Analyzing Social Network Security and Privacy: Capstone Project
VerifiedAdded on 2021/04/17
|14
|1787
|49
Capstone Project
AI Summary
This capstone project examines the critical issues of social network security and privacy, which are increasingly important due to the potential for data breaches and the theft of personal information. The project begins with an introduction and outlines the project's rationale, including problem domain, purpose, and justification. It then presents research questions, a conceptual framework, and the methodology used, which involves both secondary data analysis and user surveys. The project also addresses ethical considerations and compliance requirements. The deliverables include an in-depth analysis of security loopholes, a conceptual framework, and a prototype system. The project plan includes a work breakdown structure, risk analysis, and a Gantt chart. The project aims to develop a new security and privacy framework to protect user data and enhance social network security.

Running Head: EMERGING TECHNOLOGIES AND INNOVATION
Capstone Project: Analyzing Social Network Security and Privacy
Name of the Student
Name of the University
Capstone Project: Analyzing Social Network Security and Privacy
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1EMERGING TECHNOLOGIES AND INNOVATION
Executive Summary
This project is based on the analysis of social networking privacy and security as it is becoming a
growing issue for the users. Unless these issues are addressed, many more users will lose
personal information and data due to data breach and security attacks. Hence, this project aims to
develop a new security and privacy framework that will benefit the social network issues faced
by the users.
Executive Summary
This project is based on the analysis of social networking privacy and security as it is becoming a
growing issue for the users. Unless these issues are addressed, many more users will lose
personal information and data due to data breach and security attacks. Hence, this project aims to
develop a new security and privacy framework that will benefit the social network issues faced
by the users.

2EMERGING TECHNOLOGIES AND INNOVATION
Table of Contents
1.0 Introduction................................................................................................................................3
1.1 Project Blog...........................................................................................................................3
1.2 Weekly Progress Reports Plan...............................................................................................3
2.0 Rationale....................................................................................................................................4
2.1 Problem Domain....................................................................................................................4
2.2 Purpose and Justification.......................................................................................................4
3.0 Sponsor / Supervisor Recommendation.....................................................................................4
4.0 Research Questions....................................................................................................................4
5.0 Conceptual Framework..............................................................................................................5
6.0 Methodology..............................................................................................................................6
7.0 Research and System Development Methods............................................................................6
8.0 Data Collection..........................................................................................................................6
9.0 Ethical Issues.............................................................................................................................6
10.0 Compliance Requirements.......................................................................................................7
11.0 Analysis of Data......................................................................................................................7
12.0 Project Plan..............................................................................................................................7
12.1 Deliverables.........................................................................................................................7
12.2 Work Breakdown Structure.................................................................................................8
12.3 Risk Analysis.......................................................................................................................8
12.4 Duration...............................................................................................................................9
12.5 Gantt Chart...........................................................................................................................9
References......................................................................................................................................11
Table of Contents
1.0 Introduction................................................................................................................................3
1.1 Project Blog...........................................................................................................................3
1.2 Weekly Progress Reports Plan...............................................................................................3
2.0 Rationale....................................................................................................................................4
2.1 Problem Domain....................................................................................................................4
2.2 Purpose and Justification.......................................................................................................4
3.0 Sponsor / Supervisor Recommendation.....................................................................................4
4.0 Research Questions....................................................................................................................4
5.0 Conceptual Framework..............................................................................................................5
6.0 Methodology..............................................................................................................................6
7.0 Research and System Development Methods............................................................................6
8.0 Data Collection..........................................................................................................................6
9.0 Ethical Issues.............................................................................................................................6
10.0 Compliance Requirements.......................................................................................................7
11.0 Analysis of Data......................................................................................................................7
12.0 Project Plan..............................................................................................................................7
12.1 Deliverables.........................................................................................................................7
12.2 Work Breakdown Structure.................................................................................................8
12.3 Risk Analysis.......................................................................................................................8
12.4 Duration...............................................................................................................................9
12.5 Gantt Chart...........................................................................................................................9
References......................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3EMERGING TECHNOLOGIES AND INNOVATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4EMERGING TECHNOLOGIES AND INNOVATION
1.0 Introduction
1.1 Project Blog
This project is based on the analysis of the existing privacy and security options in social
networks. Social media consist of a large variety of websites that are being used by people
around the world as an online public forum where people can share ideas and opinions. Hence, it
is important to maintain security and privacy of the users as their information and data can easily
be hacked or stolen through the social networks. In this project, the current options of security
and privacy have been analyzed and suitable technical and non-technical recommendations have
been made.
1.2 Weekly Progress Reports Plan
As a part of the project activity, weekly progress reports will be developed that will help
to keep track of the progress of the project.
Weekly Progress Report: Week 1 – In this week, the project has been discussed between
the team members to identify the topic and nature of the project to be executed. On day 7, the
proposed topic for the project has been approved by the project supervisor.
Weekly Progress Report: Week 2 – In this week, the project plan has been developed
including project charter, timeline and budget.
The project is yet to complete week 3 and hence, no further progress reports are available
at the moment.
1.0 Introduction
1.1 Project Blog
This project is based on the analysis of the existing privacy and security options in social
networks. Social media consist of a large variety of websites that are being used by people
around the world as an online public forum where people can share ideas and opinions. Hence, it
is important to maintain security and privacy of the users as their information and data can easily
be hacked or stolen through the social networks. In this project, the current options of security
and privacy have been analyzed and suitable technical and non-technical recommendations have
been made.
1.2 Weekly Progress Reports Plan
As a part of the project activity, weekly progress reports will be developed that will help
to keep track of the progress of the project.
Weekly Progress Report: Week 1 – In this week, the project has been discussed between
the team members to identify the topic and nature of the project to be executed. On day 7, the
proposed topic for the project has been approved by the project supervisor.
Weekly Progress Report: Week 2 – In this week, the project plan has been developed
including project charter, timeline and budget.
The project is yet to complete week 3 and hence, no further progress reports are available
at the moment.

5EMERGING TECHNOLOGIES AND INNOVATION
2.0 Rationale
2.1 Problem Domain
The main problem identified is that social networks are open to all and hence, there are
high chances of possible data breach and stealing of personal information of the users (Gritzalis
et al., 2014). Hence, it is important to develop a suitable privacy and security system that will
help to protect the user data in the social networks.
2.2 Purpose and Justification
The purpose of this project is to recommend suitable technical arrangements and non-
technical requirements to ensure the security and privacy of social network users.
Although social networks are subject to extensive research and development, the works
on social media privacy and security have not been very significant and hence, addressing this
particular is necessary.
3.0 Sponsor / Supervisor Recommendation
For this project, the necessary funding will be done by the university under which the
project will be executed.
Project supervisor will be needed to guide the team through various difficulties like
understanding the technical aspects of a social network including the privacy setting and
methods currently deployed and used.
4.0 Research Questions
As per the analysis, the following research questions can be used for the study.
2.0 Rationale
2.1 Problem Domain
The main problem identified is that social networks are open to all and hence, there are
high chances of possible data breach and stealing of personal information of the users (Gritzalis
et al., 2014). Hence, it is important to develop a suitable privacy and security system that will
help to protect the user data in the social networks.
2.2 Purpose and Justification
The purpose of this project is to recommend suitable technical arrangements and non-
technical requirements to ensure the security and privacy of social network users.
Although social networks are subject to extensive research and development, the works
on social media privacy and security have not been very significant and hence, addressing this
particular is necessary.
3.0 Sponsor / Supervisor Recommendation
For this project, the necessary funding will be done by the university under which the
project will be executed.
Project supervisor will be needed to guide the team through various difficulties like
understanding the technical aspects of a social network including the privacy setting and
methods currently deployed and used.
4.0 Research Questions
As per the analysis, the following research questions can be used for the study.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
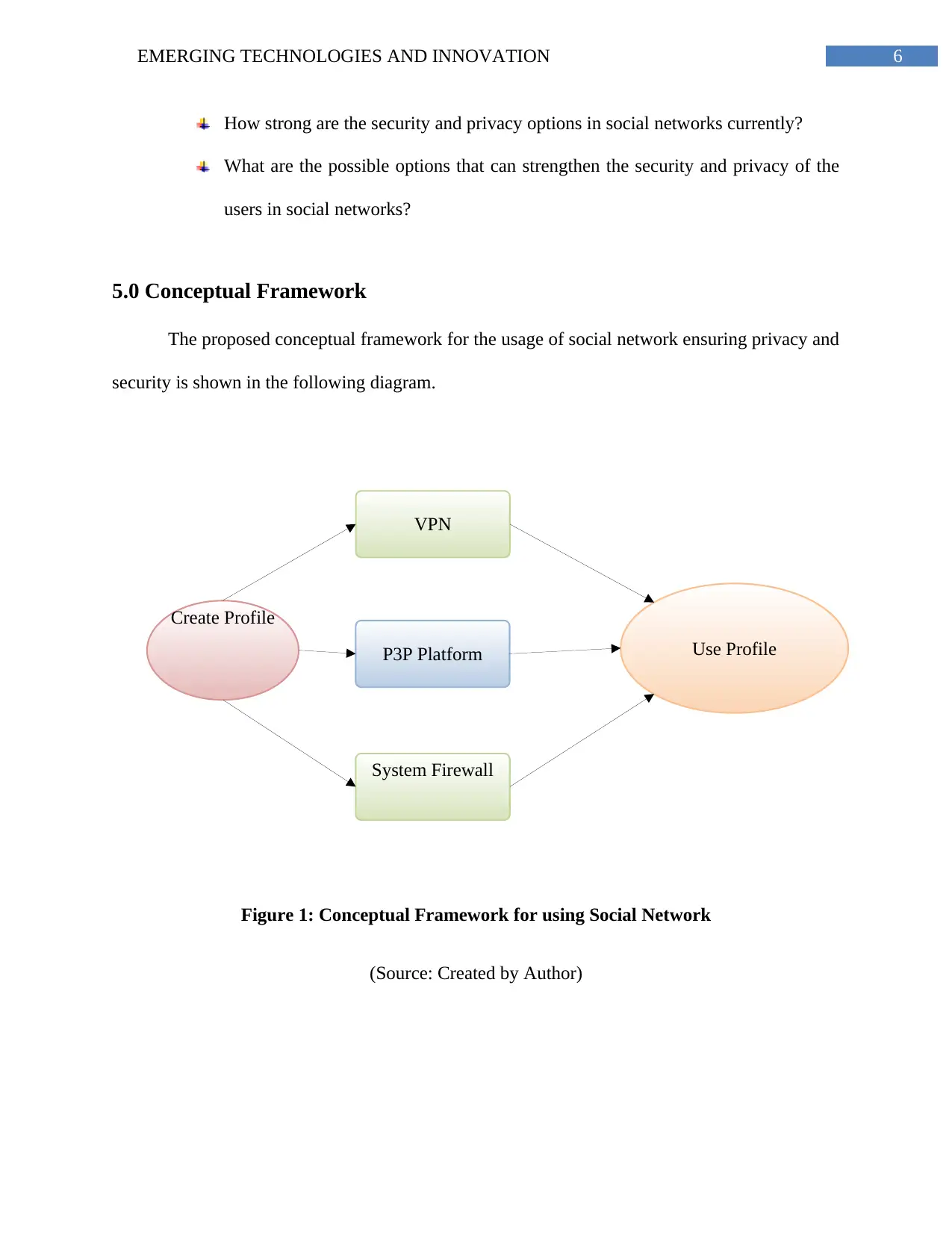
6EMERGING TECHNOLOGIES AND INNOVATION
Create Profile
VPN
P3P Platform
System Firewall
Use Profile
How strong are the security and privacy options in social networks currently?
What are the possible options that can strengthen the security and privacy of the
users in social networks?
5.0 Conceptual Framework
The proposed conceptual framework for the usage of social network ensuring privacy and
security is shown in the following diagram.
Figure 1: Conceptual Framework for using Social Network
(Source: Created by Author)
Create Profile
VPN
P3P Platform
System Firewall
Use Profile
How strong are the security and privacy options in social networks currently?
What are the possible options that can strengthen the security and privacy of the
users in social networks?
5.0 Conceptual Framework
The proposed conceptual framework for the usage of social network ensuring privacy and
security is shown in the following diagram.
Figure 1: Conceptual Framework for using Social Network
(Source: Created by Author)
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





