Analysis of Spectre, Meltdown, Countermeasures, and Future Impact
VerifiedAdded on 2021/04/16
|17
|4180
|48
Report
AI Summary
This report provides a detailed analysis of the Spectre and Meltdown vulnerabilities, including their operational mechanisms, differences, and critical factors. It explores the vulnerabilities' impact on computer systems, particularly focusing on the exploitation of speculative execution and branch prediction. The report then delves into the various countermeasures and patching processes implemented to mitigate these vulnerabilities, covering both software and hardware approaches. Finally, it offers predictions on the future impact of Spectre and Meltdown, considering the ongoing developments in security measures and their potential effects on system performance and design. The report's structure includes an introduction, detailed sections on Spectre and Meltdown, a comparison of the two, critical analysis, countermeasure discussions, vulnerability fixing, and future impact predictions, followed by a conclusion and references.

Running head: SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
Spectre, Meltdown, Countermeasures and Future Impact
Name of student
Name of University
Author’s Note
Spectre, Meltdown, Countermeasures and Future Impact
Name of student
Name of University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
Executive Summary
This report discusses about the Meldown and Spectre attack following with the table that
differentiate between the two attacks. The critical analysis of both the attacks has been provided
that has identified several factors for this attack. In the later section, counter measures of the
vulnerabilities have been discussed and the process of fixing those vulnerabilities. Finally
provide the future impact of the Meltdown and Spectre vulnerabilities.
Executive Summary
This report discusses about the Meldown and Spectre attack following with the table that
differentiate between the two attacks. The critical analysis of both the attacks has been provided
that has identified several factors for this attack. In the later section, counter measures of the
vulnerabilities have been discussed and the process of fixing those vulnerabilities. Finally
provide the future impact of the Meltdown and Spectre vulnerabilities.

2SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
Table of Contents
Introduction..................................................................................................................................................3
Spectre.........................................................................................................................................................3
Meltdown.....................................................................................................................................................4
Difference between Meltdown and Spectre.................................................................................................4
Critical analysis of Meltdown and Spectre..................................................................................................5
Counter measures of the Spectre and Meltdown vulnerabilities.................................................................9
Fixing vulnerabilities of Meltdown and Spectre.......................................................................................11
Predictions on the future impact of Spectre and Meltdown vulnerabilities...............................................12
Conclusion.................................................................................................................................................12
References..................................................................................................................................................14
Table of Contents
Introduction..................................................................................................................................................3
Spectre.........................................................................................................................................................3
Meltdown.....................................................................................................................................................4
Difference between Meltdown and Spectre.................................................................................................4
Critical analysis of Meltdown and Spectre..................................................................................................5
Counter measures of the Spectre and Meltdown vulnerabilities.................................................................9
Fixing vulnerabilities of Meltdown and Spectre.......................................................................................11
Predictions on the future impact of Spectre and Meltdown vulnerabilities...............................................12
Conclusion.................................................................................................................................................12
References..................................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
Introduction
The study will be about the Meltdown and Spectre attack and provide detail information
about the vulnerabilities and software patches done by these attacks. The study has analysed that
isolation is the basic computer premises for security. As machines of Kernel are the most inner
sanctum that has access to the memory in the computer, it has some bug that allows low-
privilege process to access the Kernel memory of the computer. The study has also revealed the
information about the malicious software attack that has done through Meltdown and the data
stolen by the Spectre. Finally, the study had discussed about the future impact of Meltdown and
Spectre.
Spectre
Spectre can break down the isolation between different applications. It helps attackers to
get an error-free program to leak secret information (Kocher et al. 2018). The safety checks
increase the attack on the surface that makes applications to be more susceptible to Spectre. The
patches of Spectre reported to significantly reduce the performance on the old computers and to
new Core platforms of eight-generation. The vulnerability of Spectre affects the modern
microprocessor through which the branch prediction performed. The attackers can extract
information from the private data by using the timing attack that has affected the processor of
speculative execution which has resulted from the branch misprediction (Arondekar and Patel
2016). The data stored on another website or the browser's memory can be read easily by a
particular website. The attackers may be able to read the memory content that they have access,
and thus some sensitive data are potentially achieved.
Introduction
The study will be about the Meltdown and Spectre attack and provide detail information
about the vulnerabilities and software patches done by these attacks. The study has analysed that
isolation is the basic computer premises for security. As machines of Kernel are the most inner
sanctum that has access to the memory in the computer, it has some bug that allows low-
privilege process to access the Kernel memory of the computer. The study has also revealed the
information about the malicious software attack that has done through Meltdown and the data
stolen by the Spectre. Finally, the study had discussed about the future impact of Meltdown and
Spectre.
Spectre
Spectre can break down the isolation between different applications. It helps attackers to
get an error-free program to leak secret information (Kocher et al. 2018). The safety checks
increase the attack on the surface that makes applications to be more susceptible to Spectre. The
patches of Spectre reported to significantly reduce the performance on the old computers and to
new Core platforms of eight-generation. The vulnerability of Spectre affects the modern
microprocessor through which the branch prediction performed. The attackers can extract
information from the private data by using the timing attack that has affected the processor of
speculative execution which has resulted from the branch misprediction (Arondekar and Patel
2016). The data stored on another website or the browser's memory can be read easily by a
particular website. The attackers may be able to read the memory content that they have access,
and thus some sensitive data are potentially achieved.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
Meltdown
Meltdown can break down the isolation between the operating system and the user
application. With this attack, the program gets access to the memory (Maisuradze and Rossow
2018). It also gets access to the secret of other program and operating system. If the user
computer has a vulnerable processor and runs an unpatched operating system, in that case, it is
unsafe for the sensitive information to work because it leads to leakage of the information. The
application is in both cloud infrastructure and personal computers. Meltdown read the machines
entire kernel memory that has executed. It includes all the physical memory and maps it to the
kernel region. Meltdown works on almost all the operating system that is vulnerable. It mainly
exploits the information of the side-channel available on some of the modern processors that
include Intel 2010 microarchitectures and other vendors of CPU (Ahmed 2016). The hardware
vulnerability of Meltdown affects the IBM POWER processors, an ARM based microprocessor,
and Intel x86 microprocessors (Lipp et al. 2018). A wide range of system has affected by
Meltdown, the most recent system and the patched versions are macOS, Linux, iOS or Windows
(Clark et al. 2017). It has its impact on the embedded devices, networking equipment of ARM
processor, cloud services and servers. There is loss of performance also produce by the patches
of meltdown.
Difference between Meltdown and Spectre
Meltdown Spectre
Method Execution that is Speculative+
Escalation with Intel Privileges
Execution that is Speculative + prediction
of branch
Meltdown
Meltdown can break down the isolation between the operating system and the user
application. With this attack, the program gets access to the memory (Maisuradze and Rossow
2018). It also gets access to the secret of other program and operating system. If the user
computer has a vulnerable processor and runs an unpatched operating system, in that case, it is
unsafe for the sensitive information to work because it leads to leakage of the information. The
application is in both cloud infrastructure and personal computers. Meltdown read the machines
entire kernel memory that has executed. It includes all the physical memory and maps it to the
kernel region. Meltdown works on almost all the operating system that is vulnerable. It mainly
exploits the information of the side-channel available on some of the modern processors that
include Intel 2010 microarchitectures and other vendors of CPU (Ahmed 2016). The hardware
vulnerability of Meltdown affects the IBM POWER processors, an ARM based microprocessor,
and Intel x86 microprocessors (Lipp et al. 2018). A wide range of system has affected by
Meltdown, the most recent system and the patched versions are macOS, Linux, iOS or Windows
(Clark et al. 2017). It has its impact on the embedded devices, networking equipment of ARM
processor, cloud services and servers. There is loss of performance also produce by the patches
of meltdown.
Difference between Meltdown and Spectre
Meltdown Spectre
Method Execution that is Speculative+
Escalation with Intel Privileges
Execution that is Speculative + prediction
of branch
5SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
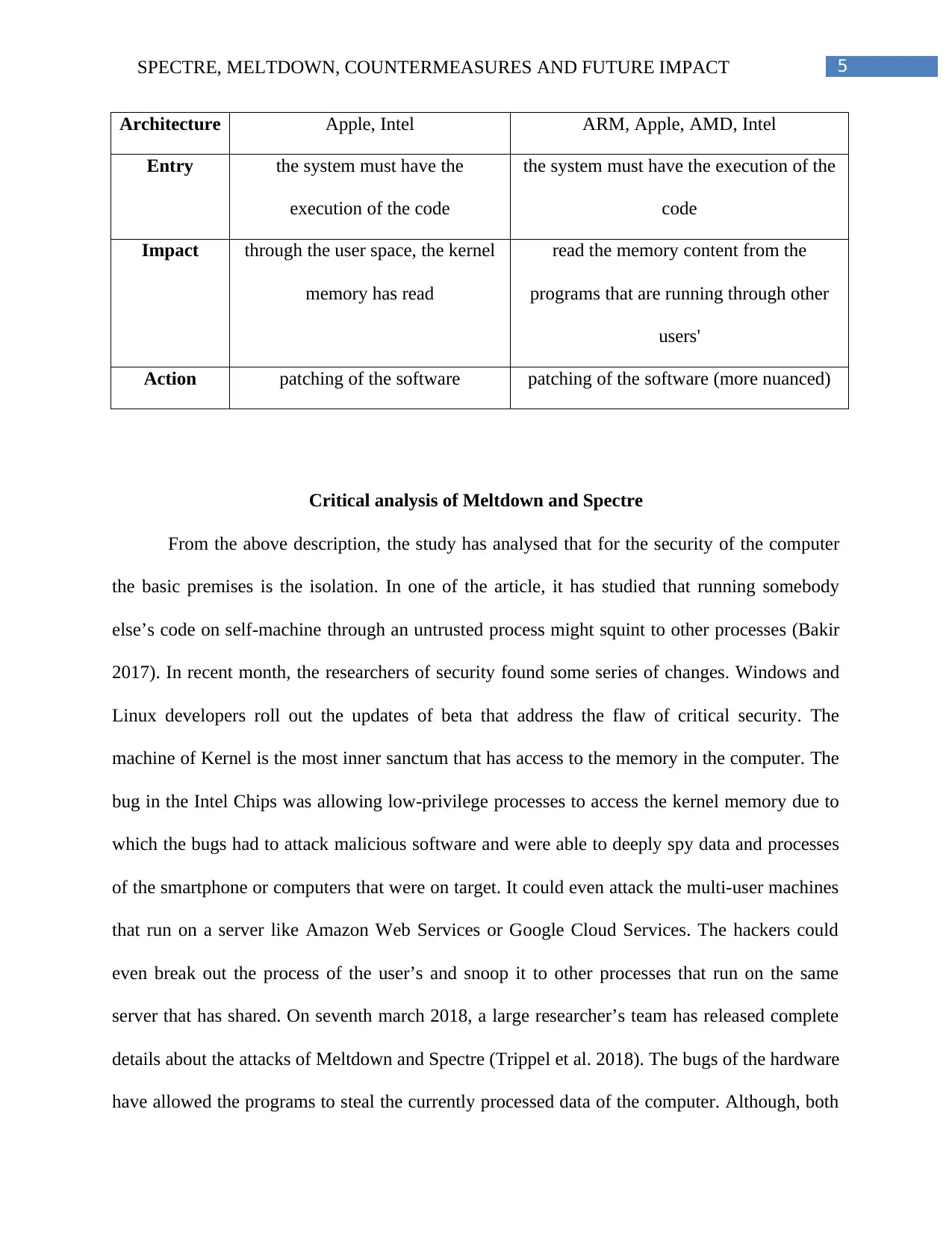
Architecture Apple, Intel ARM, Apple, AMD, Intel
Entry the system must have the
execution of the code
the system must have the execution of the
code
Impact through the user space, the kernel
memory has read
read the memory content from the
programs that are running through other
users'
Action patching of the software patching of the software (more nuanced)
Critical analysis of Meltdown and Spectre
From the above description, the study has analysed that for the security of the computer
the basic premises is the isolation. In one of the article, it has studied that running somebody
else’s code on self-machine through an untrusted process might squint to other processes (Bakir
2017). In recent month, the researchers of security found some series of changes. Windows and
Linux developers roll out the updates of beta that address the flaw of critical security. The
machine of Kernel is the most inner sanctum that has access to the memory in the computer. The
bug in the Intel Chips was allowing low-privilege processes to access the kernel memory due to
which the bugs had to attack malicious software and were able to deeply spy data and processes
of the smartphone or computers that were on target. It could even attack the multi-user machines
that run on a server like Amazon Web Services or Google Cloud Services. The hackers could
even break out the process of the user’s and snoop it to other processes that run on the same
server that has shared. On seventh march 2018, a large researcher’s team has released complete
details about the attacks of Meltdown and Spectre (Trippel et al. 2018). The bugs of the hardware
have allowed the programs to steal the currently processed data of the computer. Although, both
Architecture Apple, Intel ARM, Apple, AMD, Intel
Entry the system must have the
execution of the code
the system must have the execution of the
code
Impact through the user space, the kernel
memory has read
read the memory content from the
programs that are running through other
users'
Action patching of the software patching of the software (more nuanced)
Critical analysis of Meltdown and Spectre
From the above description, the study has analysed that for the security of the computer
the basic premises is the isolation. In one of the article, it has studied that running somebody
else’s code on self-machine through an untrusted process might squint to other processes (Bakir
2017). In recent month, the researchers of security found some series of changes. Windows and
Linux developers roll out the updates of beta that address the flaw of critical security. The
machine of Kernel is the most inner sanctum that has access to the memory in the computer. The
bug in the Intel Chips was allowing low-privilege processes to access the kernel memory due to
which the bugs had to attack malicious software and were able to deeply spy data and processes
of the smartphone or computers that were on target. It could even attack the multi-user machines
that run on a server like Amazon Web Services or Google Cloud Services. The hackers could
even break out the process of the user’s and snoop it to other processes that run on the same
server that has shared. On seventh march 2018, a large researcher’s team has released complete
details about the attacks of Meltdown and Spectre (Trippel et al. 2018). The bugs of the hardware
have allowed the programs to steal the currently processed data of the computer. Although, both
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
of this attacks has same general principle. The malicious program of meltdown gain access to the
memory of a computer that has higher-privilege and on the other hand, a machine that is running
other application memory has data which are stolen by Spectre (Greskovits 2015). Due to the
architecture of Meltdown and Spectre, their vulnerabilities have affected most of the processor.
By email, both of the malware get delivered that has exploited this pair of vulnerabilities. In
another case study, it was found that there are multiple approaches taken by NoSpamProxy
towards the process of attachment and contain the blocks attachments reliably. Microsoft,
browser, developers supply patches to fend the attacks (Paci-Green and Berardi 2015). The
security of the computer has ensured by installing all the security updates that are available for
all the operating system.
Even in the research statement of Meltdown and Spectre, Intel has noted that the
exploitation of Meltdown and Spectre cannot modify, corrupt or delete the data even if the
privileged data have spied (Watson et al. 2018). Intel also noted that the computing devices with
different processors of vendors and the operating systems are harmful to this exploit which even
includes the processor of the AMD and ARM. AMD has noted that the performed research was
in a dedicated, controlled lab environment because it was the belief of the company regarding the
processor architecture that the products of AMD are almost near to zero risks (Derrida 2016). As
known that Microsoft completely relies on its computer processors of Intel that has forthcoming
updates for the problem to be addressed. The company was aware of the wide issues of the
industry and was also working with the chip manufacturers to protect their customers by
developing and testing the mitigations. Today the company are deploying services of the cloud
by mitigations and releasing the updates of security that can protect from the vulnerabilities that
are affecting the customers Windows that supports the hardware chips are from the ARM, AMD
of this attacks has same general principle. The malicious program of meltdown gain access to the
memory of a computer that has higher-privilege and on the other hand, a machine that is running
other application memory has data which are stolen by Spectre (Greskovits 2015). Due to the
architecture of Meltdown and Spectre, their vulnerabilities have affected most of the processor.
By email, both of the malware get delivered that has exploited this pair of vulnerabilities. In
another case study, it was found that there are multiple approaches taken by NoSpamProxy
towards the process of attachment and contain the blocks attachments reliably. Microsoft,
browser, developers supply patches to fend the attacks (Paci-Green and Berardi 2015). The
security of the computer has ensured by installing all the security updates that are available for
all the operating system.
Even in the research statement of Meltdown and Spectre, Intel has noted that the
exploitation of Meltdown and Spectre cannot modify, corrupt or delete the data even if the
privileged data have spied (Watson et al. 2018). Intel also noted that the computing devices with
different processors of vendors and the operating systems are harmful to this exploit which even
includes the processor of the AMD and ARM. AMD has noted that the performed research was
in a dedicated, controlled lab environment because it was the belief of the company regarding the
processor architecture that the products of AMD are almost near to zero risks (Derrida 2016). As
known that Microsoft completely relies on its computer processors of Intel that has forthcoming
updates for the problem to be addressed. The company was aware of the wide issues of the
industry and was also working with the chip manufacturers to protect their customers by
developing and testing the mitigations. Today the company are deploying services of the cloud
by mitigations and releasing the updates of security that can protect from the vulnerabilities that
are affecting the customers Windows that supports the hardware chips are from the ARM, AMD
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
and Intel (Hagen 2014). The company yet not receives any information about the use of
vulnerabilities to attack the customers. The developers of Linux paper are recommending some
deep changes in the operating system which is known as KAISER. After someday the statement
of Apple confirms that, all the devices of iOS and Mac system are affected. Luckily, the Apple
watch has not got affected. In macOS 10.13.2, iOS 11.2 and tv OS 11.2 mitigation has already
been released against Meltdown to help them to defend from the attack (Yavuz and Özcan 2015).
There are certain processes that significantly slowdowns the unprivileged memory from
isolating the memory of the Kernel. According to the Register analysis, the delays in some cases
could be almost 30% (Van Munster and Sylvest 2015). However, there are some and newer
processors that experience less significant slowdowns. According to the statement written by
Intel explains that the impacts of the performance are workload-dependent and the average users
of the computer are not significant, as it would get mitigated over time. Until the patches of
Meltdown and Spectre rolled out more widely, the attacks neutering the speed cost will not be
clear. The performance hit even with the results of the updates. Patching the vulnerabilities
across the industry need coordination in large-scale and the effects of performance in the
computer (Alibasic et al. 2016).
Although, Meltdown attacks can be resolved through the design of hardware and by re-
architect of the software which is not possible for Spectre. As mention in the above section that
macOS 10.13.2, iOS 11.2 and tv OS 11.2 mitigation has already released against Meltdown
(Rausch 2014). The company has now plan to release the mitigation in few days against Spectre
to defend and help Safari from getting affected. Thus, due to such issues, the mitigations
continued to develop and further test by the company to release them in the updates that are
upcoming for tv OS, macOS, iOS and watchOS (Standring 2018). The next thing is that the
and Intel (Hagen 2014). The company yet not receives any information about the use of
vulnerabilities to attack the customers. The developers of Linux paper are recommending some
deep changes in the operating system which is known as KAISER. After someday the statement
of Apple confirms that, all the devices of iOS and Mac system are affected. Luckily, the Apple
watch has not got affected. In macOS 10.13.2, iOS 11.2 and tv OS 11.2 mitigation has already
been released against Meltdown to help them to defend from the attack (Yavuz and Özcan 2015).
There are certain processes that significantly slowdowns the unprivileged memory from
isolating the memory of the Kernel. According to the Register analysis, the delays in some cases
could be almost 30% (Van Munster and Sylvest 2015). However, there are some and newer
processors that experience less significant slowdowns. According to the statement written by
Intel explains that the impacts of the performance are workload-dependent and the average users
of the computer are not significant, as it would get mitigated over time. Until the patches of
Meltdown and Spectre rolled out more widely, the attacks neutering the speed cost will not be
clear. The performance hit even with the results of the updates. Patching the vulnerabilities
across the industry need coordination in large-scale and the effects of performance in the
computer (Alibasic et al. 2016).
Although, Meltdown attacks can be resolved through the design of hardware and by re-
architect of the software which is not possible for Spectre. As mention in the above section that
macOS 10.13.2, iOS 11.2 and tv OS 11.2 mitigation has already released against Meltdown
(Rausch 2014). The company has now plan to release the mitigation in few days against Spectre
to defend and help Safari from getting affected. Thus, due to such issues, the mitigations
continued to develop and further test by the company to release them in the updates that are
upcoming for tv OS, macOS, iOS and watchOS (Standring 2018). The next thing is that the

8SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
isolation technique of software is widely deployed that includes sandboxing, containerization,
proof-carrying code, process separation, memory safety. CPU will execute the software
including the safety checks. Unfortunately, the Speculative execution has violated the secrecy of
contents of the register and the memory. Thus, results in a broad range of the isolation of
software that has their impact. In 2018, Spectre has affected almost every system of the computer
that includes laptops, desktops, and devices of the mobiles (Stafford 2016). When Spectre was
shown working on the ARM, Intel, ARM-based and the processors of IBM, Intel has responded
with an official statement to report the vulnerabilities of the security.
Counter measures of the Spectre and Meltdown vulnerabilities
This section will discuss about the countermeasures of Meltdown attack.
Hardware: The security domain of hardware-enforced isolation has by-passes through
Meltdown and the Vulnerability of software is not there in Meltdown. There is a small amount of
memory that has exposed through the patches of software like KAISER. No documentations
were made to fix the microcode update uses or the requirement of the new hardware
development.
The trivial countermeasure will completely disable the out-of–order execution that has exploited
by the Meltdown. However, the impact of the performance is devastating, as it could not
leverage the parallelism of the modern CPUs. Thus, through this it has indicated that the solution
is not viable.
If the register fetch and the permission check has serialized, the race that has form between the
address of the permission check and the address of the memory that has fetch will be prevented
from the Meltdown attack. However, if in any case the permission check fails, it means that the
isolation technique of software is widely deployed that includes sandboxing, containerization,
proof-carrying code, process separation, memory safety. CPU will execute the software
including the safety checks. Unfortunately, the Speculative execution has violated the secrecy of
contents of the register and the memory. Thus, results in a broad range of the isolation of
software that has their impact. In 2018, Spectre has affected almost every system of the computer
that includes laptops, desktops, and devices of the mobiles (Stafford 2016). When Spectre was
shown working on the ARM, Intel, ARM-based and the processors of IBM, Intel has responded
with an official statement to report the vulnerabilities of the security.
Counter measures of the Spectre and Meltdown vulnerabilities
This section will discuss about the countermeasures of Meltdown attack.
Hardware: The security domain of hardware-enforced isolation has by-passes through
Meltdown and the Vulnerability of software is not there in Meltdown. There is a small amount of
memory that has exposed through the patches of software like KAISER. No documentations
were made to fix the microcode update uses or the requirement of the new hardware
development.
The trivial countermeasure will completely disable the out-of–order execution that has exploited
by the Meltdown. However, the impact of the performance is devastating, as it could not
leverage the parallelism of the modern CPUs. Thus, through this it has indicated that the solution
is not viable.
If the register fetch and the permission check has serialized, the race that has form between the
address of the permission check and the address of the memory that has fetch will be prevented
from the Meltdown attack. However, if in any case the permission check fails, it means that the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
memory address has never fetched. There has a significant overhead that has involved to fetch
every kind of memory, until the completion of the permission check.
The solution would be realistic if the modern kernel could optionally enable a new hard-split bit
of a control register CPU as it has introduced between the kernel space and user space. Once the
hard-bit is set, the address space has taken by the user space residing in the lower half and the
kernel space residing in the upper half. Thus, the destination fetch is immediately identified by
the memory fetch which could violate the security boundary. Without further lookups the virtual
device will derive the privilege level. For such solution, the impact of the performance is
minimal. The kernel set the backwards compatibility, if it is supported by the features of the
hard-split.
KAISER: KAISER was developed for the mitigation of the side-channel attacks against KASLR
that protects from meltdown. It is not so easy to patch a hardware. It needs a software to work
around unless any new hardware is deployed. A modification in the kernel was proposed to
kernel as it does not map with the user space. With this modification the side-channel attack that
is breaking KASLR has prevented. Meltdown ensures that the kernel space and the physical
memory that is available in the user space has no valid mapping. Under the isolation of kernel
page-table, Linux kernel will be release. Such similar patches have introduced in Mac OS X, iOS
AND Microsoft Windows 10 Build 17035.
There has still some limitations when basic protection has been provided to KAISER against
Meltdown. In the user space several locations of privileged memory are required that has to be
mapped due to the design of the x86 architecture. There is no credential to memory location but
contains some pointers. KAISER is still considered as a short-time solution available and
memory address has never fetched. There has a significant overhead that has involved to fetch
every kind of memory, until the completion of the permission check.
The solution would be realistic if the modern kernel could optionally enable a new hard-split bit
of a control register CPU as it has introduced between the kernel space and user space. Once the
hard-bit is set, the address space has taken by the user space residing in the lower half and the
kernel space residing in the upper half. Thus, the destination fetch is immediately identified by
the memory fetch which could violate the security boundary. Without further lookups the virtual
device will derive the privilege level. For such solution, the impact of the performance is
minimal. The kernel set the backwards compatibility, if it is supported by the features of the
hard-split.
KAISER: KAISER was developed for the mitigation of the side-channel attacks against KASLR
that protects from meltdown. It is not so easy to patch a hardware. It needs a software to work
around unless any new hardware is deployed. A modification in the kernel was proposed to
kernel as it does not map with the user space. With this modification the side-channel attack that
is breaking KASLR has prevented. Meltdown ensures that the kernel space and the physical
memory that is available in the user space has no valid mapping. Under the isolation of kernel
page-table, Linux kernel will be release. Such similar patches have introduced in Mac OS X, iOS
AND Microsoft Windows 10 Build 17035.
There has still some limitations when basic protection has been provided to KAISER against
Meltdown. In the user space several locations of privileged memory are required that has to be
mapped due to the design of the x86 architecture. There is no credential to memory location but
contains some pointers. KAISER is still considered as a short-time solution available and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
immediately deployed on every system. When leaking a pointer break KASLR to calculate the
randomization from the value of pointer. KAISER can avoid the pointers of kernel on the
memory locations to map with the user space that would leak the information. For every kernel
pointer, the location for a trampoline function is required. Trampoline function map with the
kernel and randomized with different offset of the remaining kernel. The consequence to it is that
attacker leak pointers to the code of trampoline but not to the randomized offsets. Such code of
trampoline has to be assessed for the future work as the kernel memory still has to mapped in the
user space that contains a kernel addresses.
The countermeasure of Spectre attack has discussed below in four steps:
Firstly, in the modern processor, the logic of branch prediction can be trained to hit or
miss the malicious programs that are working internally.
Secondly, the difference between the non-functional cache hits and misses has subverted
to covert channel that has some internal workings information extracted from unrelated
processes.
Thirdly, it synthesises the return-oriented programming that exploits the principles
through a JavaScript program that run under a sandboxing browser. The basic idea is that
searching an existing code for the speculation that touches the inaccessible data, manipulates the
processor into speculative execution.
Finally, the attack briefly discusses the bus arbitration latency to any non-obvious or non-
functional state.
immediately deployed on every system. When leaking a pointer break KASLR to calculate the
randomization from the value of pointer. KAISER can avoid the pointers of kernel on the
memory locations to map with the user space that would leak the information. For every kernel
pointer, the location for a trampoline function is required. Trampoline function map with the
kernel and randomized with different offset of the remaining kernel. The consequence to it is that
attacker leak pointers to the code of trampoline but not to the randomized offsets. Such code of
trampoline has to be assessed for the future work as the kernel memory still has to mapped in the
user space that contains a kernel addresses.
The countermeasure of Spectre attack has discussed below in four steps:
Firstly, in the modern processor, the logic of branch prediction can be trained to hit or
miss the malicious programs that are working internally.
Secondly, the difference between the non-functional cache hits and misses has subverted
to covert channel that has some internal workings information extracted from unrelated
processes.
Thirdly, it synthesises the return-oriented programming that exploits the principles
through a JavaScript program that run under a sandboxing browser. The basic idea is that
searching an existing code for the speculation that touches the inaccessible data, manipulates the
processor into speculative execution.
Finally, the attack briefly discusses the bus arbitration latency to any non-obvious or non-
functional state.

11SPECTRE, MELTDOWN, COUNTERMEASURES AND FUTURE IMPACT
Fixing vulnerabilities of Meltdown and Spectre
All vulnerabilities that affect the microprocessors of AMD, Intel and ARM are for pre-
execute instructions. These vulnerabilities bypass the isolation of address space for the integrity
of the processor. An emergency patch has release by Microsoft for Windows 10. This will
address the patch that can incorporate KAISER with KB4056892. The fix will add extra
processing, and will affect the overall performance of Intel CPUs.
The software patches are there for both the vulnerabilities, but for Meltdown, they are
straightforward, and for Spectre, they are nuanced and difficult (Simakov et al. 2018). Risk
occurs in multiple accounts, cloud, internet browser, the environment virtualisation. Depending
on the use of hardware platform where the operating systems are running, the risk in the user
system may be different (Daianu, D., 2017). However, the overall concept of this two attacks has
considered when allowing to run someone else code on a system that is affected. For this, the
attacker takes advantage of the local account to execute the code through ads and JavaScript.
Speculative execution defines the technology that enhances the performance virtually for all the
modern CPUs (Chen et al. 2018). Through Speculative execution, the memory’s sensitive
information will read the low privilege users that are allowed by the Meltdown and the Spectre to
execute the code on the user system. The difference found here is the advantage that the
Meltdown takes for the issue of escalation of a specific escalation privilege. On the other hand,
Spectre prefers to use both the combination of Branch Prediction and Speculative Execution.
However, the software patches can address both the issues, but Meltdown will be more effective
than Spectre (Dorey 2017).
Fixing vulnerabilities of Meltdown and Spectre
All vulnerabilities that affect the microprocessors of AMD, Intel and ARM are for pre-
execute instructions. These vulnerabilities bypass the isolation of address space for the integrity
of the processor. An emergency patch has release by Microsoft for Windows 10. This will
address the patch that can incorporate KAISER with KB4056892. The fix will add extra
processing, and will affect the overall performance of Intel CPUs.
The software patches are there for both the vulnerabilities, but for Meltdown, they are
straightforward, and for Spectre, they are nuanced and difficult (Simakov et al. 2018). Risk
occurs in multiple accounts, cloud, internet browser, the environment virtualisation. Depending
on the use of hardware platform where the operating systems are running, the risk in the user
system may be different (Daianu, D., 2017). However, the overall concept of this two attacks has
considered when allowing to run someone else code on a system that is affected. For this, the
attacker takes advantage of the local account to execute the code through ads and JavaScript.
Speculative execution defines the technology that enhances the performance virtually for all the
modern CPUs (Chen et al. 2018). Through Speculative execution, the memory’s sensitive
information will read the low privilege users that are allowed by the Meltdown and the Spectre to
execute the code on the user system. The difference found here is the advantage that the
Meltdown takes for the issue of escalation of a specific escalation privilege. On the other hand,
Spectre prefers to use both the combination of Branch Prediction and Speculative Execution.
However, the software patches can address both the issues, but Meltdown will be more effective
than Spectre (Dorey 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




