Social Media Privacy Report
VerifiedAdded on 2019/10/12
|42
|15288
|349
Report
AI Summary
This extensive report delves into the multifaceted issue of privacy and security within social media platforms. It begins by differentiating between security and privacy breaches, highlighting the increased vulnerability of popular sites due to the sheer volume of data processed. The report then examines specific instances of security lapses, such as the MySpace "Samy" worm, and explores vulnerabilities inherent in the design of social media APIs, using Facebook as a prime example. A significant portion of the report is dedicated to a literature review, synthesizing existing research on privacy definitions, online personal information privacy, online social network privacy, and online privacy risks. The review covers various perspectives on privacy, including the challenges faced by website developers, the importance of user control over privacy settings, and the potential for misuse of personal information. The report also discusses the role of protective technologies, social awareness, and legislation in addressing privacy concerns. The research methodology section details the qualitative approach employed, including in-depth interviews conducted within a government organization. The data analysis section presents findings from surveys and interviews, revealing user behaviors, awareness of privacy settings, and attitudes towards privacy protection. The report concludes by discussing the ethical code of conduct and legal frameworks designed to regulate social media use and protect user privacy, acknowledging limitations in the current regulatory landscape.

Introduction
When it comes to privacy and security issues on social networks, "the sites most likely to suffer
from issues are the most popular ones," Graham Cluley, Chief Technology Officer at UK tech
security firm Sophos says. But security issues and privacy issues are entirely two different
beasts. A security issue occurs when a hacker gains unauthorized access to a site's protected
coding or written language. Privacy issues, those involving the unwarranted access of private
information, don't necessarily have to involve security breaches. Someone can gain access to
confidential information by simply watching you type your password. But both types of breaches
are often intertwined on social networks, especially since anyone who breaches a site's security
network opens the door to easy access to private information belonging to any user. But the
potential harm to an individual user really boils down to how much a user engages in a social
networking site, as well as the amount of information they're willing to share. In other words, the
Facebook user with 900 friends and 60 group memberships is a lot more likely to be harmed by a
breach than someone who barely uses the site.
Security lapses on social networks don't necessarily involve the exploitation of a user's private
information. Take, for example, the infamous "Samy" MySpace XSS worm that effectively shut
the site down for a few days in October 2005. The "Samy" virus (named after the virus' creator)
was fairly harmless, and the malware snarkily added the words "Samy Is My Hero" to the top of
every affected user's MySpace profile page. A colossal inconvenience, naturally, but nobody's
identity was stolen and no private information was leaked. In the end, the problem galvanized the
MySpace team to roll up their sleeves and seriously tighten the site's security. Result: no major
break-ins since. Unfortunately, these kinds of breaches, purely for sport in "Samy's" case, are
rare.
The reason social network security and privacy lapses exist results simply from the astronomical
amounts of information the sites process each and every day that end up making it that much
easier to exploit a single flaw in the system. Features that invite user participation — messages,
invitations, photos, open platform applications, etc. — are often the avenues used to gain access
to private information, especially in the case of Facebook. Adrienne Felt, a Ph.D. candidate at
Berkeley, made small headlines last year when she exposed a potentially devastating hole in the
framework of Facebook's third-party application programming interface (API) which allows for
easy theft of private information. Felt and her co-researchers found that third-party platform
applications for Facebook gave developers access to far more information (addresses, pictures,
interests, etc.) than needed to run the app.
This potential privacy breach is actually built into the systematic framework of Facebook, and
unfortunately the flaw renders the system almost indefensible. "The question for social networks
is resolving the difference between mistakes in implementation and what the design of the
application platform is intended to allow," David Evans, Assistant Professor of Computer
Science at the University of Virginia, says. There's also the question of whom we should hold
responsible for the over-sharing of user data? That resolution isn't likely to come anytime soon,
says Evans, because a new, more regulated API would require Facebook "to break a lot of
When it comes to privacy and security issues on social networks, "the sites most likely to suffer
from issues are the most popular ones," Graham Cluley, Chief Technology Officer at UK tech
security firm Sophos says. But security issues and privacy issues are entirely two different
beasts. A security issue occurs when a hacker gains unauthorized access to a site's protected
coding or written language. Privacy issues, those involving the unwarranted access of private
information, don't necessarily have to involve security breaches. Someone can gain access to
confidential information by simply watching you type your password. But both types of breaches
are often intertwined on social networks, especially since anyone who breaches a site's security
network opens the door to easy access to private information belonging to any user. But the
potential harm to an individual user really boils down to how much a user engages in a social
networking site, as well as the amount of information they're willing to share. In other words, the
Facebook user with 900 friends and 60 group memberships is a lot more likely to be harmed by a
breach than someone who barely uses the site.
Security lapses on social networks don't necessarily involve the exploitation of a user's private
information. Take, for example, the infamous "Samy" MySpace XSS worm that effectively shut
the site down for a few days in October 2005. The "Samy" virus (named after the virus' creator)
was fairly harmless, and the malware snarkily added the words "Samy Is My Hero" to the top of
every affected user's MySpace profile page. A colossal inconvenience, naturally, but nobody's
identity was stolen and no private information was leaked. In the end, the problem galvanized the
MySpace team to roll up their sleeves and seriously tighten the site's security. Result: no major
break-ins since. Unfortunately, these kinds of breaches, purely for sport in "Samy's" case, are
rare.
The reason social network security and privacy lapses exist results simply from the astronomical
amounts of information the sites process each and every day that end up making it that much
easier to exploit a single flaw in the system. Features that invite user participation — messages,
invitations, photos, open platform applications, etc. — are often the avenues used to gain access
to private information, especially in the case of Facebook. Adrienne Felt, a Ph.D. candidate at
Berkeley, made small headlines last year when she exposed a potentially devastating hole in the
framework of Facebook's third-party application programming interface (API) which allows for
easy theft of private information. Felt and her co-researchers found that third-party platform
applications for Facebook gave developers access to far more information (addresses, pictures,
interests, etc.) than needed to run the app.
This potential privacy breach is actually built into the systematic framework of Facebook, and
unfortunately the flaw renders the system almost indefensible. "The question for social networks
is resolving the difference between mistakes in implementation and what the design of the
application platform is intended to allow," David Evans, Assistant Professor of Computer
Science at the University of Virginia, says. There's also the question of whom we should hold
responsible for the over-sharing of user data? That resolution isn't likely to come anytime soon,
says Evans, because a new, more regulated API would require Facebook "to break a lot of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

applications, and a lot of companies are trying to make money off applications now." Felt agrees,
noting that now "there are marketing businesses built on top of the idea that third parties can get
access to data on Facebook."
The problems plaguing social network security and privacy issues, for now, can only be resolved
if users take a more careful approach to what they share and how much. With the growth of
social networks, it's becoming harder to effectively monitor and protect site users and their
activity because the tasks of security programmers becomes increasingly spread out. Imagine if a
prison whose inmate count jumped from a few dozen to 250 million in less than five years only
employed 300 guards (in the case of MySpace). In response to the potential threats that users are
expose to, most of the major networks now enable users to set privacy controls for who has the
ability to view their information. But, considering the application loophole in Facebook,
increased privacy settings don't always guarantee privacy. But even when the flawed API was
publicly exposed, "Facebook changed the wording of the user agreement a little bit, but nothing
technically to solve the problem," says Evans. That means if a nefarious application developer
wanted to sell the personal info of people who used his app to advertising companies, he or she
could.
Yet users still post tons of personal data on social networks without batting an eye. It's only
natural. Anonymity and the fact that you're communicating with a machine instead of an actual
person (or people in the case of social networking) makes sharing a lot easier. "People should
just exercise common sense online, but the problem with common sense is that it's not very
common. If you wouldn't invite these people into your house to see your cat, you certainly
wouldn't let them see pictures from holiday," says Cluley.
In the end, the only tried and true solution to social network privacy and security issues is to
limit your presence altogether. Don't post anything you wouldn't mind telling a complete
stranger, because in reality that's the potential for access. Be careful who you add as a "friend,"
because there's simply no way of verifying a user's actual identity online. Cluley compares it to a
rep from your company's IT department calling to ask for your login password — "Most people
will give it over" with no proof of the IT rep actually existing. The caller might be your IT rep,
or she might not. "This kind of scam happens all the time," says Cluley. Friends on social
networks should know that real friends should know personal information already, negating the
need to post it online.
Will there ever be a security breach-free social network? Probably not. "Any complex system has
vulnerabilities in it. It's just the nature of building something above a certain level of
complexity," says Professor Evans. According to Felt, the best idea is a completely private social
network. "It simply requires that there's no gossip in the circle, by which I mean one person who
sets their privacy settings so low that third parties can use them to get to their friends."
"Social networks are great fun, and can be advantageous but people really need to understand
that it's complicated world and you need to step wisely," Cluley says.
noting that now "there are marketing businesses built on top of the idea that third parties can get
access to data on Facebook."
The problems plaguing social network security and privacy issues, for now, can only be resolved
if users take a more careful approach to what they share and how much. With the growth of
social networks, it's becoming harder to effectively monitor and protect site users and their
activity because the tasks of security programmers becomes increasingly spread out. Imagine if a
prison whose inmate count jumped from a few dozen to 250 million in less than five years only
employed 300 guards (in the case of MySpace). In response to the potential threats that users are
expose to, most of the major networks now enable users to set privacy controls for who has the
ability to view their information. But, considering the application loophole in Facebook,
increased privacy settings don't always guarantee privacy. But even when the flawed API was
publicly exposed, "Facebook changed the wording of the user agreement a little bit, but nothing
technically to solve the problem," says Evans. That means if a nefarious application developer
wanted to sell the personal info of people who used his app to advertising companies, he or she
could.
Yet users still post tons of personal data on social networks without batting an eye. It's only
natural. Anonymity and the fact that you're communicating with a machine instead of an actual
person (or people in the case of social networking) makes sharing a lot easier. "People should
just exercise common sense online, but the problem with common sense is that it's not very
common. If you wouldn't invite these people into your house to see your cat, you certainly
wouldn't let them see pictures from holiday," says Cluley.
In the end, the only tried and true solution to social network privacy and security issues is to
limit your presence altogether. Don't post anything you wouldn't mind telling a complete
stranger, because in reality that's the potential for access. Be careful who you add as a "friend,"
because there's simply no way of verifying a user's actual identity online. Cluley compares it to a
rep from your company's IT department calling to ask for your login password — "Most people
will give it over" with no proof of the IT rep actually existing. The caller might be your IT rep,
or she might not. "This kind of scam happens all the time," says Cluley. Friends on social
networks should know that real friends should know personal information already, negating the
need to post it online.
Will there ever be a security breach-free social network? Probably not. "Any complex system has
vulnerabilities in it. It's just the nature of building something above a certain level of
complexity," says Professor Evans. According to Felt, the best idea is a completely private social
network. "It simply requires that there's no gossip in the circle, by which I mean one person who
sets their privacy settings so low that third parties can use them to get to their friends."
"Social networks are great fun, and can be advantageous but people really need to understand
that it's complicated world and you need to step wisely," Cluley says.

LITERATURE REVIEW
Currently, in the era of advanced internet technology, Social Network becomes incredibly
popular tool on the internet and becomes widely used around the world. It is powerful tool in any
ages of people especially among teenagers and young adults in the propose of communication
and self-expression [1], and it is easy mean of sharing information with other users who has a
common interest such as photos, likes, dislikes, interests, relationship status, job details, current
town details, political views, religious views etc. [2] [3] [4].Social networking sites and
associated privacy concerns is one of the most debated topic nowadays as participation in such
sites has increased dramatically. A number of journals and articles come up with this issue that
how the increase in the usage of social networking sites is leading to various online crimes.
Unfortunately, though this technology most of users are not aware of the privacy risk associated
whenever they shared sensitive information in the internet [4], so that privacy concern will be
raised among those online interactions if their personal information has been shared to other
people [3] [5].
Definitions of privacy
The word privacy has many subtly different meanings, ranging from personal privacy (which
includes seclusion and bodily privacy) to information privacy, each with their own definition.
Privacy on the Web in general revolves mostly around Information Privacy, as defined below in
the IITF wording that Kang uses: Information Privacy is “an individual’s claim to control the
terms under which personal information–information identifiable to the individual–is acquired,
disclosed or used.”Palen and Dourish classify three privacy boundaries with which individuals
are struggling. 1. The disclosure boundary (managing the tension between private and public), 2.
The identity boundary (managing self representation with specific audience, e.g. one will behave
differently at work than when among friends), 3. The temporal boundary (managing past actions
with future expectations; user behavior may change over time).
Online personal information privacy
Protecting the privacy of personal information is one of the biggest challenges facing website
developers, especially social network providers. Several researchers have discussed the issue of
privacy. Bae and Kim (2010) suggested that, in order to achieve a high level of privacy, the user
should be given the authority to control the privacy settings when he/she receives or requests a
service related to his/her personal information. The authors noted the importance of designing a
privacy policy to protect personal information by blocking some people from seeing all or part of
the user’s personal information. They also designed a privacy model using mobile agents.
Dötzer (2006, p.4) stated that “once privacy is lost, it is very hard to re-establish that state of
personal rights.” This shows that privacy is essential to the construction of all communication
systems, particularly mobile systems. The concept of self-representation enables users to interact
and introduce themselves based on the data placed on profile pages such as name and pictures
with others. Privacy is an important aspect of self-representation on online social networks since
people share certain information with the public and receive information or comments from
others. The nature and complexity of the Internet cause some threats to web privacy
(Bouguettaya&Eltoweissy 2003). According to Wang and Cui (2008), privacy is a state or
Currently, in the era of advanced internet technology, Social Network becomes incredibly
popular tool on the internet and becomes widely used around the world. It is powerful tool in any
ages of people especially among teenagers and young adults in the propose of communication
and self-expression [1], and it is easy mean of sharing information with other users who has a
common interest such as photos, likes, dislikes, interests, relationship status, job details, current
town details, political views, religious views etc. [2] [3] [4].Social networking sites and
associated privacy concerns is one of the most debated topic nowadays as participation in such
sites has increased dramatically. A number of journals and articles come up with this issue that
how the increase in the usage of social networking sites is leading to various online crimes.
Unfortunately, though this technology most of users are not aware of the privacy risk associated
whenever they shared sensitive information in the internet [4], so that privacy concern will be
raised among those online interactions if their personal information has been shared to other
people [3] [5].
Definitions of privacy
The word privacy has many subtly different meanings, ranging from personal privacy (which
includes seclusion and bodily privacy) to information privacy, each with their own definition.
Privacy on the Web in general revolves mostly around Information Privacy, as defined below in
the IITF wording that Kang uses: Information Privacy is “an individual’s claim to control the
terms under which personal information–information identifiable to the individual–is acquired,
disclosed or used.”Palen and Dourish classify three privacy boundaries with which individuals
are struggling. 1. The disclosure boundary (managing the tension between private and public), 2.
The identity boundary (managing self representation with specific audience, e.g. one will behave
differently at work than when among friends), 3. The temporal boundary (managing past actions
with future expectations; user behavior may change over time).
Online personal information privacy
Protecting the privacy of personal information is one of the biggest challenges facing website
developers, especially social network providers. Several researchers have discussed the issue of
privacy. Bae and Kim (2010) suggested that, in order to achieve a high level of privacy, the user
should be given the authority to control the privacy settings when he/she receives or requests a
service related to his/her personal information. The authors noted the importance of designing a
privacy policy to protect personal information by blocking some people from seeing all or part of
the user’s personal information. They also designed a privacy model using mobile agents.
Dötzer (2006, p.4) stated that “once privacy is lost, it is very hard to re-establish that state of
personal rights.” This shows that privacy is essential to the construction of all communication
systems, particularly mobile systems. The concept of self-representation enables users to interact
and introduce themselves based on the data placed on profile pages such as name and pictures
with others. Privacy is an important aspect of self-representation on online social networks since
people share certain information with the public and receive information or comments from
others. The nature and complexity of the Internet cause some threats to web privacy
(Bouguettaya&Eltoweissy 2003). According to Wang and Cui (2008), privacy is a state or
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

condition of limited access to a person. Privacy regulations can be defined as a set of rules or
policies set by users to achieve a certain level of privacy. In terms of location privacy, privacy
regulations restrict access to information on a user’s location. Each privacy rule or policy can
include some restrictions (Sadeh& Hong 2009). Although there is no policy mandating online
personal information privacy, some types of privacy solutions do exist (Passant et al. 2009).
These solutions can be classified into: protective technologies, social awareness and legislative
support. Protective technologies, such as strong authentication and access control, have
developed quickly and have evolved over time. These rely on encryption as a way to solve
privacy concerns. The second type of solution, social awareness, involves educating people
about the possible risks of personal information misuse when they provide data such as their
home address and mobile phone number. Lastly, legislation can be enacted to clarify aspects of
the agreement with users to protect the collection of personal information under the framework
of the law (Campisi, Maiorana&Neri 2009).
Since the inception of the first social networking site, SixDegrees.com at 1997 (Boyd and
Ellison, 2008), the social networking craze has grown beyond all expectations. Data privacy is a
fundamental problem in today's information era. Enormous amounts of data are collected by
government agencies, search engines, social networking systems, hospitals, financial institutions,
and other organizations, and are stored in databases. Those stored information is very crucial for
individuals, people might misuse this information. The problems that exist in the real world such
as theft, fraud, vandalism also exists in online Web 2 environments an identity thief.
According to consumer security risks survey 2014, is done by B2B International in conjunction
with Kaspersky Lab shown that even using social networking is worldwide, but however there
are minority of them understanding the risks of using social networking especially in terms of
using mobile device to access the sites. Correspondingly, more than 78% of correspondents did
not concern their information to be targeted by cyber-attacks or cyber-crime and they though that
no any dangerous with any activities on their social network. The survey also found that one of
ten has ever conversed to anonymous person about personal information, while 15% sending
personal information which has not been exposed anywhere before through social network.
Furthermore, 12 % of correspondents using public Wi-Fi to fill online account information, but
only 18% of them who concerned that their personal information disclosure is excessive or not
and 7% seriously considered their communicating through social networking is one of major
factor which information will be lose [6]. Every social network sites ask users to accomplish a
profile which contains privacy information including name, address, email and so on. Through
this information is claim to be danger which can be easily accessed by unexpected person [7] [8],
but what is happening today, most of social network users tend to public real identity and post
private information where privacy will be raised [9]. Accordingly, [3] [4] [7] [8] [10], they
described that online social networking data is of great help to the researchers, analysts, and any
kind of third party who has opportunity to mine and use data for particular purposes such as
spamming, fishing, targeted advertising and so on [4]. This is because sensitive information and
their interaction are stored in social OSN server are not always honest and transparent due to the
nature of OSN allows third parties to collect and analyze easily [9]. Raji and her colleagues
demonstrated that there are some principle privacy problems in social network like Facebook.
policies set by users to achieve a certain level of privacy. In terms of location privacy, privacy
regulations restrict access to information on a user’s location. Each privacy rule or policy can
include some restrictions (Sadeh& Hong 2009). Although there is no policy mandating online
personal information privacy, some types of privacy solutions do exist (Passant et al. 2009).
These solutions can be classified into: protective technologies, social awareness and legislative
support. Protective technologies, such as strong authentication and access control, have
developed quickly and have evolved over time. These rely on encryption as a way to solve
privacy concerns. The second type of solution, social awareness, involves educating people
about the possible risks of personal information misuse when they provide data such as their
home address and mobile phone number. Lastly, legislation can be enacted to clarify aspects of
the agreement with users to protect the collection of personal information under the framework
of the law (Campisi, Maiorana&Neri 2009).
Since the inception of the first social networking site, SixDegrees.com at 1997 (Boyd and
Ellison, 2008), the social networking craze has grown beyond all expectations. Data privacy is a
fundamental problem in today's information era. Enormous amounts of data are collected by
government agencies, search engines, social networking systems, hospitals, financial institutions,
and other organizations, and are stored in databases. Those stored information is very crucial for
individuals, people might misuse this information. The problems that exist in the real world such
as theft, fraud, vandalism also exists in online Web 2 environments an identity thief.
According to consumer security risks survey 2014, is done by B2B International in conjunction
with Kaspersky Lab shown that even using social networking is worldwide, but however there
are minority of them understanding the risks of using social networking especially in terms of
using mobile device to access the sites. Correspondingly, more than 78% of correspondents did
not concern their information to be targeted by cyber-attacks or cyber-crime and they though that
no any dangerous with any activities on their social network. The survey also found that one of
ten has ever conversed to anonymous person about personal information, while 15% sending
personal information which has not been exposed anywhere before through social network.
Furthermore, 12 % of correspondents using public Wi-Fi to fill online account information, but
only 18% of them who concerned that their personal information disclosure is excessive or not
and 7% seriously considered their communicating through social networking is one of major
factor which information will be lose [6]. Every social network sites ask users to accomplish a
profile which contains privacy information including name, address, email and so on. Through
this information is claim to be danger which can be easily accessed by unexpected person [7] [8],
but what is happening today, most of social network users tend to public real identity and post
private information where privacy will be raised [9]. Accordingly, [3] [4] [7] [8] [10], they
described that online social networking data is of great help to the researchers, analysts, and any
kind of third party who has opportunity to mine and use data for particular purposes such as
spamming, fishing, targeted advertising and so on [4]. This is because sensitive information and
their interaction are stored in social OSN server are not always honest and transparent due to the
nature of OSN allows third parties to collect and analyze easily [9]. Raji and her colleagues
demonstrated that there are some principle privacy problems in social network like Facebook.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

For instance, Users used their real information to create an account profile to the rest of the
Facebook users, The default privacy settings are not enough in Facebook, so users expose too
much information to others users, Users do not change the OSN default privacy settings that are
provided, and Sometime it is unavailable to adjust the privacy setting which is offered by
Facebook such as the users can see the whole his or her shared information whenever users add
his or her to be in friend list [9].
However, sometime there is a must to users to reveal personal information in particular reason,
as demonstrated by [7]. They also illustrated that users have to reveal the personal information
on social network in order to be effective and do this for maturing their identities. In reality,
online communication can bring them to be intensive revelation compared to face to face
communication. Furthermore, in the face of information of behavior of users are able to
conceptualize as continuum which describes as information privacy protection behavior. This
means information can disclose accurately in one side, but it is not for other sides. By the way,
users can participate all and can protecting their personal information at the same time by partly
disclosing of them.
A blog in a website DashBurst clearly mentions that “with the rise of social media, privacy
concerns have taken a backseat in recent years (Trenchard, 2013).” It talks about the potential
dangers that a young user may likely face while using the social networking site. Thus it
becomes very important for one to read the privacy policies and measures offered by these sites
in order to have a safe online networking. Further, the blog also states the privacy policy changes
brought out by the popular sites like Facebook and Twitter and how it has affected the users. One
of the main reasons cited by experts and research studies for such tremendous popularity of the
social networking sites is the emergence of sites that offer the scope of connectivity in this
virtual world almost at any time of the day. People get in touch with near and dear ones with the
services like Facebook, Twitter, Orkut, LinkedIn, MySpace, etc (Dutton, 2004). In social
networking sites, sharing of private information and giving updates of day to day happening is a
latest trend. These sites heavily caters to the young brigade especially the age group between 15
to 25 years. Sometimes it has been observed that youngsters use these sites for sharing news or
any information rather than sharing it personally. Even if they meet in the morning in college,
information is shared mostly through the social media sites. It shows the growing dependency on
such sites (Kabay, 2010). It is strange enough to note that communication process is hugely
getting affected through the advancement of the internet. With the controversial changes made
by the popular social networking site Facebook in 2009, it had beome quite impossible to
maintain a safe invisible account (Trenchard, 2013). By analysing the personal information
revelation behaviour of the users, it has been mainly found out that this factor mainly revolves
around hobbies and interests although it also has other directions. Like for insance, semi-public
information may include schooling or employment details, whereas personal information may
include drinking or drug habits or sexual orientation, etc (Gross & Acquisti, 2005). The apparent
openness of users of the social networking sites calls for unncessary attention from strangers
quite possibly leading to online victimization. It is very easy to join a social networking site. But
without proper knowledge of the security measures, one can be a easy trap for the third parties
like the hackers (Gross & Acquisti, 2005).
Facebook users, The default privacy settings are not enough in Facebook, so users expose too
much information to others users, Users do not change the OSN default privacy settings that are
provided, and Sometime it is unavailable to adjust the privacy setting which is offered by
Facebook such as the users can see the whole his or her shared information whenever users add
his or her to be in friend list [9].
However, sometime there is a must to users to reveal personal information in particular reason,
as demonstrated by [7]. They also illustrated that users have to reveal the personal information
on social network in order to be effective and do this for maturing their identities. In reality,
online communication can bring them to be intensive revelation compared to face to face
communication. Furthermore, in the face of information of behavior of users are able to
conceptualize as continuum which describes as information privacy protection behavior. This
means information can disclose accurately in one side, but it is not for other sides. By the way,
users can participate all and can protecting their personal information at the same time by partly
disclosing of them.
A blog in a website DashBurst clearly mentions that “with the rise of social media, privacy
concerns have taken a backseat in recent years (Trenchard, 2013).” It talks about the potential
dangers that a young user may likely face while using the social networking site. Thus it
becomes very important for one to read the privacy policies and measures offered by these sites
in order to have a safe online networking. Further, the blog also states the privacy policy changes
brought out by the popular sites like Facebook and Twitter and how it has affected the users. One
of the main reasons cited by experts and research studies for such tremendous popularity of the
social networking sites is the emergence of sites that offer the scope of connectivity in this
virtual world almost at any time of the day. People get in touch with near and dear ones with the
services like Facebook, Twitter, Orkut, LinkedIn, MySpace, etc (Dutton, 2004). In social
networking sites, sharing of private information and giving updates of day to day happening is a
latest trend. These sites heavily caters to the young brigade especially the age group between 15
to 25 years. Sometimes it has been observed that youngsters use these sites for sharing news or
any information rather than sharing it personally. Even if they meet in the morning in college,
information is shared mostly through the social media sites. It shows the growing dependency on
such sites (Kabay, 2010). It is strange enough to note that communication process is hugely
getting affected through the advancement of the internet. With the controversial changes made
by the popular social networking site Facebook in 2009, it had beome quite impossible to
maintain a safe invisible account (Trenchard, 2013). By analysing the personal information
revelation behaviour of the users, it has been mainly found out that this factor mainly revolves
around hobbies and interests although it also has other directions. Like for insance, semi-public
information may include schooling or employment details, whereas personal information may
include drinking or drug habits or sexual orientation, etc (Gross & Acquisti, 2005). The apparent
openness of users of the social networking sites calls for unncessary attention from strangers
quite possibly leading to online victimization. It is very easy to join a social networking site. But
without proper knowledge of the security measures, one can be a easy trap for the third parties
like the hackers (Gross & Acquisti, 2005).

Most social networks offer privacy settings that are simple to use, but coarse. They often require
the user to set the visibility for each profile item to either private, friends only, or public.
Sometimes a few more options are given. In the end it boils down to a list of items and check
boxes to either opt-in or opt-out of disclosing these items to certain groups, limiting user control.
Gross and Acquisti show in a case study that most users do not change the default privacy
settings as provided by the OSN. Furthermore these users share a large amount of information on
their profile. Tufecki [27] concludes in his case study that privacy-aware users are more reluctant
to join social networks. However once a privacy aware user joins he is willing to disclose a lot of
information and a user’s privacy is regulated mostly through visibility, i.e. the privacy settings of
the OSN (Online Social Networks). This privacy aware user aims to remain in control.
Furthermore users are more pre-occupied with the current visibility of their information and do
not look towards future implications. It seems that users implicitly trust social network providers
to handle user data in a fair and conscientious way.
Ahern, Eckles et al. (2007: 357) analysing the issue and conducting studies on Privacy Patterns
and Considerations in online and mobile photo sharing claim: The growing amount of online
personal content exposes users to a new set of privacy concerns. Digital cameras, and lately, a
new class of camera phone applications that can upload photos or video content directly to the
web, make publishing of personal content increasingly easy. Privacy concerns are especially
acute in the case of multimedia collections, as they could reveal much of the user’s personal and
social environment.[9]
Online social network privacy
George (2006) cited the case of US college athletes whose pictures, which they posted online,
were misused by a website, which publishes stories about scandals in sport. The author pointed
out that the issue of privacy has not gone unnoticed by social network providers. Gross and
Acquisti (2005) conducted a study on a sample of 4,000 students from Carnegie Mellon
University who use social network accounts. They found that a large proportion of students did
not care about the privacy risks that might increase the chance of a third party misusing a
student’s personal information. Another study by the same authors claimed that more than 77
percent of the respondents did not read privacy policies (Acquisti& Gross 2006). The ability to
control privacy options is essential to increasing the users’ confidence in their social network
providers. Since Internet users represent a range of different cultures and ages, privacy options
should be clear, simple and easy to use. Users must have the ability to control their privacy
options at any time. These privacy options allow users to accept or reject the dissemination of
their information to others. For example, some users do not want to publish sensitive information
such as health or medical information (Samavi&Consens 2010). These users are aware that
people with less than honourable intentions can harm adults or children by misusing their
personal information. A study conducted by Casarosa (2010) found that minors are interested in
new technologies and the Internet, and can be contacted by strangers online asking to form a
friendship. When a website publishes the personal information of a minor without giving the
child’s parents (or the child’s guardian) the authority to select privacy options, potential
predators can use some of the minor’s personal information, such as a mobile phone number, to
engage in sexual contact (Casarosa 2010).
the user to set the visibility for each profile item to either private, friends only, or public.
Sometimes a few more options are given. In the end it boils down to a list of items and check
boxes to either opt-in or opt-out of disclosing these items to certain groups, limiting user control.
Gross and Acquisti show in a case study that most users do not change the default privacy
settings as provided by the OSN. Furthermore these users share a large amount of information on
their profile. Tufecki [27] concludes in his case study that privacy-aware users are more reluctant
to join social networks. However once a privacy aware user joins he is willing to disclose a lot of
information and a user’s privacy is regulated mostly through visibility, i.e. the privacy settings of
the OSN (Online Social Networks). This privacy aware user aims to remain in control.
Furthermore users are more pre-occupied with the current visibility of their information and do
not look towards future implications. It seems that users implicitly trust social network providers
to handle user data in a fair and conscientious way.
Ahern, Eckles et al. (2007: 357) analysing the issue and conducting studies on Privacy Patterns
and Considerations in online and mobile photo sharing claim: The growing amount of online
personal content exposes users to a new set of privacy concerns. Digital cameras, and lately, a
new class of camera phone applications that can upload photos or video content directly to the
web, make publishing of personal content increasingly easy. Privacy concerns are especially
acute in the case of multimedia collections, as they could reveal much of the user’s personal and
social environment.[9]
Online social network privacy
George (2006) cited the case of US college athletes whose pictures, which they posted online,
were misused by a website, which publishes stories about scandals in sport. The author pointed
out that the issue of privacy has not gone unnoticed by social network providers. Gross and
Acquisti (2005) conducted a study on a sample of 4,000 students from Carnegie Mellon
University who use social network accounts. They found that a large proportion of students did
not care about the privacy risks that might increase the chance of a third party misusing a
student’s personal information. Another study by the same authors claimed that more than 77
percent of the respondents did not read privacy policies (Acquisti& Gross 2006). The ability to
control privacy options is essential to increasing the users’ confidence in their social network
providers. Since Internet users represent a range of different cultures and ages, privacy options
should be clear, simple and easy to use. Users must have the ability to control their privacy
options at any time. These privacy options allow users to accept or reject the dissemination of
their information to others. For example, some users do not want to publish sensitive information
such as health or medical information (Samavi&Consens 2010). These users are aware that
people with less than honourable intentions can harm adults or children by misusing their
personal information. A study conducted by Casarosa (2010) found that minors are interested in
new technologies and the Internet, and can be contacted by strangers online asking to form a
friendship. When a website publishes the personal information of a minor without giving the
child’s parents (or the child’s guardian) the authority to select privacy options, potential
predators can use some of the minor’s personal information, such as a mobile phone number, to
engage in sexual contact (Casarosa 2010).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The following links highlight some of the privacy issues that have highlighted the need for a
decentralised privacy aware social networking tool.
• Facebook’s Bewildering Privacy Policy An article by the NY Times, highlighting how
confusing Facebook’s privacy settings are http://www.nytimes.com/
interactive/2010/05/12/business/facebook-privacy.html and convoluted their privacy policy
actually is.
• Facebook’s Opengraph The following blog post http://zestyping.livejournal .com/257224.html
highlights the privacy implications of Facebook’s Open Graph Protocol [20]. Illustrated by the
web-service http://zesty.ca/facebook/
• Application that searches public Facebook wall posts The example webservice call
http://willmoffat.github.com/FacebookSearch/?q=Stupid+boss&gender=any highlights the
information that is accessible via Facebook’s Graph API [21]. It should be noted that the wall
posts shown in the aforementioned web-service call, are not apparently visible to the Web if one
simply visits an exposed user’s public profile page.
• The Evolution of Facebook’s Privacy Policy The following visualisation shows how
Facebook’s privacy policy has changed over time http://mattmckeon.com/facebookprivacy/. This
change in policy, is the main reason why there has been a sudden desire for the development of a
decentralised social network, removing the need for a central service that accumulates personal
information.
In order for any decentralised social networking service to be a success, the service’s privacy
policy with respect to the information it holds regarding its users must appeal to the privacy
aware masses. A report undertaken by Joseph Bonneau, Sren Preibusch from the Cambridge
University entitled “The Privacy Jungle: On the Market for Data Protection in Social
Networks”[22] details the findings of a study of privacy policies for popular social networking
sites, and presents best practises when it comes to creation of privacy policies [23].
Youth and the Concept of Privacy
In January 2010, Facebook’s Mark Zuckerberg told TechCrunch’s Mike Arrington [24] in a live
interview that he thought the concept of privacy no longer applies to the modern day [25]. Since
this claim the below studies have attempted to understand people’s feelings towards privacy: •
Pew Report on Online Reputation Pew Research, a US based research firm, recently conducted a
report detailing peoples attitudes to privacy, and online reputation. The report entitled
“Reputation, Management, and Social Media” [26], found that young adults are more likely than
older users to try and limit the amount of information available about them online. dannah boyd
from Microsoft research presents an overview of the research on her blog [27]. • Youth do care
about privacy A secondly unrelated piece of research undertaken by academics at University of
California Berkley, entitled “How Different are Young Adults from Older Adults When it Comes
to Information Privacy Attitudes and Policies?” [28] can be summarised in the below bullet
points: – Young Adults vs Adults The study did not find significant differences between young
or older adults regarding privacy, everyone seemed to be equally concerned and acknowledge it
as an issue. – Young American were uneducated towards issues relating to privacy 42 percent of
decentralised privacy aware social networking tool.
• Facebook’s Bewildering Privacy Policy An article by the NY Times, highlighting how
confusing Facebook’s privacy settings are http://www.nytimes.com/
interactive/2010/05/12/business/facebook-privacy.html and convoluted their privacy policy
actually is.
• Facebook’s Opengraph The following blog post http://zestyping.livejournal .com/257224.html
highlights the privacy implications of Facebook’s Open Graph Protocol [20]. Illustrated by the
web-service http://zesty.ca/facebook/
• Application that searches public Facebook wall posts The example webservice call
http://willmoffat.github.com/FacebookSearch/?q=Stupid+boss&gender=any highlights the
information that is accessible via Facebook’s Graph API [21]. It should be noted that the wall
posts shown in the aforementioned web-service call, are not apparently visible to the Web if one
simply visits an exposed user’s public profile page.
• The Evolution of Facebook’s Privacy Policy The following visualisation shows how
Facebook’s privacy policy has changed over time http://mattmckeon.com/facebookprivacy/. This
change in policy, is the main reason why there has been a sudden desire for the development of a
decentralised social network, removing the need for a central service that accumulates personal
information.
In order for any decentralised social networking service to be a success, the service’s privacy
policy with respect to the information it holds regarding its users must appeal to the privacy
aware masses. A report undertaken by Joseph Bonneau, Sren Preibusch from the Cambridge
University entitled “The Privacy Jungle: On the Market for Data Protection in Social
Networks”[22] details the findings of a study of privacy policies for popular social networking
sites, and presents best practises when it comes to creation of privacy policies [23].
Youth and the Concept of Privacy
In January 2010, Facebook’s Mark Zuckerberg told TechCrunch’s Mike Arrington [24] in a live
interview that he thought the concept of privacy no longer applies to the modern day [25]. Since
this claim the below studies have attempted to understand people’s feelings towards privacy: •
Pew Report on Online Reputation Pew Research, a US based research firm, recently conducted a
report detailing peoples attitudes to privacy, and online reputation. The report entitled
“Reputation, Management, and Social Media” [26], found that young adults are more likely than
older users to try and limit the amount of information available about them online. dannah boyd
from Microsoft research presents an overview of the research on her blog [27]. • Youth do care
about privacy A secondly unrelated piece of research undertaken by academics at University of
California Berkley, entitled “How Different are Young Adults from Older Adults When it Comes
to Information Privacy Attitudes and Policies?” [28] can be summarised in the below bullet
points: – Young Adults vs Adults The study did not find significant differences between young
or older adults regarding privacy, everyone seemed to be equally concerned and acknowledge it
as an issue. – Young American were uneducated towards issues relating to privacy 42 percent of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
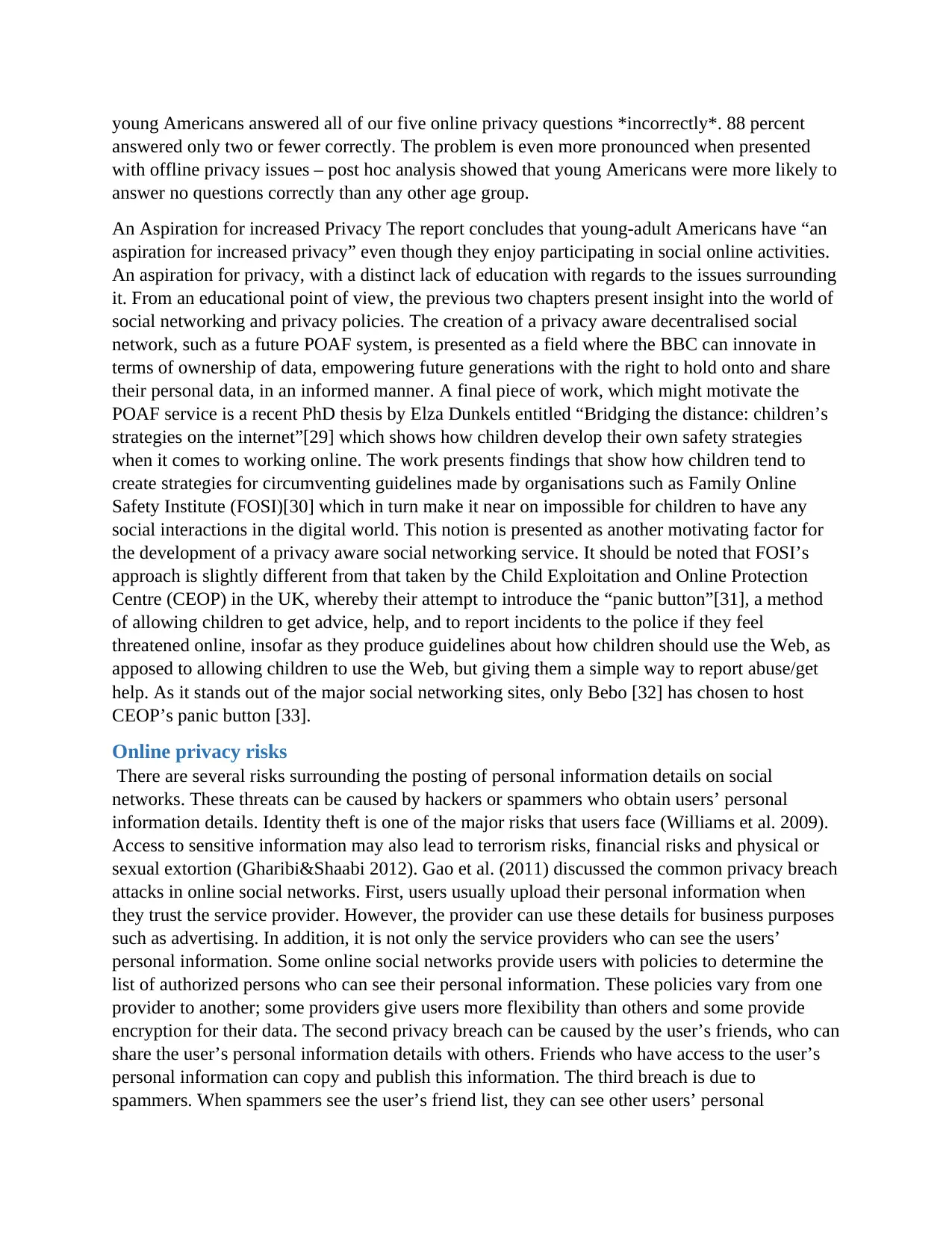
young Americans answered all of our five online privacy questions *incorrectly*. 88 percent
answered only two or fewer correctly. The problem is even more pronounced when presented
with offline privacy issues – post hoc analysis showed that young Americans were more likely to
answer no questions correctly than any other age group.
An Aspiration for increased Privacy The report concludes that young-adult Americans have “an
aspiration for increased privacy” even though they enjoy participating in social online activities.
An aspiration for privacy, with a distinct lack of education with regards to the issues surrounding
it. From an educational point of view, the previous two chapters present insight into the world of
social networking and privacy policies. The creation of a privacy aware decentralised social
network, such as a future POAF system, is presented as a field where the BBC can innovate in
terms of ownership of data, empowering future generations with the right to hold onto and share
their personal data, in an informed manner. A final piece of work, which might motivate the
POAF service is a recent PhD thesis by Elza Dunkels entitled “Bridging the distance: children’s
strategies on the internet”[29] which shows how children develop their own safety strategies
when it comes to working online. The work presents findings that show how children tend to
create strategies for circumventing guidelines made by organisations such as Family Online
Safety Institute (FOSI)[30] which in turn make it near on impossible for children to have any
social interactions in the digital world. This notion is presented as another motivating factor for
the development of a privacy aware social networking service. It should be noted that FOSI’s
approach is slightly different from that taken by the Child Exploitation and Online Protection
Centre (CEOP) in the UK, whereby their attempt to introduce the “panic button”[31], a method
of allowing children to get advice, help, and to report incidents to the police if they feel
threatened online, insofar as they produce guidelines about how children should use the Web, as
apposed to allowing children to use the Web, but giving them a simple way to report abuse/get
help. As it stands out of the major social networking sites, only Bebo [32] has chosen to host
CEOP’s panic button [33].
Online privacy risks
There are several risks surrounding the posting of personal information details on social
networks. These threats can be caused by hackers or spammers who obtain users’ personal
information details. Identity theft is one of the major risks that users face (Williams et al. 2009).
Access to sensitive information may also lead to terrorism risks, financial risks and physical or
sexual extortion (Gharibi&Shaabi 2012). Gao et al. (2011) discussed the common privacy breach
attacks in online social networks. First, users usually upload their personal information when
they trust the service provider. However, the provider can use these details for business purposes
such as advertising. In addition, it is not only the service providers who can see the users’
personal information. Some online social networks provide users with policies to determine the
list of authorized persons who can see their personal information. These policies vary from one
provider to another; some providers give users more flexibility than others and some provide
encryption for their data. The second privacy breach can be caused by the user’s friends, who can
share the user’s personal information details with others. Friends who have access to the user’s
personal information can copy and publish this information. The third breach is due to
spammers. When spammers see the user’s friend list, they can see other users’ personal
answered only two or fewer correctly. The problem is even more pronounced when presented
with offline privacy issues – post hoc analysis showed that young Americans were more likely to
answer no questions correctly than any other age group.
An Aspiration for increased Privacy The report concludes that young-adult Americans have “an
aspiration for increased privacy” even though they enjoy participating in social online activities.
An aspiration for privacy, with a distinct lack of education with regards to the issues surrounding
it. From an educational point of view, the previous two chapters present insight into the world of
social networking and privacy policies. The creation of a privacy aware decentralised social
network, such as a future POAF system, is presented as a field where the BBC can innovate in
terms of ownership of data, empowering future generations with the right to hold onto and share
their personal data, in an informed manner. A final piece of work, which might motivate the
POAF service is a recent PhD thesis by Elza Dunkels entitled “Bridging the distance: children’s
strategies on the internet”[29] which shows how children develop their own safety strategies
when it comes to working online. The work presents findings that show how children tend to
create strategies for circumventing guidelines made by organisations such as Family Online
Safety Institute (FOSI)[30] which in turn make it near on impossible for children to have any
social interactions in the digital world. This notion is presented as another motivating factor for
the development of a privacy aware social networking service. It should be noted that FOSI’s
approach is slightly different from that taken by the Child Exploitation and Online Protection
Centre (CEOP) in the UK, whereby their attempt to introduce the “panic button”[31], a method
of allowing children to get advice, help, and to report incidents to the police if they feel
threatened online, insofar as they produce guidelines about how children should use the Web, as
apposed to allowing children to use the Web, but giving them a simple way to report abuse/get
help. As it stands out of the major social networking sites, only Bebo [32] has chosen to host
CEOP’s panic button [33].
Online privacy risks
There are several risks surrounding the posting of personal information details on social
networks. These threats can be caused by hackers or spammers who obtain users’ personal
information details. Identity theft is one of the major risks that users face (Williams et al. 2009).
Access to sensitive information may also lead to terrorism risks, financial risks and physical or
sexual extortion (Gharibi&Shaabi 2012). Gao et al. (2011) discussed the common privacy breach
attacks in online social networks. First, users usually upload their personal information when
they trust the service provider. However, the provider can use these details for business purposes
such as advertising. In addition, it is not only the service providers who can see the users’
personal information. Some online social networks provide users with policies to determine the
list of authorized persons who can see their personal information. These policies vary from one
provider to another; some providers give users more flexibility than others and some provide
encryption for their data. The second privacy breach can be caused by the user’s friends, who can
share the user’s personal information details with others. Friends who have access to the user’s
personal information can copy and publish this information. The third breach is due to
spammers. When spammers see the user’s friend list, they can see other users’ personal

information by sending them a friend request, impersonating one of his/her friends by using the
friend’s name or picture. Lastly, breaches can be caused by third party applications installed by
users. These applications can be a threat to users, especially if they are not from a trusted
provider. When the application accesses the users’ personal information, others can obtain this
information. Novak and Li (2012) also claimed that privacy breaches can be caused by friends,
applications, and exploitation of personal information details by the service providers for
advertising. The authors added that understanding privacy settings is not enough to protect users,
especially from friends and other online social network users. Thus, social networking websites
such as Facebook prioritize the development of tools to protect privacy. This is manifested in the
social network providers’ requests for new users to create new privacy settings. However, some
users do not realize the risk of leakage of personal information (Lee et al. 2011). Therefore,
sensitive information such as home address and date of birth should not be published online in
order to avoid risks to online privacy. Increasing user awareness of these risks, providing a
privacy management system for users to control their personal information details, and
constantly updating privacy policies can lead to a decline of these risks (Gharibi&Shaabi 2012).
In addition, O’Brien and Torres 2012 wrote an article named Social Networking and Online
Privacy: Facebook Users’ Perceptions. As a result, the researchers found that Facebook users are
alert and cautious when using the social networking sites. However, Facebook users are not
completely informed or aware of all activities concerning privacy on the social networking sites.
Though, low trust levels to date have not hindered activity on Facebook and membership
continues to rise. Facebook users seem willing to push aside trust issues to achieve social
interaction. The importance of trust in a social networking context is clearly questionable and
perhaps different determinants for online activity exist in different online environments. There
are a number of barriers to trust in the online environment. These barriers include perceived risk,
website design and content, the user themselves and privacy concerns. Privacy concerns are
considered the greatest barrier of them all because ‘the internet, by design, lacks unified
provisions for identifying who communicates with whom; it lacks a well-designed identity
infrastructure’ (Leenes et al., 2008). Privacy concerns include online information collection
techniques such as cookie technology involving extreme surveillance. The use and analysis of
data are also a concern due to unethical merging and data mining practices to profile customers.
The instant recording and permanence of activity, loss of control and ownership of data also
creates barriers to online activity (Tavani, 2011). Social networking users claim to be concerned
about risks to privacy, yet do little to safeguard their information (Dwyer et al., 2007). Often
users openly disclose detailed and personal information on these networks, comfortable living a
part of their lives online (Rosenblum, 2007). However, Facebook has continually introduced new
features and services including the Newsfeed, Facebook Beacon, Facebook Advertisements and
Facebook Platform, which subsequently lead to changes in the privacy settings and the privacy
policy (less privacy) (Fletcher, 2010). With each additional expansion to the website has come a
growing level of discontent and concern and a general feeling that ‘the company was eroding
privacy and making substantial information public’ (Rothery, 2010).
friend’s name or picture. Lastly, breaches can be caused by third party applications installed by
users. These applications can be a threat to users, especially if they are not from a trusted
provider. When the application accesses the users’ personal information, others can obtain this
information. Novak and Li (2012) also claimed that privacy breaches can be caused by friends,
applications, and exploitation of personal information details by the service providers for
advertising. The authors added that understanding privacy settings is not enough to protect users,
especially from friends and other online social network users. Thus, social networking websites
such as Facebook prioritize the development of tools to protect privacy. This is manifested in the
social network providers’ requests for new users to create new privacy settings. However, some
users do not realize the risk of leakage of personal information (Lee et al. 2011). Therefore,
sensitive information such as home address and date of birth should not be published online in
order to avoid risks to online privacy. Increasing user awareness of these risks, providing a
privacy management system for users to control their personal information details, and
constantly updating privacy policies can lead to a decline of these risks (Gharibi&Shaabi 2012).
In addition, O’Brien and Torres 2012 wrote an article named Social Networking and Online
Privacy: Facebook Users’ Perceptions. As a result, the researchers found that Facebook users are
alert and cautious when using the social networking sites. However, Facebook users are not
completely informed or aware of all activities concerning privacy on the social networking sites.
Though, low trust levels to date have not hindered activity on Facebook and membership
continues to rise. Facebook users seem willing to push aside trust issues to achieve social
interaction. The importance of trust in a social networking context is clearly questionable and
perhaps different determinants for online activity exist in different online environments. There
are a number of barriers to trust in the online environment. These barriers include perceived risk,
website design and content, the user themselves and privacy concerns. Privacy concerns are
considered the greatest barrier of them all because ‘the internet, by design, lacks unified
provisions for identifying who communicates with whom; it lacks a well-designed identity
infrastructure’ (Leenes et al., 2008). Privacy concerns include online information collection
techniques such as cookie technology involving extreme surveillance. The use and analysis of
data are also a concern due to unethical merging and data mining practices to profile customers.
The instant recording and permanence of activity, loss of control and ownership of data also
creates barriers to online activity (Tavani, 2011). Social networking users claim to be concerned
about risks to privacy, yet do little to safeguard their information (Dwyer et al., 2007). Often
users openly disclose detailed and personal information on these networks, comfortable living a
part of their lives online (Rosenblum, 2007). However, Facebook has continually introduced new
features and services including the Newsfeed, Facebook Beacon, Facebook Advertisements and
Facebook Platform, which subsequently lead to changes in the privacy settings and the privacy
policy (less privacy) (Fletcher, 2010). With each additional expansion to the website has come a
growing level of discontent and concern and a general feeling that ‘the company was eroding
privacy and making substantial information public’ (Rothery, 2010).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Online privacy protection
Privacy settings, that allow the user to control the profile view and distribution of personal data,
vary across social networking websites, and there is no privacy standard for controlling the
user’s personal information settings. Although privacy settings should be chosen carefully, most
online social network providers have complex privacy settings (Novak & Li 2012). These
complex privacy settings may cause confusion among users (Gundecha, Barbier& Liu 2011).
Different techniques have been designed to increase personal information privacy protection.
Williams et al. (2009) listed some steps for online social network users to stay safe. These
included: being aware of the risks of social networks, limiting the posting of personal
information details, and being careful when dealing with strangers online or when reading any
information from any sender. Most social networking sites have given their users more authority
to control privacy settings. Users of some social networking sites are now able to classify their
friend list into sub-lists, which allows some personal information details, such as birthday or
relationship status, to be visible to one sub-list and hidden from others. Fang et al. (2010)
designed a privacy recommendation wizard based on user inputs to help users classify their
friend list into sub-lists. The wizard gives the user two options: to allow the friends in their sub-
list to see their personal information, or to deny them access to this information. Configuring
privacy settings so that only friends can see your posts is not enough to defend oneself from
other attacks such as applications and advertisements (Stutzman& Kramer-Duffield 2010).
Lipford, Besmer and Watson (2008) found that showing an example of privacy settings
International Journal of Security, Privacy and Trust Management ( IJSPTM) vol 2, No 2, April
2013 6 will enable users to understand their privacy settings better. It will also help them find out
who can see their personal information. For instance, Facebook allows users to see their profiles
from their friends’ point of view; this allows users to see what personal information their friends
can see. This technique helps users understand privacy settings but does not provide security to
protect them from neighbourhood attacks or other types of attacks such as viruses or spam. Fang
and Lefevre (2010) designed a privacy wizard system to make it easier for users to control their
privacy settings. It was designed based on friends classification to groups and asking questions.
It guides users in choosing privacy settings for group or individual users by allowing the users to
see or hide an item. For example, if Alice is Bob’s friend, then Bob can identify which items of
his profile Alice can see. Bob can hide some details such as his date of birth and mobile number
from Alice, and can do the same for his other friends.
There has been some previous work attempting to apply nudging to computer security. For
instance, Brustoloni et al. developed security dialogs in which users were held accountable for
their decisions to open email attachments. Those who took unjustified risks could be “subject to
a variety of sanctions, such as being unable to use the application for increasing periods of
time...” A user study found that these dialogs resulted in significantly fewer unjustified risks
[35]. An approach similar to nudging can be found in persuasive computing, a sub-field of
computer science concerned with systems intentionally designed to “change a person’s attitude
or behavior in a predetermined way” [37]. Persuasive technologies have been applied in specific
domains including computer security. For instance, Forget et al. built a text password system that
encourages users to create stronger text password [38]. A number of mechanisms have been
Privacy settings, that allow the user to control the profile view and distribution of personal data,
vary across social networking websites, and there is no privacy standard for controlling the
user’s personal information settings. Although privacy settings should be chosen carefully, most
online social network providers have complex privacy settings (Novak & Li 2012). These
complex privacy settings may cause confusion among users (Gundecha, Barbier& Liu 2011).
Different techniques have been designed to increase personal information privacy protection.
Williams et al. (2009) listed some steps for online social network users to stay safe. These
included: being aware of the risks of social networks, limiting the posting of personal
information details, and being careful when dealing with strangers online or when reading any
information from any sender. Most social networking sites have given their users more authority
to control privacy settings. Users of some social networking sites are now able to classify their
friend list into sub-lists, which allows some personal information details, such as birthday or
relationship status, to be visible to one sub-list and hidden from others. Fang et al. (2010)
designed a privacy recommendation wizard based on user inputs to help users classify their
friend list into sub-lists. The wizard gives the user two options: to allow the friends in their sub-
list to see their personal information, or to deny them access to this information. Configuring
privacy settings so that only friends can see your posts is not enough to defend oneself from
other attacks such as applications and advertisements (Stutzman& Kramer-Duffield 2010).
Lipford, Besmer and Watson (2008) found that showing an example of privacy settings
International Journal of Security, Privacy and Trust Management ( IJSPTM) vol 2, No 2, April
2013 6 will enable users to understand their privacy settings better. It will also help them find out
who can see their personal information. For instance, Facebook allows users to see their profiles
from their friends’ point of view; this allows users to see what personal information their friends
can see. This technique helps users understand privacy settings but does not provide security to
protect them from neighbourhood attacks or other types of attacks such as viruses or spam. Fang
and Lefevre (2010) designed a privacy wizard system to make it easier for users to control their
privacy settings. It was designed based on friends classification to groups and asking questions.
It guides users in choosing privacy settings for group or individual users by allowing the users to
see or hide an item. For example, if Alice is Bob’s friend, then Bob can identify which items of
his profile Alice can see. Bob can hide some details such as his date of birth and mobile number
from Alice, and can do the same for his other friends.
There has been some previous work attempting to apply nudging to computer security. For
instance, Brustoloni et al. developed security dialogs in which users were held accountable for
their decisions to open email attachments. Those who took unjustified risks could be “subject to
a variety of sanctions, such as being unable to use the application for increasing periods of
time...” A user study found that these dialogs resulted in significantly fewer unjustified risks
[35]. An approach similar to nudging can be found in persuasive computing, a sub-field of
computer science concerned with systems intentionally designed to “change a person’s attitude
or behavior in a predetermined way” [37]. Persuasive technologies have been applied in specific
domains including computer security. For instance, Forget et al. built a text password system that
encourages users to create stronger text password [38]. A number of mechanisms have been
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

proposed to help users better protect their privacy in social media. Fang et al. designed a privacy
wizard that asks users to iterate over privacy settings for some of their friends. Based on this
information, a classifier could be built automatically to categorize the remaining friends [36].
Lipford et al. investigated interfaces for social network privacy controls, comparing compact
settings in the form of expandable grids to visual policies. They found that both alternatives were
usable, but different users appreciated them for different reasons [40]. While most previous work
on privacy protections for social media has focused on helping users adjust their settings up
front, our work employs tools that encourage real-time adjustments during or immediately
following the composition of a Facebook post.
wizard that asks users to iterate over privacy settings for some of their friends. Based on this
information, a classifier could be built automatically to categorize the remaining friends [36].
Lipford et al. investigated interfaces for social network privacy controls, comparing compact
settings in the form of expandable grids to visual policies. They found that both alternatives were
usable, but different users appreciated them for different reasons [40]. While most previous work
on privacy protections for social media has focused on helping users adjust their settings up
front, our work employs tools that encourage real-time adjustments during or immediately
following the composition of a Facebook post.

Research Methodology
In this chapter, the research objective, process, research approach, methods, and instruments
used for selection of respondents and data analysis of this research are described.
Research objectives
This report is an attempt to understand how the public sector applies TM practices and initiatives
in UAE.
Many business leaders in the Middle East now understands the significance of talents in the
organization, hence, in order to be able to manage them properly, they need to put them in their
top agenda priorities. This study aims to understand how TM is perceived in the UAE and what
are the initiatives and practice that are currently undertaken. The study focuses on the public
sector organization. Moreover, the research will provide a response to the research questions in
chapter 1 of the introduction.
Purpose of research
The UAE is considered one of the preferred locations for expatriate, and since the number of
UAE nationals is increasing in the market, there is a need to manage and develop talent in the
UAE. This is considered a major push for this report.
The aim of writing a research is either to discover a new phenomenon or provide an
understanding of existing complex phenomena. Research questions determine the research
direction whether it need to describe phenomena, quantify or analyze correlations, hence the
researcher need to select the appropriate research method to adapt the purpose (Peter Strang,
2000).
In this chapter, the research objective, process, research approach, methods, and instruments
used for selection of respondents and data analysis of this research are described.
Research objectives
This report is an attempt to understand how the public sector applies TM practices and initiatives
in UAE.
Many business leaders in the Middle East now understands the significance of talents in the
organization, hence, in order to be able to manage them properly, they need to put them in their
top agenda priorities. This study aims to understand how TM is perceived in the UAE and what
are the initiatives and practice that are currently undertaken. The study focuses on the public
sector organization. Moreover, the research will provide a response to the research questions in
chapter 1 of the introduction.
Purpose of research
The UAE is considered one of the preferred locations for expatriate, and since the number of
UAE nationals is increasing in the market, there is a need to manage and develop talent in the
UAE. This is considered a major push for this report.
The aim of writing a research is either to discover a new phenomenon or provide an
understanding of existing complex phenomena. Research questions determine the research
direction whether it need to describe phenomena, quantify or analyze correlations, hence the
researcher need to select the appropriate research method to adapt the purpose (Peter Strang,
2000).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 42
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





