Social Networking Application Development: Verbania Inc. Project
VerifiedAdded on 2022/08/25
|13
|1921
|33
Project
AI Summary
This capstone project focuses on the development of a social networking application for Verbania Inc., a company aiming to re-enter the market. The project covers various aspects, including system analysis, design, and implementation. The application's core features include account creation, discussion forums, messaging, VOIP, gaming modules, calendar reminders, and a remote wipe facility. Security is a paramount concern, with measures like application code development from scratch, backend network encryption, two-factor authentication, JSON web tokens, mobile encryption policies, and rigorous software testing. The project also includes business and system design documents, use case diagrams, sequence diagrams, and class diagrams to illustrate user interaction and system functionality. The application design ensures user registration, profile management, friend management, and discussion forum posting. The solution also proposes secure wireless communication for the mobile application, incorporating optimal encryption levels and network connectivity. Overall, the project provides a comprehensive IT solution to help Verbania Inc. compete in the social media market.

Running head: SOCIAL NETWORKING APPLICATION DEVELOPMENT
Social Networking Application Development
Name of the Student
Name of the University
Author Note
Social Networking Application Development
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SOCIAL NETWORKING APPLICATION DEVELOPMENT
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Business Drivers.....................................................................................................................3
Current Process......................................................................................................................5
Proposed Process....................................................................................................................7
Software Detailed Design......................................................................................................7
User-Application Interaction..................................................................................................8
Conclusion................................................................................................................................10
Reference..................................................................................................................................11
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Business Drivers.....................................................................................................................3
Current Process......................................................................................................................5
Proposed Process....................................................................................................................7
Software Detailed Design......................................................................................................7
User-Application Interaction..................................................................................................8
Conclusion................................................................................................................................10
Reference..................................................................................................................................11

2SOCIAL NETWORKING APPLICATION DEVELOPMENT
Introduction
The Internet bubble burst incident caused many dot com company to shut down.
Verbania Inc., one of those affected companies shut down in the year 2001.Now the company
is trying to launch itself once again with a new refreshed set of systems. This section will
discuss about the conceptual model of the application part, behaviour of the system, user-
system interaction, possible network securities for the application side of the system, business
design and system design.
Discussion
The company Verbania Inc. shut down due to the internet bubble burst incident and
now wants to re-launch itself once again, the following security measures can be
implemented in the mobile application side:
- Securing the application code – It can be achieved by developing the application from
scratch (developing the whole app without using any third-party source codes).
- Securing the backend network connection of the application – This will be achieved
by incorporating local database encryption of the app (application) and encrypting the
application connection with the server. Application encryption will be made either by
a secure socket layer (SSL), by using a virtual private network (VPN) incorporated
within the application and by including transport layer security (TLS) while
developing the app (Morera et al., 2016).
- Two-factor authentication - While signing up or logging in, the user will require an
OTP (one-time-password) along with his/ her saved password (Osei, Hayfron-
Acquah, & Kumasi, 2014).
- JSON web tokens will be used for exchanging data in an encrypted manner (El-Aziz
& Kannan, 2014).
Introduction
The Internet bubble burst incident caused many dot com company to shut down.
Verbania Inc., one of those affected companies shut down in the year 2001.Now the company
is trying to launch itself once again with a new refreshed set of systems. This section will
discuss about the conceptual model of the application part, behaviour of the system, user-
system interaction, possible network securities for the application side of the system, business
design and system design.
Discussion
The company Verbania Inc. shut down due to the internet bubble burst incident and
now wants to re-launch itself once again, the following security measures can be
implemented in the mobile application side:
- Securing the application code – It can be achieved by developing the application from
scratch (developing the whole app without using any third-party source codes).
- Securing the backend network connection of the application – This will be achieved
by incorporating local database encryption of the app (application) and encrypting the
application connection with the server. Application encryption will be made either by
a secure socket layer (SSL), by using a virtual private network (VPN) incorporated
within the application and by including transport layer security (TLS) while
developing the app (Morera et al., 2016).
- Two-factor authentication - While signing up or logging in, the user will require an
OTP (one-time-password) along with his/ her saved password (Osei, Hayfron-
Acquah, & Kumasi, 2014).
- JSON web tokens will be used for exchanging data in an encrypted manner (El-Aziz
& Kannan, 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SOCIAL NETWORKING APPLICATION DEVELOPMENT
- Integrating mobile encryption policy – Since the application will be maintaining a
local database, file-level encryption will encrypt the data on a file-by-file basis. As a
result, even if the local database gets inspected by some third-party apps or users, it
cannot be read.
- Sensitive data of the user like passwords and user details will not be stored openly in
mobile devices.
- Software testing – before the final launching of the application, the app will be taken
through penetration testing to point out any possible application vulnerability and fix
them accordingly.
- A remote wipe facility will be included within the application. This facility can be
used to remove sensitive user data (if the user thinks they have any) from any stolen
or lost mobile device.
Business Drivers
Main business drivers for re-establishment of the Verbania Inc. are as follows:
- Account creation and maintaining with utmost security
- Discussion forum and posts
- VOIP (Voice over Internet Protocol) and messaging among friends
- Integration of gaming modules
- Calendar reminder inclusion
- Remote wipe facility
- 24/7 customer support availability
Account creation and maintaining
Registering a user will require the user to enter his/ her phone number and other
details; it will be sent to the database (automatic format checking and validation program
embedded with the database). If all the entered details are in a correct format and have no
- Integrating mobile encryption policy – Since the application will be maintaining a
local database, file-level encryption will encrypt the data on a file-by-file basis. As a
result, even if the local database gets inspected by some third-party apps or users, it
cannot be read.
- Sensitive data of the user like passwords and user details will not be stored openly in
mobile devices.
- Software testing – before the final launching of the application, the app will be taken
through penetration testing to point out any possible application vulnerability and fix
them accordingly.
- A remote wipe facility will be included within the application. This facility can be
used to remove sensitive user data (if the user thinks they have any) from any stolen
or lost mobile device.
Business Drivers
Main business drivers for re-establishment of the Verbania Inc. are as follows:
- Account creation and maintaining with utmost security
- Discussion forum and posts
- VOIP (Voice over Internet Protocol) and messaging among friends
- Integration of gaming modules
- Calendar reminder inclusion
- Remote wipe facility
- 24/7 customer support availability
Account creation and maintaining
Registering a user will require the user to enter his/ her phone number and other
details; it will be sent to the database (automatic format checking and validation program
embedded with the database). If all the entered details are in a correct format and have no
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SOCIAL NETWORKING APPLICATION DEVELOPMENT
possible errors in them, the user then gets registered using a captcha verification (to check
that the user is a human and not any artificial code/program) with his /her entered username
and password.
Accessing the application will require logging into the application; while logging in,
the user needs to enter his/her registered username and password. On pressing the login
button in the application, the user will be prompted to enter the OTP (one time password)
sent to his/her registered email and phone number (to check that the user is the owner of the
account s/he is trying to login). Correct OTP will give the user access to the application.
VOIP (Voice over Internet Protocol) and messaging among friends
A registered user with at least one friend in his /her friend list can avail these options
in the developed application. The registered users can share messages among each other. The
sent messages will have a P2P Encryption mechanism. P2P stands for peer-to-peer; here, the
message sent from the user gets encrypted and sent to the desired location (receiver/friend) on
receiving the encrypted message, the receiver decrypts the message (with available key
present with them) and then s/he can read the message. If the message gets intercepted by any
third party user, without the correct key combination s/he (third party user) will not be able to
decrypt the encoded message; as a result message communication privacy is preserved. A
similar scenario will also be used for the VOIP (Alshammari & Zincir-Heywood, 2015).
Discussion forum and posts
Only the users registered with the Verbania Inc. application would be able to add any
posts in the discussion forum and read the same from the forum.
Integration of gaming modules
The application will have different gaming sections for the registered users, which
they can access to get rid of their daily stress and get rejuvenated mind.
possible errors in them, the user then gets registered using a captcha verification (to check
that the user is a human and not any artificial code/program) with his /her entered username
and password.
Accessing the application will require logging into the application; while logging in,
the user needs to enter his/her registered username and password. On pressing the login
button in the application, the user will be prompted to enter the OTP (one time password)
sent to his/her registered email and phone number (to check that the user is the owner of the
account s/he is trying to login). Correct OTP will give the user access to the application.
VOIP (Voice over Internet Protocol) and messaging among friends
A registered user with at least one friend in his /her friend list can avail these options
in the developed application. The registered users can share messages among each other. The
sent messages will have a P2P Encryption mechanism. P2P stands for peer-to-peer; here, the
message sent from the user gets encrypted and sent to the desired location (receiver/friend) on
receiving the encrypted message, the receiver decrypts the message (with available key
present with them) and then s/he can read the message. If the message gets intercepted by any
third party user, without the correct key combination s/he (third party user) will not be able to
decrypt the encoded message; as a result message communication privacy is preserved. A
similar scenario will also be used for the VOIP (Alshammari & Zincir-Heywood, 2015).
Discussion forum and posts
Only the users registered with the Verbania Inc. application would be able to add any
posts in the discussion forum and read the same from the forum.
Integration of gaming modules
The application will have different gaming sections for the registered users, which
they can access to get rid of their daily stress and get rejuvenated mind.

5SOCIAL NETWORKING APPLICATION DEVELOPMENT
Calendar Reminder
This facility will be utilised to give user notification about any important date-time
reminder that the user has set in the application beforehand.
Remote Wipe
In case a user has lost his/ her mobile device or maybe s/he got the mobile device
stolen, then this facility can be used to remove sensitive user data (if the user thinks they have
any) from that stolen or lost mobile device (Yu et al., 2014).
24/7 customer support availability
A dedicated customer support system will be available to resolve any application-
related problem faced by the user at any point of time.
Current Process
The initial release of the application will comprise the following processes:
- Account creation and maintaining with the utmost security
- Discussion forum and posts
- messaging among friends
- 24/7 customer support availability
The following sequence diagram will depict most of the interactions between the user and the
current process development of the application (Sawprakhon & Limpiyakorn, 2014).
Calendar Reminder
This facility will be utilised to give user notification about any important date-time
reminder that the user has set in the application beforehand.
Remote Wipe
In case a user has lost his/ her mobile device or maybe s/he got the mobile device
stolen, then this facility can be used to remove sensitive user data (if the user thinks they have
any) from that stolen or lost mobile device (Yu et al., 2014).
24/7 customer support availability
A dedicated customer support system will be available to resolve any application-
related problem faced by the user at any point of time.
Current Process
The initial release of the application will comprise the following processes:
- Account creation and maintaining with the utmost security
- Discussion forum and posts
- messaging among friends
- 24/7 customer support availability
The following sequence diagram will depict most of the interactions between the user and the
current process development of the application (Sawprakhon & Limpiyakorn, 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
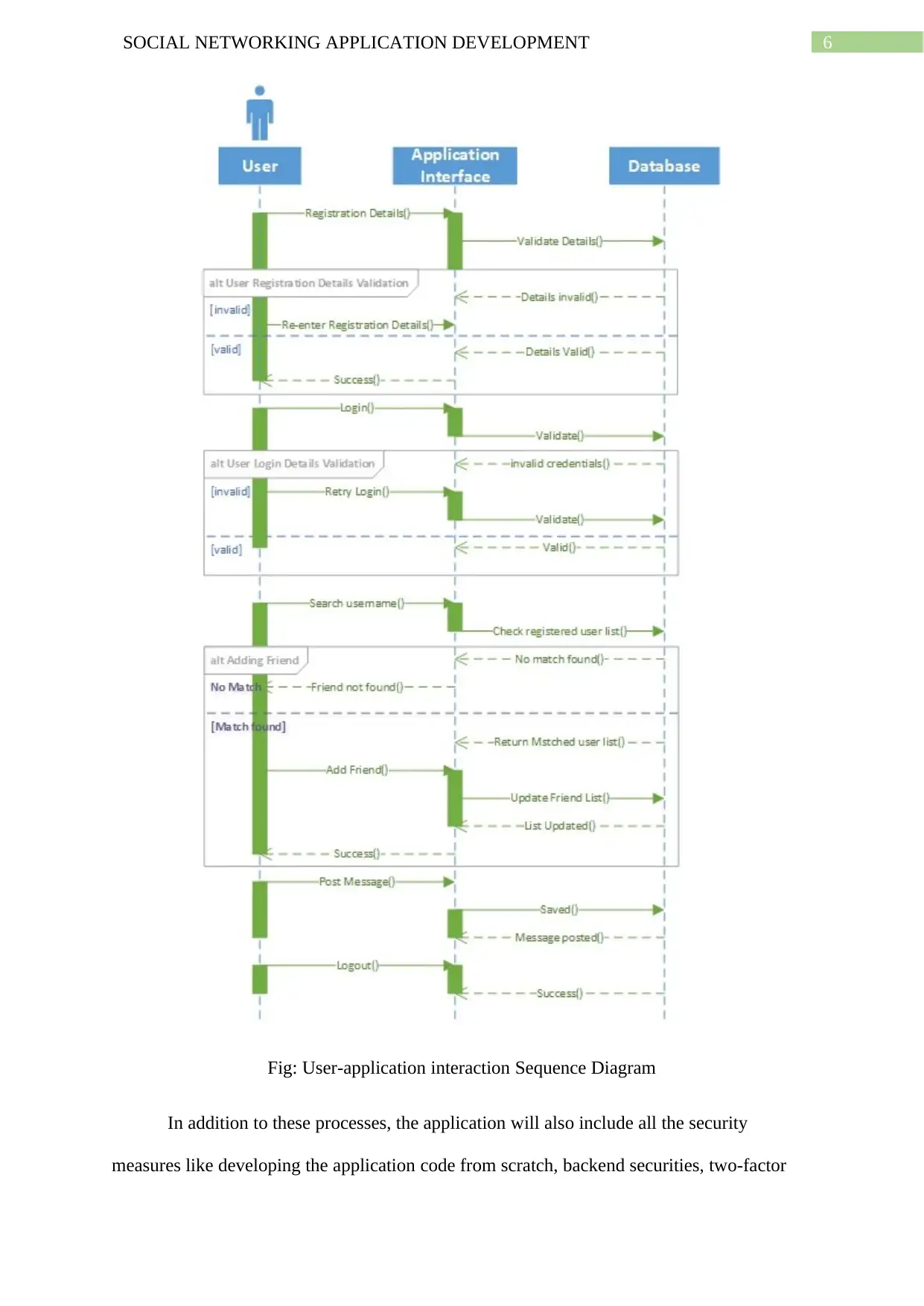
6SOCIAL NETWORKING APPLICATION DEVELOPMENT
Fig: User-application interaction Sequence Diagram
In addition to these processes, the application will also include all the security
measures like developing the application code from scratch, backend securities, two-factor
Fig: User-application interaction Sequence Diagram
In addition to these processes, the application will also include all the security
measures like developing the application code from scratch, backend securities, two-factor
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SOCIAL NETWORKING APPLICATION DEVELOPMENT
authentication, use of JSON tokens, mobile encryption policy, and rigors software testing
before release.
Proposed Process
After the inclusion of the processes as mentioned earlier in the initial release of the
application, the following processes will be implemented in the following application
releases/upgrade:
- VOIP (Voice over Internet Protocol) among friends
- Integration of gaming modules
- Calendar reminder inclusion
- Remote wipe facility
Software Detailed Design
The following class diagram will explain about the initial release application design in
detail (Thongrak & Vatanawood, 2014):
authentication, use of JSON tokens, mobile encryption policy, and rigors software testing
before release.
Proposed Process
After the inclusion of the processes as mentioned earlier in the initial release of the
application, the following processes will be implemented in the following application
releases/upgrade:
- VOIP (Voice over Internet Protocol) among friends
- Integration of gaming modules
- Calendar reminder inclusion
- Remote wipe facility
Software Detailed Design
The following class diagram will explain about the initial release application design in
detail (Thongrak & Vatanawood, 2014):

8SOCIAL NETWORKING APPLICATION DEVELOPMENT
Fig: Class Diagram of the initial app release
From the above diagram, we can conclude the following functionality of the application:
Login and Registration (Account setup)
Profile creation
Posting a message in the discussion section
Adding a user to friend list and removing of the same from the friend list
User-Application Interaction
The below use case diagram will explain about the user-application interaction in the
initial release (Singh, Sharma & Saxena, 2016):
Fig: Class Diagram of the initial app release
From the above diagram, we can conclude the following functionality of the application:
Login and Registration (Account setup)
Profile creation
Posting a message in the discussion section
Adding a user to friend list and removing of the same from the friend list
User-Application Interaction
The below use case diagram will explain about the user-application interaction in the
initial release (Singh, Sharma & Saxena, 2016):
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
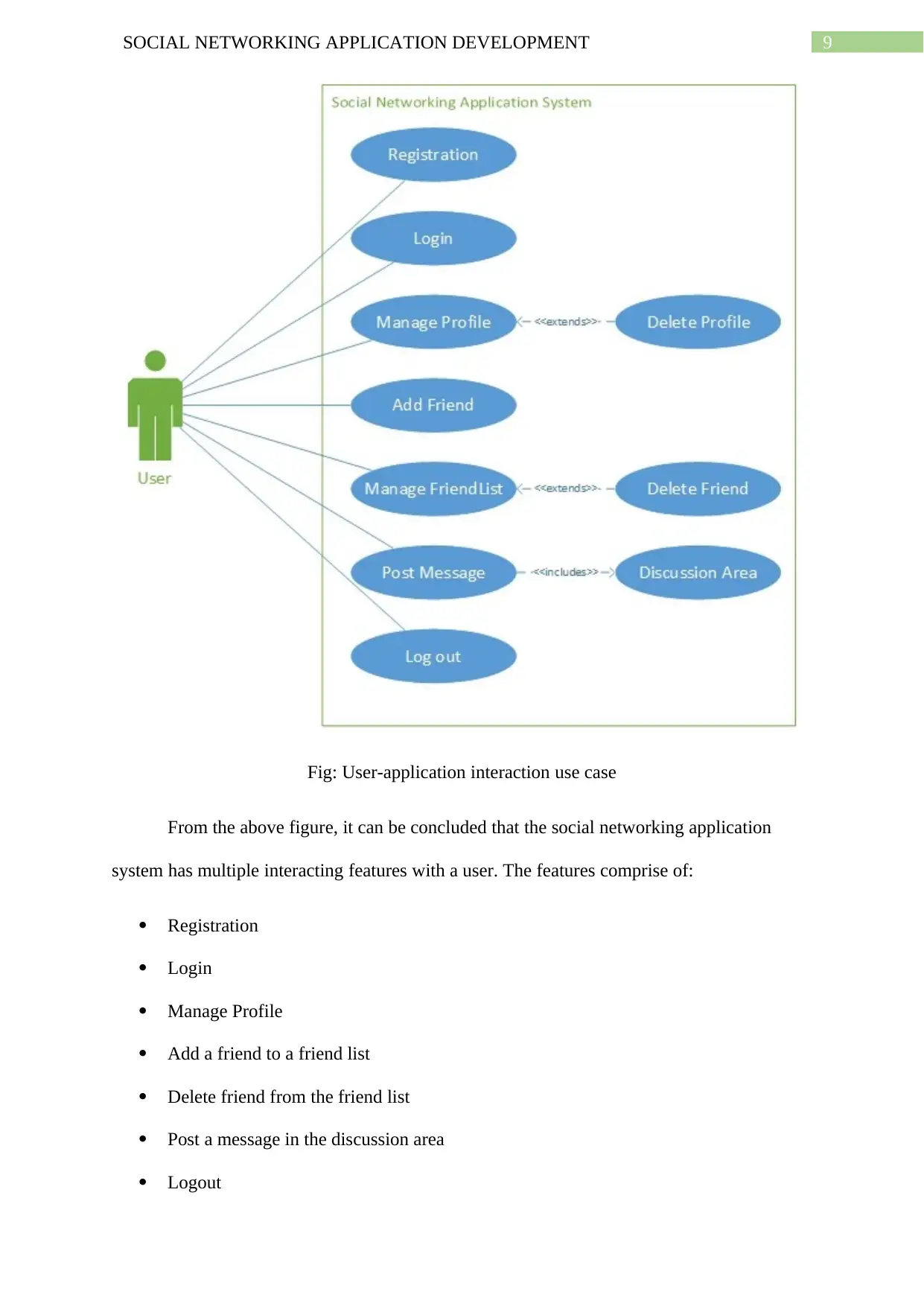
9SOCIAL NETWORKING APPLICATION DEVELOPMENT
Fig: User-application interaction use case
From the above figure, it can be concluded that the social networking application
system has multiple interacting features with a user. The features comprise of:
Registration
Login
Manage Profile
Add a friend to a friend list
Delete friend from the friend list
Post a message in the discussion area
Logout
Fig: User-application interaction use case
From the above figure, it can be concluded that the social networking application
system has multiple interacting features with a user. The features comprise of:
Registration
Login
Manage Profile
Add a friend to a friend list
Delete friend from the friend list
Post a message in the discussion area
Logout
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SOCIAL NETWORKING APPLICATION DEVELOPMENT
Conclusion
In the end, it can be concluded that the new proposed system will solve the software,
networking, and security side of the system very efficiently. Using the application the user
can register himself/herself in the application system. Upon completion of the registration
process, the user can then login to the application to manage his/her profile, add another user
as a friend in the respective friend list, manage the friend list, post a message in the
discussion area and finally logout of the application. The various security features include the
development of own software framework from scratch, VPN support, SSL support, JSON
token-based data sharing, encryption policy and many more. These will help Verbania, Inc.
stand in the market and to some extent, rival with the present marketing corporations
delivering similar types of application.
Conclusion
In the end, it can be concluded that the new proposed system will solve the software,
networking, and security side of the system very efficiently. Using the application the user
can register himself/herself in the application system. Upon completion of the registration
process, the user can then login to the application to manage his/her profile, add another user
as a friend in the respective friend list, manage the friend list, post a message in the
discussion area and finally logout of the application. The various security features include the
development of own software framework from scratch, VPN support, SSL support, JSON
token-based data sharing, encryption policy and many more. These will help Verbania, Inc.
stand in the market and to some extent, rival with the present marketing corporations
delivering similar types of application.

11SOCIAL NETWORKING APPLICATION DEVELOPMENT
Reference
Alshammari, R., & Zincir-Heywood, A. N. (2015). Identification of VoIP encrypted traffic
using a machine learning approach. Journal of King Saud University-Computer and
Information Sciences, 27(1), 77-92.
El-Aziz, A. A., & Kannan, A. (2014, January). JSON encryption. In 2014 International
Conference on Computer Communication and Informatics (pp. 1-6). IEEE.
Morera, E. P., de la Torre Díez, I., Garcia-Zapirain, B., López-Coronado, M., & Arambarri, J.
(2016). Security recommendations for mHealth apps: elaboration of a Developer’s
guide. Journal of medical systems, 40(6), 152.
Osei, E. O., Hayfron-Acquah, J. B., & Kumasi, K. N. U. S. T. (2014). Cloud computing login
authentication redesign. International Journal of Electronics and Information
Engineering, 1(1), 1-8.
Sawprakhon, P., & Limpiyakorn, Y. (2014, March). Sequence diagram generation with
model transformation technology. In Proceedings of the International
MultiConference of Engineers and Computer Scientists (Vol. 1, No. 14, pp. 20-30).
Singh, M., Sharma, A. K., & Saxena, R. (2016). Formal Transformation of UML Diagram:
Use Case, Class, Sequence Diagram with Z Notation for Representing the Static and
Dynamic Perspectives of System. In Proceedings of International Conference on ICT
for Sustainable Development (pp. 25-38). Springer, Singapore.
Thongrak, M., & Vatanawood, W. (2014, July). Detection of design pattern in class diagram
using ontology. In 2014 International Computer Science and Engineering Conference
(ICSEC) (pp. 97-102). IEEE.
Reference
Alshammari, R., & Zincir-Heywood, A. N. (2015). Identification of VoIP encrypted traffic
using a machine learning approach. Journal of King Saud University-Computer and
Information Sciences, 27(1), 77-92.
El-Aziz, A. A., & Kannan, A. (2014, January). JSON encryption. In 2014 International
Conference on Computer Communication and Informatics (pp. 1-6). IEEE.
Morera, E. P., de la Torre Díez, I., Garcia-Zapirain, B., López-Coronado, M., & Arambarri, J.
(2016). Security recommendations for mHealth apps: elaboration of a Developer’s
guide. Journal of medical systems, 40(6), 152.
Osei, E. O., Hayfron-Acquah, J. B., & Kumasi, K. N. U. S. T. (2014). Cloud computing login
authentication redesign. International Journal of Electronics and Information
Engineering, 1(1), 1-8.
Sawprakhon, P., & Limpiyakorn, Y. (2014, March). Sequence diagram generation with
model transformation technology. In Proceedings of the International
MultiConference of Engineers and Computer Scientists (Vol. 1, No. 14, pp. 20-30).
Singh, M., Sharma, A. K., & Saxena, R. (2016). Formal Transformation of UML Diagram:
Use Case, Class, Sequence Diagram with Z Notation for Representing the Static and
Dynamic Perspectives of System. In Proceedings of International Conference on ICT
for Sustainable Development (pp. 25-38). Springer, Singapore.
Thongrak, M., & Vatanawood, W. (2014, July). Detection of design pattern in class diagram
using ontology. In 2014 International Computer Science and Engineering Conference
(ICSEC) (pp. 97-102). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



