MN507 - Software Engineering: Supermarket System Report
VerifiedAdded on 2022/11/29
|17
|2941
|421
Report
AI Summary
This software engineering report details the design and development of a supermarket system. It includes functional requirements like data storage, authentication, authorization, FlyBus card creation, product purchase, and payment handling. Non-functional aspects such as security, availability, audit, and usability are also addressed. The report features a context diagram, Level 1 and Level 2 Data Flow Diagrams (DFDs), and a data dictionary defining key attributes. A Gantt chart illustrates the project timeline, and the report concludes with verification and validation methods, covering robustness analysis and proof of correctness. This comprehensive analysis provides a structured approach to system design and development, making it a valuable resource for understanding software engineering principles. The assignment also covers various aspects of software testing, including unit testing, black-box and white-box testing, performance and usability testing, and integration testing. Furthermore, the report includes sections on user acceptance testing and debugging, ensuring a thorough examination of the system's functionality and reliability.

Running head: SOFTWARE ENGINEERING
Software Engineering
Name of the Student
Name of the University
Author’s note:
Software Engineering
Name of the Student
Name of the University
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SOFTWARE ENGINEERING
Table of Contents
Functional Requirements:................................................................................................................2
Non-Functional System:..................................................................................................................4
Context Diagram:.............................................................................................................................5
Level 1 DFD:...................................................................................................................................6
Level 2 DFD:...................................................................................................................................7
Data Dictionary:...............................................................................................................................7
Gantt Chart:.....................................................................................................................................9
Verification and Validation:..........................................................................................................13
Verification Methods:................................................................................................................13
Validation Methods:..................................................................................................................14
Bibliography:.................................................................................................................................15
Table of Contents
Functional Requirements:................................................................................................................2
Non-Functional System:..................................................................................................................4
Context Diagram:.............................................................................................................................5
Level 1 DFD:...................................................................................................................................6
Level 2 DFD:...................................................................................................................................7
Data Dictionary:...............................................................................................................................7
Gantt Chart:.....................................................................................................................................9
Verification and Validation:..........................................................................................................13
Verification Methods:................................................................................................................13
Validation Methods:..................................................................................................................14
Bibliography:.................................................................................................................................15

2SOFTWARE ENGINEERING
Functional Requirements:
Data Storage: The system needs to save the information of the customer to a safe
location. The system can later retrieve these data from that location to conduct various processes.
The system will also handle stocks and purchase. Therefore, the data related to these processes
needs to be stored. The system requires a technology that can store, allow retrieving and
processing the recorded data efficiently. This data storage will be directly connected to the
system server. The data storage devices will not be responsible for only storing the data but also
checking the integrity of the data.
Authentication: The authentication method refers to the technique of validating the user
credentials. These user credentials are user name and user id. The system will identify whether
the user is a customer, staff or management using this method. The authentication method also
prevents unregistered users from accessing the system. Various systems uses authentication
using various methods. The proposed system at super market does not allow the customer to
authenticate. However, the staff will use the Customer Identification Number to authenticate the
user account. This will allow the organization to have complete control over the system
activities.
Authorization: Authorization comes into the big picture when authentication is
successfully completed and the system has allowed the user to access it. However, the proposed
system will have many levels of users from customer to manager. Each of this user group will
have different functionality to use and information to access. The system will make sure that
information will be accessed by only authorized users. This is implemented using the
authorization method into the core of the system. This way system makes sure that manager can
Functional Requirements:
Data Storage: The system needs to save the information of the customer to a safe
location. The system can later retrieve these data from that location to conduct various processes.
The system will also handle stocks and purchase. Therefore, the data related to these processes
needs to be stored. The system requires a technology that can store, allow retrieving and
processing the recorded data efficiently. This data storage will be directly connected to the
system server. The data storage devices will not be responsible for only storing the data but also
checking the integrity of the data.
Authentication: The authentication method refers to the technique of validating the user
credentials. These user credentials are user name and user id. The system will identify whether
the user is a customer, staff or management using this method. The authentication method also
prevents unregistered users from accessing the system. Various systems uses authentication
using various methods. The proposed system at super market does not allow the customer to
authenticate. However, the staff will use the Customer Identification Number to authenticate the
user account. This will allow the organization to have complete control over the system
activities.
Authorization: Authorization comes into the big picture when authentication is
successfully completed and the system has allowed the user to access it. However, the proposed
system will have many levels of users from customer to manager. Each of this user group will
have different functionality to use and information to access. The system will make sure that
information will be accessed by only authorized users. This is implemented using the
authorization method into the core of the system. This way system makes sure that manager can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SOFTWARE ENGINEERING
have overall control over the system. This method allow to implement user hierarchy in the
system.
Creating FlyBus Card: The customer will have a FlyBus card which will store every
detail of him/her. This card will be generated after the registration of the customer is done. In
order to register into the system, the customer will provide name, address, and telephone number
to the staff. During this registration, the system will enroll the customer into the scheme. The
system will auto generate the Customer Identification Number for each customer. This Customer
Identification Number will be different for each customer. Each time the customer purchase
something, the FlyBus Card has to be brought to the store.
Product Purchase: The system will allow the customer to purchase product from the
store. In contrast to the online purchase, the customer does not select all the products and pay
himself using the login credentials. In case of online purchase, the customer select the virtual
representation of the products and later receives the physical product. The proposed system
cannot track the purchase of the customer until it is not recorded by the staff into the system.
There is no virtual cart option in this store. The system will also calculate the total purchase
made by each customer and select the winners of the scheme.
Payment Handling: The system needs a payment handling sub-system that can accept
payment from the customers. The payment can be done using hard cash and cards. In case the
payment is done using cash, the staff will enter the quantity of the notes and coins provided. In
case the card is used, then the system will store the card number, card holder name, bank name
and few more details regarding payment. Each payment will be done against a single purchase.
The system does not accept payments in installment.
have overall control over the system. This method allow to implement user hierarchy in the
system.
Creating FlyBus Card: The customer will have a FlyBus card which will store every
detail of him/her. This card will be generated after the registration of the customer is done. In
order to register into the system, the customer will provide name, address, and telephone number
to the staff. During this registration, the system will enroll the customer into the scheme. The
system will auto generate the Customer Identification Number for each customer. This Customer
Identification Number will be different for each customer. Each time the customer purchase
something, the FlyBus Card has to be brought to the store.
Product Purchase: The system will allow the customer to purchase product from the
store. In contrast to the online purchase, the customer does not select all the products and pay
himself using the login credentials. In case of online purchase, the customer select the virtual
representation of the products and later receives the physical product. The proposed system
cannot track the purchase of the customer until it is not recorded by the staff into the system.
There is no virtual cart option in this store. The system will also calculate the total purchase
made by each customer and select the winners of the scheme.
Payment Handling: The system needs a payment handling sub-system that can accept
payment from the customers. The payment can be done using hard cash and cards. In case the
payment is done using cash, the staff will enter the quantity of the notes and coins provided. In
case the card is used, then the system will store the card number, card holder name, bank name
and few more details regarding payment. Each payment will be done against a single purchase.
The system does not accept payments in installment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SOFTWARE ENGINEERING
Non-Functional System:
Security: The customers will be allowed to make payment through the system using their
cards. In case they pay through cash, there is no security concern regarding payment. If the
customers are using the DBIT/CREDIT card for making payment then secure connection must
be established. The primary system security will be installed using the encryption/decryption
mechanism. The security is also needed to safeguard the sensitive information of the
organization. The organization has many information like customer details, their bank details,
purchases, inventory related. It also stores the patterns of the business and secret business deals.
The system must follow security measurements that can prevent cyber-attacks from both the
insiders and outsiders.
Availability: The system should be available while the store is open. This means that
server and system upgrade works should done after the store closes. The management may need
to access the system any time they want. They can also access the system from remote locations.
This implies that a cloud system should be implemented to provide access to the system over
internet. The system availability also needed when the staff accessing their working details. Few
staff are responsible for checking the work done in a day or week or month and submit a report
to the management.
Audit: System audit is essential requirement of this system. This system will be used by
only the internal staff. That is why the amount of issues highlighted by the users will be very low
in comparison to the online store which is accessed by thousands of customers simultaneously.
The audit will allow the management to identify the gaps in the system. Audit will also assist the
organization to prevent any security loophole the system. The audit will be done once in a
quarter of the year. The report of the audit will be stored in the system.
Non-Functional System:
Security: The customers will be allowed to make payment through the system using their
cards. In case they pay through cash, there is no security concern regarding payment. If the
customers are using the DBIT/CREDIT card for making payment then secure connection must
be established. The primary system security will be installed using the encryption/decryption
mechanism. The security is also needed to safeguard the sensitive information of the
organization. The organization has many information like customer details, their bank details,
purchases, inventory related. It also stores the patterns of the business and secret business deals.
The system must follow security measurements that can prevent cyber-attacks from both the
insiders and outsiders.
Availability: The system should be available while the store is open. This means that
server and system upgrade works should done after the store closes. The management may need
to access the system any time they want. They can also access the system from remote locations.
This implies that a cloud system should be implemented to provide access to the system over
internet. The system availability also needed when the staff accessing their working details. Few
staff are responsible for checking the work done in a day or week or month and submit a report
to the management.
Audit: System audit is essential requirement of this system. This system will be used by
only the internal staff. That is why the amount of issues highlighted by the users will be very low
in comparison to the online store which is accessed by thousands of customers simultaneously.
The audit will allow the management to identify the gaps in the system. Audit will also assist the
organization to prevent any security loophole the system. The audit will be done once in a
quarter of the year. The report of the audit will be stored in the system.

5SOFTWARE ENGINEERING
Usability: The system is not proposed for customers therefore, there is no challenge of
making the users like the system. For this reason, the designer team can implement many new
elements in the design which is not conventional. The usability of the system, however, have to
very rich in functionality and easy to use. The base design of the system such as color, header,
and login pages and media presentation will be same for each user screens. The system will
provide only the required functions to the screens so that any unwanted situation can be avoided.
Limiting the user interaction prevents the chance of taking unauthorized benefit from the system.
Context Diagram:
Figure 1: Context Diagram of Supermarket System
(Source: Created by Author)
Usability: The system is not proposed for customers therefore, there is no challenge of
making the users like the system. For this reason, the designer team can implement many new
elements in the design which is not conventional. The usability of the system, however, have to
very rich in functionality and easy to use. The base design of the system such as color, header,
and login pages and media presentation will be same for each user screens. The system will
provide only the required functions to the screens so that any unwanted situation can be avoided.
Limiting the user interaction prevents the chance of taking unauthorized benefit from the system.
Context Diagram:
Figure 1: Context Diagram of Supermarket System
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SOFTWARE ENGINEERING
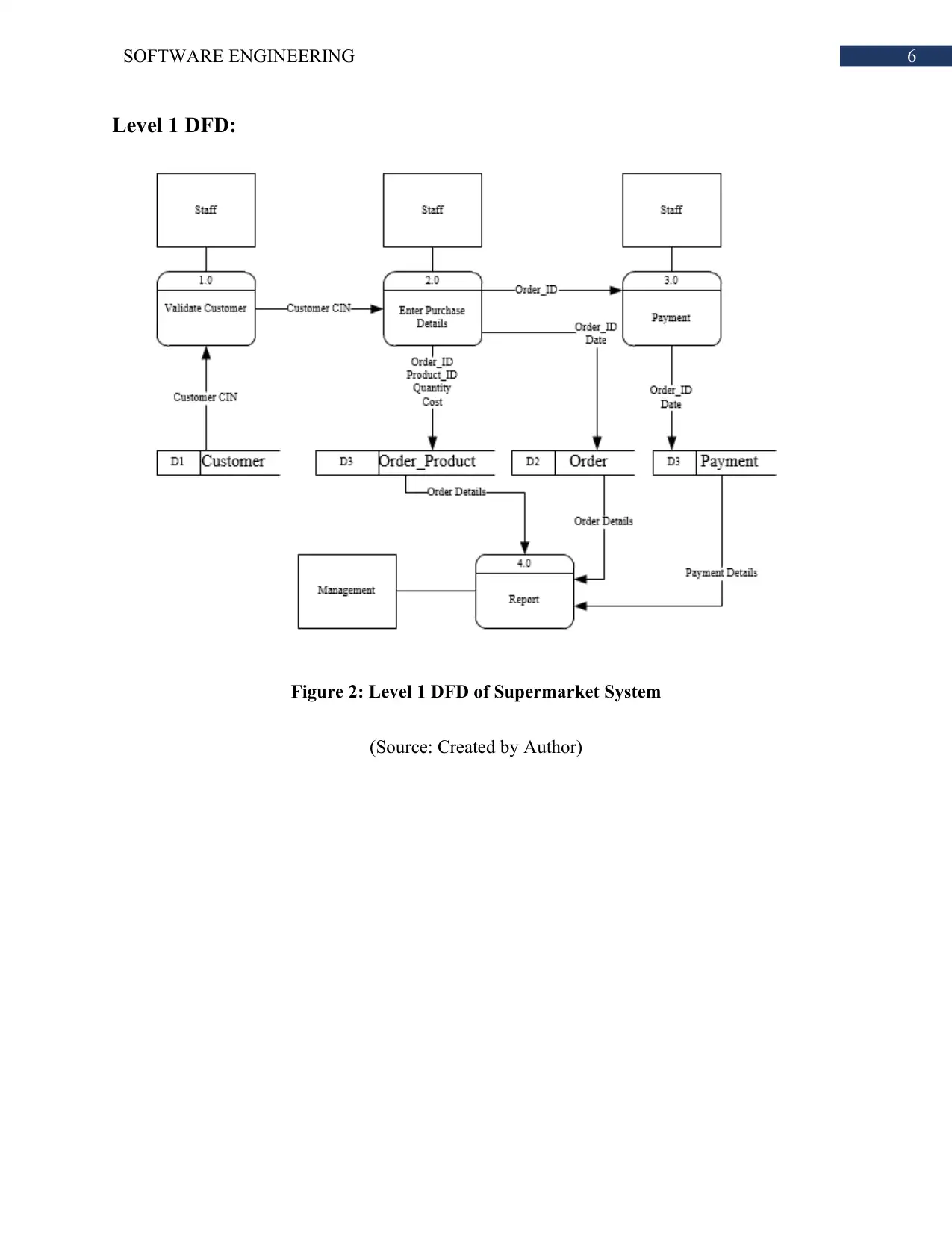
Level 1 DFD:
Figure 2: Level 1 DFD of Supermarket System
(Source: Created by Author)
Level 1 DFD:
Figure 2: Level 1 DFD of Supermarket System
(Source: Created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SOFTWARE ENGINEERING
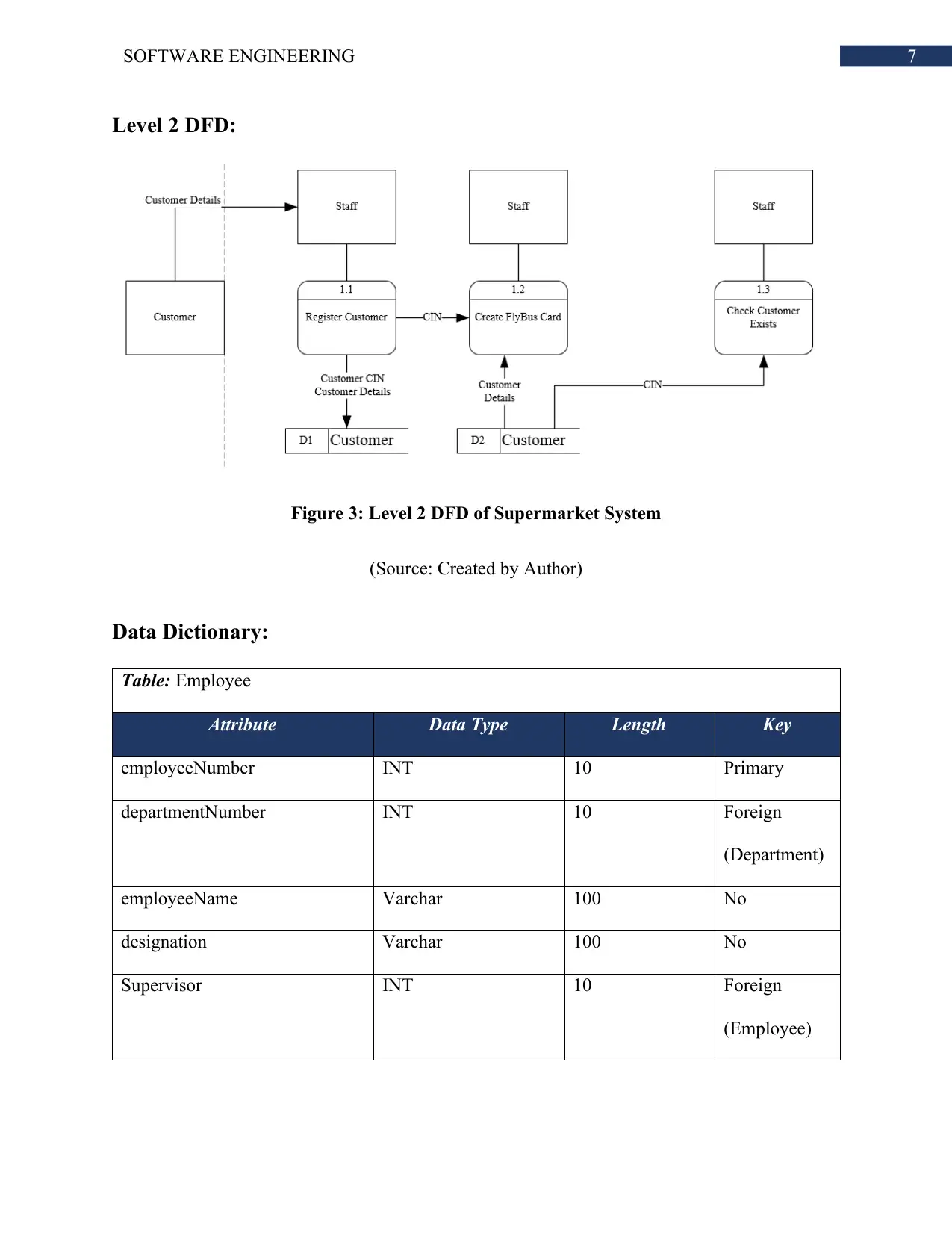
Level 2 DFD:
Figure 3: Level 2 DFD of Supermarket System
(Source: Created by Author)
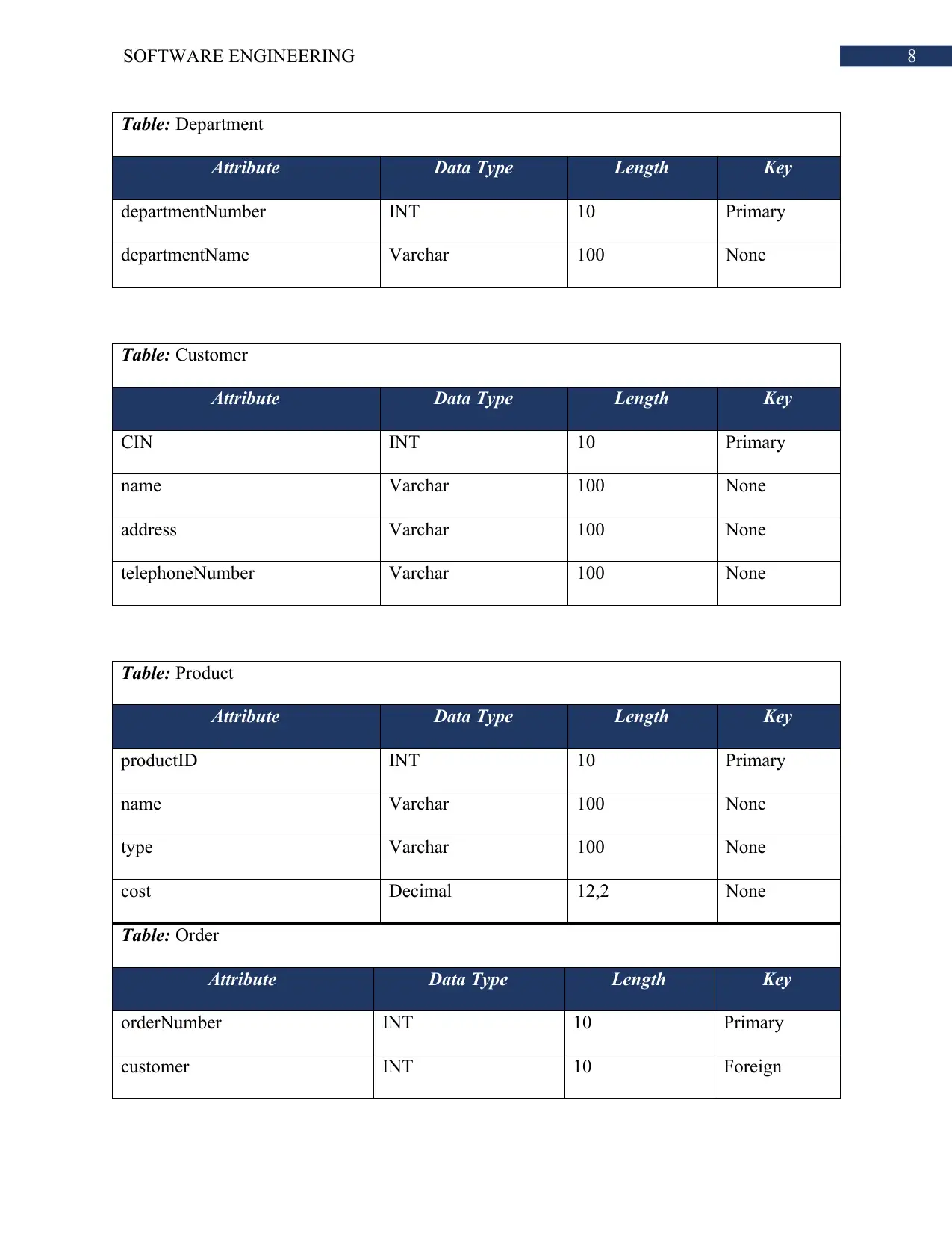
Data Dictionary:
Table: Employee
Attribute Data Type Length Key
employeeNumber INT 10 Primary
departmentNumber INT 10 Foreign
(Department)
employeeName Varchar 100 No
designation Varchar 100 No
Supervisor INT 10 Foreign
(Employee)
Level 2 DFD:
Figure 3: Level 2 DFD of Supermarket System
(Source: Created by Author)
Data Dictionary:
Table: Employee
Attribute Data Type Length Key
employeeNumber INT 10 Primary
departmentNumber INT 10 Foreign
(Department)
employeeName Varchar 100 No
designation Varchar 100 No
Supervisor INT 10 Foreign
(Employee)
8SOFTWARE ENGINEERING
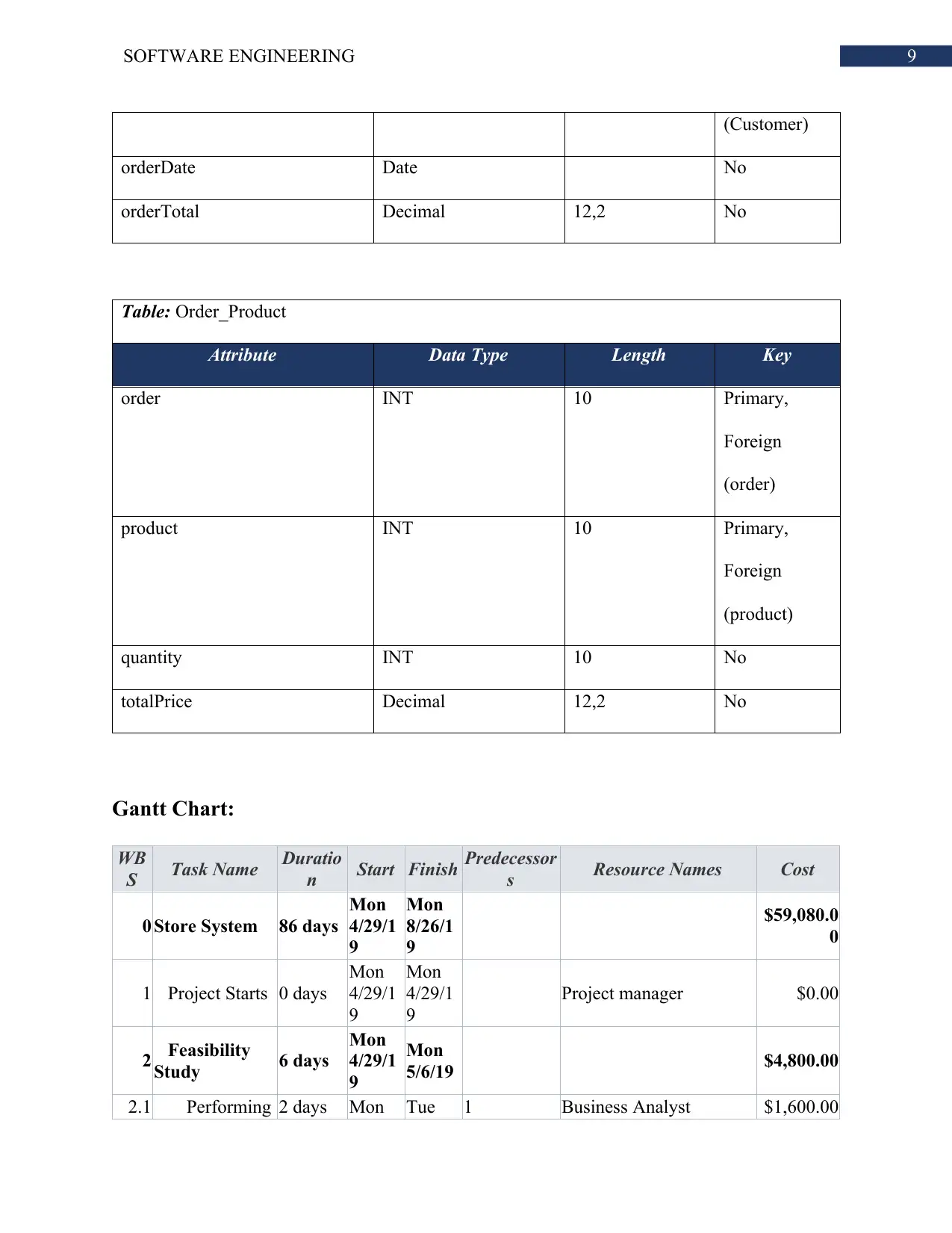
Table: Department
Attribute Data Type Length Key
departmentNumber INT 10 Primary
departmentName Varchar 100 None
Table: Customer
Attribute Data Type Length Key
CIN INT 10 Primary
name Varchar 100 None
address Varchar 100 None
telephoneNumber Varchar 100 None
Table: Product
Attribute Data Type Length Key
productID INT 10 Primary
name Varchar 100 None
type Varchar 100 None
cost Decimal 12,2 None
Table: Order
Attribute Data Type Length Key
orderNumber INT 10 Primary
customer INT 10 Foreign
Table: Department
Attribute Data Type Length Key
departmentNumber INT 10 Primary
departmentName Varchar 100 None
Table: Customer
Attribute Data Type Length Key
CIN INT 10 Primary
name Varchar 100 None
address Varchar 100 None
telephoneNumber Varchar 100 None
Table: Product
Attribute Data Type Length Key
productID INT 10 Primary
name Varchar 100 None
type Varchar 100 None
cost Decimal 12,2 None
Table: Order
Attribute Data Type Length Key
orderNumber INT 10 Primary
customer INT 10 Foreign
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9SOFTWARE ENGINEERING
(Customer)
orderDate Date No
orderTotal Decimal 12,2 No
Table: Order_Product
Attribute Data Type Length Key
order INT 10 Primary,
Foreign
(order)
product INT 10 Primary,
Foreign
(product)
quantity INT 10 No
totalPrice Decimal 12,2 No
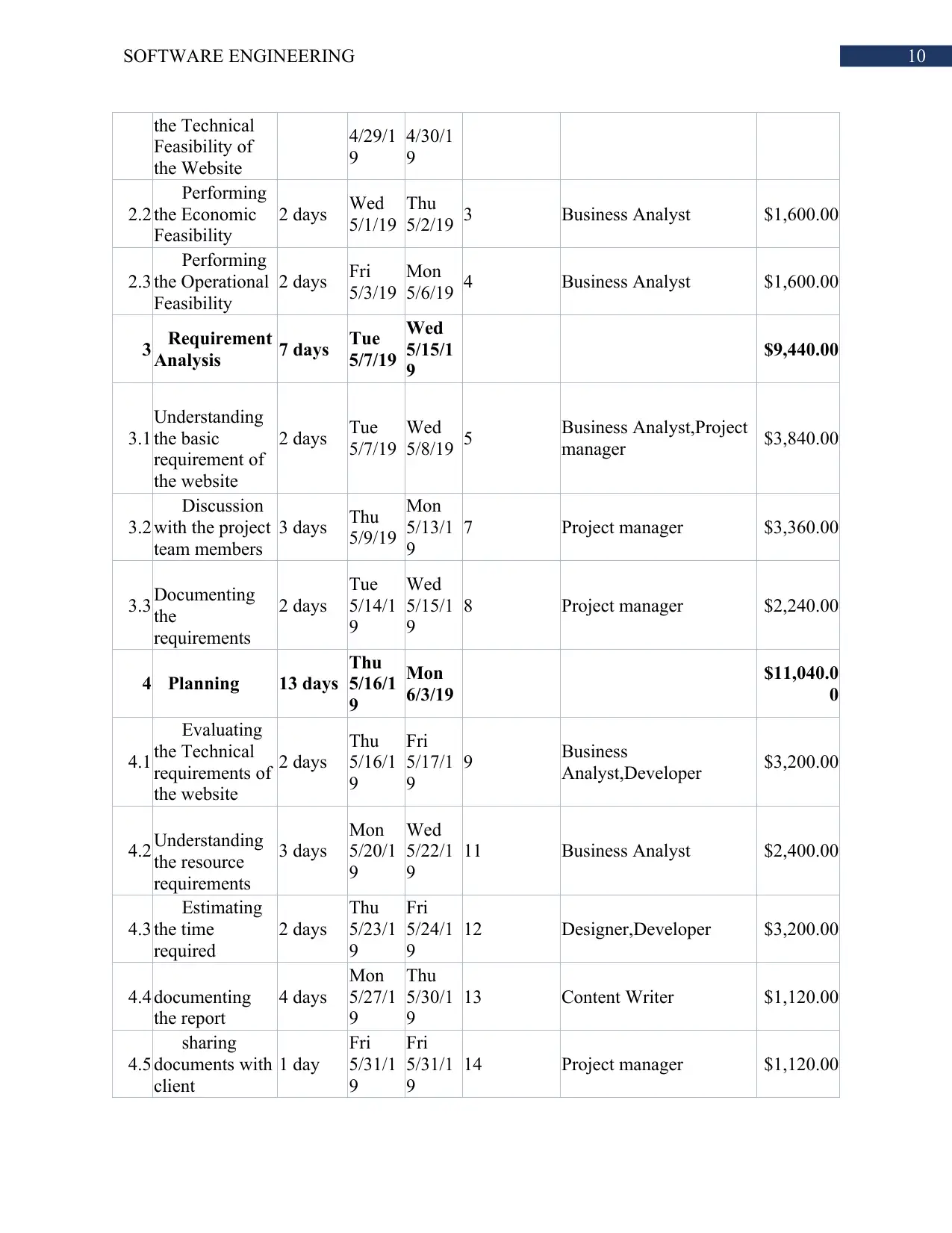
Gantt Chart:
WB
S Task Name Duratio
n Start Finish Predecessor
s Resource Names Cost
0 Store System 86 days
Mon
4/29/1
9
Mon
8/26/1
9
$59,080.0
0
1 Project Starts 0 days
Mon
4/29/1
9
Mon
4/29/1
9
Project manager $0.00
2 Feasibility
Study 6 days
Mon
4/29/1
9
Mon
5/6/19 $4,800.00
2.1 Performing 2 days Mon Tue 1 Business Analyst $1,600.00
(Customer)
orderDate Date No
orderTotal Decimal 12,2 No
Table: Order_Product
Attribute Data Type Length Key
order INT 10 Primary,
Foreign
(order)
product INT 10 Primary,
Foreign
(product)
quantity INT 10 No
totalPrice Decimal 12,2 No
Gantt Chart:
WB
S Task Name Duratio
n Start Finish Predecessor
s Resource Names Cost
0 Store System 86 days
Mon
4/29/1
9
Mon
8/26/1
9
$59,080.0
0
1 Project Starts 0 days
Mon
4/29/1
9
Mon
4/29/1
9
Project manager $0.00
2 Feasibility
Study 6 days
Mon
4/29/1
9
Mon
5/6/19 $4,800.00
2.1 Performing 2 days Mon Tue 1 Business Analyst $1,600.00
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10SOFTWARE ENGINEERING
the Technical
Feasibility of
the Website
4/29/1
9
4/30/1
9
2.2
Performing
the Economic
Feasibility
2 days Wed
5/1/19
Thu
5/2/19 3 Business Analyst $1,600.00
2.3
Performing
the Operational
Feasibility
2 days Fri
5/3/19
Mon
5/6/19 4 Business Analyst $1,600.00
3 Requirement
Analysis 7 days Tue
5/7/19
Wed
5/15/1
9
$9,440.00
3.1
Understanding
the basic
requirement of
the website
2 days Tue
5/7/19
Wed
5/8/19 5 Business Analyst,Project
manager $3,840.00
3.2
Discussion
with the project
team members
3 days Thu
5/9/19
Mon
5/13/1
9
7 Project manager $3,360.00
3.3 Documenting
the
requirements
2 days
Tue
5/14/1
9
Wed
5/15/1
9
8 Project manager $2,240.00
4 Planning 13 days
Thu
5/16/1
9
Mon
6/3/19
$11,040.0
0
4.1
Evaluating
the Technical
requirements of
the website
2 days
Thu
5/16/1
9
Fri
5/17/1
9
9 Business
Analyst,Developer $3,200.00
4.2 Understanding
the resource
requirements
3 days
Mon
5/20/1
9
Wed
5/22/1
9
11 Business Analyst $2,400.00
4.3
Estimating
the time
required
2 days
Thu
5/23/1
9
Fri
5/24/1
9
12 Designer,Developer $3,200.00
4.4 documenting
the report
4 days
Mon
5/27/1
9
Thu
5/30/1
9
13 Content Writer $1,120.00
4.5
sharing
documents with
client
1 day
Fri
5/31/1
9
Fri
5/31/1
9
14 Project manager $1,120.00
the Technical
Feasibility of
the Website
4/29/1
9
4/30/1
9
2.2
Performing
the Economic
Feasibility
2 days Wed
5/1/19
Thu
5/2/19 3 Business Analyst $1,600.00
2.3
Performing
the Operational
Feasibility
2 days Fri
5/3/19
Mon
5/6/19 4 Business Analyst $1,600.00
3 Requirement
Analysis 7 days Tue
5/7/19
Wed
5/15/1
9
$9,440.00
3.1
Understanding
the basic
requirement of
the website
2 days Tue
5/7/19
Wed
5/8/19 5 Business Analyst,Project
manager $3,840.00
3.2
Discussion
with the project
team members
3 days Thu
5/9/19
Mon
5/13/1
9
7 Project manager $3,360.00
3.3 Documenting
the
requirements
2 days
Tue
5/14/1
9
Wed
5/15/1
9
8 Project manager $2,240.00
4 Planning 13 days
Thu
5/16/1
9
Mon
6/3/19
$11,040.0
0
4.1
Evaluating
the Technical
requirements of
the website
2 days
Thu
5/16/1
9
Fri
5/17/1
9
9 Business
Analyst,Developer $3,200.00
4.2 Understanding
the resource
requirements
3 days
Mon
5/20/1
9
Wed
5/22/1
9
11 Business Analyst $2,400.00
4.3
Estimating
the time
required
2 days
Thu
5/23/1
9
Fri
5/24/1
9
12 Designer,Developer $3,200.00
4.4 documenting
the report
4 days
Mon
5/27/1
9
Thu
5/30/1
9
13 Content Writer $1,120.00
4.5
sharing
documents with
client
1 day
Fri
5/31/1
9
Fri
5/31/1
9
14 Project manager $1,120.00
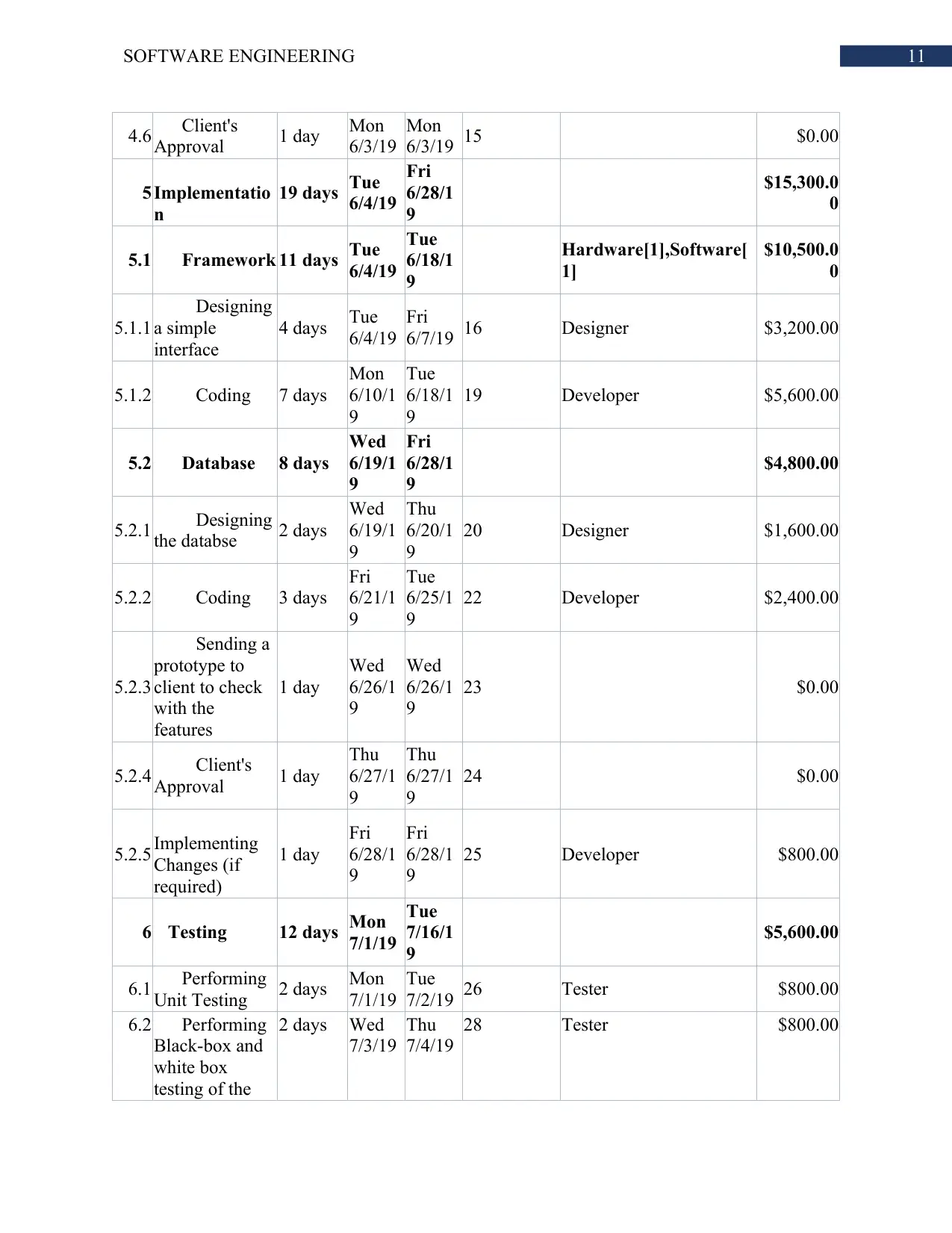
11SOFTWARE ENGINEERING
4.6 Client's
Approval 1 day Mon
6/3/19
Mon
6/3/19 15 $0.00
5 Implementatio
n
19 days Tue
6/4/19
Fri
6/28/1
9
$15,300.0
0
5.1 Framework 11 days Tue
6/4/19
Tue
6/18/1
9
Hardware[1],Software[
1]
$10,500.0
0
5.1.1
Designing
a simple
interface
4 days Tue
6/4/19
Fri
6/7/19 16 Designer $3,200.00
5.1.2 Coding 7 days
Mon
6/10/1
9
Tue
6/18/1
9
19 Developer $5,600.00
5.2 Database 8 days
Wed
6/19/1
9
Fri
6/28/1
9
$4,800.00
5.2.1 Designing
the databse 2 days
Wed
6/19/1
9
Thu
6/20/1
9
20 Designer $1,600.00
5.2.2 Coding 3 days
Fri
6/21/1
9
Tue
6/25/1
9
22 Developer $2,400.00
5.2.3
Sending a
prototype to
client to check
with the
features
1 day
Wed
6/26/1
9
Wed
6/26/1
9
23 $0.00
5.2.4 Client's
Approval 1 day
Thu
6/27/1
9
Thu
6/27/1
9
24 $0.00
5.2.5 Implementing
Changes (if
required)
1 day
Fri
6/28/1
9
Fri
6/28/1
9
25 Developer $800.00
6 Testing 12 days Mon
7/1/19
Tue
7/16/1
9
$5,600.00
6.1 Performing
Unit Testing 2 days Mon
7/1/19
Tue
7/2/19 26 Tester $800.00
6.2 Performing
Black-box and
white box
testing of the
2 days Wed
7/3/19
Thu
7/4/19
28 Tester $800.00
4.6 Client's
Approval 1 day Mon
6/3/19
Mon
6/3/19 15 $0.00
5 Implementatio
n
19 days Tue
6/4/19
Fri
6/28/1
9
$15,300.0
0
5.1 Framework 11 days Tue
6/4/19
Tue
6/18/1
9
Hardware[1],Software[
1]
$10,500.0
0
5.1.1
Designing
a simple
interface
4 days Tue
6/4/19
Fri
6/7/19 16 Designer $3,200.00
5.1.2 Coding 7 days
Mon
6/10/1
9
Tue
6/18/1
9
19 Developer $5,600.00
5.2 Database 8 days
Wed
6/19/1
9
Fri
6/28/1
9
$4,800.00
5.2.1 Designing
the databse 2 days
Wed
6/19/1
9
Thu
6/20/1
9
20 Designer $1,600.00
5.2.2 Coding 3 days
Fri
6/21/1
9
Tue
6/25/1
9
22 Developer $2,400.00
5.2.3
Sending a
prototype to
client to check
with the
features
1 day
Wed
6/26/1
9
Wed
6/26/1
9
23 $0.00
5.2.4 Client's
Approval 1 day
Thu
6/27/1
9
Thu
6/27/1
9
24 $0.00
5.2.5 Implementing
Changes (if
required)
1 day
Fri
6/28/1
9
Fri
6/28/1
9
25 Developer $800.00
6 Testing 12 days Mon
7/1/19
Tue
7/16/1
9
$5,600.00
6.1 Performing
Unit Testing 2 days Mon
7/1/19
Tue
7/2/19 26 Tester $800.00
6.2 Performing
Black-box and
white box
testing of the
2 days Wed
7/3/19
Thu
7/4/19
28 Tester $800.00
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




