Social Networking Report: Authentication, Ethics, and Cybercrime
VerifiedAdded on 2022/10/04
|11
|1854
|14
Report
AI Summary
This report provides a comprehensive analysis of social networking, exploring its evolution, benefits, and challenges. It delves into the advantages of social networks, such as improved communication and information sharing, while also addressing the ethical considerations surrounding privacy, employment, and cybercrime. The report highlights the importance of authentication technology for data security and discusses the disadvantages of social media, including the spread of fake news and potential for negative social behaviors. The conclusion emphasizes the transformative impact of social media on communication and recommends its use in various sectors, while also acknowledging the need for responsible usage and ethical practices. The report references various academic sources to support its findings and recommendations.

SOCIAL NETWORKING 1
Social networking
Student name
Registration number
Institution
Date
Social networking
Student name
Registration number
Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SOCIAL NETWORKING 2
Executive summary
Technology has evolved significantly. This evolution has led to the development of machines
and systems dedicated to solving the issue of interest. Technology evolution has also touched the
information sector and transformed it significantly hence worth to discuss social networking.
Table of Contents
Executive summary
Technology has evolved significantly. This evolution has led to the development of machines
and systems dedicated to solving the issue of interest. Technology evolution has also touched the
information sector and transformed it significantly hence worth to discuss social networking.
Table of Contents

SOCIAL NETWORKING 3
Introduction.................................................................................................................................................4
Social network infographic..........................................................................................................................4
Benefits or opportunities of social networks...............................................................................................5
Challenges of using social networks............................................................................................................6
Ethics...........................................................................................................................................................6
Privacy.....................................................................................................................................................7
Employment............................................................................................................................................7
Cyber-crime and Fake news.....................................................................................................................7
Censorship...............................................................................................................................................8
Advantages of social network technology...................................................................................................8
Disadvantages of social networks................................................................................................................9
Conclusion...................................................................................................................................................9
References...................................................................................................................................................9
Introduction.................................................................................................................................................4
Social network infographic..........................................................................................................................4
Benefits or opportunities of social networks...............................................................................................5
Challenges of using social networks............................................................................................................6
Ethics...........................................................................................................................................................6
Privacy.....................................................................................................................................................7
Employment............................................................................................................................................7
Cyber-crime and Fake news.....................................................................................................................7
Censorship...............................................................................................................................................8
Advantages of social network technology...................................................................................................8
Disadvantages of social networks................................................................................................................9
Conclusion...................................................................................................................................................9
References...................................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SOCIAL NETWORKING 4
Introduction
In the earlier generations, interaction and information exchange were characterized by
different features to the one present today. Do you know people once relied on smoke, horn-
blowing, or drum beating to communicate? How correct could be the interpretation of the
message in transit? How reliable is it in reaching masses of intended recipients?
These challenges motivated innovation in the information and communication sector.
Evolution of technology and availability of information in computing and system development
led to the development of social networks. Social networks are the websites or applications
embedded in the internet allowing interaction over the internet (Newman, 2016). These social
networks include applications like Facebook, WhatsApp, Instagram, among others in the list that
enables interaction of friends, family members, and co-workers. With the technology available, it
is convenient and reliable to hold meeting over via the internet.
This report however focuses on the need for data security on websites, applications and
the information stored online. The authentication technology in development in this application
is meant for online computation.
Authentication application info-graphic
Introduction
In the earlier generations, interaction and information exchange were characterized by
different features to the one present today. Do you know people once relied on smoke, horn-
blowing, or drum beating to communicate? How correct could be the interpretation of the
message in transit? How reliable is it in reaching masses of intended recipients?
These challenges motivated innovation in the information and communication sector.
Evolution of technology and availability of information in computing and system development
led to the development of social networks. Social networks are the websites or applications
embedded in the internet allowing interaction over the internet (Newman, 2016). These social
networks include applications like Facebook, WhatsApp, Instagram, among others in the list that
enables interaction of friends, family members, and co-workers. With the technology available, it
is convenient and reliable to hold meeting over via the internet.
This report however focuses on the need for data security on websites, applications and
the information stored online. The authentication technology in development in this application
is meant for online computation.
Authentication application info-graphic
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
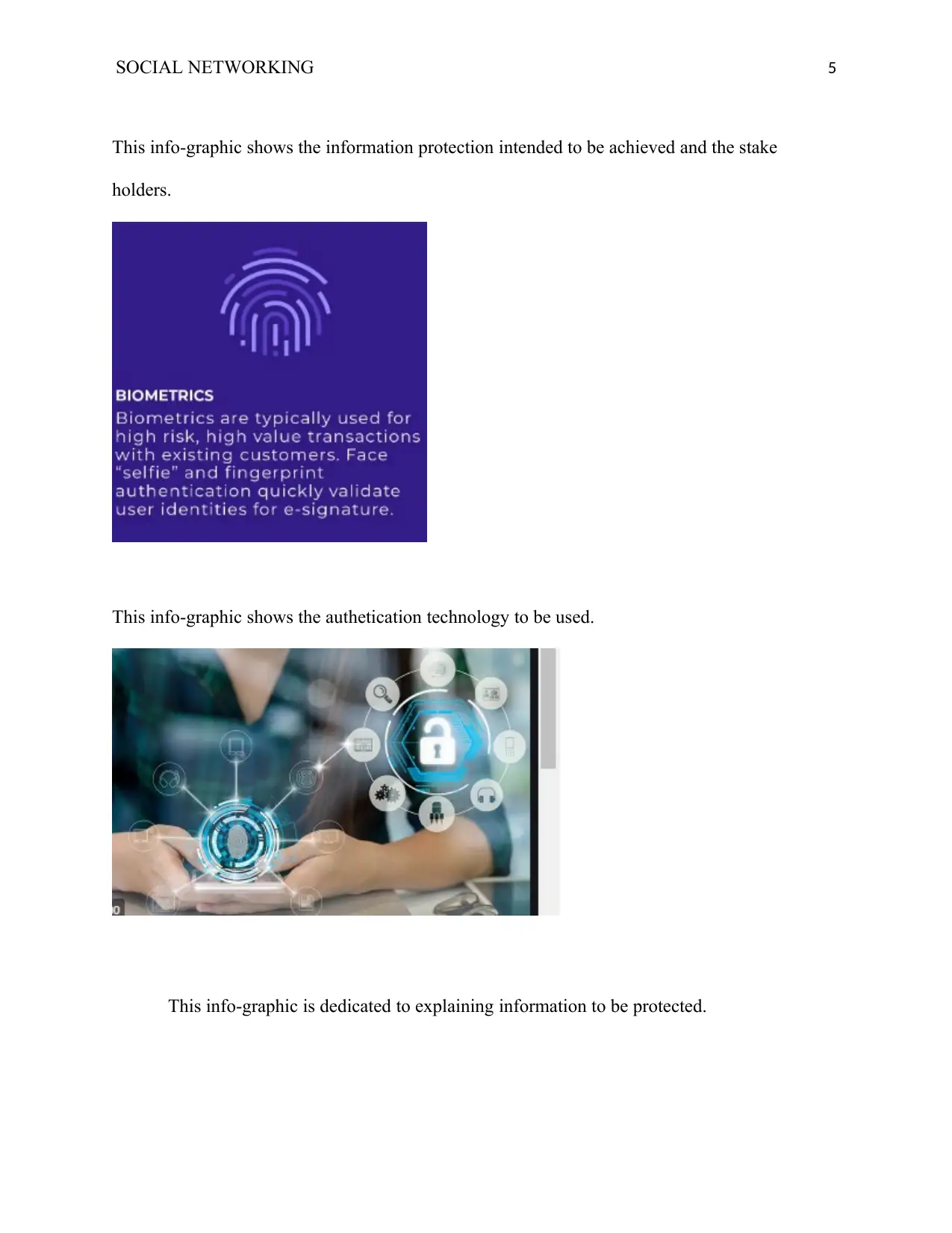
SOCIAL NETWORKING 5
This info-graphic shows the information protection intended to be achieved and the stake
holders.
This info-graphic shows the authetication technology to be used.
This info-graphic is dedicated to explaining information to be protected.
This info-graphic shows the information protection intended to be achieved and the stake
holders.
This info-graphic shows the authetication technology to be used.
This info-graphic is dedicated to explaining information to be protected.

SOCIAL NETWORKING 6
Benefits or opportunities of authentication app
We live in a social world. Interaction is not evitable. The cost of one on one interaction is
high and time-consuming hence difficult to manage. The social networks came in a bridge to
connect people from various locations (Wang, Xu, Wu and Zhou, 2015). The benefits of social
networks have provided a reliable platform for entertainers. The social media has been used by
the people in the entertainment industry to sell and distribute their content to their fans.
Social networks are also used to distribute and get the word out on informative content.
People have used social media to consult their doctors on their health status, thus reducing the
congestion in a health facility as well as improving on time management. The time that could be
wasted on travel to the facility is reduced. If it were not the power of social media, doing this
assignment would not be possible owing to the challenge of the information distribution.
The social media is an informative platform, and people access information on how to
start and run a business through social media (Blue, Tau, and Work, LinkedIn Corp, 2016). The
social media also enables access to the government and banking institution without paying them
a visit in their offices.
However, if this information sharing platforms are at risk of cyber-crimes and the
disadvantages they could cause on occurrence supersedes the combination of all this advantages.
Authentication only allows information access by only legally allowed person. Authentication
improves confidence and integrity of this information.
Benefits or opportunities of authentication app
We live in a social world. Interaction is not evitable. The cost of one on one interaction is
high and time-consuming hence difficult to manage. The social networks came in a bridge to
connect people from various locations (Wang, Xu, Wu and Zhou, 2015). The benefits of social
networks have provided a reliable platform for entertainers. The social media has been used by
the people in the entertainment industry to sell and distribute their content to their fans.
Social networks are also used to distribute and get the word out on informative content.
People have used social media to consult their doctors on their health status, thus reducing the
congestion in a health facility as well as improving on time management. The time that could be
wasted on travel to the facility is reduced. If it were not the power of social media, doing this
assignment would not be possible owing to the challenge of the information distribution.
The social media is an informative platform, and people access information on how to
start and run a business through social media (Blue, Tau, and Work, LinkedIn Corp, 2016). The
social media also enables access to the government and banking institution without paying them
a visit in their offices.
However, if this information sharing platforms are at risk of cyber-crimes and the
disadvantages they could cause on occurrence supersedes the combination of all this advantages.
Authentication only allows information access by only legally allowed person. Authentication
improves confidence and integrity of this information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SOCIAL NETWORKING 7
Challenges of using social networks without authentication
Ethics
The law has to be applied in every sector. Failure to apply it, the state of lawlessness will
take over, and human relationships will be worse. Ethics refers to the general conduct of an
individual that is said to be right according to the norms and culture of the people in question.
Ethics in the social network must be observed to avoid offending others. The information on the
people must be safeguarded to ensure integrity and confidentiality.
The laws on social networks are solid since information is crucial. The following are some of the
ethics of interest in the social network.
Privacy
Information in social media is exposed to the public. Some information is in social media
is a threat to the owners and poses safety challenges. Criminals have used the information on
transactions and photographs (Turban, Outland, King, Lee, Liang, and Turban,
2017).Confidential information of persons has been extracted from the social network and used
to alter evidence. The criminals print the photos and leave them at the crime scene hence
distracting the evidence.
In safety threat control, developers of the social network have integrated the systems with
security measures that include authentication and authorization. These measures are not
foolproof, and the user must be vigilant on the information they post in the social network.
Employment
The network also provides a marketing platform for business people. It is coming up that
the social media comprises of individuals from all the walks of life and defined as another world
Challenges of using social networks without authentication
Ethics
The law has to be applied in every sector. Failure to apply it, the state of lawlessness will
take over, and human relationships will be worse. Ethics refers to the general conduct of an
individual that is said to be right according to the norms and culture of the people in question.
Ethics in the social network must be observed to avoid offending others. The information on the
people must be safeguarded to ensure integrity and confidentiality.
The laws on social networks are solid since information is crucial. The following are some of the
ethics of interest in the social network.
Privacy
Information in social media is exposed to the public. Some information is in social media
is a threat to the owners and poses safety challenges. Criminals have used the information on
transactions and photographs (Turban, Outland, King, Lee, Liang, and Turban,
2017).Confidential information of persons has been extracted from the social network and used
to alter evidence. The criminals print the photos and leave them at the crime scene hence
distracting the evidence.
In safety threat control, developers of the social network have integrated the systems with
security measures that include authentication and authorization. These measures are not
foolproof, and the user must be vigilant on the information they post in the social network.
Employment
The network also provides a marketing platform for business people. It is coming up that
the social media comprises of individuals from all the walks of life and defined as another world
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SOCIAL NETWORKING 8
of virtual people. Marketing in social media is faster and stable. Sharing a post reaches thousands
of social media users who may develop an interest in the product. Other individuals use social
media to generate income through advertisement because they have stronger social media
influence (Cai, De Janvry, and Sadoulet, 2015.)
Employing youth has improved their living standards. This has saved them from
involvement in crime among other social injustices.
Cyber-crime and Fake news
Fake news is unethical and illegal according to the laws of many states. The social media
has significantly contributed to spreading fake news. Fake news is very traumatizing and
offending to the primary subject because most of them are false allegations. People have been
depressed to the point of committing suicide owing to social network fake news (Arnkil, 2018).
Fake news is ethical and criminal. The social network administrator works hard to ensure such
posts are revoked. They may also post a contrary post to the fake one to counter its impact.
Censorship
The social networks are designed such that an individual in the administrators’ machine
has the ability to control the information posted by a system user. The administrator has the
capacity to block the information from access by other people if he feels its offensive or
unethical (Newman, 2016). It is, however, possible to witness dictatorship in the media where
the administrator will block a system user if his opinion to her post is bias.
Advantages of social network authentication technology
The evolution of the social network brought about a massive transformation in the
communication sector. The following are among the main benefits.
of virtual people. Marketing in social media is faster and stable. Sharing a post reaches thousands
of social media users who may develop an interest in the product. Other individuals use social
media to generate income through advertisement because they have stronger social media
influence (Cai, De Janvry, and Sadoulet, 2015.)
Employing youth has improved their living standards. This has saved them from
involvement in crime among other social injustices.
Cyber-crime and Fake news
Fake news is unethical and illegal according to the laws of many states. The social media
has significantly contributed to spreading fake news. Fake news is very traumatizing and
offending to the primary subject because most of them are false allegations. People have been
depressed to the point of committing suicide owing to social network fake news (Arnkil, 2018).
Fake news is ethical and criminal. The social network administrator works hard to ensure such
posts are revoked. They may also post a contrary post to the fake one to counter its impact.
Censorship
The social networks are designed such that an individual in the administrators’ machine
has the ability to control the information posted by a system user. The administrator has the
capacity to block the information from access by other people if he feels its offensive or
unethical (Newman, 2016). It is, however, possible to witness dictatorship in the media where
the administrator will block a system user if his opinion to her post is bias.
Advantages of social network authentication technology
The evolution of the social network brought about a massive transformation in the
communication sector. The following are among the main benefits.

SOCIAL NETWORKING 9
The social network has provided the ability of people to connect and share ideas and
information across borders which were not possible in the past, and one had to travel to deliver
the information of interest (Bao, Zheng, Wilkie, and Mokbel, 2015).
The communication is fast and instant, the senders and the recipient send and receive
information in real-time as opposed the traditional communication modes that included letters
sending. The information available on social media is important in business practices. The
information in the social network may also be entertaining to the users (Espinoza, 2018).
With assured information security in the social media, the users becomes confident and
gains integrity on the media.
Disadvantages of online authentication interface
The social media has contributed significantly in the spreading of fake news and
information that can ruin the young generation. The challenge of peer pressure comes into play
and social behaviors like sex and drug abuse. If one forgets the unlocking password while having
uploaded such content as mentioned above, deleting it becomes impossible (Barclay, Guinn,
Hofer, and Schwartz, Bally Gaming Inc, 2015). The information is maintained hence affecting
generations negatively.
Conclusion
Summing up the report, it is factual to say the social media has transformed the world of
communication. This report recommends the use of social media in the business, government,
and individuals owing to the benefits accrued to their use (Sekara, Stopczynski, and Lehmann,
2016).
The social network has provided the ability of people to connect and share ideas and
information across borders which were not possible in the past, and one had to travel to deliver
the information of interest (Bao, Zheng, Wilkie, and Mokbel, 2015).
The communication is fast and instant, the senders and the recipient send and receive
information in real-time as opposed the traditional communication modes that included letters
sending. The information available on social media is important in business practices. The
information in the social network may also be entertaining to the users (Espinoza, 2018).
With assured information security in the social media, the users becomes confident and
gains integrity on the media.
Disadvantages of online authentication interface
The social media has contributed significantly in the spreading of fake news and
information that can ruin the young generation. The challenge of peer pressure comes into play
and social behaviors like sex and drug abuse. If one forgets the unlocking password while having
uploaded such content as mentioned above, deleting it becomes impossible (Barclay, Guinn,
Hofer, and Schwartz, Bally Gaming Inc, 2015). The information is maintained hence affecting
generations negatively.
Conclusion
Summing up the report, it is factual to say the social media has transformed the world of
communication. This report recommends the use of social media in the business, government,
and individuals owing to the benefits accrued to their use (Sekara, Stopczynski, and Lehmann,
2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SOCIAL NETWORKING
10
The report has defined social networks, how they are used, and the benefits they have in
the social and economic life. The report has also identified the challenges of using social
networks as well as their disadvantages and advantages when put into use.
References
Arnkil, T.E., 2018. Dialogical meetings in social networks. Routledge.
Bao, J., Zheng, Y., Wilkie, D. and Mokbel, M., 2015. Recommendations in location-based social
networks: a survey. GeoInformatica, 19(3), pp.525-565.
Barclay, B.J., Guinn, A.C., Hofer, J.D. and Schwartz, R.T., Bally Gaming Inc, 2015. Integrating
social networks and wagering games. U.S. Patent 9,218,716.
Blue, A., Tau, E. and Work, J.D., LinkedIn Corp, 2016. Searching and reference checking
within social networks. U.S. Patent 9,336,333.
Cai, J., De Janvry, A. and Sadoulet, E., 2015. Social networks and the decision to
insure. American Economic Journal: Applied Economics, 7(2), pp.81-108.
10
The report has defined social networks, how they are used, and the benefits they have in
the social and economic life. The report has also identified the challenges of using social
networks as well as their disadvantages and advantages when put into use.
References
Arnkil, T.E., 2018. Dialogical meetings in social networks. Routledge.
Bao, J., Zheng, Y., Wilkie, D. and Mokbel, M., 2015. Recommendations in location-based social
networks: a survey. GeoInformatica, 19(3), pp.525-565.
Barclay, B.J., Guinn, A.C., Hofer, J.D. and Schwartz, R.T., Bally Gaming Inc, 2015. Integrating
social networks and wagering games. U.S. Patent 9,218,716.
Blue, A., Tau, E. and Work, J.D., LinkedIn Corp, 2016. Searching and reference checking
within social networks. U.S. Patent 9,336,333.
Cai, J., De Janvry, A. and Sadoulet, E., 2015. Social networks and the decision to
insure. American Economic Journal: Applied Economics, 7(2), pp.81-108.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SOCIAL NETWORKING
11
Espinoza, V., 2018. Social networks among the urban poor: Inequality and integration in a Latin
American city. In Networks in the global village (pp. 147-184). Routledge.
Newman, M.E., 2016. Mathematics of networks. The new Palgrave dictionary of economics,
pp.1-8..
Sekara, V., Stopczynski, A. and Lehmann, S., 2016. Fundamental structures of dynamic social
networks. Proceedings of the national academy of sciences, 113(36), pp.9977-9982.
Turban, E., Outland, J., King, D., Lee, J.K., Liang, T.P. and Turban, D.C., 2017. Electronic
commerce 2018: a managerial and social networks perspective. Springer.
Wang, P., Xu, B., Wu, Y. and Zhou, X., 2015. Link prediction in social networks: the state-of-
the-art. Science China Information Sciences, 58(1), pp.1-38.
11
Espinoza, V., 2018. Social networks among the urban poor: Inequality and integration in a Latin
American city. In Networks in the global village (pp. 147-184). Routledge.
Newman, M.E., 2016. Mathematics of networks. The new Palgrave dictionary of economics,
pp.1-8..
Sekara, V., Stopczynski, A. and Lehmann, S., 2016. Fundamental structures of dynamic social
networks. Proceedings of the national academy of sciences, 113(36), pp.9977-9982.
Turban, E., Outland, J., King, D., Lee, J.K., Liang, T.P. and Turban, D.C., 2017. Electronic
commerce 2018: a managerial and social networks perspective. Springer.
Wang, P., Xu, B., Wu, Y. and Zhou, X., 2015. Link prediction in social networks: the state-of-
the-art. Science China Information Sciences, 58(1), pp.1-38.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





