Report: Security Issues and Threats in Social Networking Websites
VerifiedAdded on 2023/01/10
|23
|4896
|34
Report
AI Summary
This report delves into the critical security challenges prevalent in social networking websites. It begins by defining social networking platforms and their widespread usage, highlighting the increasing risks associated with online activities. The report explores various cyber threats, including phishing attacks, malware, and data breaches, emphasizing their impact on individuals and organizations. It examines the background of research, its significance, aims, and objectives, along with the research questions guiding the study. The scope and delimitations are defined, and the sources of knowledge are identified. A comprehensive review of literature covers different types of security issues, the reasons for social networking website usage, and ways to mitigate risks. The report also addresses research methodologies, ethical, legal, and security issues, and provides an activities timescale. The report aims to create a framework to analyze security threats and issues associated with different social networking websites. The objectives are to critically evaluate cyber threats, identify usage patterns, evaluate data collection methodologies, and recommend risk mitigation tools and strategies. The report concludes by emphasizing the importance of awareness and proactive measures to safeguard users and organizations against cybercrimes and promote safe online practices.

Analyse Security Issues and Threats
Associated with Social Networking Websites
Associated with Social Networking Websites
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION:..........................................................................................................................3
MAIN BODY ..................................................................................................................................4
Background of research :........................................................................................................4
Significance............................................................................................................................5
Aims and objectives...............................................................................................................5
Research questions.................................................................................................................6
Scope and Delimitations.........................................................................................................6
Sources of knowledge:...........................................................................................................6
Review of Literature .......................................................................................................................7
1. Types of security issues are associated with social networking websites..........................7
2. Ways or reasons of using social networking websites.......................................................8
3. Ways to mitigate risks associated with social networking websites..................................9
Research methodologies .................................................................................................................9
Ethics, legal and security issues...........................................................................................10
Activities timescale..............................................................................................................11
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13
INTRODUCTION:..........................................................................................................................3
MAIN BODY ..................................................................................................................................4
Background of research :........................................................................................................4
Significance............................................................................................................................5
Aims and objectives...............................................................................................................5
Research questions.................................................................................................................6
Scope and Delimitations.........................................................................................................6
Sources of knowledge:...........................................................................................................6
Review of Literature .......................................................................................................................7
1. Types of security issues are associated with social networking websites..........................7
2. Ways or reasons of using social networking websites.......................................................8
3. Ways to mitigate risks associated with social networking websites..................................9
Research methodologies .................................................................................................................9
Ethics, legal and security issues...........................................................................................10
Activities timescale..............................................................................................................11
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13

INTRODUCTION:
Before discussing about issues related to social networking websites it is important to
understand that what is social networking websites and how it is being used by people. So, in this
context it can be said that it is sources and platforms which allow users to share their ideas,
photos, videos, posts and also communicate or make other people aware about their real world
activities (Saleem and Ellahi, 2017). It is in trend that people make use of social networking
websites and let others know about their daily real life activities as what they are eating, what
they are doing, where they are going , with whom they are going and others. This online
platform or websites are being developed to make people beneficial in making their work easier
and also make them feel refreshed. Some examples of social networking websites which are the
most used include: Face Book, LinkedIn, Twitter and others. These activities and sharing of
people about their daily lives online is increasing risks for them and it is the reason of increasing
cyber crimes. There are several cyber crimes which are increasing day by day and which are
affecting lives of innocent people. Some examples of security threats and issues which are
associated with social networking websites include: phishing and scams. It is all about related to
social media informations risks and breach of privacy data or informations which people share
with others. There are several organizations which make a great use of social networking
websites for making their work easier and great extent use of this site due to lack of knowledge
and others are increasing risks for their employees and business like breach of banking details,
professional and personal informations of employees and clients (Kuss and Griffiths, 2017).
In the context of phishing attack it can be said that it is one of the main concerns because
this cyber attack is affecting lives of users and organizations as well. In this type of attack,
attackers’ attempts to trick users into doing unethical and wrong things y clicking on a bad link
which download malware by which attackers can get all information stored in the system. It is
easier for attackers because they can attack systems and hack them via social media, text and by
phone but one of the main attacks which arrive is by E-mail. Because phishing e mails can reach
to several and millions of people at a time and install malware.
In addition, it can also be said that this attack has been a major issue for security since
long without having a good solution in place. The main problem with this phishing attack is a
holistic solution. It can help and protect users against being phished and securing their
Before discussing about issues related to social networking websites it is important to
understand that what is social networking websites and how it is being used by people. So, in this
context it can be said that it is sources and platforms which allow users to share their ideas,
photos, videos, posts and also communicate or make other people aware about their real world
activities (Saleem and Ellahi, 2017). It is in trend that people make use of social networking
websites and let others know about their daily real life activities as what they are eating, what
they are doing, where they are going , with whom they are going and others. This online
platform or websites are being developed to make people beneficial in making their work easier
and also make them feel refreshed. Some examples of social networking websites which are the
most used include: Face Book, LinkedIn, Twitter and others. These activities and sharing of
people about their daily lives online is increasing risks for them and it is the reason of increasing
cyber crimes. There are several cyber crimes which are increasing day by day and which are
affecting lives of innocent people. Some examples of security threats and issues which are
associated with social networking websites include: phishing and scams. It is all about related to
social media informations risks and breach of privacy data or informations which people share
with others. There are several organizations which make a great use of social networking
websites for making their work easier and great extent use of this site due to lack of knowledge
and others are increasing risks for their employees and business like breach of banking details,
professional and personal informations of employees and clients (Kuss and Griffiths, 2017).
In the context of phishing attack it can be said that it is one of the main concerns because
this cyber attack is affecting lives of users and organizations as well. In this type of attack,
attackers’ attempts to trick users into doing unethical and wrong things y clicking on a bad link
which download malware by which attackers can get all information stored in the system. It is
easier for attackers because they can attack systems and hack them via social media, text and by
phone but one of the main attacks which arrive is by E-mail. Because phishing e mails can reach
to several and millions of people at a time and install malware.
In addition, it can also be said that this attack has been a major issue for security since
long without having a good solution in place. The main problem with this phishing attack is a
holistic solution. It can help and protect users against being phished and securing their
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

informations as well. So, it can be said that there is requirement of advanced security and
effective ways of eliminating this problem in an effective manner.
MAIN BODY
Background of research :
Phishing attack is one of the major problem and concern for banking and all e-
commerce services providers. Uses of social networking websites and internet of things to the
great extent is increasing risks of cyber crimes and phishing attacks which need to be reduced
and eliminated in an effective and timely manner. Phishing attacks are becoming so advanced
and hackers and criminals are focusing on new and other ways of gathering personal and
professional data which are affecting profits of E-commerce and banking sector to the great
extent.
It is stated that half of SMEs of the UK has been affected because of Phishing attacks as
hackers go after smaller targets (Half of UK SMEs Hit by Phishing Attack, 2019).
Phishing is currently the dominant attack vector for entry into networks and also understanding
its popularity is becoming hard. An impersonation phishing attack which involve user’s friends,
families and close relatives is posing a particular threat. It is also stated that still UK’s businesses
are not taking these attacks and crimes seriously and also not taking strict actions against it. They
are only paying lip services to security training for compliance reasons for reducing human cyber
risks (Bharucha, 2018).
In addition, there are some other common types of cyber attacks which include:
password attacks, malware attacks, Denial of service attacks.
Password attacks: In password attacks, attackers try to get access to user's password by looking
around their desk and sniffing the main connection to the network in order to acquire un-
encrypted passwords. Brute forced password guessing is one of the main technique of password
attack in which attackers try different passwords which are commonly used by people.
Malware attacks: In addition, in malware attacks, attackers can have access to data by installing
unwanted software in system without consent of users. Macro viruses, file infects and Trojans
are some ways of malware attacking. All these techniques and viruses infect applications like
excel and others. When injected applications are opened by users then virus executes instructions
before transferring control to the application.
effective ways of eliminating this problem in an effective manner.
MAIN BODY
Background of research :
Phishing attack is one of the major problem and concern for banking and all e-
commerce services providers. Uses of social networking websites and internet of things to the
great extent is increasing risks of cyber crimes and phishing attacks which need to be reduced
and eliminated in an effective and timely manner. Phishing attacks are becoming so advanced
and hackers and criminals are focusing on new and other ways of gathering personal and
professional data which are affecting profits of E-commerce and banking sector to the great
extent.
It is stated that half of SMEs of the UK has been affected because of Phishing attacks as
hackers go after smaller targets (Half of UK SMEs Hit by Phishing Attack, 2019).
Phishing is currently the dominant attack vector for entry into networks and also understanding
its popularity is becoming hard. An impersonation phishing attack which involve user’s friends,
families and close relatives is posing a particular threat. It is also stated that still UK’s businesses
are not taking these attacks and crimes seriously and also not taking strict actions against it. They
are only paying lip services to security training for compliance reasons for reducing human cyber
risks (Bharucha, 2018).
In addition, there are some other common types of cyber attacks which include:
password attacks, malware attacks, Denial of service attacks.
Password attacks: In password attacks, attackers try to get access to user's password by looking
around their desk and sniffing the main connection to the network in order to acquire un-
encrypted passwords. Brute forced password guessing is one of the main technique of password
attack in which attackers try different passwords which are commonly used by people.
Malware attacks: In addition, in malware attacks, attackers can have access to data by installing
unwanted software in system without consent of users. Macro viruses, file infects and Trojans
are some ways of malware attacking. All these techniques and viruses infect applications like
excel and others. When injected applications are opened by users then virus executes instructions
before transferring control to the application.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Significance
Social networking websites or internet has become an important part of people and their
daily lives as they cannot imagine their lives without internet and social networking websites. All
these sites was mainly developed to allow people to contact with their relatives friends and
anyone, anytime and also make uses in business promotion and other important activities. But
nowadays people are using these sites to the great extent and children are becoming addicted to
it. This addiction and lack of knowledge of using these sites in an effective manner is becoming
reason of cyber crimes which are affecting lives of people in a negative manner.
Some examples of cyber crimes in social networking include: malware in which due to infected
files and installed viruses by attackers, people open attachments sent by people in friend list, they
do not have knowledge that they are opening themselves up to the potential of malware infection.
Data breaches is main crime happened with social media platforms. By password attack,
attackers can get credit card informations and other personal informations which can create
several problems for users.
So, the main reason of selecting this topic is to make people aware about consequences of
using social networking sites in an ineffective manner and to the great extent (Parulekar, 2019).
To help people and prevent them against cyber crimes like breach of personal data, threats from
hackers and others and allow them to make use of internet and social media sites in an effective
manner is the main reason of conducting study on this topic.
Aims and objectives
Aim- To model a frame work that will analyze security threats and issues associated with
different social networking websites.
Objectives
To critically evaluate cyber threats in social networking websites.
To identify ways or reasons of using social networking websites.
To critically evaluate data collection methodologies for data collection relevant to the
topic.
To recommend some tools and ways to mitigate risks associated with social networking
websites.
Social networking websites or internet has become an important part of people and their
daily lives as they cannot imagine their lives without internet and social networking websites. All
these sites was mainly developed to allow people to contact with their relatives friends and
anyone, anytime and also make uses in business promotion and other important activities. But
nowadays people are using these sites to the great extent and children are becoming addicted to
it. This addiction and lack of knowledge of using these sites in an effective manner is becoming
reason of cyber crimes which are affecting lives of people in a negative manner.
Some examples of cyber crimes in social networking include: malware in which due to infected
files and installed viruses by attackers, people open attachments sent by people in friend list, they
do not have knowledge that they are opening themselves up to the potential of malware infection.
Data breaches is main crime happened with social media platforms. By password attack,
attackers can get credit card informations and other personal informations which can create
several problems for users.
So, the main reason of selecting this topic is to make people aware about consequences of
using social networking sites in an ineffective manner and to the great extent (Parulekar, 2019).
To help people and prevent them against cyber crimes like breach of personal data, threats from
hackers and others and allow them to make use of internet and social media sites in an effective
manner is the main reason of conducting study on this topic.
Aims and objectives
Aim- To model a frame work that will analyze security threats and issues associated with
different social networking websites.
Objectives
To critically evaluate cyber threats in social networking websites.
To identify ways or reasons of using social networking websites.
To critically evaluate data collection methodologies for data collection relevant to the
topic.
To recommend some tools and ways to mitigate risks associated with social networking
websites.

Research questions
1. Which types of security issues are associated with social networking websites?
2. Why and how people are making use of social networking websites nowadays?
3. How to evaluate data collection methodologies for gathering information relevant to the
topic?
4. What are some ways of eliminating all security threats related to social networking
websites?
Scope and Delimitations
The reason of conducting this study is gathering informations and ways as how hackers
get personal informations and attack on systems. By knowing different types of cyber security
issues all users can be made aware as how to prevent themselves against all these issues. It will
also focus on collecting informations and know about phishing attacks in banking and E-
commerce sector. After analysing and identifying phishing attacks, scholar will create an
effective design in order to make users aware about taking prevention measures with the help of
informations which they gather from different sources and customers’ feedbacks (McGeehan and
et.al., 2017).
So, overall it can be said that the main objective is preventing all users and companies
against phishing attacks and continuing their functions in an effective manner. It has scope to the
great extent as it can help all users of internet and social networking websites.
Sources of knowledge:
Getting informations relevant to the topic is not an easy task as researcher has to make
lists of all resources or sources from where he can get all accurate and viable informations in an
ethical manner without hurting others. There are several sources are available but identifying is
whether they are reliable or not is the main task. So, in the context of social networking issues
and threat like phishing attacks and getting all informations like how many users and
organizations have affected, researcher will make an effective use of books and journals and peer
reviewed articles. These peer reviewed articles can allow them to get all effective informations
and making the study successful as well as making users aware about how to prevent themselves
against this.
1. Which types of security issues are associated with social networking websites?
2. Why and how people are making use of social networking websites nowadays?
3. How to evaluate data collection methodologies for gathering information relevant to the
topic?
4. What are some ways of eliminating all security threats related to social networking
websites?
Scope and Delimitations
The reason of conducting this study is gathering informations and ways as how hackers
get personal informations and attack on systems. By knowing different types of cyber security
issues all users can be made aware as how to prevent themselves against all these issues. It will
also focus on collecting informations and know about phishing attacks in banking and E-
commerce sector. After analysing and identifying phishing attacks, scholar will create an
effective design in order to make users aware about taking prevention measures with the help of
informations which they gather from different sources and customers’ feedbacks (McGeehan and
et.al., 2017).
So, overall it can be said that the main objective is preventing all users and companies
against phishing attacks and continuing their functions in an effective manner. It has scope to the
great extent as it can help all users of internet and social networking websites.
Sources of knowledge:
Getting informations relevant to the topic is not an easy task as researcher has to make
lists of all resources or sources from where he can get all accurate and viable informations in an
ethical manner without hurting others. There are several sources are available but identifying is
whether they are reliable or not is the main task. So, in the context of social networking issues
and threat like phishing attacks and getting all informations like how many users and
organizations have affected, researcher will make an effective use of books and journals and peer
reviewed articles. These peer reviewed articles can allow them to get all effective informations
and making the study successful as well as making users aware about how to prevent themselves
against this.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

There are some articles which are related to cyber security for internet of things.“Cyber-
Assurance for the Internet of Things and related kinds of books is one of the main source which
discusses different ways of cyber assurance approaches and different types of cyber attack on
social networking websites.
Digital libraries can also allow researcher in getting all informations and answering of all
questions for accomplishing objectives with the main aim. Research gate, ACM is some mixed
words as anti phishing. With peer reviewed articles which consist of actual data as how many
users and companies get affected and what ways and strategies are being taken by them for
solving issues will be used by scholar.
Review of Literature
Literature review is one of the best ways of getting answers of all questions by different
views of authors. With the help of literature and comprehensive depth review researcher get
relevant informations as in this different authors argue on the same topic with appropriate
evidence. So, it becomes easier for scholar to get appropriate informations and making decision
about making use of informations.
1. Types of security issues are associated with social networking websites
There are some types of security issues which are associated with social networking
websites such as: social networking sites, impersonation and trust. In social networking sites,
hackers directly go to the sources and inject malicious code into social networking sites. It is
known as phishing attacks in which attackers use some websites into malicious sites. Twitter is
especially vulnerable to this method because it's easy to re-tweet a post (Aonzo and et.al., 2018).
In addition, trust related issues are one of the main cyber crimes. When people trust links,
videos and their pictures and they get scammed a few times. So, it can be said that phishing is
one of the main cyber attack in which attackers trick e mails recipient. E mail phishing is one of
the most effected attack or cyber crime because attackers find it easy to attack by e mails. In this
type, users are asked to open or click on link which is being sent by attackers. This fake or
modified link takes users to a fake page which asks ID and password. Due to lack of knowledge
many uses enter their ID and password which directly goes to scammers and by doing so they
can get all informations of users.
Botnet attacks:
Assurance for the Internet of Things and related kinds of books is one of the main source which
discusses different ways of cyber assurance approaches and different types of cyber attack on
social networking websites.
Digital libraries can also allow researcher in getting all informations and answering of all
questions for accomplishing objectives with the main aim. Research gate, ACM is some mixed
words as anti phishing. With peer reviewed articles which consist of actual data as how many
users and companies get affected and what ways and strategies are being taken by them for
solving issues will be used by scholar.
Review of Literature
Literature review is one of the best ways of getting answers of all questions by different
views of authors. With the help of literature and comprehensive depth review researcher get
relevant informations as in this different authors argue on the same topic with appropriate
evidence. So, it becomes easier for scholar to get appropriate informations and making decision
about making use of informations.
1. Types of security issues are associated with social networking websites
There are some types of security issues which are associated with social networking
websites such as: social networking sites, impersonation and trust. In social networking sites,
hackers directly go to the sources and inject malicious code into social networking sites. It is
known as phishing attacks in which attackers use some websites into malicious sites. Twitter is
especially vulnerable to this method because it's easy to re-tweet a post (Aonzo and et.al., 2018).
In addition, trust related issues are one of the main cyber crimes. When people trust links,
videos and their pictures and they get scammed a few times. So, it can be said that phishing is
one of the main cyber attack in which attackers trick e mails recipient. E mail phishing is one of
the most effected attack or cyber crime because attackers find it easy to attack by e mails. In this
type, users are asked to open or click on link which is being sent by attackers. This fake or
modified link takes users to a fake page which asks ID and password. Due to lack of knowledge
many uses enter their ID and password which directly goes to scammers and by doing so they
can get all informations of users.
Botnet attacks:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Botnet attacks are main types of attacks as it is a collection of internet connected devices
which got infected by malware attacks in which attackers or hackers can have control on internet
connection. It is stated that around 80% of botnet attacks are encountered through DDoS which
is most commonly done through spam. Cybercriminals gain access to all devices which are being
operated by botnet owners at a time. By using special Trojan viruses, hackers attack on
computer's security systems which can cause unplanned application downtime etc.
Imposter accounts
Creating an imposter account by hackers which looks and seems like it belongs to the
same person or victim or targeted company. This is one of the main reasons of getting OTP and
relevant messages for verification. But if attackers is relative and known to victim and mobile
phones are not secure with password then attackers can get and password and can verify
imposter accounts.
Human error
Human errors sometimes create many other major problems and it happens because of
busy and hectic schedule. It is easy for an employee to expose their company accidentally to
threats online. These errors become reasons of cyber attacks such as clicking on wrong link,
providing answers to online quiz etc.
Nowadays all people use social media platforms like Instagram, Face book and others
and there are many crimes which are mainly associated with these social websites. There are
some data which shows increasing numbers of people or adults of using social media or social
websites.
which got infected by malware attacks in which attackers or hackers can have control on internet
connection. It is stated that around 80% of botnet attacks are encountered through DDoS which
is most commonly done through spam. Cybercriminals gain access to all devices which are being
operated by botnet owners at a time. By using special Trojan viruses, hackers attack on
computer's security systems which can cause unplanned application downtime etc.
Imposter accounts
Creating an imposter account by hackers which looks and seems like it belongs to the
same person or victim or targeted company. This is one of the main reasons of getting OTP and
relevant messages for verification. But if attackers is relative and known to victim and mobile
phones are not secure with password then attackers can get and password and can verify
imposter accounts.
Human error
Human errors sometimes create many other major problems and it happens because of
busy and hectic schedule. It is easy for an employee to expose their company accidentally to
threats online. These errors become reasons of cyber attacks such as clicking on wrong link,
providing answers to online quiz etc.
Nowadays all people use social media platforms like Instagram, Face book and others
and there are many crimes which are mainly associated with these social websites. There are
some data which shows increasing numbers of people or adults of using social media or social
websites.
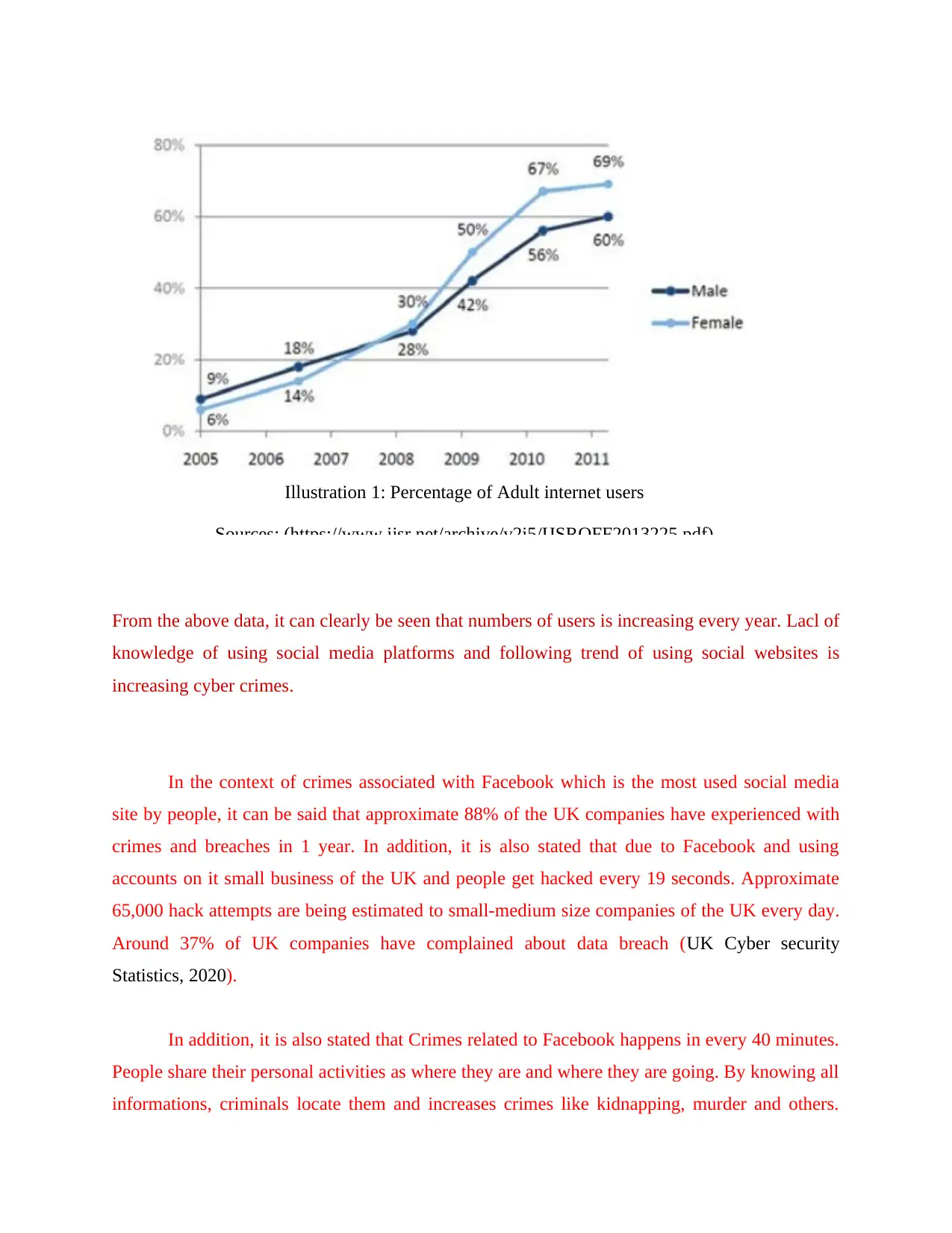
From the above data, it can clearly be seen that numbers of users is increasing every year. Lacl of
knowledge of using social media platforms and following trend of using social websites is
increasing cyber crimes.
In the context of crimes associated with Facebook which is the most used social media
site by people, it can be said that approximate 88% of the UK companies have experienced with
crimes and breaches in 1 year. In addition, it is also stated that due to Facebook and using
accounts on it small business of the UK and people get hacked every 19 seconds. Approximate
65,000 hack attempts are being estimated to small-medium size companies of the UK every day.
Around 37% of UK companies have complained about data breach (UK Cyber security
Statistics, 2020).
In addition, it is also stated that Crimes related to Facebook happens in every 40 minutes.
People share their personal activities as where they are and where they are going. By knowing all
informations, criminals locate them and increases crimes like kidnapping, murder and others.
Illustration 1: Percentage of Adult internet users
Sources: (https://www.ijsr.net/archive/v2i5/IJSROFF2013225.pdf)
knowledge of using social media platforms and following trend of using social websites is
increasing cyber crimes.
In the context of crimes associated with Facebook which is the most used social media
site by people, it can be said that approximate 88% of the UK companies have experienced with
crimes and breaches in 1 year. In addition, it is also stated that due to Facebook and using
accounts on it small business of the UK and people get hacked every 19 seconds. Approximate
65,000 hack attempts are being estimated to small-medium size companies of the UK every day.
Around 37% of UK companies have complained about data breach (UK Cyber security
Statistics, 2020).
In addition, it is also stated that Crimes related to Facebook happens in every 40 minutes.
People share their personal activities as where they are and where they are going. By knowing all
informations, criminals locate them and increases crimes like kidnapping, murder and others.
Illustration 1: Percentage of Adult internet users
Sources: (https://www.ijsr.net/archive/v2i5/IJSROFF2013225.pdf)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Hackers can also get personal informations by using passwords and Email of people (Crimes
associated with Facebook, 2012).
Cyber attacks: Past, present and future
In the context of phishing which is a hacker' term it can be said that it originated from
fraudsters whom are “fishing” for confidential information in which attackers attack system of
users by sending fake links on E-mail. There are some common problems and challenges
associated with this attack include: Spear phishing, breach or access to personal and professional
data, smishing, vising and others.
Main target of phishing attack by attackers are innocent users who do not have
appropriate knowledge about operating system. By sending fake E mail and link to them, they
deceive them. Nowadays companies and people have become aware about security and for this
they have developed some programs which make people aware about security. Advancement of
technology has also reduced phishing and other cyber attacks as with the help of technology,
they implement anti phishing measures which helps them out in protecting identities of online
customers for protecting them against phishing attacks.
2. Ways or reasons of using social networking websites.
There are several reasons of using social networking websites by companies and users.
Some main reasons of companies of using social websites are: boosting sales, generating leads,
increasing website traffics etc. Business find easier in communicating with their clients with the
help of such types of social networking websites. According to the, Abroshan and et.al., (2017)
Users can also share any type of informations, their pictures and videos with others. By making
use of these sites they make themselves beneficial. But nowadays people have changed ways of
using these sites as they share all informations related to their daily lives and daily activities and
associated with Facebook, 2012).
Cyber attacks: Past, present and future
In the context of phishing which is a hacker' term it can be said that it originated from
fraudsters whom are “fishing” for confidential information in which attackers attack system of
users by sending fake links on E-mail. There are some common problems and challenges
associated with this attack include: Spear phishing, breach or access to personal and professional
data, smishing, vising and others.
Main target of phishing attack by attackers are innocent users who do not have
appropriate knowledge about operating system. By sending fake E mail and link to them, they
deceive them. Nowadays companies and people have become aware about security and for this
they have developed some programs which make people aware about security. Advancement of
technology has also reduced phishing and other cyber attacks as with the help of technology,
they implement anti phishing measures which helps them out in protecting identities of online
customers for protecting them against phishing attacks.
2. Ways or reasons of using social networking websites.
There are several reasons of using social networking websites by companies and users.
Some main reasons of companies of using social websites are: boosting sales, generating leads,
increasing website traffics etc. Business find easier in communicating with their clients with the
help of such types of social networking websites. According to the, Abroshan and et.al., (2017)
Users can also share any type of informations, their pictures and videos with others. By making
use of these sites they make themselves beneficial. But nowadays people have changed ways of
using these sites as they share all informations related to their daily lives and daily activities and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

also store personal as well as professional data. Due to lack of knowledge, employees cannot
distinguish between fake and original links which are being sent to them via E-mail.
This way of using social networking websites can create several problems and it is the
reason as why cyber crimes are increasing. Jensen and et.al., (2017) This is the main reasons as
why attackers hack system of users so, it can be said that by providing training to users and
employees this problem can be reduced. There are several reasons of phishing attacks like
ineffective use of tools to mitigate problems. So, one of the reason of identifying reasons and
ways of using social networking sites is to identify ways to solve them and prevent people
against this.
3. Ways to mitigate risks associated with social networking websites.
According to the Lin and Armstrong, (2019) training to users and workers about how to
use internet and how to distinguish fake and original link is one of the best ways of eliminating
phishing attacks. Fake links are similar to original links but there is a just change in few words
whose identification is not impossible. So, by making people aware and educated this risk can be
reduced.
It can also be said that by using effective and difficult password, making privacy on
setting and not to share all informations about daily activities, users can prevent themselves
against cyber crimes. In addition, (Ways to Stop Phishing Attacks, Joel Witts. 2020) stated that
email filtering is also an effective ways of preventing users against E mail phishing. E mail
gateway is being used to filter out all harmful and malicious emails and also quarantine them
automatically away from user inboxes. By making an effective use of the best E mail gateway
like Proof point, IRONSCALES, Menlo security users can block 99.99% of spam mails and can
also remove E mails which have malicious links. So, it can be said that E mail gateway is one of
the best ways of stopping and preventing users from getting or receiving fraudulent phishing
emails.
There are several ways of eliminating all these risks and preventing themselves against all these
cyber crimes such as:
Creating social media policy: Creating a social media policy should compulsory for companies
and require to follow some guidelines for preventing themselves against issues such as:
distinguish between fake and original links which are being sent to them via E-mail.
This way of using social networking websites can create several problems and it is the
reason as why cyber crimes are increasing. Jensen and et.al., (2017) This is the main reasons as
why attackers hack system of users so, it can be said that by providing training to users and
employees this problem can be reduced. There are several reasons of phishing attacks like
ineffective use of tools to mitigate problems. So, one of the reason of identifying reasons and
ways of using social networking sites is to identify ways to solve them and prevent people
against this.
3. Ways to mitigate risks associated with social networking websites.
According to the Lin and Armstrong, (2019) training to users and workers about how to
use internet and how to distinguish fake and original link is one of the best ways of eliminating
phishing attacks. Fake links are similar to original links but there is a just change in few words
whose identification is not impossible. So, by making people aware and educated this risk can be
reduced.
It can also be said that by using effective and difficult password, making privacy on
setting and not to share all informations about daily activities, users can prevent themselves
against cyber crimes. In addition, (Ways to Stop Phishing Attacks, Joel Witts. 2020) stated that
email filtering is also an effective ways of preventing users against E mail phishing. E mail
gateway is being used to filter out all harmful and malicious emails and also quarantine them
automatically away from user inboxes. By making an effective use of the best E mail gateway
like Proof point, IRONSCALES, Menlo security users can block 99.99% of spam mails and can
also remove E mails which have malicious links. So, it can be said that E mail gateway is one of
the best ways of stopping and preventing users from getting or receiving fraudulent phishing
emails.
There are several ways of eliminating all these risks and preventing themselves against all these
cyber crimes such as:
Creating social media policy: Creating a social media policy should compulsory for companies
and require to follow some guidelines for preventing themselves against issues such as:

Rules related to confidentiality and personal social media use.
Guidelines related to copyright.
Guidelines of creating authenticate password and changing that password in some
intervals.
Ways of identifying scams and solving them.
Limiting access: Limiting access to social accounts is one of the best way as there are several
people in an organization but it is not necessary for company to give access to all. By providing
access to only some people they can mitigate risks.
Research methodologies
Qualitative and quantitative are 2 research types which shows form in which researcher
collect informations whether in numerical and in non-numerical form. Gathering informations in
numerical form is known as quantitative research and non-numerical form of information is
known as qualitative research. For this study, scholar will collect numerical form or quantitative
research (Mengmeng, 2018). It will also make sue of some theories and data related to cyber
crimes associated with social websites. Inductive approach and deductive approach are other
important elements of research. Inductive approach is being used for collecting data and it is
related to generating a brand-new theory while deductive is related to testing of an existing
theory. For this study, scholar will focus on deductive approach because this study is
quantitative.
Data collection is one of the main elements of research methodology which allow
researcher to collect informations by making use of data collection sources. Primary and
secondary are 2 types of data collection. In primary data collection, researcher gathers new and
first-hand data and in secondary they collect second hand data which may be used before. For
this study researcher will make use of both data collection mainly focusing on primary data
collection (Dreyer, Macedo and Velentgas, 2019). Questionnaire, survey is some sources of
primary data collection and books and journals, articles are sources of secondary data.
Ethics, legal and security issues
It is important for researcher to conduct study in an ethical manner for solving ethical and legal
issues and prevent themselves against lawsuit. Companies have data of all age group, ethnicity
Guidelines related to copyright.
Guidelines of creating authenticate password and changing that password in some
intervals.
Ways of identifying scams and solving them.
Limiting access: Limiting access to social accounts is one of the best way as there are several
people in an organization but it is not necessary for company to give access to all. By providing
access to only some people they can mitigate risks.
Research methodologies
Qualitative and quantitative are 2 research types which shows form in which researcher
collect informations whether in numerical and in non-numerical form. Gathering informations in
numerical form is known as quantitative research and non-numerical form of information is
known as qualitative research. For this study, scholar will collect numerical form or quantitative
research (Mengmeng, 2018). It will also make sue of some theories and data related to cyber
crimes associated with social websites. Inductive approach and deductive approach are other
important elements of research. Inductive approach is being used for collecting data and it is
related to generating a brand-new theory while deductive is related to testing of an existing
theory. For this study, scholar will focus on deductive approach because this study is
quantitative.
Data collection is one of the main elements of research methodology which allow
researcher to collect informations by making use of data collection sources. Primary and
secondary are 2 types of data collection. In primary data collection, researcher gathers new and
first-hand data and in secondary they collect second hand data which may be used before. For
this study researcher will make use of both data collection mainly focusing on primary data
collection (Dreyer, Macedo and Velentgas, 2019). Questionnaire, survey is some sources of
primary data collection and books and journals, articles are sources of secondary data.
Ethics, legal and security issues
It is important for researcher to conduct study in an ethical manner for solving ethical and legal
issues and prevent themselves against lawsuit. Companies have data of all age group, ethnicity
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





