Comprehensive Security Assessment in Software Development Report
VerifiedAdded on 2023/01/19
|9
|2231
|42
Report
AI Summary
This report provides a comprehensive analysis of security assessment within software development, addressing crucial aspects of web infrastructure protection. It explores essential security measures, including network segmentation, data segregation, and hardening network devices to mitigate potential threats. The report also examines web application vulnerabilities, emphasizing the importance of proactive measures to prevent attacks such as SQL injection and cross-site scripting. Furthermore, it delves into the reasons behind web application attacks, highlighting the motivations of attackers and common vulnerabilities. The report discusses the significance of secure authentication, out-of-band management, and supply chain integrity. It emphasizes the need for continuous monitoring, patching, and employee training to enhance overall security posture. The report also includes references to various sources.

Running head: SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
Name of the Student:
Name of the University:
Author Note:
SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
ANSWER TO QUESTION 1:
Web infrastructure plays an important role for a company as it is the fundamental
communication media for an organization to transmit their services, data and applications.
Some security measures are to be taken to protect their web infrastructure. They are-
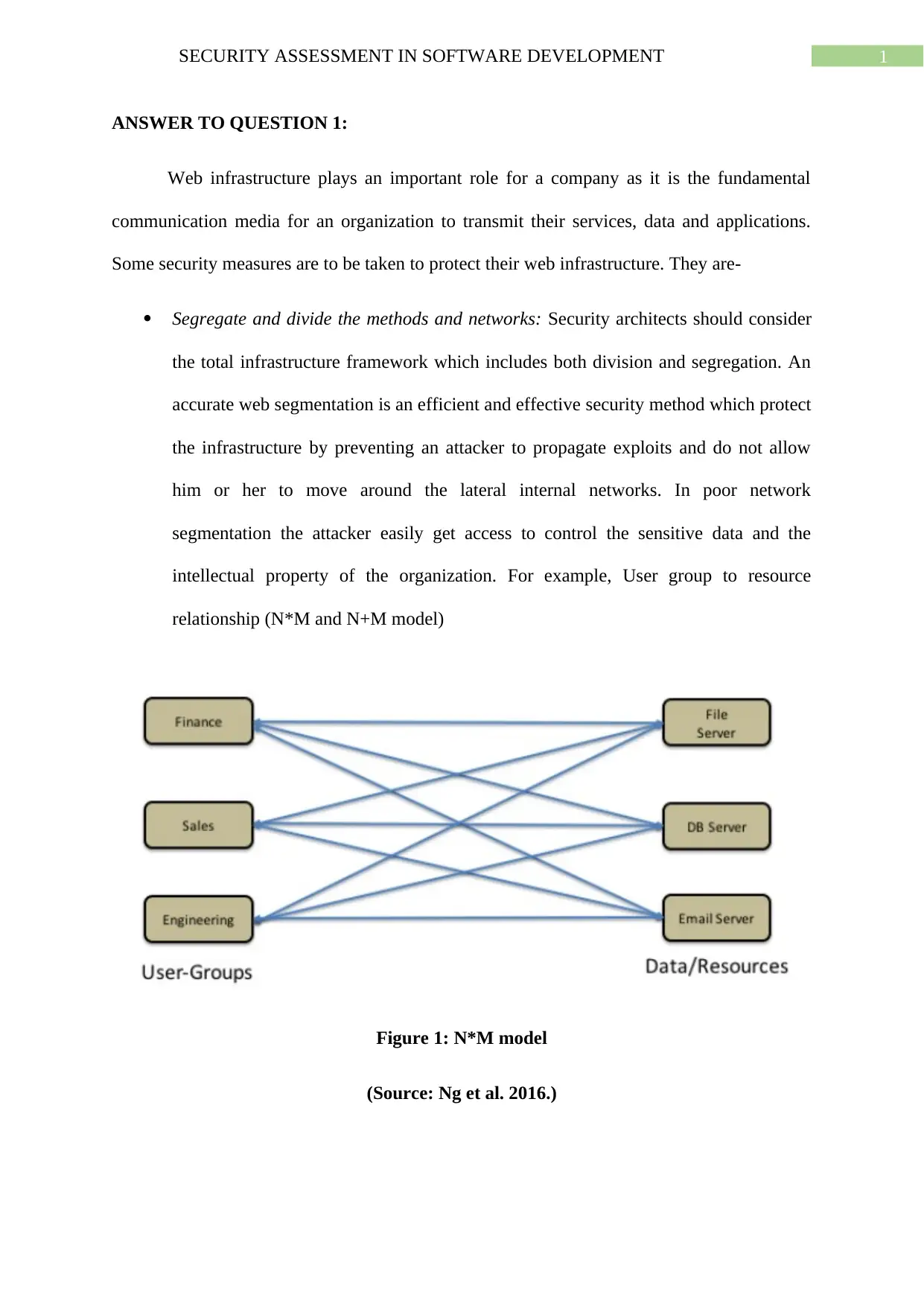
Segregate and divide the methods and networks: Security architects should consider
the total infrastructure framework which includes both division and segregation. An
accurate web segmentation is an efficient and effective security method which protect
the infrastructure by preventing an attacker to propagate exploits and do not allow
him or her to move around the lateral internal networks. In poor network
segmentation the attacker easily get access to control the sensitive data and the
intellectual property of the organization. For example, User group to resource
relationship (N*M and N+M model)
Figure 1: N*M model
(Source: Ng et al. 2016.)
ANSWER TO QUESTION 1:
Web infrastructure plays an important role for a company as it is the fundamental
communication media for an organization to transmit their services, data and applications.
Some security measures are to be taken to protect their web infrastructure. They are-
Segregate and divide the methods and networks: Security architects should consider
the total infrastructure framework which includes both division and segregation. An
accurate web segmentation is an efficient and effective security method which protect
the infrastructure by preventing an attacker to propagate exploits and do not allow
him or her to move around the lateral internal networks. In poor network
segmentation the attacker easily get access to control the sensitive data and the
intellectual property of the organization. For example, User group to resource
relationship (N*M and N+M model)
Figure 1: N*M model
(Source: Ng et al. 2016.)
2SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
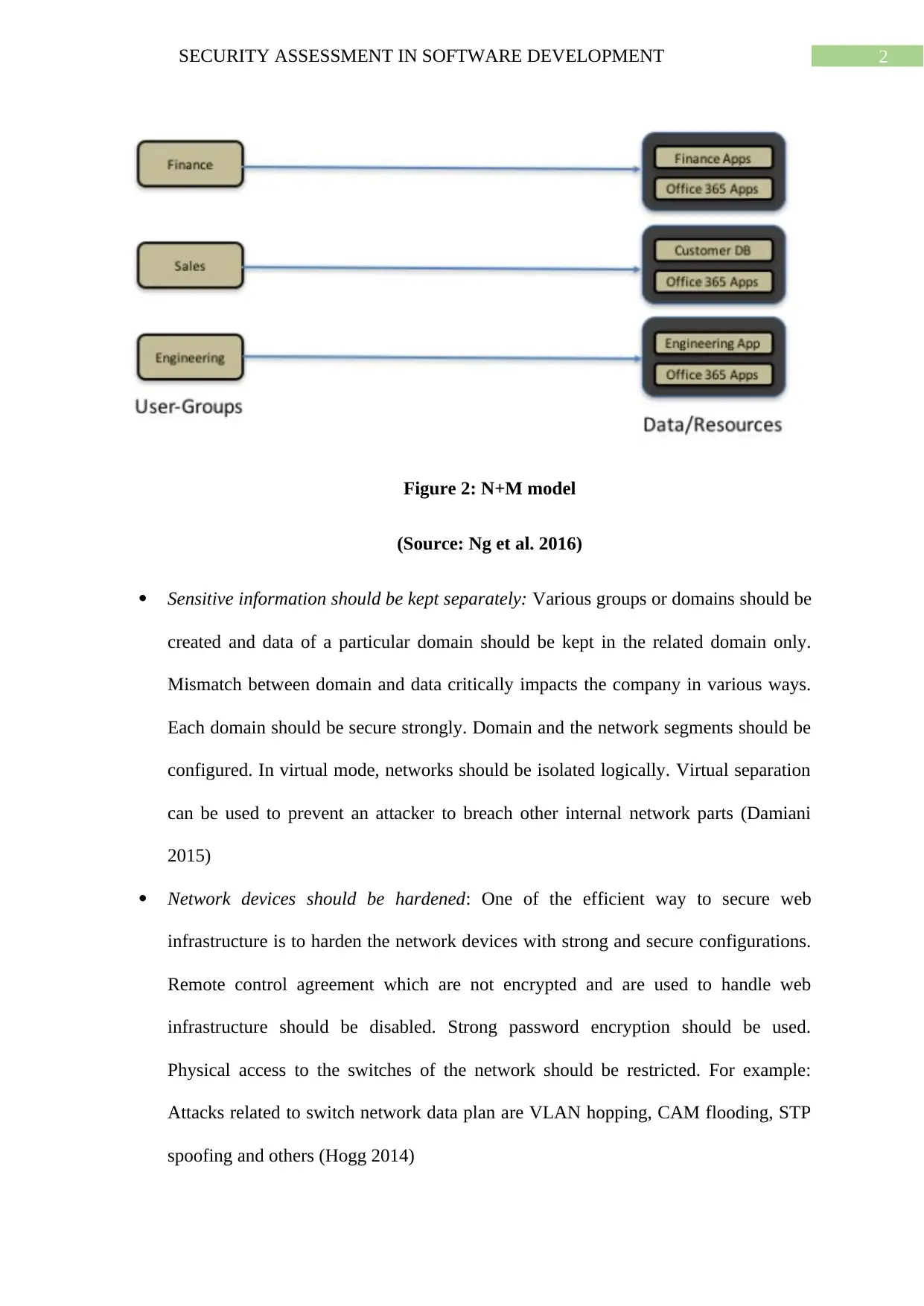
Figure 2: N+M model
(Source: Ng et al. 2016)
Sensitive information should be kept separately: Various groups or domains should be
created and data of a particular domain should be kept in the related domain only.
Mismatch between domain and data critically impacts the company in various ways.
Each domain should be secure strongly. Domain and the network segments should be
configured. In virtual mode, networks should be isolated logically. Virtual separation
can be used to prevent an attacker to breach other internal network parts (Damiani
2015)
Network devices should be hardened: One of the efficient way to secure web
infrastructure is to harden the network devices with strong and secure configurations.
Remote control agreement which are not encrypted and are used to handle web
infrastructure should be disabled. Strong password encryption should be used.
Physical access to the switches of the network should be restricted. For example:
Attacks related to switch network data plan are VLAN hopping, CAM flooding, STP
spoofing and others (Hogg 2014)
Figure 2: N+M model
(Source: Ng et al. 2016)
Sensitive information should be kept separately: Various groups or domains should be
created and data of a particular domain should be kept in the related domain only.
Mismatch between domain and data critically impacts the company in various ways.
Each domain should be secure strongly. Domain and the network segments should be
configured. In virtual mode, networks should be isolated logically. Virtual separation
can be used to prevent an attacker to breach other internal network parts (Damiani
2015)
Network devices should be hardened: One of the efficient way to secure web
infrastructure is to harden the network devices with strong and secure configurations.
Remote control agreement which are not encrypted and are used to handle web
infrastructure should be disabled. Strong password encryption should be used.
Physical access to the switches of the network should be restricted. For example:
Attacks related to switch network data plan are VLAN hopping, CAM flooding, STP
spoofing and others (Hogg 2014)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
Authentication of infrastructure devices should be secured: Administrative privileges
which are not authorized properly, granted widely and whose audit are not closed can
be easily attacked and this can be avoided by limiting the administrative privileges.
Utilizing of multifactor authentication will be a good idea to avoid such kind of
attacks (Domenech, Boukerche and Wangham 2016 ).
Execute Out-of-Band management: Out-of-Band (OoB) management utilizes a
substitute path for communication. OoB management helps web infrastructure to
strengthen the network by separating end user traffic delay from the management of
network traffic. The netwo9rk should ensure that the incoming network traffic is
coming only from OoB. All the channels of the management should be encrypted.
Apply different patches regularly.
Validation of integrity of software and hardware: Numerous media reports state that
many hardware and software are manufactured with the consent of the brand owner
but they are sold outside the brand owner’s approved channels. Grey markets have a
huge impact on the organization as they can introduce risk to the web infrastructure.
Breaches involved in the supply chain involve a risk of malicious software and
hardware which is to be installed in the web infrastructure device. This can be
maintained by- maintaining a strict control on the supply chain, serial numbers should
be validated from different sources, Monitor on log devices on a regular schedule and
perform some verification method like hash verification.
ANSWER TO QUESTION 2:
Websites and the web application should be available 24 hours of a day, and 7 days a
week to resume their services without any traffic or difficulty (Wakefield 2013). Application
vulnerability is a flaw or weakness in the application which can be exploited to exploit the
function of the app. Application vulnerability allow the attacker to get an open and public
Authentication of infrastructure devices should be secured: Administrative privileges
which are not authorized properly, granted widely and whose audit are not closed can
be easily attacked and this can be avoided by limiting the administrative privileges.
Utilizing of multifactor authentication will be a good idea to avoid such kind of
attacks (Domenech, Boukerche and Wangham 2016 ).
Execute Out-of-Band management: Out-of-Band (OoB) management utilizes a
substitute path for communication. OoB management helps web infrastructure to
strengthen the network by separating end user traffic delay from the management of
network traffic. The netwo9rk should ensure that the incoming network traffic is
coming only from OoB. All the channels of the management should be encrypted.
Apply different patches regularly.
Validation of integrity of software and hardware: Numerous media reports state that
many hardware and software are manufactured with the consent of the brand owner
but they are sold outside the brand owner’s approved channels. Grey markets have a
huge impact on the organization as they can introduce risk to the web infrastructure.
Breaches involved in the supply chain involve a risk of malicious software and
hardware which is to be installed in the web infrastructure device. This can be
maintained by- maintaining a strict control on the supply chain, serial numbers should
be validated from different sources, Monitor on log devices on a regular schedule and
perform some verification method like hash verification.
ANSWER TO QUESTION 2:
Websites and the web application should be available 24 hours of a day, and 7 days a
week to resume their services without any traffic or difficulty (Wakefield 2013). Application
vulnerability is a flaw or weakness in the application which can be exploited to exploit the
function of the app. Application vulnerability allow the attacker to get an open and public
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
access on the databases to steal the sensitive data of the organization which can profits the
attacker. Not only web application based organization but every organization should be
prepared about the possible attack the organization can face and they should also plan about
the possible counter measures for the respective vulnerable attack on the organization. The
organization mainly knows the major possible attack on their asset by an attacker. The
vulnerabilities that are overlooked by any organizations should be repaired quickly as fast as
possible. The further victim that can be affected from the attack should be kept isolated so
that it cannot attack the victim. All possible disaster recovery models should be kept ready for
the overlooked vulnerabilities. Data of an organization is the major key point for their
business, so it should be kept secure. Data should be back up and updated regularly, data
should be encrypted and tracked for the sake of data occurrence. Any unauthorized activity
seen in the web infrastructure should immediately be stopped by blocking the network.
Application vulnerabilities are often predictable and should not be overlooked by any
organization as it impacts a lot on the organization business. There are different application
based attacks like SQL injecting, LDAP injection, Cross Site Request Forgery and
Cryptographic storage attack and many more. The mentioned attacks can be mitigated by
some countermeasures (Stolfo, Salem and Hershkop 2014). Certain technical techniques
should be implemented to avoid being exploited by the web application attacks. Most of the
websites are hackable, so there should be a proper schedule plan of handling some web based
attacks. Organization website should verify all new signing customers as this can mitigate the
phishing attack. All terms and conditions should be read carefully before signing or login in
any unauthorized website (Lupton 2014). The logs of system and application should be
studied properly for the predictable and overlooked attack by the organization. Pages should
be traced because it will help to expose any cross site scripting attack, allow to debug the
page and guarantees that no further cross site scripting will be present in the pages. An event
access on the databases to steal the sensitive data of the organization which can profits the
attacker. Not only web application based organization but every organization should be
prepared about the possible attack the organization can face and they should also plan about
the possible counter measures for the respective vulnerable attack on the organization. The
organization mainly knows the major possible attack on their asset by an attacker. The
vulnerabilities that are overlooked by any organizations should be repaired quickly as fast as
possible. The further victim that can be affected from the attack should be kept isolated so
that it cannot attack the victim. All possible disaster recovery models should be kept ready for
the overlooked vulnerabilities. Data of an organization is the major key point for their
business, so it should be kept secure. Data should be back up and updated regularly, data
should be encrypted and tracked for the sake of data occurrence. Any unauthorized activity
seen in the web infrastructure should immediately be stopped by blocking the network.
Application vulnerabilities are often predictable and should not be overlooked by any
organization as it impacts a lot on the organization business. There are different application
based attacks like SQL injecting, LDAP injection, Cross Site Request Forgery and
Cryptographic storage attack and many more. The mentioned attacks can be mitigated by
some countermeasures (Stolfo, Salem and Hershkop 2014). Certain technical techniques
should be implemented to avoid being exploited by the web application attacks. Most of the
websites are hackable, so there should be a proper schedule plan of handling some web based
attacks. Organization website should verify all new signing customers as this can mitigate the
phishing attack. All terms and conditions should be read carefully before signing or login in
any unauthorized website (Lupton 2014). The logs of system and application should be
studied properly for the predictable and overlooked attack by the organization. Pages should
be traced because it will help to expose any cross site scripting attack, allow to debug the
page and guarantees that no further cross site scripting will be present in the pages. An event

5SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
monitoring and detecting mechanism should be established by every organization to fight
against the overlooked vulnerable attack. Training related to awareness of any type of attacks
should be held for all the staffs of the organization. Third party person, software and
hardware should be critically minimized. The above discussed opinions are made with
respect to the web based vulnerable attack that are overlooked by the organizations.
ANSWER TO QUESTION 3:
Web applications are attacked due to various reasons. Some of them are- to steal personal
data, customer databases, intellectual property, IT infrastructure, IT services and many more
(Hruza 2014). The main motive of web applications attack is then financial gain of the
attacker. Malicious hackers always usually look for government agencies, business and
individuals. They have many different methods to heavily attack the victim but they usually
choose that mode of attack which require less effort and has huge damage effect. According
to SANS institute, among all the cyber-attack 60% of the target are the web applications
(Awoleye, Ojuloge and Ilori 2014). Attacker mostly choose web application for any cyber-
attack because of the following reasons:
They are easier to reach: Websites and the web application are the only front end for
an organization. With respect to other targets of web attack, web applications are
easier to reach and do not require any different connection or state-sponsored
resource. They can easily be accessed with a computer and an internet connection. In
most of the cases, if a website is breached then it further serves as a beachhead for
other cyber-attacks which allow the attacker to move around the internal network and
get access to all critical sets of information like databases, decryption keys and others.
Number of beginners is huge who are writing the application codes of the web
application: Languages basically used for web programming are C, C++, Java,
monitoring and detecting mechanism should be established by every organization to fight
against the overlooked vulnerable attack. Training related to awareness of any type of attacks
should be held for all the staffs of the organization. Third party person, software and
hardware should be critically minimized. The above discussed opinions are made with
respect to the web based vulnerable attack that are overlooked by the organizations.
ANSWER TO QUESTION 3:
Web applications are attacked due to various reasons. Some of them are- to steal personal
data, customer databases, intellectual property, IT infrastructure, IT services and many more
(Hruza 2014). The main motive of web applications attack is then financial gain of the
attacker. Malicious hackers always usually look for government agencies, business and
individuals. They have many different methods to heavily attack the victim but they usually
choose that mode of attack which require less effort and has huge damage effect. According
to SANS institute, among all the cyber-attack 60% of the target are the web applications
(Awoleye, Ojuloge and Ilori 2014). Attacker mostly choose web application for any cyber-
attack because of the following reasons:
They are easier to reach: Websites and the web application are the only front end for
an organization. With respect to other targets of web attack, web applications are
easier to reach and do not require any different connection or state-sponsored
resource. They can easily be accessed with a computer and an internet connection. In
most of the cases, if a website is breached then it further serves as a beachhead for
other cyber-attacks which allow the attacker to move around the internal network and
get access to all critical sets of information like databases, decryption keys and others.
Number of beginners is huge who are writing the application codes of the web
application: Languages basically used for web programming are C, C++, Java,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
JavaScript, PHP which are used by novice developers. The developer should
specifically declare the code which satisfies the owner’s demand. Due to the huge
figure of the beginner developer they cannot meet the owner’s demand (Swain et al.
2015). Every company which contains a huge confidential data should hire
professional developers as well as well quality IT staff who have the capability to
recover the organization loss from any type of attacks. Websites that are custom made
can be easily hacked by the user.
Packages of the third party failed to update: Most of the web applications depend
mainly on the source code of the third party. This trend is especially growing as the
programming is API based (Ong et al. 2015). Many websites failed to apply required
patches and also the updates because the websites basically don’t know about the
third component which are successfully running in their respective website.
Web application targets huge audience: Once the website is breached the attacker not
only gains the access of the website resources but he or she also gains the access of
the user’s resources like their personal identity, their intellectual property and many
more (Gans 2016). The attacker spread the malware attack by compromising the
websites. Therefore, by breaching a website the attacker gains the access millions and
billions of user who are not secure, the network security agreement is not followed by
them which can become an easy task to attack for an attacker.
JavaScript, PHP which are used by novice developers. The developer should
specifically declare the code which satisfies the owner’s demand. Due to the huge
figure of the beginner developer they cannot meet the owner’s demand (Swain et al.
2015). Every company which contains a huge confidential data should hire
professional developers as well as well quality IT staff who have the capability to
recover the organization loss from any type of attacks. Websites that are custom made
can be easily hacked by the user.
Packages of the third party failed to update: Most of the web applications depend
mainly on the source code of the third party. This trend is especially growing as the
programming is API based (Ong et al. 2015). Many websites failed to apply required
patches and also the updates because the websites basically don’t know about the
third component which are successfully running in their respective website.
Web application targets huge audience: Once the website is breached the attacker not
only gains the access of the website resources but he or she also gains the access of
the user’s resources like their personal identity, their intellectual property and many
more (Gans 2016). The attacker spread the malware attack by compromising the
websites. Therefore, by breaching a website the attacker gains the access millions and
billions of user who are not secure, the network security agreement is not followed by
them which can become an easy task to attack for an attacker.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
References:
Awoleye, O.M., Ojuloge, B. and Ilori, M.O., 2014. Web application vulnerability assessment
and policy direction towards a secure smart government. Government Information
Quarterly, 31, pp.S118-S125.
Damiani, E., 2015, October. Toward big data risk analysis. In 2015 IEEE International
Conference on Big Data (Big Data) (pp. 1905-1909). IEEE.
Domenech, M.C., Boukerche, A. and Wangham, M.S., 2016, November. An authentication
and authorization infrastructure for the web of things. In Proceedings of the 12th ACM
Symposium on QoS and Security for Wireless and Mobile Networks (pp. 39-46). ACM.
Gans, H.J., 2016. Public sociology and its publics. The American Sociologist, 47(1), pp.3-11.
Hogg, S., 2014. Sdn security attack vectors and sdn hardening. Artikkeli Network.
Hruza, P., Sousek, R. and Szabo, S., 2014. Cyber-attacks and attack protection.
Lupton, D., 2014. The commodification of patient opinion: the digital patient experience
economy in the age of big data. Sociology of health & illness, 36(6), pp.856-869.
Ng, K.K., Lo, J.C., Lim, J.K., Chee, M.W. and Zhou, J., 2016. Reduced functional
segregation between the default mode network and the executive control network in healthy
older adults: a longitudinal study. Neuroimage, 133, pp.321-330.
Ong, S.P., Cholia, S., Jain, A., Brafman, M., Gunter, D., Ceder, G. and Persson, K.A., 2015.
The Materials Application Programming Interface (API): A simple, flexible and efficient API
for materials data based on REpresentational State Transfer (REST) principles.
Computational Materials Science, 97, pp.209-215.
References:
Awoleye, O.M., Ojuloge, B. and Ilori, M.O., 2014. Web application vulnerability assessment
and policy direction towards a secure smart government. Government Information
Quarterly, 31, pp.S118-S125.
Damiani, E., 2015, October. Toward big data risk analysis. In 2015 IEEE International
Conference on Big Data (Big Data) (pp. 1905-1909). IEEE.
Domenech, M.C., Boukerche, A. and Wangham, M.S., 2016, November. An authentication
and authorization infrastructure for the web of things. In Proceedings of the 12th ACM
Symposium on QoS and Security for Wireless and Mobile Networks (pp. 39-46). ACM.
Gans, H.J., 2016. Public sociology and its publics. The American Sociologist, 47(1), pp.3-11.
Hogg, S., 2014. Sdn security attack vectors and sdn hardening. Artikkeli Network.
Hruza, P., Sousek, R. and Szabo, S., 2014. Cyber-attacks and attack protection.
Lupton, D., 2014. The commodification of patient opinion: the digital patient experience
economy in the age of big data. Sociology of health & illness, 36(6), pp.856-869.
Ng, K.K., Lo, J.C., Lim, J.K., Chee, M.W. and Zhou, J., 2016. Reduced functional
segregation between the default mode network and the executive control network in healthy
older adults: a longitudinal study. Neuroimage, 133, pp.321-330.
Ong, S.P., Cholia, S., Jain, A., Brafman, M., Gunter, D., Ceder, G. and Persson, K.A., 2015.
The Materials Application Programming Interface (API): A simple, flexible and efficient API
for materials data based on REpresentational State Transfer (REST) principles.
Computational Materials Science, 97, pp.209-215.

8SECURITY ASSESSMENT IN SOFTWARE DEVELOPMENT
Stolfo, S.J., Salem, M.B. and Hershkop, S., Columbia University of New York,
2014. Methods, systems, and media for masquerade attack detection by monitoring computer
user behavior. U.S. Patent 8,769,684.
Swain, N.R., Latu, K., Christensen, S.D., Jones, N.L., Nelson, E.J., Ames, D.P. and Williams,
G.P., 2015. A review of open source software solutions for developing water resources web
applications. Environmental Modelling & Software, 67, pp.108-117.
Wakefield, R., 2013. The influence of user affect in online information disclosure. The
Journal of Strategic Information Systems, 22(2), pp.157-174.
Stolfo, S.J., Salem, M.B. and Hershkop, S., Columbia University of New York,
2014. Methods, systems, and media for masquerade attack detection by monitoring computer
user behavior. U.S. Patent 8,769,684.
Swain, N.R., Latu, K., Christensen, S.D., Jones, N.L., Nelson, E.J., Ames, D.P. and Williams,
G.P., 2015. A review of open source software solutions for developing water resources web
applications. Environmental Modelling & Software, 67, pp.108-117.
Wakefield, R., 2013. The influence of user affect in online information disclosure. The
Journal of Strategic Information Systems, 22(2), pp.157-174.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





