COMP247 Assignment 2: Soylent Co. Network Design Analysis Report
VerifiedAdded on 2022/11/14
|8
|1310
|56
Report
AI Summary
This report provides a comprehensive analysis of the network design for Soylent Co., a small consulting firm. The study begins with an executive summary outlining the company's network infrastructure, including the layout of its three-floor office space and the distribution of workstations across different departments. The core of the analysis focuses on identifying design flaws within the existing network, such as the use of daisy-chained switches, Nexus virtual port issues, and the direct connection of servers to the router. The report then proposes several solutions to rectify these issues, including the implementation of a physical star topology, the use of stackable switches, and the restructuring of the network's design using a hierarchical approach. Furthermore, the report addresses security concerns by recommending the installation of a firewall, IPS/IDS systems, and NAC control to prevent data breaches and unauthorized access. Finally, the report cites relevant references to support its findings and recommendations.

COMMUNICATION NETWORKING
Name
Instructor
Institution
Course
City
Date
Name
Instructor
Institution
Course
City
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMMUNICATION NETWORKING
Executive summary
Soylent is located in a three floor building with other three tenants. The company is
located in the 3rd floor which is on the left side. The 2nd floor is occupied by the human resource
department and the administration department. The 1st Floor is located by the engineering
department and the ground floor by the accounts department. Soylent’s network is connected via
a router with an interface address of 128.31.57.1. The administration department contains six
workstations, the engineering department have twelve workstations, the human resource
department has four workstations and the accounts department have eight workstations.
Question 1: Network design faults
Design flaws in a network is what that produces unwanted results in a certain network.
These design faults as those of Soylent’s network cannot be fixed by few commands at the CLI.
First to start with Soylent has four switches, all these switches are connected in sequence i.e. in a
ring form. The switches are connected as A-B-C-D where the network engineer just connected
them in what is referred to as daisy chain where each switch is on the top to bottom this is shown
by the figure below; it is a traditional way of connecting multiple switches.
Executive summary
Soylent is located in a three floor building with other three tenants. The company is
located in the 3rd floor which is on the left side. The 2nd floor is occupied by the human resource
department and the administration department. The 1st Floor is located by the engineering
department and the ground floor by the accounts department. Soylent’s network is connected via
a router with an interface address of 128.31.57.1. The administration department contains six
workstations, the engineering department have twelve workstations, the human resource
department has four workstations and the accounts department have eight workstations.
Question 1: Network design faults
Design flaws in a network is what that produces unwanted results in a certain network.
These design faults as those of Soylent’s network cannot be fixed by few commands at the CLI.
First to start with Soylent has four switches, all these switches are connected in sequence i.e. in a
ring form. The switches are connected as A-B-C-D where the network engineer just connected
them in what is referred to as daisy chain where each switch is on the top to bottom this is shown
by the figure below; it is a traditional way of connecting multiple switches.

Figure 1: Daisy chain
This type of connection owns certain drawbacks; first if one of the switch fails them may
be due lack of redundancy then the others will also be dragged in. Example if the engi9neering
department switch fails then all the other switch will automatically fail. This causes un-necessary
network performance issues. In here trafficjam is created in the chain and then slow up the speed
of the whole network. This means that the current switch connection which is Daisy chaining
switches is not recommended for this type of network.
Another issue is Nexus virtual port issue; this allows the network links that are physically
connected to the various switches to appear as one port channel to the third device. This issue
can result to connectivity issues i.e. the issue result to poor network connection. Other issues
which are visible on the network is that the engineering file server is connected directly to the
router which overloads the organization router in performing unnecessary functions. This goes
the same with the email web-server which has connected directly to the router. Lastly, the
network have utilized a ring type of topology. One of the issues with this type of network
topology is that the data packets must pass all the network nodes. Also the entire organizational
network is over-reliant on the wire which connects the components [1].
This type of connection owns certain drawbacks; first if one of the switch fails them may
be due lack of redundancy then the others will also be dragged in. Example if the engi9neering
department switch fails then all the other switch will automatically fail. This causes un-necessary
network performance issues. In here trafficjam is created in the chain and then slow up the speed
of the whole network. This means that the current switch connection which is Daisy chaining
switches is not recommended for this type of network.
Another issue is Nexus virtual port issue; this allows the network links that are physically
connected to the various switches to appear as one port channel to the third device. This issue
can result to connectivity issues i.e. the issue result to poor network connection. Other issues
which are visible on the network is that the engineering file server is connected directly to the
router which overloads the organization router in performing unnecessary functions. This goes
the same with the email web-server which has connected directly to the router. Lastly, the
network have utilized a ring type of topology. One of the issues with this type of network
topology is that the data packets must pass all the network nodes. Also the entire organizational
network is over-reliant on the wire which connects the components [1].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
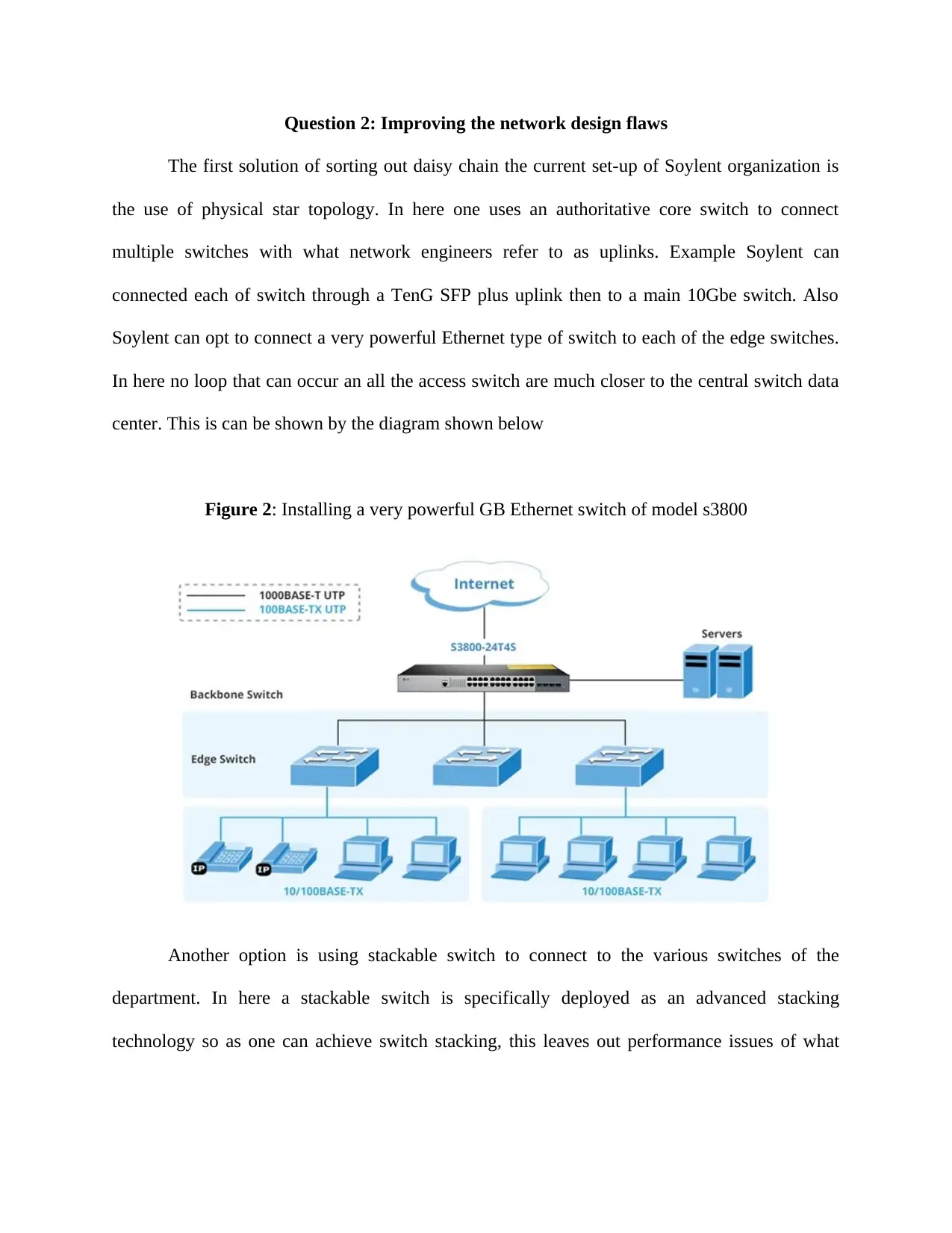
Question 2: Improving the network design flaws
The first solution of sorting out daisy chain the current set-up of Soylent organization is
the use of physical star topology. In here one uses an authoritative core switch to connect
multiple switches with what network engineers refer to as uplinks. Example Soylent can
connected each of switch through a TenG SFP plus uplink then to a main 10Gbe switch. Also
Soylent can opt to connect a very powerful Ethernet type of switch to each of the edge switches.
In here no loop that can occur an all the access switch are much closer to the central switch data
center. This is can be shown by the diagram shown below
Figure 2: Installing a very powerful GB Ethernet switch of model s3800
Another option is using stackable switch to connect to the various switches of the
department. In here a stackable switch is specifically deployed as an advanced stacking
technology so as one can achieve switch stacking, this leaves out performance issues of what
The first solution of sorting out daisy chain the current set-up of Soylent organization is
the use of physical star topology. In here one uses an authoritative core switch to connect
multiple switches with what network engineers refer to as uplinks. Example Soylent can
connected each of switch through a TenG SFP plus uplink then to a main 10Gbe switch. Also
Soylent can opt to connect a very powerful Ethernet type of switch to each of the edge switches.
In here no loop that can occur an all the access switch are much closer to the central switch data
center. This is can be shown by the diagram shown below
Figure 2: Installing a very powerful GB Ethernet switch of model s3800
Another option is using stackable switch to connect to the various switches of the
department. In here a stackable switch is specifically deployed as an advanced stacking
technology so as one can achieve switch stacking, this leaves out performance issues of what
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

network engineers refer to as clumsy daisy chaining technology. This is as shown by the diagram
below
Figure 3: Deploying s380-0 stack switch
To sort out the Nexus virtual port issue one needs to create a port channel 500 on may be
switch one and then associate it to those ports that connects to e1/26 and e1/25 on the second
switch. Third the engineering server needs to be connected to the engineering switch to avoid
overloading the organization router from performing unnecessary functions. Instead of ring type
of topology the company needs to employ a hierarchical network design. This will divide the
network into seven layers. This will helps sub-dividing the network into several layers. The
access layer is used to aggregates the organization users from the numerous workgroups. The
main layer is used to provide high speed connection between the edge distribution and edge
distribution, and the access layer. The other layers are used to provide additional security
between the enterprise edge and the enterprise campus. Specifically the edge distribution layer is
used to protect the organization network from four types of threats which are unauthorized
access, network reconnaissance, packet sniffers, and IP spoofing [2].
Question 3: Security
below
Figure 3: Deploying s380-0 stack switch
To sort out the Nexus virtual port issue one needs to create a port channel 500 on may be
switch one and then associate it to those ports that connects to e1/26 and e1/25 on the second
switch. Third the engineering server needs to be connected to the engineering switch to avoid
overloading the organization router from performing unnecessary functions. Instead of ring type
of topology the company needs to employ a hierarchical network design. This will divide the
network into seven layers. This will helps sub-dividing the network into several layers. The
access layer is used to aggregates the organization users from the numerous workgroups. The
main layer is used to provide high speed connection between the edge distribution and edge
distribution, and the access layer. The other layers are used to provide additional security
between the enterprise edge and the enterprise campus. Specifically the edge distribution layer is
used to protect the organization network from four types of threats which are unauthorized
access, network reconnaissance, packet sniffers, and IP spoofing [2].
Question 3: Security

From the current design, it is evident that Soylent Co can very easily suffer a data breach.
To pre3vent this the organization needs to install a firewall between the ISP (Internet Service
Provider) and the organization router. This will effectively isolates the organization network
from external threats. The firewall provides four types of controls which are service control,
direction control, behavior control, and user control. With service control one can determine of
internet services which can be accessed. Directional control determines the direction of a certain
service request. Behavior control is used to control certain services example this control is used
to filter e-mails so as to eliminate spams [3].
Second the organization needs to install IPS/IDS systems. The role that will performed by
IPS is to identify those traffic which will be allowed to move forwards. Specifically the IPS
looks for the dangerous incoming packets which violates certain network policies and certain
rules. Specifically the IDS is used to identify log violations. It is specifically used to perform
passive monitoring.
Third from the network it is evident that anyone can view what other departments are
doing. Example the engineering department is able to view what human resource department is
doing. This can be prevented by implementing NAC control. NAC is a control plane solution
which can be deployed anywhere in an organization network. As suggested in the previous
sections, the organization needs to have a data center module, hence the organization needs to
deploy a NAC control plane which will be used to intercept what network engineers refer to as
DHCP requests from all the devices connecting to the data center. This will then profile each
user or device and authenticate them against the identity source. To do this one requires to define
authentication and profiling rules on the NAC server. This will help in determining the resources
that certain devices and users have to access to [4].
To pre3vent this the organization needs to install a firewall between the ISP (Internet Service
Provider) and the organization router. This will effectively isolates the organization network
from external threats. The firewall provides four types of controls which are service control,
direction control, behavior control, and user control. With service control one can determine of
internet services which can be accessed. Directional control determines the direction of a certain
service request. Behavior control is used to control certain services example this control is used
to filter e-mails so as to eliminate spams [3].
Second the organization needs to install IPS/IDS systems. The role that will performed by
IPS is to identify those traffic which will be allowed to move forwards. Specifically the IPS
looks for the dangerous incoming packets which violates certain network policies and certain
rules. Specifically the IDS is used to identify log violations. It is specifically used to perform
passive monitoring.
Third from the network it is evident that anyone can view what other departments are
doing. Example the engineering department is able to view what human resource department is
doing. This can be prevented by implementing NAC control. NAC is a control plane solution
which can be deployed anywhere in an organization network. As suggested in the previous
sections, the organization needs to have a data center module, hence the organization needs to
deploy a NAC control plane which will be used to intercept what network engineers refer to as
DHCP requests from all the devices connecting to the data center. This will then profile each
user or device and authenticate them against the identity source. To do this one requires to define
authentication and profiling rules on the NAC server. This will help in determining the resources
that certain devices and users have to access to [4].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
[1] S. C. -H. Huang, Network security., Chicago: John & Wiley Press, 2018.
[1] S. C. -H. Huang, Network security., Chicago: John & Wiley Press, 2018.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[2] M. Strebe, Network Security JumpStart: Computer and network security basics, New York:
Hoben Press, 2006.
[3] N. Krawetz, Introduction to Network Security, Boston: O'Reilly Media Press, 2008.
[4] A. Perez, Network Security, New Jersey: John Wiley & Sons Press, 2017.
Hoben Press, 2006.
[3] N. Krawetz, Introduction to Network Security, Boston: O'Reilly Media Press, 2008.
[4] A. Perez, Network Security, New Jersey: John Wiley & Sons Press, 2017.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





