Exploring Privacy Issues on Social Media: Risks, and Recommendations
VerifiedAdded on 2023/04/20
|53
|14799
|487
Report
AI Summary
This report examines the privacy issues faced by users on social media platforms, focusing on the risks, ethical considerations, and user awareness surrounding the sharing of personal information. It begins by introducing the concept of social media and its various forms, highlighting the increasing concerns about data security and privacy breaches. The report delves into the violation of privacy on social networking sites like Facebook, Twitter, WhatsApp, Snapchat, and Skype, discussing issues such as spamming and social engineering risks. It explores account risks and content threats, offering potential remedies for mitigating these challenges. The research methodology employed is detailed, including the research philosophy, approach, design, data collection techniques, sampling method, data analysis method, and ethical considerations. The findings from quantitative data analysis are presented, leading to conclusions and recommendations aimed at improving social media privacy and security. The report emphasizes the need for greater user awareness and proactive measures to protect personal information in the digital age. Desklib provides access to similar solved assignments and resources for students.

Running head: SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Social Media and other people’s privacy
Name of the Student
Name of the University
Social Media and other people’s privacy
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Table of Contents
Chapter 1: Introduction....................................................................................................................3
1.1 Background.......................................................................................................................3
1.2 Problem statement.............................................................................................................4
1.3 Aim, Objectives and Research Questions.........................................................................5
1.4 Research Structure............................................................................................................6
Chapter 2: Literature Review...........................................................................................................7
2.1 Concept of Social Media.......................................................................................................7
2.2 Different forms of social media.............................................................................................7
2.3 Violation of Privacy in Social Networking Sites...................................................................9
Twitter........................................................................................................................................14
Whatsapp...................................................................................................................................14
Snapchat.....................................................................................................................................15
Skype.........................................................................................................................................15
Spamming......................................................................................................................................16
2.4 Social Engineering Risks.....................................................................................................18
Account risks.................................................................................................................................21
Content Threats:.............................................................................................................................22
2.5 Remedies..............................................................................................................................24
Chapter 3: Research Methodology................................................................................................25
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Table of Contents
Chapter 1: Introduction....................................................................................................................3
1.1 Background.......................................................................................................................3
1.2 Problem statement.............................................................................................................4
1.3 Aim, Objectives and Research Questions.........................................................................5
1.4 Research Structure............................................................................................................6
Chapter 2: Literature Review...........................................................................................................7
2.1 Concept of Social Media.......................................................................................................7
2.2 Different forms of social media.............................................................................................7
2.3 Violation of Privacy in Social Networking Sites...................................................................9
Twitter........................................................................................................................................14
Whatsapp...................................................................................................................................14
Snapchat.....................................................................................................................................15
Skype.........................................................................................................................................15
Spamming......................................................................................................................................16
2.4 Social Engineering Risks.....................................................................................................18
Account risks.................................................................................................................................21
Content Threats:.............................................................................................................................22
2.5 Remedies..............................................................................................................................24
Chapter 3: Research Methodology................................................................................................25

3
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
3.1 Research Philosophy............................................................................................................25
3.2 Research Approach..............................................................................................................26
3.3 Research Design..................................................................................................................27
3.4 Data Collection technique....................................................................................................28
3.5 Sampling Method and Size..................................................................................................28
3.6 Data Analysis Method.........................................................................................................29
3.7 Ethical Consideration...........................................................................................................30
Chapter 4: Data Findings and Analysis.........................................................................................31
4.1 Quantitative Data Analysis..................................................................................................31
Chapter 5: Conclusion and Recommendations..............................................................................41
5.1 Conclusion...........................................................................................................................41
5.2 Recommendations................................................................................................................43
5.3 Future work..........................................................................................................................43
References......................................................................................................................................44
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
3.1 Research Philosophy............................................................................................................25
3.2 Research Approach..............................................................................................................26
3.3 Research Design..................................................................................................................27
3.4 Data Collection technique....................................................................................................28
3.5 Sampling Method and Size..................................................................................................28
3.6 Data Analysis Method.........................................................................................................29
3.7 Ethical Consideration...........................................................................................................30
Chapter 4: Data Findings and Analysis.........................................................................................31
4.1 Quantitative Data Analysis..................................................................................................31
Chapter 5: Conclusion and Recommendations..............................................................................41
5.1 Conclusion...........................................................................................................................41
5.2 Recommendations................................................................................................................43
5.3 Future work..........................................................................................................................43
References......................................................................................................................................44
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Chapter 1: Introduction
1.1 Background
Social media is a proper collection of different channels of online communication that have
been dedicated for taking inputs from community for collaborating and sharing contents. These
websites have been dedicated with social networking forums, social networking, micro blogging
and other social media types (Perrin 2015). Social media has become a part of the human life.
Most of the youngsters have been active on various social media platforms. They used to share
their personal details over different social media platforms including Facebook, Twitter, Snap
chat, Instagram and WhatsApp. Therefore, security and privacy of data has become a serious
issue over these social media platforms. There have been various cases reported related to breach
of privacy and security of data and information of users over social media.
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Chapter 1: Introduction
1.1 Background
Social media is a proper collection of different channels of online communication that have
been dedicated for taking inputs from community for collaborating and sharing contents. These
websites have been dedicated with social networking forums, social networking, micro blogging
and other social media types (Perrin 2015). Social media has become a part of the human life.
Most of the youngsters have been active on various social media platforms. They used to share
their personal details over different social media platforms including Facebook, Twitter, Snap
chat, Instagram and WhatsApp. Therefore, security and privacy of data has become a serious
issue over these social media platforms. There have been various cases reported related to breach
of privacy and security of data and information of users over social media.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
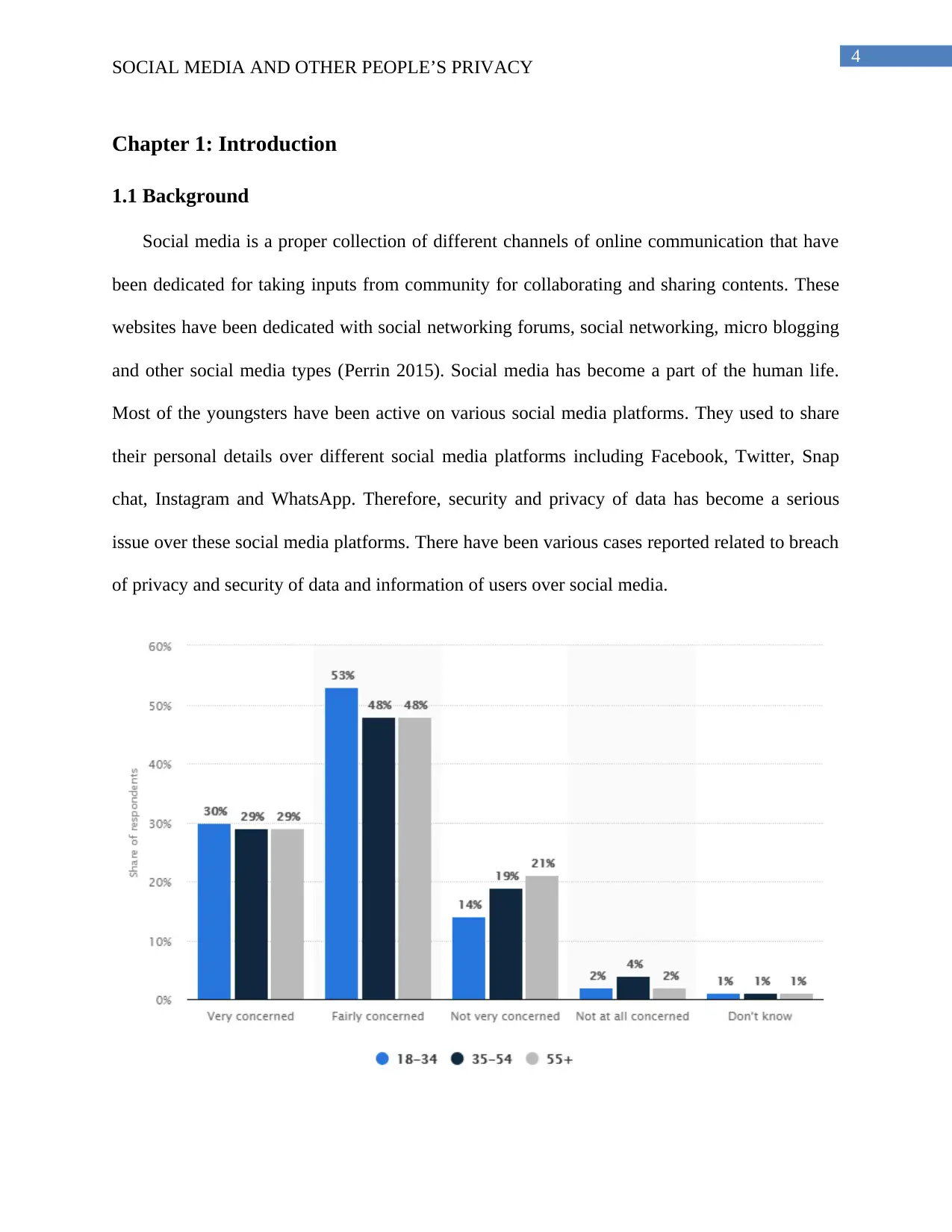
Figure 1: Level of concern about online privacy in the United Kingdom
(Source: Fuchs 2017)
Social media has been becoming an integral part of users in the real world. Most of the users
have been active on social media websites every day. Users have been positing their daily life
activities over the social media. Social media has brought various revolutionary changes in all
over the world (Tuten and Solomon 2017). The driving factors for the adoption of social media
have been progressively accessing proper functionality and flexibility of social technologies.
However, there have been various limitations and challenges faced over social media.
Users have been facing security and private issues over social media. There have been various
cases reported over the social media related to privacy and security of personal data of users.
This has been becoming a new threat over social media. Both males and females have been
facing cyber bullying issues over social media.
1.2 Problem statement
The major problem discussed in this research has been the security and privacy issues faced
by users over social media. The internet has been expanding its growth over various industries
and users. Most of the users have been activities over the social media and sharing their personal
and daily activities over the social media platforms. This has become an issue regarding safety
and security of their personal data uploaded over social media platforms (Yin et al. 2015). Many
researches have reported that their e have been increase in the cyber threats over social media.
Various social media platforms have been facing data breach issues. Many users have been
complaining about loss of their personal data and internet over the internet. The major problem
faced by users have been leak and misuse of their personal information on other illegal work.
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Figure 1: Level of concern about online privacy in the United Kingdom
(Source: Fuchs 2017)
Social media has been becoming an integral part of users in the real world. Most of the users
have been active on social media websites every day. Users have been positing their daily life
activities over the social media. Social media has brought various revolutionary changes in all
over the world (Tuten and Solomon 2017). The driving factors for the adoption of social media
have been progressively accessing proper functionality and flexibility of social technologies.
However, there have been various limitations and challenges faced over social media.
Users have been facing security and private issues over social media. There have been various
cases reported over the social media related to privacy and security of personal data of users.
This has been becoming a new threat over social media. Both males and females have been
facing cyber bullying issues over social media.
1.2 Problem statement
The major problem discussed in this research has been the security and privacy issues faced
by users over social media. The internet has been expanding its growth over various industries
and users. Most of the users have been activities over the social media and sharing their personal
and daily activities over the social media platforms. This has become an issue regarding safety
and security of their personal data uploaded over social media platforms (Yin et al. 2015). Many
researches have reported that their e have been increase in the cyber threats over social media.
Various social media platforms have been facing data breach issues. Many users have been
complaining about loss of their personal data and internet over the internet. The major problem
faced by users have been leak and misuse of their personal information on other illegal work.

6
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
The use of social media has been increasing on a daily basis. Therefore, the cyber security risk
has been increasing over social media platforms. Social media provide platform for sharing
personal information with others (Zhang and Gupta 2018). There has been lack of awareness
among users regarding sharing their personal information over social media. Therefore, this
create a huge threat for loss and misuse of personal information over the internet.
This research will be done identify the reasons behind privacy and security breach of data
and information users over social media. The aim of the research will be focusing in what degree
do social media users are caring about their privacy issues during sharing their personal
information over social media platforms. Therefore, there have been violation of various ethical
forms over the social media. This research has been focused on identifying the issues faced by
people over social media. This research has been done at social level for understanding their
views about their use over social media.
1.3 Aim, Objectives and Research Questions
The aim of this research has been focused on social media privacy issues faced by users over
social media.
Following are the research objectives:
To identify whether social media networks protect the personal information of their users
in the same fashion or are there any differences
To investigate who collects information about users apart from social media and spread
between parties
To investigate how much social media users know about how much information is shared
with other parties
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
The use of social media has been increasing on a daily basis. Therefore, the cyber security risk
has been increasing over social media platforms. Social media provide platform for sharing
personal information with others (Zhang and Gupta 2018). There has been lack of awareness
among users regarding sharing their personal information over social media. Therefore, this
create a huge threat for loss and misuse of personal information over the internet.
This research will be done identify the reasons behind privacy and security breach of data
and information users over social media. The aim of the research will be focusing in what degree
do social media users are caring about their privacy issues during sharing their personal
information over social media platforms. Therefore, there have been violation of various ethical
forms over the social media. This research has been focused on identifying the issues faced by
people over social media. This research has been done at social level for understanding their
views about their use over social media.
1.3 Aim, Objectives and Research Questions
The aim of this research has been focused on social media privacy issues faced by users over
social media.
Following are the research objectives:
To identify whether social media networks protect the personal information of their users
in the same fashion or are there any differences
To investigate who collects information about users apart from social media and spread
between parties
To investigate how much social media users know about how much information is shared
with other parties
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Following are the research questions:
Do social media networks protect the personal information of their users in the same
fashion or are there any differences?
Other than the social media network itself, who else collects information about its users
and how is the information spread between parties?
What do social media users know in the terms of how and how much information is being
spread? Do they care?
1.4 Research Structure
Figure 2: Research Structure
(Source: Created by author)
Chapter 1: Introduction
Chapter 2: Literature Review
Chapter 3: Research Methodology
Chapter 4: Data findings and analysis
Chapter 5: Conclusion and Recommendations
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Following are the research questions:
Do social media networks protect the personal information of their users in the same
fashion or are there any differences?
Other than the social media network itself, who else collects information about its users
and how is the information spread between parties?
What do social media users know in the terms of how and how much information is being
spread? Do they care?
1.4 Research Structure
Figure 2: Research Structure
(Source: Created by author)
Chapter 1: Introduction
Chapter 2: Literature Review
Chapter 3: Research Methodology
Chapter 4: Data findings and analysis
Chapter 5: Conclusion and Recommendations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Chapter 2: Literature Review
2.1 Concept of Social Media
Social Media refers to the form of media, which involves interactive participation. The
development of media can be divided into two different ages namely the broadcast age and the
interactive age. Broadcast age witnessed transferring of messages via television and radio and the
way of transferring messages was impersonal and time-consuming (Benson, Saridakis and
Tennakoon 2015). With the advancements in technology, interactive media came into force and
it became easier for individuals to interact in a more personal way. Social media enables
individuals to interact with many at a time and instant feedback can be obtained. The ease of
accessibility of social media has made it popular and it is the core of the ongoing revolution.
Social media involves some kind of digital platform that may be stationary or mobile. The two
main characteristics of social media are that it allows some sort of participation and it is
interactive in nature.
2.2 Different forms of social media
Some popular forms of social media in use are:
Email- The most common form of social media that is used in everyday life is electronic mail or
email. It is a form of exchanging messages between people using electronic devices. Email was
invented by Ray Tomlinson in the year 1960 (Wu, Shin and Luke 2017). It operates across the
network of computers that is termed as the internet. Previously it was mandatory for the sender
and the recipient to be online in order to send messages but at present, the emails use store and
forward model. Email acts as a reliable media to send documents, pictures and important files.
Examples of email are Gmail and Yahoo mail.
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Chapter 2: Literature Review
2.1 Concept of Social Media
Social Media refers to the form of media, which involves interactive participation. The
development of media can be divided into two different ages namely the broadcast age and the
interactive age. Broadcast age witnessed transferring of messages via television and radio and the
way of transferring messages was impersonal and time-consuming (Benson, Saridakis and
Tennakoon 2015). With the advancements in technology, interactive media came into force and
it became easier for individuals to interact in a more personal way. Social media enables
individuals to interact with many at a time and instant feedback can be obtained. The ease of
accessibility of social media has made it popular and it is the core of the ongoing revolution.
Social media involves some kind of digital platform that may be stationary or mobile. The two
main characteristics of social media are that it allows some sort of participation and it is
interactive in nature.
2.2 Different forms of social media
Some popular forms of social media in use are:
Email- The most common form of social media that is used in everyday life is electronic mail or
email. It is a form of exchanging messages between people using electronic devices. Email was
invented by Ray Tomlinson in the year 1960 (Wu, Shin and Luke 2017). It operates across the
network of computers that is termed as the internet. Previously it was mandatory for the sender
and the recipient to be online in order to send messages but at present, the emails use store and
forward model. Email acts as a reliable media to send documents, pictures and important files.
Examples of email are Gmail and Yahoo mail.

9
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Texters- Texting refers to the process of composing and sending e-messages, which
consist of alphanumeric characters in between users of laptops or desktops. The term originally
referred to messages being sent using SMS that is Short Message Service. Since then it has
grown widely to include multimedia images other than the alphanumeric texts. According to a
survey in 2017, it was seen that text messages are not only used by youth but also by adults for
social and personal purposes (Areni 2019). It has its applications in government and private
sectors as well where it is used as a medium to communicate between colleagues and authorities.
Text messages are used as an interaction medium with automated systems for example in case of
ordering products from e-commerce websites. Advertisers and service providers send messages
to mobile phone users about payment due dates and various promotion schemes using direct text
marketing.
Blogs- The word blog has been derived from the word weblog. It is a webpage that can be
accessed by an individual or a group to share information with a large group of people via
internet. Blogs are of many types according to the type of content shared and the way in which
the content is written. Information in a blog is displayed in reverse chronophilosophyal order so
that the recent ones come first (Kumar, Saravanakumar and Deepa 2016). Many blogs provide
comment section for particular subject and topic. Blogging can be used as a marketing strategy
as it helps in increasing online exposure thereby enabling small-scale businesses to become
leading industries.
Social Networking Sites- The social networking sites are a medium to reconnect with old
friends and acts as a bridge between the users staying at faraway places. Some popular sites are
Snapchat, Facebook and Whatsapp. Facebook is the widely used social networking site. It is an
American company that is headquartered in Menlo Park, California. Founded by Mark
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Texters- Texting refers to the process of composing and sending e-messages, which
consist of alphanumeric characters in between users of laptops or desktops. The term originally
referred to messages being sent using SMS that is Short Message Service. Since then it has
grown widely to include multimedia images other than the alphanumeric texts. According to a
survey in 2017, it was seen that text messages are not only used by youth but also by adults for
social and personal purposes (Areni 2019). It has its applications in government and private
sectors as well where it is used as a medium to communicate between colleagues and authorities.
Text messages are used as an interaction medium with automated systems for example in case of
ordering products from e-commerce websites. Advertisers and service providers send messages
to mobile phone users about payment due dates and various promotion schemes using direct text
marketing.
Blogs- The word blog has been derived from the word weblog. It is a webpage that can be
accessed by an individual or a group to share information with a large group of people via
internet. Blogs are of many types according to the type of content shared and the way in which
the content is written. Information in a blog is displayed in reverse chronophilosophyal order so
that the recent ones come first (Kumar, Saravanakumar and Deepa 2016). Many blogs provide
comment section for particular subject and topic. Blogging can be used as a marketing strategy
as it helps in increasing online exposure thereby enabling small-scale businesses to become
leading industries.
Social Networking Sites- The social networking sites are a medium to reconnect with old
friends and acts as a bridge between the users staying at faraway places. Some popular sites are
Snapchat, Facebook and Whatsapp. Facebook is the widely used social networking site. It is an
American company that is headquartered in Menlo Park, California. Founded by Mark
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Zuckerberg and his college friends it was the first networking site to achieve one billion accounts
(Subramaniyaswamy et al. 2017). Facebook helps to find and connect with friends, keeps
individuals updated with recent news related to the pages liked in the person’s profile and to
create a common page or group to voice on common concerns. LinkedIn is one of the
professional social networking sites and is available in more than 20 languages. It is a platform
that connects different businesses and helps them find and hire eligible candidates.
2.3 Violation of Privacy in Social Networking Sites
Some people are of the opinion that online privacy is their private matter as it is up to
them whether to share informations online but it is a wrong conception as an individual cannot
fully control this. For example, pictures shared on social networking sites by friends and if a
person is tagged then an individual’s information is leaking out though without he himself
directly uploading any such content. The results of a study by a dysfunctional social media site
showed that the population of this digital era might need to reconsider ways to control their
private information being published on social media and the limits of their privacy (Wang,
Pauleen and Zhang 2016). When individuals join social networking sites, in order to connect
with their friends there are many apps, which import the contacts from the contact list and this
gets available to the social networking sites. Social media collects and curates informations and
makes use of these informations and creates shadow profiles. In 2013, shadow profiles were first
detected with a Facebook bug, which shared the phone numbers, and the e-mail addresses of
approximately 6 million users with their friends without their prior consent (Wamba and Akter
2016). Though the bug was immediately addressed by Facebook, still some of its users had their
phone numbers updated on the site and available publicly. Facebook had collected the phone
numbers from the contact list of its users and used the informations to note the contacts of their
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Zuckerberg and his college friends it was the first networking site to achieve one billion accounts
(Subramaniyaswamy et al. 2017). Facebook helps to find and connect with friends, keeps
individuals updated with recent news related to the pages liked in the person’s profile and to
create a common page or group to voice on common concerns. LinkedIn is one of the
professional social networking sites and is available in more than 20 languages. It is a platform
that connects different businesses and helps them find and hire eligible candidates.
2.3 Violation of Privacy in Social Networking Sites
Some people are of the opinion that online privacy is their private matter as it is up to
them whether to share informations online but it is a wrong conception as an individual cannot
fully control this. For example, pictures shared on social networking sites by friends and if a
person is tagged then an individual’s information is leaking out though without he himself
directly uploading any such content. The results of a study by a dysfunctional social media site
showed that the population of this digital era might need to reconsider ways to control their
private information being published on social media and the limits of their privacy (Wang,
Pauleen and Zhang 2016). When individuals join social networking sites, in order to connect
with their friends there are many apps, which import the contacts from the contact list and this
gets available to the social networking sites. Social media collects and curates informations and
makes use of these informations and creates shadow profiles. In 2013, shadow profiles were first
detected with a Facebook bug, which shared the phone numbers, and the e-mail addresses of
approximately 6 million users with their friends without their prior consent (Wamba and Akter
2016). Though the bug was immediately addressed by Facebook, still some of its users had their
phone numbers updated on the site and available publicly. Facebook had collected the phone
numbers from the contact list of its users and used the informations to note the contacts of their
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
friends and it was fed in their account. It is more shocking to those who are not even in the social
networking platforms but still get their informations shared via their friend’s contact list. Thus, it
can be inferred that an individual is not in full control of his privacy as if his friends are in social
media he indirectly becomes a part of this. Informations from a friends profile can easily leak out
an individual’s private information such as his marital status, location, sexual orientation or
political affiliation (Wukich 2015). The issues related to the privacy of persons on online
platforms are growing at a faster rate. The smart phones are a revolutionary invention and have
enabled users to share anything at a click’s go. With the increasing use of smartphones, it has
become easy to share any content online and with every passing day the amount of informations
available online is increasing at an alarming rate. The context of some posts arouses privacy
issues as they reveal much about the physical and social information of the subject (Aldawood
and Skinner 2019). Privacy concerns are deep-rooted in the case of multimedia collections, as
they have the potential to reveal much of user’s personal data. Sharing of videos and pictures
pose a great threat to the teenagers succumbing to their vulnerability.
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
friends and it was fed in their account. It is more shocking to those who are not even in the social
networking platforms but still get their informations shared via their friend’s contact list. Thus, it
can be inferred that an individual is not in full control of his privacy as if his friends are in social
media he indirectly becomes a part of this. Informations from a friends profile can easily leak out
an individual’s private information such as his marital status, location, sexual orientation or
political affiliation (Wukich 2015). The issues related to the privacy of persons on online
platforms are growing at a faster rate. The smart phones are a revolutionary invention and have
enabled users to share anything at a click’s go. With the increasing use of smartphones, it has
become easy to share any content online and with every passing day the amount of informations
available online is increasing at an alarming rate. The context of some posts arouses privacy
issues as they reveal much about the physical and social information of the subject (Aldawood
and Skinner 2019). Privacy concerns are deep-rooted in the case of multimedia collections, as
they have the potential to reveal much of user’s personal data. Sharing of videos and pictures
pose a great threat to the teenagers succumbing to their vulnerability.

12
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
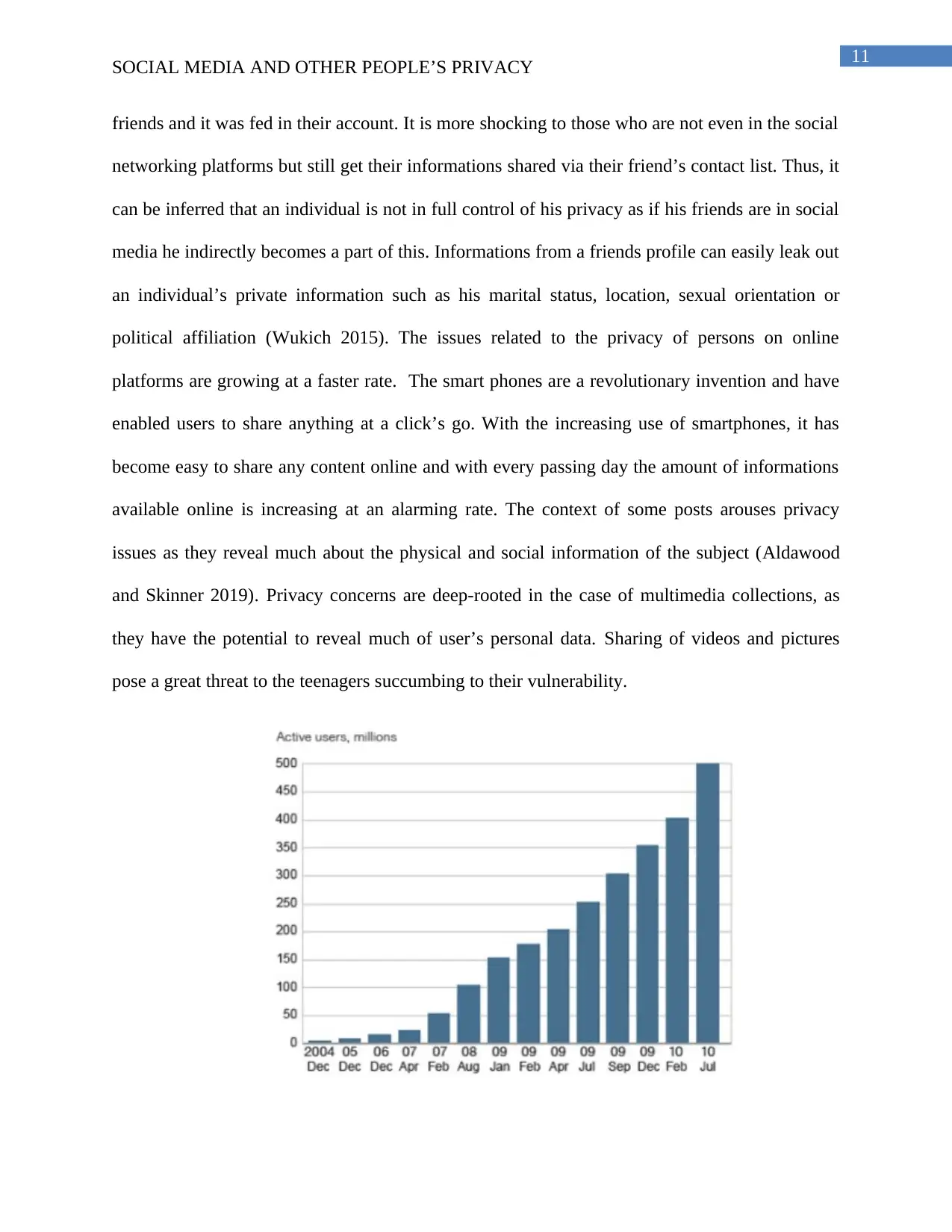
Figure 2: The rise of Facebook
(Source: Zhang 2018)
There has been several hacks in privacy issues of Facebook users. Considering the case in
August 2007, the code used by users to access the home page of Facebook had been made
public. Beacon, a system launched by Facebook was in trouble when it was spying on the users
actions on other sites and feeding it to the giant site.(Soomro, Shah and Ahmed 2016). In June
2011, Facebook came up with automatic facial recognition feature named “Tag Suggestions”.
This feature makes a comparison between newly uploaded pictures and those of the user’s
friends and then suggests photo tags. European Union data-protection regulators were of the
opinion that if privacy rules are violated it would investigate the feature. Facebook speaking for
the feature said that if a user wants he could disable the feature. Location based social networks
are a part of Location based services. It refers to the link being made by GPS that is Global
Positioning System that tracks user’s location. They are referred to as Geosocial Networking.
As reported in Microsoft Research “a LBSN does not only mean adding a location to an
existing social network so that people in the social structure can share location-embedded
information, but also consists of the new social structure made up of individuals connected by
the interdependency derived from their locations in the physical world as well as their location-
tagged media content, such as photos, video, and texts” (Hajli and Lin 2016). The connection
between users far exceeds sharing only physical locations as it also involves sharing common
interests and activities. These pervasive tools are a challenge to privacy. LBSN users publish
their information without thinking of the privacy issues related such as anyone will be able to
track their whereabouts and could easily stalk them. The Russian-built app named Girls Around
Me aroused privacy concerns as it was using Foursquare’s API to find out people based on their
SOCIAL MEDIA AND OTHER PEOPLE’S PRIVACY
Figure 2: The rise of Facebook
(Source: Zhang 2018)
There has been several hacks in privacy issues of Facebook users. Considering the case in
August 2007, the code used by users to access the home page of Facebook had been made
public. Beacon, a system launched by Facebook was in trouble when it was spying on the users
actions on other sites and feeding it to the giant site.(Soomro, Shah and Ahmed 2016). In June
2011, Facebook came up with automatic facial recognition feature named “Tag Suggestions”.
This feature makes a comparison between newly uploaded pictures and those of the user’s
friends and then suggests photo tags. European Union data-protection regulators were of the
opinion that if privacy rules are violated it would investigate the feature. Facebook speaking for
the feature said that if a user wants he could disable the feature. Location based social networks
are a part of Location based services. It refers to the link being made by GPS that is Global
Positioning System that tracks user’s location. They are referred to as Geosocial Networking.
As reported in Microsoft Research “a LBSN does not only mean adding a location to an
existing social network so that people in the social structure can share location-embedded
information, but also consists of the new social structure made up of individuals connected by
the interdependency derived from their locations in the physical world as well as their location-
tagged media content, such as photos, video, and texts” (Hajli and Lin 2016). The connection
between users far exceeds sharing only physical locations as it also involves sharing common
interests and activities. These pervasive tools are a challenge to privacy. LBSN users publish
their information without thinking of the privacy issues related such as anyone will be able to
track their whereabouts and could easily stalk them. The Russian-built app named Girls Around
Me aroused privacy concerns as it was using Foursquare’s API to find out people based on their
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 53
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





