Network Problem Identification and Redesign for Soylent Co. (COMP247)
VerifiedAdded on 2022/11/13
|10
|1623
|218
Report
AI Summary
This report provides a comprehensive analysis of Soylent Co.'s upgraded network, identifying existing faults such as bandwidth limitations, network outages due to single points of failure, and security vulnerabilities. The report then proposes a redesigned network architecture utilizing a three-layer hierarchical model with VLANs to segment network traffic and improve security. Detailed IP addressing schemes, including subnetting calculations for each VLAN, are presented. Furthermore, the report emphasizes the implementation of a firewall to protect against external threats. The report concludes by summarizing the analysis, the proposed design, and the importance of the implemented security measures, highlighting the benefits of the redesigned network for Soylent Co.

Running head: NETWORK PROBLEM IDENTIFICATION
Network Problem Identification
Name of the Student
Name of the University
Author Note
Network Problem Identification
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK PROBLEM IDENTIFICATION
Summary
The purpose of the report is to analyse the upgraded network of Soylent and identify the
faults that exists there and based on that propose an improved design with justification. The
report also involves investigating the security of the network and implement effective
security in the improved design. First the report talks about the faults that exists in the
network and then it presents a redesigned network and tries to justify the changes that are
applied. The redesigned network consists of VLANs that require subnetting of the major
network and the respective IP addressing details and calculations are listed. Then, after
discussing further about the security, the report ends with concluding notes.
Summary
The purpose of the report is to analyse the upgraded network of Soylent and identify the
faults that exists there and based on that propose an improved design with justification. The
report also involves investigating the security of the network and implement effective
security in the improved design. First the report talks about the faults that exists in the
network and then it presents a redesigned network and tries to justify the changes that are
applied. The redesigned network consists of VLANs that require subnetting of the major
network and the respective IP addressing details and calculations are listed. Then, after
discussing further about the security, the report ends with concluding notes.

2NETWORK PROBLEM IDENTIFICATION
Table of Contents
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
Identification of Faults...........................................................................................................3
Solution..................................................................................................................................4
IP Addressing.........................................................................................................................5
Security..................................................................................................................................6
Conclusion..................................................................................................................................7
References..................................................................................................................................7
Table of Contents
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
Identification of Faults...........................................................................................................3
Solution..................................................................................................................................4
IP Addressing.........................................................................................................................5
Security..................................................................................................................................6
Conclusion..................................................................................................................................7
References..................................................................................................................................7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK PROBLEM IDENTIFICATION
Introduction
This report analyses the network of Soylent and identifies the faults existing there
based on which an improved design is proposed with justification. Also the report
investigates the security of the network and implements effective security in the improved
design. The report begins by discussing about the faults existing in the network and then it
presents a redesigned network and tries to justify the changes that are applied [1]. The
redesigned network consists of VLANs that require subnetting of the major network and the
respective IP addressing details and calculations are listed. Then, after discussing further
about the security, the report ends with concluding notes.
Discussion
Identification of Faults
Problems Soylent can suffer from their upgraded network can be many. Some of these
problems can be reduced bandwidth, increased ping and interruptions resulting from too
much physical branching of the ISP network. Presently the firm obtains one network through
the switch of engineering department, one for the web and email server and another for the
printer. The network from engineering department gets branched through switch after switch
of other departments till it can provide network to respective devices thereby affecting
network performance. While a separate connection for the web and mail server is
understandable it is totally a waste of money and networking potential to obtain a connection
solely to provide access to one printer. Any network failure in the switch of the engineering
department can result in complete network outage except for one printer which is pretty much
useless without a host and the web and mail servers which again becomes unusable if the
devices trying to access them themselves are devoid of network connectivity. Members of the
engineering department can also alter network configuration to suit their benefits. Thus, the
Introduction
This report analyses the network of Soylent and identifies the faults existing there
based on which an improved design is proposed with justification. Also the report
investigates the security of the network and implements effective security in the improved
design. The report begins by discussing about the faults existing in the network and then it
presents a redesigned network and tries to justify the changes that are applied [1]. The
redesigned network consists of VLANs that require subnetting of the major network and the
respective IP addressing details and calculations are listed. Then, after discussing further
about the security, the report ends with concluding notes.
Discussion
Identification of Faults
Problems Soylent can suffer from their upgraded network can be many. Some of these
problems can be reduced bandwidth, increased ping and interruptions resulting from too
much physical branching of the ISP network. Presently the firm obtains one network through
the switch of engineering department, one for the web and email server and another for the
printer. The network from engineering department gets branched through switch after switch
of other departments till it can provide network to respective devices thereby affecting
network performance. While a separate connection for the web and mail server is
understandable it is totally a waste of money and networking potential to obtain a connection
solely to provide access to one printer. Any network failure in the switch of the engineering
department can result in complete network outage except for one printer which is pretty much
useless without a host and the web and mail servers which again becomes unusable if the
devices trying to access them themselves are devoid of network connectivity. Members of the
engineering department can also alter network configuration to suit their benefits. Thus, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4NETWORK PROBLEM IDENTIFICATION
current design can encourage misuse of privileges [5]. The network also lacks any form of
security measures and hence can be compromised very easily by cyber criminals, information
security threats, vulnerabilities as well as internal rogue employees resulting in serious
damages for the firm Soylent.
Solution
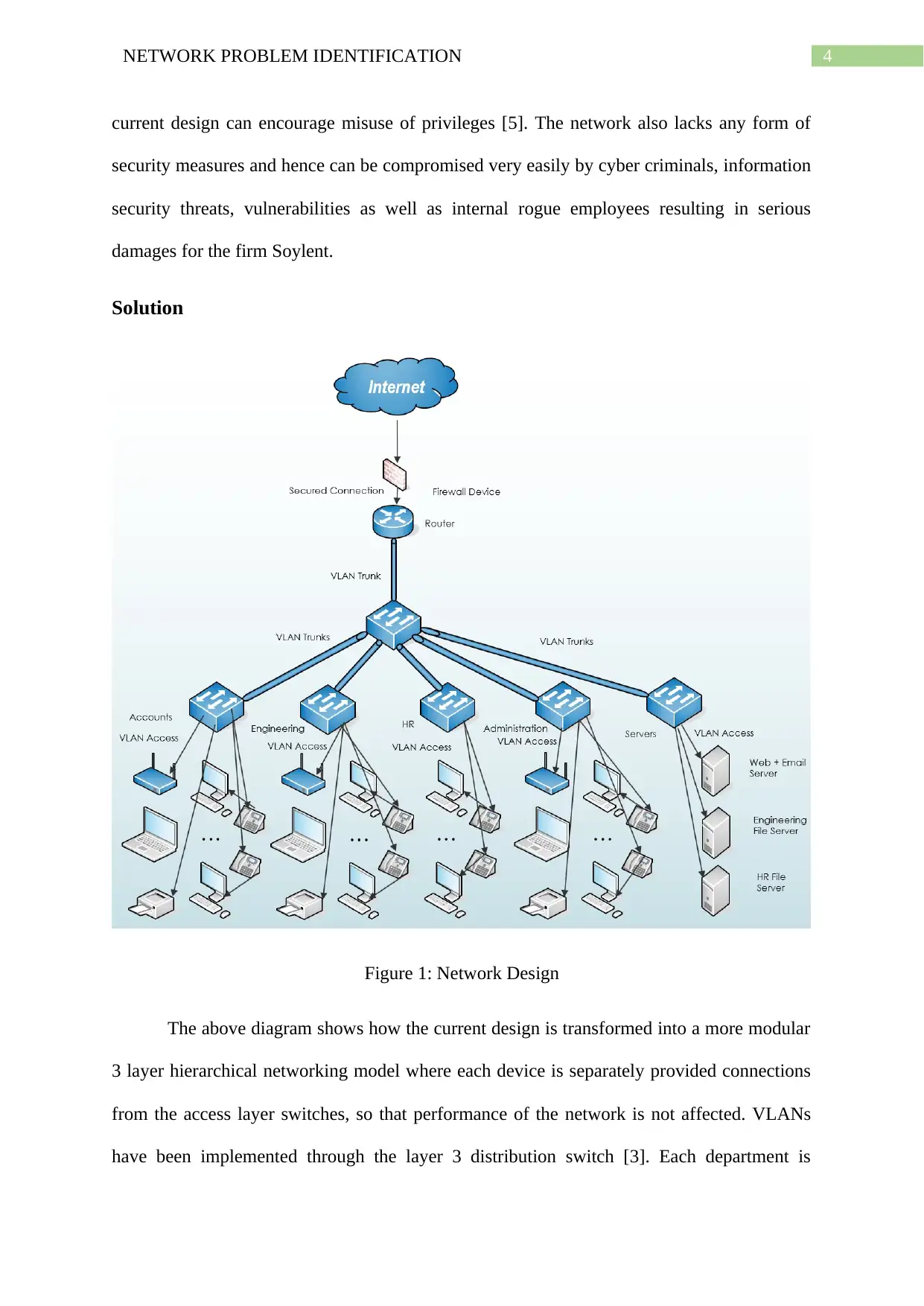
Figure 1: Network Design
The above diagram shows how the current design is transformed into a more modular
3 layer hierarchical networking model where each device is separately provided connections
from the access layer switches, so that performance of the network is not affected. VLANs
have been implemented through the layer 3 distribution switch [3]. Each department is
current design can encourage misuse of privileges [5]. The network also lacks any form of
security measures and hence can be compromised very easily by cyber criminals, information
security threats, vulnerabilities as well as internal rogue employees resulting in serious
damages for the firm Soylent.
Solution
Figure 1: Network Design
The above diagram shows how the current design is transformed into a more modular
3 layer hierarchical networking model where each device is separately provided connections
from the access layer switches, so that performance of the network is not affected. VLANs
have been implemented through the layer 3 distribution switch [3]. Each department is

5NETWORK PROBLEM IDENTIFICATION
assigned a specific VLAN, the servers are clubbed to another VLAN. These VLANs can help
the firm better manage the access levels for the different departments through separate sub
networks. Individual devices are connected to specific VLANs through switchport mode
access. The respective switches are connected to distribution layer switch in trunk mode so
communications from multiple VLANs can be made possible. The distribution layer switch
is connected to the router through switchport mode trunk so the different sub networks are all
accessible [6]. As a result, communication between the devices of all the five VLANs is
possible even though these devices can be managed independently. In this way unauthorized
access of the servers from internal department networks can be prevented. Having different
VLANs with unique sub networks also eliminate chances of slowdown in networks. The
overall network is also secured by a firewall device before it reaches the router [2]. This
ensures the network is difficult to penetrate by foreign cyber security threats like malware,
denial of service attacks and hackers [7]. VLANs involves creating virtual networks from a
single network and hence sub networks need to be created for every VLAN that is to be
created [8]. The IP addressing is given below.
IP Addressing
Departm
ents
IP
Nee
ds
IP
Allocat
ion
Network
Address
CID
R
Subnet Mask
Assignable
IPs
Broadcast
Address
Eng 27 30
128.31.57.
0
/27
255.255.255.
224
128.31.57.1
-
128.31.57.3
0
128.31.57.3
1
Acc 19 30 128.31.57.
32
/27 255.255.255.
224
128.31.57.3
3 -
128.31.57.6
assigned a specific VLAN, the servers are clubbed to another VLAN. These VLANs can help
the firm better manage the access levels for the different departments through separate sub
networks. Individual devices are connected to specific VLANs through switchport mode
access. The respective switches are connected to distribution layer switch in trunk mode so
communications from multiple VLANs can be made possible. The distribution layer switch
is connected to the router through switchport mode trunk so the different sub networks are all
accessible [6]. As a result, communication between the devices of all the five VLANs is
possible even though these devices can be managed independently. In this way unauthorized
access of the servers from internal department networks can be prevented. Having different
VLANs with unique sub networks also eliminate chances of slowdown in networks. The
overall network is also secured by a firewall device before it reaches the router [2]. This
ensures the network is difficult to penetrate by foreign cyber security threats like malware,
denial of service attacks and hackers [7]. VLANs involves creating virtual networks from a
single network and hence sub networks need to be created for every VLAN that is to be
created [8]. The IP addressing is given below.
IP Addressing
Departm
ents
IP
Nee
ds
IP
Allocat
ion
Network
Address
CID
R
Subnet Mask
Assignable
IPs
Broadcast
Address
Eng 27 30
128.31.57.
0
/27
255.255.255.
224
128.31.57.1
-
128.31.57.3
0
128.31.57.3
1
Acc 19 30 128.31.57.
32
/27 255.255.255.
224
128.31.57.3
3 -
128.31.57.6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6NETWORK PROBLEM IDENTIFICATION
128.31.57.6
2
3
Adm 14 14
128.31.57.
64
/28
255.255.255.
240
128.31.57.6
5 -
128.31.57.7
8
128.31.57.7
9
HRM 10 14
128.31.57.
80
/28
255.255.255.
240
128.31.57.8
1 -
128.31.57.9
4
128.31.57.9
5
Servers 3 6
128.31.5
7.96
/29
255.255.255
.248
128.31.57.
97 -
128.31.57.
102
128.31.57.
103
Security
The two key ways by which security in the network has been ensured are –
installation of a firewall device and managing the different departments using VLANs. The
firewall helps in securing the network from external security threats like hackers, malware,
exploits, vulnerability while VLANs help in managing the access levels of individual devices
of various departments without affect interdepartmental communication [4]. Denial of service
attacks and exploit attempts are very common for computer networks connected over the
internet. Getting compromised by such attacks can lead to theft of sensitive data, network
outage, damages to computer hardware and networking equipment, attackers charging
ransoms for recovery. The VLANs help isolate the networks of the different networks of the
128.31.57.6
2
3
Adm 14 14
128.31.57.
64
/28
255.255.255.
240
128.31.57.6
5 -
128.31.57.7
8
128.31.57.7
9
HRM 10 14
128.31.57.
80
/28
255.255.255.
240
128.31.57.8
1 -
128.31.57.9
4
128.31.57.9
5
Servers 3 6
128.31.5
7.96
/29
255.255.255
.248
128.31.57.
97 -
128.31.57.
102
128.31.57.
103
Security
The two key ways by which security in the network has been ensured are –
installation of a firewall device and managing the different departments using VLANs. The
firewall helps in securing the network from external security threats like hackers, malware,
exploits, vulnerability while VLANs help in managing the access levels of individual devices
of various departments without affect interdepartmental communication [4]. Denial of service
attacks and exploit attempts are very common for computer networks connected over the
internet. Getting compromised by such attacks can lead to theft of sensitive data, network
outage, damages to computer hardware and networking equipment, attackers charging
ransoms for recovery. The VLANs help isolate the networks of the different networks of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK PROBLEM IDENTIFICATION
four departments as well as the servers without affecting intercommunications between them.
This prevents members of a particular department have unauthorized access to other
resources and devices which means the engineering department can no longer view the
contents of any of the servers. VLANs also help isolating security failures in the network as it
offers segmentation of the network such that if the engineering department gets compromised
the by a cyber-attack, it can be prevented from spreading to the accounts and other
departments.
Conclusion
This report analyses the network of Soylent and identifies the faults existing there
based on which an improved design is proposed with justification. Also the report
investigates the security of the network and implements effective security in the improved
design. The report begins by discussing about the faults existing in the network and then it
presents a redesigned network and tries to justify the changes that are applied. The redesigned
network consists of VLANs that require subnetting of the major network and the respective
IP addressing details and calculations are listed. Then the report ends after discussing further
about the security.
four departments as well as the servers without affecting intercommunications between them.
This prevents members of a particular department have unauthorized access to other
resources and devices which means the engineering department can no longer view the
contents of any of the servers. VLANs also help isolating security failures in the network as it
offers segmentation of the network such that if the engineering department gets compromised
the by a cyber-attack, it can be prevented from spreading to the accounts and other
departments.
Conclusion
This report analyses the network of Soylent and identifies the faults existing there
based on which an improved design is proposed with justification. Also the report
investigates the security of the network and implements effective security in the improved
design. The report begins by discussing about the faults existing in the network and then it
presents a redesigned network and tries to justify the changes that are applied. The redesigned
network consists of VLANs that require subnetting of the major network and the respective
IP addressing details and calculations are listed. Then the report ends after discussing further
about the security.

8NETWORK PROBLEM IDENTIFICATION
References
[1] A. Babay, C. Danilov, J. Lane, M. Miskin-Amir, D. Obenshain, J. Schultz, J. Stanton, T.
Tantillo, and Y. Amir, Structured overlay networks for a new generation of internet services.
In 2017 IEEE 37th International Conference on Distributed Computing Systems
(ICDCS) (pp. 1771-1779). IEEE. , 2017, June.
[2] D.E. Bassey, J.C. Ogbulezie, and E.O. Effiom, Local Area Network (LAN) Mock-up and
the Prevention of Cybernetics Related Crimes in Nigermills Company using Firewall
Security Device. International Journal of Scientific & Engineering Research, 7(3), pp.1124-
1130. , 2016.
[3] J. Lin, C. Wan, Y. Song, R. Huang, X. Chen, W. Guo, Y. Zong, and Y. Shi, Situation
awareness of active distribution network: Roadmap, technologies, and bottlenecks. CSEE
Journal of Power and Energy Systems, 2(3), pp.35-42. , 2016.
[4] L. Yong, L. Dunbar, M. Toy, A. Isaac, and V. Manral, Use Cases for Data Center
Network Virtualization Overlay Networks (No. RFC 8151). , 2017.
[5] S. Zerkane, D. Espes, P. Le Parc, and F. Cuppens, Vulnerability analysis of software
defined networking. In International Symposium on Foundations and Practice of
Security (pp. 97-116). Springer, Cham. , 2016, October.
[6] T. Nelson, A.D. Ferguson, D. Yu, R. Fonseca, and S. Krishnamurthi, Exodus: toward
automatic migration of enterprise network configurations to SDNs. In Proceedings of the 1st
ACM SIGCOMM Symposium on Software Defined Networking Research (p. 13). ACM. ,
2015, June.
[7] W. Yang, and C. Fung, A survey on security in network functions virtualization. In 2016
IEEE NetSoft Conference and Workshops (NetSoft) (pp. 15-19). IEEE. , 2016, June.
References
[1] A. Babay, C. Danilov, J. Lane, M. Miskin-Amir, D. Obenshain, J. Schultz, J. Stanton, T.
Tantillo, and Y. Amir, Structured overlay networks for a new generation of internet services.
In 2017 IEEE 37th International Conference on Distributed Computing Systems
(ICDCS) (pp. 1771-1779). IEEE. , 2017, June.
[2] D.E. Bassey, J.C. Ogbulezie, and E.O. Effiom, Local Area Network (LAN) Mock-up and
the Prevention of Cybernetics Related Crimes in Nigermills Company using Firewall
Security Device. International Journal of Scientific & Engineering Research, 7(3), pp.1124-
1130. , 2016.
[3] J. Lin, C. Wan, Y. Song, R. Huang, X. Chen, W. Guo, Y. Zong, and Y. Shi, Situation
awareness of active distribution network: Roadmap, technologies, and bottlenecks. CSEE
Journal of Power and Energy Systems, 2(3), pp.35-42. , 2016.
[4] L. Yong, L. Dunbar, M. Toy, A. Isaac, and V. Manral, Use Cases for Data Center
Network Virtualization Overlay Networks (No. RFC 8151). , 2017.
[5] S. Zerkane, D. Espes, P. Le Parc, and F. Cuppens, Vulnerability analysis of software
defined networking. In International Symposium on Foundations and Practice of
Security (pp. 97-116). Springer, Cham. , 2016, October.
[6] T. Nelson, A.D. Ferguson, D. Yu, R. Fonseca, and S. Krishnamurthi, Exodus: toward
automatic migration of enterprise network configurations to SDNs. In Proceedings of the 1st
ACM SIGCOMM Symposium on Software Defined Networking Research (p. 13). ACM. ,
2015, June.
[7] W. Yang, and C. Fung, A survey on security in network functions virtualization. In 2016
IEEE NetSoft Conference and Workshops (NetSoft) (pp. 15-19). IEEE. , 2016, June.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK PROBLEM IDENTIFICATION
[8] Y. Lee, H. Park, and Y. Lee, Ip geolocation with a crowd-sourcing broadband
performance tool. ACM SIGCOMM Computer Communication Review, 46(1), pp.12-20. ,
2016.
[8] Y. Lee, H. Park, and Y. Lee, Ip geolocation with a crowd-sourcing broadband
performance tool. ACM SIGCOMM Computer Communication Review, 46(1), pp.12-20. ,
2016.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





