Enhancing Cloud Security at Inshore Insurance: Statement of Work
VerifiedAdded on 2021/06/18
|16
|2880
|44
Report
AI Summary
This statement of work outlines a project to enhance cloud security for Inshore Insurance Limited (IIL). The core problem addressed is the vulnerability of sensitive data stored in the cloud to breaches and intrusions. The proposed solution is the implementation of RAP as a Service, a third-party managed security solution. The project scope includes defining requirements, evaluating the current IT infrastructure, and executing the implementation of RAP as a Service, including configuration, auditing, and user training. The project is planned over six months using agile methodology, with detailed schedules, acceptance criteria, and required technologies outlined. The report includes a project management plan, detailing tasks, durations, resource allocation, and budget. The goal is to secure IIL's network, protect data, and ensure the organization's operational efficiency and reputation.

Running head: STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD
SECURITY
Statement of Work for the Enhancement in the Cloud Security
Inshore Insurance Limited (IIL)
Name of Student
Name of the University
Author Note
SECURITY
Statement of Work for the Enhancement in the Cloud Security
Inshore Insurance Limited (IIL)
Name of Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Table of Contents
Introduction......................................................................................................................................2
Scope of Work.................................................................................................................................2
Problem Statement...........................................................................................................................3
Period of Performance.....................................................................................................................3
Requirement Specifications.............................................................................................................4
Schedule...........................................................................................................................................5
Acceptance Criteria.........................................................................................................................6
Other Requirements.........................................................................................................................7
Technologies Required....................................................................................................................7
Project Management Plan................................................................................................................7
Tools and Methodologies..............................................................................................................11
Bibliography..................................................................................................................................13
Bibliography..................................................................................................................................15
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Table of Contents
Introduction......................................................................................................................................2
Scope of Work.................................................................................................................................2
Problem Statement...........................................................................................................................3
Period of Performance.....................................................................................................................3
Requirement Specifications.............................................................................................................4
Schedule...........................................................................................................................................5
Acceptance Criteria.........................................................................................................................6
Other Requirements.........................................................................................................................7
Technologies Required....................................................................................................................7
Project Management Plan................................................................................................................7
Tools and Methodologies..............................................................................................................11
Bibliography..................................................................................................................................13
Bibliography..................................................................................................................................15

2
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Introduction
Inshore Insurance Limited (IIL) has implemented and established Cloud Services for the
accomplishment of the operational activities. The head office of the IIL is located at Sydney,
different branches are located at all over the state, and it has been the profitable Australian
Financial Institution. The Cloud service application has many benefits and it has boosted the
daily operational activities of the organization however; security has been the biggest concern for
the application of cloud services. The organization collects personal and sensitive information
related to the employees and their customers and save them in the cloud. Recent accidents and
successful attempts of data breach and intrusion have explained the need for the secure network
is an essential factor for managing the efficient and effective output of the project. The purpose
of this statement of work is to provide detailed explanation on how the problem can be
eliminated for good and secure the network of the IIL. The introduction of RAP as a Service is
capable of enhancing the security level of the cloud infrastructure of the organization. Proper
managerial and leadership skills are needed for the successful implementation of this service
within the existing system of the company. Securing the data and information collected by the
organization will be helpful in assuring that the operational activities and reputation of the
organization is protected from such unwanted activities.
Scope of Work
Project scope is to implement a solution that is capable of eliminating the problem of
security through the implementation of the RAP as a Service within the existing IT infrastructure
of the IIL. The third party will be responsible for managing all the technical works however;
certain technicians will be needed for managing the in-house IT infrastructure. RAP as a Service
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Introduction
Inshore Insurance Limited (IIL) has implemented and established Cloud Services for the
accomplishment of the operational activities. The head office of the IIL is located at Sydney,
different branches are located at all over the state, and it has been the profitable Australian
Financial Institution. The Cloud service application has many benefits and it has boosted the
daily operational activities of the organization however; security has been the biggest concern for
the application of cloud services. The organization collects personal and sensitive information
related to the employees and their customers and save them in the cloud. Recent accidents and
successful attempts of data breach and intrusion have explained the need for the secure network
is an essential factor for managing the efficient and effective output of the project. The purpose
of this statement of work is to provide detailed explanation on how the problem can be
eliminated for good and secure the network of the IIL. The introduction of RAP as a Service is
capable of enhancing the security level of the cloud infrastructure of the organization. Proper
managerial and leadership skills are needed for the successful implementation of this service
within the existing system of the company. Securing the data and information collected by the
organization will be helpful in assuring that the operational activities and reputation of the
organization is protected from such unwanted activities.
Scope of Work
Project scope is to implement a solution that is capable of eliminating the problem of
security through the implementation of the RAP as a Service within the existing IT infrastructure
of the IIL. The third party will be responsible for managing all the technical works however;
certain technicians will be needed for managing the in-house IT infrastructure. RAP as a Service
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
will allow the organization to secure the network and manage the data and information handling.
The constraints of the project is listed in the below sections and the scope of this implementation
will be capable of the mitigating the raised problem.
Problem Statement
The organization is collecting very sensitive and personal information that needs to be
protected in manner to let the organization’s workflow in an efficient and effective manner. Data
and information stored in the cloud are vulnerable to the intrusion and data breaches and thus,
proper precautions are very crucial in the context of the long run for the company. Expose of
personal and sensitive information have may negative impacts on the organization’s reputation,
and privacy and security of the stakeholders associated with the organization. Expose of such
crucial information could even led to the closure of the organization and thus, it has been the
greatest concern for the IIL in manner to allow employees and staffs to accomplish the daily
operational activities. RAP as a Service can be proposed as an effective approach towards
enhancing the security of the network that will be allowing the organization to hire a third party
responsible for managing the security of the data and information.
Period of Performance
The period of performance would be approximately six months (180 days) as it will
started at May 7, 2018 and will be ending at January 25, 2019. The activities and schedule
mentioned in the below report demonstrates the list of the activities, milestones and their
delivery in manner to accomplish the objectives of the project. The proposed work will be
delivered through utilizing the agile methodology and all the changes will be accepted during the
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
will allow the organization to secure the network and manage the data and information handling.
The constraints of the project is listed in the below sections and the scope of this implementation
will be capable of the mitigating the raised problem.
Problem Statement
The organization is collecting very sensitive and personal information that needs to be
protected in manner to let the organization’s workflow in an efficient and effective manner. Data
and information stored in the cloud are vulnerable to the intrusion and data breaches and thus,
proper precautions are very crucial in the context of the long run for the company. Expose of
personal and sensitive information have may negative impacts on the organization’s reputation,
and privacy and security of the stakeholders associated with the organization. Expose of such
crucial information could even led to the closure of the organization and thus, it has been the
greatest concern for the IIL in manner to allow employees and staffs to accomplish the daily
operational activities. RAP as a Service can be proposed as an effective approach towards
enhancing the security of the network that will be allowing the organization to hire a third party
responsible for managing the security of the data and information.
Period of Performance
The period of performance would be approximately six months (180 days) as it will
started at May 7, 2018 and will be ending at January 25, 2019. The activities and schedule
mentioned in the below report demonstrates the list of the activities, milestones and their
delivery in manner to accomplish the objectives of the project. The proposed work will be
delivered through utilizing the agile methodology and all the changes will be accepted during the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
execution of the project however; approval from the executives of the IIL and the third party will
be necessary to implement and modify the workflow.
Requirement Specifications
Kickoff: all the stakeholders need to agree on the same point as a solution and they will
have to approve the planning and solution proposed to the organization. It will include the
schedule, work breakdown structure, budget, transition plan, implementation plan, and training.
After reviewing this, the executives of the organization will have to provide approval for further
execution of the project.
Identification of the current environment: The IT infrastructure present for managing the
operational activities that is necessary for the feasibility and compliance of the proposed solution
with the existing system of the IIL. This will be helpful in identifying the problems, features, and
requirements of the organization.
Evaluation of proposed solution: RAP as a Service is capable of solving the existing and
identified solution however; it is a vital objective to consider its compliance with the existing
system, and whether it will be able to fulfill the needs and requirements of the organization or
not.
Execution phase: The execution phase will include the transformation on the IT
infrastructure and implementation of the RAP as a Service for the establishment of the security
within the existing system of the organization. This will also include the Instalment of the RAP
and configuration those need to be made according to the requirements of the IIL considering the
access level and authority of the web access for the employees and staffs. The third party will
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
execution of the project however; approval from the executives of the IIL and the third party will
be necessary to implement and modify the workflow.
Requirement Specifications
Kickoff: all the stakeholders need to agree on the same point as a solution and they will
have to approve the planning and solution proposed to the organization. It will include the
schedule, work breakdown structure, budget, transition plan, implementation plan, and training.
After reviewing this, the executives of the organization will have to provide approval for further
execution of the project.
Identification of the current environment: The IT infrastructure present for managing the
operational activities that is necessary for the feasibility and compliance of the proposed solution
with the existing system of the IIL. This will be helpful in identifying the problems, features, and
requirements of the organization.
Evaluation of proposed solution: RAP as a Service is capable of solving the existing and
identified solution however; it is a vital objective to consider its compliance with the existing
system, and whether it will be able to fulfill the needs and requirements of the organization or
not.
Execution phase: The execution phase will include the transformation on the IT
infrastructure and implementation of the RAP as a Service for the establishment of the security
within the existing system of the organization. This will also include the Instalment of the RAP
and configuration those need to be made according to the requirements of the IIL considering the
access level and authority of the web access for the employees and staffs. The third party will
5
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
manage the installment however; the infrastructure will have to be established by the
organization itself.
Auditing and Training: This phase will be emphasizing on the evaluation of the proposed
solution that will be helpful in identifying the level of security for the data and information being
collected and stored in the cloud by IIL. Education and training is one of the most crucial aspect
for enhancing the efficiency of the new system proposed as a solution for the problem. It will
allow the users to understand and learn about the functioning of the proposed solution ad hoe it
can be utilized with higher efficiency.
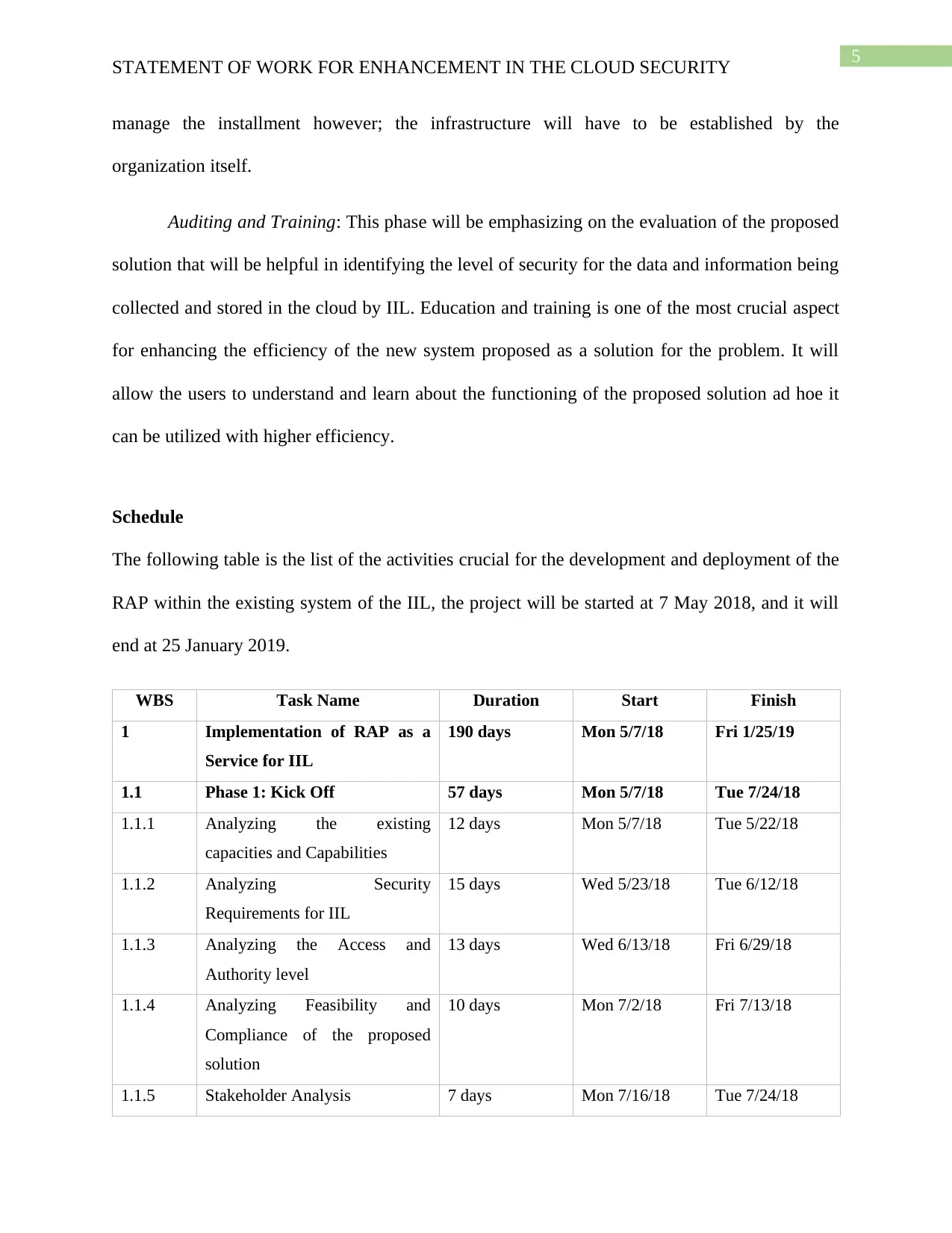
Schedule
The following table is the list of the activities crucial for the development and deployment of the
RAP within the existing system of the IIL, the project will be started at 7 May 2018, and it will
end at 25 January 2019.
WBS Task Name Duration Start Finish
1 Implementation of RAP as a
Service for IIL
190 days Mon 5/7/18 Fri 1/25/19
1.1 Phase 1: Kick Off 57 days Mon 5/7/18 Tue 7/24/18
1.1.1 Analyzing the existing
capacities and Capabilities
12 days Mon 5/7/18 Tue 5/22/18
1.1.2 Analyzing Security
Requirements for IIL
15 days Wed 5/23/18 Tue 6/12/18
1.1.3 Analyzing the Access and
Authority level
13 days Wed 6/13/18 Fri 6/29/18
1.1.4 Analyzing Feasibility and
Compliance of the proposed
solution
10 days Mon 7/2/18 Fri 7/13/18
1.1.5 Stakeholder Analysis 7 days Mon 7/16/18 Tue 7/24/18
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
manage the installment however; the infrastructure will have to be established by the
organization itself.
Auditing and Training: This phase will be emphasizing on the evaluation of the proposed
solution that will be helpful in identifying the level of security for the data and information being
collected and stored in the cloud by IIL. Education and training is one of the most crucial aspect
for enhancing the efficiency of the new system proposed as a solution for the problem. It will
allow the users to understand and learn about the functioning of the proposed solution ad hoe it
can be utilized with higher efficiency.
Schedule
The following table is the list of the activities crucial for the development and deployment of the
RAP within the existing system of the IIL, the project will be started at 7 May 2018, and it will
end at 25 January 2019.
WBS Task Name Duration Start Finish
1 Implementation of RAP as a
Service for IIL
190 days Mon 5/7/18 Fri 1/25/19
1.1 Phase 1: Kick Off 57 days Mon 5/7/18 Tue 7/24/18
1.1.1 Analyzing the existing
capacities and Capabilities
12 days Mon 5/7/18 Tue 5/22/18
1.1.2 Analyzing Security
Requirements for IIL
15 days Wed 5/23/18 Tue 6/12/18
1.1.3 Analyzing the Access and
Authority level
13 days Wed 6/13/18 Fri 6/29/18
1.1.4 Analyzing Feasibility and
Compliance of the proposed
solution
10 days Mon 7/2/18 Fri 7/13/18
1.1.5 Stakeholder Analysis 7 days Mon 7/16/18 Tue 7/24/18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
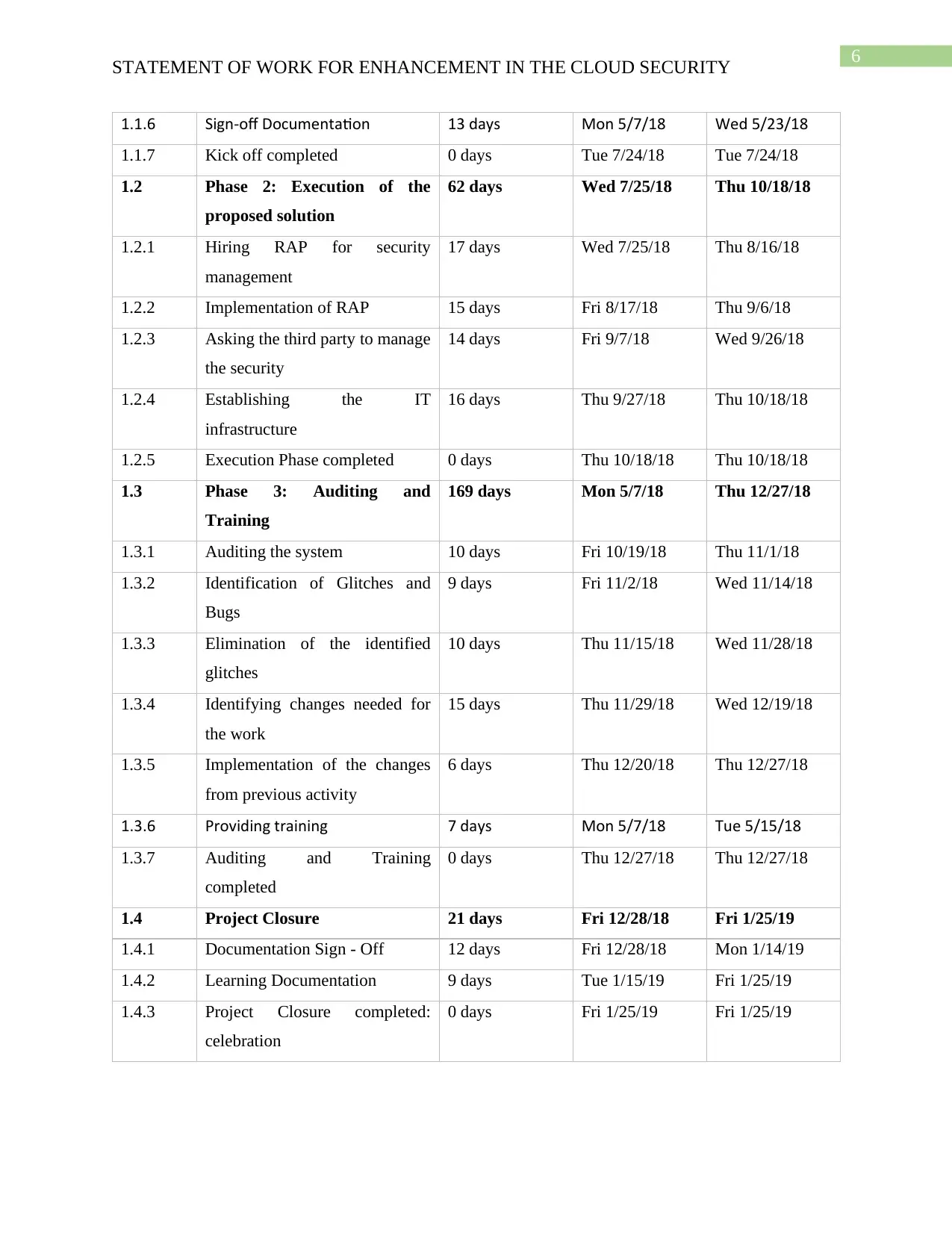
1.1.6 Sign-off Documentation 13 days Mon 5/7/18 Wed 5/23/18
1.1.7 Kick off completed 0 days Tue 7/24/18 Tue 7/24/18
1.2 Phase 2: Execution of the
proposed solution
62 days Wed 7/25/18 Thu 10/18/18
1.2.1 Hiring RAP for security
management
17 days Wed 7/25/18 Thu 8/16/18
1.2.2 Implementation of RAP 15 days Fri 8/17/18 Thu 9/6/18
1.2.3 Asking the third party to manage
the security
14 days Fri 9/7/18 Wed 9/26/18
1.2.4 Establishing the IT
infrastructure
16 days Thu 9/27/18 Thu 10/18/18
1.2.5 Execution Phase completed 0 days Thu 10/18/18 Thu 10/18/18
1.3 Phase 3: Auditing and
Training
169 days Mon 5/7/18 Thu 12/27/18
1.3.1 Auditing the system 10 days Fri 10/19/18 Thu 11/1/18
1.3.2 Identification of Glitches and
Bugs
9 days Fri 11/2/18 Wed 11/14/18
1.3.3 Elimination of the identified
glitches
10 days Thu 11/15/18 Wed 11/28/18
1.3.4 Identifying changes needed for
the work
15 days Thu 11/29/18 Wed 12/19/18
1.3.5 Implementation of the changes
from previous activity
6 days Thu 12/20/18 Thu 12/27/18
1.3.6 Providing training 7 days Mon 5/7/18 Tue 5/15/18
1.3.7 Auditing and Training
completed
0 days Thu 12/27/18 Thu 12/27/18
1.4 Project Closure 21 days Fri 12/28/18 Fri 1/25/19
1.4.1 Documentation Sign - Off 12 days Fri 12/28/18 Mon 1/14/19
1.4.2 Learning Documentation 9 days Tue 1/15/19 Fri 1/25/19
1.4.3 Project Closure completed:
celebration
0 days Fri 1/25/19 Fri 1/25/19
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
1.1.6 Sign-off Documentation 13 days Mon 5/7/18 Wed 5/23/18
1.1.7 Kick off completed 0 days Tue 7/24/18 Tue 7/24/18
1.2 Phase 2: Execution of the
proposed solution
62 days Wed 7/25/18 Thu 10/18/18
1.2.1 Hiring RAP for security
management
17 days Wed 7/25/18 Thu 8/16/18
1.2.2 Implementation of RAP 15 days Fri 8/17/18 Thu 9/6/18
1.2.3 Asking the third party to manage
the security
14 days Fri 9/7/18 Wed 9/26/18
1.2.4 Establishing the IT
infrastructure
16 days Thu 9/27/18 Thu 10/18/18
1.2.5 Execution Phase completed 0 days Thu 10/18/18 Thu 10/18/18
1.3 Phase 3: Auditing and
Training
169 days Mon 5/7/18 Thu 12/27/18
1.3.1 Auditing the system 10 days Fri 10/19/18 Thu 11/1/18
1.3.2 Identification of Glitches and
Bugs
9 days Fri 11/2/18 Wed 11/14/18
1.3.3 Elimination of the identified
glitches
10 days Thu 11/15/18 Wed 11/28/18
1.3.4 Identifying changes needed for
the work
15 days Thu 11/29/18 Wed 12/19/18
1.3.5 Implementation of the changes
from previous activity
6 days Thu 12/20/18 Thu 12/27/18
1.3.6 Providing training 7 days Mon 5/7/18 Tue 5/15/18
1.3.7 Auditing and Training
completed
0 days Thu 12/27/18 Thu 12/27/18
1.4 Project Closure 21 days Fri 12/28/18 Fri 1/25/19
1.4.1 Documentation Sign - Off 12 days Fri 12/28/18 Mon 1/14/19
1.4.2 Learning Documentation 9 days Tue 1/15/19 Fri 1/25/19
1.4.3 Project Closure completed:
celebration
0 days Fri 1/25/19 Fri 1/25/19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Acceptance Criteria
The proposed solution should must follow the policies and regulations set by the
organization for the security and privacy of the data and information being collected about the
stakeholders involved in the project. The Executives of the IIL must be agree on delivering this
project after identifying the capabilities of eliminating the problem. The executives should
approve the changes and deformation introduced by the vendor or the project manager if certain
changes need to be implemented in the middle of the project execution ensuring the management
of the security. The schedule and the budget of the project should not exceed by 10%, as it has
been consider at the contingency plan and escalation in the time, budget will affect the delivery
of the project, and thus, organization will be similarly affected.
Other Requirements
Legal agreement between the vendor and the organization should be documented in
manner to assure the agreement between both the parties and restricting the changes in between
of the project. The organization is sharing the most crucial part as the information is the key to
business and thus, legal contracts and complying paper must be evaluated and signed-off
between them.
Technologies Required
IT infrastructure, RAP as a Service, access control, different authorization level, data
backup, proper and simple user interface system, proper API are the technological requirements
for the successful deployment of the proposed work. These are crucial aspect for the third party
who will be restricting the web access and securing the internal environment of the organization.
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Acceptance Criteria
The proposed solution should must follow the policies and regulations set by the
organization for the security and privacy of the data and information being collected about the
stakeholders involved in the project. The Executives of the IIL must be agree on delivering this
project after identifying the capabilities of eliminating the problem. The executives should
approve the changes and deformation introduced by the vendor or the project manager if certain
changes need to be implemented in the middle of the project execution ensuring the management
of the security. The schedule and the budget of the project should not exceed by 10%, as it has
been consider at the contingency plan and escalation in the time, budget will affect the delivery
of the project, and thus, organization will be similarly affected.
Other Requirements
Legal agreement between the vendor and the organization should be documented in
manner to assure the agreement between both the parties and restricting the changes in between
of the project. The organization is sharing the most crucial part as the information is the key to
business and thus, legal contracts and complying paper must be evaluated and signed-off
between them.
Technologies Required
IT infrastructure, RAP as a Service, access control, different authorization level, data
backup, proper and simple user interface system, proper API are the technological requirements
for the successful deployment of the proposed work. These are crucial aspect for the third party
who will be restricting the web access and securing the internal environment of the organization.
8
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
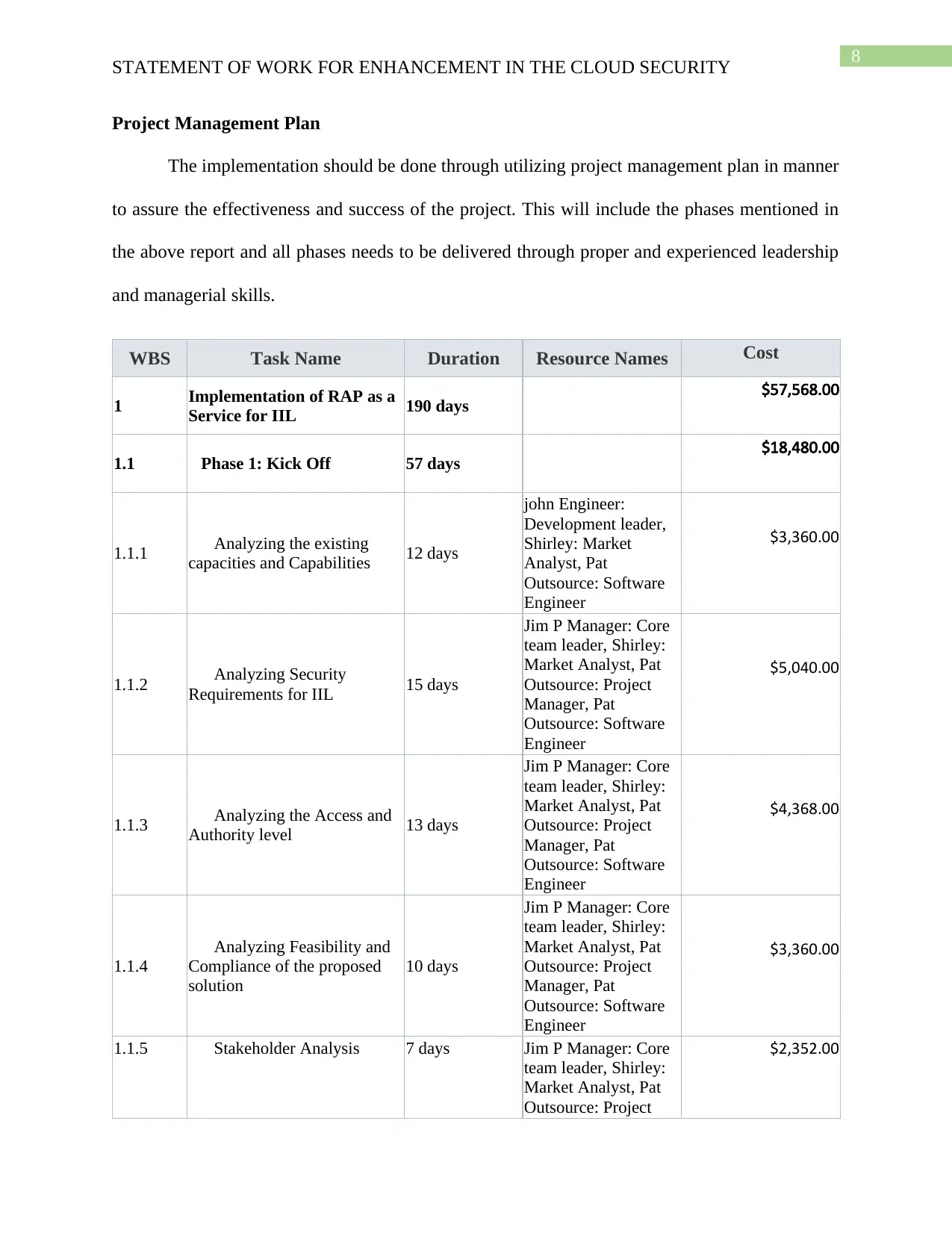
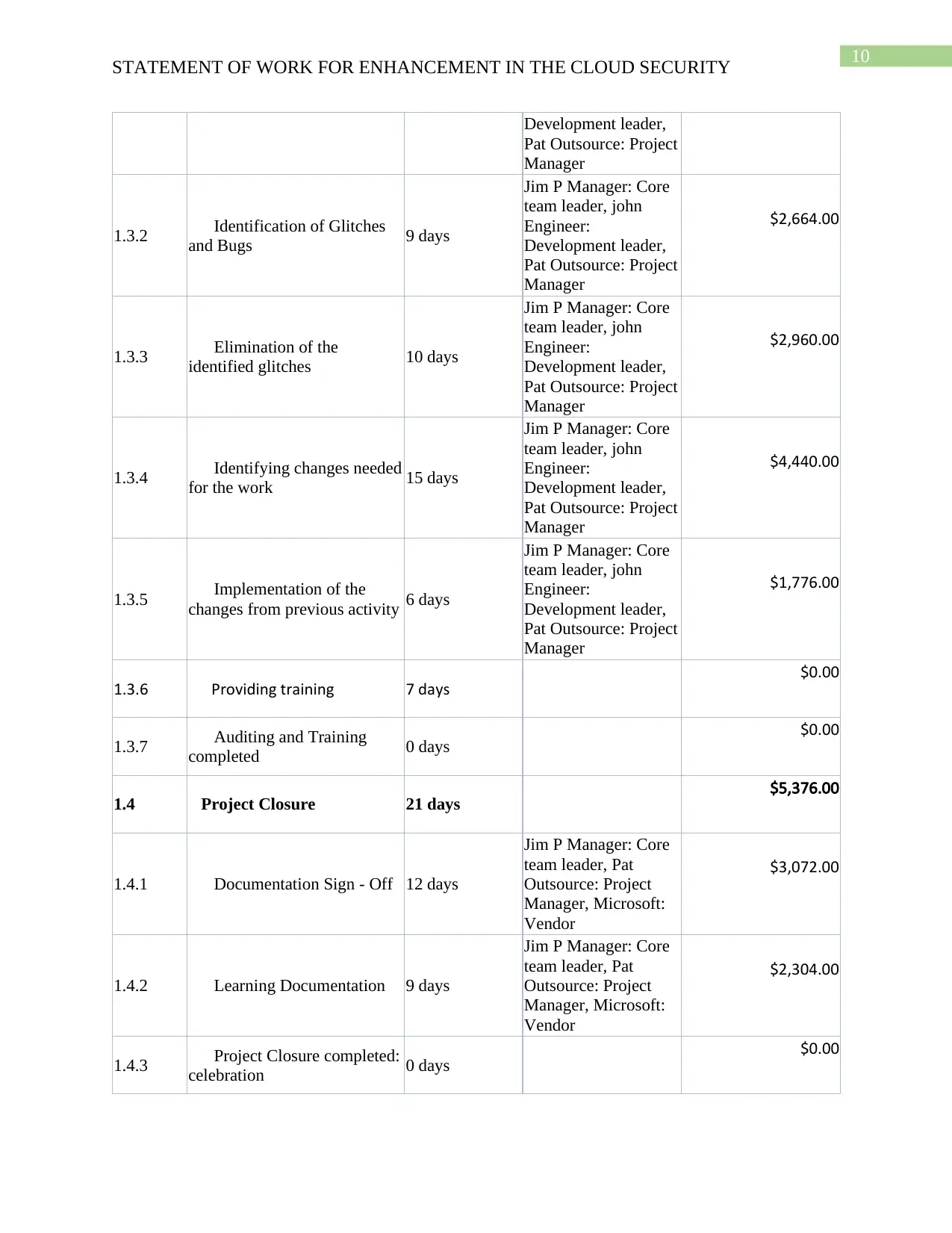
Project Management Plan
The implementation should be done through utilizing project management plan in manner
to assure the effectiveness and success of the project. This will include the phases mentioned in
the above report and all phases needs to be delivered through proper and experienced leadership
and managerial skills.
WBS Task Name Duration Resource Names Cost
1 Implementation of RAP as a
Service for IIL 190 days $57,568.00
1.1 Phase 1: Kick Off 57 days $18,480.00
1.1.1 Analyzing the existing
capacities and Capabilities 12 days
john Engineer:
Development leader,
Shirley: Market
Analyst, Pat
Outsource: Software
Engineer
$3,360.00
1.1.2 Analyzing Security
Requirements for IIL 15 days
Jim P Manager: Core
team leader, Shirley:
Market Analyst, Pat
Outsource: Project
Manager, Pat
Outsource: Software
Engineer
$5,040.00
1.1.3 Analyzing the Access and
Authority level 13 days
Jim P Manager: Core
team leader, Shirley:
Market Analyst, Pat
Outsource: Project
Manager, Pat
Outsource: Software
Engineer
$4,368.00
1.1.4
Analyzing Feasibility and
Compliance of the proposed
solution
10 days
Jim P Manager: Core
team leader, Shirley:
Market Analyst, Pat
Outsource: Project
Manager, Pat
Outsource: Software
Engineer
$3,360.00
1.1.5 Stakeholder Analysis 7 days Jim P Manager: Core
team leader, Shirley:
Market Analyst, Pat
Outsource: Project
$2,352.00
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Project Management Plan
The implementation should be done through utilizing project management plan in manner
to assure the effectiveness and success of the project. This will include the phases mentioned in
the above report and all phases needs to be delivered through proper and experienced leadership
and managerial skills.
WBS Task Name Duration Resource Names Cost
1 Implementation of RAP as a
Service for IIL 190 days $57,568.00
1.1 Phase 1: Kick Off 57 days $18,480.00
1.1.1 Analyzing the existing
capacities and Capabilities 12 days
john Engineer:
Development leader,
Shirley: Market
Analyst, Pat
Outsource: Software
Engineer
$3,360.00
1.1.2 Analyzing Security
Requirements for IIL 15 days
Jim P Manager: Core
team leader, Shirley:
Market Analyst, Pat
Outsource: Project
Manager, Pat
Outsource: Software
Engineer
$5,040.00
1.1.3 Analyzing the Access and
Authority level 13 days
Jim P Manager: Core
team leader, Shirley:
Market Analyst, Pat
Outsource: Project
Manager, Pat
Outsource: Software
Engineer
$4,368.00
1.1.4
Analyzing Feasibility and
Compliance of the proposed
solution
10 days
Jim P Manager: Core
team leader, Shirley:
Market Analyst, Pat
Outsource: Project
Manager, Pat
Outsource: Software
Engineer
$3,360.00
1.1.5 Stakeholder Analysis 7 days Jim P Manager: Core
team leader, Shirley:
Market Analyst, Pat
Outsource: Project
$2,352.00
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
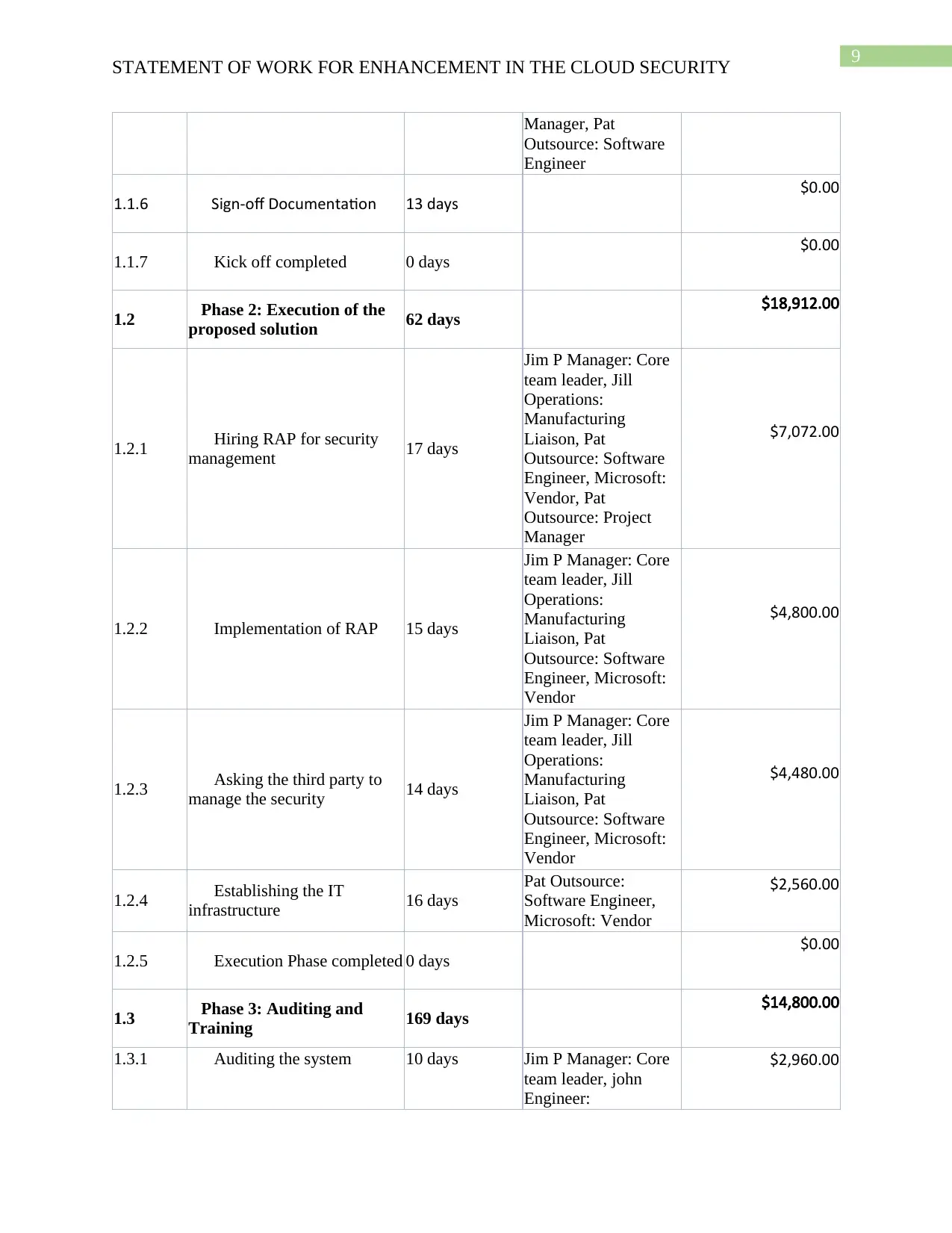
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Manager, Pat
Outsource: Software
Engineer
1.1.6 Sign-off Documentation 13 days $0.00
1.1.7 Kick off completed 0 days $0.00
1.2 Phase 2: Execution of the
proposed solution 62 days $18,912.00
1.2.1 Hiring RAP for security
management 17 days
Jim P Manager: Core
team leader, Jill
Operations:
Manufacturing
Liaison, Pat
Outsource: Software
Engineer, Microsoft:
Vendor, Pat
Outsource: Project
Manager
$7,072.00
1.2.2 Implementation of RAP 15 days
Jim P Manager: Core
team leader, Jill
Operations:
Manufacturing
Liaison, Pat
Outsource: Software
Engineer, Microsoft:
Vendor
$4,800.00
1.2.3 Asking the third party to
manage the security 14 days
Jim P Manager: Core
team leader, Jill
Operations:
Manufacturing
Liaison, Pat
Outsource: Software
Engineer, Microsoft:
Vendor
$4,480.00
1.2.4 Establishing the IT
infrastructure 16 days
Pat Outsource:
Software Engineer,
Microsoft: Vendor
$2,560.00
1.2.5 Execution Phase completed 0 days $0.00
1.3 Phase 3: Auditing and
Training 169 days $14,800.00
1.3.1 Auditing the system 10 days Jim P Manager: Core
team leader, john
Engineer:
$2,960.00
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Manager, Pat
Outsource: Software
Engineer
1.1.6 Sign-off Documentation 13 days $0.00
1.1.7 Kick off completed 0 days $0.00
1.2 Phase 2: Execution of the
proposed solution 62 days $18,912.00
1.2.1 Hiring RAP for security
management 17 days
Jim P Manager: Core
team leader, Jill
Operations:
Manufacturing
Liaison, Pat
Outsource: Software
Engineer, Microsoft:
Vendor, Pat
Outsource: Project
Manager
$7,072.00
1.2.2 Implementation of RAP 15 days
Jim P Manager: Core
team leader, Jill
Operations:
Manufacturing
Liaison, Pat
Outsource: Software
Engineer, Microsoft:
Vendor
$4,800.00
1.2.3 Asking the third party to
manage the security 14 days
Jim P Manager: Core
team leader, Jill
Operations:
Manufacturing
Liaison, Pat
Outsource: Software
Engineer, Microsoft:
Vendor
$4,480.00
1.2.4 Establishing the IT
infrastructure 16 days
Pat Outsource:
Software Engineer,
Microsoft: Vendor
$2,560.00
1.2.5 Execution Phase completed 0 days $0.00
1.3 Phase 3: Auditing and
Training 169 days $14,800.00
1.3.1 Auditing the system 10 days Jim P Manager: Core
team leader, john
Engineer:
$2,960.00
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Development leader,
Pat Outsource: Project
Manager
1.3.2 Identification of Glitches
and Bugs 9 days
Jim P Manager: Core
team leader, john
Engineer:
Development leader,
Pat Outsource: Project
Manager
$2,664.00
1.3.3 Elimination of the
identified glitches 10 days
Jim P Manager: Core
team leader, john
Engineer:
Development leader,
Pat Outsource: Project
Manager
$2,960.00
1.3.4 Identifying changes needed
for the work 15 days
Jim P Manager: Core
team leader, john
Engineer:
Development leader,
Pat Outsource: Project
Manager
$4,440.00
1.3.5 Implementation of the
changes from previous activity 6 days
Jim P Manager: Core
team leader, john
Engineer:
Development leader,
Pat Outsource: Project
Manager
$1,776.00
1.3.6 Providing training 7 days $0.00
1.3.7 Auditing and Training
completed 0 days $0.00
1.4 Project Closure 21 days $5,376.00
1.4.1 Documentation Sign - Off 12 days
Jim P Manager: Core
team leader, Pat
Outsource: Project
Manager, Microsoft:
Vendor
$3,072.00
1.4.2 Learning Documentation 9 days
Jim P Manager: Core
team leader, Pat
Outsource: Project
Manager, Microsoft:
Vendor
$2,304.00
1.4.3 Project Closure completed:
celebration 0 days $0.00
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Development leader,
Pat Outsource: Project
Manager
1.3.2 Identification of Glitches
and Bugs 9 days
Jim P Manager: Core
team leader, john
Engineer:
Development leader,
Pat Outsource: Project
Manager
$2,664.00
1.3.3 Elimination of the
identified glitches 10 days
Jim P Manager: Core
team leader, john
Engineer:
Development leader,
Pat Outsource: Project
Manager
$2,960.00
1.3.4 Identifying changes needed
for the work 15 days
Jim P Manager: Core
team leader, john
Engineer:
Development leader,
Pat Outsource: Project
Manager
$4,440.00
1.3.5 Implementation of the
changes from previous activity 6 days
Jim P Manager: Core
team leader, john
Engineer:
Development leader,
Pat Outsource: Project
Manager
$1,776.00
1.3.6 Providing training 7 days $0.00
1.3.7 Auditing and Training
completed 0 days $0.00
1.4 Project Closure 21 days $5,376.00
1.4.1 Documentation Sign - Off 12 days
Jim P Manager: Core
team leader, Pat
Outsource: Project
Manager, Microsoft:
Vendor
$3,072.00
1.4.2 Learning Documentation 9 days
Jim P Manager: Core
team leader, Pat
Outsource: Project
Manager, Microsoft:
Vendor
$2,304.00
1.4.3 Project Closure completed:
celebration 0 days $0.00
11
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Following Gantt chart will be describing the visual representation of the activities, schedule, and
resources being utilized for the execution of the project
STATEMENT OF WORK FOR ENHANCEMENT IN THE CLOUD SECURITY
Following Gantt chart will be describing the visual representation of the activities, schedule, and
resources being utilized for the execution of the project
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





