Software Engineering Report: System Design, Testing, and Validation
VerifiedAdded on 2023/02/01
|11
|1598
|80
Report
AI Summary
This software engineering report provides a detailed analysis of a supermarket system, likely for Coles, covering both functional and non-functional requirements. It outlines the system's features, such as customer registration, Flybuys card integration, and the calculation of customer spending. The report includes a context diagram, Level 1 and Level 2 Data Flow Diagrams (DFD), and a data dictionary to illustrate the system's architecture and data flow. A Gantt chart is also included, detailing the project timeline and tasks involved in system development, from initiation to closure. Furthermore, the report discusses requirement verification and validation techniques, focusing on static and dynamic techniques to ensure the accuracy and reliability of the software. Static techniques emphasize model design and source code accuracy, while dynamic techniques involve model execution and testing. The report concludes by highlighting the importance of these techniques in the software development lifecycle, demonstrating a comprehensive approach to software engineering principles.

Running head: SOFTWARE ENGINEERING
Software Engineering
Name of Student-
Name of University-
Author’s Note-
Software Engineering
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SOFTWARE ENGINEERING
1. Functional Requirements
The functional requirements related with the supermarket Coles are discussed below:
The system of Coles will take the name, address and telephone number of the customer.
The system will register the custom by providing them with a Flybuys card having the unique
customer identification number [7].
The system will records the CIN number at the time of checkout and when the CIN number is
scanned the total value of purchase is also scanned for evaluating.
The system calculates highest three value purchasing customer at the end of the year.
The system also shows all the customer who has spent an amount of more than $1000 over the
year to reward them with gold coins.
2. Non-Functional Requirements
The non-functional requirements related with the supermarket Coles are discussed below:
The system will have a good interface where the name, address, and telephone number is to be
entered for registration.
The system will have a good performance that will support wide number of concurrent users at
a time.
The scanning of the CIN number should also support concurrent users [5].
The system should be secured as it contains the personal details of all the customer of Coles.
The system will be available all 24/7 and there will be maintenance on the very first day of the
year when the supermarket is closed.
1. Functional Requirements
The functional requirements related with the supermarket Coles are discussed below:
The system of Coles will take the name, address and telephone number of the customer.
The system will register the custom by providing them with a Flybuys card having the unique
customer identification number [7].
The system will records the CIN number at the time of checkout and when the CIN number is
scanned the total value of purchase is also scanned for evaluating.
The system calculates highest three value purchasing customer at the end of the year.
The system also shows all the customer who has spent an amount of more than $1000 over the
year to reward them with gold coins.
2. Non-Functional Requirements
The non-functional requirements related with the supermarket Coles are discussed below:
The system will have a good interface where the name, address, and telephone number is to be
entered for registration.
The system will have a good performance that will support wide number of concurrent users at
a time.
The scanning of the CIN number should also support concurrent users [5].
The system should be secured as it contains the personal details of all the customer of Coles.
The system will be available all 24/7 and there will be maintenance on the very first day of the
year when the supermarket is closed.
2SOFTWARE ENGINEERING
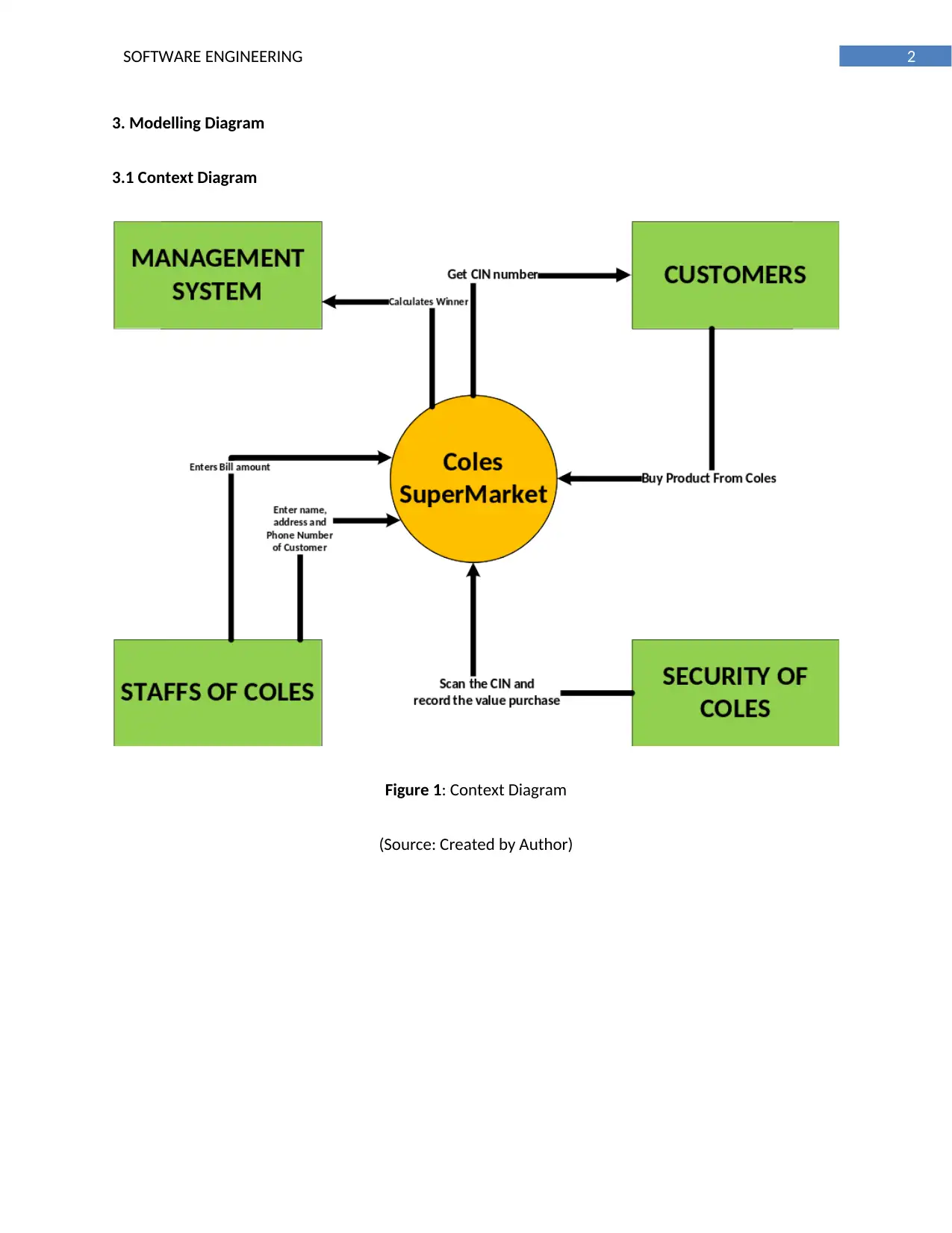
3. Modelling Diagram
3.1 Context Diagram
Figure 1: Context Diagram
(Source: Created by Author)
3. Modelling Diagram
3.1 Context Diagram
Figure 1: Context Diagram
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3SOFTWARE ENGINEERING
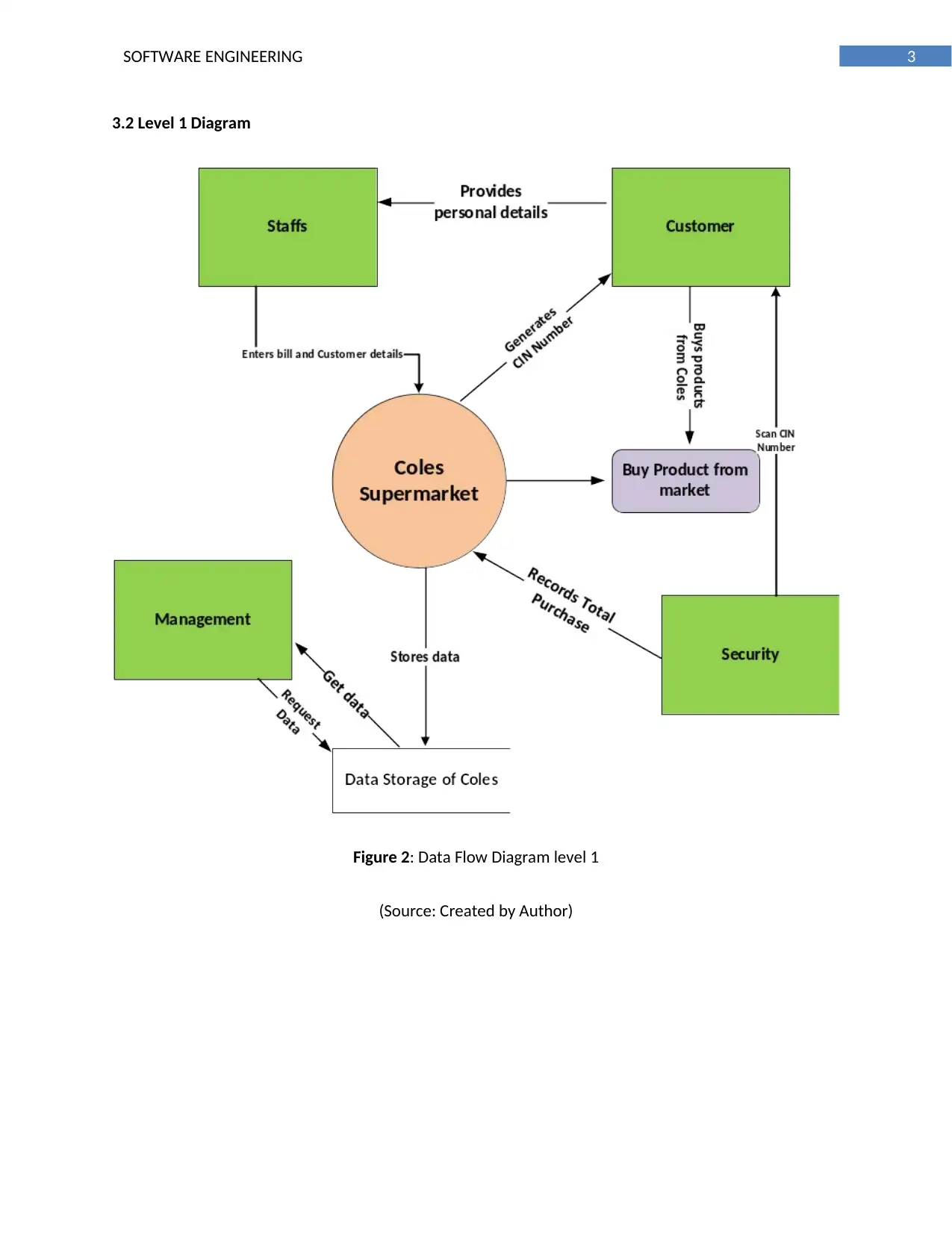
3.2 Level 1 Diagram
Figure 2: Data Flow Diagram level 1
(Source: Created by Author)
3.2 Level 1 Diagram
Figure 2: Data Flow Diagram level 1
(Source: Created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SOFTWARE ENGINEERING
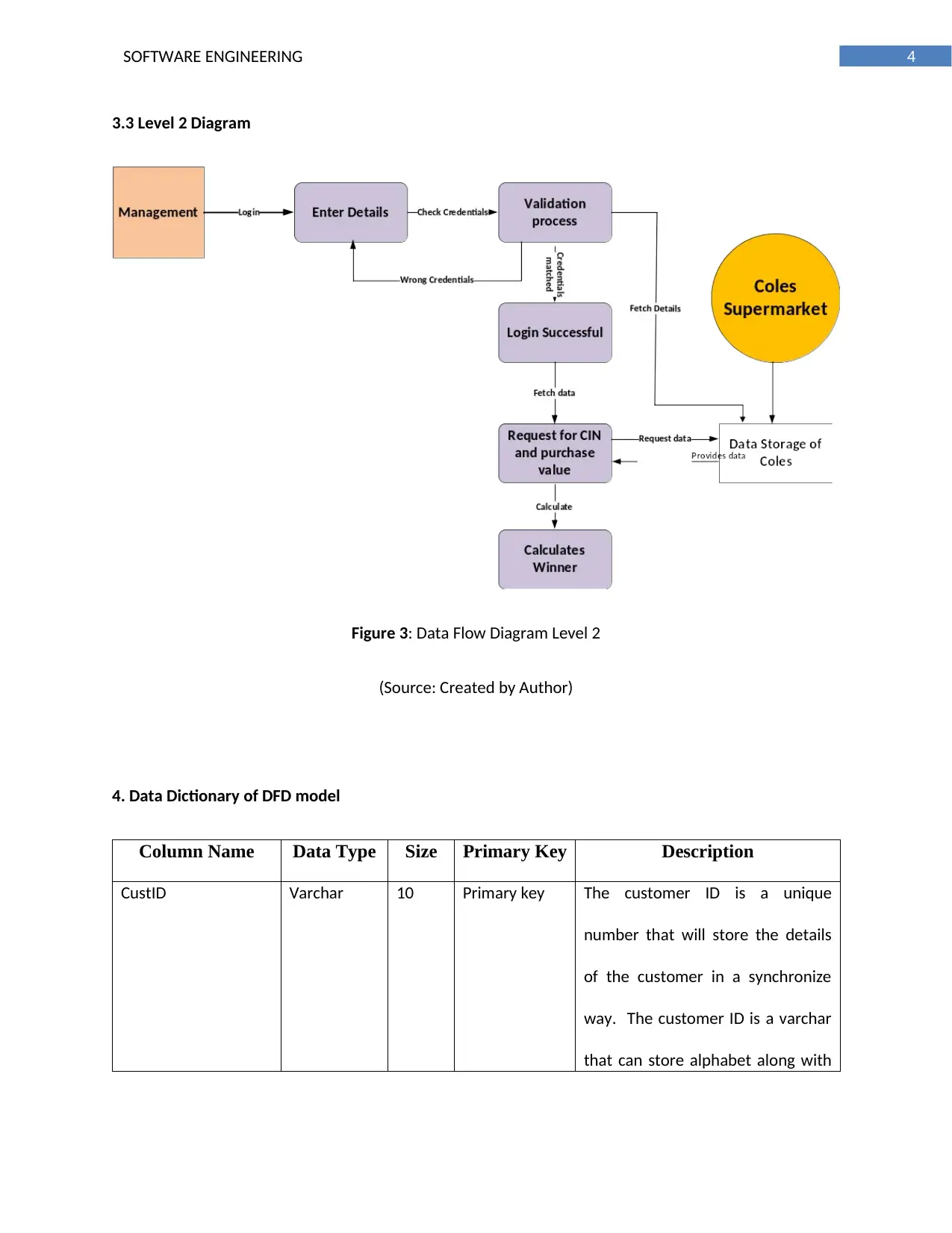
3.3 Level 2 Diagram
Figure 3: Data Flow Diagram Level 2
(Source: Created by Author)
4. Data Dictionary of DFD model
Column Name Data Type Size Primary Key Description
CustID Varchar 10 Primary key The customer ID is a unique
number that will store the details
of the customer in a synchronize
way. The customer ID is a varchar
that can store alphabet along with
3.3 Level 2 Diagram
Figure 3: Data Flow Diagram Level 2
(Source: Created by Author)
4. Data Dictionary of DFD model
Column Name Data Type Size Primary Key Description
CustID Varchar 10 Primary key The customer ID is a unique
number that will store the details
of the customer in a synchronize
way. The customer ID is a varchar
that can store alphabet along with
5SOFTWARE ENGINEERING
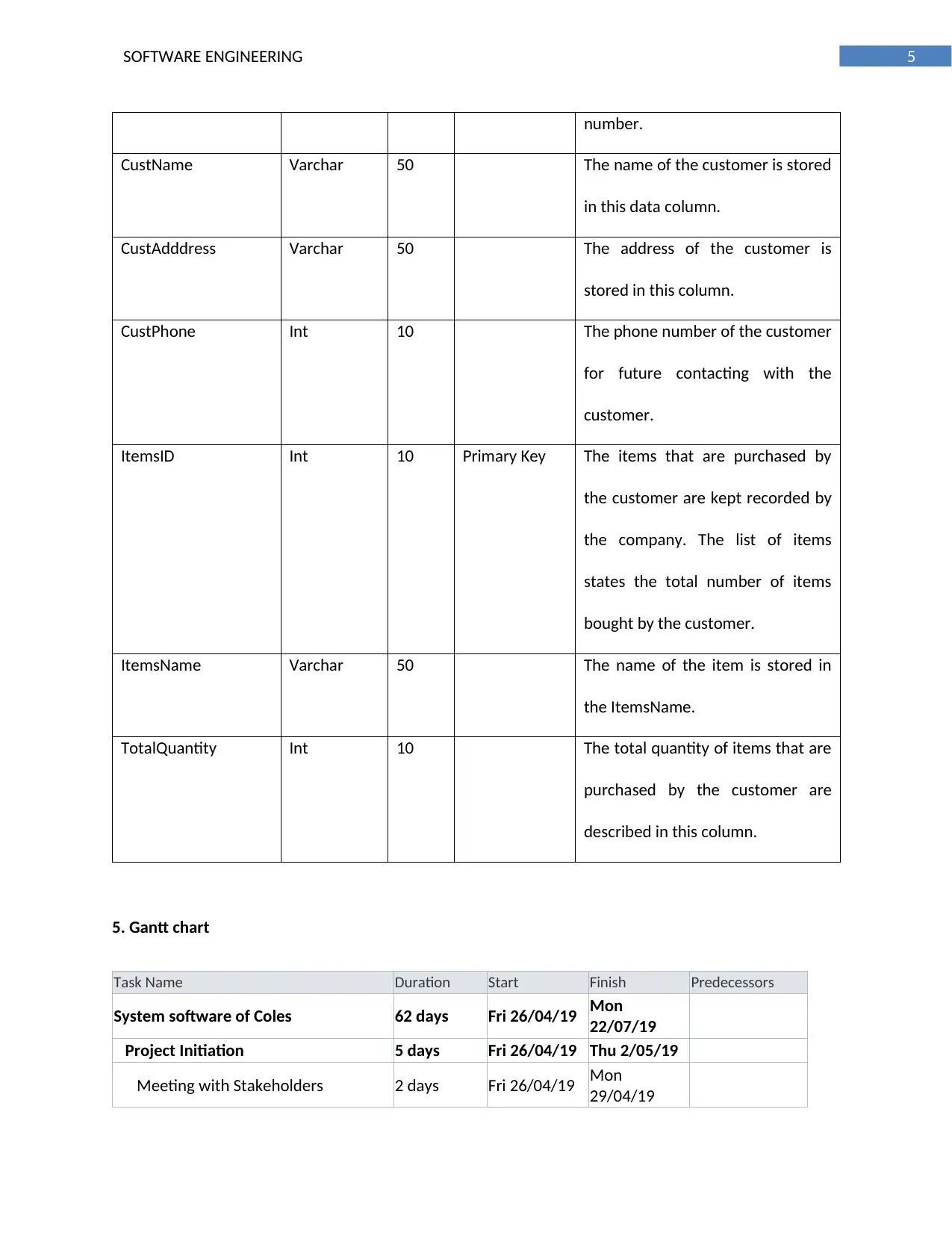
number.
CustName Varchar 50 The name of the customer is stored
in this data column.
CustAdddress Varchar 50 The address of the customer is
stored in this column.
CustPhone Int 10 The phone number of the customer
for future contacting with the
customer.
ItemsID Int 10 Primary Key The items that are purchased by
the customer are kept recorded by
the company. The list of items
states the total number of items
bought by the customer.
ItemsName Varchar 50 The name of the item is stored in
the ItemsName.
TotalQuantity Int 10 The total quantity of items that are
purchased by the customer are
described in this column.
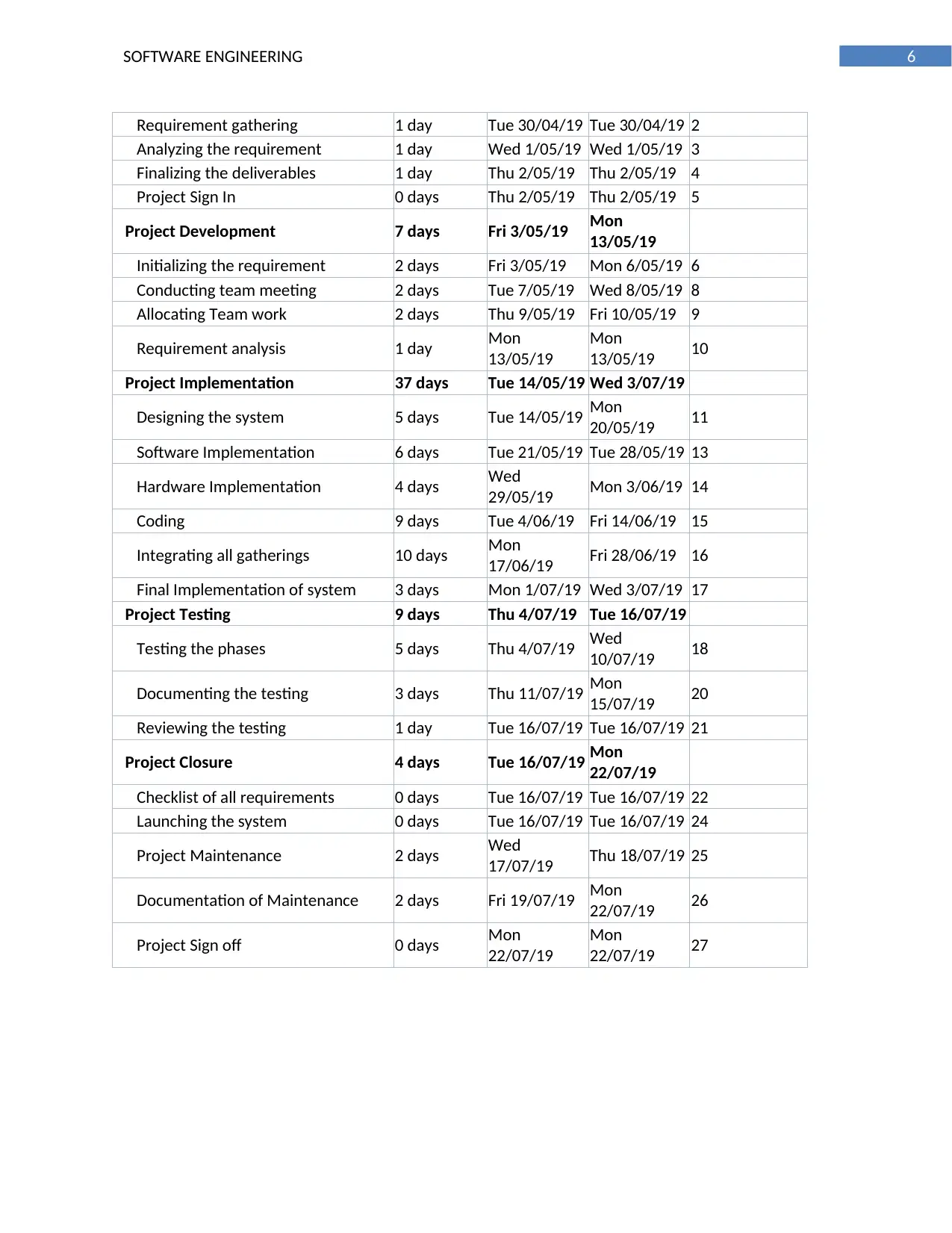
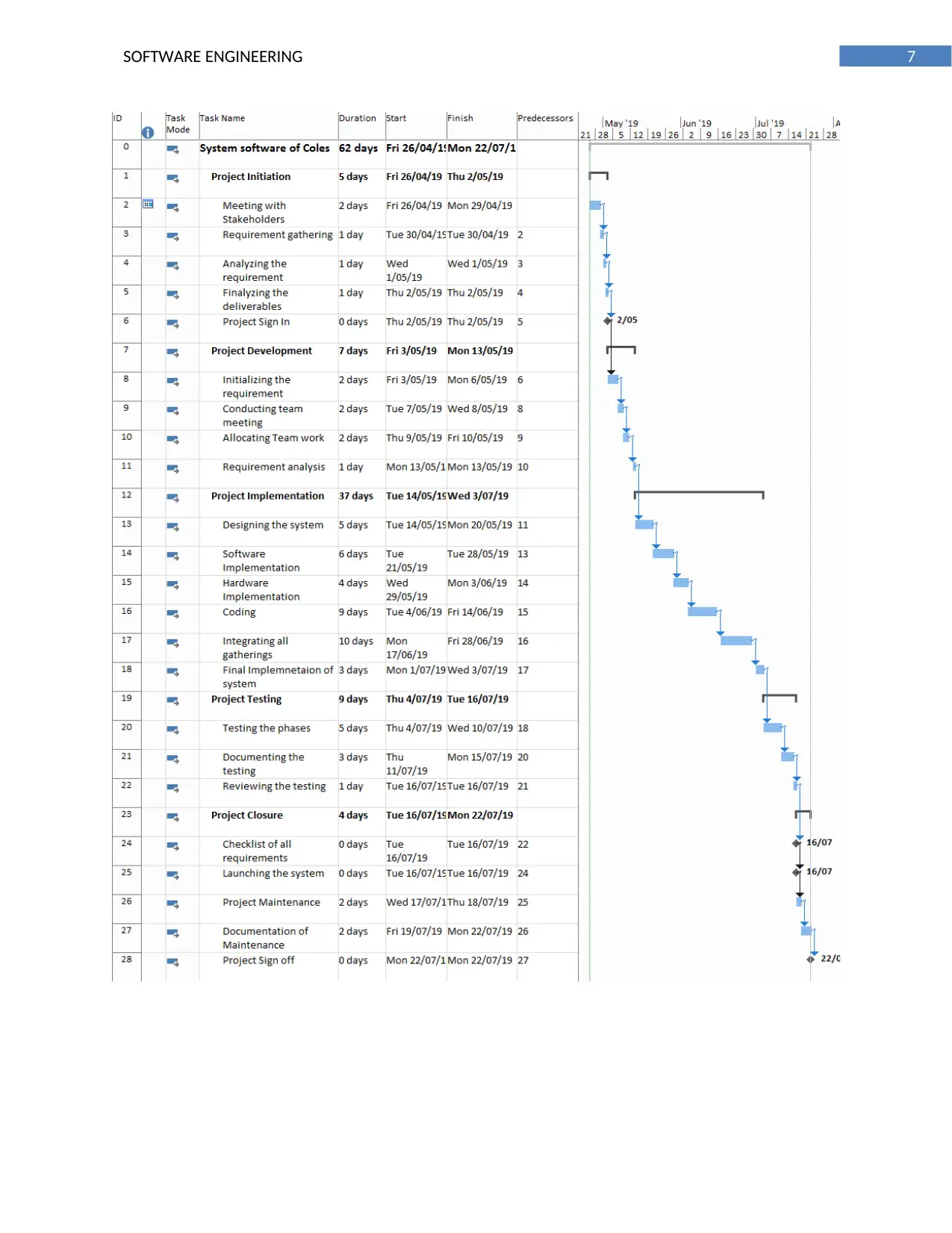
5. Gantt chart
Task Name Duration Start Finish Predecessors
System software of Coles 62 days Fri 26/04/19 Mon
22/07/19
Project Initiation 5 days Fri 26/04/19 Thu 2/05/19
Meeting with Stakeholders 2 days Fri 26/04/19 Mon
29/04/19
number.
CustName Varchar 50 The name of the customer is stored
in this data column.
CustAdddress Varchar 50 The address of the customer is
stored in this column.
CustPhone Int 10 The phone number of the customer
for future contacting with the
customer.
ItemsID Int 10 Primary Key The items that are purchased by
the customer are kept recorded by
the company. The list of items
states the total number of items
bought by the customer.
ItemsName Varchar 50 The name of the item is stored in
the ItemsName.
TotalQuantity Int 10 The total quantity of items that are
purchased by the customer are
described in this column.
5. Gantt chart
Task Name Duration Start Finish Predecessors
System software of Coles 62 days Fri 26/04/19 Mon
22/07/19
Project Initiation 5 days Fri 26/04/19 Thu 2/05/19
Meeting with Stakeholders 2 days Fri 26/04/19 Mon
29/04/19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SOFTWARE ENGINEERING
Requirement gathering 1 day Tue 30/04/19 Tue 30/04/19 2
Analyzing the requirement 1 day Wed 1/05/19 Wed 1/05/19 3
Finalizing the deliverables 1 day Thu 2/05/19 Thu 2/05/19 4
Project Sign In 0 days Thu 2/05/19 Thu 2/05/19 5
Project Development 7 days Fri 3/05/19 Mon
13/05/19
Initializing the requirement 2 days Fri 3/05/19 Mon 6/05/19 6
Conducting team meeting 2 days Tue 7/05/19 Wed 8/05/19 8
Allocating Team work 2 days Thu 9/05/19 Fri 10/05/19 9
Requirement analysis 1 day Mon
13/05/19
Mon
13/05/19 10
Project Implementation 37 days Tue 14/05/19 Wed 3/07/19
Designing the system 5 days Tue 14/05/19 Mon
20/05/19 11
Software Implementation 6 days Tue 21/05/19 Tue 28/05/19 13
Hardware Implementation 4 days Wed
29/05/19 Mon 3/06/19 14
Coding 9 days Tue 4/06/19 Fri 14/06/19 15
Integrating all gatherings 10 days Mon
17/06/19 Fri 28/06/19 16
Final Implementation of system 3 days Mon 1/07/19 Wed 3/07/19 17
Project Testing 9 days Thu 4/07/19 Tue 16/07/19
Testing the phases 5 days Thu 4/07/19 Wed
10/07/19 18
Documenting the testing 3 days Thu 11/07/19 Mon
15/07/19 20
Reviewing the testing 1 day Tue 16/07/19 Tue 16/07/19 21
Project Closure 4 days Tue 16/07/19 Mon
22/07/19
Checklist of all requirements 0 days Tue 16/07/19 Tue 16/07/19 22
Launching the system 0 days Tue 16/07/19 Tue 16/07/19 24
Project Maintenance 2 days Wed
17/07/19 Thu 18/07/19 25
Documentation of Maintenance 2 days Fri 19/07/19 Mon
22/07/19 26
Project Sign off 0 days Mon
22/07/19
Mon
22/07/19 27
Requirement gathering 1 day Tue 30/04/19 Tue 30/04/19 2
Analyzing the requirement 1 day Wed 1/05/19 Wed 1/05/19 3
Finalizing the deliverables 1 day Thu 2/05/19 Thu 2/05/19 4
Project Sign In 0 days Thu 2/05/19 Thu 2/05/19 5
Project Development 7 days Fri 3/05/19 Mon
13/05/19
Initializing the requirement 2 days Fri 3/05/19 Mon 6/05/19 6
Conducting team meeting 2 days Tue 7/05/19 Wed 8/05/19 8
Allocating Team work 2 days Thu 9/05/19 Fri 10/05/19 9
Requirement analysis 1 day Mon
13/05/19
Mon
13/05/19 10
Project Implementation 37 days Tue 14/05/19 Wed 3/07/19
Designing the system 5 days Tue 14/05/19 Mon
20/05/19 11
Software Implementation 6 days Tue 21/05/19 Tue 28/05/19 13
Hardware Implementation 4 days Wed
29/05/19 Mon 3/06/19 14
Coding 9 days Tue 4/06/19 Fri 14/06/19 15
Integrating all gatherings 10 days Mon
17/06/19 Fri 28/06/19 16
Final Implementation of system 3 days Mon 1/07/19 Wed 3/07/19 17
Project Testing 9 days Thu 4/07/19 Tue 16/07/19
Testing the phases 5 days Thu 4/07/19 Wed
10/07/19 18
Documenting the testing 3 days Thu 11/07/19 Mon
15/07/19 20
Reviewing the testing 1 day Tue 16/07/19 Tue 16/07/19 21
Project Closure 4 days Tue 16/07/19 Mon
22/07/19
Checklist of all requirements 0 days Tue 16/07/19 Tue 16/07/19 22
Launching the system 0 days Tue 16/07/19 Tue 16/07/19 24
Project Maintenance 2 days Wed
17/07/19 Thu 18/07/19 25
Documentation of Maintenance 2 days Fri 19/07/19 Mon
22/07/19 26
Project Sign off 0 days Mon
22/07/19
Mon
22/07/19 27
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SOFTWARE ENGINEERING

8SOFTWARE ENGINEERING
6. Requirement verification and validation technique
The requirement verification as well as validation technique that are basically used while
developing a software is informal technique, Static Technique, dynamic technique, and formal technique
[2]. From the above mentioned techniques, the most suitable techniques that can be used for
developing the application of Coles are: Static Technique and dynamic technique. Both the techniques
are explained below:
Static Verification and validation technique: This particular verification and validation technique
helps to access the accuracy of the model design as well as the source code that is used for developing
the application [5]. The static techniques are mainly used for developing the application and does not
require many machine execution for that particular model. The static technique mainly uses mental
execution for carrying out this technique [1]. This particular technique is a popular technique and is
widely used. This technique has many automated tools that helps to enhance the process of verification
and validation. The static technique helps to reveal different types of information included in the model
structure and technique that are used and the data flow and the data control that comes within this
particular model.
The models that are used in static verification and validation technique are cause effect
graphing, control analysis consisting of calling structure, concurrent process, the control flow and the
state transition [8]. In static Verification and validation, data analysis is done and the data dependency is
also followed. There can be fault and failure analysis in static verification and validation technique along
with model interface and the user interface [6]. The Static V & V technique follows the semantic analysis
and the structural analysis along with symbolic evaluation and syntax analysis.
Dynamic Verification and validation technique: This particular model requires a model
execution. They helps in evaluating the model that are based on the execution behavior [4]. Most of the
6. Requirement verification and validation technique
The requirement verification as well as validation technique that are basically used while
developing a software is informal technique, Static Technique, dynamic technique, and formal technique
[2]. From the above mentioned techniques, the most suitable techniques that can be used for
developing the application of Coles are: Static Technique and dynamic technique. Both the techniques
are explained below:
Static Verification and validation technique: This particular verification and validation technique
helps to access the accuracy of the model design as well as the source code that is used for developing
the application [5]. The static techniques are mainly used for developing the application and does not
require many machine execution for that particular model. The static technique mainly uses mental
execution for carrying out this technique [1]. This particular technique is a popular technique and is
widely used. This technique has many automated tools that helps to enhance the process of verification
and validation. The static technique helps to reveal different types of information included in the model
structure and technique that are used and the data flow and the data control that comes within this
particular model.
The models that are used in static verification and validation technique are cause effect
graphing, control analysis consisting of calling structure, concurrent process, the control flow and the
state transition [8]. In static Verification and validation, data analysis is done and the data dependency is
also followed. There can be fault and failure analysis in static verification and validation technique along
with model interface and the user interface [6]. The Static V & V technique follows the semantic analysis
and the structural analysis along with symbolic evaluation and syntax analysis.
Dynamic Verification and validation technique: This particular model requires a model
execution. They helps in evaluating the model that are based on the execution behavior [4]. Most of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SOFTWARE ENGINEERING
strategies that are used in this technique is model instrumentation. There is an insertion of additional
code that might be in some executable model for collecting the information about the behavior in the
execution phase [3]. The technique of Dynamic validation and verification are mainly done in three
steps; executable model us mainly instrumented, instrumented model is then executed, and the output
of the model is always analyzed.
The techniques that are used in this model are acceptance testing, alpha testing and all other
types of testing that are used in developing a software. This phase also includes predictive validation
along with top down testing and visualization or animation.
strategies that are used in this technique is model instrumentation. There is an insertion of additional
code that might be in some executable model for collecting the information about the behavior in the
execution phase [3]. The technique of Dynamic validation and verification are mainly done in three
steps; executable model us mainly instrumented, instrumented model is then executed, and the output
of the model is always analyzed.
The techniques that are used in this model are acceptance testing, alpha testing and all other
types of testing that are used in developing a software. This phase also includes predictive validation
along with top down testing and visualization or animation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SOFTWARE ENGINEERING
Bibliography
[1] M. Gogolla and F. Hilken, Model validation and verification options in a contemporary UML and OCL
analysis tool. Modellierung 2016, 2016.
[2] G. Kirbiš, D. Selčan and I. Kramberger, Software Reliability Validation and Verification Using Fault
Injection Techniques on a Fault Tolerant Processor. IFAC-PapersOnLine, 48(10), pp.252-257, 2015.
[3] M.A. Niazi, A. Hussain and M. Kolberg, Verification & validation of agent based simulations using the
VOMAS (virtual overlay multi-agent system) approach. arXiv preprint arXiv:1708.02361, 2017.
[4] M. Imran, N.A. Zafar, M.A. Alnuem, M.S. Aksoy, and A.V. Vasilakos, Formal verification and validation
of a movement control actor relocation algorithm for safety–critical applications. Wireless
Networks, 22(1), pp.247-265, 2016.
[5] R.G. Sargent, December. An introductory tutorial on verification and validation of simulation models.
In 2015 Winter Simulation Conference (WSC) (pp. 1729-1740). IEEE, 2015.
[6] X. Zheng and C. Julien, Verification and validation in cyber physical systems: research challenges and
a way forward. In 2015 IEEE/ACM 1st International Workshop on Software Engineering for Smart Cyber-
Physical Systems (pp. 15-18). IEEE, May 2015.
[7] R. Mejía-Gutiérrez and R. Carvajal-Arango, Design Verification through virtual prototyping techniques
based on Systems Engineering. Research in Engineering Design, 28(4), pp.477-494, 2017.
[8] P. Bagby, A. Hebert, R.G. White, S. Cafarelli and J. Shaver, Open Architecture Modeling, Verification,
and Validation. In 2018 AIAA Modeling and Simulation Technologies Conference (p. 1921), 2018.
Bibliography
[1] M. Gogolla and F. Hilken, Model validation and verification options in a contemporary UML and OCL
analysis tool. Modellierung 2016, 2016.
[2] G. Kirbiš, D. Selčan and I. Kramberger, Software Reliability Validation and Verification Using Fault
Injection Techniques on a Fault Tolerant Processor. IFAC-PapersOnLine, 48(10), pp.252-257, 2015.
[3] M.A. Niazi, A. Hussain and M. Kolberg, Verification & validation of agent based simulations using the
VOMAS (virtual overlay multi-agent system) approach. arXiv preprint arXiv:1708.02361, 2017.
[4] M. Imran, N.A. Zafar, M.A. Alnuem, M.S. Aksoy, and A.V. Vasilakos, Formal verification and validation
of a movement control actor relocation algorithm for safety–critical applications. Wireless
Networks, 22(1), pp.247-265, 2016.
[5] R.G. Sargent, December. An introductory tutorial on verification and validation of simulation models.
In 2015 Winter Simulation Conference (WSC) (pp. 1729-1740). IEEE, 2015.
[6] X. Zheng and C. Julien, Verification and validation in cyber physical systems: research challenges and
a way forward. In 2015 IEEE/ACM 1st International Workshop on Software Engineering for Smart Cyber-
Physical Systems (pp. 15-18). IEEE, May 2015.
[7] R. Mejía-Gutiérrez and R. Carvajal-Arango, Design Verification through virtual prototyping techniques
based on Systems Engineering. Research in Engineering Design, 28(4), pp.477-494, 2017.
[8] P. Bagby, A. Hebert, R.G. White, S. Cafarelli and J. Shaver, Open Architecture Modeling, Verification,
and Validation. In 2018 AIAA Modeling and Simulation Technologies Conference (p. 1921), 2018.
1 out of 11
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


