Software Solution: Coles Supermarket System Requirements Analysis
VerifiedAdded on 2023/04/21
|14
|1751
|134
Report
AI Summary
This report details the software solution for the Coles supermarket system, designed to enhance customer loyalty. It begins with an introduction outlining the system's core modules, including customer registration, checkout, gift award, and annual account resetting. The report then defines both functional and non-functional requirements, specifying how the system will operate and its performance characteristics. A detailed analysis follows, including context diagrams, level 1 and level 2 data flow diagrams, and a comprehensive data dictionary. The report further outlines the main tasks involved in the software development, with identification, duration, and a Gantt chart for project management. It also discusses suitable verification and validation techniques, such as technical, business, and management reviews, along with unit, integrated, system, and acceptance testing. The report concludes by providing references to relevant sources.

Running head: Software Solution 1
Software solution
Student name
Student Number
Professor’s name
Institution
Location of Institution
Date
Software solution
Student name
Student Number
Professor’s name
Institution
Location of Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Software Solution 2
Table of Contents
1 Introduction...................................................................................................................................3
2 Requirements................................................................................................................................3
2.1 Functional requirement..........................................................................................................3
2.2 Non-functional requirements.................................................................................................4
3 Analysis........................................................................................................................................6
3.1 Context diagram.....................................................................................................................6
3.2 Level 1 Data Flow.................................................................................................................6
3.3 Level 2 Data Flow.................................................................................................................8
4 Data Dictionary.............................................................................................................................9
5 Main tasks...................................................................................................................................10
5.1 Identification and Duration..................................................................................................10
5.2 Gantt Chat............................................................................................................................11
6 Suitable requirements.................................................................................................................11
6.1 Verification techniques........................................................................................................11
6.2 Validation techniques..........................................................................................................13
References......................................................................................................................................14
Table of Contents
1 Introduction...................................................................................................................................3
2 Requirements................................................................................................................................3
2.1 Functional requirement..........................................................................................................3
2.2 Non-functional requirements.................................................................................................4
3 Analysis........................................................................................................................................6
3.1 Context diagram.....................................................................................................................6
3.2 Level 1 Data Flow.................................................................................................................6
3.3 Level 2 Data Flow.................................................................................................................8
4 Data Dictionary.............................................................................................................................9
5 Main tasks...................................................................................................................................10
5.1 Identification and Duration..................................................................................................10
5.2 Gantt Chat............................................................................................................................11
6 Suitable requirements.................................................................................................................11
6.1 Verification techniques........................................................................................................11
6.2 Validation techniques..........................................................................................................13
References......................................................................................................................................14

Software Solution 3
1 Introduction
Software that will enhance customer loyalty by employing different security tactics such
as giving each customer a unique identity. The modules that will be included in this software
are; Registration module, checkout module that will record the value of the of purchase for each
and every customer, gift award module that will check the customer who will have spent more
than 1000 dollars at the end of the year and give the award to him or her, the module that will
automatically reset the CIN totals at the end of every year when the organization will be breaking
for holidays. This paper aims at explaining the software development for the Australian
supermarket Coles system.
2 Requirements
2.1 Functional requirement
Functional requirements explain how the software system is supposed to operate by looking at
the components that make up the system[1].
a) Customer registration
The customers will be required to give in their details like their full names, identification
number, their location, the mobile phone number to enable the staff to the monitor the
customers and the system to have the total number of the customers in that organization.
This will be done through customer registration. Once the customer has registered, when
visiting the system, the time, he will be required to give in to the system the name and the
identification number to login.
1 Introduction
Software that will enhance customer loyalty by employing different security tactics such
as giving each customer a unique identity. The modules that will be included in this software
are; Registration module, checkout module that will record the value of the of purchase for each
and every customer, gift award module that will check the customer who will have spent more
than 1000 dollars at the end of the year and give the award to him or her, the module that will
automatically reset the CIN totals at the end of every year when the organization will be breaking
for holidays. This paper aims at explaining the software development for the Australian
supermarket Coles system.
2 Requirements
2.1 Functional requirement
Functional requirements explain how the software system is supposed to operate by looking at
the components that make up the system[1].
a) Customer registration
The customers will be required to give in their details like their full names, identification
number, their location, the mobile phone number to enable the staff to the monitor the
customers and the system to have the total number of the customers in that organization.
This will be done through customer registration. Once the customer has registered, when
visiting the system, the time, he will be required to give in to the system the name and the
identification number to login.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Software Solution 4
b) Checkout
This module will enable the organization’s staff to identify the customer in the system
using the customer’s identification number (because it is supposed to be unique for every
customer) and put down what the customer would have bought. This will also help the
supermarket to know the customers that would have spent more than one hundred
thousand dollars to awarded.
c) Account resetting
At the end of every financial year of the organization, before going for holidays, the
system will be required to discard all the customer's records so that when coming back
they should start afresh in the next year.
2.2 Non-functional requirements
The development of the Australian supermarket giant Coles system will focus on the following
non-functional requirements in aid of the functional requirements to ensure the overall
functionality is achieved [2].
a) Performance requirement
Performance of the system is dependent on the bandwidth of the internet and also the
hardware itself.
b) Security requirement
There is only one person who is authorized to access confidential information. All the
information regarding the customers is only available to the system administrator.
c) Software Quality Attributes
b) Checkout
This module will enable the organization’s staff to identify the customer in the system
using the customer’s identification number (because it is supposed to be unique for every
customer) and put down what the customer would have bought. This will also help the
supermarket to know the customers that would have spent more than one hundred
thousand dollars to awarded.
c) Account resetting
At the end of every financial year of the organization, before going for holidays, the
system will be required to discard all the customer's records so that when coming back
they should start afresh in the next year.
2.2 Non-functional requirements
The development of the Australian supermarket giant Coles system will focus on the following
non-functional requirements in aid of the functional requirements to ensure the overall
functionality is achieved [2].
a) Performance requirement
Performance of the system is dependent on the bandwidth of the internet and also the
hardware itself.
b) Security requirement
There is only one person who is authorized to access confidential information. All the
information regarding the customers is only available to the system administrator.
c) Software Quality Attributes
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Software Solution 5
The system is intended to be user-friendly, interoperable and flexible to ease the
operations.
d) Maintainability
The development uses best practices for coding including modularity and well commented
for ease in the need for future maintenance.
e) Recovery
The system will allow all restoration top already backed up data to allow full functionality in
case of any data loss, in this case, all the data will be auto-recovered [3].
The system is intended to be user-friendly, interoperable and flexible to ease the
operations.
d) Maintainability
The development uses best practices for coding including modularity and well commented
for ease in the need for future maintenance.
e) Recovery
The system will allow all restoration top already backed up data to allow full functionality in
case of any data loss, in this case, all the data will be auto-recovered [3].
Software Solution 6
3 Analysis
3.1 Context diagram
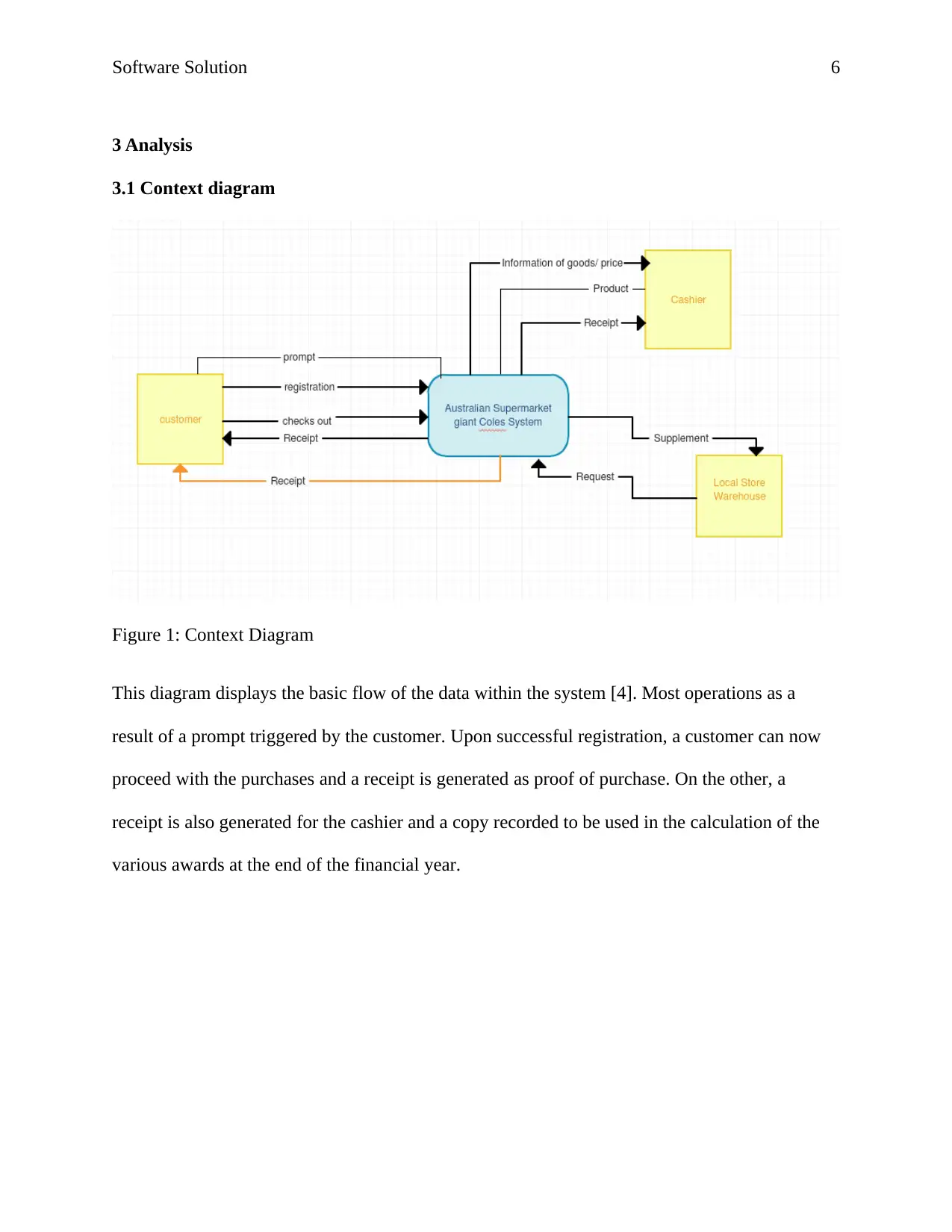
Figure 1: Context Diagram
This diagram displays the basic flow of the data within the system [4]. Most operations as a
result of a prompt triggered by the customer. Upon successful registration, a customer can now
proceed with the purchases and a receipt is generated as proof of purchase. On the other, a
receipt is also generated for the cashier and a copy recorded to be used in the calculation of the
various awards at the end of the financial year.
3 Analysis
3.1 Context diagram
Figure 1: Context Diagram
This diagram displays the basic flow of the data within the system [4]. Most operations as a
result of a prompt triggered by the customer. Upon successful registration, a customer can now
proceed with the purchases and a receipt is generated as proof of purchase. On the other, a
receipt is also generated for the cashier and a copy recorded to be used in the calculation of the
various awards at the end of the financial year.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Software Solution 7
3.2 Level 1 Data Flow
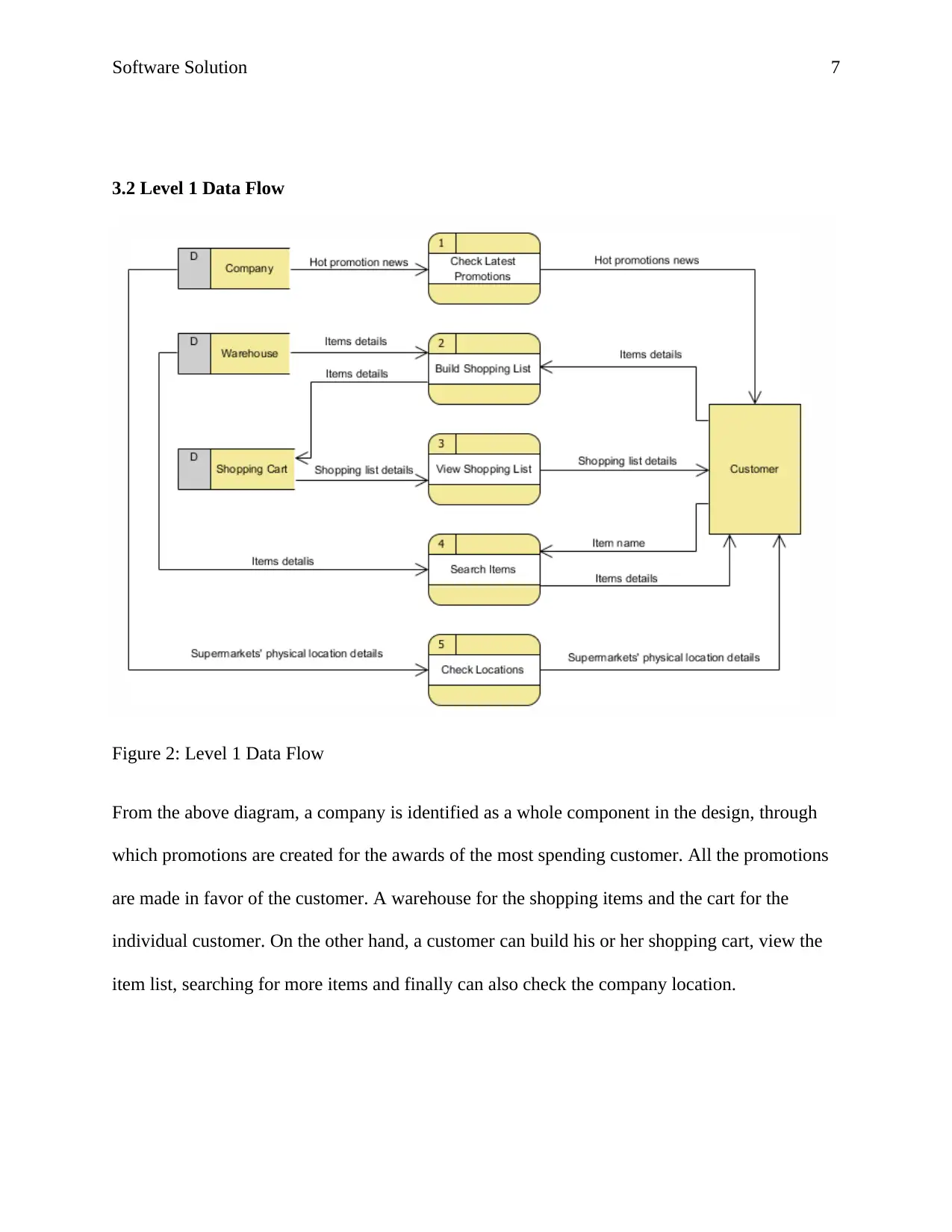
Figure 2: Level 1 Data Flow
From the above diagram, a company is identified as a whole component in the design, through
which promotions are created for the awards of the most spending customer. All the promotions
are made in favor of the customer. A warehouse for the shopping items and the cart for the
individual customer. On the other hand, a customer can build his or her shopping cart, view the
item list, searching for more items and finally can also check the company location.
3.2 Level 1 Data Flow
Figure 2: Level 1 Data Flow
From the above diagram, a company is identified as a whole component in the design, through
which promotions are created for the awards of the most spending customer. All the promotions
are made in favor of the customer. A warehouse for the shopping items and the cart for the
individual customer. On the other hand, a customer can build his or her shopping cart, view the
item list, searching for more items and finally can also check the company location.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Software Solution 8
3.3 Level 2 Data Flow
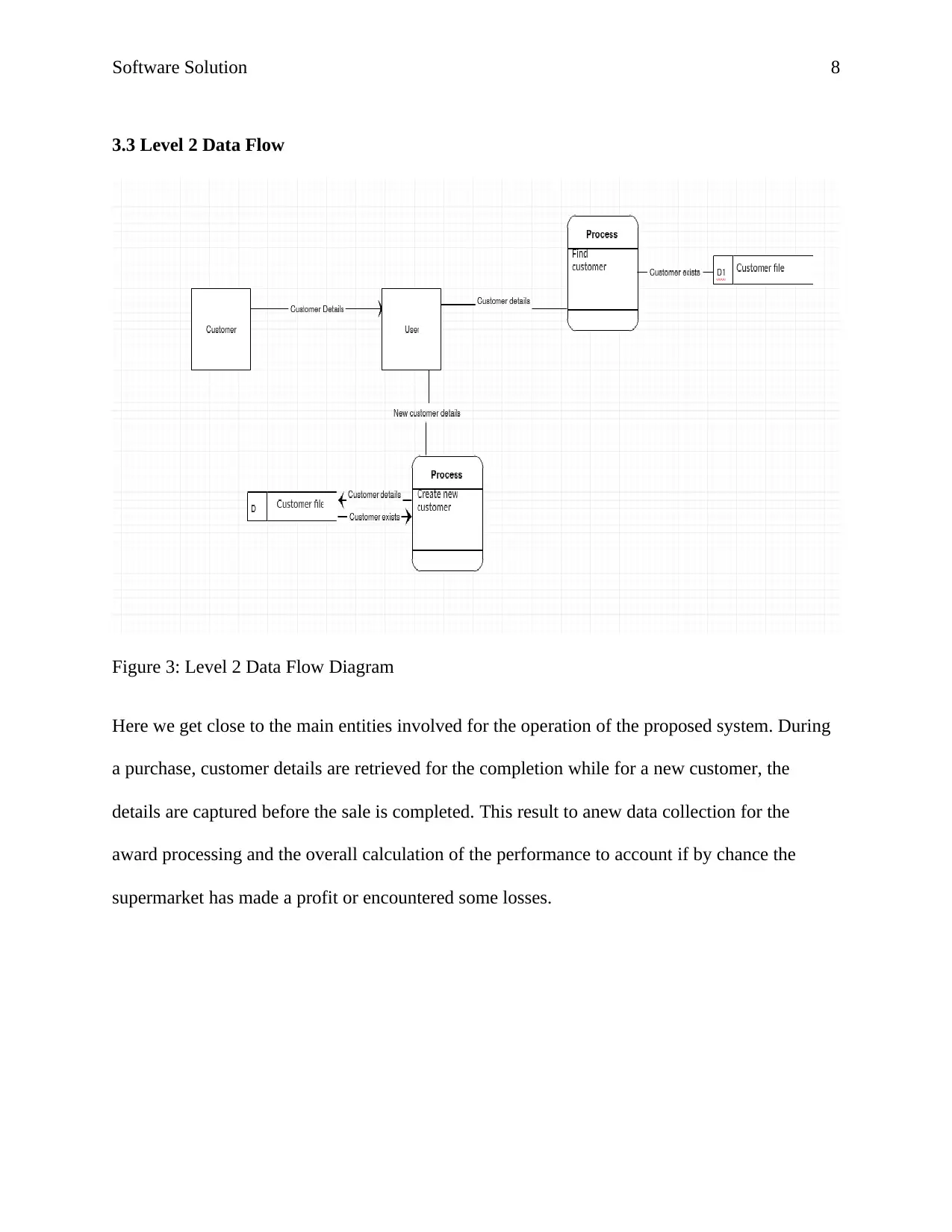
Figure 3: Level 2 Data Flow Diagram
Here we get close to the main entities involved for the operation of the proposed system. During
a purchase, customer details are retrieved for the completion while for a new customer, the
details are captured before the sale is completed. This result to anew data collection for the
award processing and the overall calculation of the performance to account if by chance the
supermarket has made a profit or encountered some losses.
3.3 Level 2 Data Flow
Figure 3: Level 2 Data Flow Diagram
Here we get close to the main entities involved for the operation of the proposed system. During
a purchase, customer details are retrieved for the completion while for a new customer, the
details are captured before the sale is completed. This result to anew data collection for the
award processing and the overall calculation of the performance to account if by chance the
supermarket has made a profit or encountered some losses.

Software Solution 9
4 Data Dictionary
This list all the entities used in the construction of the data flow diagram.
Customer- the customer is the main entity for major operations in the running of the business.
Cashier- carriers all the sales and records in the system.
Warehouse- stores all the item of sale within the supermarket. For the operation of the business,
the goods to be sold should be stored within the locality to allow faster operations.
Company- this shows the overall body under which the Australian supermarket is operating,
concerned with the management of the supermarket, the calculation of the profits and the losses
in case of any for the growth of the supermarket.
4 Data Dictionary
This list all the entities used in the construction of the data flow diagram.
Customer- the customer is the main entity for major operations in the running of the business.
Cashier- carriers all the sales and records in the system.
Warehouse- stores all the item of sale within the supermarket. For the operation of the business,
the goods to be sold should be stored within the locality to allow faster operations.
Company- this shows the overall body under which the Australian supermarket is operating,
concerned with the management of the supermarket, the calculation of the profits and the losses
in case of any for the growth of the supermarket.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Software Solution 10
5 Main tasks
5.1 Identification and Duration
ID Task Duration Dependency
A Planning initialization 2 days -
B Resource Planning 2 days A
C Quality Planning 2 days B
D Contacting 2 days A
E Phase Review 4 days A
F Gathering Business requirements 7 days D
G Building trust and rapport with the customers 2 days C
H Documenting the system in use 3 days G
I Development of preliminary data and process models 7 days H
J System design 3 days I
K Implementation 10 days J
L System Installation 3 days K
M System support plan development 5 days L
N System maintenance and Evaluation 8 days M
5 Main tasks
5.1 Identification and Duration
ID Task Duration Dependency
A Planning initialization 2 days -
B Resource Planning 2 days A
C Quality Planning 2 days B
D Contacting 2 days A
E Phase Review 4 days A
F Gathering Business requirements 7 days D
G Building trust and rapport with the customers 2 days C
H Documenting the system in use 3 days G
I Development of preliminary data and process models 7 days H
J System design 3 days I
K Implementation 10 days J
L System Installation 3 days K
M System support plan development 5 days L
N System maintenance and Evaluation 8 days M
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Software Solution 11
5.2 Gantt Chat
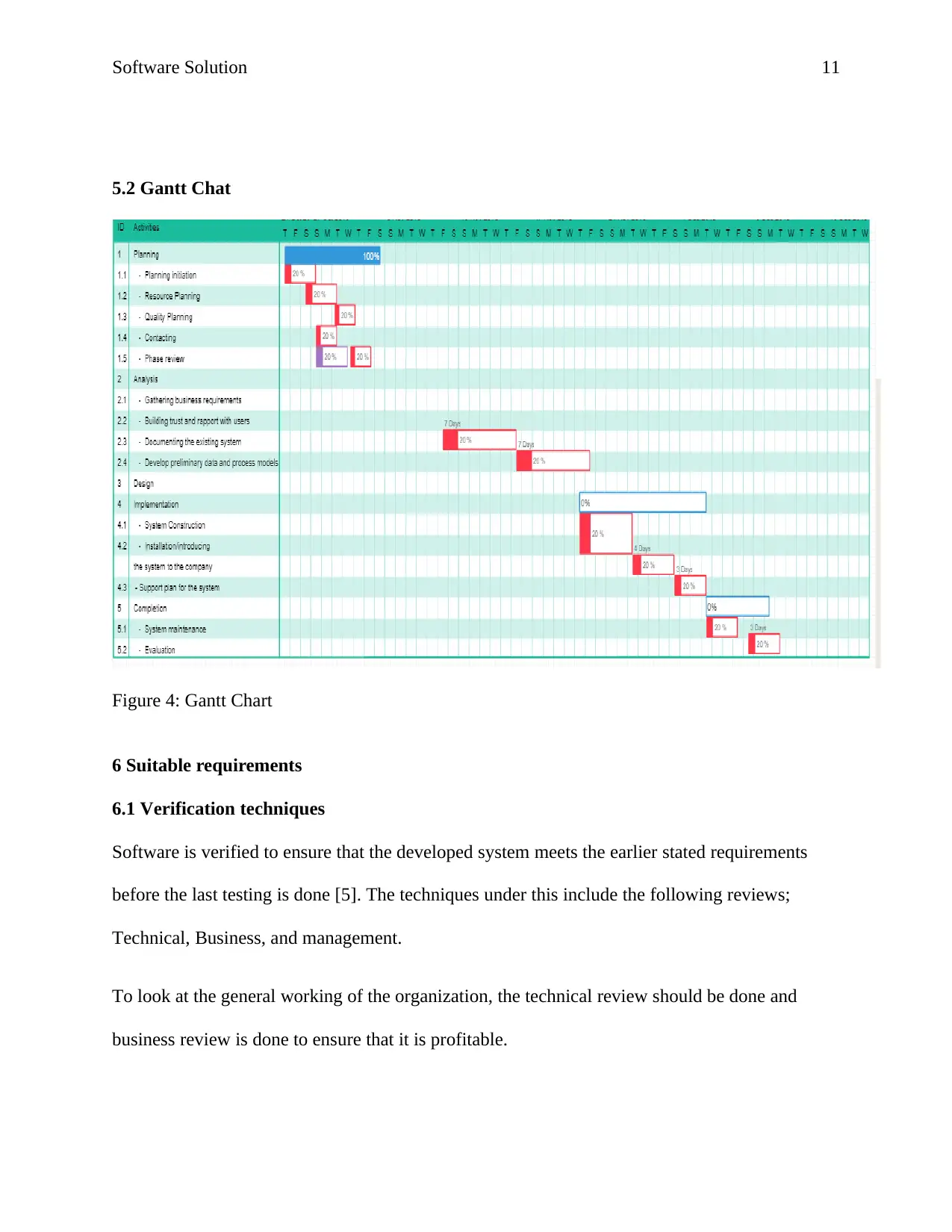
Figure 4: Gantt Chart
6 Suitable requirements
6.1 Verification techniques
Software is verified to ensure that the developed system meets the earlier stated requirements
before the last testing is done [5]. The techniques under this include the following reviews;
Technical, Business, and management.
To look at the general working of the organization, the technical review should be done and
business review is done to ensure that it is profitable.
5.2 Gantt Chat
Figure 4: Gantt Chart
6 Suitable requirements
6.1 Verification techniques
Software is verified to ensure that the developed system meets the earlier stated requirements
before the last testing is done [5]. The techniques under this include the following reviews;
Technical, Business, and management.
To look at the general working of the organization, the technical review should be done and
business review is done to ensure that it is profitable.
Software Solution 12
Management review should be done to ensure that there is a good rapport between the customers
and the staff to enable smooth running in the organization.
Management review should be done to ensure that there is a good rapport between the customers
and the staff to enable smooth running in the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





