile
apps. Due to the use of the mobile devices, the social media apps run in a different way than the
desktop version. These include including the device features like the camera or the location apps.
This is another reason for businesses to get more engagement from the targeted demographics.
Disadvantages:
For businesses implementing the social media platform, there are certain disadvantages to
its use that are to be considered before running an ad campaign.
The first disadvantage is the presence of a feedback feature in the posts. These are mainly
done to present the users the opportunity to comment and engage on the posts made by the
Page 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SOCIAL MEDIA ANALYSIS USING BYOD
company. This is a disadvantage as one negative comment can lower the brand engagement as
required.
Another disadvantage for a social media platform is the time requirements needed. A post
to reach the vast audience, takes a large amount of time to create its awareness among them
(Cochrane et al. 2014). Thus, a business need to stay updated to the recent trends and post
accordingly for a long time before their posts will become viral.
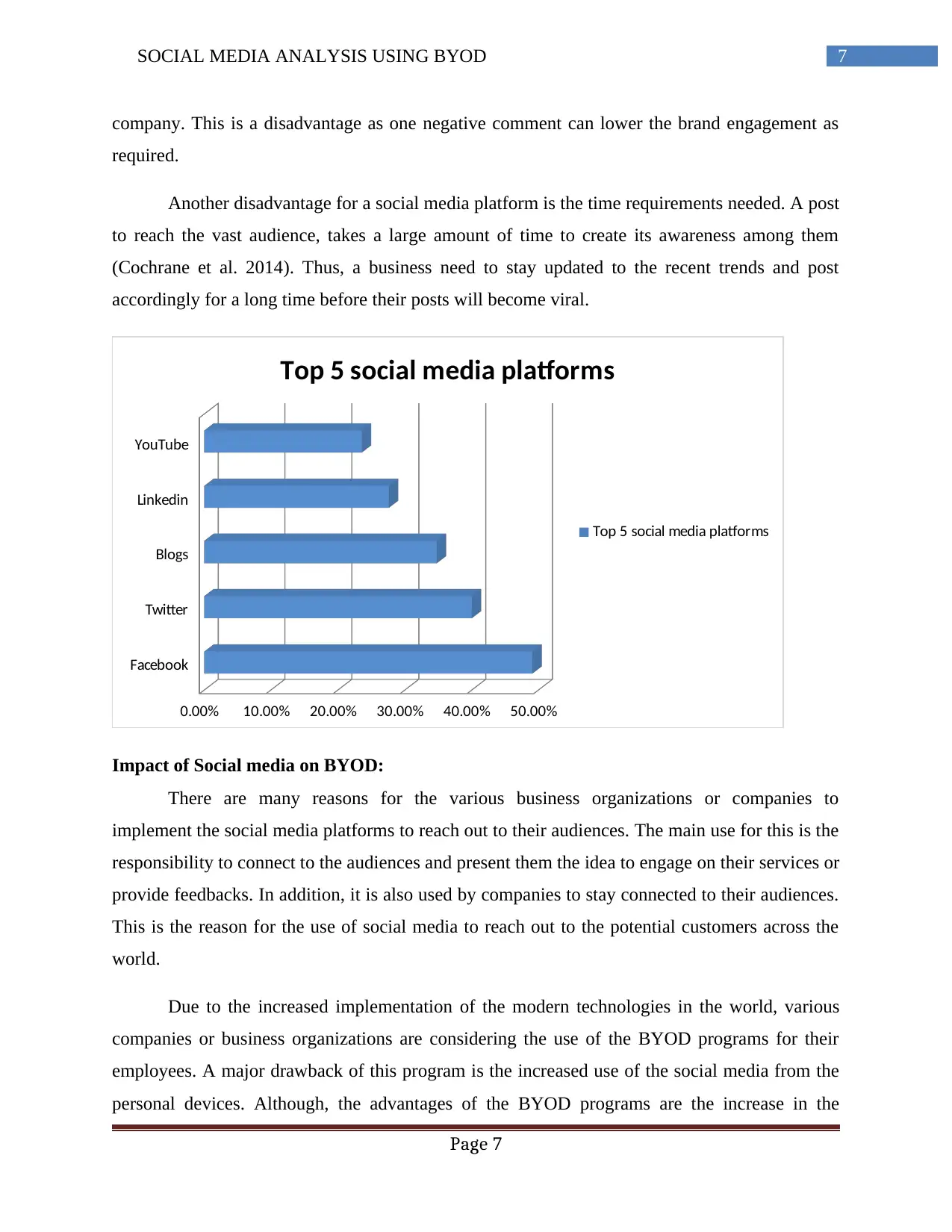
Facebook
Twitter
Blogs
Linkedin
YouTube
0.00% 10.00% 20.00% 30.00% 40.00% 50.00%
Top 5 social media platforms
Top 5 social media platforms
Impact of Social media on BYOD:
There are many reasons for the various business organizations or companies to
implement the social media platforms to reach out to their audiences. The main use for this is the
responsibility to connect to the audiences and present them the idea to engage on their services or
provide feedbacks. In addition, it is also used by companies to stay connected to their audiences.
This is the reason for the use of social media to reach out to the potential customers across the
world.
Due to the increased implementation of the modern technologies in the world, various
companies or business organizations are considering the use of the BYOD programs for their
employees. A major drawback of this program is the increased use of the social media from the
personal devices. Although, the advantages of the BYOD programs are the increase in the
Page 7
company. This is a disadvantage as one negative comment can lower the brand engagement as
required.
Another disadvantage for a social media platform is the time requirements needed. A post
to reach the vast audience, takes a large amount of time to create its awareness among them
(Cochrane et al. 2014). Thus, a business need to stay updated to the recent trends and post
accordingly for a long time before their posts will become viral.
Blogs
YouTube
0.00% 10.00% 20.00% 30.00% 40.00% 50.00%
Top 5 social media platforms
Top 5 social media platforms
Impact of Social media on BYOD:
There are many reasons for the various business organizations or companies to
implement the social media platforms to reach out to their audiences. The main use for this is the
responsibility to connect to the audiences and present them the idea to engage on their services or
provide feedbacks. In addition, it is also used by companies to stay connected to their audiences.
This is the reason for the use of social media to reach out to the potential customers across the
world.
Due to the increased implementation of the modern technologies in the world, various
companies or business organizations are considering the use of the BYOD programs for their
employees. A major drawback of this program is the increased use of the social media from the
personal devices. Although, the advantages of the BYOD programs are the increase in the
Page 7

8SOCIAL MEDIA ANALYSIS USING BYOD
productivity and the efficiency, the disadvantages it poses are greater which is of a great concern
for a company or business organizations implementing them (de Waard 2014). These
disadvantages include the presence of the various security threats or the privacy risks pertaining
to the access of the company credentials. This is the main requirement of the Bring Your Own
Device programs which needs the presence of various security protection acts for addressing
them.
Policies in place:
The main process of implementation of the BYOD program includes the presence of
existing languages for referencing them. This is the main concern for the employees who wants
to safeguard themselves from the constitution or the National Labor Relations Board (NLRB)
(Morrow 2012). The BYOD programs are not included in the association of the NLRB program,
but the protection of vulnerable assets and information of the companies or organizations are
under the jurisdiction of the program.
In addition, the employees associated in an organization having BYOD programs must
identify those policies or other unethical means to get access of information from them. These
means includes the social media or the use of the personal devices to get company information.
In cases like this, the National Labor Relations Board (NLRB) might take measure to bring down
such uses to prevent the likely impact of such actions in the company or business organizations
concerned.
Advantages:
Due to the modern trends in the adoption of the various technologies, mobile devices are
on the rise. This is the main reason for businesses to target the mobile users for increasing the
visitors to their websites (Perrin 2015). Although, the disadvantages it poses are greater which is
of a great concern for a company or business organizations implementing them, the advantages
of the BYOD programs are the increase in the productivity and the efficiency. This is the main
consideration for a business to consider them.
1. Ease in customer access: The business solutions in the past times consisted of the
various sales people targeting the clients of the company by reaching out to them in their own
Page 8
productivity and the efficiency, the disadvantages it poses are greater which is of a great concern
for a company or business organizations implementing them (de Waard 2014). These
disadvantages include the presence of the various security threats or the privacy risks pertaining
to the access of the company credentials. This is the main requirement of the Bring Your Own
Device programs which needs the presence of various security protection acts for addressing
them.
Policies in place:
The main process of implementation of the BYOD program includes the presence of
existing languages for referencing them. This is the main concern for the employees who wants
to safeguard themselves from the constitution or the National Labor Relations Board (NLRB)
(Morrow 2012). The BYOD programs are not included in the association of the NLRB program,
but the protection of vulnerable assets and information of the companies or organizations are
under the jurisdiction of the program.
In addition, the employees associated in an organization having BYOD programs must
identify those policies or other unethical means to get access of information from them. These
means includes the social media or the use of the personal devices to get company information.
In cases like this, the National Labor Relations Board (NLRB) might take measure to bring down
such uses to prevent the likely impact of such actions in the company or business organizations
concerned.
Advantages:
Due to the modern trends in the adoption of the various technologies, mobile devices are
on the rise. This is the main reason for businesses to target the mobile users for increasing the
visitors to their websites (Perrin 2015). Although, the disadvantages it poses are greater which is
of a great concern for a company or business organizations implementing them, the advantages
of the BYOD programs are the increase in the productivity and the efficiency. This is the main
consideration for a business to consider them.
1. Ease in customer access: The business solutions in the past times consisted of the
various sales people targeting the clients of the company by reaching out to them in their own
Page 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SOCIAL MEDIA ANALYSIS USING BYOD
convenient time. This was a cause of problem as the clients were not always able to understand
or engage on the product. This was the main concern of a B2B perspective of a business solution.
The emergence of the mobile network is a boon to the business solutions where the salespeople
are not required to commit to their work time (Raths 2012). Instead, they can contact the clients
from anywhere leading to more customer services. Due to the emergence of the Bring Your Own
Device program in the business solutions, the employees are finding it easier to access the client
information and contact them anytime. This hugely affects the income stream of the company
and leads to more revenue made.
2. Leveraging Social media in business solutions: Social media is a great way for
communicating to the people around the world. In terms of a business perspective, the social
media is a great way to stay connected with their customers and customize accordingly. In the
past times, employees were only allowed to use the social media in their past times or after their
office time. Now-a-days, BYOD program has removed the gap between such restrictions
whereas businesses allow their employees to check their social accounts during office premises.
The main reason for that is to stay updated on the company profiles in the social media (Ruths
and Pfeffer 2014). In addition, companies or business organizations now-a-days are making a
dedicated work profile for people who will be responsible for the social media campaigns. These
are possible due to the BYOD program where the employee is allowed to stay updated to the
social account for tending to the client’s requests anytime and anywhere. This is the main
advantages for leveraging the social media to utilize the productive power of such platforms.
3. Big data and BYOD: Businesses are mainly about connecting to the customers and
keeping updated with the trends. This causes the need for a big data an analytical program to be
installed in the business perspective of the company. The use of cloud computing and big data
analytics are intended for the business purposes so that their activities can be applied in the
business processes. The main use for such innovations is that the employees can tend to the
business anytime and from anywhere. This helps in the business continuity and makes the
business get more engagement from their clients or customers in the market (Scarfo 2012). The
use of the big data analytics is mainly intended for applying the business researches in the
solutions so that they can be enhanced. A reach of a business is bound to increase in a slow and
constant rate where new innovations are always expected. This is the main requirement for big
Page 9
convenient time. This was a cause of problem as the clients were not always able to understand
or engage on the product. This was the main concern of a B2B perspective of a business solution.
The emergence of the mobile network is a boon to the business solutions where the salespeople
are not required to commit to their work time (Raths 2012). Instead, they can contact the clients
from anywhere leading to more customer services. Due to the emergence of the Bring Your Own
Device program in the business solutions, the employees are finding it easier to access the client
information and contact them anytime. This hugely affects the income stream of the company
and leads to more revenue made.
2. Leveraging Social media in business solutions: Social media is a great way for
communicating to the people around the world. In terms of a business perspective, the social
media is a great way to stay connected with their customers and customize accordingly. In the
past times, employees were only allowed to use the social media in their past times or after their
office time. Now-a-days, BYOD program has removed the gap between such restrictions
whereas businesses allow their employees to check their social accounts during office premises.
The main reason for that is to stay updated on the company profiles in the social media (Ruths
and Pfeffer 2014). In addition, companies or business organizations now-a-days are making a
dedicated work profile for people who will be responsible for the social media campaigns. These
are possible due to the BYOD program where the employee is allowed to stay updated to the
social account for tending to the client’s requests anytime and anywhere. This is the main
advantages for leveraging the social media to utilize the productive power of such platforms.
3. Big data and BYOD: Businesses are mainly about connecting to the customers and
keeping updated with the trends. This causes the need for a big data an analytical program to be
installed in the business perspective of the company. The use of cloud computing and big data
analytics are intended for the business purposes so that their activities can be applied in the
business processes. The main use for such innovations is that the employees can tend to the
business anytime and from anywhere. This helps in the business continuity and makes the
business get more engagement from their clients or customers in the market (Scarfo 2012). The
use of the big data analytics is mainly intended for applying the business researches in the
solutions so that they can be enhanced. A reach of a business is bound to increase in a slow and
constant rate where new innovations are always expected. This is the main requirement for big
Page 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10SOCIAL MEDIA ANALYSIS USING BYOD
data analytic software which helps make it easier to address in the businesses as well. This
causes the use of the BYOD program where the employees can monitor the analytics using their
own devices and get insights from them to address in the company’s business solutions.
4. Keeping up with innovations: A business does not need the presence of upgraded
infrastructure as the BYOD is already considering the employees to bring their own devices
(Song 2014). As people are already up to date with their technologies, the need for a business to
maintain such requirements is reduced.
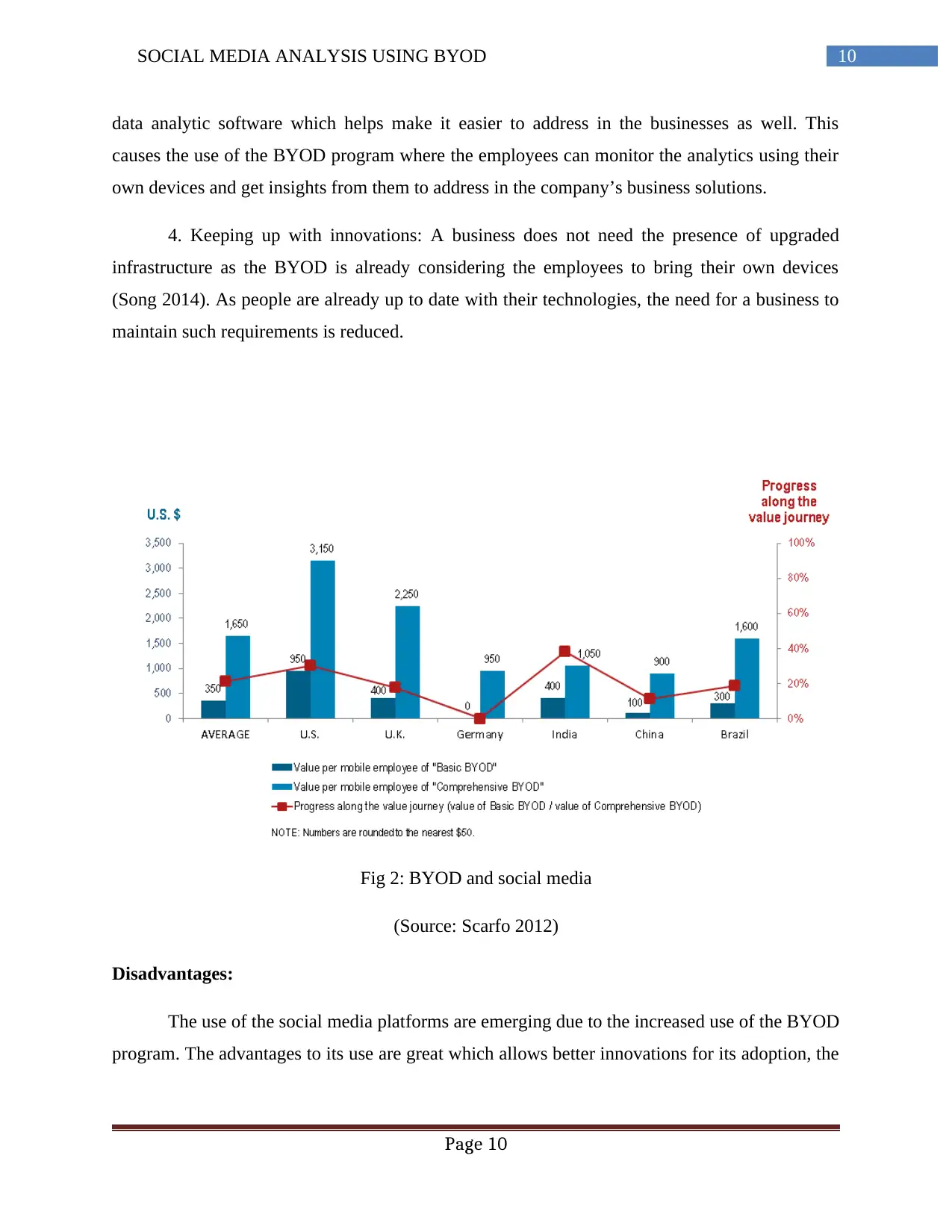
Fig 2: BYOD and social media
(Source: Scarfo 2012)
Disadvantages:
The use of the social media platforms are emerging due to the increased use of the BYOD
program. The advantages to its use are great which allows better innovations for its adoption, the
Page 10
data analytic software which helps make it easier to address in the businesses as well. This
causes the use of the BYOD program where the employees can monitor the analytics using their
own devices and get insights from them to address in the company’s business solutions.
4. Keeping up with innovations: A business does not need the presence of upgraded
infrastructure as the BYOD is already considering the employees to bring their own devices
(Song 2014). As people are already up to date with their technologies, the need for a business to
maintain such requirements is reduced.
Fig 2: BYOD and social media
(Source: Scarfo 2012)
Disadvantages:
The use of the social media platforms are emerging due to the increased use of the BYOD
program. The advantages to its use are great which allows better innovations for its adoption, the
Page 10

11SOCIAL MEDIA ANALYSIS USING BYOD
disadvantages that it poses are extremely great. These disadvantages are to be referenced for
addressing the business continuity of the company or concerned organization.
1. Hacking and security breaches: These are the major security disadvantages that can
lead to grave impacts in the company process. Due to the use of one’s own devices for accessing
the social media accounts, it can be hacked by hackers as the unethical activities are now
spreading to various users by the social media as well (Thomson 2012). Due to the establishment
of a successful network between the personal devices and the company, a hacker may get access
to the company information. In extreme cases, a virus or malware programs can be released from
them leading to grave business activities or disclosure of information from them.
2. Bandwidth exhaustion: This is another disadvantage as the presence of various
employee devices takes up a lot of internet bandwidth from the system. A company device is
made to block the internet connection to various applications which makes up the smooth
processing of work (Tokuyoshi 2013). As a personal device of an employee has many
applications installed in them, it takes up a whole lot of data packets which unnecessarily reduce
the internet speed as well.
Recommendations:
Although there are some disadvantages to the use of the social media platforms for
businesses, the advantages it provides can serve as a great benefit for businesses adopting them
(Tubaro, Casilli and Sarabi 2013). It is thus, recommended that the presence of an open policy
program must be removed and a secure infrastructure must be in place to detect the incoming
packets of the data transmission. In addition, the BYOD policies to reference the program must
also be utilized to address the rules to be followed by the employees as well.
Conclusion:
Thus, the conclusion that can be drawn from this report is that the organizations or
companies that can apply the Bring Your Own Device program can enjoy higher advantageous
benefits than their competitors. In addition, as fast approaching applications are consuming the
market place, devices are also getting produced more now. This is the main cause for the rise of
the digital innovation in the market which leads to the implementation of more BYOD programs.
Page 11
disadvantages that it poses are extremely great. These disadvantages are to be referenced for
addressing the business continuity of the company or concerned organization.
1. Hacking and security breaches: These are the major security disadvantages that can
lead to grave impacts in the company process. Due to the use of one’s own devices for accessing
the social media accounts, it can be hacked by hackers as the unethical activities are now
spreading to various users by the social media as well (Thomson 2012). Due to the establishment
of a successful network between the personal devices and the company, a hacker may get access
to the company information. In extreme cases, a virus or malware programs can be released from
them leading to grave business activities or disclosure of information from them.
2. Bandwidth exhaustion: This is another disadvantage as the presence of various
employee devices takes up a lot of internet bandwidth from the system. A company device is
made to block the internet connection to various applications which makes up the smooth
processing of work (Tokuyoshi 2013). As a personal device of an employee has many
applications installed in them, it takes up a whole lot of data packets which unnecessarily reduce
the internet speed as well.
Recommendations:
Although there are some disadvantages to the use of the social media platforms for
businesses, the advantages it provides can serve as a great benefit for businesses adopting them
(Tubaro, Casilli and Sarabi 2013). It is thus, recommended that the presence of an open policy
program must be removed and a secure infrastructure must be in place to detect the incoming
packets of the data transmission. In addition, the BYOD policies to reference the program must
also be utilized to address the rules to be followed by the employees as well.
Conclusion:
Thus, the conclusion that can be drawn from this report is that the organizations or
companies that can apply the Bring Your Own Device program can enjoy higher advantageous
benefits than their competitors. In addition, as fast approaching applications are consuming the
market place, devices are also getting produced more now. This is the main cause for the rise of
the digital innovation in the market which leads to the implementation of more BYOD programs.
Page 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





