Virtual Private Network Technologies: BN305 Assignment 1 Report
VerifiedAdded on 2023/06/07
|9
|2302
|280
Report
AI Summary
This report delves into the critical aspects of SSL VPN technologies, focusing on their role in securing organizational data. It begins with an introduction highlighting the importance of VPNs in contemporary organizations, emphasizing cost savings, scalability, and security. The report then explores authentication methods, including the communication between browsers and servers, the role of digital signatures, and the verification of information shared by servers. It further examines confidentiality and integrity processes, detailing the use of symmetric and asymmetric encryption, hash algorithms, and their roles in SSL communication. The report concludes with a discussion on protection against replay attacks, including the migration of anti-replay mechanisms in SSL communication. The report emphasizes the importance of these security measures in addressing vulnerabilities and ensuring secure web-based transactions. The report is submitted by a student and available on Desklib, a platform offering AI-based study tools for students.

Virtual private network
Assignment 1
BN305
shree
Submitted by Shreeyash Devkota( mit170489)
– SSL VPN Technologies
Tutor name = mehdi pishva
Assignment 1
BN305
shree
Submitted by Shreeyash Devkota( mit170489)
– SSL VPN Technologies
Tutor name = mehdi pishva
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents and Table of Figures
Introduction...........................................................................................................................................1
Authentication.......................................................................................................................................1
Confidentiality and Integrity Processes.................................................................................................3
Protection against Replay Attacks.........................................................................................................4
Conclusion.............................................................................................................................................5
References.............................................................................................................................................6
Introduction...........................................................................................................................................1
Authentication.......................................................................................................................................1
Confidentiality and Integrity Processes.................................................................................................3
Protection against Replay Attacks.........................................................................................................4
Conclusion.............................................................................................................................................5
References.............................................................................................................................................6

Introduction
This report focuses on the aspect of use of VPN based technologies for securing the
information of contemporary organisations. The Virtual Private Networks would help for the offering
of wide range of solutions in order to establish a secure mode of network based connection. The
VPN enabled technologies are largely implemented within the use of many big organizations. The
various forms of advantages that are offered by VPN enabled technological solutions within the
organizations are that they help in the savings of various incurred costs by the organization, scale the
network availability within the organization and maintain the proper level of security measures
within the organization [1]. As different large scale organizations help in the surfing of web based
technologies, hence they become vulnerable to the exposure of the private information. Hence, to
protect the organizations from their data to become vulnerable to various forms of attacks, there
should be proper methods of VPN enabled technologies for securing the confidential information of
the organizations.
Authentication
Ensuring the Communication of the Browser with the Right Server – There are different
kinds of web browsers such as Internet Explorer, Chrome, Mozilla Firefox and Safari that are ranked
as the top network based applications on the internet platforms. These are mainly used for basic
browsing of the internet and also serving various other needs that would also include online
shopping and also performing various other kinds of online transactions [2].
The web browsers and the web server work together in order to function together as a
systems of client and server. In the networking based systems of the computer, the client-server is
one of the best standard method that would be useful for the designing of much number of
applications in which the data would be stored in several central locations. There are numerous
client based web browsers that would be able to request data from the same server or website.
These request could happen from the same server at different times or can come simultaneously.
The systems of client-server would handle such kind of requests based on any server [3].
This report focuses on the aspect of use of VPN based technologies for securing the
information of contemporary organisations. The Virtual Private Networks would help for the offering
of wide range of solutions in order to establish a secure mode of network based connection. The
VPN enabled technologies are largely implemented within the use of many big organizations. The
various forms of advantages that are offered by VPN enabled technological solutions within the
organizations are that they help in the savings of various incurred costs by the organization, scale the
network availability within the organization and maintain the proper level of security measures
within the organization [1]. As different large scale organizations help in the surfing of web based
technologies, hence they become vulnerable to the exposure of the private information. Hence, to
protect the organizations from their data to become vulnerable to various forms of attacks, there
should be proper methods of VPN enabled technologies for securing the confidential information of
the organizations.
Authentication
Ensuring the Communication of the Browser with the Right Server – There are different
kinds of web browsers such as Internet Explorer, Chrome, Mozilla Firefox and Safari that are ranked
as the top network based applications on the internet platforms. These are mainly used for basic
browsing of the internet and also serving various other needs that would also include online
shopping and also performing various other kinds of online transactions [2].
The web browsers and the web server work together in order to function together as a
systems of client and server. In the networking based systems of the computer, the client-server is
one of the best standard method that would be useful for the designing of much number of
applications in which the data would be stored in several central locations. There are numerous
client based web browsers that would be able to request data from the same server or website.
These request could happen from the same server at different times or can come simultaneously.
The systems of client-server would handle such kind of requests based on any server [3].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
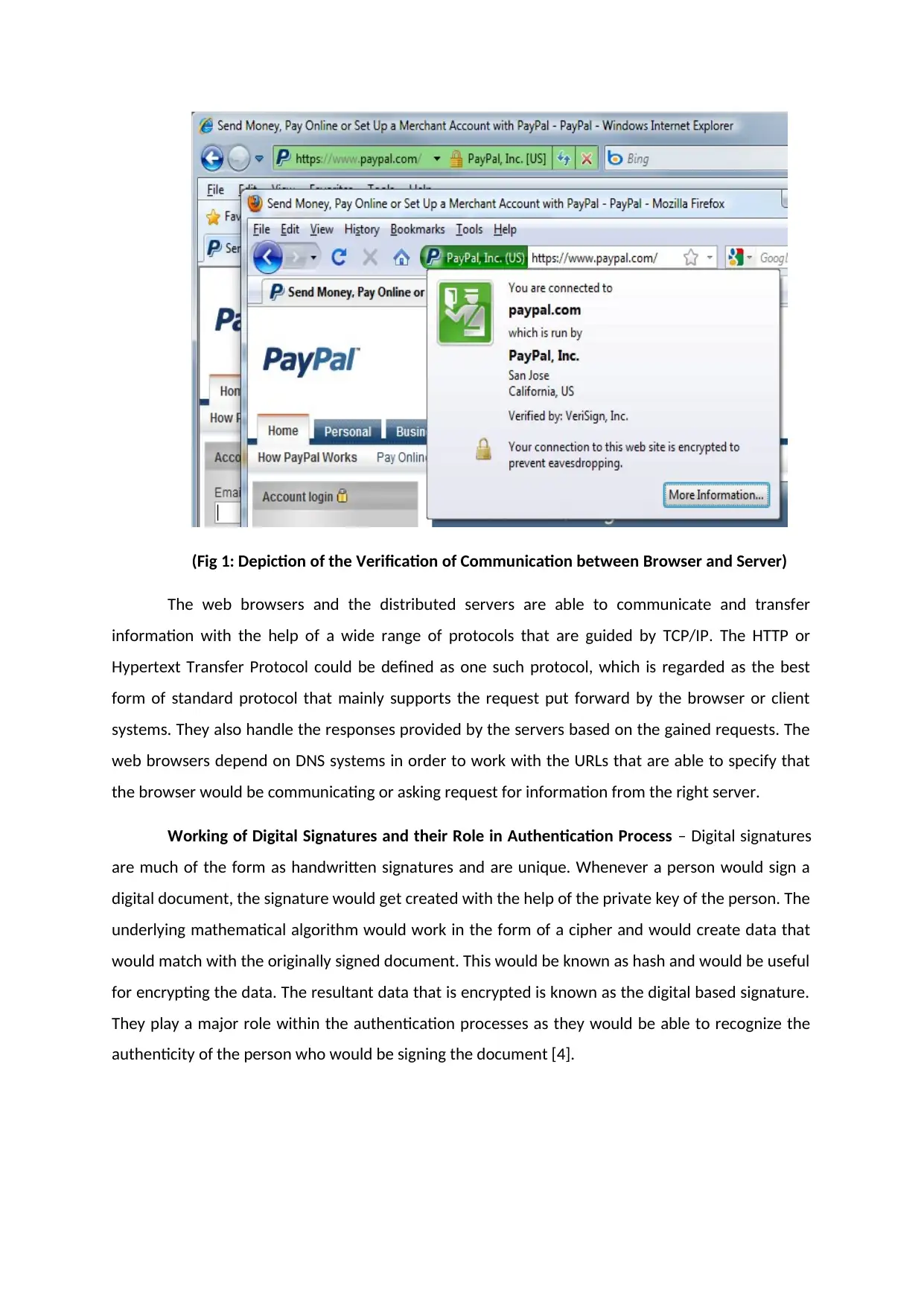
(Fig 1: Depiction of the Verification of Communication between Browser and Server)
The web browsers and the distributed servers are able to communicate and transfer
information with the help of a wide range of protocols that are guided by TCP/IP. The HTTP or
Hypertext Transfer Protocol could be defined as one such protocol, which is regarded as the best
form of standard protocol that mainly supports the request put forward by the browser or client
systems. They also handle the responses provided by the servers based on the gained requests. The
web browsers depend on DNS systems in order to work with the URLs that are able to specify that
the browser would be communicating or asking request for information from the right server.
Working of Digital Signatures and their Role in Authentication Process – Digital signatures
are much of the form as handwritten signatures and are unique. Whenever a person would sign a
digital document, the signature would get created with the help of the private key of the person. The
underlying mathematical algorithm would work in the form of a cipher and would create data that
would match with the originally signed document. This would be known as hash and would be useful
for encrypting the data. The resultant data that is encrypted is known as the digital based signature.
They play a major role within the authentication processes as they would be able to recognize the
authenticity of the person who would be signing the document [4].
The web browsers and the distributed servers are able to communicate and transfer
information with the help of a wide range of protocols that are guided by TCP/IP. The HTTP or
Hypertext Transfer Protocol could be defined as one such protocol, which is regarded as the best
form of standard protocol that mainly supports the request put forward by the browser or client
systems. They also handle the responses provided by the servers based on the gained requests. The
web browsers depend on DNS systems in order to work with the URLs that are able to specify that
the browser would be communicating or asking request for information from the right server.
Working of Digital Signatures and their Role in Authentication Process – Digital signatures
are much of the form as handwritten signatures and are unique. Whenever a person would sign a
digital document, the signature would get created with the help of the private key of the person. The
underlying mathematical algorithm would work in the form of a cipher and would create data that
would match with the originally signed document. This would be known as hash and would be useful
for encrypting the data. The resultant data that is encrypted is known as the digital based signature.
They play a major role within the authentication processes as they would be able to recognize the
authenticity of the person who would be signing the document [4].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

(Fig 2: Details of Digital Signature based on a Web Browser)
Verification of Information shared by Server to the right Client – The SSH is a kind of
cryptographic keys that are mainly used to authenticate the information shared by a server. A
private and a public key are generated prior to sharing of information with the client. Whenever the
client would ask for some form of information, the server would ask for the proper kind of proof,
which would be the proper kind of private key. After the process of verification, the server would
permit the client in order to connect without any kind of password. Some of the common discussed
methods for the purpose of verification are safe browsing, 2-step Verification and Security Check-up
[5].
Confidentiality and Integrity Processes
Confidentiality and Integrity - The SSL makes a combination of asymmetric and symmetric
encryption for the purpose of ensuring the privacy of a certain message. During the process of SSL
based handshaking, the SSL based server and client would agree upon an algorithm of encryption
that would be supported by a share form of secret key. This secret key would be used only for a
Verification of Information shared by Server to the right Client – The SSH is a kind of
cryptographic keys that are mainly used to authenticate the information shared by a server. A
private and a public key are generated prior to sharing of information with the client. Whenever the
client would ask for some form of information, the server would ask for the proper kind of proof,
which would be the proper kind of private key. After the process of verification, the server would
permit the client in order to connect without any kind of password. Some of the common discussed
methods for the purpose of verification are safe browsing, 2-step Verification and Security Check-up
[5].
Confidentiality and Integrity Processes
Confidentiality and Integrity - The SSL makes a combination of asymmetric and symmetric
encryption for the purpose of ensuring the privacy of a certain message. During the process of SSL
based handshaking, the SSL based server and client would agree upon an algorithm of encryption
that would be supported by a share form of secret key. This secret key would be used only for a

single session. The entire set of messages that are transmitted between the SLL based client and
server would be tightly encrypted with the help of a key and algorithm [6]. This would be extremely
useful for the purpose of ensuring that the message would remain in its private form even if they get
intercepted. The Secure Sockets Layer makes use of high range of algorithms based on cryptographic
techniques. As SSL ensures the asymmetric encryption during the transportation of the secret key,
there would be no such problem of distribution of keys. The integrity within data is provided by SSL
by the help of calculation of a form of message digest. The proper use of data integrity makes use of
hash algorithms [7].
The SSL connection would initiate with a handshake. This handshake would be able to
determine the type of cipher suite, which would be used in order to encrypt the communication. It
would also ensure the verification of the server and would be able to establish a secure mode of
communication [8].
Role of symmetric encryption and hash algorithms in SSL communication - Symmetric
encryption is one form of single key that would be majorly used for the purpose of encryption and
decryption of data, his form of encryption is shared among the sender and the receiver. In the
methods of digital system of encryption and during the process of SSL handshaking, the Symmetric
based algorithm would make use of single key for the purpose of performing encryption and
decryption of the message. The use of symmetric encryption would be mainly to encrypt the data
and thus decrypt them during the process of SSL handshake [9].
A cryptographic hash function would be able to convert the long data inputs into a form of a
fixed length value based on output. These hash functions are primarily used within different kinds of
security protocols such as SSL applications, which mainly depend on the integrity of data. Some of
the applications where the hash functions are widely used is cryptocurrency. These different kinds of
cryptocurrencies make use of hash functions in order to update a blockchain technology with several
forms of newer blocks for the purpose of verifiable and secure mode of transaction based on data
[10].
Protection against Replay Attacks
Migration of Anti-Replay Attacks in SSL Communication – The anti-replays are a form of
sub-protocol of IPSec. The primary goal of anti-replay would be to avoid the hackers for the purpose
of injecting and thus be able to make different kinds of changes within the packets of data that
would be able to travel from one source to another destination of information. The anti-replay
protocol employs the association of unidirectional security for the purpose of establishing a secure
server would be tightly encrypted with the help of a key and algorithm [6]. This would be extremely
useful for the purpose of ensuring that the message would remain in its private form even if they get
intercepted. The Secure Sockets Layer makes use of high range of algorithms based on cryptographic
techniques. As SSL ensures the asymmetric encryption during the transportation of the secret key,
there would be no such problem of distribution of keys. The integrity within data is provided by SSL
by the help of calculation of a form of message digest. The proper use of data integrity makes use of
hash algorithms [7].
The SSL connection would initiate with a handshake. This handshake would be able to
determine the type of cipher suite, which would be used in order to encrypt the communication. It
would also ensure the verification of the server and would be able to establish a secure mode of
communication [8].
Role of symmetric encryption and hash algorithms in SSL communication - Symmetric
encryption is one form of single key that would be majorly used for the purpose of encryption and
decryption of data, his form of encryption is shared among the sender and the receiver. In the
methods of digital system of encryption and during the process of SSL handshaking, the Symmetric
based algorithm would make use of single key for the purpose of performing encryption and
decryption of the message. The use of symmetric encryption would be mainly to encrypt the data
and thus decrypt them during the process of SSL handshake [9].
A cryptographic hash function would be able to convert the long data inputs into a form of a
fixed length value based on output. These hash functions are primarily used within different kinds of
security protocols such as SSL applications, which mainly depend on the integrity of data. Some of
the applications where the hash functions are widely used is cryptocurrency. These different kinds of
cryptocurrencies make use of hash functions in order to update a blockchain technology with several
forms of newer blocks for the purpose of verifiable and secure mode of transaction based on data
[10].
Protection against Replay Attacks
Migration of Anti-Replay Attacks in SSL Communication – The anti-replays are a form of
sub-protocol of IPSec. The primary goal of anti-replay would be to avoid the hackers for the purpose
of injecting and thus be able to make different kinds of changes within the packets of data that
would be able to travel from one source to another destination of information. The anti-replay
protocol employs the association of unidirectional security for the purpose of establishing a secure
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
mode of connection between any two nodes of the network. Whenever a secure mode of
communication would be established, the protocol of anti-replay would make use of the numbers
based on the sequence of packets in order to defeat the replay based attacks. The anti-replay based
attacks are one of the major form of infiltration within the networks that would have many form of
harmful effects. The anti-replay attacks are majorly used for the purpose of compromising the SSL
sessions, perform various forms of fraudulent transactions based on chip-based credit card. They are
also being used to compromise within the SSL sessions [11].
In the attacks based on anti-replay, the hacker might make a wide form of usage based on
the packet sniffer in order to intercept with the data and thus be able to retransmit the data. With
the help of this kind of process, the hacker would be able to imitate the particular entity that would
send the data originally.
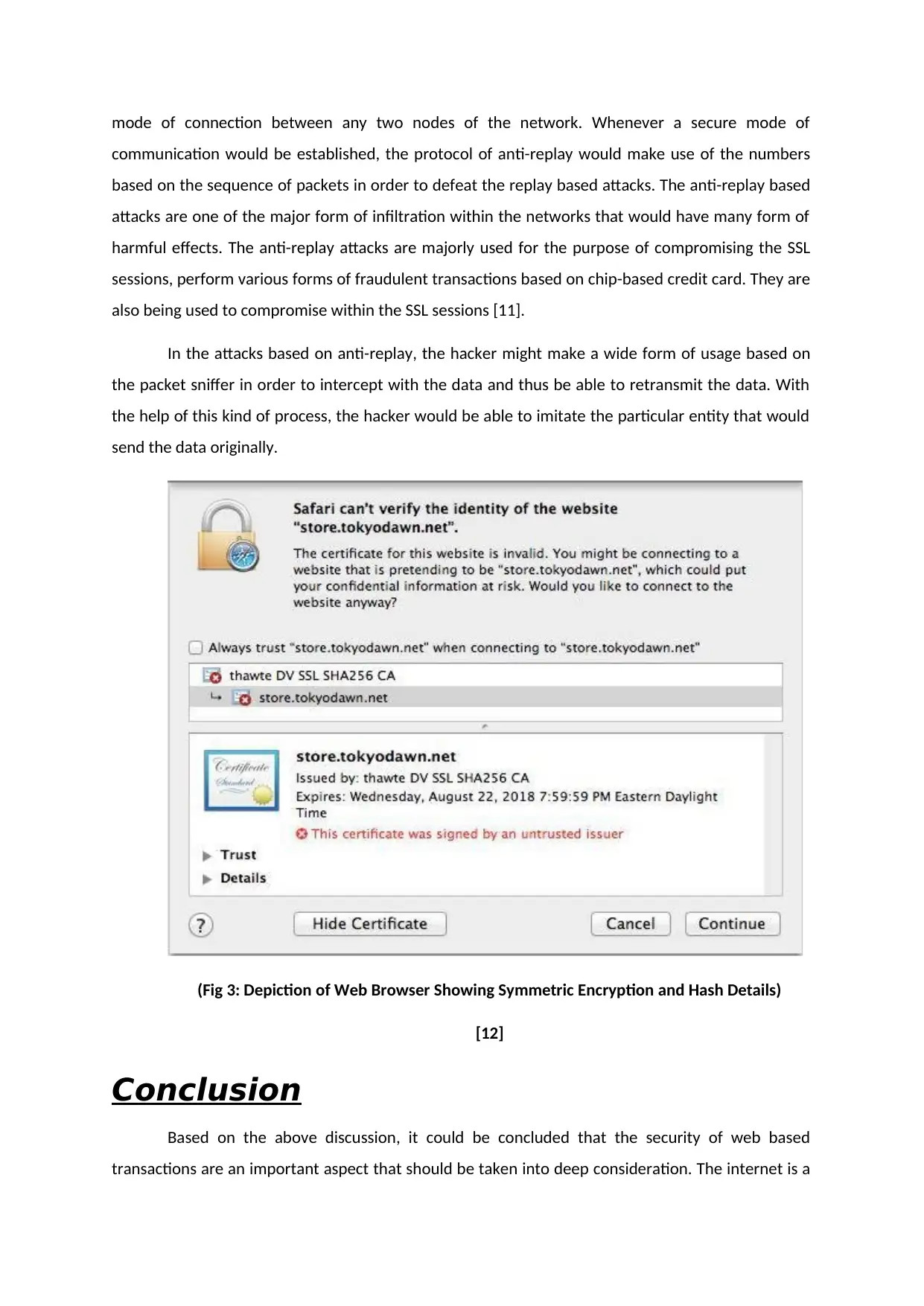
(Fig 3: Depiction of Web Browser Showing Symmetric Encryption and Hash Details)
[12]
Conclusion
Based on the above discussion, it could be concluded that the security of web based
transactions are an important aspect that should be taken into deep consideration. The internet is a
communication would be established, the protocol of anti-replay would make use of the numbers
based on the sequence of packets in order to defeat the replay based attacks. The anti-replay based
attacks are one of the major form of infiltration within the networks that would have many form of
harmful effects. The anti-replay attacks are majorly used for the purpose of compromising the SSL
sessions, perform various forms of fraudulent transactions based on chip-based credit card. They are
also being used to compromise within the SSL sessions [11].
In the attacks based on anti-replay, the hacker might make a wide form of usage based on
the packet sniffer in order to intercept with the data and thus be able to retransmit the data. With
the help of this kind of process, the hacker would be able to imitate the particular entity that would
send the data originally.
(Fig 3: Depiction of Web Browser Showing Symmetric Encryption and Hash Details)
[12]
Conclusion
Based on the above discussion, it could be concluded that the security of web based
transactions are an important aspect that should be taken into deep consideration. The internet is a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

form of public network, which is prone to various forms of attacks on the information systems. This
report focuses on the right form of communication between the web browser and the server. It also
discusses the need of digital signatures and the various aspects based on authenticity and
confidentiality. The aspect of integrity and confidentiality is a matter of high concern in the recent
times, which should be highly ensured within the SSL based communication. Hence the ensuring of
security within these aspects should be taken into consideration for dealing with the various issues
related to the internet platforms.
References
[1] Lospoto, Gabriele, Massimo Rimondini, Benedetto Gabriele Vignoli, and Giuseppe Di Battista.
"Rethinking virtual private networks in the software-defined era." In Integrated Network
Management (IM), 2015 IFIP/IEEE International Symposium on, pp. 379-387. IEEE, 2015.
[2] Holmberg, Christer, Stefan Hakansson, and G. Eriksson. Web real-time communication use cases
and requirements. No. RFC 7478. 2015.
[3] Tsuchiya, Takashi, Masahiro Fujita, Kenta Takahashi, Takehisa Kato, Fumihiko Magata, Yoshimi
Teshigawara, Ryoichi Sasaki, and Masakatsu Nishigaki. "Secure Communication Protocol Between a
Human and a Bank Server for Preventing Man-in-the-Browser Attacks." In International Conference
on Human Aspects of Information Security, Privacy, and Trust, pp. 77-88. Springer, Cham, 2016.
[4] Horng, Shi-Jinn, Shiang-Feng Tzeng, Yi Pan, Pingzhi Fan, Xian Wang, Tianrui Li, and Muhammad
Khurram Khan. "b-SPECS+: Batch verification for secure pseudonymous authentication in
VANET." IEEE Transactions on Information Forensics and Security 8, no. 11 (2013): 1860-1875.
[5] Liao, Yi-Pin, and Chih-Ming Hsiao. "A novel multi-server remote user authentication scheme using
self-certified public keys for mobile clients." Future Generation Computer Systems29, no. 3 (2013):
886-900.
[6] Nirmala, V., R. K. Sivanandhan, and R. Shanmuga Lakshmi. "Data confidentiality and integrity
verification using user authenticator scheme in cloud." In Green High Performance Computing
(ICGHPC), 2013 IEEE International Conference on, pp. 1-5. IEEE, 2013.
[7] Rewagad, Prashant, and Yogita Pawar. "Use of digital signature with diffie hellman key exchange
and AES encryption algorithm to enhance data security in cloud computing." In Communication
Systems and Network Technologies (CSNT), 2013 International Conference on, pp. 437-439. IEEE,
2013.
report focuses on the right form of communication between the web browser and the server. It also
discusses the need of digital signatures and the various aspects based on authenticity and
confidentiality. The aspect of integrity and confidentiality is a matter of high concern in the recent
times, which should be highly ensured within the SSL based communication. Hence the ensuring of
security within these aspects should be taken into consideration for dealing with the various issues
related to the internet platforms.
References
[1] Lospoto, Gabriele, Massimo Rimondini, Benedetto Gabriele Vignoli, and Giuseppe Di Battista.
"Rethinking virtual private networks in the software-defined era." In Integrated Network
Management (IM), 2015 IFIP/IEEE International Symposium on, pp. 379-387. IEEE, 2015.
[2] Holmberg, Christer, Stefan Hakansson, and G. Eriksson. Web real-time communication use cases
and requirements. No. RFC 7478. 2015.
[3] Tsuchiya, Takashi, Masahiro Fujita, Kenta Takahashi, Takehisa Kato, Fumihiko Magata, Yoshimi
Teshigawara, Ryoichi Sasaki, and Masakatsu Nishigaki. "Secure Communication Protocol Between a
Human and a Bank Server for Preventing Man-in-the-Browser Attacks." In International Conference
on Human Aspects of Information Security, Privacy, and Trust, pp. 77-88. Springer, Cham, 2016.
[4] Horng, Shi-Jinn, Shiang-Feng Tzeng, Yi Pan, Pingzhi Fan, Xian Wang, Tianrui Li, and Muhammad
Khurram Khan. "b-SPECS+: Batch verification for secure pseudonymous authentication in
VANET." IEEE Transactions on Information Forensics and Security 8, no. 11 (2013): 1860-1875.
[5] Liao, Yi-Pin, and Chih-Ming Hsiao. "A novel multi-server remote user authentication scheme using
self-certified public keys for mobile clients." Future Generation Computer Systems29, no. 3 (2013):
886-900.
[6] Nirmala, V., R. K. Sivanandhan, and R. Shanmuga Lakshmi. "Data confidentiality and integrity
verification using user authenticator scheme in cloud." In Green High Performance Computing
(ICGHPC), 2013 IEEE International Conference on, pp. 1-5. IEEE, 2013.
[7] Rewagad, Prashant, and Yogita Pawar. "Use of digital signature with diffie hellman key exchange
and AES encryption algorithm to enhance data security in cloud computing." In Communication
Systems and Network Technologies (CSNT), 2013 International Conference on, pp. 437-439. IEEE,
2013.

[8] Fahl, Sascha, Marian Harbach, Henning Perl, Markus Koetter, and Matthew Smith. "Rethinking
SSL development in an appified world." In Proceedings of the 2013 ACM SIGSAC conference on
Computer & communications security, pp. 49-60. ACM, 2013.
[9] He, Debiao, and Sherali Zeadally. "Authentication protocol for an ambient assisted living
system." IEEE Communications Magazine 53, no. 1 (2015): 71-77.
[10] Yoon, Eun-Jun, and Kee-Young Yoo. "Robust biometrics-based multi-server authentication with
key agreement scheme for smart cards on elliptic curve cryptosystem." The Journal of
supercomputing 63, no. 1 (2013): 235-255.
[11] Meyer, Christopher, and Jörg Schwenk. "Lessons Learned From Previous SSL/TLS Attacks-A Brief
Chronology Of Attacks And Weaknesses." IACR Cryptology ePrint Archive2013 (2013): 49.
[12] Meyer, Christopher, and Jörg Schwenk. "SoK: Lessons learned from SSL/TLS attacks."
In International Workshop on Information Security Applications, pp. 189-209. Springer, Cham, 2013.
SSL development in an appified world." In Proceedings of the 2013 ACM SIGSAC conference on
Computer & communications security, pp. 49-60. ACM, 2013.
[9] He, Debiao, and Sherali Zeadally. "Authentication protocol for an ambient assisted living
system." IEEE Communications Magazine 53, no. 1 (2015): 71-77.
[10] Yoon, Eun-Jun, and Kee-Young Yoo. "Robust biometrics-based multi-server authentication with
key agreement scheme for smart cards on elliptic curve cryptosystem." The Journal of
supercomputing 63, no. 1 (2013): 235-255.
[11] Meyer, Christopher, and Jörg Schwenk. "Lessons Learned From Previous SSL/TLS Attacks-A Brief
Chronology Of Attacks And Weaknesses." IACR Cryptology ePrint Archive2013 (2013): 49.
[12] Meyer, Christopher, and Jörg Schwenk. "SoK: Lessons learned from SSL/TLS attacks."
In International Workshop on Information Security Applications, pp. 189-209. Springer, Cham, 2013.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





