Internet Censorship: An Analysis of Social Media Content Regulation
VerifiedAdded on 2020/05/28
|28
|5073
|215
Report
AI Summary
This report investigates the critical issue of internet censorship, particularly concerning social media content. It begins by highlighting the internet's role as a global communication network and the challenges arising from the lack of content censorship, including threats to user security, safety, and privacy. The research, conducted among social media users, employs empirical methods such as interviews and secondary data analysis, including statistical approaches, to assess the necessity of censorship. The study examines the background, objectives, and justification for censorship, exploring literature on internet privacy, security, and social issues. It addresses key questions such as the impact of free internet content on relationships, safety, and social unrest. The methodology includes purposive sampling and the use of structured questionnaires. Findings reveal insights into user behavior, incidents related to misleading comments, and the reasons behind using social media for sensitive discussions. The report concludes with recommendations for implementing censorship to protect internet users from identified threats, emphasizing the need for companies to be held accountable for user data and the spread of misinformation. The report also includes a conceptual framework and detailed tables of the objectives to provide a comprehensive analysis of the issue.

Should Social Media Censor Content
By <Name of Student>
<Institutional Affialiation>
<Instructor’s Name>
<Date of Submission>
By <Name of Student>
<Institutional Affialiation>
<Instructor’s Name>
<Date of Submission>
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The internet is recognized as a global network of communication in which passing of the
information from one point to another saturates in seconds. The shared information on the
internet is hardly censored something which exposes threats to the users in many ways. The
threats, which are reviewed in this study, include security, safety, privacy as well as some of
the social issues. The research was conducted among the frequent users of the social media
and on the results that were obtained was analysed and applied to see how the censorship of
the social media content is essential. This research uses empirical and some part of the
theoretical methods in the analysis. The empirical method is based on the interviews and the
analysis of the secondary data. The secondary data analysis entails application of the
various statistical approaches to determine validity of the results. The study also identifies
some substantial gaps, which, should be bridged through internet censorship. Therefore,
after critical analysis of the results, I was able to draw conclusion that there should be
censorship of the content of the social media to protect the users of the internet from these
threats.
2
The internet is recognized as a global network of communication in which passing of the
information from one point to another saturates in seconds. The shared information on the
internet is hardly censored something which exposes threats to the users in many ways. The
threats, which are reviewed in this study, include security, safety, privacy as well as some of
the social issues. The research was conducted among the frequent users of the social media
and on the results that were obtained was analysed and applied to see how the censorship of
the social media content is essential. This research uses empirical and some part of the
theoretical methods in the analysis. The empirical method is based on the interviews and the
analysis of the secondary data. The secondary data analysis entails application of the
various statistical approaches to determine validity of the results. The study also identifies
some substantial gaps, which, should be bridged through internet censorship. Therefore,
after critical analysis of the results, I was able to draw conclusion that there should be
censorship of the content of the social media to protect the users of the internet from these
threats.
2

Table of contents
Abstract.............................................................................................................................................2
1 Introduction................................................................................................................................5
1.1 Background of the study.....................................................................................................5
1.2 Objectives............................................................................................................................5
2 Literature review.........................................................................................................................7
2.1 Internet and privacy.........................................................................................................7
2.2 Internet and security as well as safety.............................................................................8
2.3 Internet and social issues..................................................................................................9
2.4 Conceptual framework........................................................................................................9
3 Research methodology.............................................................................................................10
3.1 Target population..............................................................................................................10
3.2 Sampling procedure and sample size................................................................................10
3.3 Data collection methods and tools....................................................................................10
3.4 Research design................................................................................................................11
3.5 Data analysis.....................................................................................................................11
4 Results and Findings..................................................................................................................11
4.1 Descriptive statistics..........................................................................................................11
4.1.1 Gender......................................................................................................................11
4.1.2 Age-range..................................................................................................................11
4.1.3 Internet use...............................................................................................................12
4.1.4 Purpose of using online transactions........................................................................12
4.1.5 Online transaction website........................................................................................13
4.2 Incidents that have happened due to misleading comments within the last 10 years.....13
4.2.1 Hypothesis testing.....................................................................................................14
4.2.2 Relationship between the number of fans and receipt of negative feedback...........14
4.2.3 Relationship between the purpose of the webpage and negative feedback.............14
4.2.4 Relationship between negative feedback and source of webpage popularity..........15
4.3 Why people use social media as a platform for sensitive comments...............................15
4.3.1 Relationship between negative feedback/experience and social media use............16
5 Conclusions and Recommendations.........................................................................................17
5.1 Conclusions.......................................................................................................................17
3
Abstract.............................................................................................................................................2
1 Introduction................................................................................................................................5
1.1 Background of the study.....................................................................................................5
1.2 Objectives............................................................................................................................5
2 Literature review.........................................................................................................................7
2.1 Internet and privacy.........................................................................................................7
2.2 Internet and security as well as safety.............................................................................8
2.3 Internet and social issues..................................................................................................9
2.4 Conceptual framework........................................................................................................9
3 Research methodology.............................................................................................................10
3.1 Target population..............................................................................................................10
3.2 Sampling procedure and sample size................................................................................10
3.3 Data collection methods and tools....................................................................................10
3.4 Research design................................................................................................................11
3.5 Data analysis.....................................................................................................................11
4 Results and Findings..................................................................................................................11
4.1 Descriptive statistics..........................................................................................................11
4.1.1 Gender......................................................................................................................11
4.1.2 Age-range..................................................................................................................11
4.1.3 Internet use...............................................................................................................12
4.1.4 Purpose of using online transactions........................................................................12
4.1.5 Online transaction website........................................................................................13
4.2 Incidents that have happened due to misleading comments within the last 10 years.....13
4.2.1 Hypothesis testing.....................................................................................................14
4.2.2 Relationship between the number of fans and receipt of negative feedback...........14
4.2.3 Relationship between the purpose of the webpage and negative feedback.............14
4.2.4 Relationship between negative feedback and source of webpage popularity..........15
4.3 Why people use social media as a platform for sensitive comments...............................15
4.3.1 Relationship between negative feedback/experience and social media use............16
5 Conclusions and Recommendations.........................................................................................17
5.1 Conclusions.......................................................................................................................17
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5.2 Recommendations............................................................................................................17
References........................................................................................................................................18
APPENDIX..........................................................................................................................................21
4
References........................................................................................................................................18
APPENDIX..........................................................................................................................................21
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1 Introduction
This covers the background of the study, objectives of the study, justification of the study and
study limitations
1.1 Background of the study
In the modern day life, the internet a far-reaching aspect. It has been recognized as one of
the most crucial tools for many people in the globe to express themselves, to freely
communicate and share or receive news and information. In fact, the internet penetration
rates are rising exponentially (Duggan and Smith, 2015). Before social media, sharing of the
opinions, receiving information and news was mostly based on the traditional mass media
forms in which the content of these parameters were censored. The rise of social media over
the last decades has given many states more difficult task of censoring the information that
is shared by the citizens. Likewise, the penetration of internet has also been more influential
in the field of business as companies rely on it for activities such as marketing of the
products and services. Moreover, there are even private companies, which are consistently
improving access to the internet, because of the financial opportunities, which are inherent
in the internet. For example, Facebook intends to introduce the internet to the remotest areas
in the world. Likewise, Google also intends to introduce Google Loon, which is also aimed
at increasing the rates of internet access in different countries. However, the current
adoption rates of the internet also come with their own challenges, which are discussed in
the objectives below.
1.2 Objectives
The main aim of this study is justify whether or not there should be censorship of the social
media content. The social media has rapidly grown faster than any other type of the social
media but the concern is directed over the internet control and censorship, which has formed
an interesting discussion. Hence, the aim is meant to give the yes answer on online
5
This covers the background of the study, objectives of the study, justification of the study and
study limitations
1.1 Background of the study
In the modern day life, the internet a far-reaching aspect. It has been recognized as one of
the most crucial tools for many people in the globe to express themselves, to freely
communicate and share or receive news and information. In fact, the internet penetration
rates are rising exponentially (Duggan and Smith, 2015). Before social media, sharing of the
opinions, receiving information and news was mostly based on the traditional mass media
forms in which the content of these parameters were censored. The rise of social media over
the last decades has given many states more difficult task of censoring the information that
is shared by the citizens. Likewise, the penetration of internet has also been more influential
in the field of business as companies rely on it for activities such as marketing of the
products and services. Moreover, there are even private companies, which are consistently
improving access to the internet, because of the financial opportunities, which are inherent
in the internet. For example, Facebook intends to introduce the internet to the remotest areas
in the world. Likewise, Google also intends to introduce Google Loon, which is also aimed
at increasing the rates of internet access in different countries. However, the current
adoption rates of the internet also come with their own challenges, which are discussed in
the objectives below.
1.2 Objectives
The main aim of this study is justify whether or not there should be censorship of the social
media content. The social media has rapidly grown faster than any other type of the social
media but the concern is directed over the internet control and censorship, which has formed
an interesting discussion. Hence, the aim is meant to give the yes answer on online
5
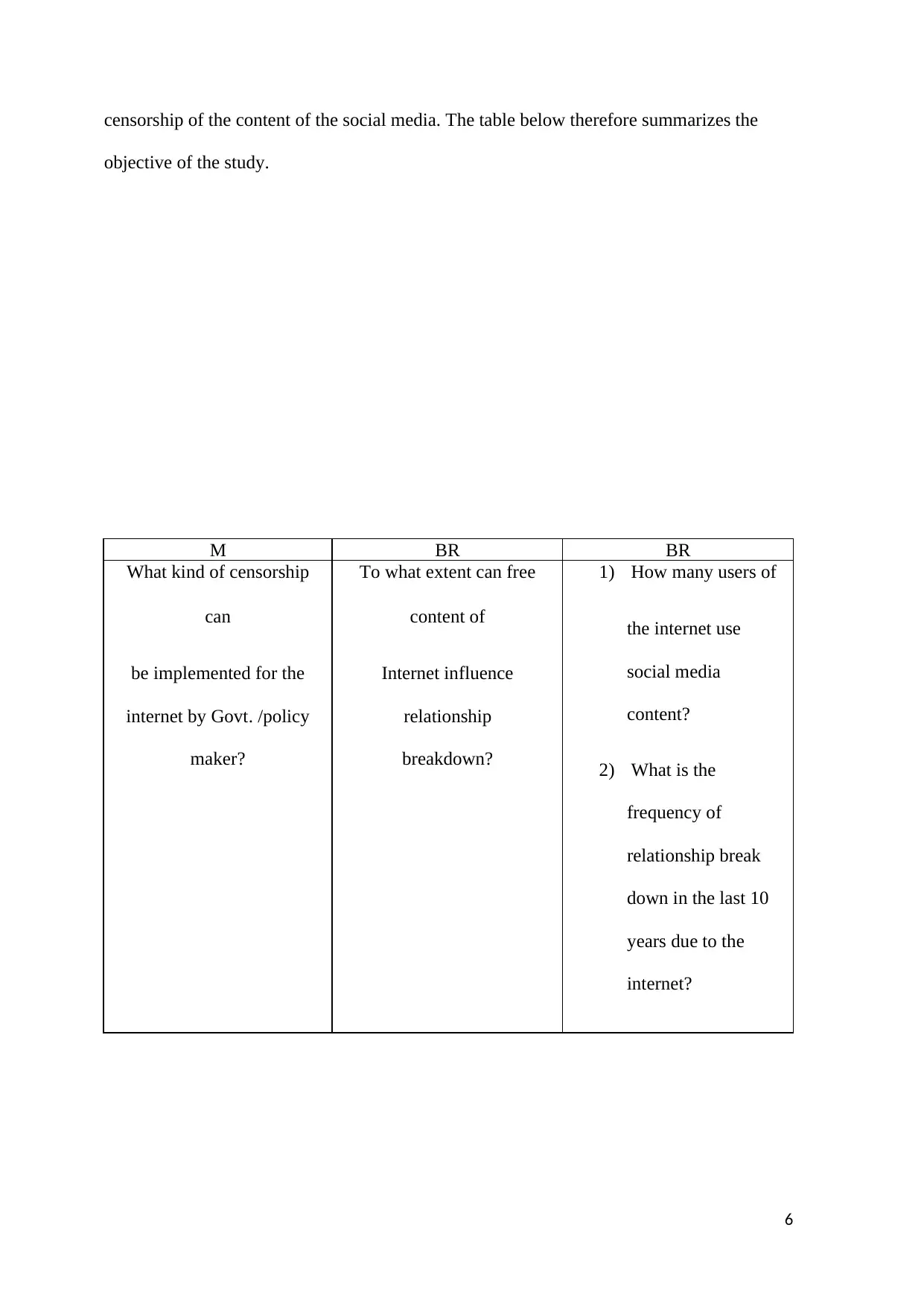
censorship of the content of the social media. The table below therefore summarizes the
objective of the study.
M BR BR
What kind of censorship
can
be implemented for the
internet by Govt. /policy
maker?
To what extent can free
content of
Internet influence
relationship
breakdown?
1) How many users of
the internet use
social media
content?
2) What is the
frequency of
relationship break
down in the last 10
years due to the
internet?
6
objective of the study.
M BR BR
What kind of censorship
can
be implemented for the
internet by Govt. /policy
maker?
To what extent can free
content of
Internet influence
relationship
breakdown?
1) How many users of
the internet use
social media
content?
2) What is the
frequency of
relationship break
down in the last 10
years due to the
internet?
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

To what extent can free
access to the internet be a
threat to safety and security
1) What
percentage
of customers
are using
internet
banking?
2) How many financial
transaction is
occurred throughHow significant can the
internet contribute as a
platform to discuss social
sensitive issues, which
may lead to social unrest?
1) How many incidents
have happened due to
misleading comments
within last 10 years?
2) Why are people
using social media
as a platform for
sensitive
comments?
2 Literature review
2.1 Internet and privacy
The internet is a collection of files about different things. Moreover, each time someone
uses the internet, some information about him or her remains with the internet. In fact,
Zarouali et al. (2017) perceive the use of cookies as one of the biggest privacy contentions
on the internet. The websites use these cookies to monitor the behavioral patterns of their
7
access to the internet be a
threat to safety and security
1) What
percentage
of customers
are using
internet
banking?
2) How many financial
transaction is
occurred throughHow significant can the
internet contribute as a
platform to discuss social
sensitive issues, which
may lead to social unrest?
1) How many incidents
have happened due to
misleading comments
within last 10 years?
2) Why are people
using social media
as a platform for
sensitive
comments?
2 Literature review
2.1 Internet and privacy
The internet is a collection of files about different things. Moreover, each time someone
uses the internet, some information about him or her remains with the internet. In fact,
Zarouali et al. (2017) perceive the use of cookies as one of the biggest privacy contentions
on the internet. The websites use these cookies to monitor the behavioral patterns of their
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

users, and in most cases, when someone declines to accept the cookie policy, then they are
denied the services of the aforementioned website. This is a questionable behavior, because
the user might not want to leave a trail behind. In fact, companies use these cookies for big
data analytics to identify consumer-purchasing patterns, which patterns then they use to
serve the customers with greater levels of accuracy. However, it is usually the case that they
do not consult the user about how and when they can use their information, thereby
infringing on personal privacy. Take the example of the father who found out that his
teenage daughter was pregnant, because of a card from Target. The company had been
collecting information about her purchases, and then sent her a congratulations card, with a
baby catalog. Consequently, there is room for more censoring on the internet.
2.2 Internet and security as well as safety
Typically, a person uses a password for their internet accounts to secure their private
information. However, the accuracy of the protection is not always top notch. In most cases,
with a few key strokes, the hackers can access this data. In fact, if a website does not have
strong security, then it might be hacked, and the information of the customers might be
stolen, including credit card data (Kashmiri, Nicol, and Hsu, 2017). Hacking is already
illegal, and therefore, there is no contest about the protection of customers' piracy on that
score. Furthermore, the companies, which fail to implement measures against the human
threat to the security of the user data, also expose their users, and therefore, stronger
legislation is required on that measure. For example, one Eric severally reported to Amazon
that the customer care assistants had provided his information to the identity thieves, but the
issue was never fixed. He had discovered that when someone pretended to be him, the
customer representatives would provide him with information about his credit card, his
previous purchases, and even his home address. The problem therefore arises, that someone
can easily be compromised both line and in their personal lives, without the company
8
denied the services of the aforementioned website. This is a questionable behavior, because
the user might not want to leave a trail behind. In fact, companies use these cookies for big
data analytics to identify consumer-purchasing patterns, which patterns then they use to
serve the customers with greater levels of accuracy. However, it is usually the case that they
do not consult the user about how and when they can use their information, thereby
infringing on personal privacy. Take the example of the father who found out that his
teenage daughter was pregnant, because of a card from Target. The company had been
collecting information about her purchases, and then sent her a congratulations card, with a
baby catalog. Consequently, there is room for more censoring on the internet.
2.2 Internet and security as well as safety
Typically, a person uses a password for their internet accounts to secure their private
information. However, the accuracy of the protection is not always top notch. In most cases,
with a few key strokes, the hackers can access this data. In fact, if a website does not have
strong security, then it might be hacked, and the information of the customers might be
stolen, including credit card data (Kashmiri, Nicol, and Hsu, 2017). Hacking is already
illegal, and therefore, there is no contest about the protection of customers' piracy on that
score. Furthermore, the companies, which fail to implement measures against the human
threat to the security of the user data, also expose their users, and therefore, stronger
legislation is required on that measure. For example, one Eric severally reported to Amazon
that the customer care assistants had provided his information to the identity thieves, but the
issue was never fixed. He had discovered that when someone pretended to be him, the
customer representatives would provide him with information about his credit card, his
previous purchases, and even his home address. The problem therefore arises, that someone
can easily be compromised both line and in their personal lives, without the company
8

conducting due diligence to discover where the problem emanated from. On that score,
companies should therefore be held to higher standards of accountability, because their
carelessness could be catastrophic to the users of their services.
2.3 Internet and social issues
The internet is a hive of information, not all of which is correct (Wilkie, Michael and
Plummer-Fernandez, 2015). However, it is never easy to find out which information is
correct, and which is not. It is therefore left to the discretion of the internet sites, to provide
proof of their information, and therefore, they should be held accountable for their
information. The problem however, is that it is not always possible to comb through the
internet for who is posting what. Accordingly, within a matter of hours, information on the
internet can reach millions of people and then advance an agenda, which is either beneficial
or even harmful. For example, there are certifiably manual and automated robots on Twitter
which post flagrant and inciting information, which the users have no means of identifying
whether they is correct or not (Wilkie, Michael and Plummer-Fernandez, 2015). This
information is meant to be inciting, yet people find negative information more accurate than
positive information, and they remember it for longer. Consequently, it should be
mandatory for companies like Twitter to instate measures against the aforementioned bots,
to reduce the extent to which this information spreads without accountability.
2.4 Conceptual framework
9
To what extent can free content of
internet influence relationship
breakdown:
1) How many users of the
internet use social media content?
To what extent can free access to the
internet be a threat to safety and
security:
1) What percentage
of customers are
using internet
banking?
2) How many
financial
transaction is
occurred through
internet?
How significant can the internet
contribute as a platform to discuss
social sensitive issues which may lead
to social unrest:
1) How many incidents have
happened due to misleading
comments within last 10 years?
2) Why are people using social
media as a platform for sensitive
comments?
companies should therefore be held to higher standards of accountability, because their
carelessness could be catastrophic to the users of their services.
2.3 Internet and social issues
The internet is a hive of information, not all of which is correct (Wilkie, Michael and
Plummer-Fernandez, 2015). However, it is never easy to find out which information is
correct, and which is not. It is therefore left to the discretion of the internet sites, to provide
proof of their information, and therefore, they should be held accountable for their
information. The problem however, is that it is not always possible to comb through the
internet for who is posting what. Accordingly, within a matter of hours, information on the
internet can reach millions of people and then advance an agenda, which is either beneficial
or even harmful. For example, there are certifiably manual and automated robots on Twitter
which post flagrant and inciting information, which the users have no means of identifying
whether they is correct or not (Wilkie, Michael and Plummer-Fernandez, 2015). This
information is meant to be inciting, yet people find negative information more accurate than
positive information, and they remember it for longer. Consequently, it should be
mandatory for companies like Twitter to instate measures against the aforementioned bots,
to reduce the extent to which this information spreads without accountability.
2.4 Conceptual framework
9
To what extent can free content of
internet influence relationship
breakdown:
1) How many users of the
internet use social media content?
To what extent can free access to the
internet be a threat to safety and
security:
1) What percentage
of customers are
using internet
banking?
2) How many
financial
transaction is
occurred through
internet?
How significant can the internet
contribute as a platform to discuss
social sensitive issues which may lead
to social unrest:
1) How many incidents have
happened due to misleading
comments within last 10 years?
2) Why are people using social
media as a platform for sensitive
comments?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6.
3 Research methodology
This is a systematic method of solving a problem .It is the process by which researchers go about
their work of describing, explaining and predicting phenomena (Kumar, 2014).
3.1 Target population
This is the entire units from which the survey data is to be collected to make statistical inferences
(Feldman, 1990).In our study; the target population is the internet users.
3.2 Sampling procedure and sample size
Purposive sampling was used to acquire the sample that responded to the questionnaires. The
researchers’ judgment was used to select the sample that had characteristics of internet users. This
was to save on time and related costs.Moreso, this sampling method was appropriate because
there was only limited number of primary data sources who could contribute to the study.
Purposive sampling is a non-probability technique of sampling where the researcher relies on
his/her judgment in selection of a sample (Kothari, 2004)
A sample of size 30 was obtained for this study.
3.3 Data collection methods and tools
A structured questionnaire was administered to the sample; this was self-report where the
respondent was supposed to tick the appropriate answer. The questions given were closed-ended
while only one question was open-ended.
10
Internet Censorship
3 Research methodology
This is a systematic method of solving a problem .It is the process by which researchers go about
their work of describing, explaining and predicting phenomena (Kumar, 2014).
3.1 Target population
This is the entire units from which the survey data is to be collected to make statistical inferences
(Feldman, 1990).In our study; the target population is the internet users.
3.2 Sampling procedure and sample size
Purposive sampling was used to acquire the sample that responded to the questionnaires. The
researchers’ judgment was used to select the sample that had characteristics of internet users. This
was to save on time and related costs.Moreso, this sampling method was appropriate because
there was only limited number of primary data sources who could contribute to the study.
Purposive sampling is a non-probability technique of sampling where the researcher relies on
his/her judgment in selection of a sample (Kothari, 2004)
A sample of size 30 was obtained for this study.
3.3 Data collection methods and tools
A structured questionnaire was administered to the sample; this was self-report where the
respondent was supposed to tick the appropriate answer. The questions given were closed-ended
while only one question was open-ended.
10
Internet Censorship
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3.4 Research design
This study utilized both qualitative and quantitave research design.Qualitative method is used to
describe the characteristics of the study population while quantitave method is used to test
hypothesis and determine relationships between variables.
3.5 Data analysis
Primary data was used for this study, obtained from structured questionnaires. The data for this
study was then, cleaned, coded and entered into SPSS for analysis.
Descriptives are carried out first; this is to describe our sample. Further, inferential statistics is then
carried out to test hypotheses.
4 Results and Findings
4.1 Descriptive statistics
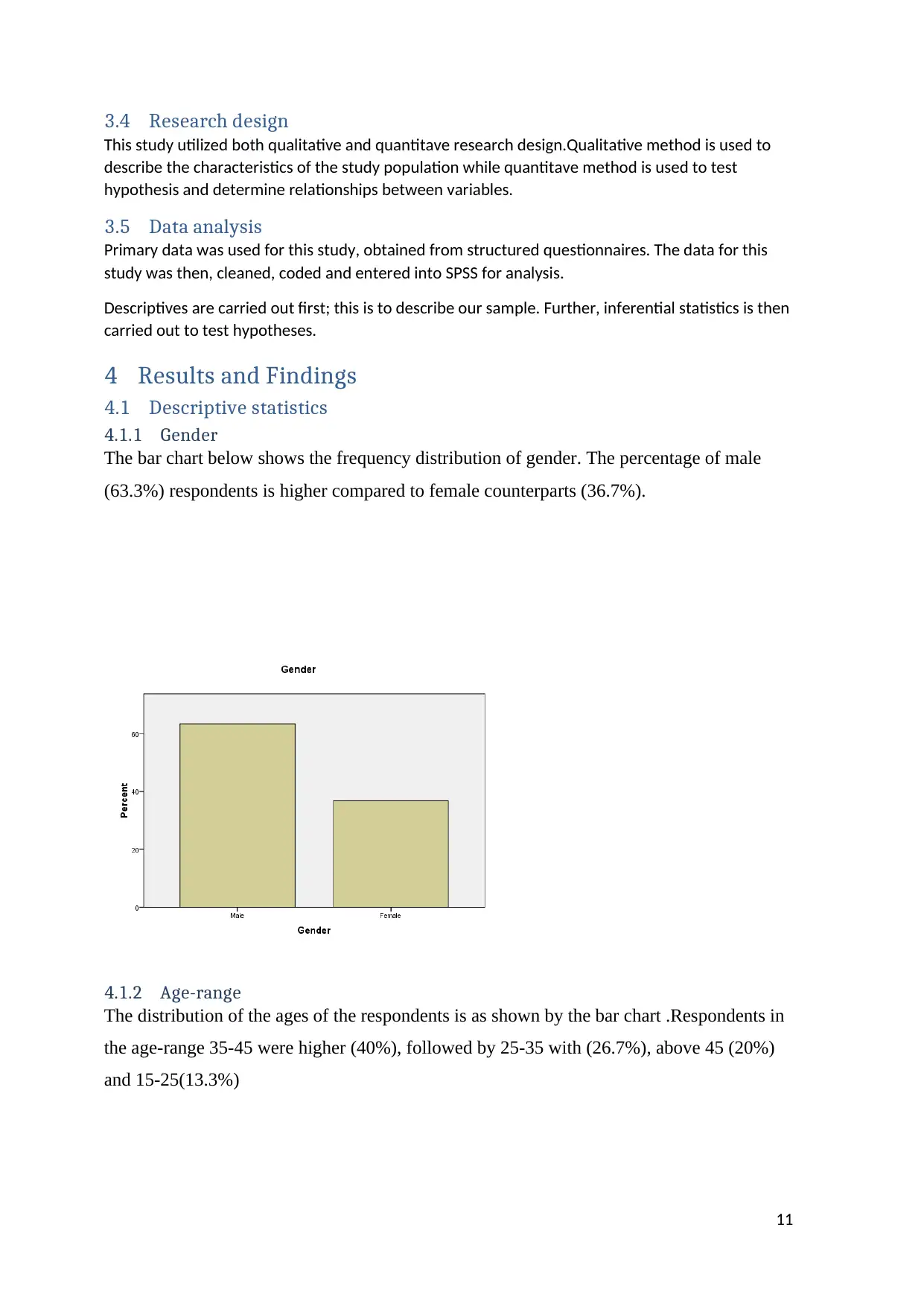
4.1.1 Gender
The bar chart below shows the frequency distribution of gender. The percentage of male
(63.3%) respondents is higher compared to female counterparts (36.7%).
4.1.2 Age-range
The distribution of the ages of the respondents is as shown by the bar chart .Respondents in
the age-range 35-45 were higher (40%), followed by 25-35 with (26.7%), above 45 (20%)
and 15-25(13.3%)
11
This study utilized both qualitative and quantitave research design.Qualitative method is used to
describe the characteristics of the study population while quantitave method is used to test
hypothesis and determine relationships between variables.
3.5 Data analysis
Primary data was used for this study, obtained from structured questionnaires. The data for this
study was then, cleaned, coded and entered into SPSS for analysis.
Descriptives are carried out first; this is to describe our sample. Further, inferential statistics is then
carried out to test hypotheses.
4 Results and Findings
4.1 Descriptive statistics
4.1.1 Gender
The bar chart below shows the frequency distribution of gender. The percentage of male
(63.3%) respondents is higher compared to female counterparts (36.7%).
4.1.2 Age-range
The distribution of the ages of the respondents is as shown by the bar chart .Respondents in
the age-range 35-45 were higher (40%), followed by 25-35 with (26.7%), above 45 (20%)
and 15-25(13.3%)
11
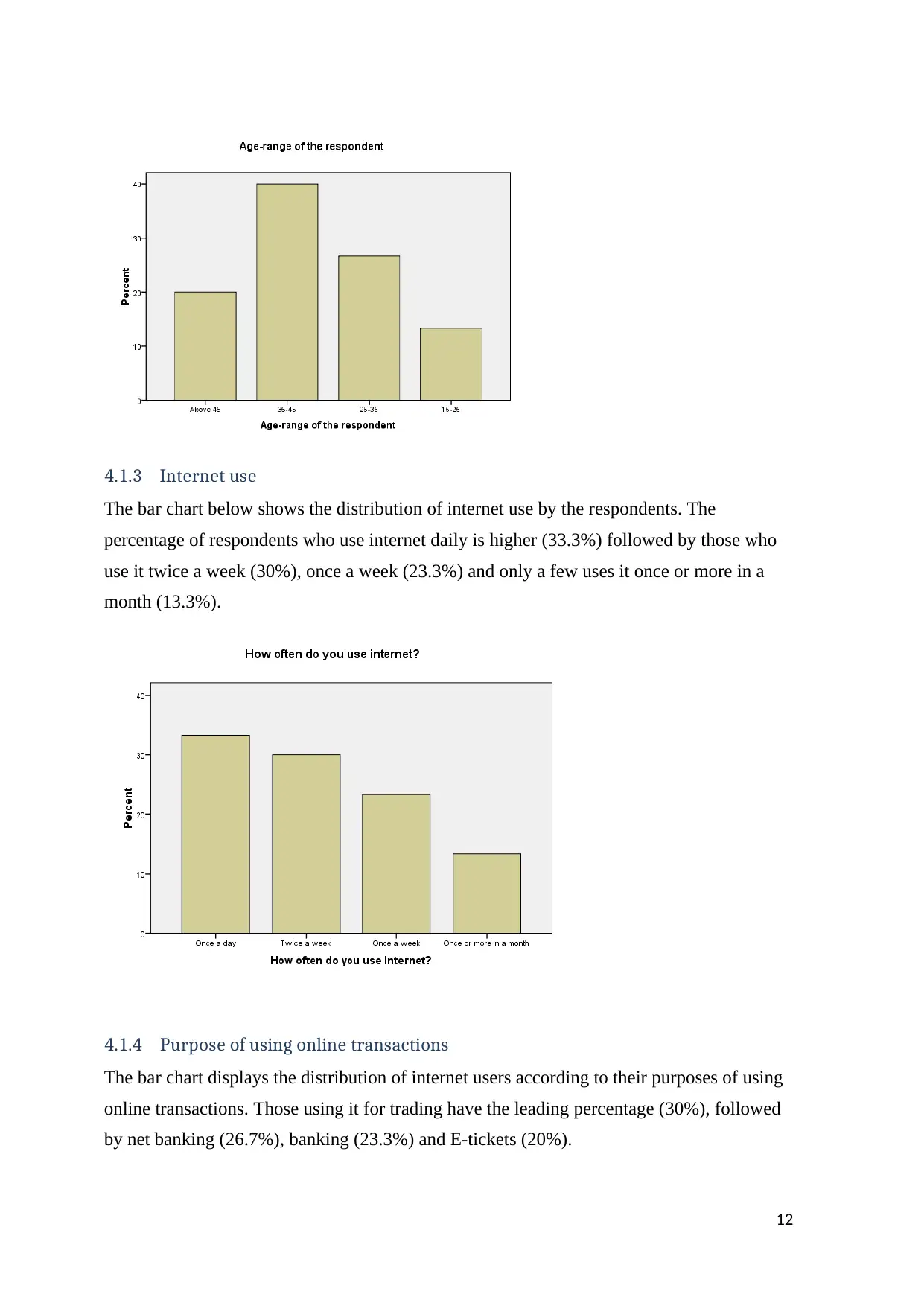
4.1.3 Internet use
The bar chart below shows the distribution of internet use by the respondents. The
percentage of respondents who use internet daily is higher (33.3%) followed by those who
use it twice a week (30%), once a week (23.3%) and only a few uses it once or more in a
month (13.3%).
4.1.4 Purpose of using online transactions
The bar chart displays the distribution of internet users according to their purposes of using
online transactions. Those using it for trading have the leading percentage (30%), followed
by net banking (26.7%), banking (23.3%) and E-tickets (20%).
12
The bar chart below shows the distribution of internet use by the respondents. The
percentage of respondents who use internet daily is higher (33.3%) followed by those who
use it twice a week (30%), once a week (23.3%) and only a few uses it once or more in a
month (13.3%).
4.1.4 Purpose of using online transactions
The bar chart displays the distribution of internet users according to their purposes of using
online transactions. Those using it for trading have the leading percentage (30%), followed
by net banking (26.7%), banking (23.3%) and E-tickets (20%).
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





